山石2022冬令营结营赛
前言
第一次参加CTF冬令营,师傅们讲的都很好,也学到了不少东西,结营赛没想到WEB都是0解,题目质量很高,只能在其他方向上拿点分了,最终排名第四,继续加油吧,距离大佬还差的很远
签到题
关注公众号发送签到题得到flag
hsnctf{welcome_to_hsnctf}
daobudao
base64解码得到kvqfwi{j00g_oxfn_kdyh_ixq}
凯撒解密,得到flag
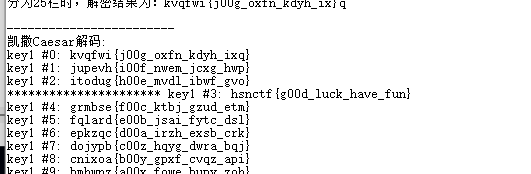
hsnctf{g00d_luck_have_fun}
S7_analysis
0x29 - PLC Stop,查询得到两组数据
s7comm.param.func == 0x29
399 269.522771 192.168.1.103 95.182.246.171 S7COMM 87 ROSCTR:[Job ] Function:[PLC Stop]得到编号399,所以得到flag
hsnctf{399}
外星电波~
首先文件内容是base64,python脚本转一下发现是pk头
保存为pk文件
import base64
with open("./flag.txt", "r") as f:
data = base64.b64decode(f.read())
#print(data)
file = open("flag.zip", "wb")
file.write(data)发现需要密码
然后使用ntfs隐写解密得到wav音频

然后sstv隐写得到压缩包密码passwd@hillstone
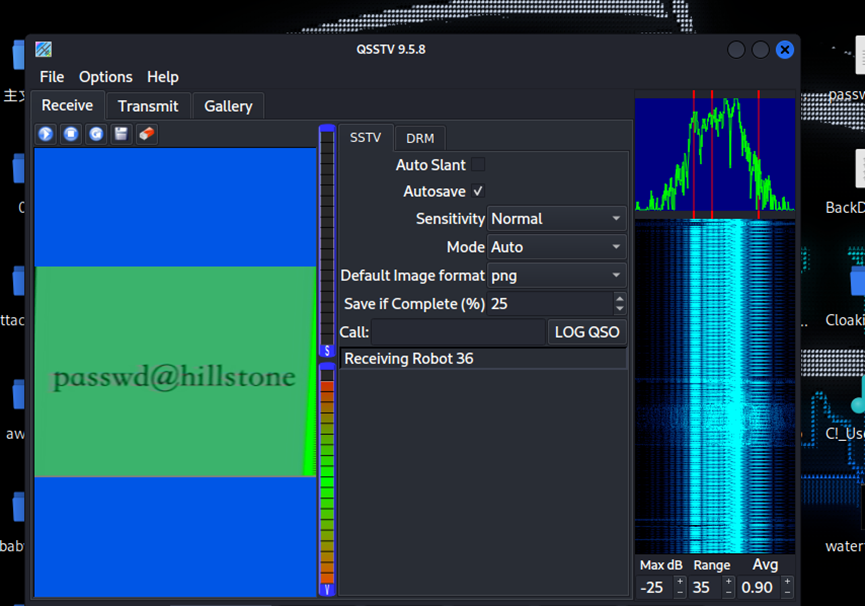
解压得到flag
hsnctf{70995fb0-eb60-0787-f305-77066aeb6730}
extract
看文件附件就是提示Cloakify,然后去github下载工具进行解密
https://github.com/TryCatchHCF/Cloakify/blob/master/cloakifyFactory.py
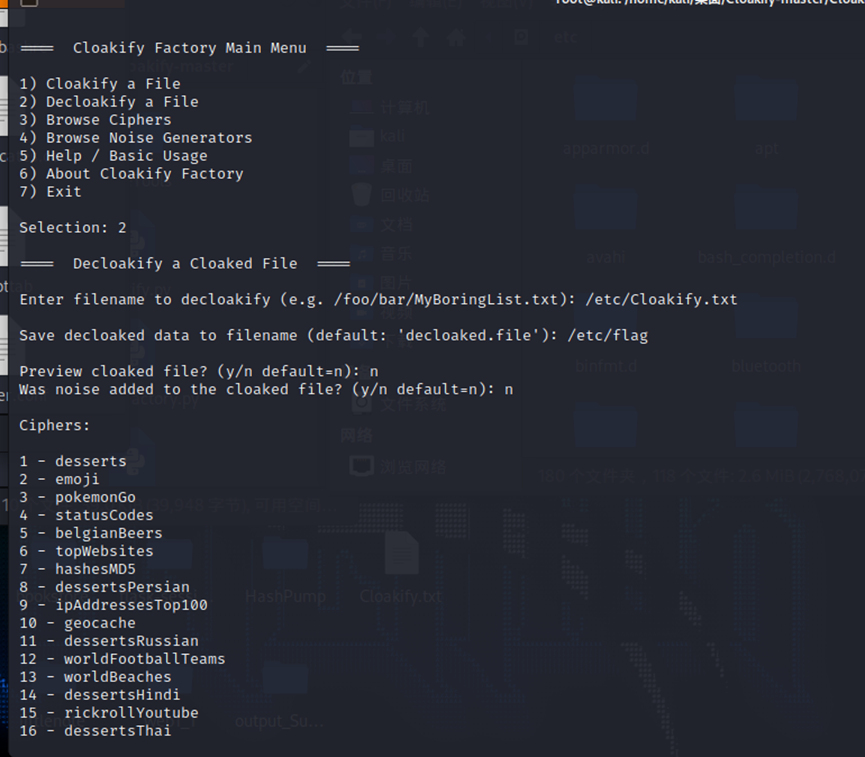
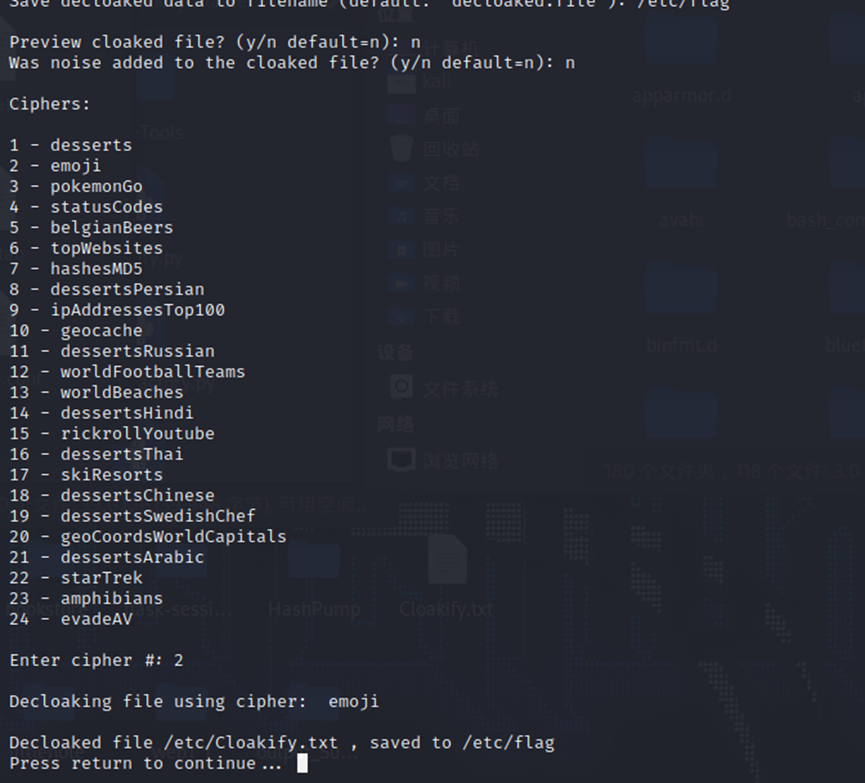
得到flag文件是压缩包
解压发现是套娃,解压2332次左右就会得到flag文件
脚本如下
import zipfile
import re
zipname = "C:\\Users\\25963\\Desktop\\flag\\"+"f2332.zip"
while True:
if zipname != "C:\\Users\\25963\\Desktop\\flag\\flag.txt":
ts1 = zipfile.ZipFile(zipname)
print (ts1.namelist()[0])
res = re.search('[0-9]*',ts1.namelist()[0])
print (res.group())
passwd = res.group()
ts1.extractall("C:\\Users\\25963\\Desktop\\flag\\",pwd=passwd)
zipname = "C:\\Users\\25963\\Desktop\\flag\\"+ts1.namelist()[0]
else:
print ("find")得到flag
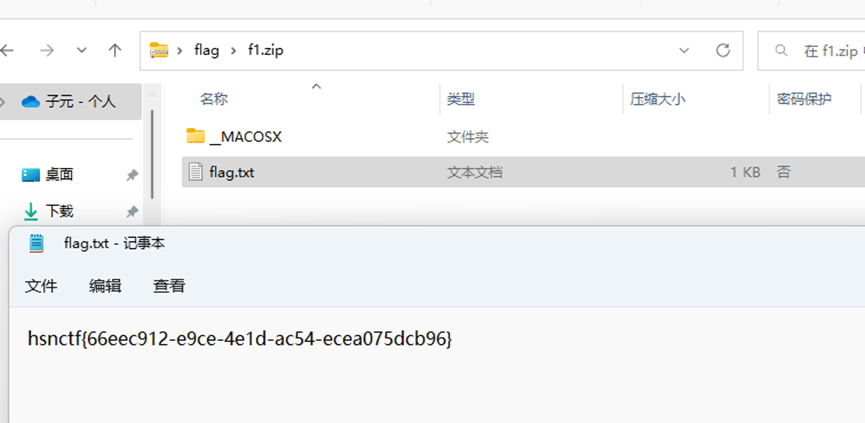
hsnctf{66eec912-e9ce-4e1d-ac54-ecea075dcb96}
re_easy
查壳
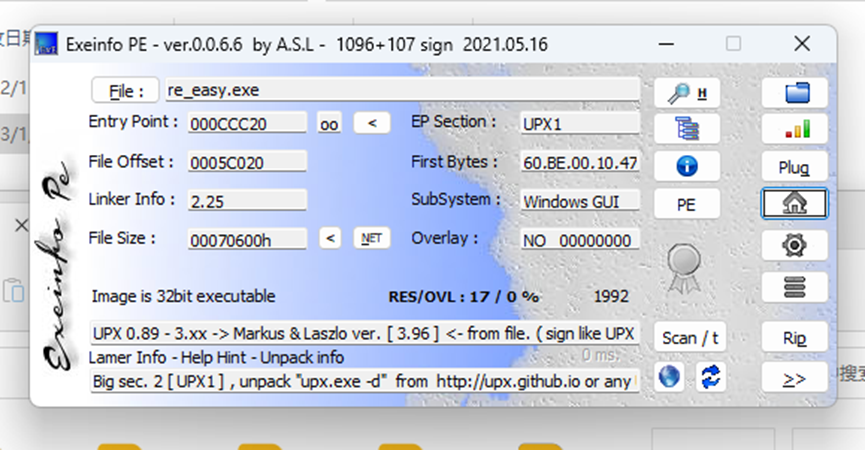
Upx先用upx shell脱壳

寻找到数据
7,127,121,92,110,67,101,84,3,71,4,82,122,111,121,2,5,71,117,2,109,99,101,71,3,100,113,77脚本如下
s=[7,127,121,92,110,67,101,84,3,71,4,82,122,111,121,2,5,71,117,2,109,99,101,71,3,100,113,77]
print(''.join(chr(c^55)for c in s))得到
0HNkYtRc4p3eMXN52pB5ZTRp4SFz
Ida打开可以得到base64码表,解码得到flag
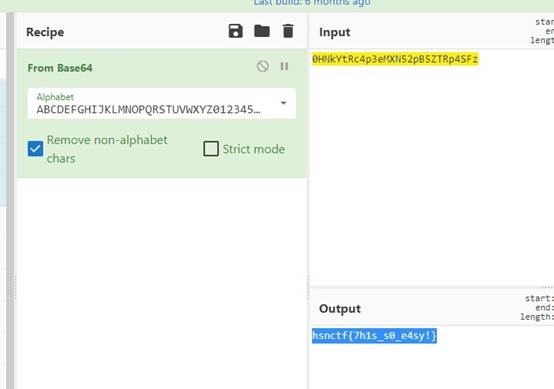
hsnctf{7h1s_s0_e4sy}
Babypy
脚本如下
import random
from Crypto.Util.number import long_to_bytes
from Crypto.Cipher import AES
ans0 = b'\xa2\xeb\xbb\n9\xb70\xc8G\x84h\xd9\xd0\xf1\xf9\x13/_\xa7\xe4f\xbeN\xfaw.i\x067\xd1\x02^'
random.seed(12648430)
shuf1 = [i for i in range(32)]
random.shuffle(shuf1)
shuf2 = [i for i in range(32)]
random.shuffle(shuf2)
a = []
b = []
for _ in range(32):
a.append(random.randint(0, 255))
b.append(random.randint(0, 255))
shuf3 = [i for i in range(32)]
random.shuffle(shuf3)
key = long_to_bytes(random.getrandbits(256))
aes = AES.new(key, AES.MODE_ECB)
ans1 = aes.decrypt(ans0)
ans1 = list(ans1)
ans2 = [0 for _ in range(32)]
for i in range(32):
ans2[shuf3[i]] = ans1[i]
for i in range(32):
ans2[shuf2[i]] ^= a[i] ^ b[i]
ans3 = [0 for _ in range(32)]
for i in range(32):
ans3[shuf1[i]] = ans2[i]
print(ans3)得到104, 115, 110, 99, 116, 102, 123, 82, 52, 110, 100, 111, 109, 95, 113, 117, 49, 116, 101, 95, 105, 110, 116, 51, 114, 101, 115, 116, 105, 110, 57, 125
十进制转Hex转str得到flag(ps:手搓的)
hsnctf{R4ndom_qu1te_int3restin9}
HSAndroid1
首先反编译apk
找到主函数进行分析,找到S和·Key
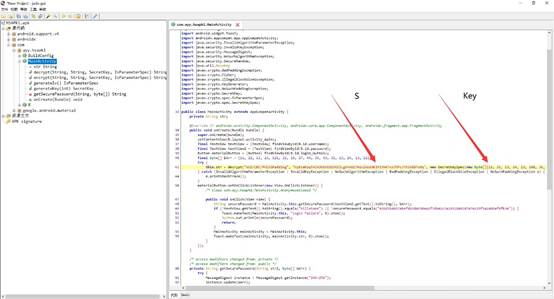
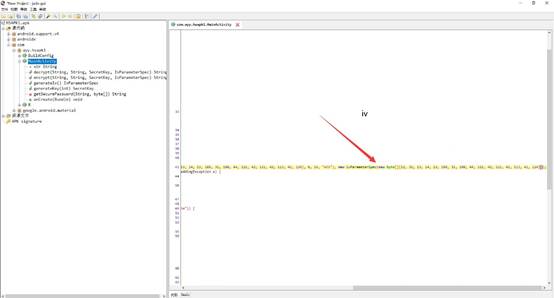
主体逻辑如上,先进行aes解迷然后进行base64解码即可得到flag
代码如下
from Crypto.Cipher import *
s= "HyKsaPpqT4l436tHiSEXtIlLgVV4GE7mGc2WoI0KlP2YhKFco7OPcJYtS58BFwDq"
key=[12, 32, 13, 14, 23, 108, 31, 108, 44, 121, 42, 121, 42, 113, 41, 124]
key=''.join(map(chr,key))
iv=[12, 32, 13, 14, 23, 108, 31, 108, 44, 121, 42, 121, 42, 113, 41, 124]
iv = ''.join(map(chr,iv))
obj = AES.new(key,AES.MODE_CBC,iv)
obj.decrypt(s.decode('base64'))
#'hsnctf{android_is_not_e4sy_will_caref1ul}\x07\x07\x07\x07\x07\x07\x07'得到flag
hsnctf{android_is_not_e4sy_will_caref1ul}

