国外的比赛,参加一些,多见见题型,大部分都是web,其他的也涉及了一点,就会这些。。。我还是fw,心态炸了。
Web
real deal html
I have just made the most ultimate html site. This site, this html. This is the real deal
看源代码得到flag
bcactf{tH4TZ_D4_R34l_D3Al_cb8949}
Agent Rocket
I need to launch the BCA CTF ROCKET to the moon! Unfortunately I lost my launch code (flag). You can find the launch code in the control panel.
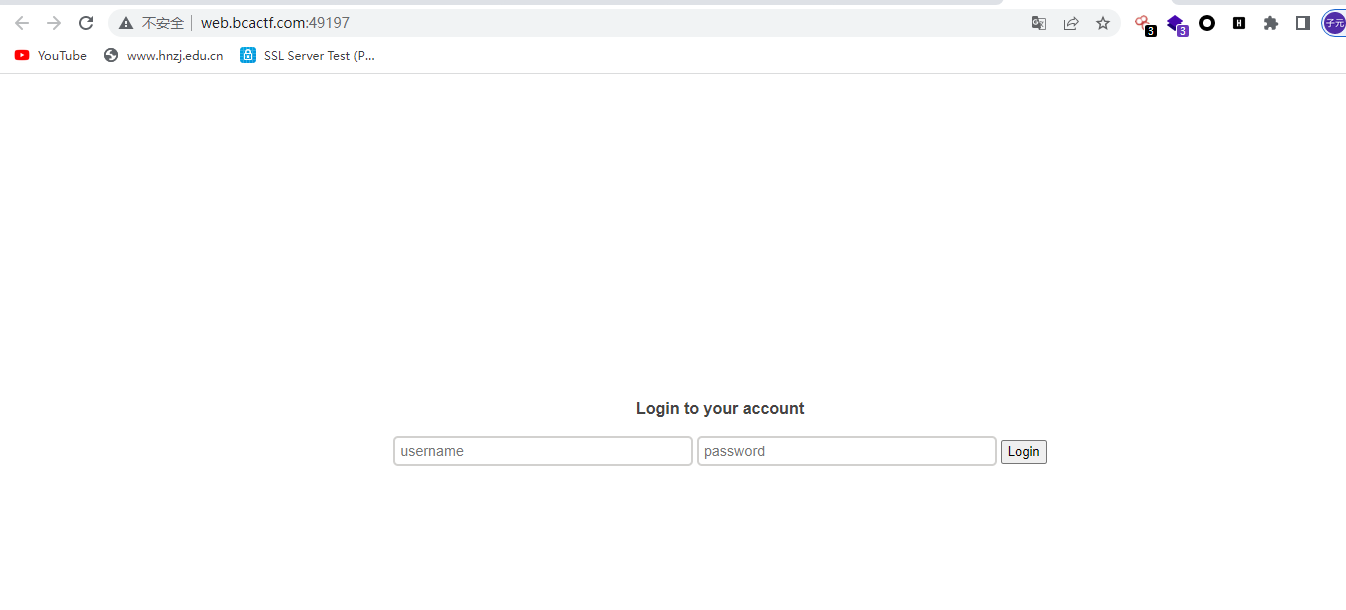
看源码得到提示,你说不是就不是了?我偏要试试
成功登陆进去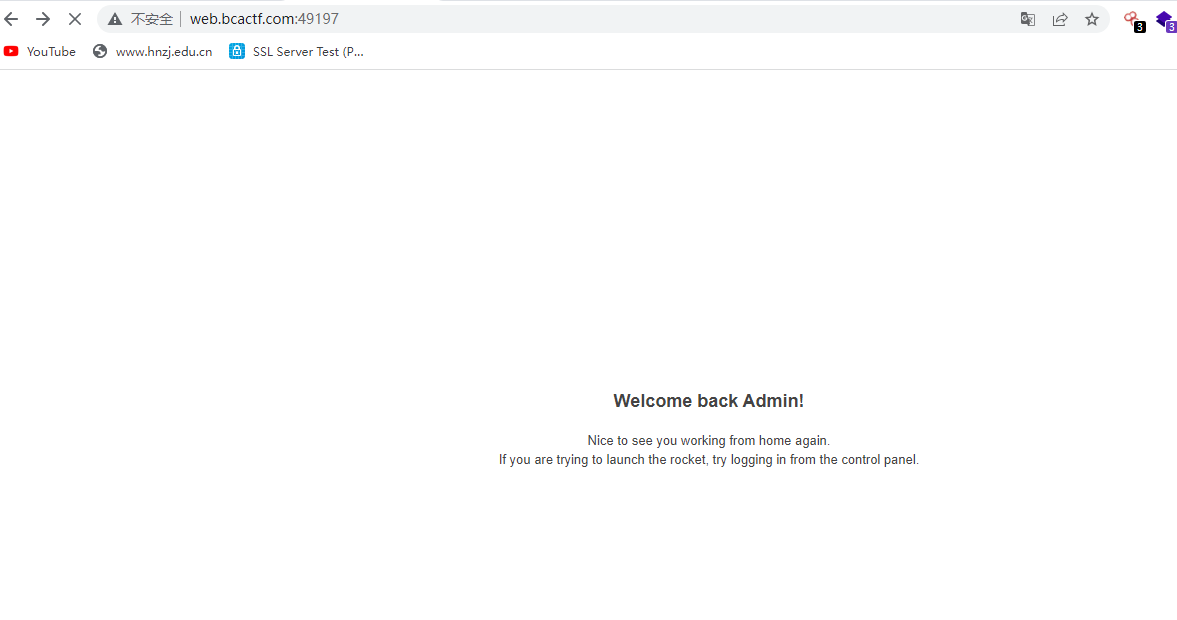
没啥利用点,继续看源码,得到提示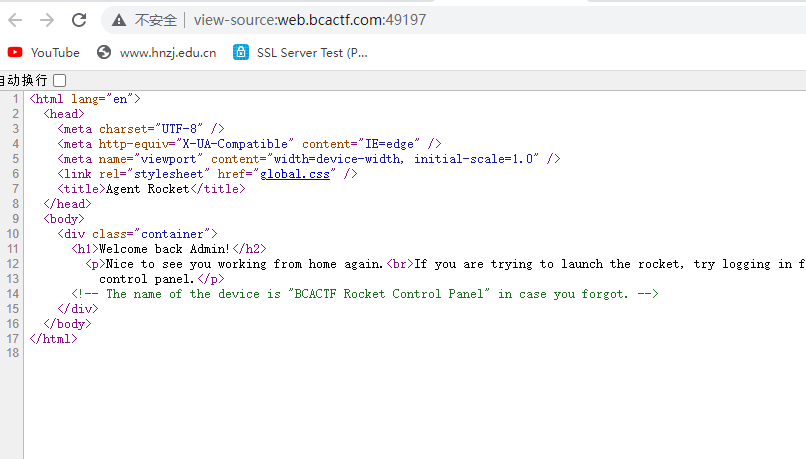
一开始我在想控制面板的地址是啥,一直不知道,看到题目提示说在这个页面是进不去控制面板的,很不解,问了一下学长,需要修改UA头,得到flag
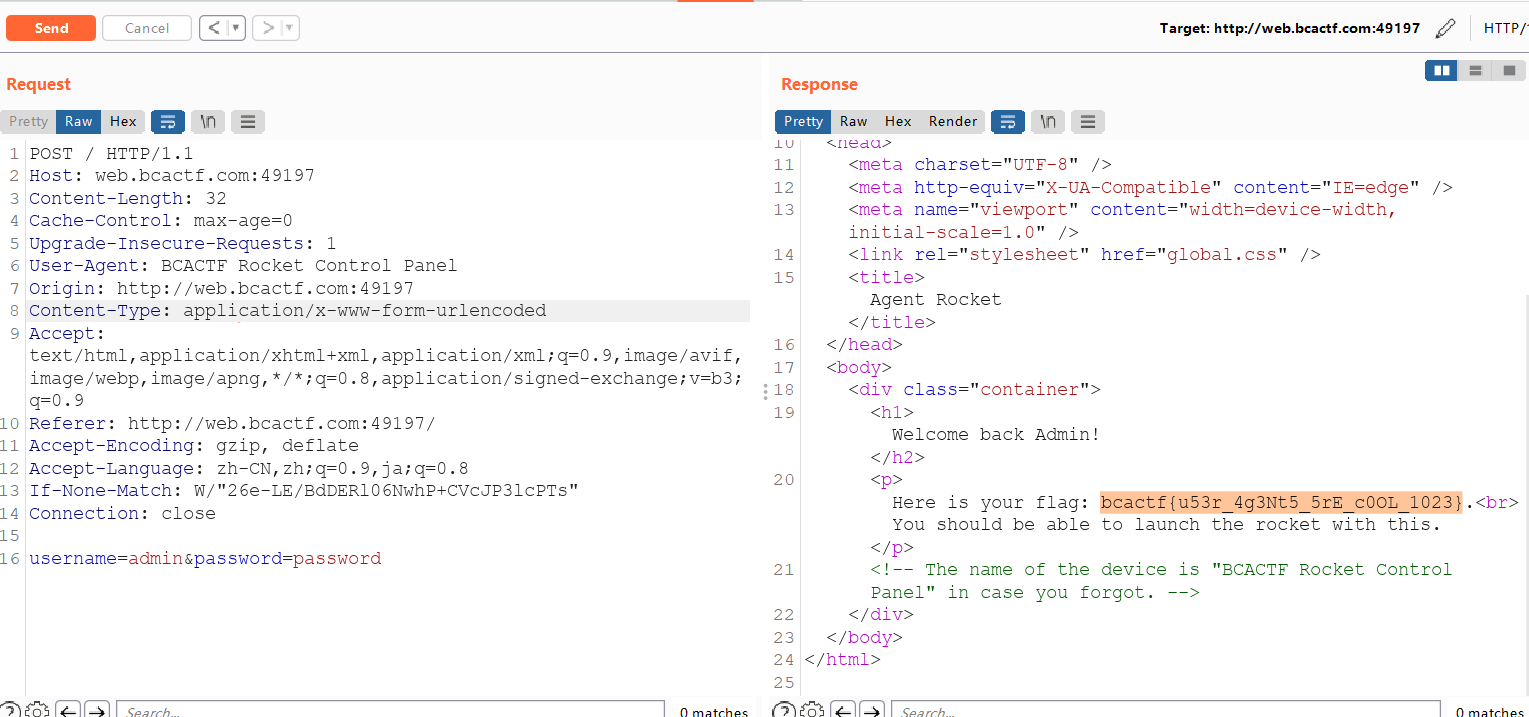
bcactf{u53r_4g3Nt5_5rE_c0OL_1023}
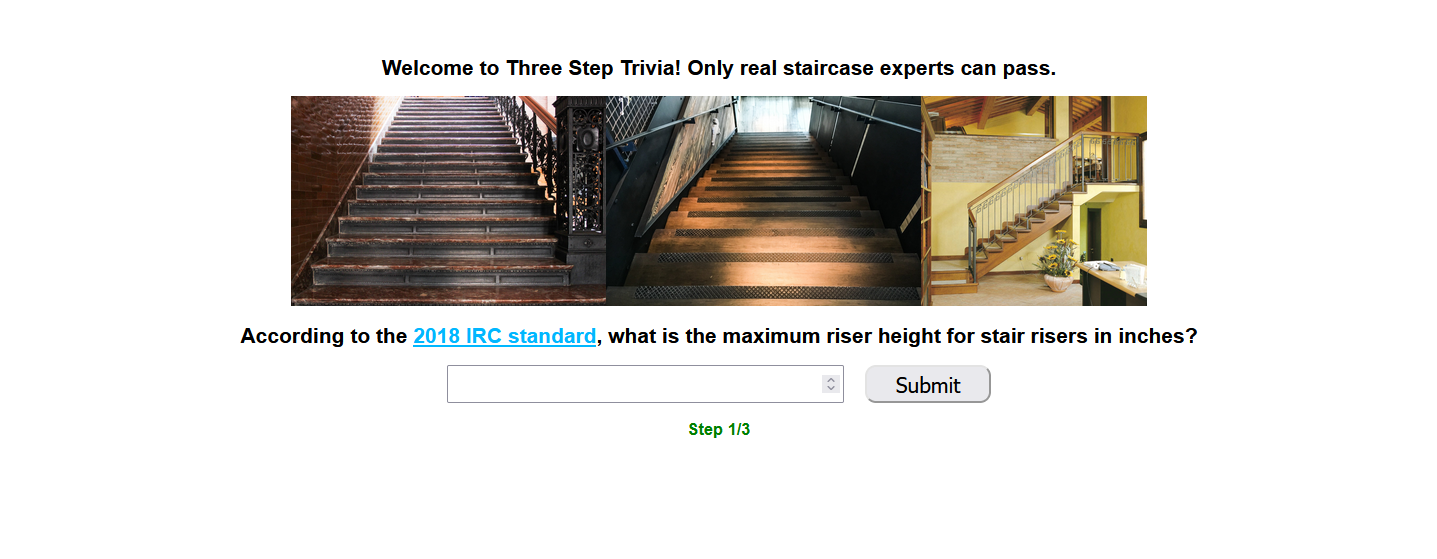
Three Step Trivia
Us at BCACTF love staircases so much that we decided to make a trivia quiz about them! Are you a staircase expert? Can you solve all three steps?
hint: The internet is a helpful resource
没啥巧,都是在网上直接搜
第一个答案是7.75英尺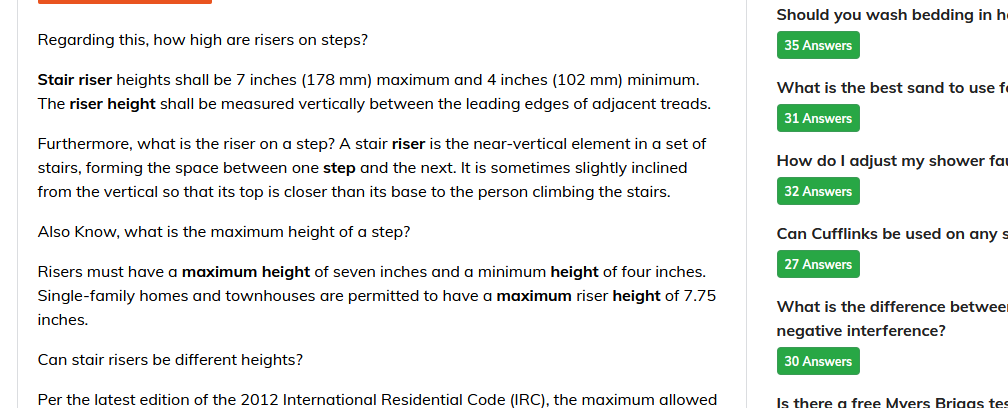
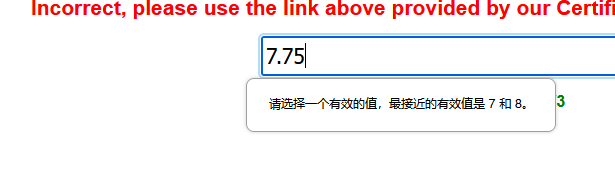
但是只输入7却显示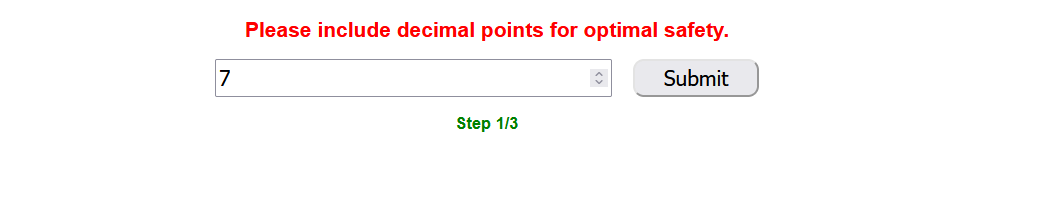
猜想是前端校验,f12改一下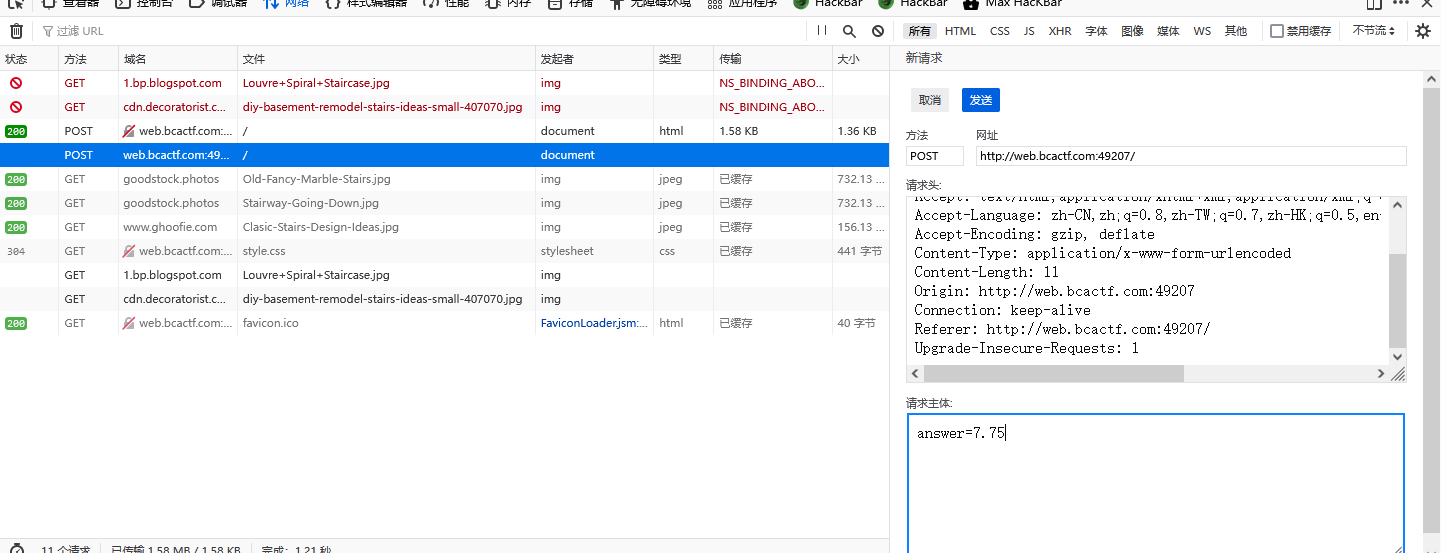
发送之后又得到个get请求,传7_75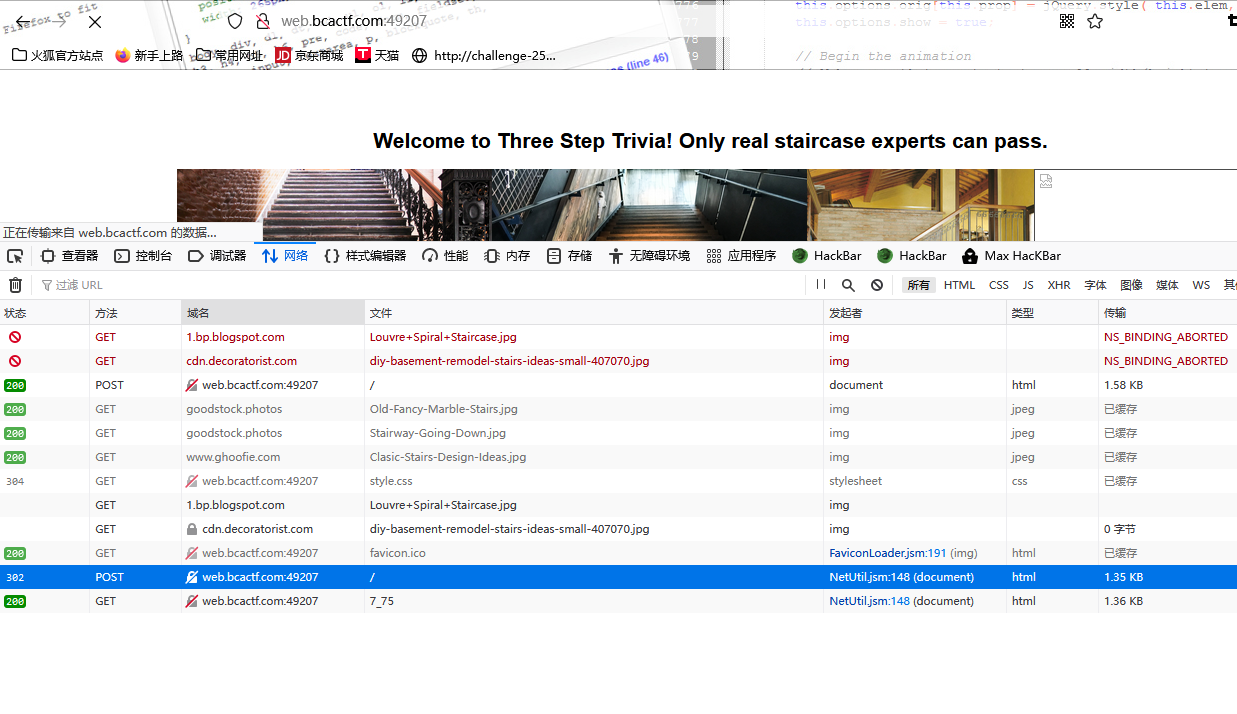
第二题
直接get传11674,第三题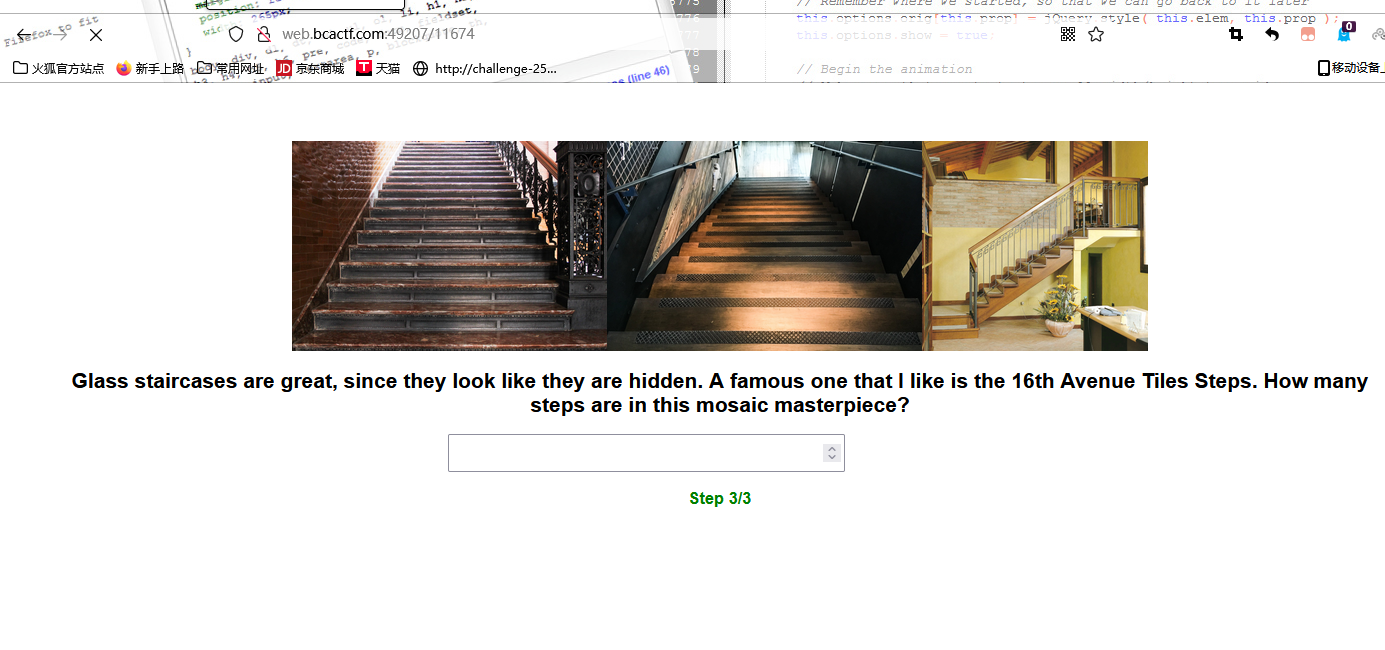
依然搜素,The 16th Avenue Tiled Steps project has been a neighborhood collaboration to create a sea to stars themed mosaic flowing up a 163 step stairway located in San Francisco’s Golden Gate Heights Neighborhood.
没有提交按钮,f12看一下
<button type="submit" class="btn" style="visibility: hidden;">Submit</button> // hidden-->visitibly
bcactf{sT41r_c4A3_m45T3R_5jfUn9Z}Cookies
Look, I made a website to teach you how to make cookies. There’s some other recipes there too, and I made a super secure portal to add more.
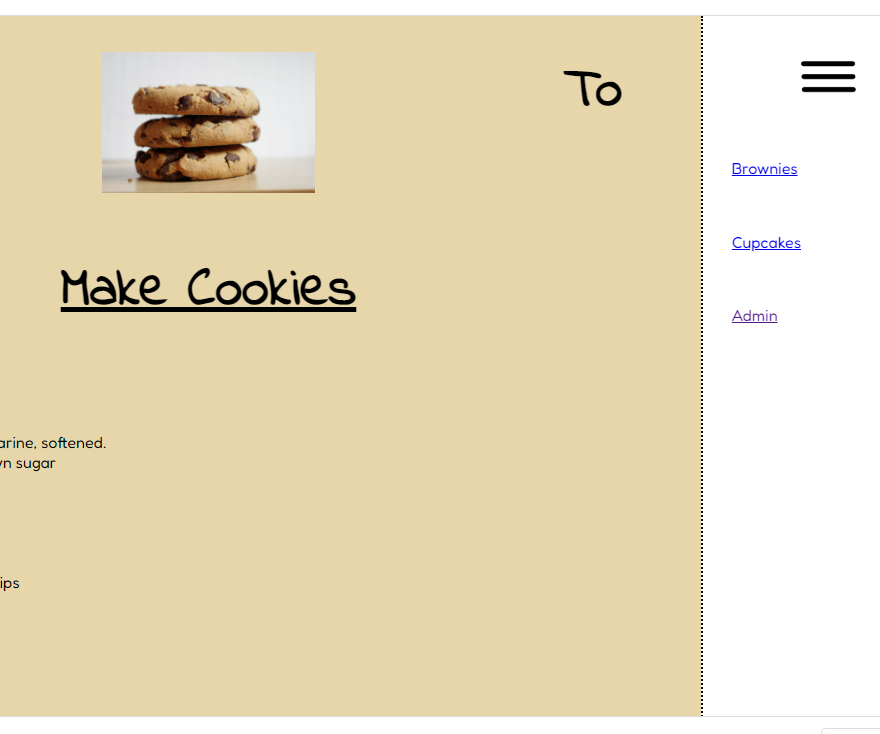
主界面长这个样子
目录里面有个admin,点进去发现是登陆后台的界面
看源代码,查看adminLog.js文件发现这段代码
function handleInput() {
let uname=unameElem.value;
if (uname != "admin") {
alert("You're not admin");
return;
}
let pwd = pwdElem.value;
let encodedPwd = fancyEncode(pwd);
setCookie("pwd", encodedPwd, 365);
window.location.replace("adminEditor.html");
}
//dont worry about the intricacies of the setCookie and getCookie functions
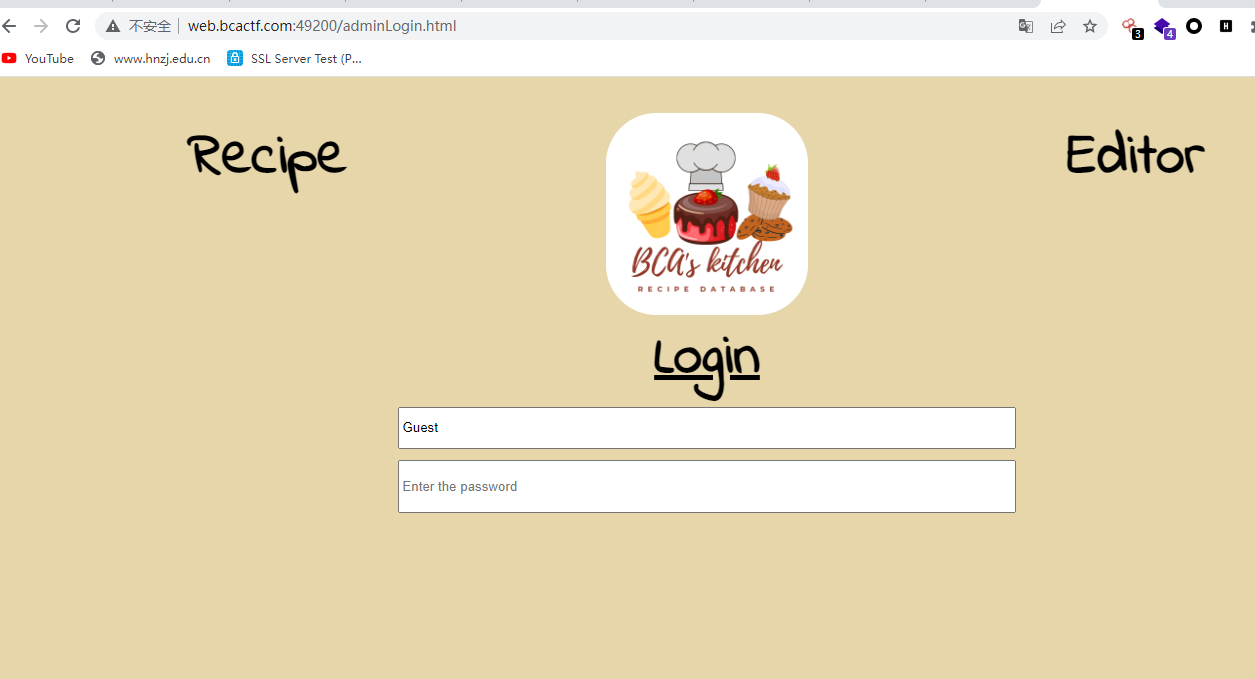
//just understand what they do and how to use them说明用户名需要修改成admin,密码的话貌似随便就行,然后就可正常登陆进去。
但是这个用户名初始是Guest,不能直接改,用f12改一下就可以。
登陆进去之后是空白页面,应该就是cookie问题吧,继续查看源代码,发现两个js文件,看一下editor.js文件,发现下面这段代码
if (getCookie("pwd") == "98e99e97e99e116e102e123e117e36e101e114e115e95e115e51e51e95e99e48e48e107e33e101e115e95e55e111e111e95e56e54e51e111e52e116e53e125e") {
window.location.replace("flag.html");
}意思就是把pwd这个cookie的值改成这些就会出来flag.html的页面内容,修改刷新得到flag。
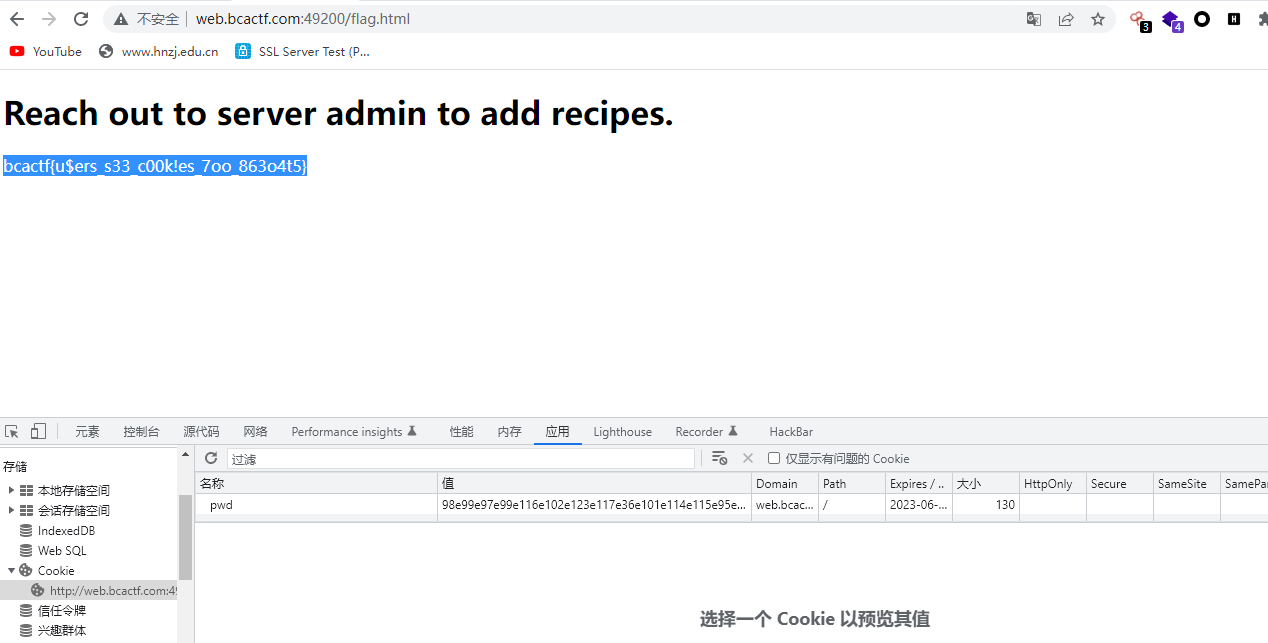
bcactf{u$ers_s33_c00k!es_7oo_863o4t5}
Misc
Broken Image
My friend said that he made a really cool drawing in MS Paint but I can’t open it! Maybe my computer is broken? Or the image? I really don’t know. Could you try opening it for me and telling me what it is?
下载个chall.svg,010查看是png格式,改后缀得到flag
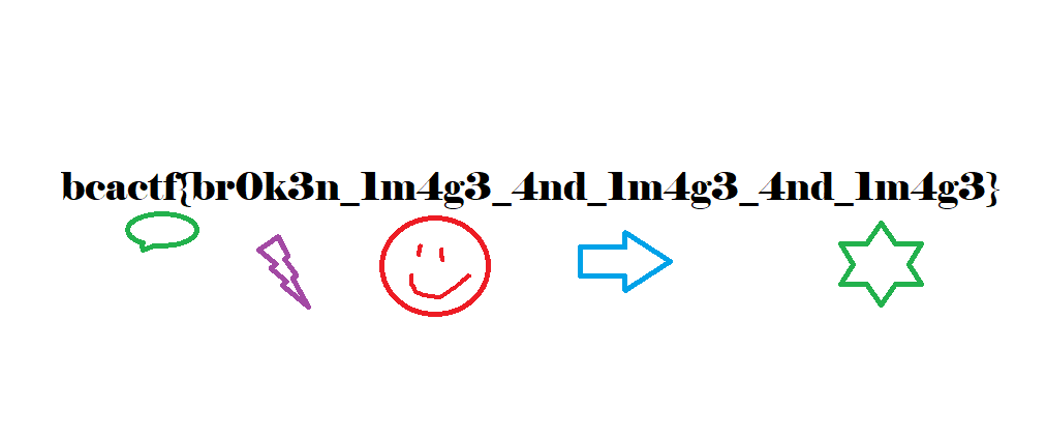
bcactf{br0k3n_1m4g3_4nd_1m4g3_4nd_1m4g3}
My New Friend
附件一个图片,lsb得到flag
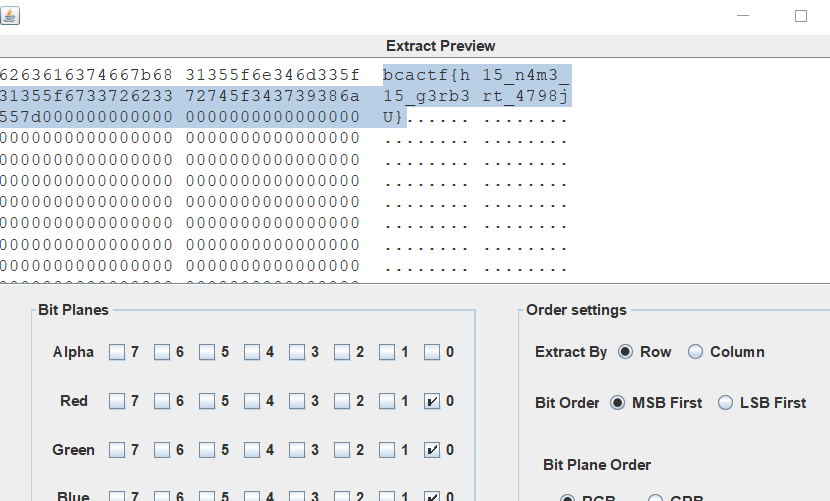
bcactf{h15_n4m3_15_g3rb3rt_4798jU}
pwn
Intro 2 Pwn
So… you want to learn how to pwn?
就是玩玩wpn,我不会,这个就是送分的,nc之后是这样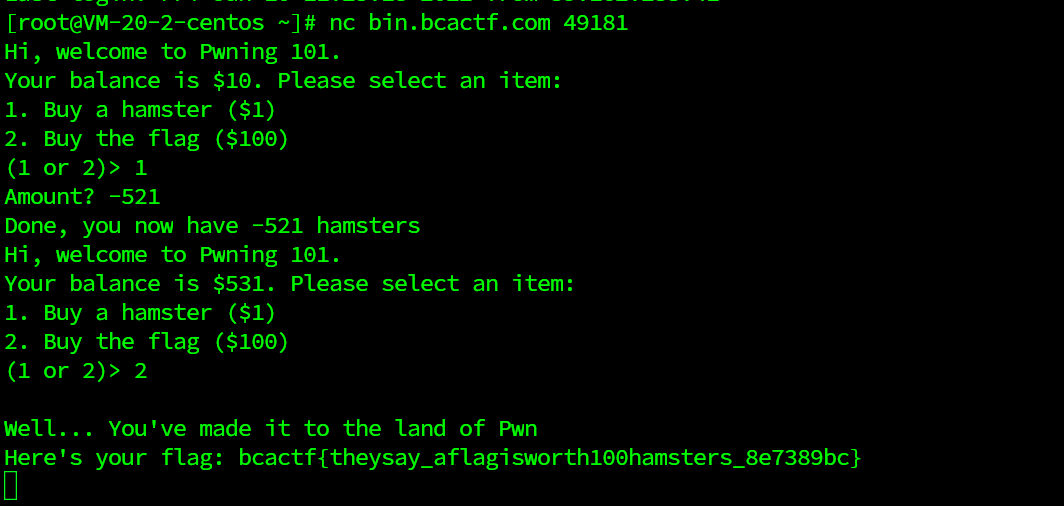
bcactf{theysay_aflagisworth100hamsters_8e7389bc}
